Chapter 5: Threat and Vulnerability Management
In this chapter, we will primarily deal with security operation center activities. Security professionals need to identify different types of threats. Insider threats and Advanced Persistent Threats (APT) are two of the biggest threats currently targeting government departments and commercial organizations. It is important to understand the threat actor skills and motivations, and also the resources that they have available to them – how much time can they afford to spend planning attacks? What is their level of financial backing? How sophisticated are the attackers? Is money an objective of the attack (for example, ransomware is nearly always about financial gain)? We need to use threat frameworks to understand how to recognize threats and respond. It is important for security professionals to be able to identify indicators of compromise, and within our security operations center, we also need to respond using a variety of techniques. In this chapter, we will cover the following topics:
- Intelligence types
- Actor types
- Threat actor properties
- Intelligence collection methods
- Frameworks
- Indicators of compromise
- Responses
Intelligence types
Gathering threat intelligence is important as this will allow security professionals to be proactive and equipped to meet the challenges of cyberattacks. We will look at tactical, strategic, and operational intelligence. From a practical point of view, we also need to understand what tools are available to gather this knowledge.
Tactical intelligence
Tactical threat intelligence gathering would be performed primarily by security experts and analysts. It is primarily focused on short-term objectives. This would be the job of the Security Operations Center (SOC) staff who would analyze feeds from multiple security tools, including Security Information and Event Management (SIEM) systems. To gather tactical intelligence, we can use threat feeds and open source and closed source/proprietary feeds, depending upon the business. Tactical intelligence will use real-time events and technical analysis to understand adversaries and their tools and tactics. We need the latest tools to identify new and zero-day exploits (threats that have no known patches or mitigation). The shorter-term goals will be to identify current threats and emerging threats using technology and automation.
Strategic intelligence
Strategic threat intelligence should be conveyed to senior managers and leaders within an enterprise. It is based on long-term goals – for example, what are the threats to our industry? Or who are the primary threat actors targeting our industry? An organization would collect historical data and use this to look at trends. You could say strategic intelligence is more about Who and Why. A military defense contractor should know that China may target them to steal their intellectual property (IP). Based on this assumption, we must address this risk with the appropriate countermeasures.
Operational intelligence
Operational threat intelligence gathering is often performed by forensics or incident first responders. We need to understand an adversary's techniques and methodologies. We can search through previous data logs looking for signatures from particular activities from known threat actors. We would use this technique to discover previous attacks that were not detected. If you are searching for evidence of nation-state threat actors, you may look at one of the known documented groups, APT30 (indicators strongly suggest they are sponsored at a government level), and their mode of operation is well documented. Previous attacks have used spear phishing as the first step.
See the following link for more intelligence on APT30 activities:
https://attack.mitre.org/versions/v9/groups/G0013/
Commodity malware
One common form of attack is to use commodity malware. This is malware that is cross-platform and has multiple purposes. A good example of commodity malware would be a remote access trojan. This could be used against many different operating systems and the end goal can be very different. Effective defenses include patching systems.
Targeted attacks
Targeted attacks may use very specific tools. Examples of targeted attacks include the following:
- Supply chains: Attacking software or hardware that is provided by third parties to your organization.
- Botnets: This will target your organization with a DDOS (distributed denial of service).
- Spear phishing attack: Employees of your organization may receive malicious links within email messages.
Actor types
Organizations must consider threats from many different sources, from the unsophisticated script kiddie to government-sponsored attacks involving nation-state actors. We must also consider attacks from cybercriminals – at present, organized crime is the fastest-growing adversary. In over half of reported cases, major information system breaches can be attributed to insiders. We will highlight these threat actors in the following section.
Advanced persistent threat – nation-state
APTs are persistent in nature and have a strong determination to compromise your systems, typically using advanced techniques, and often have access to high-level resources (nation-states).
As APTs are difficult to detect and highly sophisticated, they may remain unknown for many months or years.
Cybersecurity professionals have labeled all the known adversaries and collected evidence of tools and activities undertaken by these adversaries. There are over 30 known APT groups currently active. For an up-to-date list, follow this URL:
https://www.fireeye.com/current-threats/apt-groups.html
Massachusetts Institute of Technology Research and Engineering (MITRE) also publishes a list of APT threat actors:
https://attack.mitre.org/versions/v9/groups/
The goals of APTs are high-level access to intellectual property, government systems, military intelligence, and more. The groups are split between organized crime and nation-state actors.
The goal of nation-state attacks can be to destabilize governments, interfere with the money supply, or attack critical infrastructure.
Insider threat
Insider threats are one of the biggest reasons for security breaches. It is estimated that more than 50% of breaches are attributable to insiders. It could be accidental or it could be a user who has a grudge against the organization (such as a disgruntled employee).
Competitor
A competitor is an entity that works in the same field as your organization. You might be a manufacturer of a very specific and valuable item. Your IP and design plans are therefore very important. There is evidence that foreign powers have sponsored attacks that have actually led to data breaches that allowed those nations to enhance their military manufacturing at the expense of United States defense corporations. There are many instances where commercial enterprises have resorted to underhand tactics to gain access to Intellectual Property (IP)
Some best practices to mitigate these threats would include the following:
- Robust screening for new employees
- Non-Disclosure agreements (NDAs)
- User behavior analysis (UBA)
- Data loss Prevention (DLP)
Hacktivist
The hacktivist has a political goal. They may have a grudge against banks, governments, and other high-profile targets. Environmentalists may target oil and gas companies. A good example is a group called Anonymous. They have launched many successful attacks over the years against big businesses, including Sony, PayPal, VISA, and Mastercard. Recently, the group targeted tech billionaire Elon Musk in retaliation for his activity concerning cryptocurrency. See the following link for more information: https://tinyurl.com/anonymoustarget
Script kiddie
Script kiddies are often untrained and lack sophistication. However, they can still cause a lot of damage. They download tools and scripts to attack your organization. A goal may be just to vandalize a site or to prove they can gain access. They often do it for the rush and the high of being a hacker.
Organized crime
Organized crime cybercriminals are a big threat. Their goal is to gain access to finances. They are often sophisticated – they can attack individuals and they can attack big businesses using many different techniques, including phishing, spear-phishing, and pharming sites. The goal is generally to steal money or your valuable information and they will sell the information on the dark web to the highest bidder. Cybercriminals and organized crime actors also launch attacks against your organization using ransomware (this is currently a major source of income for organized crime). Security professionals are now referring to these groups as Big Game Hunters (BGH).
Individuals may also be targeted through ransomware, where the victim believes they have committed a crime and are willing to pay to avoid further action.
To further understand threats, we need to understand why they are targeting our organization and how.
Threat actor properties
When building up a picture of an adversary, it is important to understand what motivates them, what backing they have, and what approaches they may use.
Resources
The resources available to a threat actor can make a big difference to the effectiveness of the attack. Government-sponsored threat actors working in large teams will have lots of available resources, including sophisticated hardware and software tools. They have access to money, time, skilled people, intelligence, and so on. They can deploy personnel physically to perform reconnaissance missions. They can also access intelligence gathered by other government agencies.
Time
Nation-states or organized crime threat actors are full-time professional hackers (it's their job); they are not doing this as a hobby. Another consideration is the amount of time that they have access to your systems for. APTs may be in place for months or years without an organization's knowledge. This means the amount of information that may have been stolen may also be difficult to assess.
Money
How well funded are the attackers? In many cases, very well funded. The potential gains for cybercriminals are enormous. Ransomware alone is believed to have accounted for $20 billion in damages globally in 2020. The FBI has estimated the cost worldwide to be in excess of $4.2 trillion for 2020, and this is predicted to grow to over $10 trillion by 2025, according to reports in this Cybercrime Magazine article: https://tinyurl.com/cybercrimegrowth
Supply chain access
You must always consider any third-party involvement to be a risk. Your supply chain is where you may be targeted. This could be third-party supplied software or while working with Business-To-Business (B2B) partners or contracting out services to third-party suppliers. Anything that you do not directly control could be considered a supply chain attack. The firmware in embedded devices or firmware updates on a smartphone could contain malware. When changing part of your network infrastructure, for example, deploying a new firewall may put you at risk of a supply chain threat.
In 2020, SolarWinds was attacked by hackers who were able to plant malware into updates destined for SolarWinds customers. There are over 33,000 installed instances of SolarWinds Orion and around 18,000 customers installed the patch. The customers included fortune 500 companies, critical infrastructure-related businesses, and government agencies. Hackers were able to access these systems through a backdoor for over nine months before the breach was discovered. By putting our trust in third parties, we run the risk of creating vulnerabilities. For more details, see the following link:
https://www.bbc.co.uk/news/technology-55321643
Capabilities and sophistication
Mainstream attacks may be more frequent, but the capabilities of the attackers are usually unsophisticated. These are the types of attacks used by script kiddies or hackers using widely distributed tools and techniques. When we are dealing with a more capable and sophisticated adversary, there will be a lower volume of attacks. These attacks, however, will be much more sophisticated. For example, APTs launched by nation-states.
Identifying techniques
Identifying attacks has become very challenging and we must use many tools and techniques, such as advanced analytics, machine learning (ML), and artificial intelligence (AI). These are just some of the tools that can help us to detect these types of attacks.
It is vitally important for security professionals to understand the tools and techniques that enable an organization to be well prepared for future attacks.
Intelligence collection methods
There are multiple sources to gather intelligence. Some are automated but, in many cases, there will need to be an investment in time to truly research the available intelligence resources.
Intelligence feeds
There are many sources of intelligence that can be displayed in a dashboard format. We might want to see threat maps from a live feed. A good example would be showing the current activity globally for things like botnets and command and control (C2) servers. There is a good example hosted by spamhaus.com, which can be found at the following link: https://www.spamhaus.com/threat-map/. There are many good open source options and many commercial (paid for) options from security organizations such as Fortinet, FireEye, Symantec, and many others. In the United Kingdom, the National Cyber Security Centre (NCSC) offers a free threat feed, but only to affiliated government departments.
A good example of an all-round cyber threat feed can be found at the following link:
https://otx.alienvault.com/preview
See Figure 5.1 for an example threat feed:
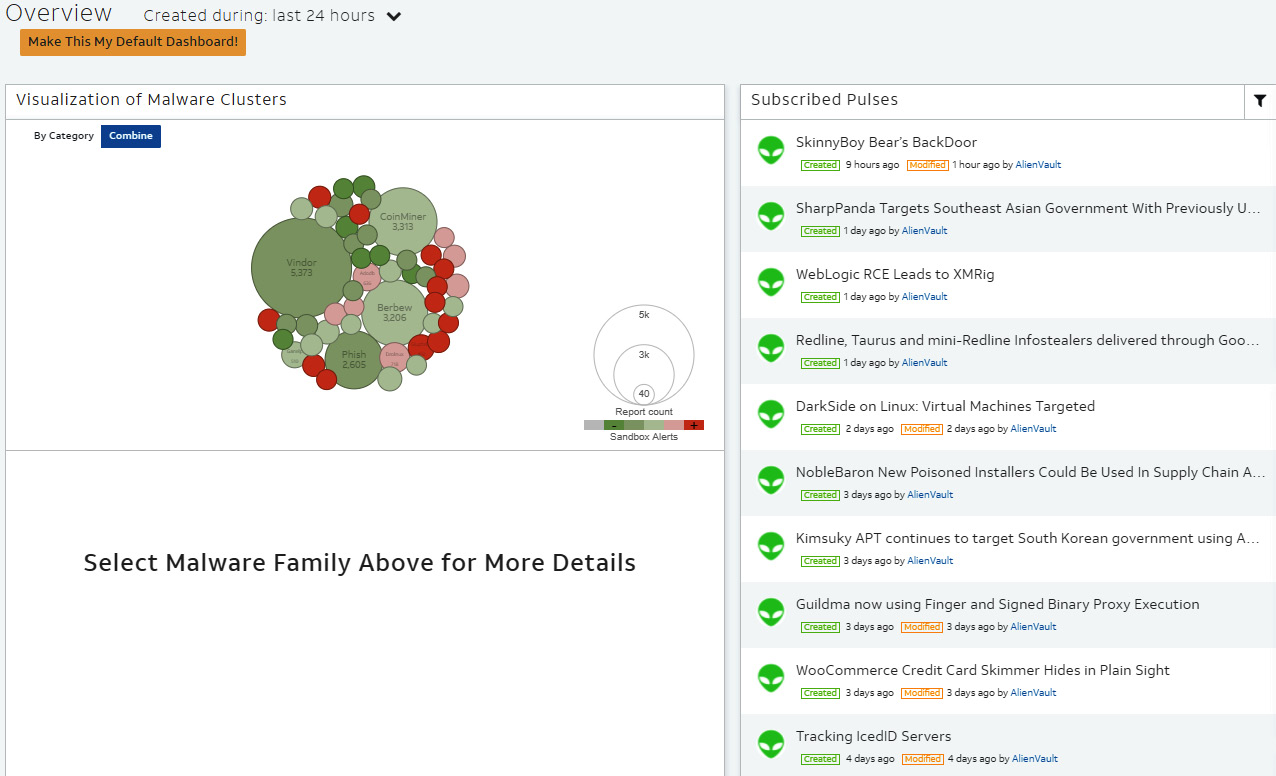
Figure 5.1 – Threat feed
While general cybersecurity threat feeds are very useful in understanding the current threat landscape, more specific feeds are available for different industries, including critical infrastructure. Figure 5.2 shows options available for different business sectors:
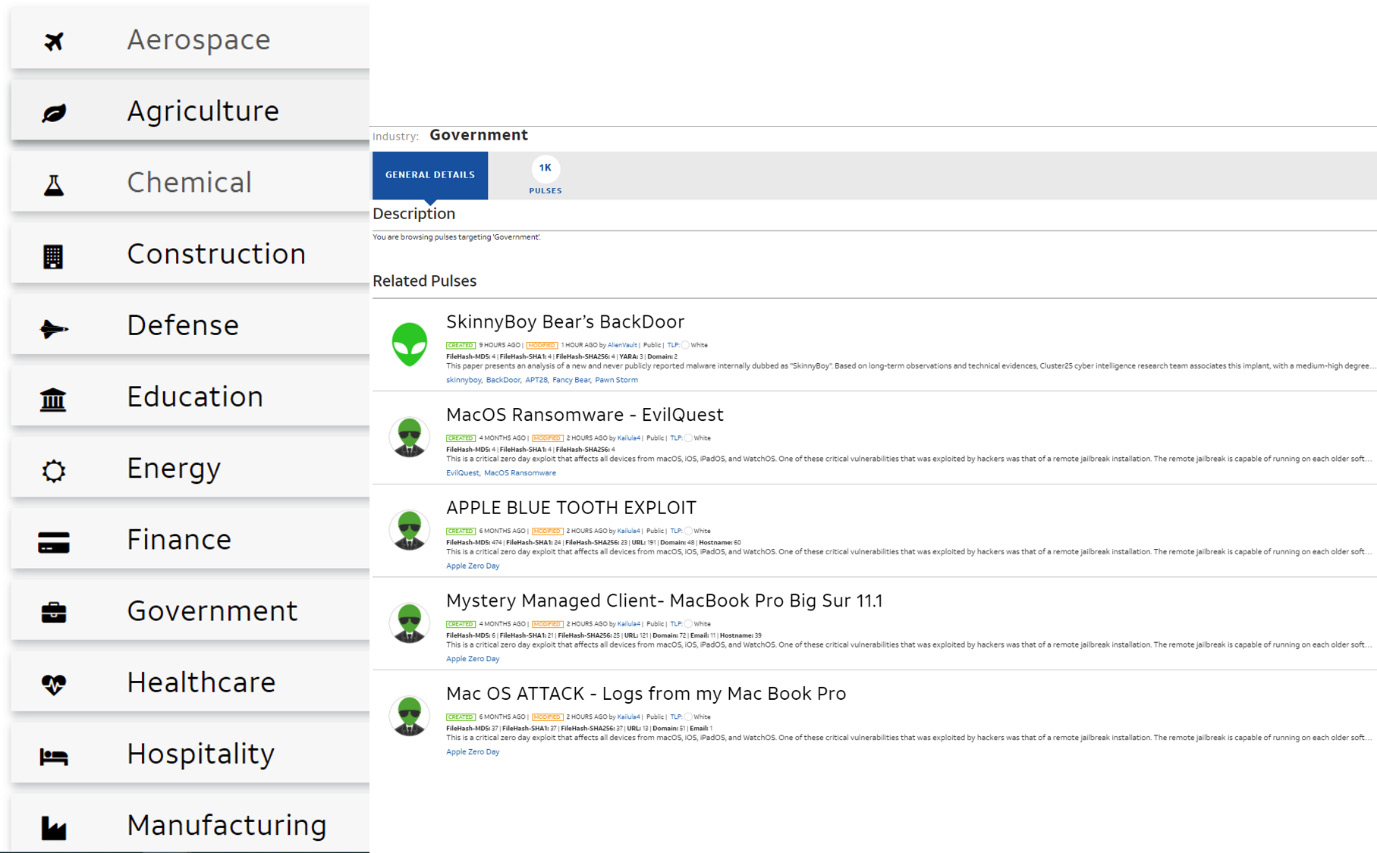
Figure 5.2 – Industry-specific threat feed
There is a supported standard for information sharing of threat feeds. Trusted Automated eXchange of Indicator Information (TAXII) is a collection of services to support information sharing and Structured Threat Information eXpression (STIX) is a standard language supported by MITRE.
Deep web
The deep web, also known as the dark web, is an alternative to the regular internet (also sometimes referred to as the surface web). There is no content indexing on the deep web. The deep web is used in countries where personal freedoms are restricted and censorship is in place. But a significant proportion of content on the deep web is generated by criminal activity. Criminals will sell stolen credentials and zero-day exploits to the highest bidders. It is important for law enforcement and cybersecurity professionals to remain aware of the activities and data that criminals are sharing on the deep web. To access sites on the dark web, you will have to gain access to the URL, as it will not be indexed. You will also need to install a browser such as Tor. Figure 5.3 shows the Tor browser, which looks similar to many other regular web browsers. However, you will need to be given access to a site URL, as they cannot be searched:
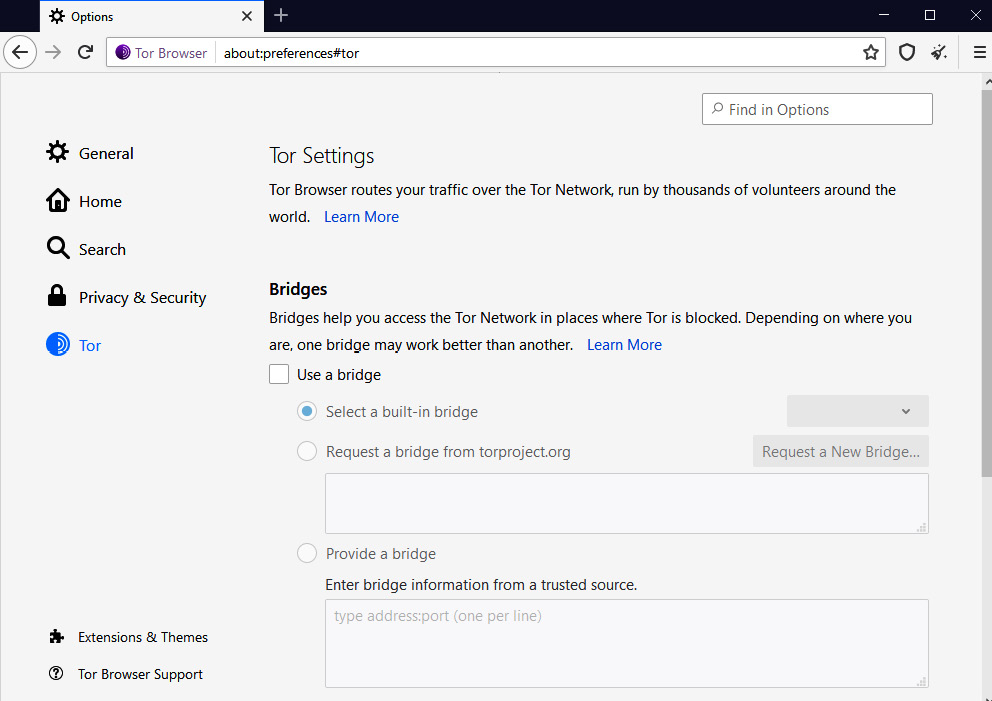
Figure 5.3 – Tor browser
Not all threat intelligence is easy to find and, in some cases, it may require research time and monetary outlay.
Proprietary intelligence
Propriety threat intelligence will only be made available to subscribers. Good examples of this would be certain government threat intelligence that will only be available to certain government agencies. Law enforcement may share information only with certain agencies or related law enforcement departments. Military and classified government intelligence will not be shared and can be considered proprietary.
Open source intelligence
Open source intelligence (OSINT) is freely available. It can be used for many different reasons. It is useful to understand this from an attacker's perspective. Email addresses, company information on websites, and DNS records are just some of the pieces of information that are freely available, indexed, and searchable across the internet.
Human intelligence
Human intelligence (HUMINT) is intelligence gathered by real people (not machines). This means putting boots on the ground, in a military sense. This could involve physical reconnaissance of a site of interest (perhaps a factory or military site). This skill set will require a certain amount of tradecraft by the intelligence officer. They will be able to read signs and body language, and they will use profiling to understand the motivations and goals of attackers.
To help security professionals understand how to use threat intelligence we can use one of the industry frameworks.
Frameworks
An attack framework is very useful to allow us to understand the tools, the tactics, and the techniques attackers will use to launch successful attacks. Security professionals must be able to understand how they plan their attacks right from the initial reconnaissance through to completion of the attack. We will cover some of the industry-accepted approaches in this section.
MITRE adversarial tactics, techniques, and common knowledge (ATT&CK)
MITRE is a not-for-profit organization. It was founded in 1958, primarily as an organization to support government and industry. Many of the current members come from industry (for example, Microsoft and Fujitsu are current members). MITRE receives government funding to carry out research and is well known for its published attack frameworks and tactics. The matrices are created to understand the tactics and techniques that attackers will use against operating systems, cloud network mobility, and industrial control systems. In Figure 5.4, we can see a subset of the Enterprise MITRE ATT&CK framework:
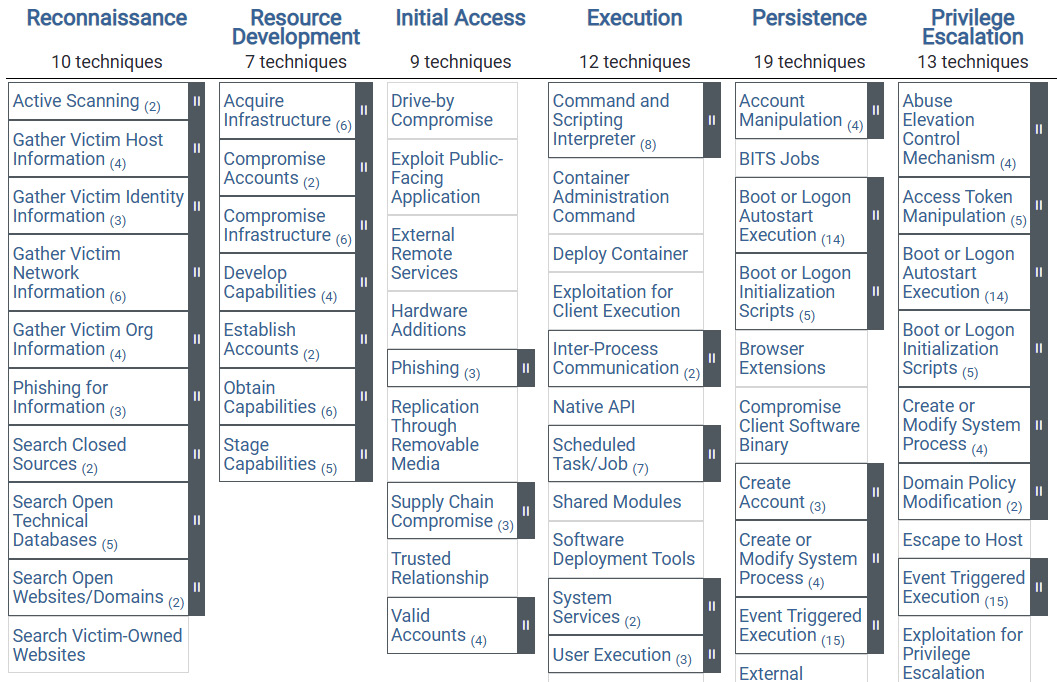
Figure 5.4 – MITRE Att&ck framework (© 2021 The MITRE Corporation. This work is reproduced and distributed with the permission of The MITRE Corporation)
In the Enterprise model, there are 14 headings to give good clear guidance on attack vectors and their impacts. The matrix can be found at the following link:
https://attack.mitre.org/versions/v9/matrices/enterprise/
ATT&CK for industrial control systems
As industrial control systems (ICSes) are seen as critical assets, there are government agencies to support these industries in the United States. The Cybersecurity and Infrastructure Security Agency (CISA) was formed to offer cybersecurity services to the critical industries sectors. CISA has identified 16 sectors that are considered critical infrastructure, including energy, food and agriculture, and critical manufacturing. MITRE also publishes an ATT&CK matrix for these ICSes, helping cybersecurity professionals to identify common tactics used. The ICS matrix can be found at the following link:
https://collaborate.mitre.org/attackics/index.php/Main_Page
MITRE has identified and labeled known attacker groups and their countries of origin. For example, the Sandworm Team has been identified as a nation-state-sponsored military intelligence unit. This group has been accused of attacks against the Ukrainian national power grid and was also responsible for the NotPetya malware attacks in 2017. For more information, see the following link:
https://attack.mitre.org/groups/G0034/
The Diamond model of intrusion analysis
The Diamond model is very useful when profiling threat actors. You can build up a picture of their capabilities and the target or victims. Forensic analysts can use this model when looking for indicators of compromise, in historical logs. When security professionals understand the exact methods used by the adversary, it can help to speed up the detection process. It is important to understand the capabilities of your adversary. This type of framework is very useful for threat hunting, allowing an organization to understand the motivations and the tools and techniques that will be used for an attack. Shown in Figure 5.5 is an example of the Diamond model in use:
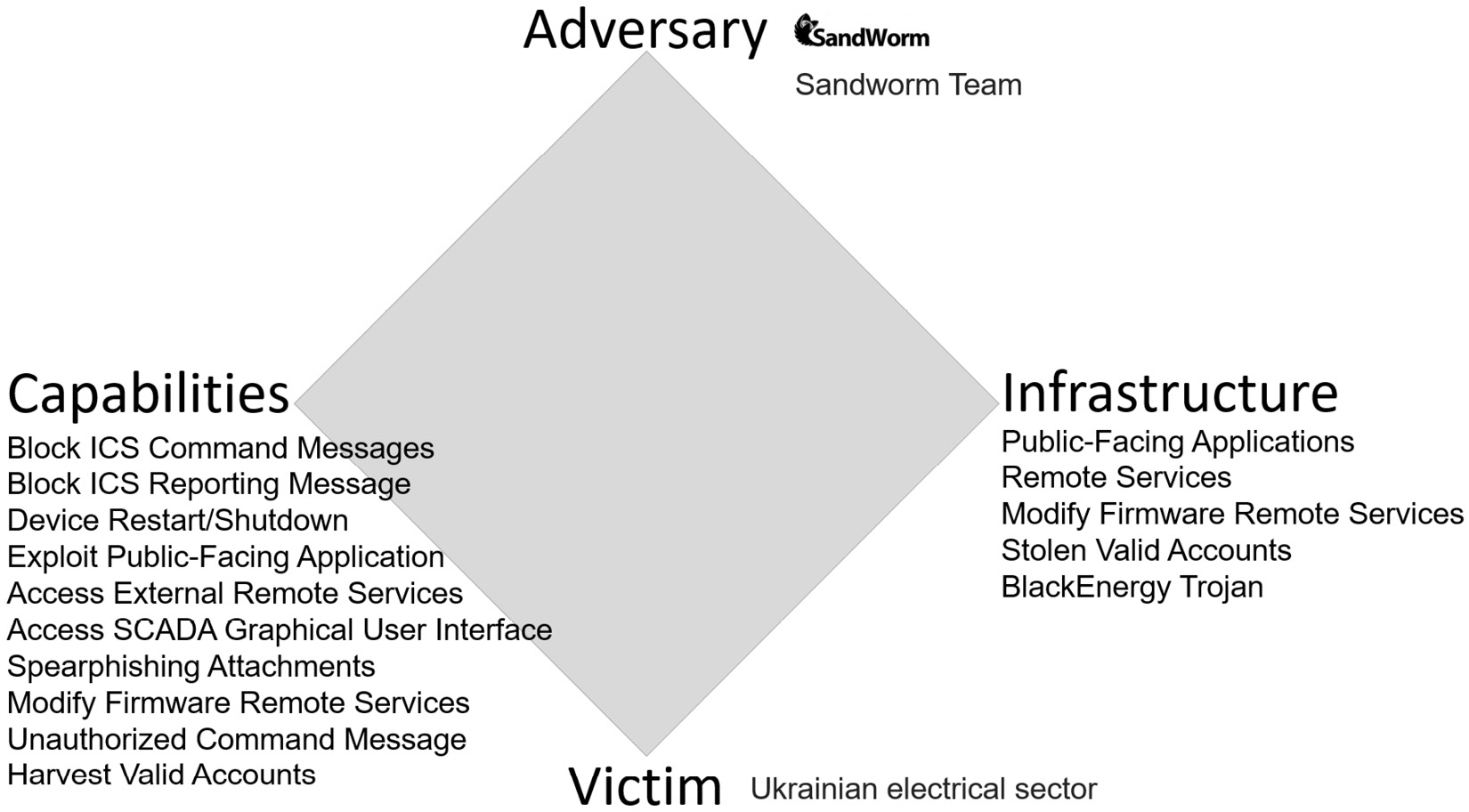
Figure 5.5 – The Diamond model of intrusion analysis
This is a very good approach when focusing on a single attack, maybe during a forensic hunt.
Cyber Kill Chain
The Cyber Kill Chain is a method developed by Lockheed Martin. It is a seven-stage model, which is useful to document each of the steps in the model. If we can break any one of the steps, it can prevent an attack. The seven stages documented by Lockheed Martin are shown in Figure 5.6:
https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html#Resources
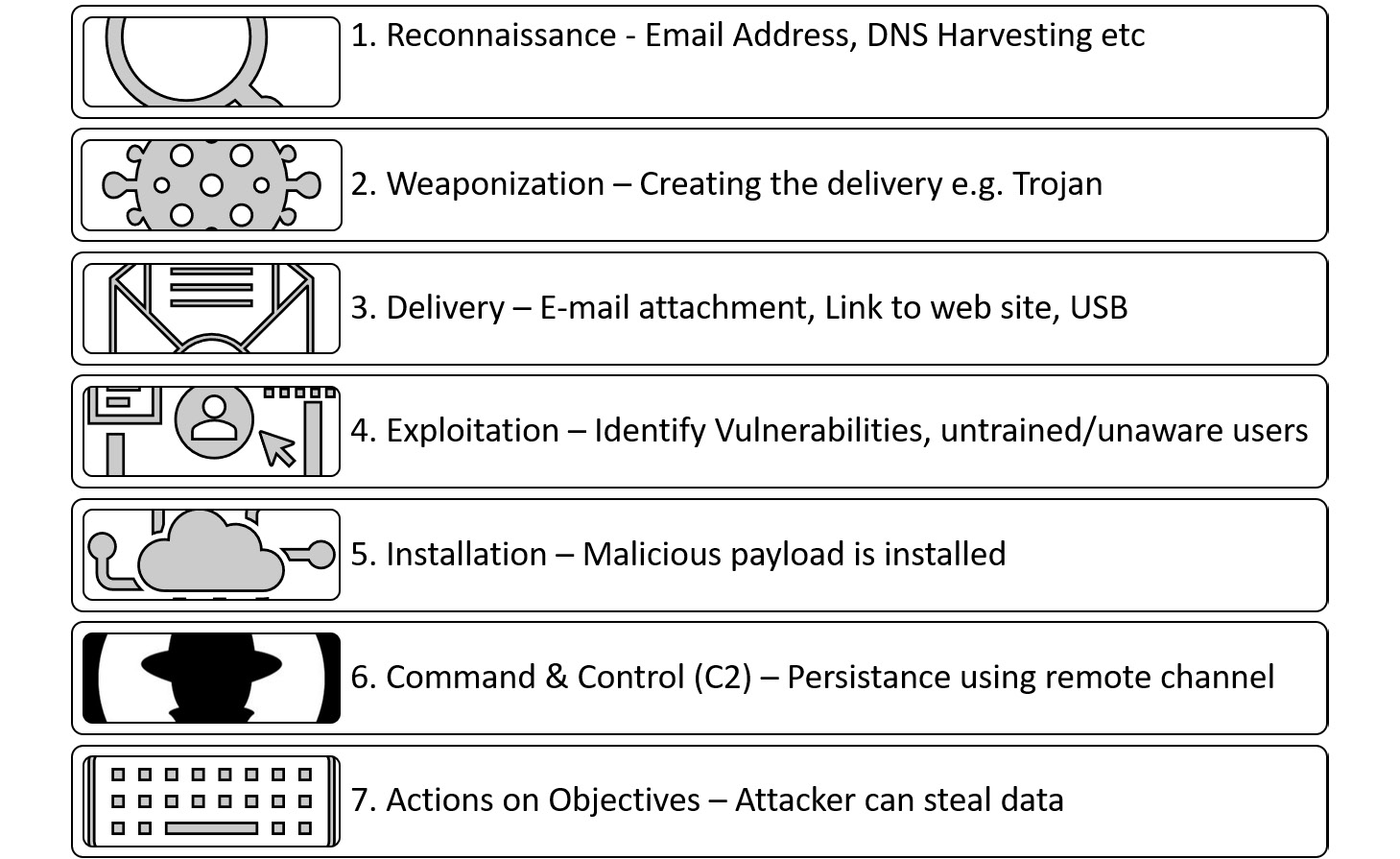
Figure 5.6 – Cyber Kill Chain
Frameworks are a very important asset and can be useful for creating incident response playbooks or giving additional context during an investigation.
Threat hunting
Threat hunting can be used within the context of operational intelligence. We need to adopt one of the threat frameworks and search for Indicators of Compromise (IOC) with a much better understanding of our adversaries' tools and methods. Using this methodology, we are better able to detect APTs.
Threat emulation
Threat emulation allows security professionals to fine-tune their approach to threats using a variety of Tools, Techniques, and Procedures (TTPs). Team security exercises could be one approach, with the red team using the adversary TTP and the blue team defending the network.
To respond to a threat, we need to recognize what event or series of events is actually threatening.
Indicators of compromise
There are many events that would take place on a busy network. Events can be recorded in logs (where an event is unusual) or coupled with another event that itself appears unusual. This could be an indicator of compromise (IOC). Another example of an IOC could be several unsuccessful attempts to connect using SSH to a core network appliance, followed by a successful authentication attempt from an unusual or gray-listed IP address. It is important for the security operation center to be able to identify attacks or threats. To identify IOCs, we need inputs in the form of logs and captured network traffic.
Packet capture
Packet capture (PCAP) files use a standard log format. They allow us to capture real-time data. Captured data can be analyzed using Wireshark, tcpdump, or tshark. See Wireshark capture in Figure 5.7:
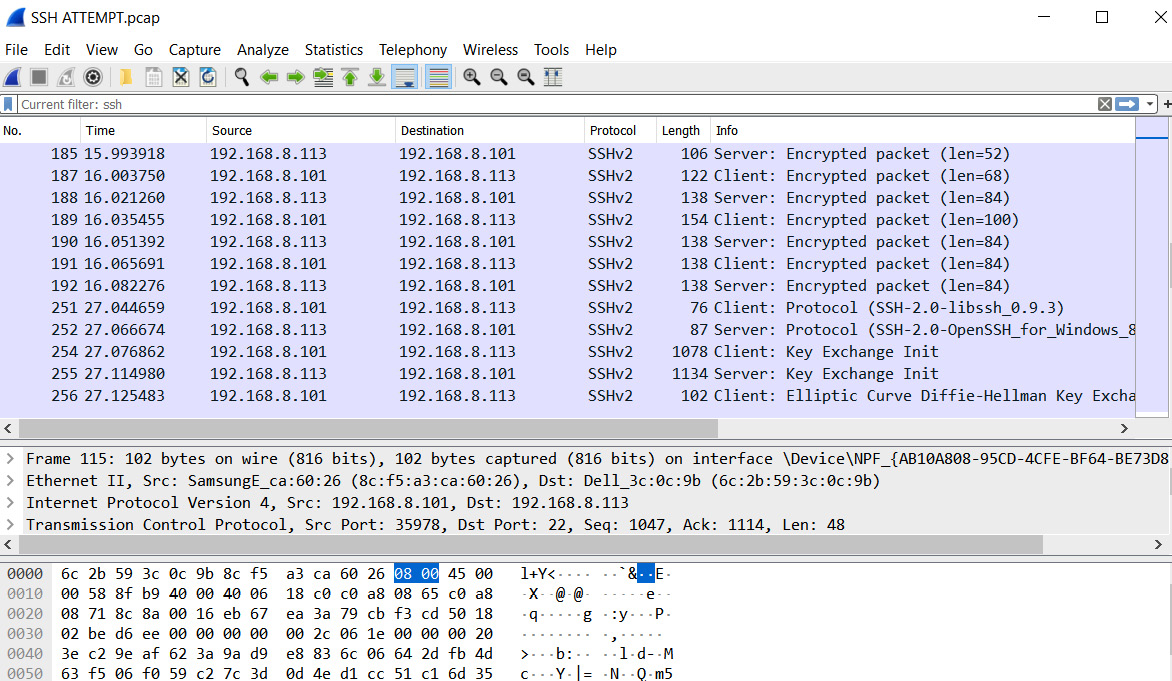
Figure 5.7 – PCAP file
The PCAP format allows logs to be analyzed using different vendor tools and platforms.
Logs
Many different appliances and services will log activities. This could be from applications and services running on a desktop to server-based services. All of this log data can be useful in seeing the big picture. A standard for Linux/Unix-based operating systems is syslog. This allows for facility codes to be assigned to events. For example, email events would be tagged with a facility code of 2. See Figure 5.8 for a full list. This is fully documented in RFC 5424. Full documentation can be found at the following URL:
https://datatracker.ietf.org/doc/html/rfc5424
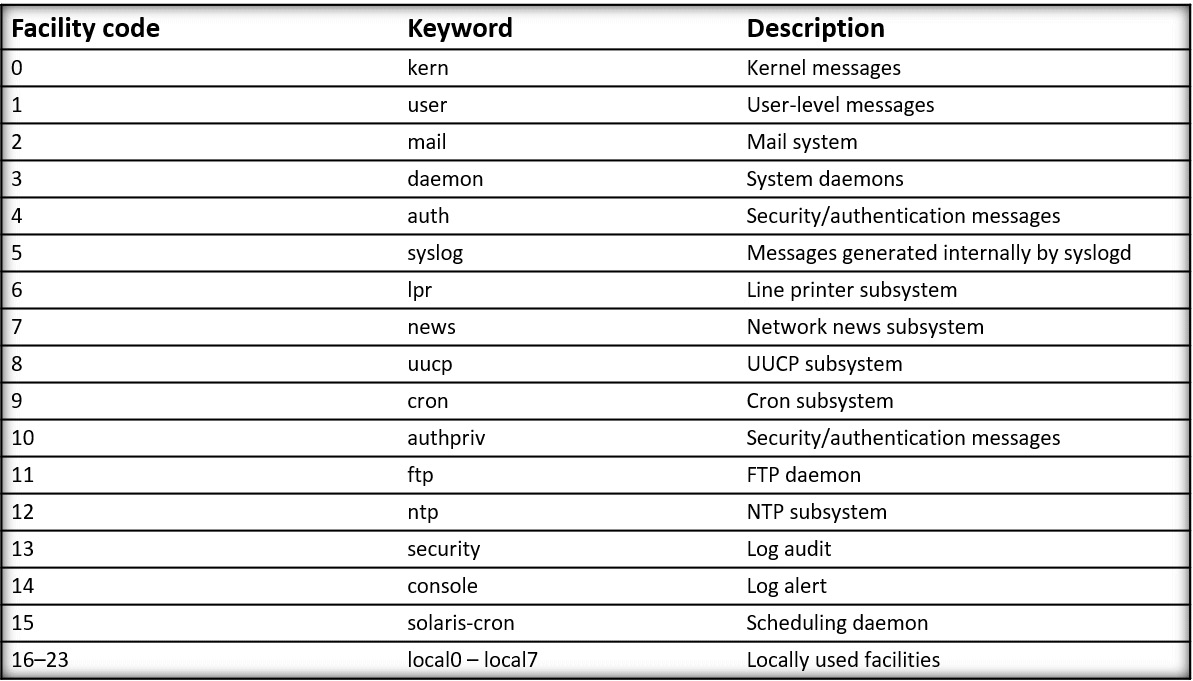
Figure 5.8 – Syslog facility codes
Additional logs showing network activity can also be useful.
Network logs
Network logs allow us to capture network traffic activity on switches, routers, firewalls, intrusion detection systems, and many more network appliances. Figure 5.9 shows an example of a firewall log:
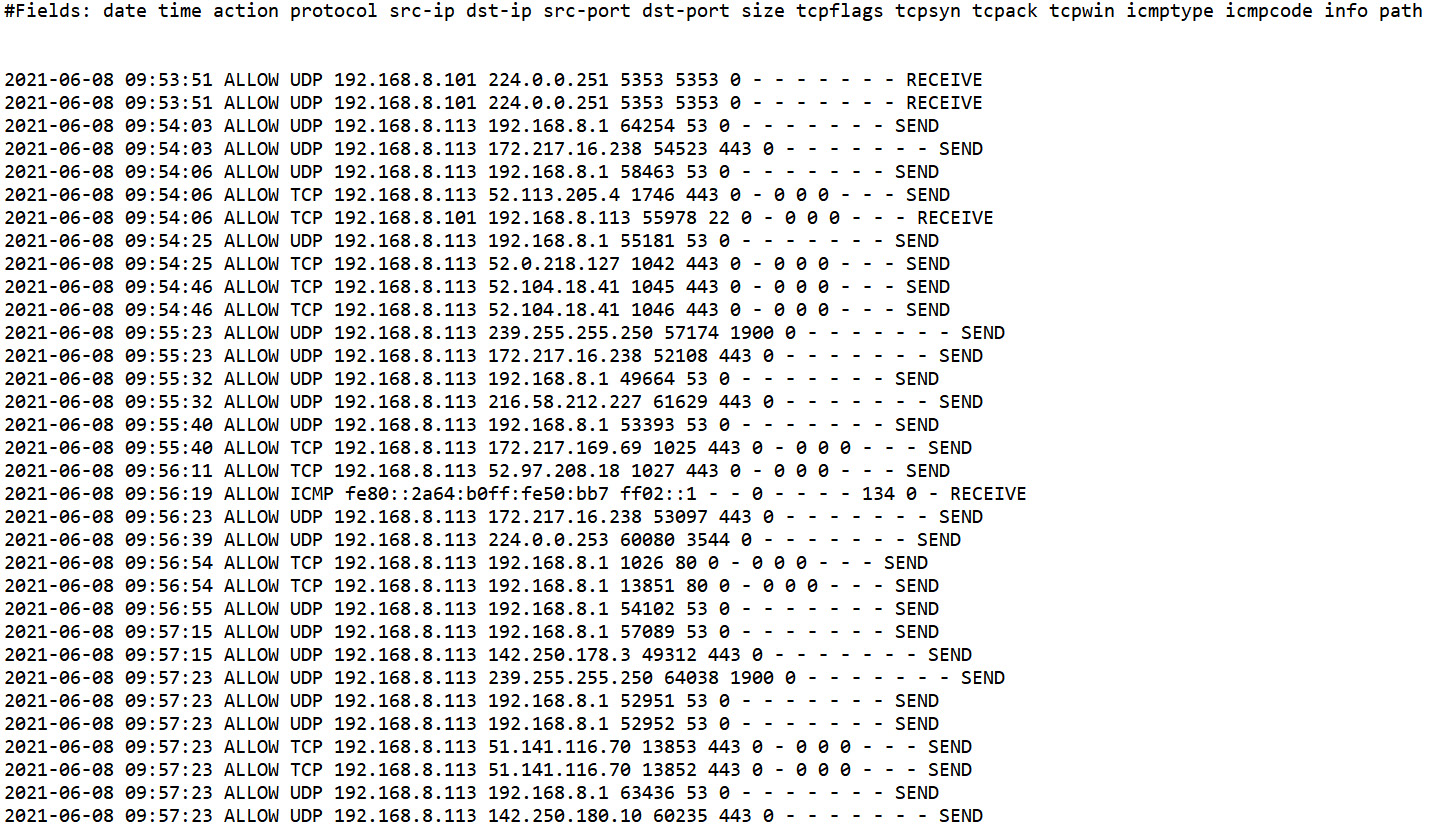
Figure 5.9 – Network firewall logs
Network logs can be forwarded to SIEM for more analysis.
Vulnerability logs
Vulnerability logs will be created by vulnerability scanning tools such as Nessus, OpenVAS, and Nmap. It can be useful to consolidate and have a single pane of glass to present all of this collected data. Vulnerability logs can be forwarded to SIEM for automation and alerts. Figure 5.10 shows a log from a vulnerability scan:
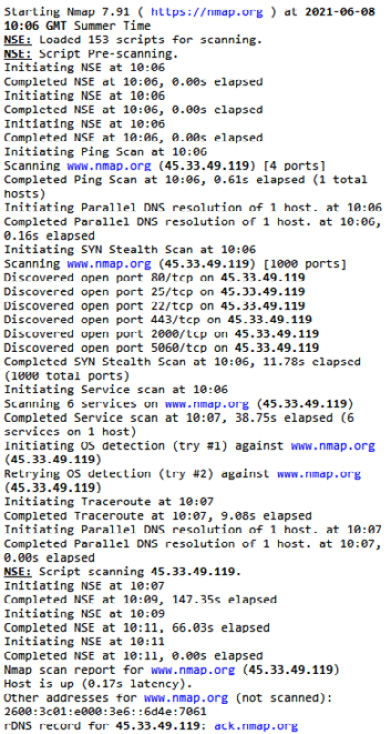
Figure 5.10 – Vulnerability log
When we run a vulnerability scan, it is important to log the results.
Operating system logs
Operating systems will create logged data. This can be useful, as many services may be hosted on an operating system platform. These logs can be uploaded to endpoint detection and response (EDR) systems, allowing more granular control and visibility of that data. Logs can include application events, security events, and service logs, such as DNS or DHCP. Figure 5.11 shows a partial security log from a Windows client:
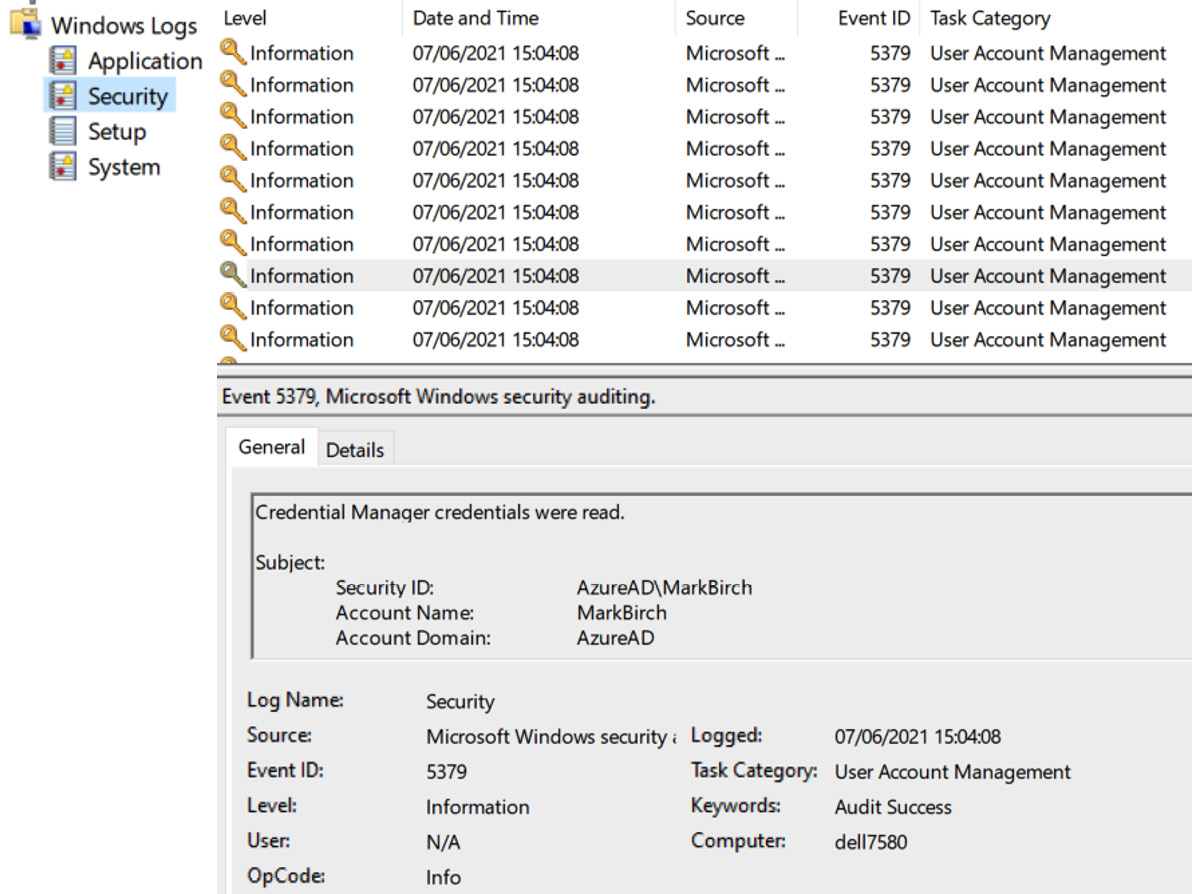
Figure 5.11 – Windows operating system security log
Security logs are very important for accountability and regulatory compliance.
Access logs
Access logs provide an audit trail, when accountability must be established. A security audit may be conducted to establish who accessed an information system through remote access services or who changed permissions on a user's mailbox. We may want to record physical access to a location, such as who gained physical access to the data center at the time when a security breach occurred. Access logs will be important for accountability and may be required to meet regulatory compliance.
NetFlow logs
NetFlow logs are forwarded by network switches, routers, and other network appliances. Logs are gathered by a collector and can be used to baseline the network and visualize the flows and data types. Figure 5.12 shows a Cisco NetFlow log:
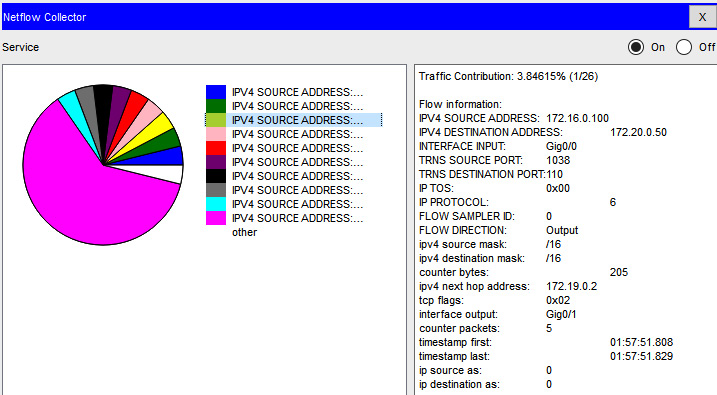
Figure 5.12 – Cisco NetFlow collector
We can also determine where the majority of network traffic originates.
Notifications
Notifications can be sent to an operator console. This could be in the form of an alert or any email message to indicate a threshold value has been hit or a particular event needs some administrator's attention.
File integrity monitoring alerts
File integrity monitoring (FIM) systems will alert on modification to key system files or any files that have been identified as important. Specialist products such as Tripwire are designed for this task. Windows also has its own system file checker in place to detect any attempts to modify key Windows operating system files. Reporting and alerting are important for real-time protection and may be required for regulatory compliance.
SIEM alerts
SIEM alerts will consolidate events from many sources of log data. We can then use smart analytics machine learning and behavioral analysis on the logged data. SIEM allows for automated alerts on unusual activity or suspicious events.
Data loss prevention alerts
Data loss prevention (DLP) systems prevent the exfiltration of sensitive data, intellectual property, and sensitive customer records, such as personally identifiable information (PII) or protected health information (PHI). Typically, this is done by using labeling techniques where users label their files with certain classifications to allow the DLP system to understand what level of classification the data is. It is important to monitor this activity, as while the DLP may stop unwanted exfiltration, we need to be aware of these events. Figure 5.13 shows an event detected by Microsoft DLP:
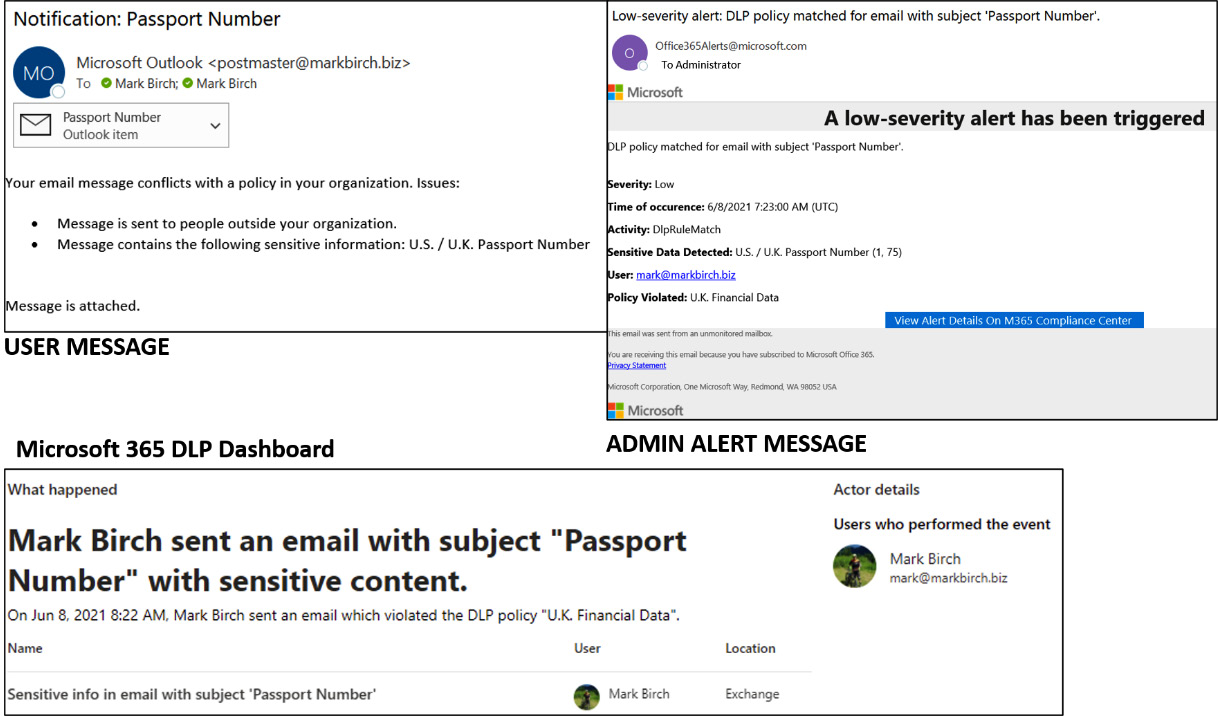
Figure 5.13 – Microsoft 365 DLP alert
DLP is all about threats for data leaving the network. We also need to analyze traffic entering the network.
Intrusion detection system and intrusion prevention system alerts
Intrusion detection systems (IDSes) and intrusion prevention systems (IPSes) offer passive or active approaches respectively. IDSes detect threats but do not take action. IPSes detect and prevent the threat from happening. We need to monitor this activity and be alerted when there is a high number of events or high-importance events. Even though the tool may be doing its job, we still need to be aware of this activity. Threatening and malicious events should be reported either through monitoring alerts or through automated emails.
Antivirus alerts
Antivirus systems are in place to prevent the proliferation of malicious code and programs. Even if the antivirus is successful, we should still log and monitor events to understand the level of this activity. Ideally, this is done from centralized reporting dashboards.
Notification severity and priorities
It is important that severe events are prioritized when considering reporting. It is important to separate the noise in the system if we can filter the logs to highlight severe events, then a quick response can be activated. Any unusual process activity that is automatically remediated should be investigated by security professionals in a timely fashion. It is important to prioritize by Common Vulnerability Scoring System (CVSS) or impact score, as it will never be possible to fix everything.
Once we have recognized unwanted activity within the enterprise, we need to put controls in place to stop or prevent unwanted activities.
Responses
When we have many security tools to guard our networks, it is important that we use automation to identify events and where possible to provide an automated response. This frees up the security operation center (SOC) staff to be able to take on board other useful security tasks. Security Orchestration Automation and Response (SOAR) is a modern approach to respond to real-time threats and alerts. Playbooks can be used to create or provide an automated response. A playbook could be a simple ruleset or a complex set of actions.
Firewall rules
Firewall rules are important to have in place, as they protect your perimeter network services placed in your Demilitarized Zone (DMZ). Firewall rules will also protect your internal resources when deployed as host-based firewalls. Firewall rules may be modified based upon a changing threat landscape and new adversaries. Bad actor IP address ranges may need to be updated on your firewalls.
Intrusion prevention system and intrusion detection system rules
IPSes and IDSes are a very important layer of protection from threats launched from outside your network (see Chapter 1, Designing a Secure Network Architecture, for more details). As a response to changing threat landscapes and new threats, these rules need to be constantly updated.
Access control list rules
An access control list (ACL) is quite a generic term. ACLs can comprise permissions on the security tab on a file or a folder. Firewall rules are also often referred to as ACLs. Other examples could be rules created for network devices, for example, a Layer 2 device such as a wireless access point or a network switch could restrict access based on your MAC address. In response to threats to Layer 2 devices, we can create a whitelist of authorized devices. Figure 5.14 shows an example of MAC filtering:
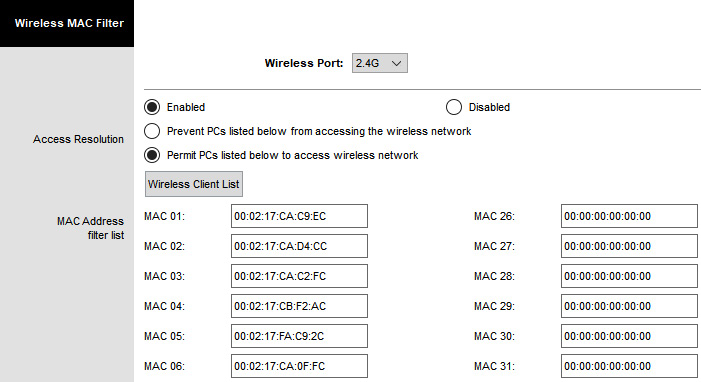
Figure 5.14 – MAC address ACL
Other rules could be based on a known signature or checksum.
Signature rules
Signature rules are normally configured based on what is known, such as a definition file that can be updated as new threats are constantly being detected and are evolving. It is important that signatures are kept up to date and an antivirus engine is very dependent on signatures and updates.
A signature could be a hash match for a known malicious file. For example, the European Institute for Computer Antivirus Research (EICAR) test file was developed to allow security personnel to check if antivirus software is functional. It uses a well-known string of characters shown here:
Figure 5.15 – EICAR test file
The signature for this string would be as follows:
SHA1 3395856ce81f2b7382dee72602f798b642f14140
Important Note
If you try to create the EICAR string and save it as a file, your anti-malware will likely quarantine the file.
Behavior rules
Behavior rules have critical importance when we store so much important data within a modern enterprise. We need systems that detect anomalies based on behavioural analysis. The system would use AI and ML to build rulesets for normal activity. But in the event of an anomaly, for example, a user beginning to transfer a large amount of data to a cloud-based data repository, or a user beginning to delete an unusual number of files within a certain amount of time, the system would generate alerts and notify an administrator. This is typically done by modeling normal user behavior and then comparing the abnormal bahavior against the normal.
The following is an example of a report from Netwrix Auditor. More information can be found at https://tinyurl.com/uebarules. Figure 5.16 shows a user behavior report:
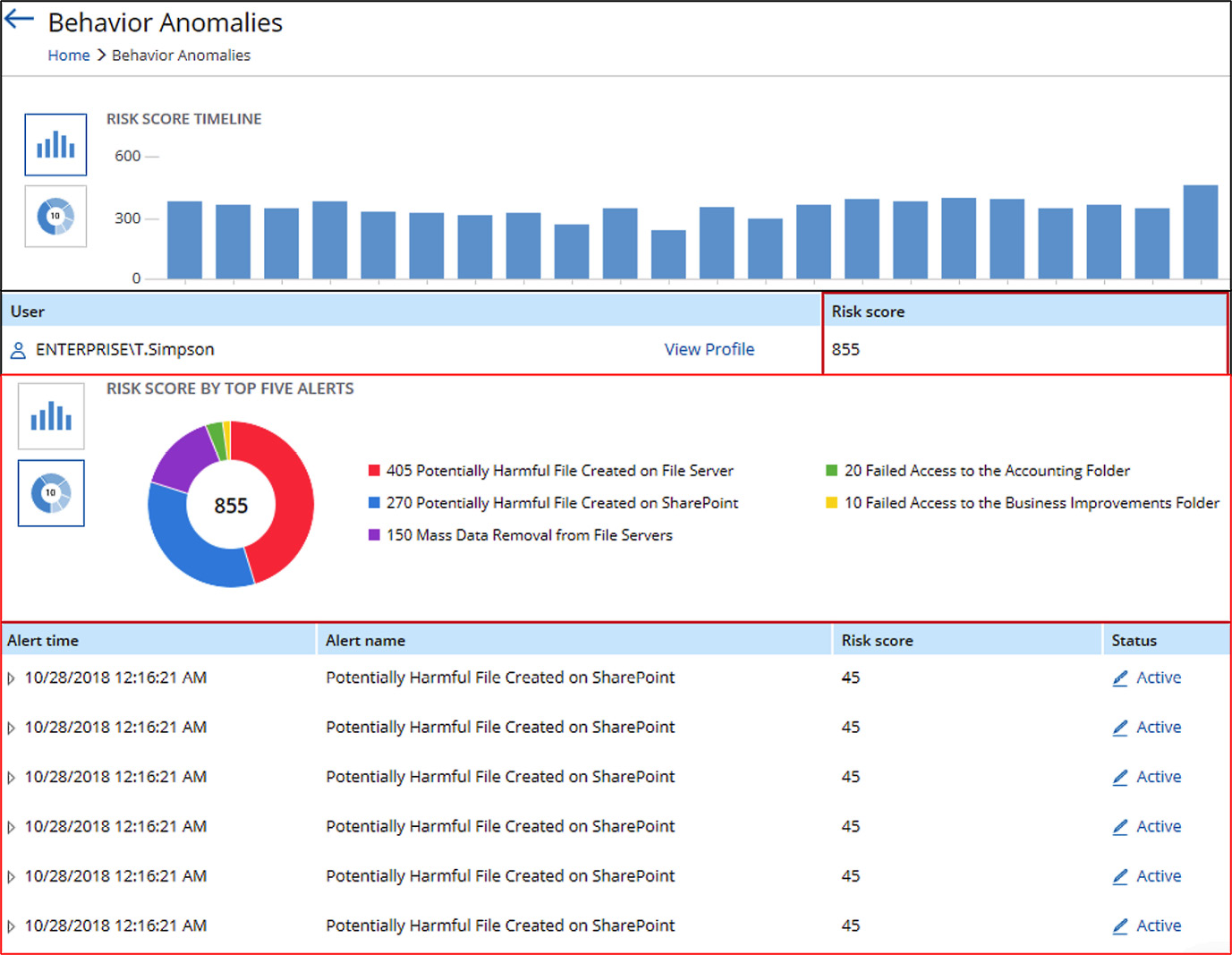
Figure 5.16 – User behavior analytics reporting
We need to put these controls in place to be better prepared for anomalous user activity.
Data loss prevention rules
DLP rules must be constantly updated. Regulatory compliance requirements may change, requiring stricter controls. The search strings that are used to detect PII, PHI, intellectual property, and financial details may need changing and new rulesets will have to be added to your DLP solution. Figure 5.17 shows a sample DLP ruleset:
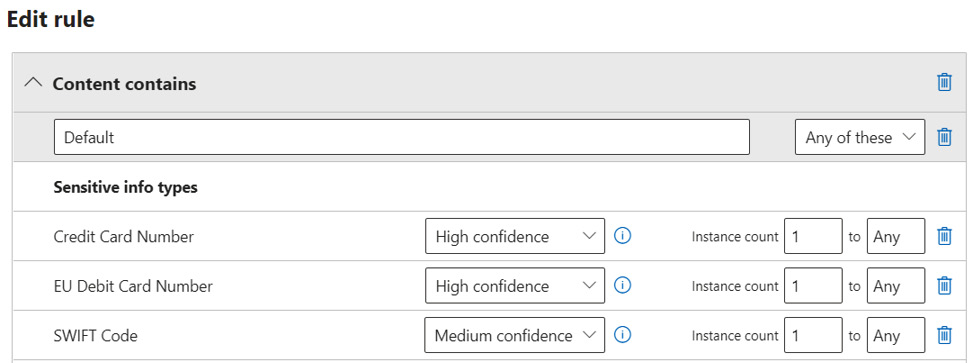
Figure 5.17 – Microsoft 365 DLP rules
Many rules that are implemented are searching for words or particular character sets.
Scripts/regular expressions
Automation could include scripting. Scripts could be created to search for keywords using regular expressions. This may provide protection by scanning captured log data or searching incoming requests to your web server. DLP is a good example of searching outgoing network traffic. We can formulate rules based on these search patterns.
It is vitally important that an organization has identified potential IOCs and has put mitigation in place to respond effectively to these attacks.
Summary
In this chapter, we have looked at the varied tools and techniques that would be used within an enterprise SOC. A security professional will need to identify different types of threats and be able to select the correct approach and framework. We have covered the main industry approaches. We have examined how an organization can identify IOCs and how to respond to a variety of threats.
In this chapter, you have gained the following skills:
- An understanding of the different sources for threat intelligence
- An understanding of the main threat actor types
- An understanding of threat actor properties
- An understanding of intelligence collection methods
- An understanding of frameworks, including MITRE, the Diamond model, and the cyber kill chain model.
- An understanding of how an enterprise detects indicators of compromise.
- How to respond to threats.
This knowledge gained will be very useful as we look into vulnerability management and pen testing in the next chapter.
Questions
Here are a few questions to test your understanding of the chapter:
- Which of the following intelligence types focuses on the threat actor and the reason for the attack?
- Tactical
- Strategic
- Targeted
- Operational
- What is used as a common vector to launch a broad range of attacks?
- Tactical
- Strategic
- Commodity malware
- Targeted attacks
- What type of attack would use spear-phishing against engineers in the Ukraine electricity supply industry with the goal of gaining user credentials?
- Deep web
- Proprietary
- Commodity malware
- Targeted attacks
- Which of the following intelligence types focuses on the technical and automated discovery of everyday threats, threat actors, and the reason for the attack?
- Tactical
- Strategic
- Commodity malware
- Targeted attacks
- Which of the following intelligence types uses forensics and historical logs to identity threats?
- Tactical
- Strategic
- Commodity malware
- Operational threat intelligence
- What framework could a forensics team use to document a specific adversary, victim, capabilities, and infrastructure?
- Threat emulation
- Threat hunting
- Diamond model
- STIX
- What is the most likely threat actor if your router firmware has been tampered with over a period of two years, without being detected?
- Advanced persistent threat
- Competitor
- Hacktivist
- Script kiddie
- What is the most likely threat actor if your electrical power delivery capabilities are attacked?
- Nation-state
- Insider threat
- Hacktivist
- Script kiddie
- What threat actor will most likely steal your intellectual property?
- Advanced persistent threat
- Competitor
- Hacktivist
- Script kiddie
- What is the threat when vulnerabilities are present on your network due to misconfiguration by poorly trained technicians?
- Advanced persistent threat
- Insider threat
- Script kiddie
- Organized crime
- What is the threat when vulnerabilities are present due to the use of third-party libraries in our code base?
- Advanced persistent threat
- Supply Chain
- Insider threat
- Organized crime
- What is the likely threat actor when thousands of systems are targeted with crypto malware followed up with a demand for $5,000 in bitcoin?
- Advanced persistent threat
- Supply chain
- Insider threat
- Organized crime
- What is the public network that hosts unindexed and unsearchable content that may be used for unlawful activities?
- World Wide Web
- Intranet
- Deep web
- Proprietary networks
- What type of intelligence gathering would involve DNS record harvesting?
- Intelligence feeds
- Deep web
- Open source intelligence (OSINT)
- Human intelligence (HUMINT)
- What type of intelligence gathering would involve physical reconnaissance?
- Intelligence feeds
- Deep Web
- Open source intelligence (OSINT)
- Human intelligence (HUMINT)
- What framework would be the best choice to build up a picture of threat actors and their tactics and techniques for a water treatment plant?
- MITRE ATT&CK
- ATT&CK for industrial control system (ICS)
- Diamond model of intrusion analysis
- Cyber kill chain
- What framework would be used to understand the capabilities of APT29 and how they will target your enterprise information systems?
- MITRE (ATT&CK)
- ATT&CK for industrial control system (ICS)
- Scripts/regular expressions
- SRTM
- What framework uses seven stages, starting with reconnaissance and ending in actions on objectives?
- MITRE (ATT&CK)
- ATT&CK for industrial control system (ICS)
- Diamond model of intrusion analysis
- Cyber kill chain
- What file type will allow for the analysis of network traffic captured by Wireshark or tcpdump?
- Packet capture (PCAP)
- Vulnerability logs
- Operating system logs
- Portable Data Format (PDF)
- What can be used to centrally correlate events from multiple sources and raise alerts?
- FIM alerts
- SIEM alerts
- DLP alerts
- IDS/IPS alerts
- What type of logging can be used for accountability?
- Vulnerability logs
- Operating system logs
- Access logs
- NetFlow logs
- What type of logging can identify the source of most noise on a network?
- Vulnerability logs
- Operating system logs
- Access logs
- NetFlow logs
- How will I know if my critical files have been tampered with?
- FIM alerts
- SIEM alerts
- DLP alerts
- IDS/IPS alerts
- George has tried to email his company credit card details to his Gmail account. The security team has contacted him and reminded him this is not acceptable use. How were they informed?
- FIM alerts
- SIEM alerts
- DLP alerts
- IDS/IPS alerts
- An attacker has had their session reset after they successfully logged on to the Private Branch Exchange (PBX) after three unsuccessful attempts using SSH. What is the reason for this?
- FIM alerts
- Firewall alerts
- DLP rules
- IPS rules
- The Acme corporation needs to block the exfiltration of United States medical-related data due to a new regulatory requirement. What is most likely going to get updated?
- ACL rules
- Signature rules
- Behavior rules
- DLP rules
- Bill the network technician has been tasked with updating security based upon a threat exchange update. Five known bad actor IP addresses must be blocked. What should be updated?
- Firewall rules
- Signature rules
- Behavior rules
- DLP rules
- What is used to search for character strings in my DLP solution?
- Signature rules
- Behavior rules
- Firewall rules
- Regular expressions
- What type of rule will alert administrators that Colin is deleting significant amounts of sensitive company data?
- Signature rules
- Behavior rules
- Firewall rules
- Regular expressions
- What will alert the SOC team to IOCs detected in logs of multiple network appliances?
- SIEM alerts
- Behavior alerts
- DLP alerts
- Syslogs
- What type of rule will alert administrators about a known malware variant that has the following checksum:
sha1 checksum 29386154B7F99B05A23DC9D04421AC8B0534CBE1?
- ACL rules
- Signature rules
- Behavior rules
- DLP rules
- Charles notices several endpoints have been infected by a recently discovered malware variant. What has allowed Charles to receive this information?
- SIEM alerts
- Antivirus alerts
- DLP alerts
- Syslogs
Answers
- A
- C
- D
- A
- D
- C
- A
- A
- B
- B
- B
- D
- C
- C
- D
- B
- A
- D
- A
- B
- C
- D
- A
- C
- D
- D
- A
- D
- B
- A
- B
- B
