Chapter 9: Enterprise Mobility and Endpoint Security Controls
In a large enterprise, there is a business need for flexibility and mobility, but it is vitally important to address the risks, in terms of cybersecurity. Many business solutions comprise heterogeneous workloads on the server side and have to deal with a large number of end devices. These can include traditional desktop computers, laptops, tablets, handheld devices, and wearable technology. We need to assess the security of these devices, choose the appropriate technologies that the enterprise should adopt, and ensure that we can provide the necessary attestation that they do not present unacceptable business risks. There are security requirements to ensure that deployed system images are built from a validated secure template. Services should only be enabled if there is a business need for them. There is also the challenge of providing network access to a variety of mobile devices, including personal devices that are Wi-Fi enabled. Compensating controls should be deployed to offer additional protection – for example, Firewalls, Endpoint Detection and Response (EDR) plans, and antivirus tools.
In this chapter, we will learn about the tools and techniques needed to secure our endpoint devices. We will study the following topics:
- Implementing enterprise mobility management
- Security considerations for mobility management
- Implementing endpoint security controls
- Deploying host hardening
- Understanding endpoint security software
Implementing enterprise mobility management
One of the challenges of supporting devices in a hybrid network is the fact that the traditional network perimeter has been moved, so there is no longer a fixed enterprise boundary – in other words, users are accessing information systems from outside the enterprise. In many cases, information systems can be managed by third parties such as cloud providers. We call this phenomenon de-perimeterization.
Enterprise mobility management is the process of ensuring that mobile devices comply with the enterprise security policy. An enterprise will have the challenge of supporting mobile users, home/remote working setups, and personal computing devices that are not managed using traditional on-premises controls. We must accept that the business will have a need for this hybrid approach, but we also must understand the controls needed to protect the business from the loss, theft, and exfiltration of valuable business data. To ease the administration of security controls, we should choose vendor solutions that allow enterprise-owned and personal devices to be managed with a single-enterprise toolset, often referred to as a single pane of glass. In this section, we will look at the security features that need to be managed in this situation.
Managed configurations
There are many configuration settings available on the typical operating system, no matter who the vendor is. Without the proper management of these settings, devices that access corporate data will present a security risk. In the following subsections, we will take a look at some of the available configuration options.
Application control
It is important that we can control applications that are installed in the enterprise workspace – that is, every application should be justified by a business need. When users have access to the Google Play Store, Apple App Store, or Microsoft Store, they have the option to install hundreds of applications. Applications often have multiple configuration options, such as access to contacts information or access to location data. These settings can be controlled by using mobile application management (MAM) tools, deployment scripts, or Microsoft Group Policy Objects (GPOs). To allow for some flexibility in our application control, we can enable containerization for enterprise applications and data. Many vendors offer solutions that allow an organization to host a customized or restricted list of applications on their own company-branded portal. Figure 9.1 shows a user view of the Microsoft Store with Trainingpartners company branding:

Figure 9.1 – A restricted Microsoft Store application
Normally, a Windows user can choose from hundreds of available applications to install on their devices. But with the restricted view, this can be controlled. If we only allow devices to have access to an approved subset of application store programs, we can reduce our security footprint.
Passwords
At a minimum, we should enable screen locks and a minimum password length (based on company standards). This is to ensure that the data on the device will not be accessible if the device is lost or stolen.
Multi-factor authentication requirements
Passwords alone are not always considered to be adequate security for enterprise mobile devices. We may choose to enable additional authentication factors, such as one-time passwords (OTPs) using hardware tokens or mobile authenticator applications. Another useful authentication option for mobile devices is to use built-in biometric readers. Biometric authentication can include reading fingerprints, facial recognition, voice authentication, and iris scans. Many devices come with card reader functionality, making it easier to implement smart cards for multi-factor authentication (MFA). Microsoft also supports secure tokens in the form of a secure USB key, which provides the same functionality as a smart card. Smart cards and USB keys are considered a form of token-based authentication.
Figure 9.2 displays some additional sign-in options for Windows:
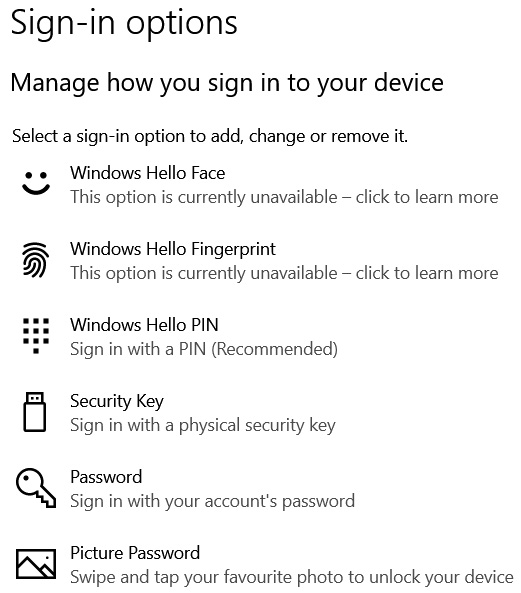
Figure 9.2 – MFA authentication methods on Windows
MFA adds another line of defense in cases where a password could be compromised.
Patch repositories
In order to offer the best levels of protection, it is important to access the latest patches for supported end devices and ensure that they are deployed in a timely fashion. Failure to implement patches will result in vulnerabilities that could have been mitigated. Additionally, not installing the latest patches may render a device non-compliant, and the user may not be able to access company resources until the device is updated and made compliant.
Firmware over-the-air (FOTA)
For mobile operating systems such as Android and Apple iOS, it is important that firmware updates are downloaded and installed when they become available. These updates add functionality to the device, but more importantly, they add security features and updates. It is important to control this process by allowing updates only over approved cellular networks.
Remote wipe options
It is important to render enterprise data unrecoverable by initiating a remote wipe process, when a device has been reported as missing or stolen. It is possible that this instruction will not be received by the mobile device management (MDM) agent due to a lack of cellular or network signal. Figure 9.3 shows some of the remote wipe options available for a lost or stolen mobile device:
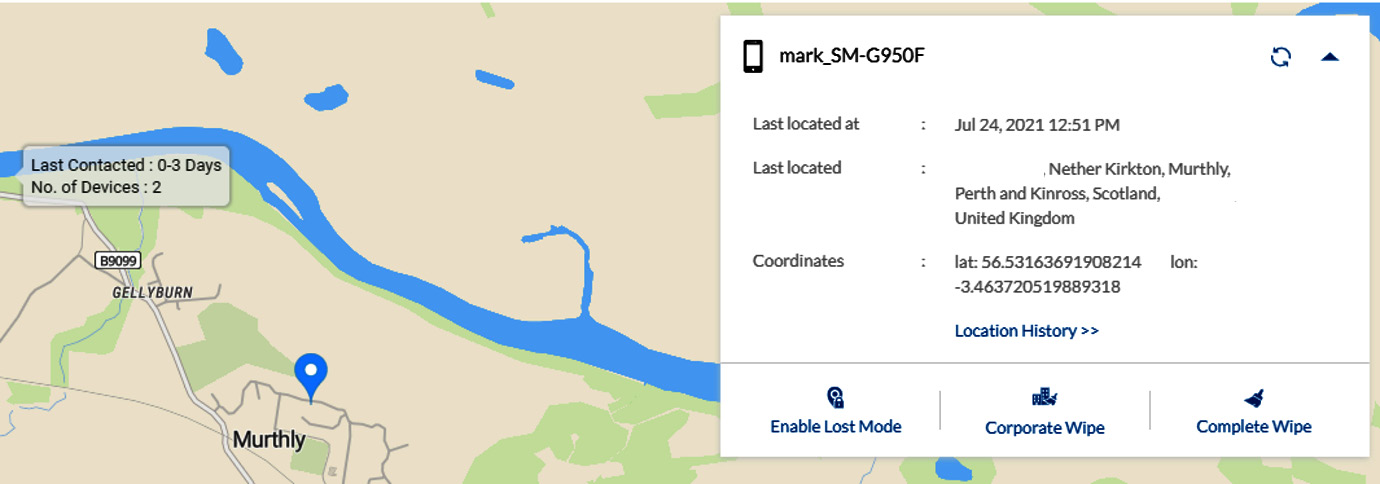
Figure 9.3 – Remote wipe options
For personal devices, we may only need the option for a corporate wipe. In Figure 9.3 we see the options to secure an Android smartphone.
Wi-Fi
Wi-Fi is the primary connection type for most mobile devices, although it is also commonplace to access 4G+ and 5G cellular networks at high speed with limitless data plans. In both instances, we should look to secure these links.
Wi-Fi protected access (WPA2/3)
WPA2 offers increased security over the older options of Wireless Encryption Privacy (WEP) and the Wireless Protected Access (WPA) Temporal Key Integrity Protocol (TKIP). It supports the Advanced Encryption Standard (AES), offering a greater level of security than the older protocols. WPA3 was introduced in 2018 and offers additional levels of security. WPA3 supports the use of 256 bit AES encryption and also secures access to the network if we cannot use 802.1x and RADIUS. The previous Wi-Fi implementations use pre-shared keys (PSKs), which are vulnerable to password cracking and brute force attacks. WPA3 uses Simultaneous Authentication of Equals (SAE) instead of PSKs – this limits the number allowed of password attempts and uses additional security protection methods.
Device certificates
It is common for security certificates to be distributed to users and devices for a variety of purposes. We can use certificates to gain trusted access to the network using 802.1X security. There are many security applications that also require the use of certificates, such as IPsec-based virtual private networks (VPNs), the S/MIME standard, and Pretty Good Privacy (PGP).
To automate the deployment of certificates, we can use the Simple Certificate Enrolment Protocol (SCEP). This is supported in most MDM solutions. Figure 9.4 shows the SCEP enrolment process:
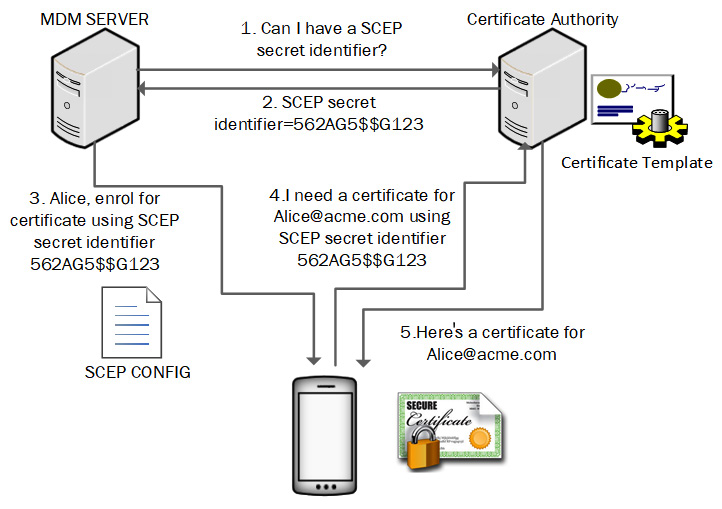
Figure 9.4 – The SCEP enrolment process
If we control the deployment of certificates, it is less likely that users will be able to install certificates from untrustworthy certificate authorities.
Device profiles
To automate common settings on mobile devices, a profile with a set of configuration objects can be deployed to the devices. Common profiles can include settings for Wi-Fi, VPNs, and many more. Figure 9.5 displays some available settings when deploying device configuration profiles:
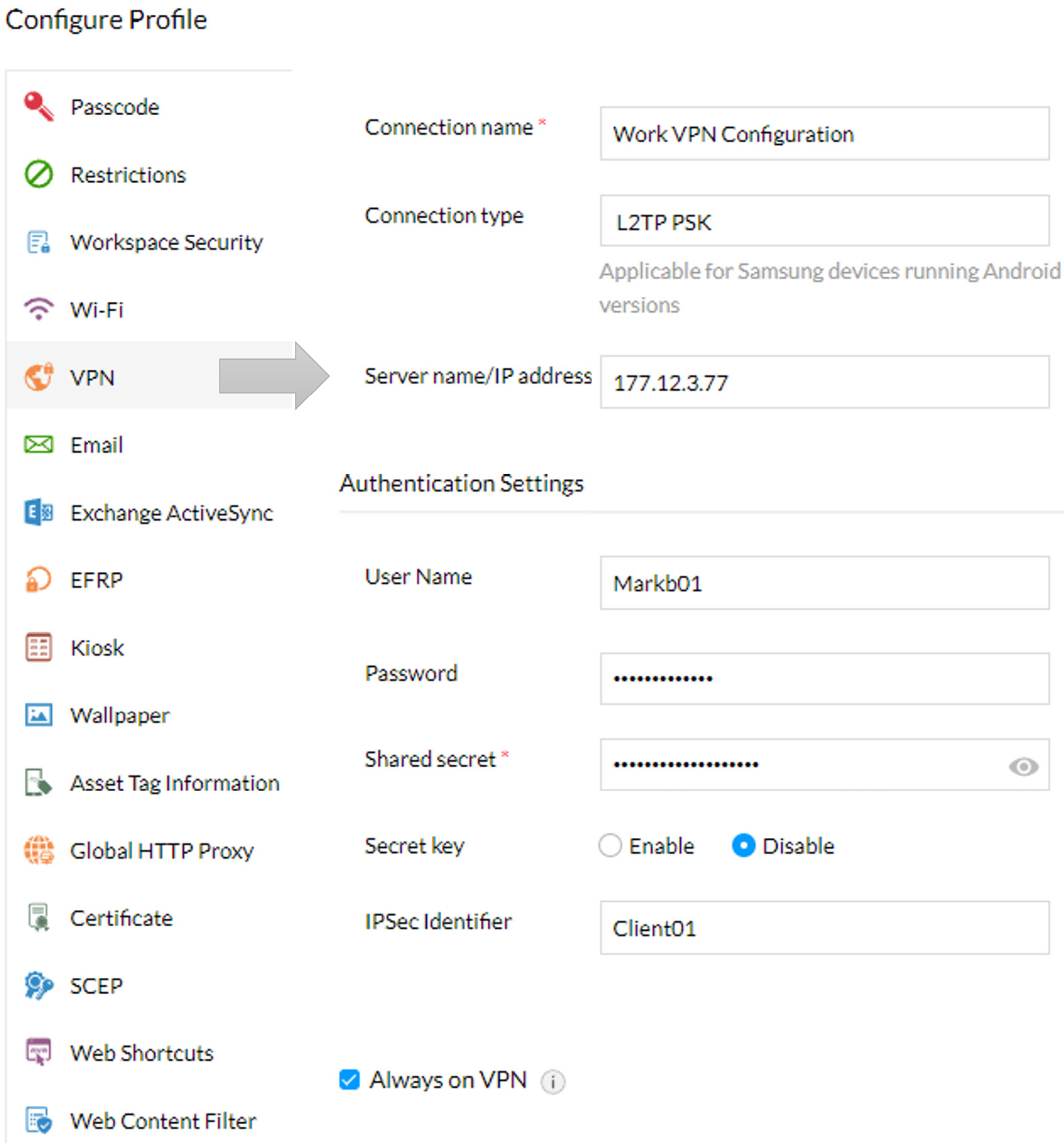
Figure 9.5 – An example VPN device configuration profile
When there are many settings to manage, a profile is a convenient way to deploy custom configuration settings. In Figure 9.5 we are deploying a VPN profile to Android devices.
Bluetooth
Bluetooth is a relatively short-range radio frequency. Class 2 Bluetooth (which is most common for consumer devices) transmits at 2.5 mW and has a range of around 10 meters. It allows data to be sent wirelessly with no encryption. This means wireless headsets could allow users to attend a secure web conference but a wireless listening device could be used to eavesdrop on the conference. It is common to restrict the use of Bluetooth in these situations.
Near-field communication
Near-field communication (NFC) operates at low speeds over short distances (up to 4 cm). It can be used to transfer data – such as configuration data or print jobs – to an NFC-enabled printer. It is commonly used in the wireless payment systems for Apple Pay and Google Pay. Once a user has unlocked a mobile device, then NFC-enabled applications may transfer data without any user verification. This function could lead to fraudulent payment transactions (currently the United Kingdom allows up to £100 to be transferred using contactless payment). It could also allow confidential data to be transferred.
Peripherals
Mobile devices can support extensibility through SD and MicroSD cards or USB On-The-Go (OTG). This allows for data transfer and connectivity using USB devices.
Geofencing
One effective way to control the functionality of mobile devices is to use GPS tracking to locate devices and restrict functions based upon the proximity of the device to a site of interest. So, we could map out the coordinates of a secure site and create a geofence. When devices are inside the geofence, we can disable the devices' cameras and any recording capability, and when devices are outside the geofence, normal service can be restored. In case a company device is stolen, we can create conditions where the device is wiped of all its enterprise data when it is taken outside the geofence.
VPN settings
VPN settings can be configured by deploying a VPN profile to a mobile device. It is important to ensure confidentiality of business data when company employees are outside the workplace. An always-on profile ensures that the device will always connect through the secure VPN. Implementing a full tunnel configuration will ensure all applications and browser activity is routed through the company network. This configuration will make sure all security protocols can be applied. Figure 9.6 shows an example of a VPN client using a full tunnel VPN:
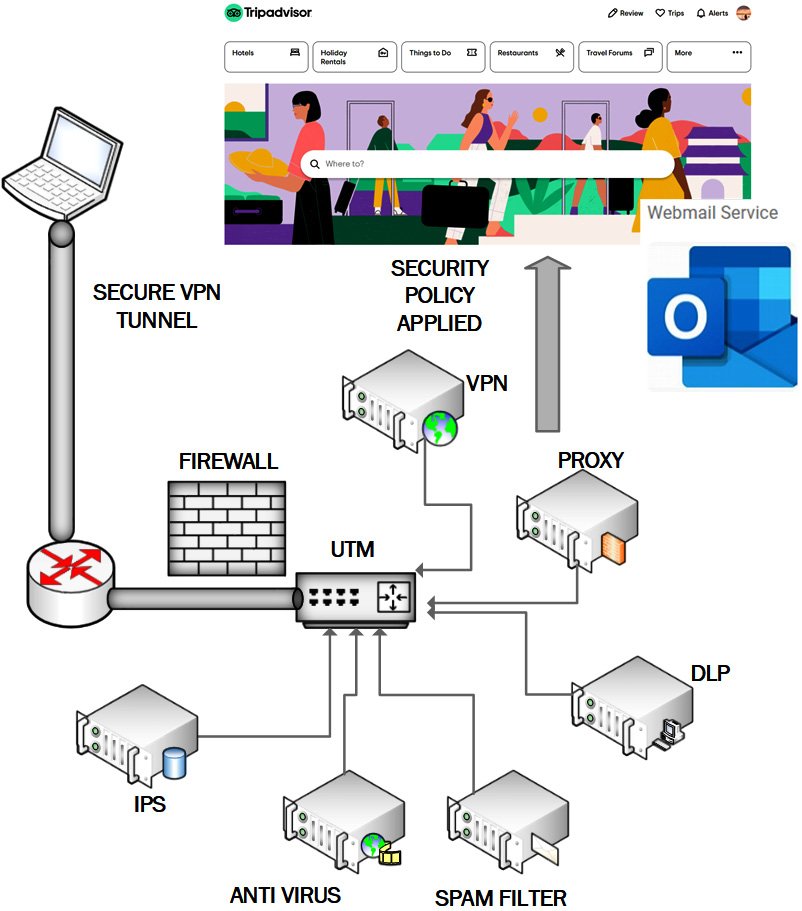
Figure 9.6 – A VPN client connecting through a full tunnel configuration
Without this configuration, the device can connect directly to external applications without the appropriate security policies being applied.
Geotagging
An organization should consider the security of applications that use geotagging. For example, users could install a fitness application on a mobile phone that automatically uploads their activity (complete with maps) to social media. This is quite common when you look at applications such as Strava or MapMyRun. In Figure 9.7, we can see the mapping feature on the Strava application:
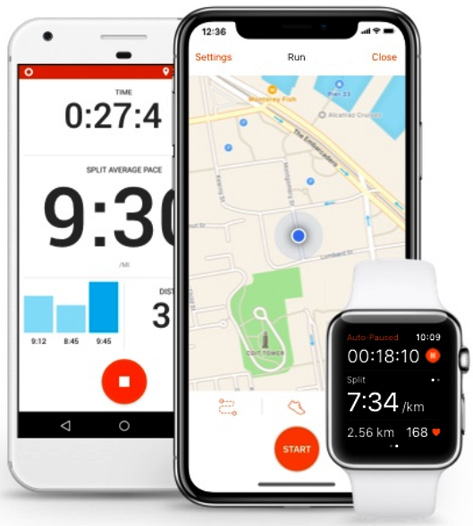
Figure 9.7 – The Strava mapping feature
If you allow other users to view your activities, then you may reveal sensitive details about your movements or reveal information regarding sensitive locations.
Full device encryption
It is important to secure enterprise data stored on mobile devices. At a minimum, we should enforce the use of screen lock and storage encryption (including for SD cards). If a password-enabled screen lock is not required, then access to the data may still be possible if the device is lost or stolen. If the mobile device contains removable storage, it should be encrypted, as the media may otherwise be readable when mounted on another piece of hardware.
It is important that the device is hardened against tampering so that any attempt to change the boot process will result in the data being unrecoverable.
Tethering
Because mobile data plans can be very affordable on cellular networks, it is common for users to use their mobile phones as a hotspot for their laptops. This presents a security risk when a laptop is plugged into the enterprise local area network (LAN), as the laptop can now bridge two networks.
Airplane mode
Mobile devices commonly have a setting that turns off all radio frequency channels (for example, airplane mode). This could be a useful configuration option to invoke when location-based security is a priority. Disabling radio frequency channels protects the device from network based threats. It also means the device cannot download security updates or be managed using Mobile Device Management (MDM).
Location services
Mobile operating systems often have privacy options associated with location services. If location services are enabled, then content providers can deliver more tailored information for users. Microsoft now includes a feature on Windows operating systems called News and Interests that delivers traffic reports, weather forecasts, and local news to devices based on their location. You may not want this location information to be available for all applications. We can restrict these features in the Microsoft privacy settings seen in Figure 9.8:
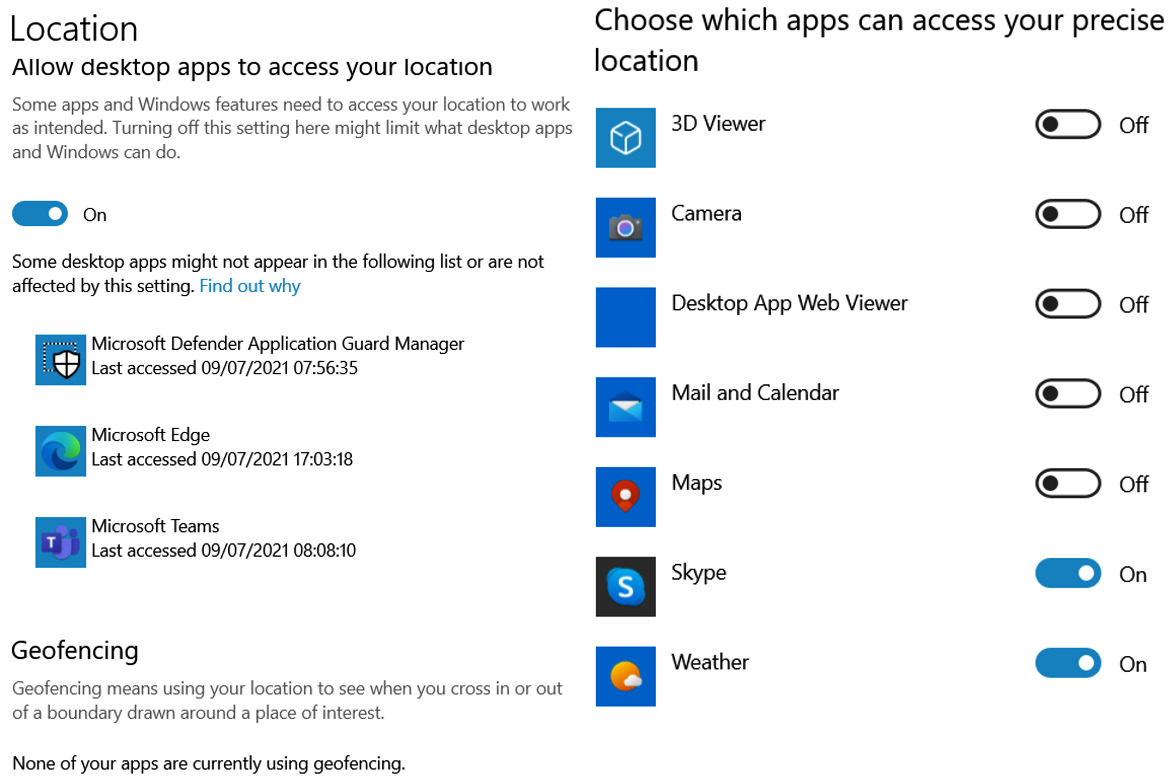
Figure 9.8 – The Microsoft location services privacy settings
Location sevices can also be useful when enforcing context based authentication. User and Entity Behavior Analytics UEBA can block suspicious authentication attempts from unusual locations. Impossible Time Travel can also be detected, where separate login attempts are not feasable based upon the time duration and location of the attempts.
DNS over HTTPS (DoH)
When using traditional Domain Name Services (DNS) for name queries, we are sending requests to a designated DNS server with no security – this means that every request and reply is sent in plaintext. This may reveal useful intelligence to an eavesdropper on a network segment. Many web browsers, including Edge and Chrome, allow configuration settings to be updated, allowing for secure TLS connections to be made to public DoH servers. In Figure 9.9, we can see the security settings for the Microsoft Edge browser:
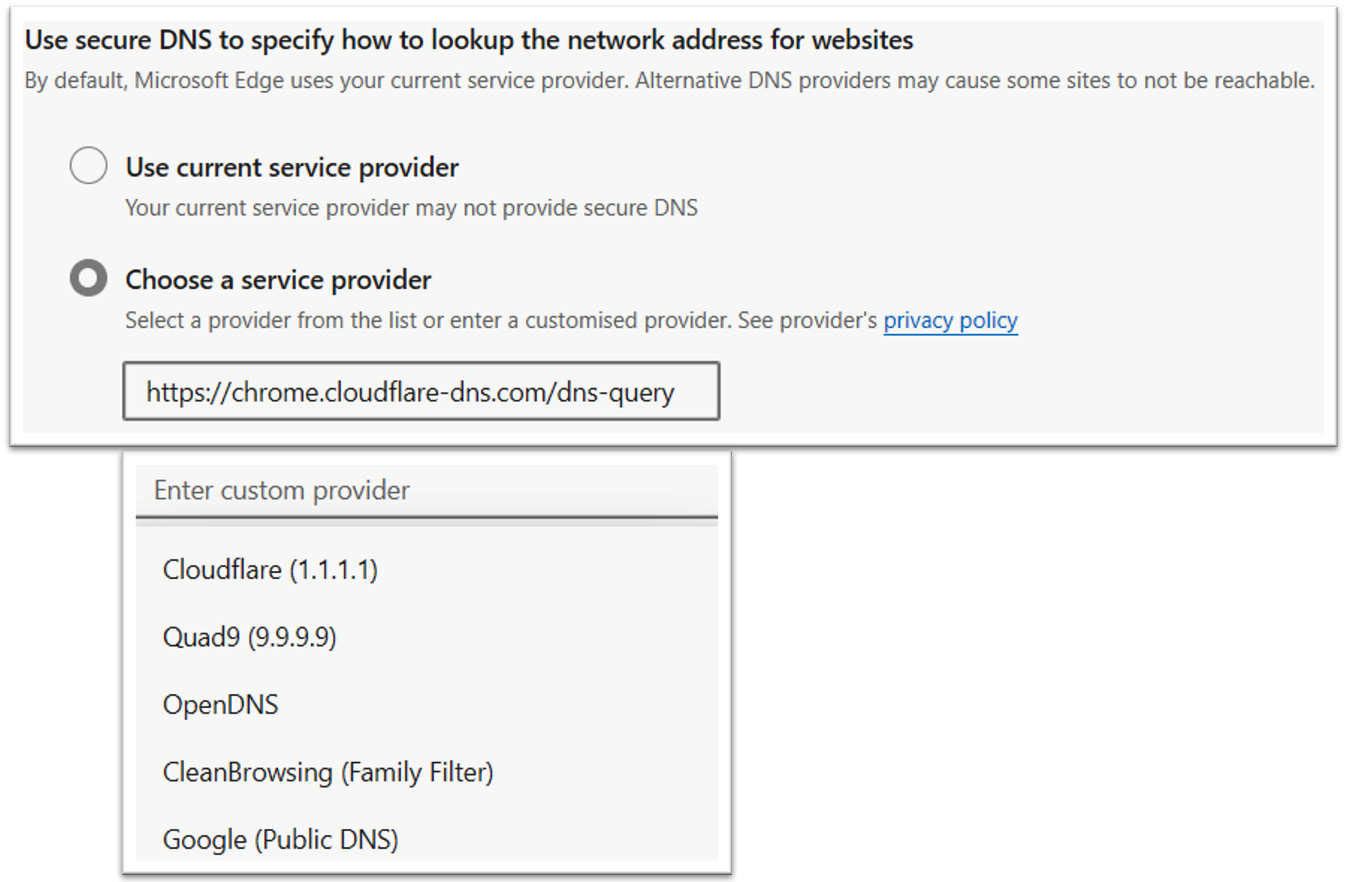
Figure 9.9 – The Microsoft Edge browser DoH settings
Another alternative is to use a secure VPN connection back to the enterprise network where we can safely send DNS queries to the enterprise DNS servers.
Custom DNS settings
Many ISPs may limit their customers' access to content by restricting and filtering DNS queries. This can also be an effective control for enterprise users by blocking name resolutions for certain websites. Users may find a workaround to these restrictions by using a custom DNS server that does not log any activity or block name resolution requests. By restricting access to these settings, we can ensure that all internet activity is controlled.
Deployment scenarios
There are many different scenarios that an organization may consider when deploying mobility management. For example, costs can be a driving factor and support issues may be important. But security and management will always be the priority when implementing MDM.
Bring your own device challenges
When users access enterprise data on a personal device, it can present many challenges for the organization. There is the issue of what devices the organization is willing to support. There are also many different versions of operating systems to support and also different hardware platforms. It is important to define a secure encrypted container on the device to hold corporate applications and data. We will need to define policies to secure any sensitive company data. It is also important to identify MDM tools that will enable the management of all the personal device types that will be supported.
Corporate-owned devices
When an organization is responsible for purchasing the mobile devices that will be used by employees, there can be much more control in selecting the operating systems and devices that best suit the organization's business needs.
Corporate-owned, personally enabled (COPE) devices
When a company allows users to access personal data using its devices, it is important to separate the business data and applications from the personal data. In the same way that we protect business data with bring your own device (BYOD) policies, we must use the same strategy with corporate-owned, personally enabled (COPE) devices. This means separating business data and personal data. MDM will be used to ensure that containerization is implemented.
Choose your own device (CYOD) challenges
Often, enterprise users are familiar with a particular technology and will be more engaged with the technology if it is a device or operating system that they find easy to use. The challenge for the enterprise is to allow users to have a degree of choice in the devices they use but to restrict the list of available devices to a manageable number. This will ensure that we only have to support a small number of hardware devices and operating systems. Android fragmentation is a term used to describe the proliferation of devices running many different versions of the Android operating system. There have been numerous versions of Android operating system releases (currently 19 versions at the end of 2021). The goal of the organization is to restrict the handsets and the operating systems that will be allowed to connect to the business network. This will help to reduce support complexity and will reduce the security footprint.
With mobility being a major consideration for most organizations, it is important to recognize the possible security implications when supporting end devices, operating systems, and applications. We will now investigate some of the security features and configurations that we can manage for mobile devices.
Security considerations for mobility management
Many security considerations arise when an enterprise wants to support a mobile workforce. Devices offer a wide range of features and functions that may represent a risk to the organization.
The unauthorized remote activation and deactivation of devices or features
While many devices support an array of security features, many of these can be deactivated – for example, the user may inadvertently disable or deactivate a security feature such as a daemon supporting an anti-malware application. This risk should be mitigated by using secure operating systems (such as Security-Enhanced Linux (SELinux) or Security-Enhanced Android (SEAndroid)) along with MDM.
Encrypted and unencrypted communication concerns
When we are supporting mobility, we should always identify the weakest links in a network. This means that if we harden the device using full device encryption (FDE), screen locks, and application whitelisting, we also need to ensure that network communication is secured. We should restrict the use of Bluetooth and also restrict Wi-Fi access to trusted WLANs.
Physical reconnaissance
Mobile devices can be used to gather intelligence. If we allow the use of camera, video, audio, and GPS functionality on mobile devices, a malicious user could capture accurate data about a site that could later be used in an attack. This device may belong to an insider threat actor or the data could be stolen from an unsecured mobile device.
Personal data theft
While the main focus of MDM is to protect business data, it is also important to protect a user's personal data. Personal data may include protected health information (PHI), personally identifiable information (PII), and other types of confidential data.
Health privacy
Many devices will support fitness applications that can store the medical records of users. Due to the COVID-19 pandemic, public health service tracking applications are also commonplace. In the United Kingdom, there are National Health Service (NHS) applications that can store a citizen's COVID-19 status and records of their immunization history. This data would be referred to as PHI in the United States. It is important that this type of data is held securely.
The implications of wearable devices
Wearable devices may have GPS tracking capabilities and they frequently store detailed personal information, including heart rates and blood pressure readings. The synchronization of data between the wearable device and an application on another system may also be a vulnerability. Many wearable devices may use low-powered Bluetooth or NFC to transfer data. Senitive data may be exposed as a result of unsecured data transmission.
The digital forensics of collected data
It is important to keep forensic toolkits and techniques updated, as new technologies, such as wearable technology, may be the target of attacks. It is important that we can access the storage and memory of mobile devices to search for indicators of compromise (IOCs).
Unauthorized application stores
The default settings on most mobile operating systems block access to sideloading applications. Sideloading involves the acquisition of an installation package from sources that are not approved – for example, Android APK or iOS IPA files can be installed directly, without the need to download them from the approved online store. This restriction can be circumvented by jailbreaking an iOS device or rooting an Android device.
When you jailbreak or root a device, you are modifying the vendor operating system to break away from the secure restricted settings that are in place by default. For example, on iOS, it is not possible to install applications from outside of the Apple App Store, so installing jailbreaking software will allow users to install applications and themes that have not been officially approved by Apple. Apple also provides developer licenses that allow the use of sideloading applications on an iOS device (this developer license currently costs $99 per year). There is also a free Apple Store application called Xcode that allows for sideloading when you have the application source code of the unapproved application.
Containerization
When we allow the personal use of mobile devices that will also access or store business data, we need to implement segmentation. Segmenting applications and data on mobile devices is referred to as containerization. On Samsung devices, there is a vendor-created container called Secure Folder. This can be managed using the Samsung Knox security tools, or it can be managed using third-party MDM tools. Currently, Knox is supported by Microsoft Endpoint Manager (previously Microsoft Intune), VMware AirWatch, Ivanti MobileIron, and many more. Figure 9.10 shows the Secure Folder application on a Samsung 9.0 device:

Figure 9.10 – Samsung Secure Folder
These applications and any business data are stored completely separately from the personal space on the device.
Original equipment manufacturer (OEM) and carrier differences
Many cellular operators will provide their customers with customized versions of popular operating systems and will lock the mobile device into their network offerings. When you purchase a device that is not locked into a cellular provider, the user has more flexibility to choose between providers simply by changing the subscriber identity module (SIM) card. This offers the opportunity for the user to use any cellular operator, including operators in other countries. For example if a company buys cellular handsets from T-Mobile, then they will only allow the handsets to work on T-Mobile cellular networks.
Supply chain issues
There have been many instances of security breaches due to the installation of default applications by vendors that turned out to be malicious. Adups (software used to monitor user behavior) was installed, by default, on a variety of devices using the Android operating system. This software allowed for backdoor access to call logs, contact lists, SMS messages, and location tracking. For more information, see the report at https://tinyurl.com/adupshack.
The use of an eFuse
An eFuse can be useful when for protecting the integrity of a mobile device. An eFuse will trip under certain conditions. The main reasons for the tripping of an eFuse are normally an unsigned bootloader, an unsigned kernel, or unsigned scripts that might be running. In these circumstances, the eFuse will disable access to the secure container. This also updates the security status of the device from official to untrusted. An eFuse is like a regular electrical fuse that protects electrical devices. In this case it is embedded directly into the firmware. For more details on eFuse, see the following URL: https://tinyurl.com/samsungefuse.
Implementing endpoint security controls
It is important to understand all the risks that endpoints pose to an organization and implement the appropriate controls to mitigate these risks. These controls can include choosing trusted hardware and software platforms and utilizing attestation services to ensure the platforms have a strong security posture. We must also protect our systems from unauthorized changes using tools such as host intrusion detection systems (HIDSes) and host intrusion prevention systems (HIPSes). In addition, endpoint detection and response (EDR) software can help an organization where there are threats that are sophisticated and currently undocumented (such as zero day exploits). Now, we will investigate a number of techniques to secure endpoint devices.
Hardening techniques
It is important to recognize that there are many ways to strengthen the security posture of devices. In this section, we will investigate some of the hardening techniques available.
Removing unneeded services
Running unneeded services on a computer system offers additional connection opportunities for malicious actors such as malware (remote access trojans (RATs) and worms). To reduce the overall security footprint of a system we should disable these services based on the business needs of the system. For example, an internet-facing public web server will not need to run file and print sharing services, although this might be a requirement when the server is deployed as a departmental internal server.
Disabling unused accounts
It is important to identify built-in system or user accounts that may present a security risk. Examples of risks could include guest accounts and vendor-created support accounts. There should be a security policy that ensures this becomes an automated process. In Figure 9.11, we can see which default local accounts have been disabled on a Windows 10 host computer.

Figure 9.11 – Disabled default Windows accounts
When an account does not need to be used in an information system, it should be disabled.
Images and templates
To assist with the goal of implementing a strong security posture for end devices, a customized hardened operating system image is a good building block for security. On United States Department of Defense (DoD) networks, there is a Windows operating system build image called the Windows Secure Host Baseline (SHB). This ensures the deployment is hardened by default. In this instance, there are over 200 specific security requirements that must be enabled by default. All the tools needed to create an operating system build image and verify it can be found in the GitHub repository at https://tinyurl.com/windowsDoDshb.
Removing end-of-life devices (obsolescence management)
When a device is no longer considered serviceable or represents too big a risk to the enterprise, it should be decommissioned. It is important to ensure, when removing a device, that this action does not weaken the security posture of the network. If it is a security appliance, then it should be replaced.
Removing end-of-support devices
When a device can no longer be protected through vendor support and patching then it will become a vulnerability. For example, Microsoft withdrew support for the Windows 7 operating system in January 2020. In July 2021, there were 135 vulnerabilities listed as Common Vulnerabilities and Exposures (CVEs) affecting Windows 7. As there is no automated patching offered for end-of-support devices or operating systems, vulnerabilities often remain unmitigated.
Local drive encryption
Managed FDE will provide protection for valuable business data in the case of the loss or theft of mobile devices. BitLocker is the built-in FDE option for Windows operating systems.
Enabling no execute (NX)/execute never (XN) bit
For any system hosting applications that may be vulnerable to attacks against the system memory (Random Access Memory (RAM)), it is important to ensure that built-in security is enabled to offer protection against this attack vector. No execute (NX) is a security feature supported by 64 bit AMD CPUs, while execute never (XN) is supported by 64 bit Intel CPUs. These features are designed to prevent the execution of code in areas of memory assigned for the storage of data. It is a design that makes it difficult for an attacker to cause a buffer overflow when trying to re-purpose the memory location for the execution of arbitrary commands. Figure 9.12 shows how this setting is enabled by default on Windows in a security feature called Data Execution Protection (DEP).
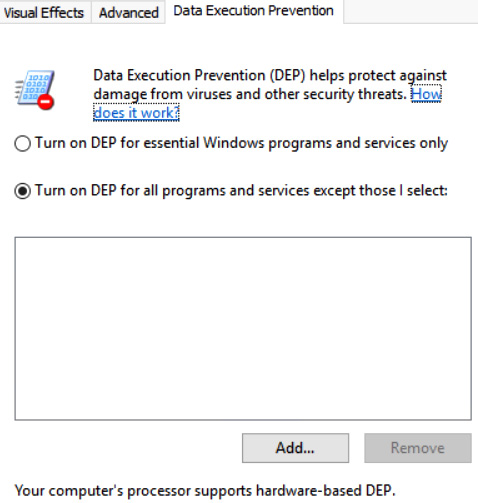
Figure 9.12 – The Microsoft DEP feature
On Windows servers, this setting is enabled for all Windows applications and services. ARM RISC processor chips support the XN bit. For more information see the following URL: https://tinyurl.com/nxdep.
Disabling central processing unit (CPU) virtualization support
The setting for virtualization support is normally found in the firmware settings of the endpoint device. If this is enabled, it allows for virtual images to be launched in a hypervisor. This is not something that is normally required for the majority of user desktops. If enabled, it may allow a user to run unauthorized applications on a virtual machine.
Secure encrypted enclaves and AMD Secure Memory Encryption
Many processors now have built-in support for the encryption of memory in use. This means that the contents of the RAM and the CPU memory itself can be secured. AMD CPUs support a feature called Secure Memory Encryption (SME). This uses AES 128 bit encryption and creates an ephemeral key at boot time. When support is enabled in the system firmware/BIOS, the feature can run transparently with most operating systems (there is no additional requirement for any coding within the operating system). Software applications can use this support to encrypt and decrypt pages of memory.
Shell restrictions
To limit the ability of a user to access command shell tools and utilities, it is common to block access to the shell itself or to limit the commands that can be accessed within the shell. On Windows operating systems, it is common practice to block access to the Command Prompt (CMD) and PowerShell interfaces for standard users. This is not really an option for Linux and Unix systems because most of the functionality of these operating systems is accessed outside of the graphical user interface (GUI). Common shells used on Linux include Bash and KornShell. In Figure 9.13, we have created a new user account with a restricted shell by using the -s switch command:
Figure 9.13 – Implementing a restricted shell
There are a limited number of commands available within the restricted shell. The user cannot call up any commands that exist in other directories or use powerful administrator utilities.
Address space layout randomization
Address space layout randomization (ASLR) is designed to protect computer systems from attacks against memory. By enabling this feature, it prevents an attacker from being able to use memory addressing to predict where applications will be located. For example, an attacker may attempt to launch a buffer overflow attack followed by a call to a memory location where they expect a shell to be running. In ASLR, the running applications will always be allocated random memory locations, so this mitigates this type of attack.
In Figure 9.14, we can see the default settings for a Windows 10 client:
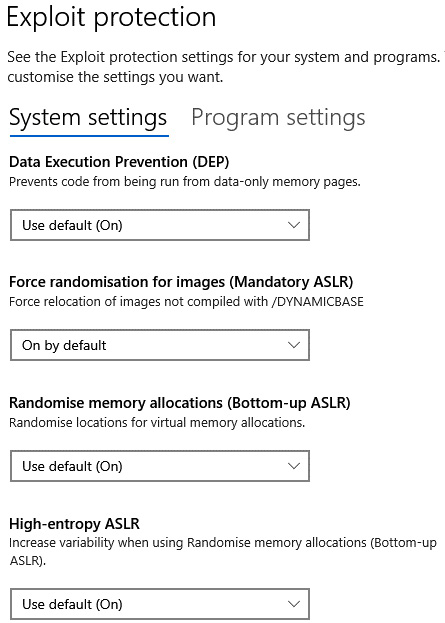
Figure 9.14 – Microsoft Windows ASLR settings
This feature is supported on most operating systems, including Linux, Microsoft Windows, and macOS.
Patching
It is important to identify all of our assets and ensure we have the automated patching of these devices enabled. If we cannot deploy vendor patches, we risk the possibility of vulnerabilities leading to data loss or we might encounter availability issues. Patching should be planned to avoid the potential of these disruptions and availability issues. Ideally, we would fully test the effects of operating system or software application patches in a test/staging area before deploying them into production. Figure 9.15 shows a screenshot from ManageEngine Patch Manager Plus:
Figure 9.15 – ManageEngine Patch Manager Plus
It is important to choose patch management products that support heterogeneous environments (mixture of host operating systems). For more details on the ManageEngine product see the following URL: https://tinyurl.com/MEpatchmanager.
Firmware
It is important to update embedded operating system code, as this could be vulnerable to attacks if not kept up to date. For example, Cisco IOS has several vulnerabilities posted for potential attacks against its Session Initiation Protocol (SIP) that can cause a Denial of Service (DoS) condition. CVE-2008-3799 documents a cybersecurity vulnerability, where an attack can cause a memory leak, eventually resulting in resource exhaustion. SIP is used with Voice over Internet Protocol (VOIP), it is used to place a call to another subscriber. As many business-based telephony solutions have adopted this technology it is important to secure this important functionality.
Logging and monitoring of endpoint devices
The continuous monitoring of endpoint devices allows security professionals to be alerted to any discrepancies in configuration changes or anomalous activities relating to the devices. Figure 9.16 shows the health status for monitored endpoint devices using the ManageEngine MDM platform:
Figure 9.16 – Endpoint device monitoring
It is important to be alerted when devices do not comply with security policies or have been targeted by malware.
Mandatory access control
When we are looking for a high level of protection for operating systems, mandatory access control (MAC) can be used. Using this results in additional security controls being available to the operating systems. The controls, once enabled, enforce security settings. There are two examples of operating systems that support MAC, which we detail in the following subsections.
SELinux
SELinux was originally developed as a series of Linux security modules that were added as patches to the Linux operating systems. It was originally developed by the U.S. National Security Agency (NSA) but is now open source. It is incorporated into most Linux distributions. With most operating systems, file ownership is controlled through discretionary access control (DAC), which means the owner can set or change permissions on files and folders that they own. The root account normally also has the right to change the permissions on other users' files and folders, however, SELinux enforces MAC, which means changing other users' permissions will not work (as the system will override these changes).
SELinux has three main settings:
- Enforcing: In this setting, the SELinux security policy is enforced.
- Permissive: In this setting, SELinux prints warning messages instead of enforcing the security policy.
- Disabled: In this setting, no SELinux policy is loaded.
There are hundreds of possible enforcement settings. These are delivered via Boolean settings (that is, on/off options). To view all of the currently enforced settings, you can run getsebool -a from the Linux command shell.
Figure 9.17 shows the partial output of the preceding command for some SELinux enforcable settings:
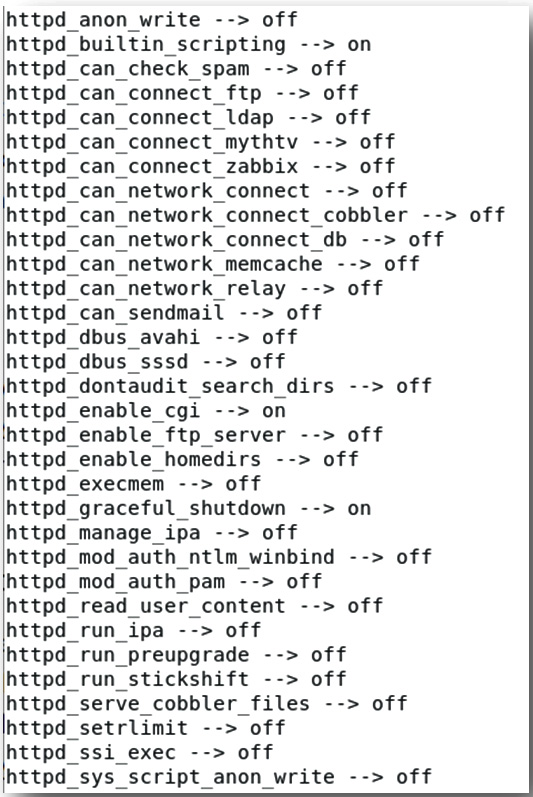
Figure 9.17 – SELinux enforcable settings
The output displayed in Figure 9.17 shows a subset of an SELinux security policy, this just lists some of the web application server settings.
Next, we will look at how Android uses Security-Enhanced Linux (SELinux) to enforce MAC on Android mobile devices.
Android Security-Enhanced Linux
The Android operating system adds security extensions by incorporating SELinux into the Android mobile operating system (sometimes referred to as SEAndroid). It was incorporated into Android version 4.4 and is based on the same security model as SELinux. There are many security controls available, including protecting privileged services/daemons from misuse. Applications must be run in a sandbox and there is an extensible policy available to add additional restrictions. Much of the security is included within the Kernel, but the use of middleware mandatory access control (MMAC) allows application privileges to be assigned during installation and at runtime. SEAndroid uses the enforcing mode as a default.
Many additional security enhancements for SEAndroid rely on hardware support to store measurements or certificates securely.
Trusted Platform Module technology
Many system boards have built-in support for a specific hardware security module (HSM) called a Trusted Platform Module (TPM). This secure module has crypto-processing capabilities and also provides for the secure storage of measurements or values. The TPM standard is a recognized standard (ISO/IEC 11889) and is supported by many hardware and software vendors. A TPM is typically used to ensure the integrity of an operating system platform. In the case of Microsoft BitLocker, if the recorded values are not consistent at boot time, then the boot process will halt. The values that are stored are called platform configuration registers (PCRs), and around six of these PCRs are normally used to attest that the platform has not been tampered with.
Figure 9.18 shows some of the typical values that can be stored. These values are stored as a cryptographic hash:

Figure 9.18 – PCR values
There are many additional value types that can be stored, such as software application versions or the current status of anti-virus updates.
Secure Boot
To ensure the integrity of operating systems, it has become a standard procedure to check the integrity of the bootloader needed to launch the installed operating system. Windows operating systems from Windows 8.0 onward have supported this feature. This requires a supported firmware interface ( that is, one following the Unified Extensible Firmware Interface (UEFI) specification) that comes with a pre-loaded security key. The boot files are signed using the pre-loaded key and then validated during the boot sequence. Systems sold with Microsoft Windows 10 pre-installed have Secure Boot enabled by default. Figure 9.19 shows the components required for Secure Boot:
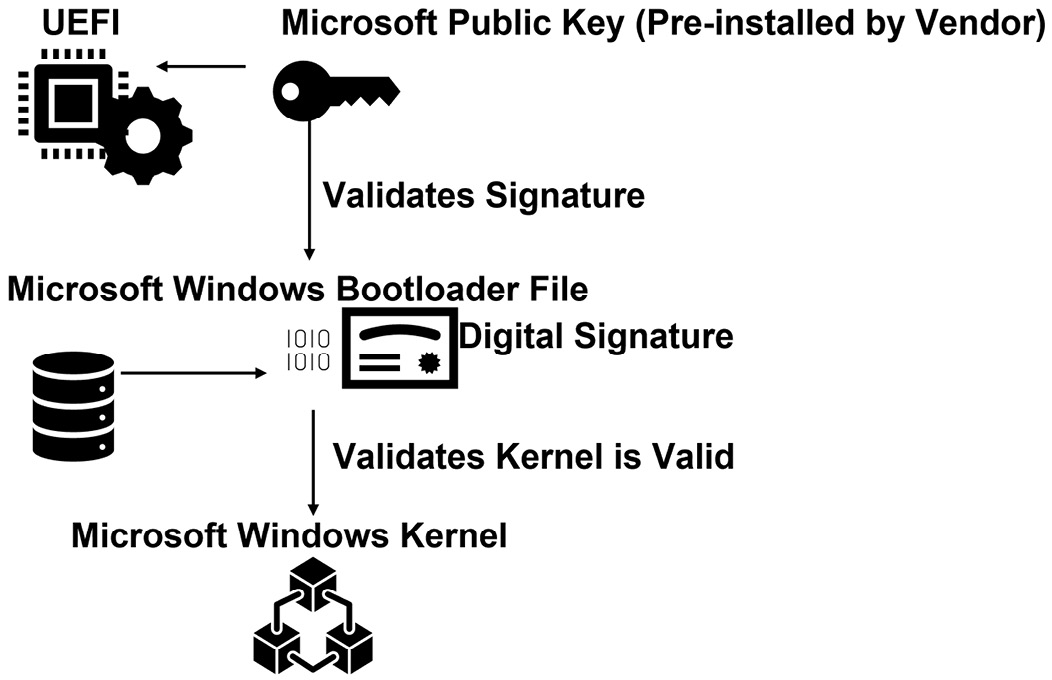
Figure 9.19 – The Microsoft Windows Secure Boot components
To add support for Linux Secure Boot, we would need to ensure there is a signed Linux bootloader. To do this, we could add the operating system vendor's public key into UEFI.
UEFI
UEFI has been the standard firmware to support PC systems since Windows 8.0 was released, in 2008. It offers many advantages over the previous option (the Basic Input Output System (BIOS)), including a mouse-driven graphical environment. UEFI allows for system checks and security processing to be carried out before launching the operating system. As operating systems launch quickly when installed on solid-state drives (SSDs), it is hard to press the correct function key quickly enough to access the menu. It is common to access the UEFI settings through the Windows Advanced Recovery options menu, within the operating system. Figure 9.20 shows the Windows menu used to access the UEFI settings:
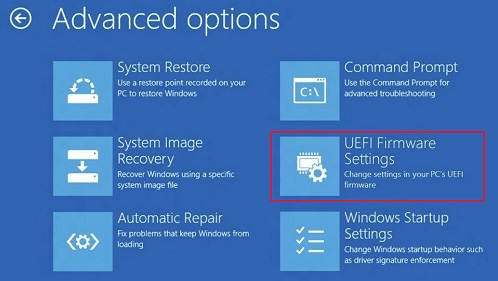
Figure 9.20 – The Windows UEFI menu
All modern business computers now support the UEFI firmware.
BIOS protection
The BIOS component has been standard within computing systems since the 1980s. It allows for a series of power-on self-tests (POSTs) and for configuration settings to be saved to the complementary metal-oxide semiconductor (CMOS), which needs a power supply or battery to retain settings. It offers little in the way of security, apart from allowing for passwords to protect the BIOS settings.
Attestation services
Attestation services allow for secure values to be forwarded from a hardware device to an attestation service. Microsoft supports a service called the Host Attestation Service within Azure Cloud Services. Once a device has been registered, the host TPM can be used to store values that cannot be tampered with. An example use of this service is ensuring that host operating systems are not running debugging tools as part of the host operating system. This is because debugging tools could allow attackers to gain access to local system memory and therefore access to confidential data.
Hardware security modules
A hardware security module (HSM) is an independent hardware device that supports crypto-processing capabilities and the secure storage of encryption keys. This can be a valuable addition to security when hosting applications that will need access to valuable private keys. E-commerce and banking websites will typically need to deploy HSMs. Most implementations are rack mounted appliances and allow for the secure storage of server keys within the data center.
Measured Boot
With mMeasured Boot, PCR values can be validated from the TPM. The values themselves are stored as cryptographic hashes. The hashes form a blockchain, which means a number of values can be combined into a single hash value. Figure 9.21 shows the hash chaining function:
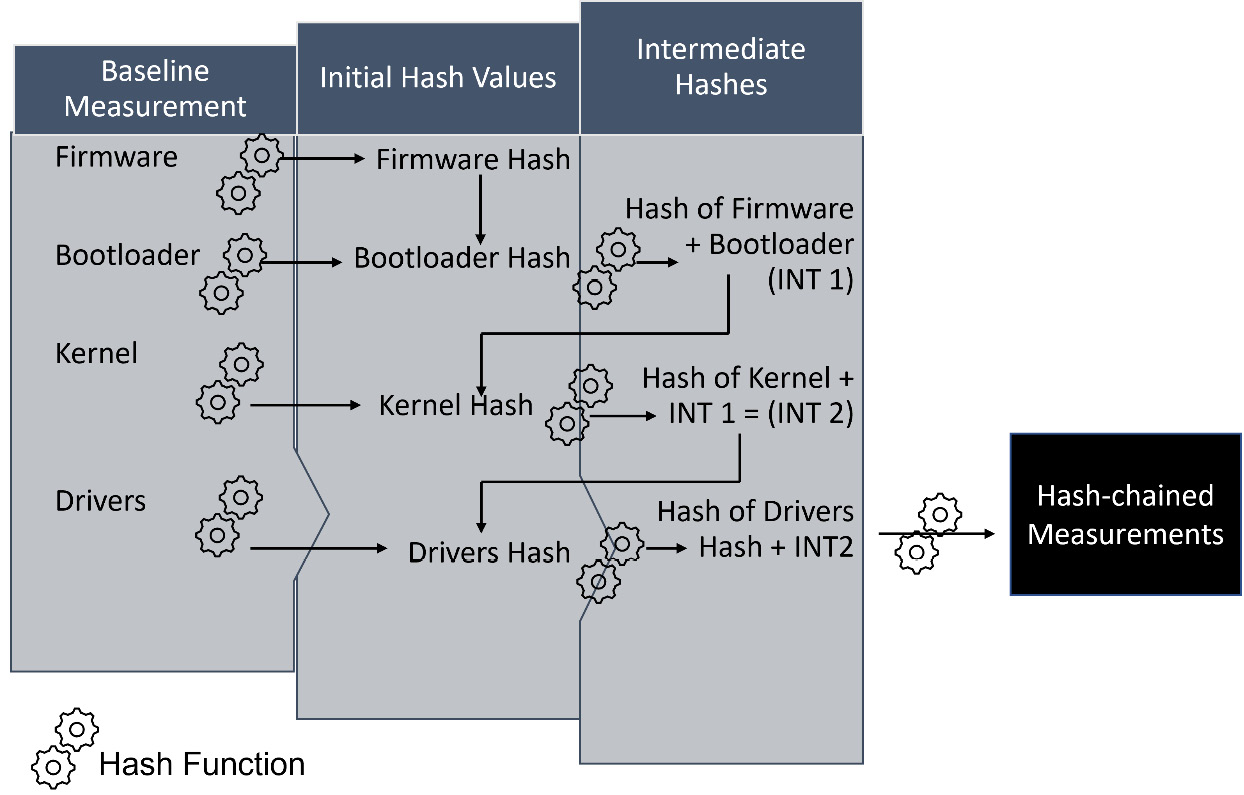
Figure 9.21 – The Measured Boot process
Hash chained measurements can be forwarded to server-based attestation services and can be used locally when unlocking BitLocker-encrypted hard drives.
Self-encrypting drives
When considering using FDE, performance may also be a goal. Self-encrypting drives (SEDs) use built-in hardware to provide encryption, thereby offering a performance advantage over software encryption. This is useful when incorporated into mobile computing devices.
Compensating controls
Once an organization has deployed secured/hardened computing systems, we cannot guarantee that the systems will be 100% protected. Depending on the new external threats, insider threats, and attack techniques that may develop for an organization, additional compensating controls may have to be considered. We will discuss some examples of these in the following subsections.
Antivirus tools
Antivirus tools should be deployed as a centrally managed solution for Windows operating systems. Windows is the main target for malware – there are very few examples of malware infections for Unix and Linux systems. However, Linux file servers and mail servers could pass on infected files if they are serving Windows clients. Traditional antivirus software works by identifying malware by using signature definition files. However, a virus may be programmed to change its signature, therefore defeating the signature definition approach. As a result, newer antivirus tools can look for common strings within a suspicious file. Windows comes with built-in protection with Microsoft Windows Defender, but additional malware detection application suites are available to further complement this.
Host-based intrusion detection systems (HIDSes) and host-based intrusion prevention systems (HIPSes)
When implementing security for your end devices, it is important to recognize where defense in depth (DiD) can be useful. A HIDS or HIPS will complement any network-based protection that is in place. Host systems will help to prevent anomalous administrator actions and any attempts to replace system files, and they will generally block any malicious actions. A HIDS or HIPS will also work alongside other anti-malware tools.
Host-based firewalls
A local firewall will complement the network firewalls by blocking unwanted connections on internal network segments also known as east-west traffic. To do this, host-based firewalls are frequently deployed on the most commonly used operating systems. Microsoft Windows has Windows Defender Firewall, which can be managed using graphical tools or with PowerShell commands. Figure 9.22 shows a screenshot of Windows Firewall:
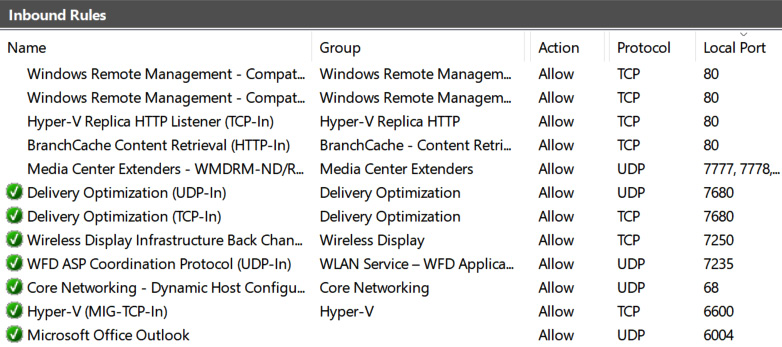
Figure 9.22 – Windows Defender Firewall
Linux systems can be protected by using the iptables service. The following command drops all packets from the 10.10.0.0/24 source network:
iptables -A INPUT -I eth0 -s 10.10.0.0/24 -j DROP.
To display the firewall rules that are currently configured, we use the iptables –help command.
To discard all firewall rules that are currently set, we can use the iptables –flush command.
Figure 9.23 shows some iptables firewall rules that are set to block traffic being received from any private network address:
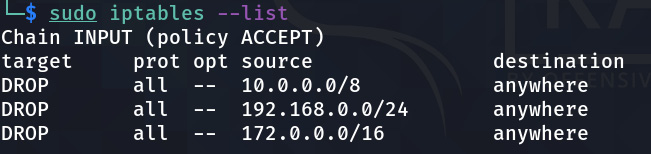
Figure 9.23 – Some iptables firewall rules
To display rulesets (called chains), we use the iptables –list command from the Linux bash shell.
It is normal to add a rule to a security device to block source traffic originating from a private network address (like the example in Figure 9.23).This is done where traffic is routed from external networks, as this type of traffic normally indicates the addresses are being spoofed.
Endpoint detection and response (EDR) software
EDR software allows an agent to be deployed on endpoint devices. It will work alongside traditional anti-malware solutions but does not rely on definition files and known malware hashes. To best prepare for future threats, endpoint monitoring should be continuous, with logs being forwarded to the EDR provider. Actions can be processed in real time, with databases of Advanced Persistent Threat (APT) actors, TTPs, and collected baseline data from normal activity, which allows Indicators of Compromise (IOC) to be detected. Many security providers will offer complete managed solutions for organizations that do not have Security Operations Center (SOC) staff to spare (these are known as managed security service providers (MSSPs)). With new attacks constantly being initiated, EDR software will better protect organizations from ransomware attacks, fileless malware attacks, and zero-day exploits. Popular options for this include CrowdStrike and Microsoft Defender for Endpoint. Please see the following URLs for more details of these solutions:
Redundant hardware
When hosting important systems that may result in a disproportionate impact if they fail, we must identify ways to make them more resilient. On data center servers, it is common to deploy redundant power supplies, network interface cards, and storage. In these situations, it is important to identify where single points of failure can negatively impact a workload.
Self-healing hardware
Wherever it is possible to increase resilience, we should implement systems that can identify problematic events and where necessary, make an adjustment. One example of this is using hardware clusters, where a failure to send a heartbeat signal would result in a workload being hosted on another hardware node. Modern hard disk drives automatically mark out bad blocks and replace them with reserve blocks held in a reserve pool. On Microsoft operating systems from Windows Server 2012 onward, the Resilient File System (ReFS) has been an available feature that allows this. The ReFS deploys an integrity scanner that constantly scans the hosted drives and initiates a repair process if needed.
User and entity behavior analytics (UEBA)
To protect valuable company data, it is becoming increasingly common to use analytics to detect patterns of behavior. If a user account was suddenly used out of context, then the system could alert administrators or block the action. So, imagine that a user, Joe, based in the United Kingdom, logs into his work email from a location identified as North Korea on December 25. He subsequently begins to delete large amounts of important manufacturing data from the engineering team's shared drive – if using UEBA, this would trigger an immediate alert to his line manager and SOC team members.
Summary
In this chapter, we have learned how to provide security for endpoint devices running a variety of operating systems. We have understood the need to harden end devices such as traditional desktop computers, laptops, tablets, and handheld and wearable technology. We have discussed how to assess the security of these devices, how to choose the appropriate technologies that the enterprise should adopt, and how to ensure we can provide the attestation that these devices are compliant with security policies. We have also understood the need for deployed images to be built from a validated secure template. We have learned that services should only be enabled if there is a business need to justify them. We investigated compensating controls, including host firewalls, EDR software, and antivirus tools. We also learned about the tools and techniques needed to secure our endpoints. We have studied technologies to support host attestation and Secure Boot options.
This information should give the reader a good baseline understanding of endpoint security, before we move on to the next chapter, where we will study how to secure critical infrastructure.
Questions
- Some executives from an organization attend an industry conference. Using mobile devices and wireless headsets, they are able to stay in touch with colleagues back at the workplace. What may present a security concern in this situation?
- Tethering
- WPA3
- Device certificates
- Bluetooth
- Some marketing executives from an organization attend an international trade exhibition and must connect to the company email by using their mobile devices during the event. The CISO is concerned this may represent a risk. What would best mitigate this risk?
- NFC
- A split-tunnel VPN
- Geofencing
- Always-on VPN settings
- What function should be disabled to ensure scientists cannot use their mobile devices to bridge the corporation's network with a cellular operator's network?
- Tethering
- WPA3
- Device certificates
- Bluetooth
- What should be implemented to ensure only company-approved applications can be installed on company devices?
- Containerization
- Token-based access
- A patch repository
- Whitelisting
- A user calls the service desk because her Samsung smartphone is prompting her to install updates that the vendor says will offer more functionality and security. What is this an example of?
- MFA requirements
- Token-based access
- A patch repository
- Firmware over-the-air
- An employee's company mobile device is reported as stolen 24 hours after the event. Sensitive data has been posted online by hackers. What would have mitigated this risk if the report had been made earlier?
- MFA requirements
- A remote wipe
- A patch repository
- Firmware over-the-air
- What type of setting will ensure mobile devices will only be able to access Wi-Fi when they connect securely to the company WLAN?
- WPA3 SAE
- Device certificates
- Device profiles
- Bluetooth
- An employee has noticed several suspicious payments made from a company debit card via Google Pay on their company smartphone. They recently attended a busy trade conference. What technology was likely used to make the payments?
- NFC
- Peripherals
- Geofencing
- VPN settings
- How can we prevent certain mobile applications from being accessible when employees take COPE devices out of the warehouse?
- NFC
- MFA
- Geofencing
- VPN settings
- The service desk receives a call from a senior manager. She is concerned that spyware may be installed on her smartphone. Recent news, traffic, and weather updates have been targeted specifically for her location. What is the most likely reason for this activity?
- Airplane mode
- Location services
- NFC
- Geofencing
- A user is concerned that DNS lookups may be logged by government agencies. The user would like to protect their privacy. What would be the best method to protect privacy during name resolution?
- Geofencing
- VPN settings
- DNS over HTTPS (DoH)
- Containerization
- A nation-state sends a security team to scope out a military site in California in the United States. They use mobile devices to gather images, map the locations of communications equipment, and record detailed information about troop movements. What are they performing?
- Geotagging
- Geofencing
- Physical reconnaissance
- Personal data theft
- A personal device has many applications installed that are not available through the Apple App Store. The device subsequently fails compliance checks. What has likely made the device fail to be compliant with the security policies?
- Jailbreaking
- Sideloading
- Containerization
- An unauthorized application store
- A senior employee has followed a QC link and installed a mobile application used to order food and beverages at a local restaurant. The application is not available on the Google Play Store. Acceptable Use Policy (AUP) states that applications can only be downloaded from the official vendor store. What best describes what has allowed this application to be installed?
- Supply chain issues
- Sideloading
- Containerization
- An unauthorized application store
- Developers need to test mobile applications on a variety of hardware before making them available on official application stores. How can they install the applications locally on mobile devices?
- Update the supply chain.
- Use sideloading.
- Use containerization.
- Use an unauthorized application store.
- A sales director would like to allow sales employees to use their personal devices for accessing company applications and data as part of an effort to reduce business costs. What would be the best control to mitigate the risk of employees co-mingling personal and company data?
- Geotagging
- Geofencing
- Containerization
- Remote wipes
- When on a business trip, a CEO was detained for several hours at border control. When he was eventually reunited with his mobile phone, it had physical evidence of tampering. He powered on the device and input the correct pin, but found that all of the company applications and data were inaccessible. What has led to this situation?
- Geofencing
- Containerization
- Remote wipes
- An eFuse
- A user has been able to run an unmanaged Linux operating system alongside a managed Windows 10 build on a company laptop. What actions would allow security professionals to prevent this issue from re-occurring?
- Removing end-of-support devices
- Using local drive encryption
- Disabling CPU virtualization support
- Enforcing secure encrypted enclaves and SME
- Security administrators have deployed SELinux in enforcing mode. All unnecessary services have been removed. In a further attempt to enforce security, a number of commands – including vmstat and grep – have been blocked from some user accounts. What best describes this action?
- Whitelisting
- Shell restrictions
- ASLR
- Memory encryption
- The CISO is meeting with software engineers to better understand some of the challenges that they face. He is asking if there are any settings that can be incorporated into build images that will help to prevent attacks against the system memory. What two features should be chosen?
- ASLR
- Patching
- Firmware
- NX/XN
- What is deployed to mitigate the risk of privilege elevation and the misuse of applications on Android mobile devices?
- SELinux
- TPM technology
- SEAndroid
- Attestation services
- What built-in module stores PCR values and enforces integrity on a hardware platform?
- The TPM module
- Secure Boot mode
- UEFI
- The BIOS
- What would be the best choice of technical control to block a fast-spreading worm that targets a well-known NetBIOS port?
- UEBA
- A host-based firewall
- A HIDS
- Redundant hardware
- A reporting tool has alerted the administrator that Joe Smith, who is leaving the company in 4 weeks, has uploaded a large number of PDF documents to his personal cloud storage. What has likely triggered this event?
- UEBA
- A host-based firewall
- EDR software
- Self-healing hardware
- A system administrator needs to ensure the root account cannot be used to gain access to user data on a Linux Network File System (NFS) server. What actions would allow security professionals to prevent this issue from occurring?
- Ensuring passwords are stored in a shadow file
- Running SELinux in enforcing mode
- Disabling CPU virtualization support
- Enforcing secure encrypted enclaves and SME
Answers
- D
- D
- A
- D
- D
- B
- C
- A
- C
- B
- C
- C
- A
- D
- B
- C
- D
- C
- B
- A and D
- C
- A
- B
- A
- B
