Chapter 16: Mock Exam 1
Welcome to the study guide assessment test! These test questions are designed to resemble real-world CASP 004 exam questions. To make this test as realistic as possible, you should attempt to answer these questions closed book and allocate the correct amount of time. You can use some paper or a scratchpad to jot down notes, although this will be different in a real test environment. If you wish to look at the PearsonVue candidate testing rules, check out the following URL: https://home.pearsonvue.com/comptia/onvue.
- End of Study Assessment Test
- Number of Questions: 50
- Passing Score: 83% (Estimated)
Questions
- Developers are building sensitive references and account details into the application code. Security engineers need to ensure that the organization can secure the continuous integration/continuous delivery (CI/CD) pipeline. What would be the best choice?
- Perform dynamic application security testing.
- Use a centralized trusted secrets manager service.
- Use interactive application security testing.
- Ensure the developers are using version control.
- What type of assessment should be performed by an organization that stores, transmits, or processes data that contains private information?
- Business Impact Assessment
- Privacy Impact Assessment
- Risk assessment
- Safety assessment
- The ACME corporation has recently run an annual risk assessment as part of its regulatory compliance. The risk management team has identified a high-level risk that could lead to fraudulent activities. The team has recommended that certain privileged tasks must be performed by more than one person for the task to be validated. What is this an example of?
- Job rotation
- Least privilege
- Separation of duties
- Multi-factor authentication
- Security professionals are analyzing logs that have been collected from MDM software. The following log entries are available:
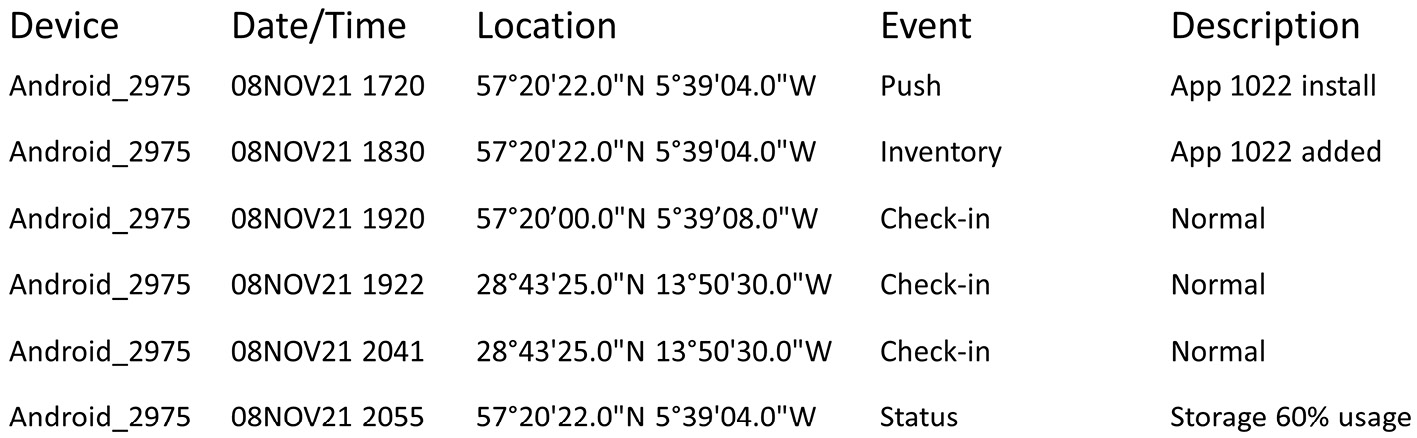
Figure 16.1 – MDM audit log
What is the security concern and what response would best mitigate the risks of the mobile device?
- An application was installed maliciously; change the MDM configuration to remove application ID 1022.
- Sensitive data exposure; recover the device for analysis and clean up the local storage.
- Impossible time travel; disable the device's account and carry out further investigation.
- Anomalous status reporting; initiate a remote wipe of the device.
- An e-commerce site has recently upgraded its web application servers to use TLS 1.3, though some customers are calling the service desk as they can no longer access the services. After analyzing the logs that had been generated on the client's devices, the following was observed:
ERROR_SSL_VERSION_OR_CIPHER_MISMATCH
What is the most likely cause of the reported error?
- Clients are configured to use ECDHE.
- Clients are configured to use RC4.
- Clients are configured to use PFS.
- Clients are configured to use AES-256 GCM.
- The security professionals are reviewing all the servers in the company and discover that a server is missing crucial patches that would mitigate a recent exploit that could gain root access. Which of the following describes the teams' discovery?
- A vulnerability
- A threat
- A breach
- A risk
- ACME bank has a compliance requirement. They require a third-party penetration test of the customer-facing banking application to be conducted annually. What type of penetration testing would ensure the lowest resource usage?
- Black-box testing
- Gray-box testing
- Red-team exercises
- White-box testing
- Blue-team exercises
- Recently, the ACME corporation has merged with a similar-sized organization. The SOC staff now have an increased workload and are failing to respond to all alerts. What is the likely cause of this behavior?
- False positive
- Alert fatigue
- False negative
- True positive
- A small regional bank, with no dedicated security team, must deploy security at the edge of the network. They will need a solution that will offer protection from multiple threats that may target the bank's network. What would be the best solution for the bank?
- Router
- WAF
- UTM
- DLP
- During baseline security training for new developers, attention must be focused on the use of third-party libraries. What is the most important aspect for a commercial development team that's considering the use of third-party libraries? Choose two.
- Third-party libraries may have vulnerabilities.
- Third-party libraries may be incompatible.
- Third-party libraries may not support DNSSEC.
- Third-party libraries may have licensing restrictions.
- A CISO wants to change the culture of the organization to strengthen the company's security posture. The initiative will bring the development and operations teams together when code is released to the production environment. What is the best description of this initiative?
- DevOps
- A team-building exercise
- A tabletop exercise
- SecDevOps
- A development team is working with a customer to develop a mobile application. The customer has already defined all the requirements upfront and wants the application to be developed using very strict timelines. It is not anticipated that any changes will be made to the initial definition. What software development approach would be the most suitable for this engagement?
- Agile
- Waterfall
- Spiral
- Build and Fix
- A CISO for a large multinational bank would like to address security concerns regarding the use and auditing of local administrator credentials on end devices. Currently, users are given local administrator privileges when access is required. This current practice has resulted in undocumented changes, a lack of accountability, and account lockouts. What could be implemented to address these issues?
- Use Privileged Access Management (PAM) to maintain user accounts in the local admin group.
- Deploy EDR to remove users from local admins group and enable audit logs.
- Use Privileged Access Management (PAM) to remove user accounts from the local admin group and prompt the user for explicit approval when elevation is required.
- Deploy EDR to remove users from the local admins group and enable UEBA.
- The ACME corporation has been suffering from increasing numbers of service outages on the endpoints due to ever-increasing instances of new malware. The Chief Financial Officer's laptop was impacted while working remotely from a hotel. The objective is to prevent further instances of endpoint disruption. Currently, the company has deployed a web proxy at the edge of the network. What should the company deploy to mitigate these threats?
- Replace the current antivirus with an EDR solution.
- Remove the web proxy and install a UTM appliance.
- Implement application blacklisting on the endpoints.
- Add a firewall module to the current antivirus solution.
- A company has been testing its Disaster Recovery Plan (DRP) while team members have been assessing challenges that had been encountered while testing in parallel. Computing resources ran out at 65% of the restoration process for critical services. What documentation should be modified to address this issue?
- Recovery point objective
- Business Impact Assessment
- Mission-essential functions
- Recovery service level
- A security professional is performing a system penetration test. They successfully gain access to a shell on a Linux host as a standard user and want to elevate their privilege levels. What would be the most effective way to perform privilege escalation?
- Spawn a shell using sudo and use a text editor to update the sudoer's file.
- Perform ASIC password cracking on the host.
- Access the /etc/passwd file to extract the usernames.
- Use the UNION operator to extract the database schema.
- A security analyst is concerned that a malicious piece of code was downloaded on a Linux system. After running various diagnostics tools, the analyst determines that the suspect code is performing a lot of input/output (I/O) on the disk drive. The following screenshot shows the output from one of the diagnostics tools:

Figure 16.2 – Diagnostic output
Based on this output, which ID should the analyst focus their attention on?
- ID 99
- ID 40
- ID 22
- ID 12
- A CISO needs to ensure there is an effective incident response plan. As part of the plan, a CSIRT team needs to be identified, including leadership with a clear reporting and escalation process. At what part of the incident response process should this be done?
- Preparation
- Detection
- Analysis
- Containment
- The ACME corporation's CSIRT team responded to an incident where several routers failed at the same time. The cause of the failure is unknown, and the routers have been reconfigured and restored to operational condition. The integrity of the router's configuration has also been verified. Which of the following should the team perform to understand the failure and prevent it in the future?
- Root cause analysis
- Continuity of operations plan
- After-action report
- Lessons learned
- Jeff, a developer with the ACME corporation, is concerned about the impact of new malware on an ARM CPU. He knows that the malware can insert itself in another process memory location. Which of the following technologies can the developer enable on the ARM architecture to prevent this type of malware?
- Execute-never (XN)
- EDR software
- Total memory encryption
- Virtual memory encryption
- Security professionals have detected anomalous activity on the edge network. To investigate the activity further, they intend to examine the contents of the pcap file. They are looking for evidence of data exfiltration from a suspect host computer. To minimize disruption, they need to identify a command-line tool that will provide this functionality. What should they use?
- netcat
- tcpdump
- Aircrack-ng
- Wireshark
- Ann, a security analyst, is investigating anomalous activity within syslog files. She is looking for evidence of unusual activity based on reports from User Entity Behavior Analytics (UEBA). Several events may be indicators of compromise. Which of the following requires further investigation?
- Netstat -bn
- vmstat -a 5
- nc -w 180 -p 12345 -l < shadow.txt
- Exiftool companylogo.jpg
- UEBA has generated alerts relating to significant amounts of PNG image uploads to a social networking site. The account that has generated the reports is a recent hire in the Research and Development division. A rival manufacturer is selling products that appear to be based on the company's sensitive designs.
The payloads are now being analyzed by forensics investigators. What tool will allow them to search for evidence in the PNG files?
- Steganalysis tool
- Cryptanalysis tool
- Binary analysis tool
- Memory analysis tool
- Marketing executives are attending an international trade exhibition and must connect to their company's email using their mobile devices during the event. The CISO is concerned that this may present a risk. What would best mitigate this risk?
- Near-field communication (NFC)
- Split-tunnel VPN
- Geofencing
- Always-on VPN settings
- A company employee has followed a QC link and installed a mobile application that's used to book and schedule activities at a vacation resort. The application is not available on Google Play Store. Company policy states that applications can only be downloaded from the official vendor store or company portal. What best describes what has allowed this app to be installed?
- Supply chain issues
- Side loading
- Containerization
- Unauthorized application stores
- A company has deployed a hardened Linux image to mobile devices. The restrictions are as follows:
- All unnecessary services must be removed.
- Only company-deployed apps can be run.
- The runtime code is protected against memory exploits.
The CISO is concerned that an attacker may be able to launch attacks using common utilities and command-line tools. What could be deployed to mitigate the CISO's concerns?
- Whitelisting
- Shell restrictions
- ASLR
- Memory encryption
- A regional Internet Service Provider (ISP) is experiencing outages and poor service levels over some of its copper-based infrastructure. These faults are due to the reliance on legacy hardware and software. Several times during the month, a contracted company must follow a checklist of 12 different commands that must be run in serial to restore performance to an acceptable level. The ISP would like to make this an automated process. Which of the following techniques would be best suited for this requirement?
- Deploy SOAR utilities and runbooks.
- Replace the associated hardware.
- Provide the contractors with direct access to syslog data.
- Switch the copper-based infrastructure to fiber.
- A security analyst is investigating a possible buffer overflow attack. The attack seems to be attempting to load a program file. Analysis of the live memory reveals that the following string is being run:
code.linux_access.prg
Which of the following technologies would best mitigate the manipulation of memory segments?
- NX bit
- ASLR
- DEP
- HSM
- A CISO at a regional power supply company is performing a risk assessment. The CISO must consider what the most important security objective is when applying cryptography to control messages. The control messages are critical and enable the operational technology to ensure the generators are outputting the correct electrical power levels. What is the most important consideration here?
- Importing the availability of messages
- Ensuring the non-repudiation of messages
- Enforcing protocol conformance for messages
- Ensuring the integrity of messages
- Alan, a CISO for an online retailer, is performing a quantitative risk assessment. The assessment is based on the public-facing web application server. Current figures show that the application server experiences 80 attempted breaches per day. In the past 4 years, the company's data has been breached two times. Which of the following represents the ARO for successful breaches?
- 50
- 0.8
- 0.5
- 29,200
- Security engineers are assessing the capabilities and vulnerabilities of a widely used mobile operating system. The company intends to deploy a secure image to mobile phones and tablets. The mobile devices mustn't be vulnerable to the risk of privilege elevation and the misuse of applications. What would be the most beneficial to the company for addressing these concerns?
- Security-Enhanced Linux (SELinux)
- Trusted Platform Module (TPM)
- Security-Enhanced Android (SEAndroid)
- Attestation services
- Gerry, a CISO for a national healthcare provider, is assessing proposals for network storage solutions. The proposal is for NAS to be deployed to all regional hospitals and clinics. As the data that will be stored will be sensitive and subject to strict regulatory compliance, security is the most important consideration. The proposal is for appliances running a Linux kernel and providing secure access to authenticated users through NFS. One major concern is ensuring that the root account cannot be used to gain access to user data on the Linux NFS appliances. What would best prevent this issue from occurring?
- Ensure passwords are stored in a shadow file.
- Run SELinux in enforced mode.
- Disable central processing unit (CPU) virtualization support.
- Enforce secure encrypted enclaves/memory encryption.
- ACME chemicals is conducting a risk assessment for its legacy operational technology. One of their major concerns is the widespread use of a standard message transport protocol that's used in industrial environments. After performing a vulnerability assessment, several CVEs are discovered with high CVSS values. The findings describe the following vulnerabilities:
- CVE-2018-11452: Denial-of-service of the affected device
- CVE-2018-7842: Elevation of privilege by conducting a brute-force attack on the parameters that were sent to the controller
- CVE-2017-6034: An attacker can replay the run, stop, upload, and download commands
Additional CVEs report multiple vulnerabilities, including no security against message integrity being tampered with and being vulnerable to MITM attacks. What is the network/protocol that has most likely been assessed?
- Ethernet
- Modbus
- Distributed Network Protocol 3 (DNP3)
- Zigbee
- Mechanical engineers are using a simple programming language based on relay-based logic, as shown in the following diagram:
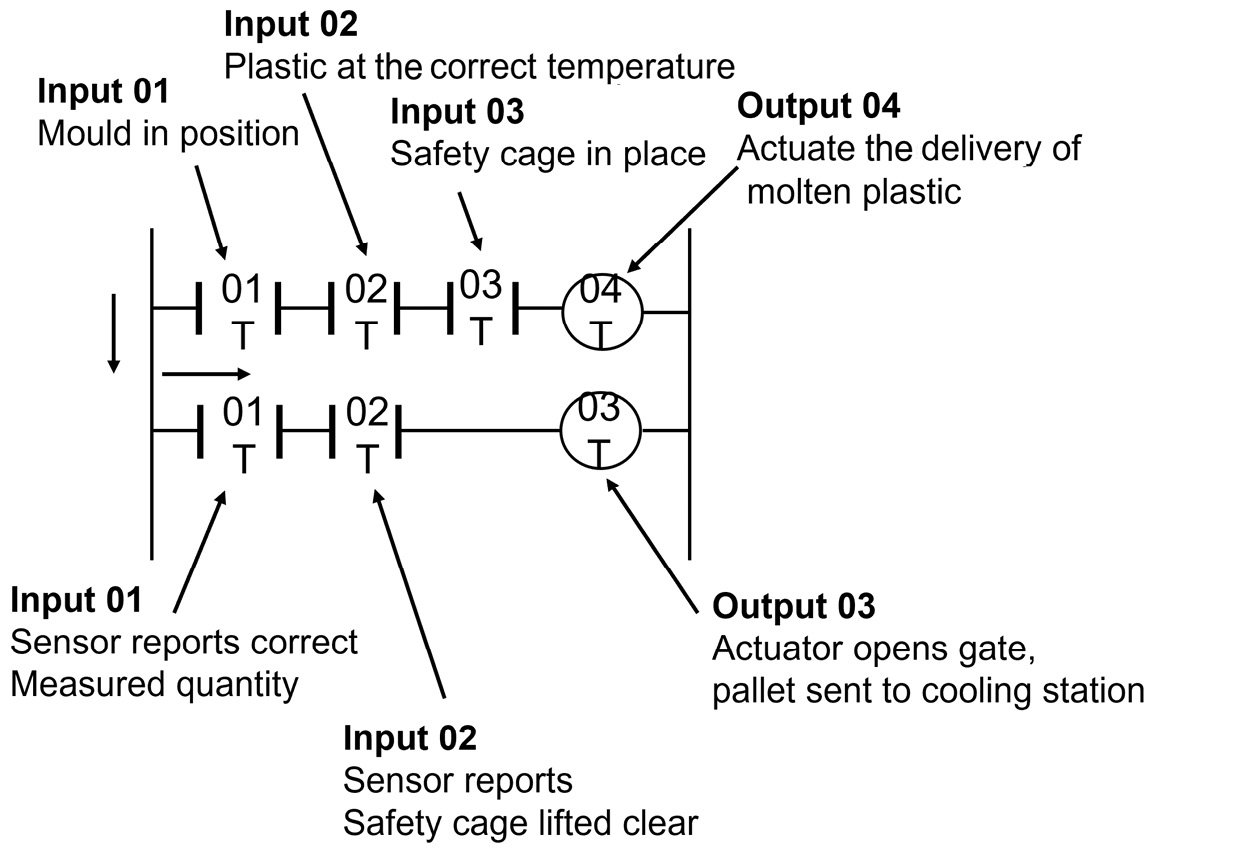
Figure 16.3 – Relay-based logic
What language/protocol are the engineers are using?
- Historian
- Ladder logic
- Zigbee
- Modbus
- A small water treatment plant is being controlled by a SCADA system. There are four main treatment tanks, each being serviced by an input pump and an output pump. The design of the plant offers redundancy as the plant can operate without all the tanks being available. The plant is comprised of a standard SCADA mix of operational technology, including PLCs and a supervisory computer.
What system failure will cause the biggest outage?
- Loss of a treatment tank
- Loss of supervisory computer
- Failure of an input pump
- Failure of a PLC
- A development team is implementing a customer-facing API that uses a database backend. Before the deployment, the team is concerned about attacks, such as XSS, XSRF, and injection attacks. To mitigate these types of attacks, the team needs to identify security controls that could be implemented. Which of the following sources could the team consult to address these security concerns?
- SDLC
- OVAL
- IEEE
- OWASP
- The customers of a large online retailer are reporting high levels of latency when they are searching for products on the e-commerce site. The site consists of an array of load-balanced APIs that do not require authentication. The application servers that host the APIs are showing heavy CPU utilization. WAFs that have been placed in front of the APIs are not generating any alerts.
Which of the following should a security engineer recommend to best remedy these performance issues promptly?
- Implement rate limiting on the API.
- Implement geo-blocking on the WAF.
- Implement OAuth 2.0 on the API.
- Implement input validation on the API.
- ACME bank engineers are configuring security for a new data center. They are looking to implement SSL/TLS for customer-facing application servers. Customers will connect to the bank API through a deployed mobile application. They must now choose a symmetric algorithm that offers the greatest speed and security. Which should they choose?
- ChaCha256 + poly1305
- 3DES + CBC
- AES256 + CBC
- Salsa256 + CBC
- Hackers can gain access to encrypted data transmissions. After performing vulnerability assessments on the application servers, several cipher suites are available for backward compatibility. Which of the following would represent the greatest risk?
- TLS_RSA_WITH_AES_128_CBC_SHA
- TLS_RSA_WITH_RC4_40_MD5
- TLS_DHE_RSA_WITH_AES_256_CBC_SHA
- TLS_RSA_WITH_3DES_EDE_CBC_SHA
- A company is deploying an online streaming service for customers. The content needs to be protected; only the paid subscribers should be able to view the streams. The company wants to choose the best solution for low latency and security. What would be the best choice?
- 3DES
- AES
- ChaCha
- RC4
- A government agency is configuring a VPN connection between Fort Meade and a field office in New York. Of primary importance is having a highly secure key exchange protocol due to the threats posed by nation state threat actors. Which encryption protocol would be a good choice?
- Advanced Encryption Standard (AES)
- ECDHE p521
- ChaCha-256
- SHA-512
- Software developers are deploying a new customer-facing CRM tool. The deployment will require the customers to download an application on their system. Customers must be able to verify that the application is trustworthy. What type of certificate will the software developers request to fulfill this requirement?
- Client authentication
- Server authentication
- Digital signatures
- Code signing
- A large insurance provider has grown in size and now supports customers in many different countries. Due to this increased footprint, they are looking to minimize administration by allocating a single certificate to multiple sites. The sites will be country-specific, with different domain names. What would be the best choice for delivering this requirement?
- Wildcard certificate
- Extended validation
- General-purpose
- Subject Alternate Name (SAN)
- The CISO is delivering a security briefing to senior members of staff. One of the topics of conversation concerns the current e-commerce site. During a Q&A session, the CISO is asked questions about PKI and certificates. A rudimentary question is asked – what key is stored on a certificate? What should the CISO answer?
- Public key
- Private key
- Public and private keys
- Signing key
- A large online bank would like to ensure that customers can quickly validate that the bank's certificates are not part of a CRL. What would best meet this requirement?
- Extended validation
- Certificate pinning
- OCSP
- CRL
- Website engineers are configuring security extensions to be deployed to all customer-facing web application servers. What HTTP extension will ensure that all the connections to the application servers will also be encrypted using the assigned X.509 certificate?
- HTTP X-FRAME headers
- HTTP Strict Transport Security (HSTS)
- HTTPS SSL 3.0 CBC
- Extended validation
- Nation state-sponsored actors have stolen the smartphone of a government official. They have attempted to guess the PIN code several times, eventually locking the device. They are attempting to gain access to the data using forensic tools and techniques but the data cannot be accessed. What has likely prevented a data breach from occurring?
- Hardware write blocker
- USB data blocker
- Crypto shredding
- Improper key handling
- A small startup energy company has built up a database of clients. It is estimated that this database is worth $100,000. During a data breach, a cyber-criminal (working for a competitor) steals 10% of the records. The company fails to put adequate controls in place and a second breach occurs within 12 months.
What is the Annual Loss Expectancy (ALE)?
- $200,000
- $1,000
- $20,000
- $10,000
- A defense contractor currently loses an estimated $2,000,000 each year due to intellectual property theft. The company has a solid reputation for R&D and manufacturing but has no dedicated security staff. A Managed Security Service Provider (MSSP) guarantees that they will provide 90% protection for the data over a 5-year contract at an annual cost of $250,000 per annum. What is the ROI in dollars?
- $10,000,000
- $9,000,000
- $750,000
- $7,750,000
- An automobile manufacturer suffers a power outage at one of its foundries. The facility supplies critical components for the company. The COOP designated the foundry as a mission-essential service, and it was agreed that the foundry must be operational within 24 hours. The energy supplier has struggled to repair severe storm-damaged cables. As a result, the facility is without power for 72 hours. What is the metric that describes this 72-hour outage?
- Mean time to recovery (MTTR)
- Mean time between failure (MTBF)
- Recovery Time Objective (RTO)
- Annualized rate of occurrence (ARO)
Assessment test answers
- B. Use a centralized trusted secrets manager service. Secrets can include user or auto-generated passwords, APIs, and other application keys/credentials, SSH keys, databases, and other system-to-system passwords. You should use private certificates for secure communication and private encryption keys.
External reference: https://www.beyondtrust.com/resources/glossary/secrets-management.
See Chapter 4, Deploying Enterprise Authentication and Authorization Controls, for more details on secure account management concepts.
- B. Privacy Impact Assessment. A PIA should be undertaken by any organization that stores, transmits, or processes data that contains private information. Data types will vary but can include documents, database records, and media such as CCTV footage and voice recordings. See Chapter 15, Business Continuity and Disaster Recovery Concepts.
- C. Separation of duties. When an employee has privileges that enable them to make high-level decisions without needing the consent of another employee, then we are missing essential checks and balances. Consider a Chief Financial Officer (CFO), who approves new suppliers, approves the suppliers' invoices for services, and signs their paychecks. This example would allow for fraudulent activities and would be mitigated by establishing accounts receivable and accounts payable business functions. See Chapter 13, Applying Appropriate Risk Strategies.
- C. Impossible time travel. Disable the device's account and carry out further investigations.
See Chapter 9, Enterprise Mobility and Endpoint Security Controls (covers location services and user and entity behavior analytics (UEBA)).
- B. Clients are configured to use RC4. RC4 is considered weak encryption and would not be supported while using TLS 1.3. See Chapter 11, Implementing Cryptographic Protocols and Algorithms.
- A. A vulnerability. When a system is missing patches, it is vulnerable to attacks. During a risk assessment, we need to assess vulnerabilities and potential threats that could target the vulnerability. See Chapter 6, Vulnerability Assessment and Penetration Testing Methods and Tools.
- A. Black-box testing will take the least amount of time but may not discover all vulnerabilities. See Chapter 6, Vulnerability Assessment and Penetration Testing Methods and Tools.
- B. Alert fatigue. This is when the staff are overwhelmed with too many alerts. See Chapter 1, Designing a Secure Network Architecture.
- C. Unified Threat Management (UTM). This can combine multiple security functions into a single appliance. See Chapter 1, Designing a Secure Network Architecture.
- A and D. Third-party libraries may have vulnerabilities and Third-party libraries may have licensing restrictions. See Chapter 2, Integrating Software Applications into the Enterprise.
- D. SecDevOps. The development team and operations teams work together to ensure code is delivered error-free. See Chapter 2, Integrating Software Applications into the Enterprise.
- B. The waterfall methodology means that we must have defined all the requirements at the start of the process and that no changes will be made during the development cycle. See Chapter 2, Integrating Software Applications into the Enterprise.
- C. Use Privileged Access Management (PAM) to remove user accounts from the local admin group and prompt the user for explicit approval when elevation is required. This solution allows accounts to elevate their privileges and that these actions will be audited. See Chapter 4, Deploying Enterprise Authentication and Authorization Controls.
- A. Replace the current antivirus with an EDR solution. The end devices must be protected when they are not on the company network. The other solutions will not adequately fulfill the requirements. See Chapter 9, Enterprise Mobility and Endpoint Security Controls.
- D. Recovery Service Level. See Chapter 15, Business Continuity and Disaster Recovery Concepts.
- C. Access the /etc/passwd file to extract the usernames. As the account is a standard user, they will not have the right to edit configuration files (sudoers), so the best option is to access the passwd file (you do not need any privileges to do this). See Chapter 7, Risk Mitigation Controls.
- C. ID22 shows a high amount of disk I/O using the vmstat command. See Chapter 8, Implementing Incident Response and Forensics Procedures.
- A. Preparation. For details on creating an incident response plan, see Chapter 8, Implementing Incident Response and Forensics Procedures.
- A. Root cause analysis. This would be performed as a result of lessons learned/AAR. See Chapter 8, Implementing Incident Response and Forensics Procedures.
- A. Execute-never (XN). CPU chips support memory protection within the hardware. See Chapter 9, Enterprise Mobility and Endpoint Security Controls.
- B. tcpdump. This is a command-line protocol analyzer that's capable of capturing traffic and can be used to analyze previous captures. pcap is a standard packet capture file format. See Chapter 8, Implementing Incident Response and Forensics Procedures.
- C. nc -w 180 -p 12345 -l < shadow.txt. Netcat can be used to run remote commands on a target system, allowing for files to be transferred. See Chapter 8, Implementing Incident Response and Forensics Procedures.
- A. Steganalysis tool. This tool would search for data hidden within the graphics file. See Chapter 8, Implementing Incident Response and Forensics Procedures.
- D. Always-on VPN settings. They will always have an encrypted connection that's routed through the company network. See Chapter 9, Enterprise Mobility and Endpoint Security Controls.
- D. Unauthorized application stores. See Chapter 9, Enterprise Mobility and Endpoint Security Controls.
- B. Shell restrictions. The current settings mitigate the main threats but do not prevent built-in commands from being run. See Chapter 9, Enterprise Mobility and Endpoint Security Controls.
- A. Deploy SOAR utilities and runbooks. This will automate this repetitive process and take some of the workload off the technicians. See Chapter 8, Implementing Incident Response and Forensics Procedures.
- B. ASLR. This mitigation is built into the operating system and is considered a better option (NX+DEP is hardware-based and less effective).
- D. Ensuring the integrity of messages. Control messages will not normally be confidential but must be tamper-proof. This is the best solution. See Chapter 10, Security Considerations Impacting Specific Sectors and Operational Technologies.
- C. 0.5. The ARO over 4 years is 0.5 as there were only two successful breaches. See Chapter 13, Applying Appropriate Risk Strategies.
- C. Security-Enhanced Android (SEAndroid). This is SELinux for mobile devices. See Chapter 9, Enterprise Mobility and Endpoint Security Controls.
- B. Run SELinux in enforced mode. This will enforce Mandatory Access Control (MAC). See Chapter 9, Enterprise Mobility and Endpoint Security Controls.
- B. Modbus. This is a well-used control protocol that's used within industrial controlled environments. It is vulnerable to many different threats. See Chapter 10, Security Considerations Impacting Specific Sectors and Operational Technologies.
- B. Ladder logic. See Chapter 10, Security Considerations Impacting Specific Sectors and Operational Technologies.
- B. Loss of a supervisory computer. See Chapter 10, Security Considerations Impacting Specific Sectors and Operational Technologies. This can also be seen in the following diagram:

Figure 16.4 – The hierarchy of and dependencies within a SCADA system
- D. OWASP. This will be the best source of reference when securing web applications.
- A. Implement rate limiting on the API. This will allow for the number of connections that are forwarded to the web servers to be throttled.
- A. ChaCha256 + poly1305. This offers a major performance advantage over existing technologies. See Chapter 11, Implementing Cryptographic Protocols and Algorithms.
- B. TLS_RSA_WITH_RC4_40_MD5. RC4 (symmetric encryption) should not be used and will cause systems to be out of compliance. MD5 (hashing algorithm) is also weak and should not be used. See Chapter 11, Implementing Cryptographic Protocols and Algorithms.
- C. ChaCha. This is a stream cipher and will offer very good performance for streaming media. See Chapter 11, Implementing Cryptographic Protocols and Algorithms.
- B. ECDHE p521. This is currently the strongest form of key exchange. The other answers refer to symmetric encryption or hashing. See Chapter 11, Implementing Cryptographic Protocols and Algorithms.
- D. Code signing. The application code needs to be digitally signed. See Chapter 12, Implementing Appropriate PKI Solutions, Cryptographic Protocols, and Algorithms for Business Needs.
- D. Subject Alternate Name (SAN). This will allow a single certificate to be issued for multiple sites. A wildcard would not be suitable as the domain names will be different. See Chapter 12, Implementing Appropriate PKI Solutions, Cryptographic Protocols, and Algorithms for Business Needs.
- A. Public key. A digital certificate validates the public key. Private keys are not shared but can be stored in escrow if a copy needs to be made. See Chapter 12, Implementing Appropriate PKI Solutions, Cryptographic Protocols, and Algorithms for Business Needs.
- C. OCSP. This allows a quick response to be provided when a CRL check is required. See Chapter 12, Implementing Appropriate PKI Solutions, Cryptographic Protocols, and Algorithms for Business Needs.
- B. HTTP Strict Transport Security (HSTS). This will ensure that all the connections are forced to use HTTPS/TLS. See Chapter 2, Integrating Software Applications into the Enterprise.
- C. Crypto shredding. The symmetric key that was used to encrypt the data is destroyed, making data recovery ineffective. See Chapter 12, Implementing Appropriate PKI Solutions, Cryptographic Protocols, and Algorithms for Business Needs.
- C. $20,000.
Asset Value (AV) = 100,000
Exposure Factor (EF) = 10%
Single Loss Expectancy (SLE) = 10,000
Annual Rate of Occurrence (ARO) = 2
Annual Loss Expectancy (ALO) = 20,000 (SLE x ARO)
See Chapter 13, Applying Appropriate Risk Strategies.
- D. $7,750,000. ROI= (9,000,000 Reduction in risk – 750,000 cost of control). The contract is for 5 years, so the potential loss would be 10,000,000. As we mitigate 90% of the loss, we have saved 9,000,000 but must pay 5 x 250,000 = 1,250,000. See Chapter 13, Applying Appropriate Risk Strategies.
- A. Mean time to recovery (MTTR). See Chapter 13, Applying Appropriate Risk Strategies.
Hopefully, you have enjoyed testing yourself via a typical mix of CASP questions. For more exam resources, please visit https://www.casp.training.
