Chapter 1. Introduction to Cisco Software-Defined Wide Area Networking (SD-WAN)
This chapter covers the following topics:
Networks of Today: This section covers the technologies and challenges of today’s networks.
Common Business and IT Trends: This section of the chapter covers the most common trends having a considerable impact on the WAN.
Common Desired Benefits: This section examines the benefits and desired outcomes of what businesses are looking for.
High-Level Design Considerations: This section covers various aspects of WAN design and things that impact the deployment and operations of WANs today.
Introduction to Cisco Software-Defined WAN (SD-WAN): This section examines, from a high level, the benefits and drivers of Cisco SD-WAN.
Use Cases Demanding Changes in the WAN: This section covers a variety of use cases businesses are adopting that are putting pressure on the WAN environment.
Building an ROI to Identify Cost Savings: This section examines the potential cost savings of deploying Cisco SD-WAN and the value of a well-prepared return on investment (ROI).
Introduction to Multidomain: This section examines the purpose of Multidomain and the value associated with having a Mult,idomain environment.
Networks of Today
The IT industry is constantly changing and evolving. As time goes on, there is an ever-increasing amount of technologies putting a strain on the network. New paradigms are formed as others are being shifted away from. New advances are being developed and adopted within the networking realm. These advances are being created to provide faster innovation and the ability to adopt relevant technologies in a simplified way. This requires the need for more intelligence and the capability to leverage the data from connected and distributed environments such as the campus, branch, data center, and wide area network (WAN). Doing so allows for the use of data in interesting and more powerful ways than ever seen in the past. Some of the advances driving these outcomes are the following:
Artificial intelligence (AI)
Machine learning (ML)
Cloud services
Virtualization
Internet of Things (IoT)
The influx of these technologies is putting strain on the IT operations staff. This strain comes in the form of more robust planning, agreed-upon relevant use cases, and having detailed adoption journey materials for easy consumption. All these requirements are becoming critical to success. Another area of importance is the deployment and day-to-day operations of these technologies as well as how they fit within the network environment. Disruption to typical operations is more imminent with regards to some of these technologies and how they will be consumed by the business. Other advances in technology are being adopted to reduce cost of operations as well as reduce complexity. It can be said that every network, to some degree, has inherent complexity. However, having tools that can help manage this burden is becoming a necessity these days.
Automation is something that many in the industry are striving for. This is because the networks of today are becoming more and more complicated. Oftentimes businesses are operating with a lean IT staff, a flat or reduced budget, and are struggling to find ways to increase the output of what the network can do for the business. Another driver for the adoption of these technologies is improving the overall user experience within the environment. This includes users being able to have the flexibility and capability to access any business-critical application from anywhere in the network and have an exceptional experience. In addition to improving user experience, IT operations is searching for ways to simplify the operations of the network.
There are many inherent risks associated with manually configuring networks. There is risk in the form of not being able to move fast enough when deploying new applications or services to the network. Risk could also be seen as misconfigurations that could cause an outage or suboptimal network performance, resulting in impacted business operations and potentially causing financial repercussions. Finally, there is risk that the business itself, relying on the network for some business-critical services, might not be available due to the IT operations staff not being able to keep up with the scalability demand. According to a Cisco Technical Assistance Center (TAC) survey taken in 2016, 95% of Cisco customers are performing configuration and deployment tasks manually in their networks. The survey also stated that 70% of TAC cases created are related to misconfigurations. This means that typos or incorrectly used commands are the culprit for a majority of issues seen in the network environment. This is where automation shines: being able to have the capability to signify the intent of the change that needs to be made, such as deploying quality of service (QoS) across the network, and then having the network configure it properly and automatically. Consistently and correctly configuring services or features with great speed is a tremendous value to the business. Simplifying operations and reducing human error ultimately reduces risk.
A simple analogy for this would be to think of an automobile. As consumers of automobiles, most people use them to meet a specific desired outcome (in this case, it would be to get from point A to point B). An automobile is operated as a holistic system, not a collection of parts that make up that system. For example, there is a dashboard that provides the user all the necessary information of how the vehicle is operating and the current state of the vehicle. When the user wants to use the vehicle, there are certain operational steps required to do so. Drivers simply signify the intent to drive the car by putting it in gear and using the system to get from point A to point B. Figure 1-1 illustrates this analogy.

Figure 1-1 Automobile as a System
Why can’t networks be thought of in the same way? Thinking of a network as a collection of devices such as routers, switches, and wireless components is how the industry has been doing it for over 30 years. The shift in mindset to look at the network as a holistic system is a more recent concept that stems from the advent of network controllers. The splitting of role and functionality from one another can be described as separating the control plane from the data plane. Having a controller that sits on top of a collection of network devices gives the advantage of taking a step back and operating the network as a whole from a centralized management point—similar to operating an automobile from the driver’s seat versus trying to manage the automobile via individual pieces and components. To put this in more familiar terms, think of the command line interface (CLI). The CLI was not designed to make massive scale configuration changes to multiple devices at the same time. Traditional methods of managing and maintaining the network aren’t sufficient to keep up with the pace and demands of the networks of today. The IT operations staff needs to be able to move faster and simplify all the operations and configurations that have traditionally gone into networking. Cisco Software-Defined Networking (SDN) and controller capabilities are becoming areas of focus in the industry, and they are evolving to a point where they can address the challenges faced by IT operations teams. Controllers offer the ability to manage the network as a system, which means that policy management can be automated and abstracted. This provides the capability of supporting dynamic, scalable, and consistent policy changes throughout the network.
Common Business and IT Trends
Traditional networking infrastructure was deployed when the security perimeter was well defined. Most applications were low bandwidth, and most content and applications resided in centralized corporate data centers. Today, enterprises have very different requirements. High-bandwidth, real-time, and big-data applications are pushing the capacity limits of the network. In some cases, the majority of traffic is destined for the Internet or public cloud, and the security perimeter, as it existed in the past, is quickly disappearing. This is due to a surge in bring-your-own-device (BYOD), cloud, and dynamic business-to-business (B2B) ecosystems. The downside and risks of staying status quo are significant, and technological innovation has failed to comprehensively address the problem. There has been a huge increase in the use of Software as a Service (SaaS) and Infrastructure as a Service (IaaS) offerings. It seems as if more applications are moving to the cloud each day. The adoption of solutions like Microsoft Office 365, Google Apps, Salesforce.com (SFDC), and other SaaS-based productivity and business applications is not effectively addressed by traditional designs that utilize Internet capabilities out of one or more centralized data centers. The following list contains some of the most common trends being seen in the industry:
Applications are moving to the cloud (private and public)
Internet edge is moving to the remote branch sites
Mobile devices (BYOD and guest access)
High-bandwidth applications
IoT devices
The number of mobile devices at the remote sites accessing these applications and accessing the Internet as a result of BYOD and guest services is increasing. The additional load of traffic resulting from all of these devices as well as trends such IoT are putting an additional strain on the network. In addition to everything mentioned, interactive video has finally become the new voice-over IP. Converging voice and data services was an important transition. When it comes to video, however, today’s networks not only have to account for optimized QoS handling for video applications, but also need to address the high-bandwidth, latency-sensitive applications that users are demanding. This is going to require rethinking capacity planning to include looking for ways to maximize on current investments. Offloading certain types of traffic and moving to active/active WAN deployment models are some of the ways to accomplish this; however, traditionally these tasks are not easy to implement and require many manual configurations to deploy. Manual intervention when failover or redundancy was required was almost a must. This also led to additional complexity in the network environment.
With everything that was covered from a business and IT trend perspective still in mind, it is important to translate these trends into real challenges that businesses are facing and put them into IT vernacular. As mentioned previously, the WAN is seeing pressure like never before. This is forcing IT teams to look for ways to alleviate that pressure. Businesses are also looking for ways to improve the user and application experience with what they currently own as well as to drive cost down. Lack of control over visibility, application performance, and keeping up with the ever-growing security attack surface is also contributing to businesses looking for a better way forward. However, organizational silos have also caused many businesses to not be able to achieve the benefits from some of these newer technologies. Breaking down silos to work toward a common goal for the business as a whole is required for businesses to take full advantage of what some of these software-defined advancements have to offer.
Common Desired Benefits
This section of this chapter will cover some of the most common benefits that businesses are looking for from their network and WAN. Designing and deploying the next-generation WAN is about taking advantage of some very useful benefits and the impact they have on the network environment and overall user experience. Here is each of the benefits we will discuss:
Prioritize and secure traffic with granular control
Reduce costs and lower operational complexity
Augment or replace premium WAN bandwidth
Provide a consistent, high-quality user experience
Offload guest and public cloud traffic
Ensure remote site uptime
Oftentimes businesses want to augment or replace premium bandwidth services and move from active/standby WAN transport models to active/active models. This alone will help them to reduce costs. However, the challenge becomes that augmentation of services can increase operational complexity. Complexity is something that must be avoided as businesses look to simplify IT and create a consistent operational model. Ensuring remote site uptime to support business continuity is about more than simply protecting against blackout situations. Critical applications that are impacted by conditions such as latency, jitter, and loss can ultimately render the applications unusable. This is analogous to the applications being completely unavailable. These are called brownouts. Providing a consistent high-quality application experience is top of mind for most businesses today. Because not all applications are created equal, each organization or department might have its own applications that are critical to it and are required to support its business. Voice and video, for example, may be the most critical applications for one business, such as a contact center. However, in the retail vertical, the point of sales (PoS) system or online marketplace may be more critical. It comes down to the level of importance each application plays within a specific organization. Businesses demand the flexibility and power to prioritize applications with granular control. There is a shift to take back control and not have to rely on the service provider for making changes and for ensuring connectivity. This goes beyond typical routing or QoS and extends into application experience and availability. Many businesses are still not comfortable with the Internet edge moving into their remote site edge. This is necessary to more effectively support the rollout of public cloud applications such as Software as a Service (SaaS) and productivity applications. This is also needed for more optimized access to Infrastructure as a Service (IaaS). However, many businesses are interested in offloading guest traffic to directly attached Internet connectivity in remote branches. This is because it is better to offload this traffic locally rather than consume WAN bandwidth by routing it through a centralized data center for Internet services. This is not efficient and wastes expensive WAN bandwidth.
Networks of today cannot scale at the speed necessary to address the changing needs that the businesses require. Hardware-centric networks are traditionally more expensive and have fixed capacity. They are also more difficult to support due to the box-by-box configurations approach, siloed management tools, and lack of automated provisioning. Conflicting policies between domains and different configurations between services make them inflexible, static, expensive, and cumbersome to maintain. This leads to the network being more prone to misconfigurations and security vulnerabilities. It is important to shift from a connectivity-centric architecture to an application- or service-centric infrastructure that focuses on user experience and simplicity. Figure 1-2 shows the key factors affecting critical service level agreements (SLAs) that can disrupt business continuity.

Figure 1-2 Issues That Impact Critical SLAs
The solution required to support today’s cloud-enabled enterprise needs to be complete and comprehensive. It should be based on the software-defined approach mentioned earlier by leveraging the controller concept. The solution must also include a robust set of capabilities that reduce cost and complexity as well as promote business continuity and rapid innovation. These capabilities should include the separation of the management plane, control plane, and data plane. This will provide more horizontal scaling capabilities and the security of knowing where the data is at all times.
It should provide various consumption models, such as being hosted in the cloud or being managed on-premises, with complete redundancy between the two. The solution must also provide a complete set of network visibility and troubleshooting tools that are all accessible from a single place. Having this type of solution would assist in providing the following business outcomes and use cases:
Faster branch deployment with no operational interaction
Complete end-to-end network segmentation for enhanced security and privacy
Increased WAN performance
Topology independence
Better user experience
All of the things mentioned thus far are critical in terms of what businesses are demanding to drive their network into becoming an asset that truly sets them apart from their industry peers. Many organizations rely on the network to function at its best to provide value and competitive differentiation so their businesses can excel. This is what is driving the industry to these types of technologies. This is also why the industry has increased the speed of adoption and deployment of these solutions.
High-Level Design Considerations
Considering the complexity of a majority of the networks out there today, they can be classified in a couple of categories, such as redundant and non-redundant. Typically, redundancy leads to increased complexity. Oftentimes, the simplest of networks do not plan for failures or outages and are commonly single-homed designs with multiple “single points of failure.” Networks can contain different aspects of redundancy. There can be redundant links, routers, and service providers when speaking strictly of the WAN portion of the environment. Table 1-1 lists some of the common techniques introduced when dealing with redundancy.
Table 1-1 Common Redundancy Techniques
Redundant Links |
Redundant Devices |
|---|---|
Administrative distance |
Redistribution |
Traffic engineering |
Loop prevention |
Preferred path selection |
Preferred path selection |
Prefix summarization |
Advanced filtering |
Filtering |
Having a visual of what some of these topologies look like is often helpful. Figure 1-3 showcases some of these various topologies and their associated redundancy types, putting into context how the network will need to be configured and managed to support these types of redundancy options.
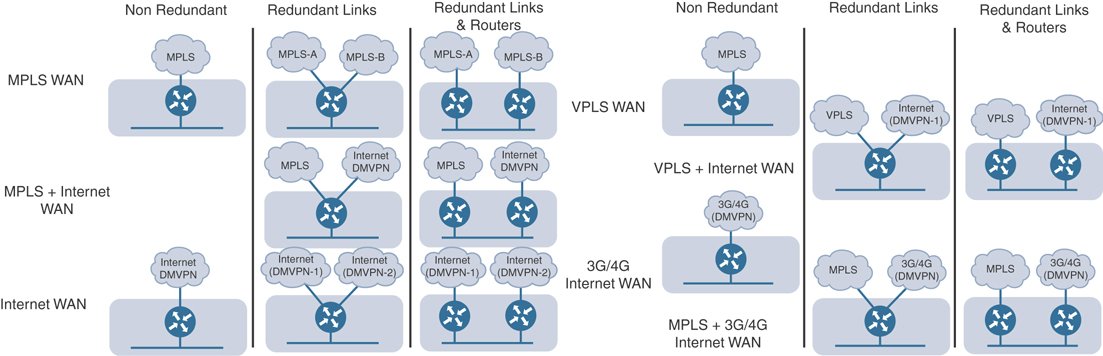
Figure 1-3 Topology-Based and Link Redundancy Options
Outside of the complexity associated with redundancy, there are many other aspects of the network that cause complexity within a network environment. Some of these aspects can include things such as securing the network, to shield it from malicious behavior; leveraging network segmentation, to keep traffic types separate for compliance or governance reasons; and even implementing quality of service (QoS), to ensure application performance and increase users’ quality of experience. What further complicates the network is having to manually configure these options. The networks of today are too rigid, and things need to evolve. The industry is moving from the era of connectivity-centric network delivery models to an era of digital transformation. A shift is required to transition to a digital transformation model. The shift is from hardware and device-centric options to open, extensible, software-driven, programmable and cloud-enabled solutions. Figure 1-4 depicts the transition in a simple summary. Intent-based networking (IBN) is taking the industry by storm. The concept revolves around signifying the intent of the business and automatically translating that intent into the appropriate corresponding networking tasks—relying more on automation to handle the day-to-day operational tasks and getting back time to focus on how to make the network provide value to the business. This is delivered through policy-driven, automated, and self-optimizing capabilities. This provides closed-loop, automated service assurance that will empower network operations staff to transition from a reactive nature to a more proactive and predictive approach. Freeing up more of the operations staff’s time will hopefully allow them to focus on more strategic initiatives within the business.

Figure 1-4 Digital Transformation Transition
Introduction to Cisco Software-Defined WAN (SD-WAN)
Shifting focus from a network-centric model to a business intent-based WAN network is a very powerful change. The WAN architecture can provide simplicity in terms of application deployment and management. However, the mindset must shift from a network topology focus to an application services topology. A common challenge for network operations staff is to support new and existing applications on the WAN. As mentioned previously in this chapter, these applications consume tremendous amounts of bandwidth and are very sensitive to variations in the quality of bandwidth that’s available. Things such as jitter, loss, and delay impact most applications, which makes it more important to improve the WAN environment for these applications. Furthermore, cloud-based applications such as Enterprise Resource Planning (ERP) and Customer Relationship Management (CRM) are placing bandwidth demands on the WAN. Non-flexible connectivity options to keep up with the growing amount of cloud applications requiring bandwidth make it costly and difficult to provision new applications and services. Most businesses today have to rely on service providers for MPLS L3VPN to control their WAN routing and network SLAs. This impacts their ability to change and adapt to application delivery methods such as cloud and SaaS. Service providers could take months to implement the necessary changes to their environment in order to support these applications. In addition, some service providers will charge their customers a large amount of money to make these changes, and some may not make the changes at all. Because service providers currently have control of the WAN core, there’s no way to instantiate VPNs independent of the underlying transport. Because of this, implementing differentiated service levels for individual applications becomes extremely difficult, if not impossible.
This is why the concept of hybrid WAN was originated. Hybrid WAN is where additional non-MPLS links are acquired by businesses and added to the WAN to provide alternate paths that the applications can take across the WAN environment. These are circuits that businesses have complete control over—from routing control to application performance. Typically, VPN tunnels are created over the top of these circuits to provide secure transport over any type of link. Examples of these types of links are commodity broadband Internet, L2VPN, wireless, and 4G/LTE. This provides what is called transport independence. This allows for the capability to use any type of transport underneath the VPN and get deterministic routing and application performance. This means that some applications can be sent over these commodity links versus the traditional service provider–controlled L3VPN MPLS links. This provides unique granularity of traffic control, redundancy, and resiliency. Figure 1-5 illustrates some common hybrid WAN topologies.

Figure 1-5 Common Hybrid WAN Topologies
Hybrid WANs need connectivity that is based on a service topology and can be centrally managed using policies. Currently, WAN connectivity is based on the network topology and managed using a peer-to-peer model. This means routing relationships are established by multiple control planes that operate independently of each other. Routing protocols such as Open Shortest Path First (OSPF) and Border Gateway Protocol (BGP) are used to establish site VPN routes, and IPsec is commonly used to secure the transport. These routing and security control planes run independently of each other and have their own scaling limitations, convergence requirements, and policy enforcement. This means each control plane is required to have its own independent policy and configuration. As a result, when a configuration change is required in the network, it has to be provisioned and propagated across all the control plane peers, for all transports, which creates operational pitfalls. This also creates the potential risk of misconfigurations or missing configuration that might cause applications to suffer.

Transport Independence
Cisco Software-Defined WAN (SD-WAN) leverages a transport-independent fabric technology that is used to connect remote locations together. This is accomplished by using an overlay technology. The overlay works by tunneling traffic over any kind of transport between any destination within the WAN environment. This is the VPN concept that was mentioned earlier in this chapter—for example, being able to connect remote branches that use MPLS to remote branches that use broadband Internet circuits. This gives true flexibility to routing applications across any portion of the network regardless of what type of circuit or transport is in use. This is the definition of transport independence. By having a fabric overlay network, it means that every remote site, regardless of physical or logical separation, is always a single hop away from another. This is of great benefit in terms of application latency and dynamic communication scenarios such as voice or interactive video. This not only provides increased simplicity in terms of network operations, but also provides seamless mobility from a user experience perspective. Transport independence is also one of the primary aspects of Cisco SD-WAN that allows for the use of flexible, lower-cost commodity circuits versus high-cost, inflexible static bandwidth. Although service providers can upgrade the bandwidth of a circuit, cost is usually a barrier. In addition, there are many times that, based on the type of circuit the bandwidth is riding on, an entire physical circuit upgrade or swap may be more likely. An example of this is having a 100Mbps MPLS handoff wherein the physical circuit it is delivered on is also only 100Mbps. In cases like this, another higher-speed port on the provider side is required, such as gigabit or 10-gigabit Ethernet ports. Many times, the circuit may ride over a different type of medium, and the entire circuit and delivery mechanism must be changed—for example, trying to go from a 45Mbps DS3 to a 1-gigabit Ethernet link. All of this takes time, and that is one of the things SD-WAN was created to address. Businesses can typically order a high-speed commodity Internet circuit and have it delivered within weeks. This new Internet circuit can be immediately added to the environment and taken advantage of by using SD-WAN. There are situations where multiple branch locations need to act as a single large branch across the WAN. This means having a virtual fabric over disparate transports such as MPLS and Internet. Given everything that has been covered thus far, it is important to show what an example of a Cisco SD-WAN diagram would look like. Figure 1-6 illustrates the high-level overview of a Cisco SD-WAN environment and how users, devices, and applications fit into the overall design.
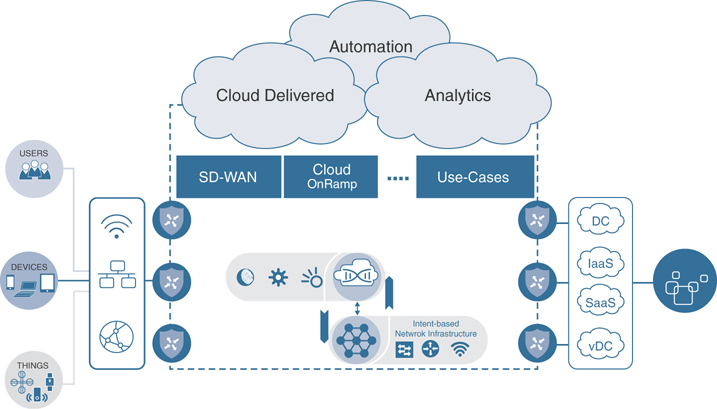
Figure 1-6 High-Level SD-WAN Overview
Moving from a network-centric WAN to an application- and services-focused WAN requires a different view of the wide area network. Figure 1-7 illustrates the new view of a business intent–based network, its components, and how they fit within the new model.
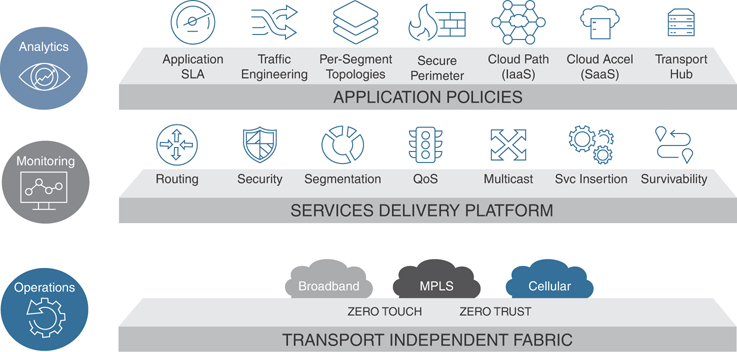
Figure 1-7 Business Intent–Based Network Components
Rethinking the WAN
If the current WAN technology and approach were to be redefined, it would have to include some fundamental changes to how WANs are constructed and managed today. These changes would involve the following key areas:
Secure elastic connectivity
Cloud-first approach
Application quality of experience
Agile operations
From a security perspective, end-to-end segmentation and policy are critical. The control, data, and management planes must be separated across the entire environment. The environment should be able to support native encryption that is robust and scalable, offer lightweight key management, and leverage a zero-trust model, meaning every aspect of the onboarding process must be authenticated and verified.
Rethinking the WAN from a connectivity perspective, these elements would be built on top of security functionality by integrating routing, security, and policy for optimal use of connectivity. The solution must allow for multiple types of transport connectivity options simultaneously and ultimately create a transport-independent operation model. Scale, both horizontally and vertically, is necessary at any layer. Additionally, advanced VPN capabilities and topologies to address any business intent or requirements are critical.
In terms of application support, the solution should support full application awareness across all elements in the system and offer built-in optimization techniques for the networks and applications. The network has evolved to be application aware, and it must be capable of choosing the most optimal path to connect to on-premises or cloud-based applications. The application experience must be optimal in terms of both access and security.
When it comes to the operation of this new application- and services-oriented WAN, network operations staff must be able to define network-wide policies that leverage templates, rather than just a device- or node-level policy. The controller must have the ability to coordinate the paths between the WAN Edge routers, based on centralized policy orchestration. As organizations’ network requirements change and evolve over time, the policy should be able to be changed in one single place. This not only reduces the amount of time spent on configuration, but it also lowers the risk associated with misconfiguration errors as well. Programmable, open application programming interfaces (APIs) should be available to provide northbound access for automation and orchestration capabilities. Support of southbound APIs for integration with other solutions should also be included.
Use Cases Demanding Changes in the WAN
In this day and age, there are many reasons to look at enhancing the WAN environment—from load-balancing traffic to ensuring applications have the best performance possible. The following sections cover some of the use cases causing changes to the WAN.
Bandwidth Aggregation and Application Load-Balancing
There are many different use cases that demand changes to the way WANs are handled today. Some are as simple as businesses wanting bandwidth aggregation. This is the ability to use both public and private transports together at the same time. This is what is considered using A + B versus A or B, meaning the secondary transport link (Link B) usually sits idle without any traffic using it until Link A fails. However, in a hybrid WAN approach, being able to leverage multiple links at the same time provides an ability to use bandwidth from both links. This is considered an A + A or an Active/Active scenario. Application load-balancing is achieved using these types of designs as well. This type of hybrid environment allows for greater application performance at a fraction of the cost of two premium transport links. This also increases scale and flexibility without any security compromise. Figure 1-8 illustrates the various options of application load-balancing over multiple links in a hybrid environment. You can see that, by default, per-session Active/Active load-sharing is achieved. Weighted per-session round-robin is also configurable on a device basis. Application pinning, or forcing an application to take a specific transport, is also something that can be enforced via policy. Similarly, Application-Aware Routing or SLA-compliant routing is achieved by enforcing a policy that looks for specific traffic characteristics such as jitter, loss, and delay to determine the path the application should take over the available transports.

Figure 1-8 Application Load-Balancing Options

Protecting Critical Applications with SLAs
Another use case that drives changes in the WAN is the capability to provide an SLA for critical applications. This is accomplished by being able to route traffic based on the application requirements, as mentioned briefly earlier. This also provides statistics on how the applications are performing. Based on the policy that can be created, an SLA determines if the application is adhering to that policy, and performing properly, or if it is experiencing some sort of detriment such as jitter, loss, or delay. If this is the case, the application can be routed to another transport that will ensure the application is within policy and able to perform to the SLA that is expected of it. Figure 1-9 illustrates this particular scenario. A good example of this in a hybrid WAN environment would be an MPLS link and an Internet link. If the MPLS link is experiencing 5% packet loss and the Internet link is not, it might be appropriate to route the application over the Internet link to ensure that the application is functioning properly and users are having the best experience interacting with the application.
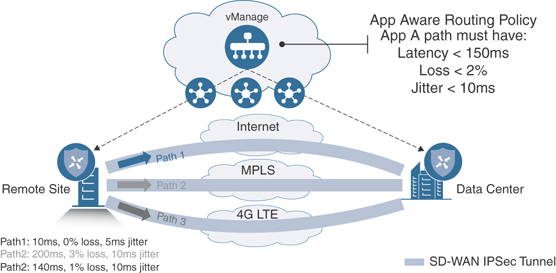
Figure 1-9 Routing Based on Application Performance
End-to-End Segmentation
Segmentation is another use case that drives these changes in the WAN. Oftentimes, businesses have different departments that require separation. For example, Research and Development may need to be segmented from the Production environment. There may be extranets that connect to partners, or the business may be merging or acquiring another business in which the networks need to be able to communicate but segmentation may still be required between the two. This may require multiple topologies that can be managed as one. Figure 1-10 depicts an end-to-end segmentation topology, along with how different VPNs are carried over the tunnels. Each of these tunnels terminates at an edge router within the environment.

Figure 1-10 End-to-End Segmentation

Direct Internet Access
One of the most common use cases is something called Direct Internet Access (DIA). DIA gives branches the capability to send traffic directly out of the local Internet transport instead of carrying it all the way back to a centralized data center to be inspected. This allows for cloud-based applications to go directly to the Internet and cloud service providers without having to use unnecessary WAN bandwidth. This is increasingly becoming the method that is being adopted. Figure 1-11 depicts the traditional way that cloud applications are accessed. This causes suboptimal performance for users trying to access these applications. This also, as mentioned earlier, puts a strain on the WAN infrastructure, as the expensive and limited WAN bandwidth is being consumed by applications that could be sent directly to the Internet from the remote site. This also introduces increased application latency, as the traffic has to cross the entire network to get to the data center to reach the Internet.

Figure 1-11 Traditional Cloud Application Access via WAN
Looking at changing and rethinking the WAN allows for different mechanisms that will allow for better performance and scale. A great example of this is using the Direct Internet Access design to offload the latency-sensitive cloud applications directly to the Internet. This method also gives the flexibility to have a local firewall or inspection device in the branch to ensure the branch is protected from any malicious threats coming into the local branch Internet link.
Figure 1-12 shows an example of what this would look like in a new WAN environment.
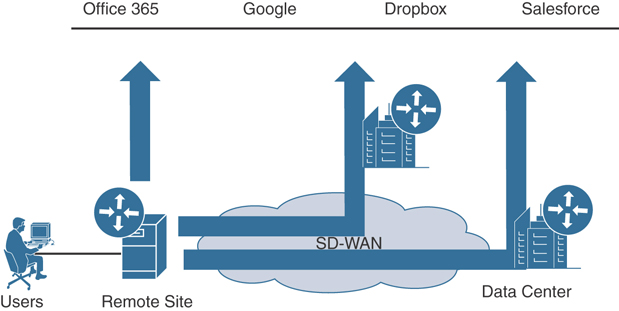
Figure 1-12 Direct Internet Access and Cloud Access Topologies
Fully Managed Network Solution
Finally, there is a use case that allows for the business to simply let someone else, such as Cisco or a Cisco Partner, manage the network as a fully managed solution. This provides the flexibility to not only have the network managed as a whole for the business, but also to allow the business to have control over the policy and reporting portion of the managed service. This is becoming a more attractive option for customers who want to move to an OpEx model. This allows them to pay for their network on a subscription basis versus the traditional CapEx model and is analogous to paying an electric or cell phone bill. The consumption models available today are really opening up new options for customers.
Note
All of these use cases and technologies will be covered in detail in the coming chapters of this book.
Building an ROI to Identify Cost Savings
A really important exercise when looking at Cisco SD-WAN is to build a quantifiable return on investment (ROI). Oftentimes businesses investigating Cisco SD-WAN find that removing certain expensive links and leveraging high-speed commodity Internet links for transport not only lowers the overall cost of the WAN but also adds redundancy and resiliency. Typically, these benefits weren’t realized in the environment prior to moving to Cisco SD-WAN.
There are many companies that provide these ROI models at no cost to the customer and have proven to be an almost mandatory step in the Cisco SD-WAN journey. Some customers have seen enough cost savings and increases in overall bandwidth that the project was completed without any additional costs to the business. Figure 1-13 shows an example of an ROI calculation. Note the staggering details of a 64% cost savings from moving from a dual MPLS link design to a dual commodity Internet link design. At the very least, this proves the exercise is worthwhile to complete prior to getting started with implementation and deployment.

Figure 1-13 Simple ROI Calculation Example
Note
These numbers were taken from a real customer example. However, every business will have different ROI calculations based on cost of circuits, type of circuits, and location. These numbers are examples only and will be different for anyone reading this book or having ROI calculations performed on their own environment.

Introduction to Multidomain
A common trend arising in the industry is data being generated and stored in many areas of the network. Traditionally, a majority of the data for a business was stored in a centralized data center. With the influx of guest users, mobile devices, bring your own device (BYOD), and Internet of Things (IoT), data is now being generated remotely in a distributed manner. This means the industry is shifting from data centers to multiple centers of data. That being said, simple, secure, and highly available connectivity is a must to allow for enhanced user and application experience. The other big piece to this is having a seamless policy that can go across these multiple centers of data. An example of this is policy that extends from the campus environment across the WAN and into the data center and back down to the campus. This provides consistency and deterministic behavior across multiple domains. Figure 1-14 illustrates a high-level example of sharing policy between a campus branch location and a data center running Cisco Application Centric Infrastructure (ACI).
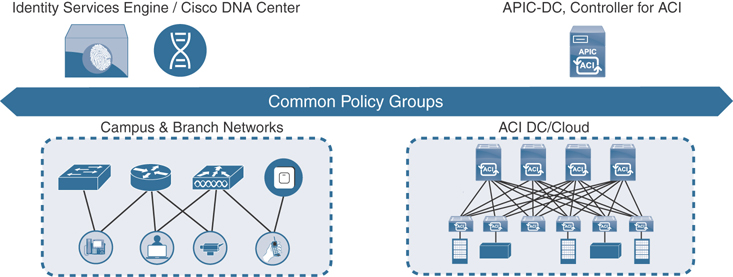
Figure 1-14 High-Level Multidomain Example
In future evolutions of Multidomain, the common policy will consequently provide end-to-end policy management across all three domains. This gives the capability of leveraging things like application SLAs from the data center to the WAN and back. This ensures the applications are performing to the best of their ability across the entire network, relieving strain on the WAN and providing a better user experience when using the applications. Figure 1-15 shows a high-level example of what this could look like from a topology perspective.
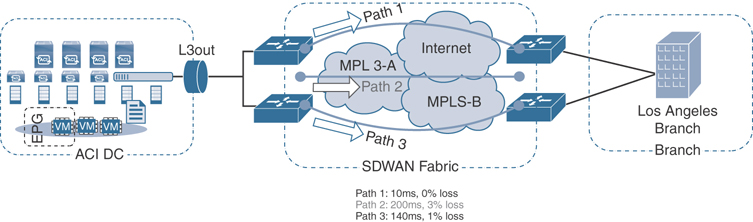
Figure 1-15 High-Level Multidomain and SD-WAN Example
Multidomain offers the capability to have the network operate as a holistic system, as mentioned previously in this chapter. This takes intent-based networks to the next level by taking policy across all domains for a seamless application experience. This also implements security everywhere and provides complete granularity in terms of control and operations.
Cloud Trends and Adoption
Cloud adoption has been taking the industry by storm. Over the years the reliance on the cloud has grown significantly, starting with music, movies, and storage and moving into Software as a Service (SaaS) and Infrastructure as a Service (IaaS). Today, there are many aspects of businesses such as application development, quality assurance, and production that are running in the cloud. To make things even more complicated, companies are relying on multiple cloud vendors to operate their business. This requires unique sets of polices, storage capacity requirements, and overall operational skills on a per-vendor basis. Companies are also struggling with things such as shadow IT and backdoor applications in their environment. This means that lines of business are going to cloud providers on their own without any knowledge or guidance from IT departments and spinning up applications on demand in the cloud. This causes major concerns from a security and privacy perspective. In addition, the potential loss of confidential information or intellectual property could damage the brand and reputation of the business. The risks are significant. Furthermore, the applications in the cloud, whether legitimate production or development, still require certain levels of priority and treatment to ensure the applications are being delivered properly to the users who consume them. This is where some of the capabilities of Cisco SD-WAN can help to ensure the applications are being treated appropriately and the experience for the users is adequate. Figure 1-16 illustrates the demand on the WAN and how the Internet is becoming critical to the operations of the business.

Figure 1-16 Demand on WAN for Internet-Based Applications
Having Direct Internet Access can assist with this, as mentioned earlier. By being able to detect application performance through one or more Direct Internet Access circuits, the edge routers are able to choose the best-performing path based on the application-specific parameters. If one of the links to the cloud application fails or has degradation in performance, the application can automatically fail over to another direct Internet link. This process is fully automated and requires no interaction from the network operations staff. Figure 1-17 shows this scenario with multiple Direct Internet Access links.

Figure 1-17 Multiple Direct Internet Access Links to Cloud Applications
This concept also works in environments that have a remote branch site that has a local direct Internet link as well as an Internet link within a centralized data center. The same process takes place in that the application performance is measured and the path that provides the best performance will be the path chosen for the application. Similarly, blackout or link failures will also be protected against because of redundancy built into the solution by having multiple available paths. Figure 1-18 depicts this scenario of having a local directly attached Internet link and an Internet link available in a centralized data center. Again, this leaves the router to make the decision based on the policy and application parameters that were configured. Not only are these decisions fully automated and made on a per-application and per-VPN basis, but ultimately an amazing amount of flexibility and control over the application performance within the environment is provided.

Figure 1-18 Direct Internet Access and Centralized Internet Link to Cloud Applications
Summary
This chapter covered a high-level overview of how the networks of today are causing challenges for businesses and their operations staff. The common business and IT trends the industry is seeing and how they impact the networks of today were also covered. The overall benefits desired by organizations and their IT staff lead to the need to rethink the WAN environment. Cloud applications and the influx of the amount of data within the network are causing strain on the WAN. This is causing businesses to look at ways to alleviate the pressure being put on the WAN and the organization as a whole. The use cases covered in this chapter will each be covered in depth in the upcoming chapters in this book. Cost is not the only driver for organizations to look at SD-WAN. Application performance, security, segmentation, improved user experience, redundancy, and resiliency are also key drivers that point to SD-WAN.

Review All Key Topics
Review the most important topics in this chapter, noted with the Key Topic icon in the outer margin of the page. Table 1-2 lists these key topics and the page numbers on which each is found.
Table 1-2 Key Topics for Chapter 1
Key Topic Element |
Description |
Page Number |
|---|---|---|
Section |
Transport Independence |
10 |
Section |
Protecting Critical Applications with SLAs |
14 |
Paragraph |
Direct Internet Access |
15 |
Section |
Introduction to Multidomain |
18 |
Key Terms
Define the following key terms from this chapter and check your answers in the glossary:
Software-Defined Networking (SDN)
Infrastructure as a Service (IaaS)
application programming interface (API)
Cisco Software-Defined WAN (Cisco SD-WAN)
Chapter Review Questions
1. What are some of the common IT trends putting pressure on the WAN? (Choose three.)
IoT
Cloud
Fog computing
BYOD
Low-bandwidth applications
2. What are some benefits businesses are looking for from their WAN? (Choose three.)
Lower operational complexity
Increased usable bandwidth
Reduced uptime in branch locations
Topology dependence
Improved overall user experience
3. What are some of the tools or technologies that may be necessary to implement when redundant links are used in branch locations? (Choose three.)
Administrative distance
Traffic engineering
Redistribution
Loop prevention
Preferred path selection
4. Part of having an intent-based network is to move to a hardware-centric approach.
True
False
5. Which of the following are part of the digital transformation journey? (Choose two.)
Automated
Manual
Proactive
Reactive
Predictive
6. Organizations are looking to deploy SD-WAN for what reasons? (Choose two.)
To take all routing control from the service provider
To create end-to-end SLAs for the organization’s traffic
To offload all routing control to the service provider
To leverage the service provider’s SLA for end-to-end traffic
7. What are some of the benefits of SD-WAN? (Choose four.)
Lower cost
Improved user experience
Transport independence
Increased cloud consumption
IoT devices
Increased bandwidth
8. What are some of the transport options for SD-WAN? (Choose three.)
Dual MPLS
Hybrid WAN
Dual route processor
Hybrid single link
Dual Internet
9. Direct Internet Access is used to offload applications directly to the data center.
True
False
10. What is one of the benefits of Cisco Multidomain?
Single policy across multiple environments
Multiple policies across single domain
Simplified reporting for IoT devices
Enhanced service provider support
