Chapter 1: Designing a Secure Network Architecture
Security professionals need to analyze security requirements and objectives to ensure an appropriate, secure network architecture for a new or existing network and to provide the appropriate authentication and authorization controls.
Designing a modern enterprise network has many practical and security challenges. De-perimeterization means that access to information systems may be made from devices outside of the enterprise network. The types of devices can range from a handheld smartphone used to access a customer record to an Internet of Things (IoT) device transmitting telemetry data to a critical monitoring dashboard.
Regulatory or industry compliance may require strict network segmentation between processes and business units (BUs).
It is important to consider all the threat actors when you plan your network—think Defense in Depth (DiD).
This first chapter is an essential building block for the following chapters. It is the information systems on our networks that provide the data and services for an enterprise.
In this chapter, we will cover the following topics:
- Physical and virtual network and security devices
- Application- and protocol-aware technologies
- Advanced network design
- Network management and monitoring tools
- Advanced configuration of network devices
- Security zones
Physical and virtual network and security devices
For the certification exam, it is important that you understand the strengths and weaknesses of all the proposed network devices/appliances, the correct placement of network devices for maximum effect, and the required security configuration.
OSI model
No introduction to networking would be complete without a brief introduction to the Open Systems Interconnection (OSI) 7-layer model. As we move through the chapters, you will occasionally see references to layers. This has become a standard reference model and it allows for different vendors to implement services, protocols, and hardware using this reference model. Throughout the book, we will discuss applications, services, protocols, and appliances that sit at different layers within the model. Although the CompTIA Advanced Security Professional 004 (CASP 004) exam will not be testing your knowledge specifically (OSI is not a listed objective), it can be useful as a reference aid when we discuss networking subjects. The model is not actually defining a complete working network model—it is a conceptual model. For example, to fully understand the details of the Simple Mail Transport Protocol (SMTP), you would need to gain access to Internet Engineering Task Force (IETF) Request for Comments (RFC) documents. Imagine you are looking to manufacture network cables to meet Category 6 (CAT 6) standards—you could access International Organization for Standardization/International Electrotechnical Commission (ISO/IEC 11801) standards documentation. See the following screenshot for an overview of the OSI 7-layer model:

Figure 1.1 – OSI 7-layer model
Vulnerabilities may exist across multiple layers within the OSI model. For example, we may be vulnerable to Man-in-the-Middle (MITM) attacks on our layer 2 switch. We will take a look at the many different threats that may impact an enterprise network throughout the book.
Unified threat management
A unified threat management (UTM) appliance offers firewall functionality and many additional security functions; it is deployed as a single security appliance or software solution. This security solution offers a comprehensive suite of security features all in a single package. While this is a good solution for small enterprises with limited resources (limited staff and limited budget), it does not offer the DiD required by enterprise customers.
UTMs may include a significant number of converged security features, but not necessarily all of the following:
- Network firewall
- Intrusion detection system (IDS)
- Intrusion prevention system (IPS)
- Deep packet inspection (DPI)
- Data loss prevention (DLP)
- Anti-virus capability
- Web application firewall (WAF)
- Web proxy and content filtering
- Spam filtering
- Security information and event management (SIEM)
The following screenshot shows the combined security features supported on a UTM appliance:
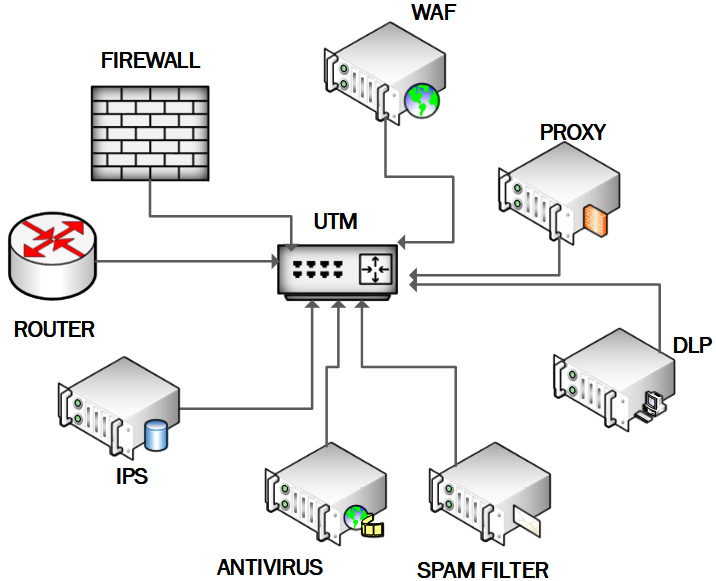
Figure 1.2 – UTM appliance
Advantages
UTM has the following advantages:
- Reduction in management actions (compare the scenario of a small information technology (IT) security team managing and monitoring multiple security appliances)
- Reduced footprint in the data center (less hardware)
- Less cost
Disadvantages
UTM has the following disadvantages.
- Risk from a single point of failure (SPOF) (limited hardware resources are providing many services)
- Negative performance impact on a network due to the workload handled by the device
IDS/IPS
Intrusion detection is an essential security function, typically implemented on the perimeter to protect your organization from incoming threats. It will alert the security team to inbound threats.
Intrusion prevention is the process of performing intrusion detection and then stopping detected incidents. These security measures are available as IDS and IPS. Active protection is the more commonly adopted approach, meaning a network intrusion prevention system (NIPS) will be seen protecting most enterprise networks.
IDS and IPS constantly watch your network, identifying possible incidents and logging information about them, stopping incidents, and reporting them to security administrators. In addition, some networks use IDS/IPS for identifying problems with security policies and deterring individuals from violating security policies. IDS/IPS have become a necessary addition to the security infrastructure of most organizations, precisely because they can stop attackers while they are gathering information about your network.
Examples of intrusions
Indicators of compromise (IOCs) can be unusual traffic, attacks against protocols (such as high volumes of Internet Control Message Protocol (ICMP) traffic), and malicious payloads. The result could be excess traffic causing denial of service (DoS) or compromised systems through unwanted deployments of Trojans and backdoors.
There are two main IDS detection techniques that are routinely used to detect incidents, as outlined here:
- Signature-based detection compares known signatures against network events to identify possible incidents. This is regarded as the simplest detection technique as it evaluates attacks based on a database of signatures written by the vendor or operator. In the same way as a first-generation firewall, this approach is limited as it is based on known patterns.
Examples:
A Secure Shell (SSH) connection using the root account would be in the ruleset.
An email with the subject password reset and an attachment with the name passregen.exe would be identified as malicious.
- Anomaly-based detection compares definitions of what is considered a normal/benign activity with observed events to identify significant deviations. This detection method can be very effective at spotting previously unknown threats. This type of detection is also known as heuristics-based detection.
Example:
The SMTP messaging server usually contributes to 23% of traffic on the network. If the SMTP server is suddenly generating 70% of the network traffic, this would generate alerts.
Network IDS versus NIPS
The NIPS sits directly behind the firewall (inline) and traffic needs to be forwarded onto the network. The NIPS can block unwanted traffic and payloads. This is illustrated in the following diagram:

Figure 1.3 – NIPS placement (inline)
Network IDS (NIDS) does not need to be inline; it can monitor traffic but will need to use port mirroring or spanning on the network switch to be effective, as illustrated in the following diagram:
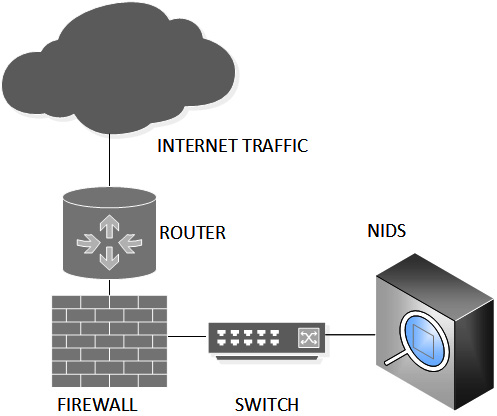
Figure 1.4 – NIDS placement
Wireless IPS
In addition to fixed or wired networks, many organizations may need the flexibility of a Wi-Fi network.
A wireless IPS (WIPS) is designed to detect the use of rogue or misconfigured wireless devices. A rogue device can spoof media access control (MAC) addresses of trusted network devices. A WIPS can build up a database of known trusted hosts on the network and can also be used to prevent DoS attacks.
An effective WIPS should mitigate the following types of threats:
- Ad hoc networks: These use peer-to-peer (P2P) connections to evade security controls and risk exposure to malware.
- Rogue access points (APs): These allow attackers to bypass perimeter security.
- Evil-twin APs: Users may connect to this lookalike network and be vulnerable to sniffing.
- Misconfigured APs: These expose a network to possible attacks due to configuration errors.
- Client misassociation: This risks infection from connecting to other service set identifiers (SSIDs) while in range of the authorized AP.
- MITM attack: An attacker will route traffic through their network device and sniff the traffic.
- MAC spoofing: This may allow the attacker to bypass access-control lists (ACLs) on the AP or allow them to impersonate another network device.
- DoS attack: This happens when a continuous stream of fake requests or messages is sent to the AP.
Inline encryptors
The High Assurance Internet Protocol Encryptor Interoperability Specification (HAIPE-IS) requires inline network encryption (INE) devices to be interoperable. For example, Tactical Local Area Network Encryptor (TACLANE) is a product used by the United States (US) government and the Department of Defense (DOD); it is military-grade and meets National Security Agency (NSA) security requirements. It is manufactured by General Dynamics. This is a device that enables encrypted communication over untrusted networks. Commercial organizations will use site-to-site virtual private network (VPN) links and not need this technology. The following figure shows a TACLANE INE device:

Figure 1.5 – INE device
This device meets the high assurance required by government and military remote connections.
Network access control
Network access control (NAC) enforces a strong, secure posture for devices that connect to our enterprise networks.
A major challenge for many enterprise networks is unmanaged bring your own device (BYOD) devices and guest devices accessing wireless and switched networks. The goal is to control access to the network, ensuring devices are compliant with baseline security policy. You would want to ensure devices had anti-virus installed and had security patches and firewall functionality.
Devices typically connect through a registration virtual local area network (VLAN) using a captive portal. If devices are found to be compliant, they could gain network access. Devices found to be uncompliant would be routed through to an isolation VLAN, able to access remediation services. The following diagram shows the components of NAC:
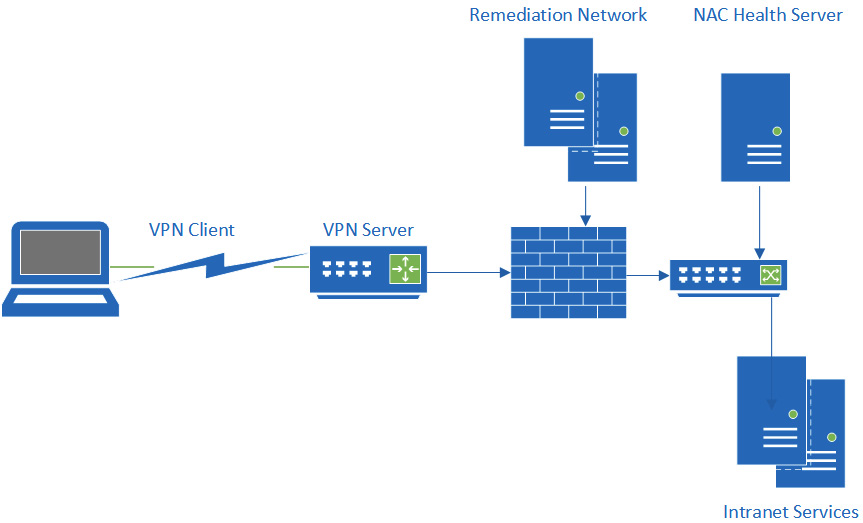
Figure 1.6 – NAC
PacketFence offers a free and open source NAC solution that is distributed under the General Public License (GPL). The software can be accessed via https://www.packetfence.org/.
SIEM
SIEM allows an organization to centralize security management events, forwarding logs from security appliances to a central system. It provides correlation and normalization for context and alerting, and also provides reporting and alerts based upon real-time logged data inputs. The following diagram shows the architecture of centralized SIEM:
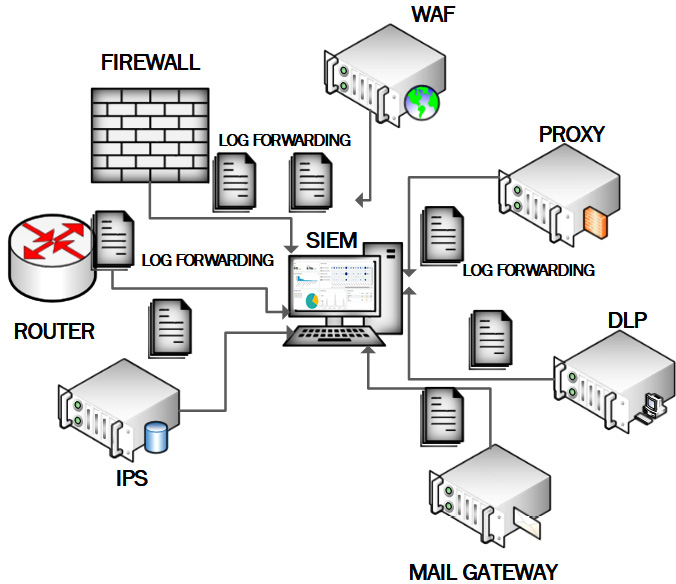
Figure 1.7 – SIEM architecture
Advanced solutions can use behavioral analytics to detect anomalous user behaviors. Privileged user monitoring is a common requirement for compliance reporting. The following screenshot shows a SIEM dashboard:
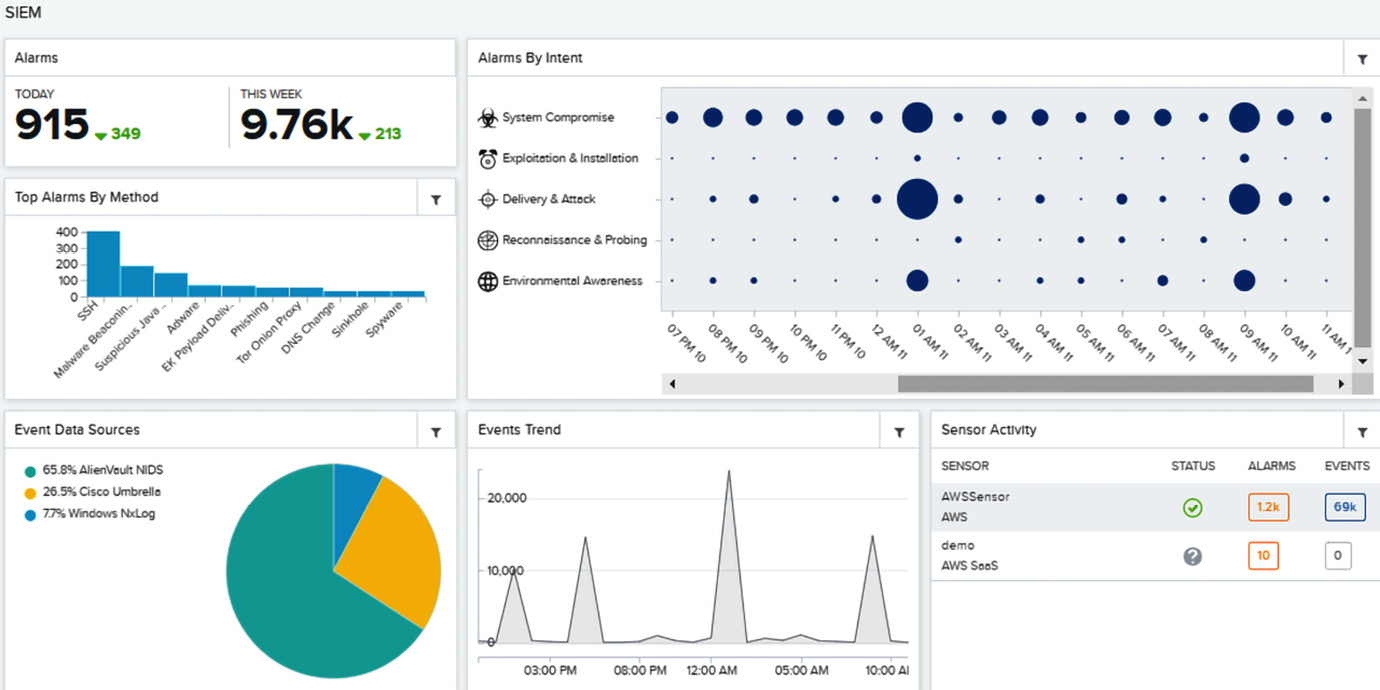
Figure 1.8 – AlienVault/AT&T SIEM dashboard
SIEM threat intelligence can help security operations center (SOC) teams pinpoint malicious or risk-based events and deliver a response. Analytics and machine learning (ML) are used to produce insights from huge amounts of collated data; they offer automation to identify hidden threats. Benefits include the following:
- Real-time monitoring: Stop threats that can be fast-moving.
- Incident response: Quickly identify threats to begin a response.
- User monitoring: This will identify unusual user behaviors and risky privilege use.
- Threat intelligence: Build up knowledge of security teams.
- Advanced analytics: Aid the analysis of large amounts of logged data.
- Advanced threat detection : SOC analysts need this advanced toolset to detect and address IOCs.
Switches
A switch is a network device that connects devices on a computer network by receiving and forwarding data to the destination device. Switches use layer 2 MAC addresses to forward data frames at layer 2 of the OSI model. Many enterprise switches will also combine layer 3 functionality in the switch. Layer 3 switches allow for routing traffic between VLANs.
Switches are vulnerable to DOS attacks; the content-addressable memory (CAM) is typically overloaded/flooded with spoof MAC addresses. Switches can be used for MITM when using Internet Protocol version 4 (IPV4) Address Resolution Protocol (ARP) broadcasting. They can also suffer performance degradation due to unwanted looping traffic.
Mitigation would include the following:
- Protect the management interface (use strong passwords).
- Enable Spanning Tree Protocol (STP) (this will block redundant connections) to prevent looping traffic.
- Connect using SSH (all management traffic is encrypted).
- Provide an out-of-band (OOB) network (all management is performed on a separate management network).
- Configure 802.1x (require all network connections to be authenticated).
The following screenshot shows what a switch table looks like:

Figure 1.9 – Switch table
Switches provide essential services on enterprise networks and will be responsible for the bulk of all network traffic.
Firewalls
Firewalls are there to block unwanted traffic entering your networks; they can also block outbound traffic. They depend upon rules to block IP addresses, protocols, and ports. More sophisticated firewalls will have more granular rules and may slow down traffic.
Firewall types
Firewalls can be implemented in many different ways; enterprise deployment will have highly capable hardware solutions from vendors such as Cisco or Check Point. Software or host-based firewalls offer additional security with DiD. Data centers and microsegmentation will accelerate the use of virtual firewall deployment. Different types of firewalls are listed here:
- Hardware firewalls provide maximum performance. These are typically dedicated appliances with a central processing unit (CPU) and memory dedicated solely to this function.
- Software firewalls generally run on a host operating system, such as Microsoft Windows Defender Firewall or Linux iptables. They share computing resources with the operating system.
- Virtual firewalls are appliances running on a virtual host controlled by a hypervisor. The performance is dependent upon the compute resources allocated by the hypervisor.
Firewall capability
Firewalls have evolved over time, with additional capabilities and functionality.
First-generation firewalls use static packet filtering. They inspect packet headers and implement static rules based upon IP addresses and port addresses. Their big advantage is high performance. A router will typically perform as a static packet filter.
Second-generation firewalls also use stateful inspection, in addition to packet filtering. This can monitor Transmission Control Protocol (TCP) streams (whole stream, not just handshake) and dynamically open ports and track sessions for bi-directional protocols (such as File Transfer Protocol (FTP)).
Next-generation firewalls (NGFWs) have evolved from second-generation firewalls to meet the requirements of a multi-functional security appliance. An NGFW offers all the functionality of the earlier generation, but will typically offer additional functionality in the form of support for VPNs and anti-virus protection. NGFWs have DPI capability, meaning they can offer additional security in the form of DLP and IPS protection. This should not be confused with UTM, although they are similar. NGFWs are designed with performance in mind.
Routers
Routers operate at layer 3 of the OSI model and are interconnection devices (they connect networks together). Routing capability may also be provided by a switch that supports VLANs (it will be called a layer 3 switch).
Routing tables
Routers are only able to forward packets if they have a route for the traffic or a default gateway. Routing tables will comprise a NETWORK DESTINATION, NETMASK, GATEWAY, INTERFACE, and METRIC value.
Here is a simple routing table:
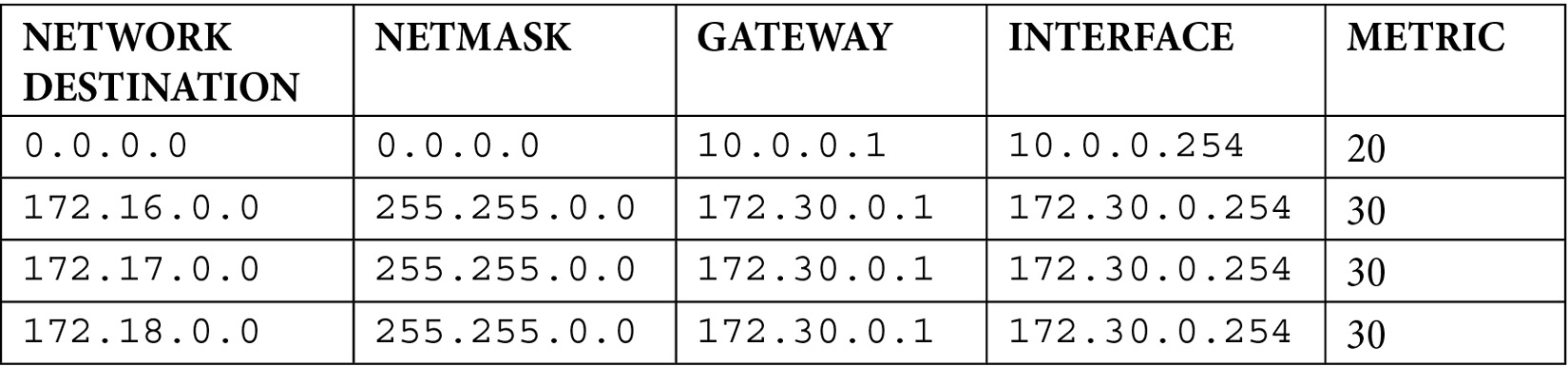
Figure 1.10 – Routing table
Static routing tables may be acceptable for small networks, but we will need to support automated dynamic routing for larger networks.
Dynamic routing
In larger, more complex networks, it is normal to use dynamic routing rather than configuring manual static routes. Within an autonomous network (the network managed by your organization), you will be using interior routing protocols. It would be time-consuming to configure routing tables statically and we would miss the resilience offered by dynamic routing protocols.
The purpose of dynamic routing protocols includes the following:
- Discovering available remote networks
- Maintaining up-to-date routing information
- Choosing the most efficient path to remote networks
- Allocating a new path if a route is unavailable
Routing Information Protocol (RIP) is the simplest and easiest routing protocol to configure. It is used for routing over smaller networks (allowing a maximum of 15 hops). It is not considered a secure routing protocol.
Enhanced Interior Gateway Routing Protocol (EIGRP) is used on Cisco networks and was developed to work around the drawbacks of using RIP. EIGRP benefits from fast convergence times whenever the network topology is changed.
CISCO devices share their capabilities using Cisco Discovery Protocol (CDP) with immediate neighbors. This can be disabled on a network.
You can prevent your router from receiving unwanted/poisoned route updates by configuring neighbor router authentication; this uses Message Digest 5 (MD5) authentication.
Open Shortest Path First (OSPF) is a good choice for larger networks because it has no restriction on hop counts. OSPF allows routers to communicate securely, and routing information is exchanged through link-state advertisements (LSA). RFC 2328 allows for the use of a keyed MD5 identifier to protect OSPF neighbor updates.
Exterior routing
To keep internet working routing tables up to date, edge routers will forward route changes via exterior routing protocols.
Border Gateway Protocol (BGP) is the routing protocol used between internet service providers (ISPs). BGP can also be used to send routing updates between an enterprise and its ISP. BGP can be secured so that only approved routers can exchange data with each other (this uses MD5 authentication).
Proxy
A proxy server acts as a gateway between users and the internet services they access online.
A proxy protects your users from directly connecting with unsafe sites. It can offer Uniform Resource Locator (URL) filtering and content filtering in addition to performance enhancements. A proxy can be a good choice when protecting our users from threats based upon outbound requests. Firewalls are not designed to deliver this more granular protection. A firewall could block an outbound connection to a port and IP address, but would not offer the same fine-tuning as a proxy server.
Network address translation gateway
Network address translation (NAT) is a networking technique commonly used to give an entire private network access to the internet without needing to assign each host a public IPv4 address. The hosts can create connections to the internet and receive responses but will not receive inbound connections initiated from the internet (as they are, in effect, hidden). The following diagram shows a NAT router forwarding traffic to the internet from an internal host:

Figure 1.11 – NAT routing
When a host on the internal (private) network sends a request to an external host, the NAT device's public IP address is used as the new source IP address for the outbound traffic. The traffic sent back in reply is returned to the internal host. Most NAT solutions use port address translation (PAT) to keep track of all the private hosts that have sessions. We can see NAT configuration in the following screenshot:
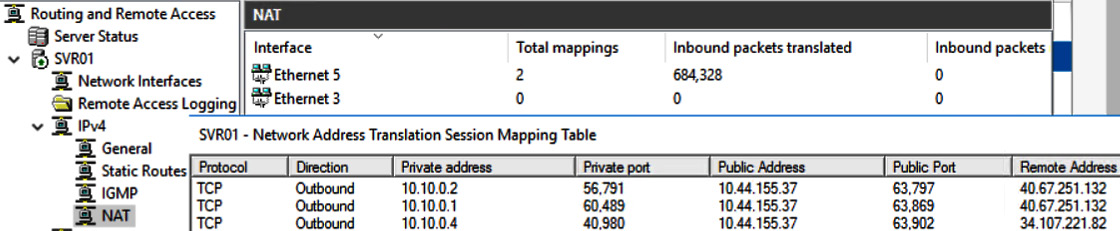
Figure 1.12 – Microsoft Routing and Remote Access Service (RRAS) with connected clients
NAT is an important service used in both enterprise and small business deployments.
Load balancer
A load balancer will be useful to enterprises that host server farms and would be a key requirement for high availability (HA) e-commerce sites. When hosting a Citrix server farm supporting remote applications, it is important that the loading on each member is constantly evaluated to ensure new requests are forwarded to a server with the least load.
Hardware security module
A hardware security module (HSM) is a special trusted network computer performing a variety of cryptographic operations: key management, key exchange, encryption, and so on. This device can be a rack-mounted appliance secured in your data center or could be a built-in module for high-end server hardware.
A trusted platform module (TPM) is typically built into system boards of laptop and desktop computer systems, allowing for the storage of sensitive protected data, including keys and attestation measurements. This is a good example of an HSM incorporated into the system board.
MicroSD HSM is built into a MicroSD form factor. It is useful when you need to extend the functionality of a mobile device and could be used on a cellular phone for secure communications. The HSM would have its own crypto-processing capability, meaning no changes are required on the mobile device. The following screenshot shows a small form-factor HSM:

Figure 1.13 – MicroSD HSM
Many of the security applications mentioned up to this point secure the entire network from threats. In the following section, we will examine more targeted/granular approaches to protect particular services or data types.
Application- and protocol-aware technologies
Some applications will benefit from dedicated security appliances/services operating on sole behalf of those applications. Imagine you wanted to protect your web application server from typical exploits, including cross-site scripting (XSS), cross-site request forgery (XSRF), and Structured Query Language (SQL) injection. In that case, you would not want to filter all traffic for these exploits using the network firewall; it would have a huge workload and would slow down traffic for the entire network. Application-aware security appliances process traffic only being forwarded to that service.
The types of security applications that inspect and apply rulesets to application layer traffic are said to be using DPI.
It is important to plan for the placement of these devices to ensure traffic can be inspected before entering or leaving the network and to also minimize latency or delay where inspection and filtering are not required.
In the following section, we will take a look at some examples of application- and protocol-aware security solutions.
DLP
We must ensure the enterprise does not breach legal or regulatory compliance by exfiltration of sensitive data, either knowingly or unknowingly. It is important that intellectual property and customer data are protected, even when compliance is not a factor. Physical restrictions and/or enforceable policy may be used to block data exfiltration to a removable storage medium. DLP can also be implemented on the edge of the network, or as part of a cloud solution. Microsoft is one of many providers offering DLP as part of the Cloud Access Security Broker (CASB) security suite. In the following screenshot, we are selecting built-in rules to block the exfiltration of financial data:
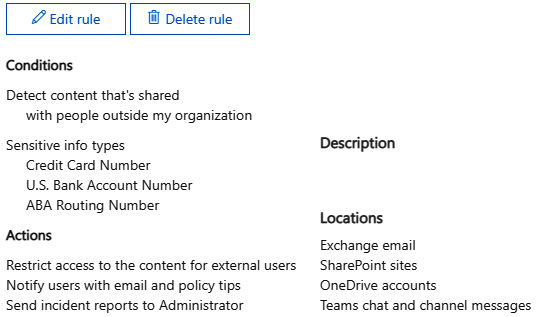
Figure 1.14 – Microsoft 365 DLP rule
There are many built-in templates for regulated industries.
WAF
A WAF is defined as a security solution on the web application level. It allows for HyperText Transfer Protocol/HTTP Secure (HTTP/HTTPS) traffic to be inspected for anomalies without slowing down the rest of the network traffic. A WAF can be implemented as an appliance, plugin, or filter that applies a set of rules to an HTTP connection.
A WAF helps prevent attacks, such as the following:
- SQL injection attacks
- XSS attacks
- Malicious file execution
- CSRF attacks
- Information leakage
- Broken authentication
- Insecure communications
A WAF can also provide URL encryption and site usage enforcement, as illustrated in the following diagram:
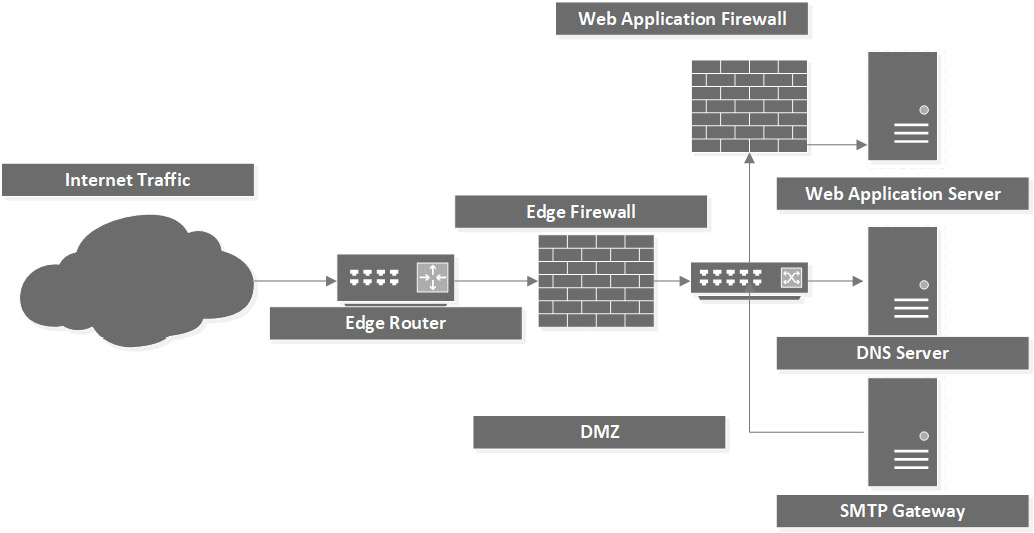
Figure 1.15 – WAF
Advantages
A WAF has the following advantages:
- Allows for the creation of custom rules
- Monitors and blocks malicious traffic
- Can prevent live attacks
- Protects vulnerable web applications
Disadvantages
A WAF has the following disadvantages:
- May slow web traffic
- Could block legitimate traffic
- Requires frequent tuning
Database activity monitoring
Database activity monitoring (DAM) tools monitor, capture, and record database activity in near real time and can generate alerts when rules are violated.
DAM can be accomplished by doing the following:
- Network sniffing
- Reading of database logs
- Memory analysis
DAM tools can correlate data and provide the administrator with the tools to detect anomalous database activity and capture a log of events, should this be required for forensics.
As a database is often a critical line-of-business (LOB) solution, often hosting enterprise resource planning (ERP), customer relationship management (CRM), sales order processing, and so on, investing in this additional technology will be worth the cost.
Spam filter
A spam filter typically scans incoming emails to protect your employees from email-borne threats. It can also scan emails leaving the organization (although this is more likely taken care of by a DLP solution). It can be deployed on the demilitarized zone (DMZ) network, filtering incoming SMTP traffic, and will typically perform additional tasks such as querying Spamhaus Block List (SBL) providers, such as Spamhaus, to drop connections from verified blocked domain names or IP addresses.
Many organizations will deploy this service in a cloud deployment, especially if the ISP hosts the email servers.
The following section covers some of the additional considerations to allow for secure remote working and administration.
Advanced network design
Since the Covid-19 pandemic began to transform the workplace in 2020, there has been a major effect on the way employees access their enterprise's desktop and company data. Enterprises have been forced to accept that the modern workplace will contain a high number of remote working employees. Many enterprises expect a significant proportion of staff to continue with this flexible way of working due to the benefits of work/life balance. What was previously considered the exception, where some workers were able to remotely access the workplace or connect from a temporary location such as a hotel or airport transit lounge, will likely now become the new normal.
There are significant risks in extending the network perimeter to these remote workers, and it is important that all access is secure and identities are verified.
Remote access
This is the term used when accessing systems remotely. We may need to access a desktop to configure settings for a remote worker or configure a network appliance ruleset. In some cases, it may be necessary to assist a remote worker by sharing their desktop. We will compare the main types of remote access in this section.
VPN
A VPN service provides you with a secure, encrypted tunnel when you need to connect across untrusted networks. External threat actors cannot access the tunnel and gain access to your enterprise data.
A VPN can be used for securing remote workers and can also be used to connect sites across untrusted networks.
Enterprise solutions include Microsoft Direct Access, Cisco AnyConnect, and OpenVPN (there are many more). Figure 1.16 shows a popular VPN client, OpenVPN Connect:
Figure 1.16 – OpenVPN client
Many enterprises will ensure their employees' mobile devices are enabled with an always-on VPN client. This ensures that when employees are working outside the corporate network, they will automatically connect over a secure connection, whenever the device is powered on. It is important that all traffic is routed through the VPN connection using a full-tunnel configuration. Figure 1.17 shows a full-tunnel configuration:

Figure 1.17 – Full-tunnel configuration
When the VPN interface is configured with the default gateway configuration, as shown in Figure 1.17, all traffic is routed through the company network, ensuring security policies are enforced.
IPsec
IP Security (IPsec) is a suite of protocols deployed in most vendor implementations of IPv4 and is a requirement for IP version 6 (IPv6). When configured, it will protect against replay attacks and ensure the integrity and confidentiality of the data.
Authentication headers (AHs) provide authentication, integrity, and protection against replay attacks.
Encapsulating Security Payload (ESP) provides authentication, integrity, and confidentiality for your data.
When using Transport mode, encryption occurs at the internet layer, protecting all of the layers above the network layer. It is used internally only.
Tunnel mode can be used to create site-to-site VPNs between trusted networks and to connect a host device across an untrusted network. In the following screenshot, we can see that Tunnel mode creates a new IP header:
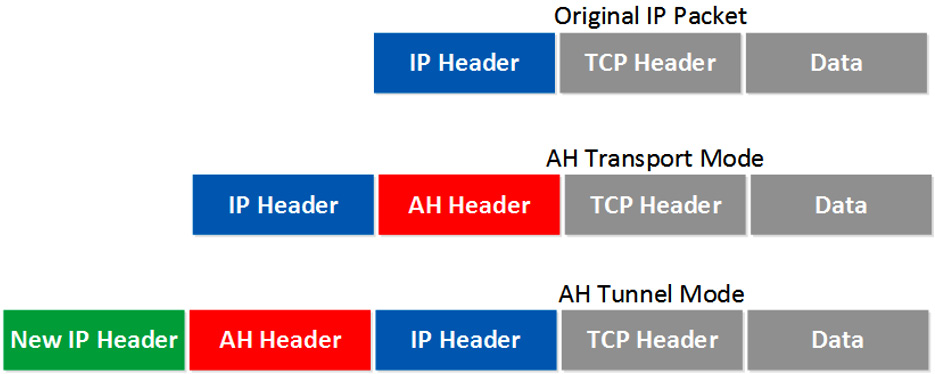
Figure 1.18 – IPsec modes
While IPsec is typically used to protect communications outside the enterprise, it can also be used internally when VLANs cannot offer adequate protection. This is when Transport mode would be appropriate.
SSH
SSH is a standard internet security protocol documented in RFCs 4251, 4253, and 4254. The SSH protocol is a protocol for secure remote login and other secure network services over an insecure network. It is recommended to use SSH in place of Telnet. (Telnet was the main protocol for remote configuration, but it is not encrypted.)
The SSH protocol is typically used across enterprise networks for the following:
- Providing secure access for users and automated processes
- Secure file transfers
- Issuing remote commands
- For admins or technicians to manage network infrastructure
A technician could administer a network switch remotely, without needing to connect a direct cable into the device. The following screenshot offers an overview of the use of SSH:

Figure 1.19 – SSH remote security
SSH has wide support across many hardware vendor platforms and operating systems, including Microsoft (it now comes as an optional feature that can be installed on Windows 10), Linux distributions, and Apple's macOS and iOS.
Tip
Make sure you are using SSH 2.0 as earlier implementations use a poor cryptographic suite.
Remote Desktop Protocol
Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft that provides a user with a graphical interface to connect to the desktop of a remote computer. An RDP client application must be installed to launch a connection, and the remote computer must run RDP server software. RDP has wide support, and software exists for non-Microsoft operating systems, including Linux, Unix, macOS, iOS, Android, and other operating systems. While RDP servers are built into most Windows operating systems (Home editions of Windows desktop editions are an exception), it is also possible to install RDP server services for Unix and macOS X. The default listening port is TCP 3389 and User Datagram Protocol (UDP) port 3389. It is important to consider the security implications of enabling RDP services, as this will give a remote user access to the full range of tools and utilities for remote configuration.
Tip
Remember that this connects to a desktop, so it will not be a choice when administering networking hardware appliances.
Virtual Network Computing
Virtual Network Computing (VNC) is used for desktop sharing, as opposed to remote control only. It is platform-independent and can be used across many different operating systems. While it is a commercial product and must be licensed for business use, there is a free edition for non-commercial use.
Reverse proxy
A reverse proxy is commonly used when accessing large websites from a public network. Reverse proxies can cache static content (much like a forward proxy), which reduces the load on your web application servers. Reverse proxies can also be used as an extra security layer, allowing for additional analysis of the incoming traffic. The following screenshot shows a client accessing a web application through a reverse proxy:

Figure 1.20 – Reverse proxy
HAProxy and Squid are open source software implementations used by large internet websites. They will decrypt the incoming HTTPS traffic and apply security rules.
Network authentication methods
It is important to authenticate access onto enterprise networks. The modern approach is to start out with the Zero Trust model, which means that no devices are trusted by default. To gain access to a network segment, authentication credentials or some other verification will be required before access is granted. In the past, the priority was always about protecting our systems from threats outside our network. This traffic moving between the internet and our perimeter network is referred to as North-South traffic. Traffic moving within our internal network segments is referred to as East-West traffic. Due to increased instances of mobility and remote workers accessing multiple networks and Information systems, it is this East-West traffic that must also be secured. We will now take a look at the options to secure access to the network.
802.1x
802.1X is an Ethernet standard using port access protocol for protecting networks via authentication. It was originally intended for use with Ethernet 802.3 switched networks but has become a useful addition to many different network types, including Wi-Fi and VPN. A connecting host or device is authenticated via 802.1X for network access—if authentication is successful, the port is opened; otherwise, it remains closed.
There are three basic pieces to 802.1X authentication, as outlined here:
- Supplicant: A software client running on the host
- Authenticator: The VPN or switch port
- Authentication server: An Authentication Authorization Accounting (AAA) service, usually a radius server such as Microsoft Network Policy Server (NPS)
There are many options when it comes to authenticating the supplicant (client device). In the first instance, we have rudimentary (for that, read insecure) methods of authentication.
Password Authentication Protocol (PAP) does not secure the authentication request.
Challenge-Handshake Authentication Protocol (CHAP) is an improvement over PAP as it supports mutual authentication and uses MD5 hashing to encrypt the challenge.
As CHAP is dependent on MD5, your networks are at risk from pass-the-hash exploits.
Extensible Authentication Protocol (EAP) is a framework of protocols, allowing for the secure transmission of the supplicant's authentication request. It allows the authentication channel to be encrypted using TLS. The following diagram shows the required components for a client to authenticate onto the wireless network:

Figure 1.21 – Network authentication
EAP-TLS provides certificate-based mutual authentication of the client onto the network. This requires certificates to be deployed on the supplicant and the AAA server, although it is worth mentioning that devices could be provisioned with Secure Certificate Enrollment Protocol (SCEP) if you are using a mobile device management (MDM) tool.
EAP-Tunneled TLS (EAP-TTLS) is an extension of EAP-TLS. This can be used for mutual authentication, or certificates can be deployed just on the AAA server.
EAP-Flexible Authentication via Secure Tunneling (EAP-FAST) was developed by Cisco. This uses something called a Protected Access Credential (PAC), which can be managed dynamically by the AAA server.
Lightweight Extensible Authentication Protocol (LEAP) is an EAP authentication type, again developed by Cisco. It is used on Wi-Fi networks and uses Wireless Equivalent Privacy (WEP) keys for mutual authentication. It is no longer considered secure.
Protected Extensible Authentication Protocol (PEAP) allows for authentication using passwords, certificates, or smartcards. The authentication traffic between PEAP clients and an authentication server is encrypted using TLS but requires only server-side certificates. PEAP was developed by a consortium of Microsoft, Cisco, and RSA Security.
Placement of hardware and applications
It is important to recognize that many different types of devices may need to be supported on an enterprise network. Some systems may have embedded processing logic that is legacy and vulnerable, or maybe regulatory compliance means certain processes must be isolated from regular business networks. In the following section, we will look at these use case scenarios.
System on a chip
A system on a chip (SoC) consolidates multiple computer components onto a single, integrated chip (IC). Components will typically include a graphical processing unit (GPU), a CPU, and system random-access memory (RAM).
As an SoC integrates hardware and software, it is designed to draw less power than traditional multi-chip solutions. The Snapdragon processor used in Microsoft Surface X tablets has eight cores plus GPU.
Examples of this SoC technology can also be found in many IoT devices, building automation systems, and Wi-Fi routers. Raspberry Pi is a good example of this technology, costing as little as $5 per device. We can see a typical SoC in the following figure:

Figure 1.22 – Raspberry Pi
It is important to consider the security implications of using SoC technology. Due to the low cost and nature of embedded logic common to these devices, vulnerabilities are common and can be difficult to mitigate without replacing the device.
In 2018, the NSA was attacked and suffered a significant data breach due to an unauthorized Raspberry Pi device connected to the agency's network. To read more about this published incident, see this link: https://tinyurl.com/nasapihack.
Heating, ventilation, and air conditioning controllers
Heating, ventilation, and air conditioning (HVAC) is a critical function; sensitive equipment must be placed in an environment that is optimized for temperature and humidity. The monitoring and adjustment for this function need to protect and should be accessed over a segmented/protected network zone. Typical protocols used to communicate and manage these systems use formats such as Modbus, Siemens, and BACnet (there are many others). Modbus does not provide any security, meaning that if these industrial networks were breached, it would be relatively easy to cause outages and disruption on them.
Sensors
Sensors are sophisticated devices that are frequently used to automate the collection of information in automated or industrial environments. A sensor converts the physical parameter (for example, temperature, blood pressure, humidity, and speed) into a signal that can be measured electrically. Examples would include magnetic field sensors, ultrasonic sensors, temperature sensors, flow sensors, and photoelectric sensors, to name but a few. It is essential that the calibration of this equipment and messages sent or received is accurate and controlled. HVAC, engineering production lines, and medical equipment providers are just some of the environments that depend on this technology. The following figure shows a typical monitoring sensor:

Figure 1.23 – Temperature monitoring sensor
Physical access control systems
A physical access control system (PACS) can be used to grant access to employees and contractors who work at or visit a site by electronically authenticating their Personal Identity Verification (PIV) credentials.
Examples could include mantraps (now referred to as access control vestibules), radio-frequency identification (RFID) card readers, and biometric identification systems.
Audiovisual systems
Audiovisual (A/V) technology systems can be comprised of an assortment of hardware that includes conference telephones, video cameras, interactive whiteboards, digital signage, computers, smartphones, tablets, wireless connectivity, and more. Examples could be video screens distributed throughout a building to broadcast information to employees.
Closed-circuit television systems
A closed-circuit television (CCTV) system is an important feature for both security and safety on a physical site. In many cases, it is a requirement to meet the needs of regulatory compliance. It is important to safeguard access to CCTV camera feeds and the networks that connect them. Many cameras will now be IP cameras, meaning they can be added directly to Ethernet or Wi-Fi networks. If they are not secured, hackers will discover their location, and you may find that camera IP addresses and locations will be posted onto internet search engines. One such search engine is https://www.shodan.io.
The following screenshot shows a listing of unsecured IP cameras worldwide (there are over 4 million):
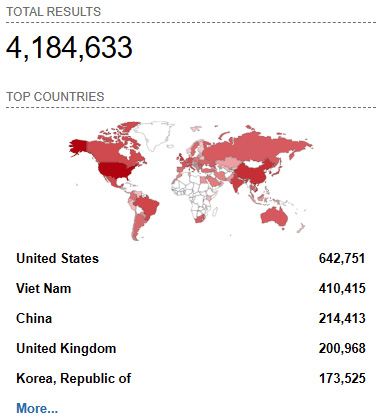
Figure 1.24 – Unsecured IP cameras
It is important to place this type of equipment onto segmented networks and change default credentials.
Critical infrastructure
Critical infrastructure is a term to describe assets that are essential for the functioning of a society and economy.
In the US, a new government agency was founded in 2018, offering guidance and helping to build secure and resilient infrastructure: the Cybersecurity and Infrastructure Security Agency (CISA).
CISA lists 16 sectors that are considered of such importance to the US that their incapacitation or destruction would have a major negative effect on security, national economic security, national public health, or safety. You can view which sectors these are in the following list:
- Chemical sector
- Commercial facilities sector
- Communications sector
- Critical manufacturing sector
- Dams sector
- Defense industrial base sector
- Emergency services sector
- Energy sector
- Financial services sector
- Food and agriculture sector
- Government facilities sector
- Healthcare and public health sector
- IT sector
- Nuclear reactors, materials, and waste sector
- Transportation systems sector
- Water and wastewater systems sector
The European Commission (EC) has launched its own program to reduce the vulnerabilities of critical infrastructures: the European Program for Critical Infrastructure Protection (EPCIP).
Supervisory control and data acquisition
Supervisory control and data acquisition (SCADA) is a system of software and hardware elements that allow industrial organizations to do the following:
- Regulate industrial processes locally or at remote locations
- Display, gather, and process real-time data
- Allow interaction with devices such as pumps, motors, and sensors through human-machine interface (HMI) software
- Populate events into a log file
SCADA systems are crucial for any organization with an industrial capacity. SCADA allows organizations to maintain efficiency, process data for smarter decisions, and communicate system issues to help mitigate downtime. SCADA has been used in industrial, scientific, and medical environments since the adoption of computers in the 1950s. Some of the equipment was not always designed with security in mind.
The basic SCADA architecture features programmable logic controllers (PLCs) or remote terminal units (RTUs). PLCs and RTUs are microcomputers that communicate with an array of objects such as factory machines, HMIs, sensors, and end devices and then carry the information from those objects to computers with SCADA software deployed. The SCADA software processes, distributes, and displays the data, helping operators and other employees analyze the data and make important decisions.
SCADA networks monitor and manage legacy/vulnerable industrial control networks, often using monolithic protocols. They are therefore an easy target to attack; it is vital that guidance is taken and controls put in place to mitigate the risks. In December 2015, 30 Ukrainian electrical substations were turned off by hackers. This left around 230,000 homes without power for several hours. Critical infrastructure tools, tactics, and protocols are documented by MITRE (see the following link: https://tinyurl.com/mitreics). For more information on the Ukrainian power grid attack, please go to this link: https://tinyurl.com/icspowerattack.
NetFlow
NetFlow was originally developed on Cisco networking equipment to log traffic. It allows network engineers to gain an understanding of bandwidth usage and types of traffic flow. It now has wide support and is supported on many other kinds of networking equipment, including Juniper, Nokia, Huawei, and Nortel (there are many more). It is not intended to replace protocols such as Simple Network Management Protocol (SNMP). It is useful to establish a baseline and see anomalies on a network. Cisco supports this protocol on most network equipment.
NetFlow consists of three main elements, as outlined here:
- Flow exporter: This passes the logs to the collector.
- Flow collector: This is where the logged data is stored.
- Analysis application: Analyzes received data and reports on the collected data.
Devices that support NetFlow can collect IP traffic statistics on all interfaces where NetFlow is enabled, and later export those statistics as NetFlow records toward at least one NetFlow collector—this is normally a server that does the actual traffic analysis. We can see an overview of the NetFlow process in the following screenshot:

Figure 1.25 – NetFlow
Not all network vendors support NetFlow, but there is an alternative that is also designed for higher-speed networks.
sFlow
The sFlow protocol (short for sampled flow) is an alternative industry standard for data packets in computer networks. Unlike NetFlow, this is not a proprietary protocol. Its participants include Hewlett-Packard (HP), Brocade, Alcatel-Lucent, Extreme Networks, Hitachi, and more. This only logs a percentage of the traffic, which is referred to as sampling. sFlow is used on high-speed networks (gigabit-per-second speeds, and higher).
Data flow diagram
A data flow diagram (DFD) is essential for understanding the flow of information across networks, which may mean interacting with customers, partners, and internal systems. In the following diagram, we can the flow of transactions between different information systems:
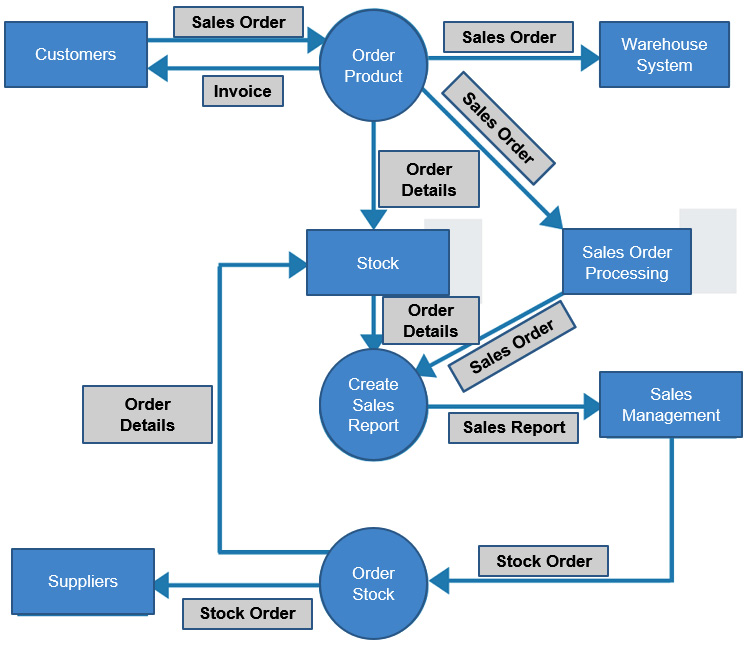
Figure 1.26 – DFD
It is important to see the movement of network traffic between the different information systems in order to place the appropriate security controls in the correct location.
Secure configuration and baselining of networking and security components
It is vitally important that all networking equipment meets a measurable security baseline. For mission-critical switches, DOD uses secure technical implementation guides (STIGs); there are over 50 security requirements in the Cisco IOS Switch STIG. We can see typical configuration items in the following screenshot:

Figure 1.27 – Cisco IOS Switch security baseline
There are configuration guides for many network appliances as well as for operating systems and applications.
Software-defined networking
Software-defined networking (SDN) technology is a well-established approach to network management and has been in existence for over 10 years (established around 2011).
It has really come about due to a movement to large, centralized data centers and the virtualization of computer systems. The move to cloud computing has also been a big driver toward the adoption of SDN.
There are many components to move to a true SDN model, and the components shown in Figure 1.28 are important parts.
SDN has been designed to address the fact that traditional networks are often decentralized and overly complex— think of all those vendor solutions (Cisco, Juniper, HP, Foundry, and so on) with their own hardware and software solutions. SDN allows for a more dynamic, configurable approach. Where the hardware switch (or virtual switch) becomes the data plane and is separated from the management or control plane, application programming interfaces (APIs) allow for dynamic updates to be controlled by business applications and services.
The following screenshot shows a depiction of SDN:
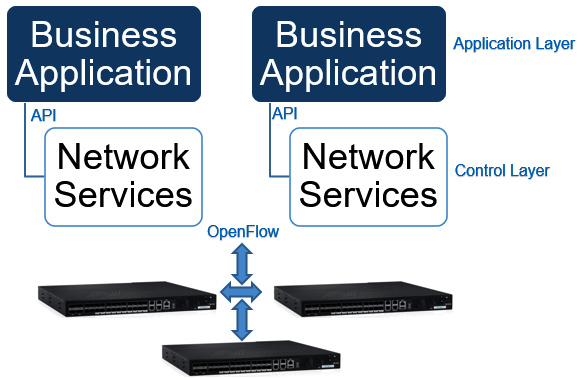
Figure 1.28 – SDN
Network function virtualization (NFV) takes the place of dedicated hardware with virtualized software. This means that network services such as firewalls, switches, and routers may now be deployed as software in the data center.
Open SDN
SDN is based upon a set of open standards, allowing for simplified network design and operation because instructions are provided by SDN controllers instead of multiple, vendor-specific devices and protocols.
OpenFlow was the first standard interface for separating network control and data planes.
Open Network Operating System (ONOS) is a popular open source SDN controller.
Hybrid SDN
Many enterprise networks still have a significant investment in traditional network infrastructure. While they move toward the goal of SDN, they need to transition and support both technologies. They will need to support a hybrid model.
SDN overlay
This basically moves traffic across physical networking infrastructure. If you compare Multiprotocol Label Switching (MPLS) links switching customers' VLAN tagged traffic across a wide-area network (WAN), then this is a similar concept.
The following diagram shows an SDN overlay model:
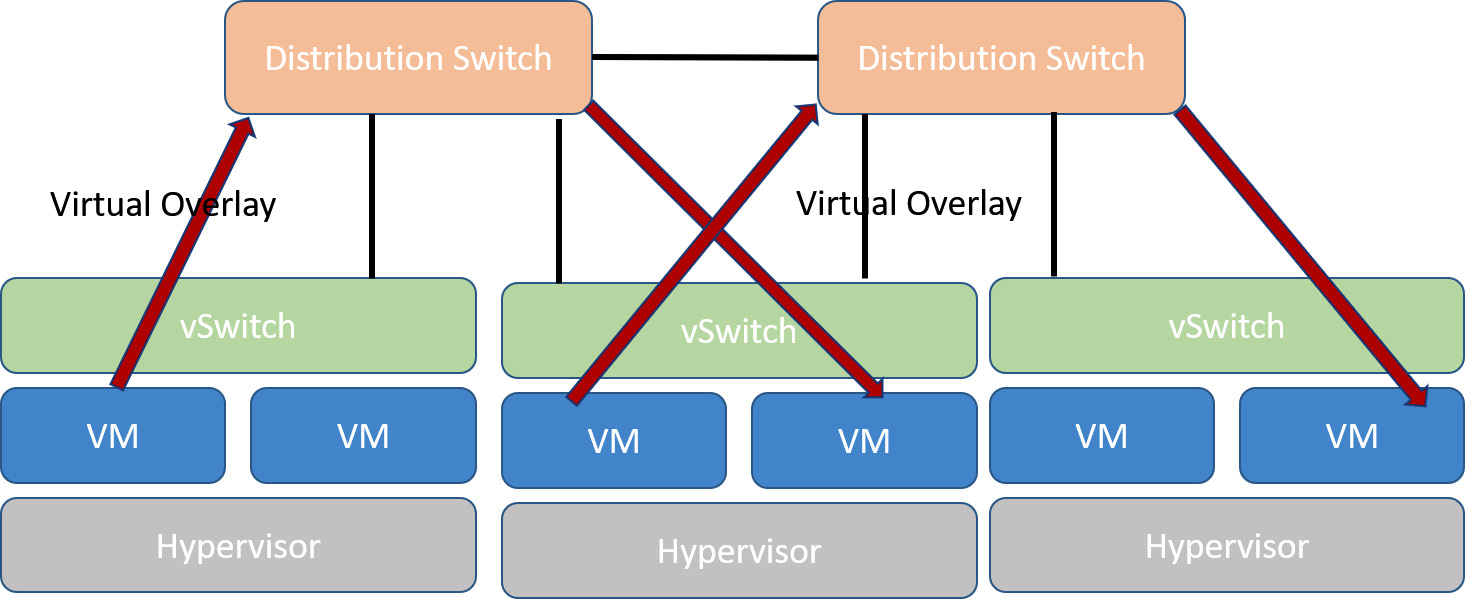
Figure 1.29 – SDN overlay
We're now at the end of this section, and you should have gained an understanding of some challenges that are presented by an enterprise network. Hybrid networks bring fresh challenges all the time and requirements for remote access. Zero Trust networks mean we must ensure all network access is authenticated and authorized. Challenges have arisen from the widespread adoption of cloud and virtualization, meaning the adoption of new technologies is increasing in our data centers. We must be able to monitor and respond to increasing network demands across the enterprise.
Network management and monitoring tools
In this section, we will look at some of the challenges that need to be considered when managing an enterprise network. In particular, we must protect networking services and equipment from unauthorized changes and ensure traffic can flow across our networks.
Alert definitions and rule writing
It is important that rules used by our advanced network protection devices do not cause unnecessary blockages or allow our networks to be overwhelmed by unwanted/malicious traffic. If rules are implemented poorly, then we may see a high number of false positives, meaning the traffic is benign (non-threatening). False negatives will mean the traffic was considered harmless when in fact it is malicious.
Tuning alert thresholds is an important step. An example could be auditing for anomalous file access to a storage device containing a mixture of data with different classification labels. You want to log all read and write access to customer records with an alert being generated for Move or Copy actions. However, if you set this rule up for all data directories, including non-sensitive data, then you may be overwhelmed by unnecessary alerts.
Eventually, your SOC staff will experience alert fatigue, meaning they may well dismiss important security events.
Advanced configuration of network devices
It is important to consider all the current threat actors and future threat actors when designing an enterprise network. Networks are complex and need thorough planning to properly mitigate against known threats and future unknown threats. Advanced tools to detect and mitigate these threats are covered in Chapter 2, Integrating Software Applications into the Enterprise, of the book. Baseline configuration guides (government/DoD networks use STIGs,) are essential, along with a configuration policy. Routers, switches, and other core network components should be compliant before being placed into a production/live environment.
Transport security
It is important when remotely configuring services and hardware over the network that all connections are encrypted and authenticated. Many organizations use the Zero Trust model, ensuring all network connections and actions must be validated.
SSH is recommended for accessing network appliances and services across the network.
Tip
When using SNMP for monitoring and management, it is important to ensure support for version 3 (v3), with full support for encryption and authentication.
Port security
Port security means restricting access to network ports using a combination of disabling unused network ports and deploying ACLs on network appliances.
On a layer 2 device, such as a Wi-Fi AP or switches, we can restrict access based on MAC addresses, and we can enable port security on a per-port basis.
There are two different approaches to restricting access to ports, as outlined here:
- Dynamic locking: You can specify the maximum number of MAC addresses that can be associated with a port. After the limit is reached, additional MAC addresses are not added to the CAM table; only the frames with allowable-source MAC addresses are forwarded.
Cisco refers to these dynamic addresses as sticky secure MAC addresses.
Figure 1.30 shows a MAC filter on a wireless AP:

Figure 1.30 – Wireless ACL
Restrictions can be implemented using either the whitelisting or blacklisting of MAC addresses.
Route protection
It is important to ensure network traffic flow is protected. Routers will send neighbors route updates using common dynamic routing protocols. If these routes are poisoned or tampered with, this could allow an attacker to route all traffic through an MITM exploit, sniffing all network traffic. Data could be sent through an endless series of loops, causing a DoS exploit. To prevent these types of attacks, we should ensure we adopt the following practices:
- Network devices are configured using an approved baseline.
- Routing updates should only be accepted after a secure authentication handshake.
- We should avoid the use of less secure routing protocols (such as RIP).
- Disable unnecessary management interfaces.
Distributed DoS protection
Distributed DoS (DDoS) attacks can cause major availability issues for an enterprise, often resulting in costly outages and disaffected customers. Recent attacks have seen traffic volumes of over 2.5 terabytes per second (Tbps) directed at a target organization. In 2017, Google was targeted in an attack that resulted in spoofed Domain Name System (DNS) requests being sent to 180,000 DNS servers. The resulting traffic was directed at Google infrastructure services. The following screenshot shows high levels of ingress traffic:

Figure 1.31 – DDoS attack traffic
DDoS mitigation is used to describe the process of guarding applications or networks against a DDoS attack. We can configure rules on our edge routers or work with our ISP to deliver this mitigation.
ISPs will incorporate these services into the services that their customers are using, or this may be an additional chargeable service.
Remotely triggered black hole
Remotely triggered black hole (RTBH) is a technique documented in IETF RFCs 5635 and 3882. RTBH filtering is a popular and effective technique for the mitigation of DoS attacks.
Often, a DDoS attack will overwhelm security devices on the enterprise perimeter. To thwart this type of attack, the customer will have an arrangement with their ISP. When a threshold is reached, a rule is triggered that sends an authorized route update to the ISP routers. The rule will automatically drop all traffic intended for the customer's internet-facing service. The ISP can then begin to identify the attack and look to block the malicious traffic. When this is done, the normal routing will be put back in place. The process is illustrated in the following diagram:

Figure 1.32 – RTBH
Blackhole used for DDOS mititigation can also be referred to as sinkholes.
Security zones
It is important to separate out network assets and services to provide the required levels of security. There will be regulatory requirements for critical infrastructure and SCADA networks. BUs may need to be on separate networks, while internet-facing servers must be placed in perimeter-based networks. Segmentation of networks makes it difficult for an attacker to gain a foothold on one compromised system and use lateral movement through the network.
Consider the following points when segmenting networks:
- Keep critical systems separate from general systems and each other if non-related.
- Limit and monitor access to assets.
- Keep an up-to-date list of personnel authorized to access critical assets.
- Train staff to err on the side of caution when dealing with access to critical assets.
- Consider air gaps when dealing with equipment supporting critical infrastructure (nuclear plant/petrochemical plant).
DMZ
A DMZ is like a border area between two nations where we do not trust our neighbor 100%. You are stopped at a checkpoint and if you are deemed to be a security risk, you are turned away. In the world of networking, we must use a combination of security techniques to implement this untrusted zone. Typically, an enterprise will create a zone using back-to-back firewalls. The assets in the zone will be accessed by users who cannot all be fully vetted or trusted.
The assets in the DMZ must be best prepared for hostile activity, and we may need to place SMTP gateways, DNS servers, and web and FTP servers into this network. It is imperative that these systems are hardened and do not run any unnecessary services.
Figure 1.33 provides an overview of a DMZ:

Figure 1.33 – DMZ network zone
A DMZ network can also be referred to as a screened subnet.
Summary
We have gained an understanding of security requirements, to ensure an appropriate, secure network architecture for a new or existing network. We have looked at solutions to provide the appropriate authentication and authorization controls.
We've studied how we can build security layers to allow access to information systems from trusted devices, outside of the enterprise network. You have seen a wide range of devices, including smartphones, laptops, tablets, and IoT devices, that must be secured on a network.
We have gained knowledge and an understanding of regulatory or industry compliance needs for strict network segmentation between processes and BUs
In this chapter, you have gained the following skills:
- Identification of the purpose of physical and virtual network and security devices
- Implementation of application- and protocol-aware technologies
- Planning for advanced network design
- Deploying the most appropriate network management and monitoring tools
- Advanced configuration of network devices
- Planning and implementing appropriate network security zones
These skills will be useful in the following chapters as we look to manage hybrid networks using cloud and virtual data centers.
Questions
Here are a few questions to test your understanding of the chapter:
- Which is the security module that would store an e-commerce server's private key?
- DLP
- HSM
- DPI
- 802.1x
- How can I mitigate the threat of data leakage?
- Through DLP
- Through HSM
- Through DPI
- Through 802.1x
- What type of IDS would I be using if I needed to update my definition files?
- Anomaly
- Behavior
- Heuristics
- Signature
- What is the purpose of iptables on a host computer?
- Routing
- Firewall
- Switching
- Encryption
- Which protocol would be used to manage a router securely from a technician's laptop?
- Telnet
- RDP
- SSH
- FTP
- How should I protect my management interface on a switch when I need to configure it remotely? Choose two answers.
- OSPF
- OOB management
- Strong password
- RIP v2
- What is an Ethernet standard for port access protocol, used for protecting networks via authentication?
- 802.11
- 802.3
- 802.1x
- d) 802.5
- What type of connectivity will allow key personnel to maintain communication with one another and key network resources when the main network is under attack?
- OOB
- Teams
- VNC
- What is a disadvantage when using a virtual desktop infrastructure (VDI)?
- Reliance on networks
- Better use of hardware resources
- Enhanced security
- Standard operating environment (SOE)
- What is used when my contractors use a tablet or thin client to access a Windows 10 desktop in my data center?
- OOB
- MDM
- VDI
- SSH
- What type of routing will help to mitigate a DDoS attack?
- OSPF
- RTBH
- RIP
- EIGRP
- What is it when SOC staff are failing to respond to alerts due to excessive levels of alerts?
- False positive
- Alert fatigue
- False negative
- True positive
- What will I need to support on my network device in order to forward truncated network traffic to a network monitoring tool?
- NetFlow
- sFlow
- SIEM
- System Logging Protocol (Syslog)
- What type of security would I use on my layer 2 switch to isolate the finance network from the development network?
- VPN
- IPsec
- VLAN
- RTBH
- What type of servers would the security team place on the DMZ network?
- Web Application server
- SMTP Gateway
- Intranet File Server
- Finance Department Payoll Server
- What type of security label would CISA assign to the chemical sector and communications sector?
- Regulated industry
- Protected infrastructure
- SCADA
- Critical infrastructure
- What will protect my Wi-Fi network against common threats, including evil-twin/rogue APs and DDoS?
- 802.1x
- Host-based IPS (HIPS)
- Firewall
- WIPS
- What should I configure on mobile users' laptop computers to ensure they will not be vulnerable to sniffing/eavesdropping when accessing the hotel's Wi-Fi network?
- Anti-malware
- Shielding
- Cable locks
- VPN
- Which edge security appliance should be recommended for an organization that has no dedicated security team and needs multiple security protection functions?
- Router
- WAF
- UTM
- DLP
- What should be used to connect a remote government agency across public networks (note that it needs to support the NSA suite of encryption protocols)?
- VPN
- HAIPE
- VLAN
- Protected distribution
Case study
You are employed as chief information security officer (CISO) for MORD Motor Cars U.K. You are meeting with the network team to discuss the proposed plan for the new data center. A new customer-facing e-commerce site will be run from a brand-new office and data center in Coventry, United Kingdom (UK).
The data center will also allow collaboration with a Chinese manufacturing company, through the addition of business-to-business (B2B) portals.
Place each device in the position that will offer the best security for the network. For bonus points, which ports need to be opened on the firewall?
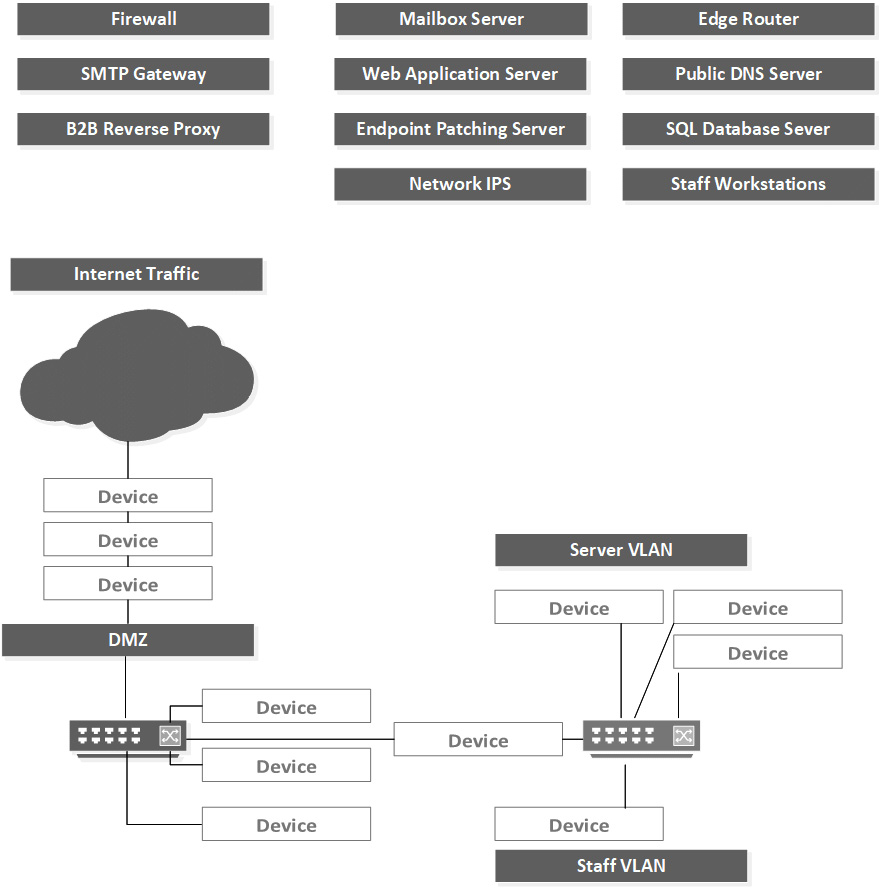
Figure 1.34 – Case study
Answers
- B
- A
- D
- B
- C
- B and C
- C
- B
- A
- C
- B
- B
- B
- C
- A and B
- D
- D
- D
- C
- B
Case study answer
The following placement will ensure a strong security posture for our network, although there are additional controls that would further enhance the organization's security, such as DLP, SIEM, and DNS Security Extensions (DNSSEC):

Figure 1.35 – Case study (answer)
