Chapter 19
Security
THE FOLLOWING COMPTIA A+ 220–902 EXAM OBJECTIVES ARE COVERED IN THIS CHAPTER:
- ✓ 3.1 Identify common security threats and vulnerabilities.
- Malware: spyware, viruses, worms, trojans, rootkits, ransomware
- Phishing
- Spear phishing
- Spoofing
- Social engineering
- Shoulder surfing
- Zero day attack
- Zombie/botnet
- Brute forcing
- Dictionary attacks
- Non-compliant systems
- Violations of security best practices
- Tailgating
- Man-in-the-middle
- ✓ 3.2 Compare and contrast common prevention methods.
- Physical security: Lock doors, Mantrap, Cable locks, Securing physical documents/passwords/shredding, Biometrics, ID badges, Key fobs, RFID badge, Smart card, Tokens, Privacy filters, Entry control roster
- Digital security: antivirus/antimalware, firewalls, user authentication/strong passwords, multifactor authentication, directory permissions, VPN, DLP, disabling ports, access control lists, smart card, email filtering, trusted/untrusted software sources
- User education/AUP
- Principle of least privilege
- ✓ 3.3 Compare and contrast differences of basic Windows OS security settings.
- User and groups: administrator, power user, guest, standard user
- NTFS vs. Share permissions: allow vs. deny, moving vs. copying folders and files, file attributes
- Shared files and folders: administrative shares vs. local shares, permission propagation, inheritance
- System files and folders
- User authentication: single sign-on
- Run as administrator vs. standard user
- Bit-locker
- Bit-locker-To-Go
- EFS
- ✓ 3.4 Given a scenario, deploy and enforce security best practices to secure a workstation.
- Password best practices: setting strong passwords, password expiration, changing default user names/passwords, screensaver required password, BIOS/UEFI passwords, requiring passwords
- Account management: restricting user permissions, login time restrictions, disabling guest account, failed attempts lockout, timeout/screen lock
- Disable autorun
- Data encryption
- Patch/update management
- ✓ 3.5 Compare and contrast various methods for securing mobile devices.
- Screen locks: fingerprint lock, face lock, swipe lock, passcode lock
- Remote wipes
- Locator applications
- Remote backup applications
- Failed login attempts restrictions
- Antivirus/antimalware
- Patching/OS updates
- Biometric authentication
- Full device encryption
- Multifactor authentication
- Authenticator applications
- Trusted sources vs. untrusted sources
- Firewalls
- Policies and procedures: BYOD vs. corporate owned, profile security requirements
- ✓ 3.6 Given a scenario, use appropriate data destruction and disposal methods.
- Physical destruction: shredder, drill/hammer, electromagnetic (degaussing), incineration, certificate of destruction
- Recycling or repurposing best practices: low level format vs. standard format, overwrite, drive wipe
- ✓ 3.7 Given a scenario, secure SOHO wireless and wired networks.
- Wireless specific: changing SSID, setting encryption, disabling SSID broadcast, antenna and access point placement, radio power levels, WPS
- Change default user names and passwords
- Enable MAC filtering
- Assign static IP addresses
- Firewall settings
- Port forwarding/mapping
- Disabling ports
- Content filtering/parental controls
- Update firmware
- Physical security
Think of how much simpler an administrator’s life was in the days before every user had to be able to access the Internet. Think of how much simpler it must have been when you only had to maintain a number of dumb terminals connected to a minitower. Much of what has created headaches for an administrator since then is the inherent security risk that comes about as the network expands. As our world—and our networks—have become more connected, the need to secure data and keep it away from the eyes of those who can do harm has increased exponentially.
Realizing this, CompTIA added the security domain to the A+ exams a few years back. Security is now a topic that every administrator and technician must not only be aware of and concerned about, they must also be actively involved in implementing methods to enforce and monitor it. In the world of production, quality may be job one, but in the IT world, it is security.
This chapter looks at security primarily from the standpoint of what you need to know to pass the exam. All of the topics relevant to the security domain of the 220–902 exam are covered, and a thorough overview of each topic is provided.
Common Prevention Methods
A great number of the security issues that plague networks today can be solved through the implementation of basic security elements. Some of those elements are physical (locked doors) and others are digital (antivirus software), but all share in common the goal of keeping problems out.
Six topic areas are key: physical security, digital security, user education, the principle of least privilege, email security, and VPNs. As you study for the exam, know the types of physical security elements that you can add to an environment to secure it. Know, as well, what types of digital security you should implement to keep malware at bay. Understand that the first line of defense is the user. You need to educate users to understand why security is important, and you need to impose the principle of least privilege to prevent them from inadvertently causing harm.
Physical Security
Physical security is a grab bag of elements that can be added to an environment to aid in securing it. It ranges from key fobs to retinal scanners. In the following sections, we will examine the list of components in the order in which CompTIA lists them.
Lock Doors
One of the easiest ways to prevent those intent on creating problems from physically entering your environment is to lock your doors and keep them out. A key aspect of access control involves physical barriers. The objective of a physical barrier is to prevent access to computers and network systems. The most effective physical barrier implementations require that more than one physical barrier be crossed to gain access. This type of approach is called a multiple-barrier system.
Ideally, your systems should have a minimum of three physical barriers. The first barrier is the external entrance to the building, referred to as a perimeter, which is protected by burglar alarms, external walls, fencing, surveillance, and so on. An access list or entry control roster should exist to identify specifically who can enter and can be verified by a guard or someone with authority. The second barrier is the entrance into the building, and it could rely upon such items as ID badges to gain access. The third barrier is the entrance to the computer room itself (and could require key fobs, or just keys to locks). Each of these entrances can be individually secured, monitored, and protected with alarm systems.
Although these three barriers won’t always stop intruders, they will potentially slow them down enough so that law enforcement can respond before an intrusion is fully developed. Inside, a truly secure site should be dependent upon a physical security token for access to the actual network resources.
Tailgating
Tailgating refers to being so close to someone when they enter a building that you are able to come in right behind them without needing to use a key, a card, or any other security device. Many social engineering intruders needing physical access to a site will use this method of gaining entry. Educate users to beware of this and other social engineering ploys and prevent them from happening.
Securing Physical Documents/Passwords/Shredding
The type and amount of information that can be gleaned from physical documents is amazing, even in the age when there is such a push to go paperless. Dumpster diving is a common problem that puts systems at risk. Companies normally generate a huge amount of paper, most of which eventually winds up in dumpsters or recycle bins. Dumpsters may contain information that is highly sensitive in nature (such as a password a user has written on a piece of paper because they haven’t memorized it yet). In high-security and government environments, sensitive papers should either be shredded or burned. Most businesses don’t do this. In addition, the advent of “green” companies has created an increase in the amount of recycled paper, which can often contain all kinds of juicy information about a company and its individual employees.
Biometrics
Biometric devices use physical characteristics to identify the user. Such devices are becoming more common in the business environment. Biometric systems include fingerprint/palm/hand scanners, retinal scanners, and soon, possibly, DNA scanners. To gain access to resources, you must pass a physical screening process. In the case of a hand scanner, this may include identifying fingerprints, scars, and markings on your hand. Retinal scanners compare your eye’s retinal pattern to a stored retinal pattern to verify your identity. DNA scanners will examine a unique portion of your DNA structure to verify that you are who you say you are.
With the passing of time, the definition of biometrics is expanding from simply identifying physical attributes about a person to being able to describe patterns in their behavior. Recent advances have been made in the ability to authenticate someone based on the key pattern that they use when entering their password (how long they pause between each key, the amount of time each key is held down, and so forth). A company adopting biometric technologies needs to consider the controversy they may face (some authentication methods are considered more intrusive than others). The error rate also needs to be considered, along with an acceptance of the fact that errors can include both false positives and false negatives.
Badges
Badges can be any form of identification intended to differentiate the holder from everyone else. This can be as simple as a name badge or photo ID.
Smart cards are difficult to counterfeit, but they’re easy to steal. Once a thief has a smart card, they have all the access the card allows. To prevent this, many organizations don’t put any identifying marks on their smart cards, making it harder for someone to utilize them. A password or PIN is required to activate many modern smart cards, and encryption is employed to protect the card’s contents.
Key Fobs
Key fobs are named after the chains that used to hold pocket watches to clothes. They are security devices that you carry with you; they display a randomly generated code that you can then use for authentication. This code usually changes very quickly (every 60 seconds is probably the average), and you combine this code with your PIN for authentication. RSA is one of the most well-known vendors of key fobs.
Multifactor Authentication Anytime more than one item (factor) is needed to authenticate a user, this is known as multifactor authentication. It may take two, three, or four factors to authenticate, but as long as it is more than one, as the name implies, it is known as multifactor. One of the most common examples where this is used in everyday life is at the bank’s ATM machine. In order to withdraw money, a user must provide a card (one card factor) and a PIN (a second factor). If you know the PIN number but do not have the card, you cannot get money from the machine. If you have the card but do not have the PIN number, you cannot get money from the machine.
RFID Badges and Smart Cards
A smart card is a type of badge or card that gives you access to resources, including buildings, parking lots, and computers. It contains information about your identity and access privileges. Each area or computer has a card scanner or a reader in which you insert your card. Radio frequency identification (RFID) is the wireless, no-contact technology used with these cards and their accompanying reader.
The reader is connected to the workstation and validates against the security system. This increases the security of the authentication process because you must be in physical possession of the smart card to use the resources. Of course, if the card is lost or stolen, the person who finds the card can access the resources it allows.
RSA Tokens
Physical tokens are anything that a user must have on them to access network resources, and they are often associated with devices that enable the user to generate a one-time password authenticating their identity. SecurID, from RSA, is one of the best-known examples of a physical token, and information on that series of products can be found at
www.emc.com/security/rsa-securid/rsa-securid-hardware-tokens.htm
Privacy Filters
Privacy filters are either film or glass add-ons that are placed over a monitor or laptop screen to prevent the data on the screen from being readable when viewed from the sides. Only the user sitting directly in front of the screen is able to read the data.
Digital Security
Whereas the topic of physical security, from CompTIA’s standpoint, focuses on keeping individuals out, digital security focuses on keeping harmful data and malware out as well as on authorization and permissions. The areas of focus are antivirus software, firewalls, antispyware, user authentication/strong passwords, and directory permissions. Each of these is addressed in the sections that follow.
Antivirus and Anti-malware Software
The primary method of preventing the propagation of malicious code involves the use of antivirus software. Antivirus software is an application that is installed on a system to protect it and to scan for viruses as well as worms and Trojan horses. Most viruses have characteristics that are common to families of viruses. Antivirus software looks for these characteristics, or fingerprints, to identify and neutralize viruses before they impact you.
More than 200,000 known viruses, worms, bombs, and other malware have been defined. New ones are added all of the time. Your antivirus software manufacturer will work very hard to keep the definition database files current. The definition database file contains the currently known viruses and countermeasures for a particular antivirus software product. You probably won’t receive a virus that hasn’t been seen by one of these companies. If you keep the virus definition database files in your software up-to-date, you probably won’t be overly vulnerable to attacks. Since viruses are a subset of malware, anti-malware software typically does everything that antivirus software does as well as identifying threats beyond just viruses. A lot of anti-malware software is marketed as antivirus software.
Firewalls
Firewalls are among the first lines of defense in a network. There are different types of firewalls, and they can be either stand-alone systems or included in devices such as routers or servers. You can find firewall solutions that are marketed as hardware only and others that are software only. Many firewalls, however, consist of add-in software that is available for servers or workstations.
The basic purpose of a firewall is to isolate one network from another. Firewalls are becoming available as appliances, meaning that they’re installed as the primary device separating two networks. Appliances are freestanding devices that operate in a largely self-contained manner, requiring less maintenance and support than a server-based product.
Firewalls function as one or more of the following:
- Packet filter
- Proxy firewall
- Stateful inspection firewall
The firewall shown in Figure 19.1 effectively limits access from outside networks while allowing inside network users to access outside resources. The firewall in this illustration is also performing proxy functions.

Figure 19.1 A proxy firewall blocking network access from external networks
The following list includes discussions of three of the most common functions that firewalls perform:
Packet filter firewalls A firewall operating as a packet filter passes or blocks traffic to specific addresses based on the type of application and the port used. The packet filter doesn’t analyze the data of a packet; it decides whether to pass it based on the packet’s addressing information. For instance, a packet filter may allow web traffic on port 80 and block Telnet traffic on port 23. This type of filtering is included in many routers. If a received packet request asks for a port that isn’t authorized, the filter may reject the request or simply ignore it. Many packet filters can also specify which IP addresses can request which ports and allow or deny them based on the security settings of the firewall.
Packet filters are growing in sophistication and capability. A packet filter firewall can allow any traffic that you specify as acceptable. For example, if you want web users to access your site, then you configure the packet filter firewall to allow data on port 80 to enter. If every network were exactly the same, firewalls would come with default port settings hard-coded, but networks vary, so the firewalls don’t include such settings (though Deny All is the most common default).
Proxy firewalls Aproxy firewall can be thought of as an intermediary between your network and any other network. Proxy firewalls are used to process requests from an outside network; the proxy firewall examines the data and makes rule-based decisions about whether the request should be forwarded or refused. The proxy intercepts all of the packages and reprocesses them for use internally. This process may include hiding IP addresses.
The proxy firewall provides better security than packet filtering because of the increased intelligence that a proxy firewall offers. Requests from internal network users are routed through the proxy. The proxy, in turn, repackages the request and sends it along, thereby isolating the user from the external network. The proxy can also offer caching, should the same request be made again, and it can increase the efficiency of data delivery.
A proxy firewall typically uses two network interface cards (NICs). This type of firewall is referred to as a dual-homed firewall. One of the cards is connected to the outside network, and the other is connected to the internal network. The proxy software manages the connection between the two NICs. This setup segregates the two networks from each other and offers increased security. Figure 19.2 illustrates a dual-homed firewall segregating two networks from each other.

Figure 19.2 A dual-homed firewall segregating two networks from each other
The proxy function can occur at either the application level or the circuit level. Application-level proxy functions read the individual commands of the protocols that are being served. This type of server is advanced and must know the rules and capabilities of the protocol used. An implementation of this type of proxy must know the difference between GET and PUT operations, for example, and have rules specifying how to execute them. A circuit-level proxy creates a circuit between the client and the server and doesn’t deal with the contents of the packets that are being processed.
A unique application-level proxy server must exist for each protocol supported. Many proxy servers also provide full auditing, accounting, and other usage information that wouldn’t normally be kept by a circuit-level proxy server.
Stateful inspection firewalls Stateful inspection is also referred to as stateful packet filtering. Most of the devices used in networks don’t keep track of how information is routed or used. After a packet is passed, the packet and path are forgotten. In stateful inspection (or stateful packet filtering), records are kept using a state table that tracks every communications channel and can deny packets that were not requested from the internal network. Stateful inspections occur at all levels of the network and provide additional security, especially in connectionless protocols such as User Datagram Protocol (UDP) and Internet Control Message Protocol (ICMP). This adds complexity to the process. Denial of service (DoS) attacks present a challenge because flooding techniques are used to overload the state table and effectively cause the firewall to shut down or reboot. When multiple computers are aimed at the target, it is known as a distributed denial of service (DDoS) attack. A smurf attack attempts to use a broadcast ping (ICMP) on a network. The return address of the ping may be a valid system in your network. This system will be flooded with responses in a large network.
Antispyware
Just as antivirus software seeks out and stops viruses from entering and spreading, so too is the purpose of antispyware software. One thing separating spyware from most other malware is that it almost always exists to provide commercial gain. The operating systems from Microsoft are the ones most affected by spyware, and Microsoft has released Windows Defender and Security Essentials (as well as System Center Endpoint Protection for the enterprise) to combat the problem.
User Authentication/Strong Passwords
You can set up many different parameters and standards to force the people in your organization to conform. In establishing these parameters, it’s important that you consider the capabilities of the people who will be working with them. If you’re working in an environment where people aren’t computer savvy, you may spend a lot of time helping them remember and recover passwords. Many organizations have had to reevaluate their security guidelines after they’ve invested great time and expense to implement high-security systems.
Enforcing authentication security, especially when supporting users, can become a high-maintenance activity for network administrators. On one hand, you want people to be able to authenticate easily; on the other hand, you want to establish security that protects your company’s resources. In a Windows domain, password policies can be configured at the domain level using Group Policy objects. Variables that you can configure include password complexity and length and the time between allowed changes to passwords. A good password includes both upper- and lowercase letters as well as numbers and symbols. Educate users not to use personal information that one could easily guess about them, such as their pet names, anniversaries, or birthdays.
Directory Permissions
A bit later in this chapter, we will examine NTFS vs. Share permissions. Pay particular attention to Table 19.1 and Table 19.2. Most of the digital security at the directory permissions level is handled by NTFS, and there is not much that users can do to improve or change the security of the directory services deployed. However, you can ensure that they don’t become a tool for an attacker bent on compromising your organization’s security:
- Ensure that the most secure form of authentication encryption is used and supported by both the client and the authentication servers.
- Use encrypted software and protocols whenever possible, even for internal communications.
- Require users to change their password according to the company’s password policy.
- Establish a minimum character limit for passwords. While many companies set the minimum at 8 characters, it is not uncommon to see this set at 16.
- Instruct users to never write their password down or, if they do, to divide it up into several pieces and store each in a different secure location (such as a home safe, a gun cabinet, a chemical supply locker, or a safe deposit box).
- Tell users to never share their password or logon session with another person; this includes friends, spouse, and children.
- Make sure users allow all approved patch updates to be installed onto their client. Patch/update management is an important part of basic security.
- Ensure that users copy all company data back to a central file server before disconnecting from a logon session.
- Users should back up personal data onto verified removable media.
- Users should never walk away from a logged-on workstation without first locking it (requiring a password to continue the session).
- Require users to employ a password-protected screensaver.
- Don’t let users use auto-logon features.
- Encourage data encryption. This can be accomplished in any number of ways (including using BitLocker and EFS, which are discussed later in this chapter).
- Tell users to be aware of who is around them (and may be watching them) when they log on and when they work with valuable data.
- Users should never leave a company notebook computer, tablet computer, or smartphone in a position where it can be stolen or compromised while they are away from the office. Cable locks should be used to keep notebook computers securely in place whenever they are off site.
The protection of a directory service is based on the initial selection of a network operating system and its deployment infrastructure. After these foundational decisions are made, you need to understand fully the technologies employed by your selected directory services system and learn how to make the most functional, yet secure, environment possible. This will usually require the addition of third-party security devices, applications, services, and solutions.
User Education/AUP
The most effective method of preventing viruses, spyware, and harm to data is education. Teach your users not to open suspicious files and to open only those files that they’re reasonably sure are virus free. They need to scan every disk, email, and document that they receive before they open it. You should also have all workstations scheduled to be scanned automatically on a regular basis.
Acceptable use policies (AUPs) describe how the employees in an organization can use company systems and resources, both software and hardware. This policy should also outline the consequences for misuse. In addition, the policy (also known as a use policy) should address the installation of personal software on company computers and the use of personal hardware such as USB devices.
Every acceptable use policy today should include a section on smartphone usage (and even presence) within the workplace. Although a smartphone is a convenience for employees (they can now more easily receive and make personal calls at work), it can be a headache for the security administrator. Most smartphones can store files in the same way as any USB device, and they can be used to copy files to and from a workstation. Additionally, the camera feature on most phones makes it possible for a user to take pictures of things such as company documents, servers, and physical security implementation, among many other things that the company may not want to share. For this reason, most secure facilities have stringent restrictions on the presence of smartphones within the vicinity.
Principle of Least Privilege
The concept of least privilege is a simple one: When assigning permissions, give users only the permissions they need to do their work and no more. This is especially true with administrators. Users who need administrative-level permissions should be assigned two accounts: one for performing nonadministrative, day-to-day tasks and the other to be used only when performing administrative tasks that specifically require an administrative-level user account. Those users should be educated on how each of the accounts should be used.
The biggest benefit to following this policy is the reduction of risk. The biggest headache with following this policy is trying to deal with users who may not understand it. Managers, for example, may assert that they should have a higher permission level than those who report to them, but giving those permissions to them also opens up all of the possibilities for inadvertently deleting files, misconfiguring resources, and so on.
A least privilege policy should exist, and be enforced, throughout the enterprise. Users should have only the permissions and privileges needed to do their jobs and no more. The ISO standard 27002 (which updates 17799) sums it up well: “Privileges should be allocated to individuals on a need-to-use basis and on an event-by-event basis, i.e., the minimum requirement for their functional role when needed.” Adopting this as the policy for your organization is highly recommended.
Email Filtering
Email filtering, as the name implies, involves filtering email before passing it on. This can be done with messages intended both to enter and leave the network, and it can head off problems before they can propagate. One of the simplest filters is the spam filter included with most email programs. None of them are 100 percent efficient, and all suffer from false positives (identifying some email as spam that really isn’t).
Virtual Private Networks
As networks grow beyond simple physical limitations (such as an office or a building) to include clients from all over the world, the need to secure data becomes paramount. One of the best methods of addressing this is to tunnel the data. Tunneling sends private data across a public network by placing (encapsulating) that data into other packets. Most tunnels are virtual private networks (VPNs).
A VPN is a private network connection that occurs through a public network. A private network provides security over an otherwise unsecure environment. VPNs can be used to connect LANs together across the Internet or other public networks. With a VPN, the remote end appears to be connected to the network as if it were connected locally. A VPN requires either special hardware to be installed or a VPN software package running on servers and workstations.
Though it is a few years old, the following blog provides a useful guide to different VPN tunnel types in Windows:
Common Security Threats
In the following sections, we discuss a number of very important topics that fall into the realm of the broad categories: social engineering and malware. We’ll look at these topics as well as some of the reasons your network is vulnerable. The discussion is far from inclusive because troublemakers create new variants of malware and social engineering attacks on a regular basis. We will cover, however, everything CompTIA expects you to know for the exam.
Social Engineering
Social engineering is a process in which an attacker attempts to acquire information about your network and system by social means, such as talking to people in the organization. A social engineering attack may occur over the phone, by email, or in person. The intent is to acquire access information, such as user IDs and passwords. When the attempt is made through email or instant messaging, this is known as phishing (discussed later), and it’s often made to look as if a message is coming from sites where users are likely to have accounts (eBay and PayPal are popular).
These are relatively low-tech attacks and are more akin to con jobs. Take the following example: Your help desk gets a call at 4:00 a.m. from someone purporting to be the vice president of your company. They tell the help desk personnel that they are out of town to attend a meeting, their computer just failed, and they are sitting in a FedEx office trying to get a file from their desktop computer back at the office. They can’t seem to remember their password and user ID. They tell the help desk representative that they need access to the information right away or the company could lose millions of dollars. Your help desk rep knows how important this meeting is and gives the user ID and password over the phone. At this point, the attacker has just successfully socially engineered an ID and password that can be used for an attack.
Another common approach is initiated by a phone call or email from someone who pretends to be your software vendor, telling you that they have a critical fix that must be installed on your computer system. It may state that if this patch isn’t installed right away, your system will crash and you’ll lose all your data. For some reason, you’ve changed your maintenance account password and they can’t log on. Your system operator gives the password to the person. You’ve been hit again.
In Exercise 19.1, you’ll test your users to determine the likelihood of a social engineering attack. The steps are suggestions for tests; you may need to modify them slightly to be appropriate at your workplace. Before proceeding, make certain that your manager knows that you’re conducting such a test and approves of it.
Password Attacks
Password attacks occur when an account is attacked repeatedly. This is accomplished by using applications known as password crackers, which send possible passwords to the account in a systematic manner. The attacks are initially carried out to gain passwords for an access or modification attack. There are several types of password attacks:
Brute-force attack A brute-force attack is an attempt to guess passwords until a successful guess occurs. As an example of this type of attack, imagine starting to guess with A and then going through z; when no match is found, the next guess series goes from AA to zz and then adds a third value (AAA to zzz). Because of the nature of this routine, this type of attack usually occurs over a long period of time. To make passwords more difficult to guess, they should be much longer than two or three characters (Microsoft recommends eight as the minimum), be complex, and have password lockout policies.
Dictionary attack A dictionary attack uses a dictionary of common words to attempt to find the user’s password. Dictionary attacks can be automated, and several tools exist in the public domain to execute them. As an example of this type of attack, imagine guessing words and word combinations found in a standard English-language dictionary.
Hybrid A hybrid attack typically uses a combination of dictionary entries and brute force. For example, if you know that there is a good likelihood that the employees of a particular company are using derivatives of the company name in their passwords, then you can seed those values into the values attempted.
Malware
We’ve all been battling malicious, invasive software since we bought our first computers. This software can go by any number of names—virus, malware, and so on—but if you aren’t aware of its presence, these uninvited intruders may damage the data on your hard drive, destroy your operating system, and possibly spread to other systems.
Make certain your systems, and the data within them, are kept as secure as possible by using antivirus and antispyware programs. Doing so prevents others from changing the data, destroying it, or inadvertently harming it.
Man-in-the-Middle Attacks
Man-in-the-middle attacks clandestinely place something (such as a piece of software or a rogue router) between a server and the user, and neither the server’s administrator nor the user is aware of it. The man-in-the-middle intercepts data and then sends the information to the server as if nothing is wrong. The server responds to the software, thinking it’s communicating with a legitimate client. The attacking software continues sending information on to the server, and so forth.
If communication between the server and user continues, what’s the harm of the software? The answer lies in whatever else the software is doing. The man-in-the-middle software may be recording information for someone to view later, altering it, or in some other way compromising the security of your system and session.
In recent years, the threat of man-in-the-middle attacks on wireless networks has increased. Because it’s no longer necessary to connect to the wire, a malicious rogue can be outside of the building intercepting packets, altering them, and sending them on. A common solution to this problem is to enforce a secure wireless authentication protocol such as WPA2.
An older term that is now generically used for all man-in-the-middle attacks is TCP/IP hijacking even though they are not technically the same. TCP/IP hijacking involves the attacker gaining access to a host in the network and logically disconnecting it from the network. The attacker then inserts another machine with the same IP address. This happens quickly, and it gives the attacker access to the session and to all of the information on the original system. The server won’t know this has occurred, and it will respond as if the client is trusted—the attacker forces the server to accept its IP address as valid. The hijacker will hope to acquire privileges and access to all of the information on the server. There is little you can do to counter this threat, but fortunately these attacks require fairly sophisticated software and are harder to engineer than a simple DoS attack.
Rootkits
Rootkits have become the software exploitation program du jour. Rootkits are software programs that have the ability to hide certain things from the operating system; they do so by obtaining (and retaining) administrative-level access. With a rootkit, there may be a number of processes running on a system that don’t show up in Task Manager, or connections that don’t appear in a Netstat display may be established or available—the rootkit masks the presence of these items. It does this by manipulating function calls to the operating system and filtering out information that would normally appear.
Unfortunately, many rootkits are written to get around antivirus and antispyware programs that aren’t kept up-to-date. The best defense you have is to monitor what your system is doing and catch the rootkit in the process of installation.
Phishing
Phishing is a form of social engineering in which you simply ask someone for a piece of information that you are missing by making it look as if it is a legitimate request. An email might look as if it is from a bank and contain some basic information, such as the user’s name. These types of messages often state that there is a problem with the person’s account or access privileges. They will be told to click a link to correct the problem. After they click the link—which goes to a site other than the bank’s—they are asked for their username, password, account information, and so on. The person instigating the phishing can then use this information to access the legitimate account.
The only preventive measure in dealing with social engineering attacks is to educate your users and staff never to give out passwords and user IDs over the phone or via email or to anyone who isn’t positively verified as being who they say they are.
When you combine phishing with Voice over IP (VoIP), it becomes known as vishing, and it is just an elevated form of social engineering. While crank calls have been in existence since the invention of the telephone, the rise in VoIP now makes it possible for someone to call you from almost anywhere in the world, without the worry of tracing/caller ID/and other features of land lines, and pretend to be someone they are not in order to get data from you.
Two other forms of phishing of which you should be aware are spear phishing andwhaling, and they are very similar in nature. With spear phishing, the attacker uses information that the target would be less likely to question because it appears to be coming from a trusted source. Suppose, for example, you receive a message that appears to be from your spouse, and it says to click here to see that video of your children from last Christmas. Because it appears far more likely to be a legitimate message, it cuts through your standard defenses like a spear, and the likelihood that you would click this link is higher. Generating the attack requires much more work on the part of the attacker, and it often involves using information from contact lists, friend lists from social media sites, and so on.
Whaling is nothing more than phishing, or spear phishing, for so-called “big” users, thus the reference to the ocean’s largest creatures. Instead of sending out a To Whom It May Concern message to thousands of users, the whaler identifies one person from whom they can gain all of the data that they want—usually a manager or business owner—and targets the phishing campaign at them.
Shoulder Surfing
One form of social engineering is known as shoulder surfing, and it involves nothing more than watching someone when they enter their sensitive data. They can see you entering a password, typing in a credit card number, or entering any other pertinent information. The best defense against this type of attack is simply to survey your environment before entering personal data.
Spyware
Spyware differs from other malware in that it works—often actively—on behalf of a third party. Rather than self-replicating, like viruses and worms, spyware is spread to machines by users who inadvertently ask for it. The users often don’t know they have asked for it but have done so by downloading other programs, visiting infected sites, and so on.
The spyware program monitors the user’s activity and responds by offering unsolicited pop-up advertisements (sometimes known as adware), gathers information about the user to pass on to marketers, or intercepts personal data such as credit card numbers.
Viruses
Viruses can be classified as polymorphic, stealth, retrovirus, multipartite, armored, companion, phage, and macro viruses. Each type of virus has a different attack strategy and different consequences.
The following sections will introduce the symptoms of a virus infection, explain how a virus works, and describe the types of viruses you can expect to encounter and how they generally behave. We’ll also discuss how a virus is transmitted through a network and look at a few hoaxes.
Symptoms of a Virus/Malware Infection
Many viruses will announce that you’re infected as soon as they gain access to your system. They may take control of your system and flash annoying messages on your screen or destroy your hard disk. When this occurs, you’ll know that you’re a victim. Other viruses will cause your system to slow down, cause files to disappear from your computer, or take over your disk space.
You should look for some of the following symptoms when determining if a virus infection has occurred:
- The programs on your system start to load more slowly. This happens because the virus is spreading to other files in your system or is taking over system resources.
- Unusual files appear on your hard drive, or files start to disappear from your system. Many viruses delete key files in your system to render it inoperable.
- Program sizes change from the installed versions. This occurs because the virus is attaching itself to these programs on your disk.
- Your browser, word-processing application, or other software begins to exhibit unusual operating characteristics. Screens or menus may change.
- The system mysteriously shuts itself down or starts itself up and does a great deal of unanticipated disk activity.
- You mysteriously lose access to a disk drive or other system resources. The virus has changed the settings on a device to make it unusable.
- Your system suddenly doesn’t reboot or gives unexpected error messages during startup.
This list is by no means comprehensive. What is an absolute, however, is the fact that you should immediately quarantine the infected system. It is imperative that you do all you can to contain the virus and keep it from spreading to other systems within your network, or beyond.
How Viruses Work
A virus, in most cases, tries to accomplish one of two things: render your system inoperable or spread to other systems. Many viruses will spread to other systems given the chance and then render your system unusable. This is common with many of the newer viruses.
If your system is infected, the virus may try to attach itself to every file in your system and spread each time you send a file or document to other users. Figure 19.3 shows a virus spreading from an infected system either through a network or by removable media. When you give removable media to another user or put it into another system, you then infect that system with the virus.

Figure 19.3 Virus spreading from an infected system using the network or removable media
Many viruses today are spread using email. The infected system attaches a file to any email that you send to another user. The recipient opens this file, thinking it’s something that you legitimately sent them. When they open the file, the virus infects the target system. The virus might then attach itself to all the emails that the newly infected system sends, which in turn infects the computers of the recipients of the emails. Figure 19.4 shows how a virus can spread from a single user to literally thousands of users in a very short period of time using email.

Figure 19.4 An email virus spreading geometrically to other users
Types of Viruses
Viruses take many different forms. The following list briefly introduces these forms and explains how they work.
These are the most common types of viruses, but this isn’t a comprehensive list:
Armored virus An armored virus is designed to make itself difficult to detect or analyze. Armored viruses cover themselves with protective code that stops debuggers or disassemblers from examining critical elements of the virus. The virus may be written in such a way that some aspects of the programming act as a decoy to distract analysis while the actual code hides in other areas in the program.
From the perspective of the creator, the more time that it takes to deconstruct the virus, the longer it can live. The longer it can live, the more time it has to replicate and spread to as many machines as possible. The key to stopping most viruses is to identify them quickly and educate administrators about them—the very things that the armor makes difficult to accomplish.
Companion virus A companion virus attaches itself to legitimate programs and then creates a program with a different filename extension. This file may reside in your system’s temporary directory. When a user types the name of the legitimate program, the companion virus executes instead of the real program. This effectively hides the virus from the user. Many of the viruses that are used to attack Windows systems make changes to program pointers in the Registry so that they point to the infected program. The infected program may perform its dirty deed and then start the real program.
Macro virus A macro virus exploits the enhancements made to many application programs. Programmers can expand the capability of applications such as Microsoft Word and Excel. Word, for example, supports a mini-BASIC programming language that allows files to be manipulated automatically. These programs in the document are called macros. For example, a macro can tell your word processor to spell-check your document automatically when it opens. Macro viruses can infect all of the documents on your system and spread to other systems via email or other methods. Macro viruses are one of the fastest-growing forms of exploitation today.
Multipartite virus A multipartite virus attacks your system in multiple ways. It may attempt to infect your boot sector, infect all of your executable files, and destroy your application files. The hope here is that you won’t be able to correct all of the problems and will allow the infestation to continue. The multipartite virus depicted in Figure 19.5 attacks a system’s boot sector, infects application files, and attacks Word documents.

Figure 19.5 A multipartite virus commencing an attack on a system
Phage virus A phage virus alters programs and databases and the only way to remove this virus is to reinstall the programs that are infected. If you miss even a single instance of this virus on the victim system, the process will start again and infect the system once more.
Polymorphic virus Polymorphic viruses change form to avoid detection. These types of viruses attack your system, display a message on your computer, and delete files on your system. The virus will attempt to hide from your antivirus software. Frequently, the virus will encrypt parts of itself to avoid detection. When the virus does this, it’s referred to as mutation. The mutation process makes it hard for antivirus software to detect common characteristics of the virus. Figure 19.6 shows a polymorphic virus changing its characteristics to avoid detection. In this example, the virus changes a signature to fool antivirus software.

Figure 19.6 The polymorphic virus changing its characteristics
Retrovirus A retrovirus attacks or bypasses the antivirus software installed on a computer. You can consider a retrovirus to be an anti-antivirus. Retroviruses can directly attack your antivirus software and potentially destroy the virus definition database file. When this information is destroyed without your knowledge, you would be left with a false sense of security. The virus may also directly attack an antivirus program to create bypasses for itself.
Stealth virus A stealth virus attempts to avoid detection by masking itself from applications. It may attach itself to the boot sector of the hard drive. When a system utility or program runs, the stealth virus redirects commands around itself to avoid detection. An infected file may report a file size different from what is actually present. Figure 19.7 shows a stealth virus attaching itself to the boot sector to avoid detection. Stealth viruses may also move themselves from file A to file B during a virus scan for the same reason.
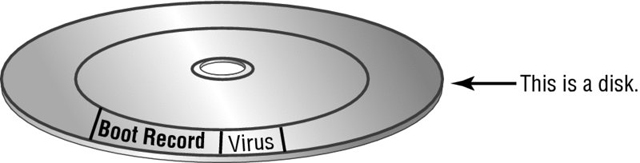
Figure 19.7 A stealth virus hiding in a disk boot sector
Virus Transmission in a Network
Upon infection, some viruses destroy the target system immediately. The saving grace is that the infection can be detected and corrected. Some viruses won’t destroy or otherwise tamper with a system; they use the victim system as a carrier. The victim system then infects servers, file shares, and other resources with the virus. The carrier then infects the target system again. Until the carrier is identified and cleaned, the virus continues to harass systems in this network and spread.
Worms
A worm is different from a virus in that it can reproduce itself, it’s self-contained, and it doesn’t need a host application to be transported. Many of the so-called viruses that have made the news were actually worms. However, it’s possible for a worm to contain or deliver a virus to a target system.
By their nature and origin, worms are supposed to propagate, and they use whatever services they’re capable of using to do that. Early worms filled up memory and bred inside the RAM of the target computer. Worms can use TCP/IP, email, Internet services, or any number of possibilities to reach their target.
Trojans
Trojan horses are programs that enter a system or network under the guise of another program. A Trojan horse may be included as an attachment or as part of an installation program. The Trojan horse can create a back door or replace a valid program during installation. It then accomplishes its mission under the guise of another program. Trojan horses can be used to compromise the security of your system, and they can exist on a system for years before they’re detected.
The best preventive measure for Trojan horses is to not allow them entry into your system. Immediately before and after you install a new software program or operating system, back it up! If you suspect a Trojan horse, you can reinstall the original program(s), which should delete the Trojan horse. A port scan may also reveal a Trojan horse on your system. If an application opens a TCP or UDP port that isn’t supported in your network, you can track it down and determine which port is being used.
Ransomware
With ransomware, software—often delivered through a Trojan horse—takes control of a system and demands that a third party be paid. The “control” can be accomplished by encrypting the hard drive, by changing user password information, or via any of a number of other creative ways. Users are usually assured that by paying the extortion amount (the ransom), they will be given the code needed to revert their systems back to normal operations.
Spoofing
A spoofing attack is an attempt by someone or something to masquerade as someone else. This type of attack is usually considered an access attack. A common spoofing attack that was popular for many years on early UNIX and other timesharing systems involved a programmer writing a fake logon program. It would prompt the user for a user ID and password. No matter what the user typed, the program would indicate an invalid logon attempt and then transfer control to the real logon program. The spoofing program would write the logon and password into a disk file, which was retrieved later.
The most popular spoofing attacks today are IP spoofing, ARP spoofing, and DNS spoofing. With IP spoofing, the goal is to make the data look as if it came from a trusted host when it didn’t (thus spoofing the IP address of the sending host).
With ARP spoofing (also known as ARP poisoning), the media access control (MAC) address of the data is faked. By faking this value, it is possible to make it look as if the data came from a networked device that it did not come from. This can be used to gain access to the network, to fool the router into sending to the device data that was intended for another host, or to launch a DoS attack. In all cases, the address being faked is an address of a legitimate user, and that makes it possible to get around such measures as allow/deny lists.
With DNS spoofing, the DNS server is given information about a name server that it thinks is legitimate when it isn’t. This can send users to a website other than the one to which they wanted to go, reroute mail, or do any other type of redirection for which data from a DNS server is used to determine a destination. Another name for this is DNS poisoning.
The important point to remember is that a spoofing attack tricks something or someone into thinking that something legitimate is occurring.
Zero-Day Attack
When a hole is found in a web browser or other software, and attackers begin exploiting it the very day it is discovered by the developer (bypassing the one-to-two-day response time that many software providers need to put out a patch once the hole has been found), it is known as a zero-day attack (orexploit). It is very difficult to respond to a zero-day exploit. If attackers learn of the weakness the same day as the developer, then they have the ability to exploit it until a patch is released. Often, the only thing that you as a security administrator can do, between the discovery of the exploit and the release of the patch, is to turn off the service. Although this can be a costly undertaking in terms of productivity, it is the only way to keep the network safe.
Several years ago, Stuxnet was found to be using a total of four zero-day vulnerabilities to spread from host to host:
www.symantec.com/connect/blogs/stuxnet-using-three-additional-zero-day- vulnerabilities
Zombie/Botnet
Software running on infected computers called zombies is often known as a botnet. Bots, by themselves, are but a form of software that runs automatically and autonomously. (For example, Google uses the Googlebot to find web pages and bring back values for the index.) Botnet, however, has come to be the word used to describe malicious software running on a zombie and under the control of a bot-herder.
Denial of service attacks—DoS and DDoS—can be launched by botnets, as can many forms of adware, spyware, and spam (via spambots). Most bots are written to run in the background with no visible evidence of their presence. Many malware kits can be used to create botnets and modify existing ones.
There is no universal approach to dealing with botnets, but knowing how to deal with various botnet types (all of which are described here) is important for exam preparation. Some can be easily detected by looking at a database of known threats, whereas others have to be identified through analysis of their behavior.
Non-Complaint Systems
One of the easiest ways to make your systems vulnerable and expose them to threats is to fail to keep them compliant. As an administrator, you should always follow security regulatory standards as well as compliance standards (such as ISO). One example of this approach is Cisco’s SAFE:
www.cisco.com/en/us/td/docs/solutions/Enterprise/Security/SAFE_RG/SAFE_rg.html
The Security Control Framework is the backbone of SAFE, and unification is the underlying key (rather than a silo approach) to security. By being modular, it can incorporate all parts of the network, including the WAN, the extranet, the Internet, and the intranet.
Workstation Security Best Practices
The user represents the weakest link in the security chain, whether harm comes to them in the form of malware, social engineering, or simply avoidable mistakes. The workstation represents the digital arm of the user, and it must be properly and adequately secured to keep the user—and the network—protected.
The following sections will explore some of the more commonly implemented best practices in greater detail.
Setting Strong Passwords
One of the most effective ways to keep a system safe is to employ strong passwords and educate your users in the best practices associated with them. Many password-generation systems are based on a one-way hashing approach. You can’t take the hash value and reverse it to guess the password. In theory, this makes it harder to guess or decrypt a password.
Passwords should be as long as possible. Most security experts believe a password of 10 characters is the minimum that should be used if security is a real concern. If you use only the lowercase letters of the alphabet, you have 26 characters with which to work. If you add the numeric values 0 through 9, you’ll get another 10 characters. If you go one step further and add the uppercase letters, you’ll then have an additional 26 characters, giving you a total of 62 characters with which to construct a password.
If you used a 4-character password, this would be 62 × 62 × 62 × 62, or approximately 14 million password possibilities. If you used 5 characters in your password, this would give you 62 to the 5th power, or approximately 920 million password possibilities. If you used a 10-character password, this would give you 62 to the 10th power, or 8.4 × 1017 (a very big number) possibilities. As you can see, these numbers increase exponentially with each position added to the password. The 4-digit password could probably be broken in a fraction of a day, while the 10-digit password would take considerably longer and much more processing power.
If your password consisted of only the 26 lowercase letters from the alphabet, the 4-digit password would have 26 to the 4th power, or 456,000, password combinations. A 5-character password would have 26 to the 5th power, or over 11 million, and a 10-character password would have 26 to the 10th power, or 1.4 × 1014. This is still a big number, but it would take considerably less time to break it.
Mathematical methods of encryption are primarily used in conjunction with other encryption methods as part of authenticity verification. The message and the hashed value of the message can be encrypted using other processes. In this way, you know that the message is secure and hasn’t been altered.
Requiring Passwords and Expiration
Make absolutely certain that you require passwords (such a simple thing to overlook in a small network) for all accounts, and change the default passwords on system accounts (as well as the default user names where possible). Not only that, but configure password expiration on all accounts so that they have to be changed on a regular basis.
Add passwords on each system to basic input/output system (BIOS) and unified extensible firmware interface (UEFI) firmware.
Account Management Given a security-related scenario, account management can take into account such settings as restricting user permissions, setting login time restrictions, disabling the guest account, locking an account after a certain number of failed attempts, and configuring a screen lock when the system times out after a certain length of inactivity. Each of these are discussed in the sections that follow.
Restricting User Permissions
When assigning user permissions, follow the principle of least privilege (discussed earlier): Give users only the bare minimum that they need to do their job. Assign permissions to groups rather than users, and make users member of groups (or remove them from groups) as they change roles or positions.
Add Login Time Restrictions
Configure user accounts so that logins can occur only during times that the user can be expected to be working. Preventing logins at 2:00 a.m. can be an effective method of keeping hackers from your systems.
Act on Failed Login Attempts
Configure user account settings so that there are a limited number of login attempts (three is a good number) before the account is locked for a period of time. Legitimate users who need to get in before the block expires can contact the administrator and explain why they weren’t able to give the right password three times in a row, and nonlegitimate users will go away in search of another system to try to enter.
Changing Default Usernames
Default accounts represent a huge weakness because everyone knows they exist. When an operating system is installed—whether on a workstation or a server—certain default accounts are created. Knowing the names of those accounts simplifies the process of potential attackers accessing them because they only have to supply the password.
Disabling the Guest Account
When Windows is installed, one of the default accounts it creates is Guest, and this represents a weakness that can be exploited by an attacker. While the account cannot do much, it can provide initial access to a system and the attacker can use that to find another account or acquire sensitive information about the system.
To secure the system, disable all accounts that are not needed, especially the Guest account. Next, rename the accounts if you can (Microsoft won’t allow you to rename some). Finally, change the passwords from the defaults and add them to the cycle of passwords that routinely get changed.
Screensaver Required Password
A screensaver should automatically start after a short period of idle time, and a password should be required before the user can begin the session again. This method of locking the workstation adds one more level of security.
There should be a screen lock/time-out setting configured on every workstation to prevent them from inadvertently becoming an open door to the network.
Disable Autorun
It is never a good idea to put any media in a workstation if you do not know where it came from or what it is. The simple reason is that said media (CD, DVD, USB) could contain malware. Compounding matters, that malware could be referenced in the AUTORUN.INF file, causing it to be summoned when the media is inserted in the machine and requiring no other action. AUTORUN.INF can be used to start an executable, access a website, or do any of a large number of different tasks. The best way to prevent a user from falling victim to such a ploy is to disable the autorun feature on the workstation.
Microsoft has changed (by default, disabled) the function on Windows so that it no longer acts as it previously did. The reason Microsoft changed the default action can be summed up in a single word: security. That text-based AUTORUN.INF file can not only take your browser to a web page, it can also call any executable file, pass along variable information about the user, or do just about anything else imaginable. Simply put, it is never a good idea to plug any media into your system if you have no idea where it came from or what it holds. Such an action opens up the user’s system—and the network—to any number of possible risks. An entire business’s data could be jeopardized by such a minuscule act if someone with elevated privileges placed a harmful CD into a computer at work.
Data Loss Prevention
Data loss prevention (DLP) systems monitor the contents of systems (workstations, servers, and networks) to make sure that key content is not deleted or removed. They also monitor who is using the data (looking for unauthorized access) and transmitting the data. DLP systems share commonalities with network intrusion prevention systems.
One of the best-known DLP systems is MyDLP, which started as an open-source solution to run on most Windows platforms. You can find MyDLP at www.mydlp.com. A large number of commercial programs are available for purchase, including Microsoft Forefront Identity Manager (www.microsoft.com/forefront/).
Working with Windows OS Security Settings
Every operating system offers security features and settings. While you need to know a little about Linux and Mac OS, the A+ exams focus primarily on Windows and the OS-specific security settings that you need to know to secure them.
The following sections will explore some of the more basic Windows OS security features and settings in more detail.
Users and Groups
There are a number of groups created on the operating system by default. The following sections look at the main ones.
Administrator
The administrator account is the most powerful of all: it has the power to do everything from the smallest task all the way up to removing the operating system. Because of the great power it holds, and the fact that it is always created, many who want to do harm will target this account as the one that they try to breach. To increase security, during the installation of the Windows operating systems in question, you are prompted for a name of a user who will be designated as the Administrator. The power then comes not from being called “Administrator” (the username might now be “edulaney,” “eadulaney,” or something similar) but from being a member of the Administrators group (notice the plural for the group and singular for the user).
Since members of the Administrators group have such power, they can inadvertently do harm (such as accidentally deleting a file that a regular user could not). To protect against this, the practice of logging in with an Administrators group account for daily interaction is strongly discouraged. Instead, we suggest that system administrators log in with a user account (lesser privileges) and change to the Administrators group account (elevated privileges) only when necessary.
Power User
Originally, Microsoft wanted to create a group in Windows that was not as powerful as the Administrators group, and that is how the Power Users group came into being. The idea was that membership in this group would be given read/write permission to the system, allowing members to install most software but keeping them from changing key operating system files. As such, it would be a good group for those who need to test software (such as programmers) and junior administrators.
The group did not work out as planned, and in Windows Vista, Windows 7, and Windows 8/8.1, the group has no more permissions than a standard user. The group is now only kept around for backward compatibility with Windows XP systems.
Guest
The guest account is created by default (and should be disabled) and is a member of the Guests group. For the most part, members of Guests have the same rights as Users except they can’t get to log files. The best reason to make users members of the Guests group is to access the system only for a limited time.
Standard User
The User group is the default to which standard users belong. Members of this group have read/write permission to their own profile. They cannot modify system-wide Registry settings or do much harm outside of their own account. Under the principle of least privilege, users should be made a member of the Users group only unless qualifying circumstances force them to have higher privileges.
If you attempt to run some utilities (such as SFC) from a standard command prompt, you will be told that you must be an administrator running a console session in order to continue. Rather than opening a standard command prompt, choose Start ➢ All Programs ➢ Accessories, and then right-click Command Prompt and choose Run As Administrator. The UAC will prompt you to continue, and then you can run SFC without a problem.
NTFS vs. Share Permissions
The new technology file system (NTFS) was introduced with Windows NT to address security problems. Before Windows NT was released, it had become apparent to Microsoft that a new file system was needed to handle growing disk sizes, security concerns, and the need for more stability. NTFS was created to address those issues.
Although the file allocation table (FAT) file system was relatively stable if the systems that were controlling it kept running, it didn’t do well when the power went out or the system crashed unexpectedly. One of the benefits of NTFS was a transaction tracking system, which made it possible for Windows NT to back out of any disk operations that were in progress when it crashed or lost power.
With NTFS, files, directories, and volumes can each have their own security. NTFS’s security is flexible and built in. Not only does NTFS track security in ACLs, which can hold permissions for local users and groups, but each entry in the ACL can specify what type of access is given—such as Read & Execute, List Folder Contents, or Full Control. This allows a great deal of flexibility in setting up a network. In addition, special file-encryption programs were developed to encrypt data while it was stored on the hard disk.
Microsoft strongly recommends that all network shares be established using NTFS. Several current OSs from Microsoft support both FAT32 and NTFS. It’s possible to convert from FAT32 to NTFS without losing data, but you can’t do the operation in reverse (you would need to reformat the drive and install the data again from a backup tape).
Share permissions apply only when a user is accessing a file or folder through the network. Local permissions and attributes are used to protect the file when the user is local. With FAT and FAT32, you do not have the ability to assign “extended” or “extensible” permissions, and the user sitting at the console effectively is the owner of all resources on the system. As such, they can add, change, and delete any data or file.
With NTFS as the file system, however, you are allowed to assign more comprehensive security to your computer system. NTFS permissions are able to protect you at the file level. Share permissions can be applied to the directory level only. NTFS permissions can affect users logged on locally or across the network to the system where the NTFS permissions are applied. Share permissions are in effect only when the user connects to the resource via the network.
Allow vs. Deny
Within NTFS, permissions for objects fall into one of three categories: allow, not allow, and deny. When viewing the permissions for a file or folder, you can check the box for Allow, which effectively allows the group selected to perform that action. You can also uncheck the box for Allow, which does not allow that group that action. Alternatively, you can check the Deny box, which prevents that group from using that action. There is a difference between not allowing (a cleared check box) and Deny (which specifically prohibits), and you tend not to see Deny used often. Deny, when used, trumps other permissions.
Permissions set on a folder are inherited down through subfolders, unless otherwise changed. Permissions are also cumulative: if a user is a member of a group that has Read permission and a member of a group that has Write permission, they effectively have both Read and Write permission.
Moving vs. Copying Folders and Files
When you copy a file, you create a new entity. When you move a file, you simply relocate it and still have but one entity. This distinction is important when it comes to understanding permissions. A copy of a file will generally have the permissions assigned to it that are placed on newly created files in the folder—regardless of what permissions were on the original file.
A moved file, on the other hand, will attempt to keep the same permissions as it had in the original location. Differences will occur if the same permissions cannot exist in the new location—for example, if you are moving a file from an NTFS volume to FAT32, the NTFS permissions will be lost. If, on the other hand, you are moving from a FAT32 volume to an NTFS volume, new permissions will be added that match those for newly created entities.
Folder copy and move operations follow guidelines that are similar to those with files.
File Attributes
Permissions can be allowed or denied individually on a per-folder basis. You can assign any combination of the values shown in Table 19.1.
Table 19.1 NTFS directory permissions
| NTFS Permission | Meaning |
| Full Control | Gives the user all of the other choices and the ability to change permissions. The user can also take ownership of the directory or any of its contents. |
| Modify | Combines the Read & Execute permission with the Write permission and further allows the user to delete everything, including the folder. |
| Read & Execute | Combines the permissions of Read with those of List Folder Contents and adds the ability to run executables. |
| List Folder Contents | The List Folder Contents permission (known simply as List in previous versions) allows the user to view the contents of a directory and to navigate to its subdirectories. It does not grant the user access to the files in these directories unless that is specified in file permissions. |
| Read | Allows the user to navigate the entire directory structure, view the contents of the directory, view the contents of any files in the directory, and see ownership and attributes. |
| Write | Allows the user to create new entities within the folder. |
Clicking the Advanced button allows you to configure auditing and ownership properties. You can also apply NTFS permissions to individual files. This is done from the Security tab for the file; Table 19.2 lists the NTFS file permissions.
Table 19.2 NTFS file permissions
| NTFS Permission | Meaning |
| Full Control | Gives the user all of the other permissions as well as permission to take ownership and change permission |
| Modify | Combines the Read & Execute permission with the Write permission and further allows the user to delete the file |
| Read | Allows the user to view the contents of the file and to see ownership and attributes |
| Read & Execute | Combines the Read permission with the ability to execute |
| Write | Allows the user to overwrite the file as well as to change attributes and see ownership and permissions |
By default, the determination of NTFS permissions is based on the cumulative NTFS permissions for a user. Rights can be assigned to users based on group membership and individually; the only time permissions do not accumulate is when the Deny permission is invoked.
Shared Files and Folders
You can share folders, and the files beneath them, by right-clicking on them and choosing Share With from the context menu. In Windows, the context menu asks you to choose with whom you want to share the folder or file. The options you see on the context menu will depend on the type of network to which you are connected—a domain, a workgroup, or a HomeGroup. If password-protected sharing is turned on (the default), the person accessing the share has to give a username and password to access the shared entity.
The Advanced Sharing settings will come up if you try to share something in one of the Public folders or make other changes. This interface can also be accessed through the Network and Sharing Center applet in the Control Panel, and it is used to change network settings relevant to sharing.
Administrative Shares vs. Local Shares
Administrative shares are created on servers running Windows on the network for administrative purposes. These shares can differ slightly based on which OS is running, but they always end with a dollar sign ($) to make them hidden. There is one for each volume on a hard drive (c$, d$, and so on) as well as admin$ (the root folder—usually c:winnt), and print$ (where the print drivers are located). These are created for use by administrators and usually require administrator privileges to access.
Local shares, as the name implies, are those that are created locally. In Windows Vista, the icon for them shows two people to indicate the share.
Permission Propagation/Inheritance
Permissions are cumulative. A user who is a member of two groups will effectively have the permissions of both groups combined.
Inheritance is the default throughout the permission structure unless a specific setting is created to override it. A user who has Read and Write permissions in one folder will have that in all the subfolders unless a change has been made specifically to one of the subfolders.
System Files and Folders
System files are usually flagged with the Hidden attribute, meaning they don’t appear when a user displays a directory listing. You should not change this attribute on a system file unless absolutely necessary. System files are required for the OS to function. If they are visible, users might delete them (perhaps thinking that they can clear some disk space by deleting files that they don’t recognize). Needless to say, that would be a bad thing!
User Authentication
As mentioned in Chapter 14, one of the big problems larger systems must deal with is the need for users to access multiple systems or applications. This may require a user to remember multiple accounts and passwords. The purpose of a single sign-on (SSO) is to give users access to all of the applications and systems that they need when they log on. Single sign-on is both a blessing and a curse. It’s a blessing in that once users are authenticated, they can access all of the resources on the network and browse multiple directories. It’s a curse in that it removes the doors that otherwise exist between the user and various resources.
In the case of Kerberos, a single token allows any “Kerberized” applications to accept a user as valid. The important thing to remember in this process is that each application that wants to use SSO must be able to accept and process the token presented by Kerberos. Active Directory (AD) uses Kerberos v5 and a server that runs AD retains information about all access rights for all users and groups in the network. When a user logs on to the system, AD issues the user a globally unique identifier (GUID). Applications that support AD can use this GUID to provide access control.
Using AD simplifies the sign-on process for users and lowers the support requirements for administrators. Access can be established through groups, and it can be enforced through group memberships: all users log into the Windows domain using their centrally created AD account. On a decentralized network, SSO passwords are stored on each server and can represent a security risk. It’s important to enforce password changes and make certain that passwords are updated throughout the organization on a frequent basis.
BitLocker and BitLocker To Go
You have to be careful, because CompTIA sometimes refers to the utility as “bit-locker” or “Bitlocker,” while it is officially known as BitLocker. This tool allows you to use drive encryption to protect files—including those needed for startup and logon. This is available only with more complete editions of Windows 8 (Pro and Enterprise), Windows 7 (Enterprise and Ultimate), and Windows Vista (Enterprise and Ultimate).
For removable drives, BitLocker To Go provides the same encryption technology to help prevent unauthorized access to the files stored on them.
EFS
Encrypting File System (EFS) is available in most editions of Windows, and it allows for encryption/decryption of files stored in NTFS volumes. All users can use EFS, whereas only administrators can turn on BitLocker. It does not require any special hardware, while BitLocker benefits from having the Trusted Platform Module (TPM). As an additional distinction, EFS can encrypt just one file, if so desired, while BitLocker encrypts the whole volume and whatever is stored on it. Last, EFS can be used in conjunction with BitLocker to increase security further.
Mobile Device Security
Apple computers have a pretty decent reputation in the industry for being somewhat resistant to malware. Whether or not this is because of the relatively small installed base or the ease with which hackers penetrate “other” operating systems, this characteristic carries over to Apple’s mobile devices. In fact, hackers don’t seem to be as interested in attacking the legions of mobile devices as much as they have gone after the Windows operating system that drives the vast majority of laptops, desktops, and servers in the world. Nevertheless, attacks occur. Coupled with how easy mobile devices are to misplace or steal, it behooves users to have proactive monitoring and contingency plans in place.
The following sections detail the built-in security utilities that are common in today’s mobile devices. Furthermore, for threats not covered by the software with which the devices ship, the protection available from third-party utilities is worth discussing.
Screen Locks
Apple and Android mobile devices include a requisite passcode locking mechanism that is off by default, but the user on the go is encouraged to enable a passcode lock. If your device acts more as a home computing device and rarely goes with you out the door, there is very little reason to set such a passcode, but knowing how to do so is important. Exercise 19.2 outlines the steps for creating a code for your iPhone. The same general concept for Android phones is presented in Exercise 19.3.
Make note of the fact that there is a switch on the final screen mentioned in Exercise 19.2 that, when on, destroys all local data on the phone if incorrect passcodes are entered 10 times in a row. While this is recommended for users with phones that contain sensitive data and that are frequently taken into public venues or placed in compromising positions, the casual user should not turn this feature on unless they can be sure there will always be a recent backup available in iTunes.
Imagine a user’s child or a mischievous, yet harmless, friend poking away at passcodes until the device informs them that it is being wiped clean. It’s not for everyone. Restoring from a backup is easy enough, but will there be a recent backup available when disaster strikes? Apple performs a backup to the computer running iTunes that the iOS device syncs with. Conditions required for synchronization to occur are discussed later in this chapter.
Apple imposes cooling-off time-out periods of increasing duration, even if the Erase Data feature is disabled and you or someone else repeatedly enters the wrong code over multiple lockouts. The final penalty with the Erase Data feature disabled is that you cannot unlock the device until it is connected to the computer with which it was last synced.
When a passcode is set, Android devices take a less punitive approach to failed login attempts when compared to their Apple counterparts, where the static “destroy after 10 failed attempts” feature is your only option. Most Android systems have no adjustment for their default behavior, aside from turning off security.
The difference is that if waiting the time-out period won’t help because you’ve forgotten the pattern or code, this device can tie your access back to the Google account you used when setting it up. This is also the account where you receive purchase notifications from the Market or Google Play, and it does not have to be a Gmail account (one of the benefits of the open-source nature of Android). If you remember how to log in to that account, you can still get into your phone. At least you can investigate the credentials to that account on a standard computer and return to the device to enter those credentials.
In addition to the commonly used passcode lock, other forms of screen locks include a fingerprint lock, face lock, or swipe lock. As the name implies, the first requires a fingerprint match to log in, the second a face match (both being biometric authentication), and the third a match to a prerecorded swipe.
Remote Wipes and Locator Applications
Should your work or personal mobile device disappear or fall into the wrong hands, it’s always nice to have a backup plan for making sure that no company secrets or personal identifiers get misused by anyone who would use the information with ill will. Apple supplies a free app called Find My iPhone that, together with iCloud, allows multiple mobile devices and Macs to be located if powered on and connected to the Internet (via 4G, 3G, WiFi, Ethernet, and so on). The app allows the device to be controlled remotely to lock it, play a sound (even if audio is off), display a message, or wipe it clean.
Within a newer iPhone’s Settings screen, you can find an iCloud settings page and select the Find My iPhone switch. With this switch off, the Find My iPhone app and iCloud web page will be unable to find your device.
On the login screen for the iPhone app, you must enter the iCloud account information that includes the device that you are attempting to control remotely.
Note that when you change the password for your Apple ID, it affects your iCloud account but does not transfer automatically within your device. Always remember to update your iCloud account information on each device when you update the associated Apple ID.
The website’s login page at www.icloud.com calls for the same credentials as the app requires. You are signing in with HTTPS, so your username and password are not traversing the Internet in the clear. With the switch in the iCloud settings screen set to off for all devices on your account, when you sign on to the app with your iCloud account credentials, you are met with a disabling switch message.
You do not need to go to the website if you have another device with the Find My iPhone app or borrow one from someone else. The device forgets your credentials when you log out, so the owner will not be able to control your device the next time they use the app.
After logging into the iCloud website, you can click the icon that matches the icon for the Find My iPhone app in iOS. Assuming that you’ve made it into the app on another device and your Find My iPhone feature is turned on in your missing device, the Info screen tells you that your device has been found and gives you options for the next step you take.
Tapping the Location button in the upper left shows you a map of where your device is currently located. You have three options for how to view the location: two-dimensional map, satellite, and a hybrid version where the two-dimensional street-name information is laid over the satellite view.
If you tap the Play Sound Or Send Message button on the Info screen instead of the Location button, the screen that pops up allows you to display a message remotely. You might consider first displaying a message without the sound, which is at maximum volume. Ask in the message to be called at another number. If you hear from someone in possession of your device, the hunt is over. Otherwise, send another message with the tone to get the attention of the nearest person. If you are at the reported location when you generate the sound, it can help you home in on the device.
If you do decide to use the remote-lock feature of the app, you’ll have the opportunity to reconsider before locking it. You should have no issue with locking the device; doing so does not prevent you from using the app further. It simply makes sure that the device is harder to break into.
Should you decide to take the sobering step of destroying the contents of the device remotely, you get a solemn notice allowing you the opportunity to reassess the situation before proceeding. Sometimes there’s just no other option.
For Android devices, the app called Lookout from Lookout Labs is a critically acclaimed application that performs some of the same functions as Apple’s Find My iPhone, including the emission of an extremely loud scream. Google also provides the Android Device Manager app that has similar functionality.
On an Android phone, the Lookout app automatically scans every app you install, performs a full scan of all of the apps on your device every week, and downloads the latest virus definitions regularly. Lookout Labs provides virus scanning of all apps on a regular basis in its Lookout product as well as in some of its more specialized offerings. Among these specialized apps, the company produces the Plan B app that boasts the ability to install itself after the device is lost, subsequently turning on location services remotely.
Remote Backup
Software companies like Lookout Labs also produce apps that are capable of backing up your device’s contents over the Internet so that in case of a catastrophic failure, your information is easily restored to a new device. The app known as MyBackup Pro is designed exclusively for the purpose of backing up your data and storing the backup sets either locally on the device or remotely on the company’s servers. You can choose the type of information to be backed up, and restoration is quite painless, resulting in your device returning to its predisaster state.
Apple iOS devices automatically back themselves up to the computer running iTunes that they sync with. In the sense that this backup exists on a system other than the iOS device, this can be considered a remote backup as well.
Operating System Updates
It’s easy to forget that these tiny yet powerful mobile devices we’ve been talking about are running operating systems that play the same role as the operating systems of their larger brethren. As such, users must be careful not to let the operating systems go too long without updates. Occasionally, mobile devices will notify the user of an important update to the operating system. Too often, however, these notifications never come. Therefore, each user should develop the habit of checking for updates on a regular basis.
Not keeping up with software updates creates an environment of known weaknesses and unfixed bugs. Mobile devices operate on a very tight tolerance of hardware and software performance. Not maintaining the device for performance at the top of its game will tend to have more pronounced repercussions than those seen in larger systems.
For the iPhone, iPod Touch, and iPad, you can check for the most important level of updates by tapping Settings ➢ General ➢ Software Update. For the Android operating system, there are multiple updates that can be checked for manually. All of them are accessible by following Menu ➢ Settings ➢ System Updates. The resulting menu includes options for updating the firmware, the profile, the preferred roaming list (PRL), and the manufacturer’s specific software.
Full Drive Encryption
BitLocker and BitLocker To Go were discussed a bit earlier in this chapter and they greatly enhance security by encrypting the data on drives (installed and removable, respectively) and helping to secure it from prying eyes. At a minimum, the same level of protection that you would apply to a desktop machine should be applied to a mobile device since it can contain confidential and personally identifiable information which could cause great harm in the wrong hands.
Full drive encryption should be done on laptops and mobile devices and you should back up regularly to be able to access a version of it should something happen to the device itself.
Multifactor Authentication
Mutlifactor authentication was mentioned previously in this chapter and involves using more than one item (factor) to authenticate. An example of this would be configuring BitLocker encrypted flash drives so that when inserted into your laptop a passwords and smart card value must be given before the data is decrypted and available.
Authenticator Applications
The Authenicator app works with mobile devices to generate security codes that can keep accounts secure by requiring 2-step verification (a code from the app in addition to your account password). Available for use with Microsoft, Google, and other mobile devices, an account is usually added to it by entering a secret key or scanning a barcode.
Policies and Procedures
When it comes to mobile devices, there are two specific policies that should be created: one related to devices (and in particular, BYOD), and the other on profile security requirements. The BYOD policy needs to address differences in the support provided to the devices and those that are corporate owned. A common clause, for example, indicates that technical support is provided only to those devices used for legitimate corporate business but all devices are expected to be secured and the data on them protected.
As an administrator, you can choose settings for mobile devices under your purview and enforce profiles security requirements in various ways. In a given scenario, you may want to enforce settings for the entire organization and in others you may want to differ the settings based on organizational unit, role, or other group type. Among the settings you may want to enforce are those requiring encryption of drives and complex passwords.
Destruction and Disposal Methods
Think of all of the sensitive data written to a hard drive. Said drive can contain information about students, clients, users—about anyone and anything. That hard drive can be in a desktop PC, in a laptop, or even in a printer (many laser printers above consumer grade offer the ability to add a hard drive to store print jobs), and if it falls into the wrong hands, you can not only lose valuable data but also risk a lawsuit for not properly protecting privacy. An appropriate data destruction/disposal plan should be in place to avoid any potential problems.
Since data on media holds great value and liability, that media should never simply be tossed away for prying eyes to stumble upon. For the purpose of this objective, the media in question is hard drives, and there are three key concepts to understand in regard to them: formatting, sanitation, and destruction. Formatting prepares the drive to hold new information (which can include copying over data already there). Sanitation involves wiping the data off the drive, while destruction renders the drive no longer usable.
Recycling or Repurposing Best Practices
For exam purposes, the best practices for recycling or repurposing fall beneath the categories of low-level formats (as opposed to standard formatting), overwrites, and drive wipes. Those are the very topics of the next few sections and we will explore each in detail.
Low-Level Format vs. Standard Format
There are multiple levels of formatting that can be done on a drive. A standard format, accomplished using the operating system’s FORMAT utility (or similar), can mark space occupied by files as available for new files without truly deleting what was there. Such erasing—if you want to call it that—doesn’t guarantee that the information isn’t still on the disk and recoverable.
A low-level format (typically only accomplished in the factory) can be performed on the system, or a utility can be used to completely wipe the disk clean. This process helps ensure that information doesn’t fall into the wrong hands.
The manufacturer performs a low-level format on integrated device electronics (IDE) hard drives. Low-level formatting must be performed even before a drive can be partitioned. In low-level formatting, the drive controller chip and the drive meet for the very first time and learn to work together. Because controllers are integrated into IDE drives, low-level formatting is a factory process. Low-level formatting is not operating system dependent.
The main thing to remember for the exams is that most forms of formatting included with the operating system do not actually erase the data completely. Formatting the drive and then disposing of it has caused many companies problems when individuals who never should have seen it retrieve the data using applications that are commercially available.
Hard Drive Sanitation and Sanitation Methods
A number of vendors offer hard drives with Advanced Encryption Standard (AES) cryptography built in, but it’s still better to keep these secure hard drives completely out of the hands of others than to trust their internal security mechanisms once their usable life span has passed for the client. Some vendors include utilities to erase the hard drive, and if it is a Serial ATA (SATA) drive, you can always run HDDERASE, but you are still taking your chances.
In addition to HDDERASE, you can find a number of other software “shredders” by doing a quick Web search. It is important to recognize and acknowledge that many of these do not meet military or GSA specifications, and those specifications should be considered as guidelines to which you must also adhere when dealing with your own, or a client’s, data. The only surefire method of rendering the hard drive contents completely eradicated is physical destruction.
Overwrite
Overwriting the drive entails copying over the data with new data. A common practice is to replace the data with 0s. A number of applications allow you to recover what was there prior to the last write operation, and for that reason, most overwrite software will write the same sequence and save it multiple times.
Drive Wipe
If it’s possible to verify beyond a reasonable doubt that a piece of hardware that’s no longer being used doesn’t contain any data of a sensitive or proprietary nature, then that hardware can be recycled (sold to employees, sold to a third party, donated to a school, and so on). That level of assurance can come from wiping a hard drive or using specialized utilities.
If you can’t be assured that the hardware in question doesn’t contain important data, then the hardware should be destroyed. You cannot, and should not, take a risk that the data your company depends on could fall into the wrong hands.
Physical Destruction
Physically destroying the drive involves rendering the component no longer usable. While the focus is on hard drives, you can also physically destroy other forms of media, such as flash drives and CD/DVDs.
Shredder
Many commercial paper shredders include the ability to destroy DVDs and CDs. Paper shredders, however, are not able to handle hard drives, and you need a shredder created for just such a purpose: Jackhammer makes a low-volume unit that will destroy eight drives a minute and carries a suggested list price of just under $30,000.
Drill/Hammer
If you don’t have the budget for a hard drive shredder, you can accomplish similar results in a much more time-consuming way with a power drill. The goal is to physically destroy the platters in the drive. Start the process by removing the cover from the drive—this is normally done with a Torx driver (while #8 does not work with all, it is a good one to try first). You can remove the arm with a slotted screwdriver and then the cover over the platters using a Torx driver. Don’t worry about damaging or scratching anything—nothing is intended to be saved. Everything but the platters can be tossed away.
As an optional step, you can completely remove the tracks using a belt sander, grinder, or palm sander. The goal is to turn the shiny surface into fine powder. Again, this step is optional, but it adds one more layer of assurance that nothing usable remains. Always wear eye protection and be careful not to breathe in any fine particles that you generate during the grinding/destruction process.
Following this, use the power drill to create as small a set of particles as possible. A drill press works much better for this task than trying to hold the drive and drill it with a handheld model.
Electromagnet (Degaussing)
A large electromagnet can be used to destroy any magnetic media, such as a hard drive or backup tape set. The most common of these is the degaussing tool. Degaussing involves applying a strong magnetic field to initialize the media (this is also referred to as disk wiping). This process helps ensure that information doesn’t fall into the wrong hands.
Degaussing involves using a specifically designed electromagnet to eliminate all data on the drive, and that destruction also includes the factory prerecorded servo tracks. You can find wand model degaussers priced at just over $500 or desktop units that sell for up to $30,000.
Incineration
A form of destruction not to be overlooked is fire. It is possible to destroy most devices by burning them up and using an accelerant such as gasoline or lighter fluid to aid the process.
Certificate of Destruction
A certificate of destruction (or certificate of recycling) may be required for audit purposes. Such a certificate, usually issued by the organization carrying out the destruction, is intended to verify that the asset was properly destroyed and usually includes serial numbers, type of destruction done, and so on.
Securing a SOHO Network (Wireless)
CompTIA wants administrators of small office, home office (SOHO) networks to be able to secure those networks in ways that protect the data stored on them. This objective looks at the security protection that can be added to a wireless SOHO network, while the one that follows examines similar procedures for a wired network.
A wireless network is not and never will be secure. Use wireless only when absolutely necessary. If you must deploy a wireless network, here are some tips to make some improvements to wireless security:
- Change the default SSID.
- Disable SSID broadcasts.
- Disable DHCP or use reservations.
- Use MAC filtering.
- Use IP filtering.
- Use the strongest security available on the wireless access point.
- Change the static security keys every two to four weeks.
- When new wireless protection schemes become available (and are reasonably priced), consider migrating to them.
- Limit the user accounts that can use wireless connectivity.
- Use a preauthentication system, such as RADIUS.
- Use remote access filters against client type, protocols used, time, date, user account, content, and so forth.
- Use IPSec tunnels over the wireless links.
- Turn down the signal strength to the minimum needed to support connectivity.
- Seriously consider removing wireless access from your LAN.
Change Default Usernames and Passwords
In addition to those created with the installation of the operating system(s), default accounts are also often associated with hardware. Wireless access points, routers, and similar devices often include accounts for interacting with, and administering, those devices. You should always change the passwords associated with those devices and, where possible, change the usernames.
If there are accounts that are not needed, disable or delete them. Make certain that you use strong password policies and protect the passwords with the same security that you use for users and administrators (in other words, don’t write the router’s password on an address label and stick it to the bottom of the router).
Changing the SSID
All radio frequency signals can be easily intercepted. To intercept 802.11a/b/g/n traffic, all you need is a PC with an appropriate 802.11a/b/g/n card installed. Many networks will regularly broadcast their name (known as an SSID broadcast) to announce their presence. Simple software on the PC can capture the link traffic in the wireless AP and then process this data to decrypt account and password information.
You should change the SSID—whether or not you choose to disable its broadcast or not—to keep it from being a value that many outsiders come to know. If you use the same SSID for years, then the number of individuals who have left the company or otherwise learned of its value will only increase. Changing the variable adds one more level of security.
Setting Encryption
The types of wireless encryption available (WEP, WPA, WPA2,and so forth) were discussed in Chapter 8, “Installing Wireless and SOHO Networks.” It’s important to remember that you should always enable encryption for any SOHO network that you may administer, and you should choose the strongest level of encryption you can work with.
Disabling SSID Broadcast
One method of “protecting” the network that is often recommended is to turn off the SSID broadcast. The access point is still there and can still be accessed by those who know of it, but it prevents those who are looking at a list of available networks from finding it. This should be considered a very weak form of security because there are still ways, albeit a bit more complicated, to discover the presence of the access point besides the SSID broadcast.
Enable MAC Filtering
Most APs offer the ability to turn on MAC filtering, but it is off by default. In the default state, any wireless client that knows of the existence of the AP can join the network. When MAC filtering is used, the administrator compiles a list of the MAC addresses associated with the users’ computers and enters them. When a client attempts to connect, an additional check of the MAC address is performed. If the address appears in the list, the client is allowed to join, otherwise they are forbidden from so doing. On a number of wireless devices, the term network lock is used in place of MAC filtering, and the two are synonymous.
Antenna and Access Point Placement
Antenna placement can be crucial in allowing clients to reach the access point. For security reasons, you do not want to overextend the reach of the network so that people can get onto the network from other locations (the parking lot, the building next door, and so on). Balancing security and access is a tricky thing to do.
There isn’t any one universal solution to this issue, and it depends on the environment in which the access point is placed. As a general rule, the greater the distance the signal must travel, the more it will attenuate, but you can lose a signal quickly in a short space as well if the building materials reflect or absorb it. You should try to avoid placing access points near metal (which includes appliances) or near the ground. They should be placed in the center of the area to be served and high enough to get around most obstacles.
Radio Power Levels
On the chance that the signal is actually traveling too far, some access points include power level controls that allow you to reduce the amount of output provided.
Assign Static IP Addresses
While DHCP can be a godsend, a SOHO network is small enough that you can get by without it issuing IP addresses to each host. The advantage to assigning the IP addresses statically is that you can make certain which host is associated with which IP address and then utilize filtering to limit network access to only those hosts.
WPS
WPS (Wi-Fi Protected Setup) can help secure the network by requiring new machines to do something before they can join the network. This often requires the user to perform an action in order to complete the enrollment process: press a button on the router within a short time period, enter a PIN number, or bring the new device close-by (so that near field communication can take place).
Securing a SOHO Network (Wired)
While a wired network can be more secure than a wireless one, there are still a number of procedures that you should follow to leave as little to chance as possible. Among them, change the default usernames and passwords to different values and secure the physical environment. You should also disable any ports that are not needed, assign static IP addresses, and use MAC filtering to limit access only to those hosts that you recognize.
Change Default Usernames and Passwords
Make sure the default password is changed after the installation of any network device. Failure to do so leaves that device open for anyone recognizing the hardware to access it using the known factory password.
In Windows, the Guest account is automatically created with the intent that it is to be used when someone must access a system but lacks a user account on that system. Because it is so widely known to exist, it is recommended that you not use this default account and create another one for the same purpose if you truly need one. The Guest account leaves a security risk at the workstation and should be disabled to deter those attempting to gain unauthorized access.
Enable MAC Filtering
Limit access to the network to MAC addresses that are known and filter out those that are not. Even in a home network, you can implement MAC filtering with most routers and typically have an option of choosing to allow only computers with MAC addresses that you list or deny only computers with MAC addresses that you list.
Assign Static IP Addresses
Static IP addresses should be used (avoid having them dynamically issued by DHCP) on small office and home office networks to keep from issuing addresses to hosts other than those you recognize and want on the network.
Disabling Ports
Disable all unneeded protocols/ports. If you don’t need them, remove the additional protocols, software, or services or prevent them (disable them) from loading. Ports not in use present an open door for an attacker to enter.
Physical Security
Just as you would not park your car in a public garage and leave its doors wide open with the key in the ignition, you should educate users to not leave a workstation that they are logged in to when they attend meetings, go to lunch, and so forth. They should log out of the workstation or lock it: “Lock when you leave” should be a mantra they become familiar with. A password (usually the same as their user password) should be required to resume working at the workstation.
You can also lock a workstation by using an operating system that provides file system security. Microsoft’s earliest file system was referred to as file allocation table (FAT). FAT was designed for relatively small disk drives. It was upgraded first to FAT-16 and finally to FAT-32. FAT-32 (also written as FAT32) allows large disk systems to be used on Windows systems.
FAT allows only two types of protection: share-level and user-level access privileges. If a user has write or change access to a drive or directory, they have access to any file in that directory. This is very unsecure in an Internet environment.
With NTFS, files, directories, and volumes can each have their own security. NTFS’s security is flexible and built in. Not only does NTFS track security in access control lists (ACLs), which can hold permissions for local users and groups, but each entry in the ACL can also specify what type of access is given. This allows a great deal of flexibility in setting up a network. In addition, special file-encryption programs can be used to encrypt data while it is stored on the hard disk.
Microsoft strongly recommends that all network shares be established using NTFS. While NTFS security is important, though, it doesn’t matter at all what file system you are using if you log in to your workstation and leave, allowing anyone to sit down at your desk and use your account.
Last, don’t overlook the obvious need for physical security. Adding a cable to lock a laptop to a desk prevents someone from picking it up and walking away with a copy of your customer database. Every laptop case we are aware of includes a built-in security slot in which a cable lock can be added to prevent it from easily being carried off the premises.
When it comes to desktop models, adding a lock to the back cover can prevent an intruder with physical access from grabbing the hard drive or damaging the internal components. You should also physically secure network devices, such as routers, access points, and the like. Place them in locked cabinets, if possible, for if they are not physically secured, the opportunity exists for them to be stolen or manipulated in such a way as to allow someone unauthorized to connect to the network.
Wired and Wireless Security Whether your SOHO network is wired or wireless, there are some basic security principles you want to keep in mind. The first is to configure firewall settings to block unwanted traffic. We’ve talked a lot about firewalls already and it is important to configure them to keep as many potential problems out as possible – turn off the ability to receive types of data that your users do not need and constantly monitor, tweak, and refine these settings.
Next, pay attention to port forwarding. On the router, the port configuration dictates what traffic is allowed to flow through. The router can be configured to enable individual port traffic in, out, or both and is referred to as port forwarding. If a port is blocked (such as 80 for HTTP or 21 for FTP), the data will not be allowed through, and users will be affected. Port forwarding is also known as port mapping and both are subsets of what a firewall does and the amount of tweaking they require to get right is about the same.
The basic premise behind content filtering is that some things are blocked – if a user attempts to go to a site that you do not want them to, for example, a message can appear telling them that access is denied. You can choose to block networks, types of sites, individual sites, or almost anything else on a granular level. While content filtering can be accomplished a number of ways, one of the most common is with parental controls (which are not available on a machine connected to the network through a domain). Within Windows 8.1, for example, choose User Accounts and Family Safety from the Control Panel then choose either to turn on Family Safety for a new child’s account and then, after choosing or creating the account, you can configure options such as those shown in Figure 19.8.

Figure 19.8 Family Safety settings in Windows 8.1
Note that you can set time limits for computer usage, monitor sites they can access and control which apps can be run by this account.
Summary
In this chapter, you learned about the various issues related to security that appear on the A+ 220–902 exam. Security is a popular topic in computing, and the ways in which a troublemaker can cause harm increase regularly. Because of this, CompTIA expects everyone who is A+ certified to understand the basic principles of security and be familiar with solutions that exist.
In this chapter, you learned of security problem areas and issues that can be easily identified. Problem areas include viruses, Trojans, worms, and spyware. Security solutions include implementing encryption technology, using authentication, implementing firewalls, and incorporating security at many levels.
Security is a set of processes and products. For a security program to be effective, all of its parts must work and be coordinated by the organization.
Exam Essentials
Be able to describe why antivirus software is needed. Antivirus software looks at a virus and takes action to neutralize it based on a virus definition database. Virus definition database files are regularly made available on vendor sites.
Understand the need for user education. Users are the first line of defense against most threats, whether physical or digital. They should be trained on the importance of security and how to help enforce it.
Know the characteristics and types of viruses used to disrupt systems and networks. Several different types of viruses are floating around today. The most common ones are polymorphic viruses, stealth viruses, retroviruses, multipartite viruses, and macro viruses.
Know the various types of social engineering. Social engineering variants include shoulder surfing (watching someone work) and phishing (tricking someone into believing they are communicating with a party other than the one with whom they are communicating). Variations on phishing include vishing and whaling as well as spear phishing.
Understand the need for good passwords. Passwords are the first line of defense for protecting an account. A password should be required for every account and strong passwords should be enforced. Users need to understand the basics of password security and work to keep their accounts protected by following company policies regarding passwords.
Disable what you don’t need. All accounts that are not in use—especially the guest account—should be disabled. You should also disable the Autorun feature to prevent it from running programs or commands that could inflict harm without your knowledge.
Understand the difference between standard and low-level formatting. Standard formatting uses operating system tools and marks the drive as available for holding data without truly removing what was on the drive (thus the data can be recovered). A low-level format is operating system independent and destroys any data that was on the drive.
Understand how to physically destroy a drive. A hard drive can be destroyed by tossing it into a shredder designed for such a purpose, or it can be destroyed with an electromagnet in a process known as degaussing. You can also disassemble the drive and destroy the platters with a drill or other tool that renders the data irretrievable.
Know the names, purpose, and characteristics of wireless security technologies. Wireless networks can be encrypted through WEP, WPA, and WPA2 technologies. Wireless controllers use service-set identifiers (SSIDs)—32-character case-sensitive strings—that must be configured in the network cards to allow communications. However, using ID string configurations doesn’t necessarily prevent wireless networks from being monitored, and there are vulnerabilities specific to wireless devices.
Understand the basics of antenna placement and radio power levels. Antenna placement can be crucial in allowing clients to reach an access point. Place access points near the center of the area to be served and high enough to get around most obstacles. Know that power level controls allow you to reduce the amount of output provided.
Understand why ports should be disabled. Disable all unneeded protocols/ports. If you don’t need them, remove them or prevent them from loading. Ports not in use present an open door for an attacker to enter.
Understand the purpose of MAC filtering. MAC filtering allows you to limit access to a network to MAC addresses that are known and filter out (deny access to) those that are not.
Review Questions
The answers to the chapter review questions can be found in Appendix A.
-
Which component of physical security addresses outer-level access control?
- Perimeter security
- Mantraps
- Security zones
- Strong passwords
-
You have a very small network in a home-based office, and you want to limit network access to only those hosts that you physically own. What should you utilize to make this possible?
- Static IP addresses
- Disabled DNS
- Default subnet mask
- Empty default gateway
-
As part of your training program, you’re trying to educate users on the importance of security. You explain to them that not every attack depends on implementing advanced technological methods. Some attacks, you explain, take advantage of human shortcomings to gain access that should otherwise be denied. What term do you use to describe attacks of this type?
- Social engineering
- IDS system
- Perimeter security
- Biometrics
-
You’re in the process of securing the IT infrastructure by adding fingerprint scanners to your existing authentication methods. This type of security is an example of which of the following?
- Access control
- Physical barriers
- Biometrics
- Softening
-
Which type of attack denies authorized users access to network resources?
- DoS
- Worm
- Logic bomb
- Social engineering
-
As the security administrator for your organization, you must be aware of all types of attacks that can occur and plan for them. Which type of attack uses more than one computer to attack the victim?
- DoS
- DDoS
- Worm
- UDP attack
-
A server in your network has a program running on it that bypasses authentication. Which type of attack has occurred?
- DoS
- DDoS
- Back door
- Social engineering
-
You’ve discovered that an expired certificate is being used repeatedly to gain logon privileges. Which type of attack is this most likely to be?
- Man-in-the-middle attack
- Back door attack
- Replay attack
- TCP/IP hijacking
-
A junior administrator comes to you in a panic. After looking at the log files, he has become convinced that an attacker is attempting to use a duplicate IP address to replace another system in the network to gain access. Which type of attack is this?
- Spoof
- Back door attack
- Worm
- TCP/IP hijacking
-
Which of the following is different from a virus in that it can reproduce itself, it’s self- contained, and it doesn’t need a host application to be transported?
- Worm
- Smurf
- Phish
- Trojan
-
A smurf attack attempts to use a broadcast ping on a network; the return address of the ping may be that of a valid system in your network. Which protocol does a smurf attack use to conduct the attack?
- TCP
- IP
- UDP
- ICMP
-
Your system log files report an ongoing attempt to gain access to a single account. This attempt has been unsuccessful to this point. What type of attack are you most likely experiencing?
- Password-guessing attack
- Back door attack
- Worm attack
- TCP/IP hijacking
-
One of the vice presidents of the company calls a meeting with the information technology department after a recent trip to competitors’ sites. She reports that many of the companies she visited granted access to their buildings only after fingerprint scans, and she wants similar technology employed at this company. Of the following, which technology relies on a physical attribute of the user for authentication?
- Smart card
- Biometrics
- Mutual authentication
- Tokens
-
Your company provides medical data to doctors from a worldwide database. Because of the sensitive nature of the data you work with, it’s imperative that authentication be established on each session and be valid only for that session. Which of the following authentication methods provides credentials that are valid only during a single session?
- Token
- Certificate
- Smart card
- License
-
Your help desk has informed you that they received an urgent call from the vice president last night requesting his logon ID and password. When talking with the VP today, he says he never made that call. What type of attack is this?
- Spoofing
- Replay attack
- Social engineering
- Trojan horse
-
Internal users suspect repeated attempts to infect their systems as reported to them by pop-up messages from their virus-scanning software. According to the pop-up messages, the virus seems to be the same in every case. What is the most likely culprit?
- A server is acting as a carrier for a virus.
- You have a caterpillar virus.
- Your antivirus software has malfunctioned.
- A DoS attack is under way.
-
You’re working late one night, and you notice that the hard drive on your new computer is very active even though you aren’t doing anything on the computer and it isn’t connected to the Internet. What is the most likely suspect?
- A disk failure is imminent.
- A virus is spreading in your system.
- Your system is under a DoS attack.
- TCP/IP hijacking is being attempted.
-
You’re the administrator for a large bottling company. At the end of each month, you routinely view all logs and look for discrepancies. This month, your email system error log reports a large number of unsuccessful attempts to log on. It’s apparent that the email server is being targeted. Which type of attack is most likely occurring?
- Software exploitation attack
- Backdoor attack
- Worm
- TCP/IP hijacking
-
Upper management has decreed that a firewall must be put in place immediately, before your site suffers an attack similar to one that struck a sister company. Responding to this order, your boss instructs you to implement a packet filter by the end of the week. A packet filter performs which function?
- Prevents unauthorized packets from entering the network
- Allows all packets to leave the network
- Allows all packets to enter the network
- Eliminates collisions in the network
-
Which media is susceptible to viruses?
- Tape
- Memory stick
- CD-R
- All of the above
Performance-Based Question
You will encounter performance-based questions on the A+ exams. The questions on the exam require you to perform a specific task, and you will be graded on whether or not you were able to complete the task. The following requires you to think creatively in order to measure how well you understand this chapter’s topics. You may or may not see similar questions on the actual A+ exams. To see how your answers compare to the authors’, refer to Appendix B.
Pop-ups are proving to be a security concern—as well as an annoyance—throughout the office. Configure your Windows 7 machine to block pop-ups but to allow www.sybex.com through so you can access the material you are studying for the A+ exams.
