Chapter 17: Mock Exam 2
Welcome to the study guide assessment test! These test questions are designed to resemble real-world CASP 004 exam questions. To make the test as realistic as possible, you should attempt these questions closed book and allocate the appropriate amount of time. You can use some notepaper or a scratchpad to jot down notes, although this will be different in a real test environment. To find the PearsonVue candidate testing rules, check out https://home.pearsonvue.com/comptia/onvue.
End of Study Assessment Test
Number of Questions: 50
Passing Score: 83% (Estimated)
Questions
- A company works with a cloud service provider (CSP) that provides bleeding-edge technology to perform data analytics and deep learning techniques on the company's data. As the technology becomes more widespread, it appears that a rival CSP can offer the same solutions for a 50% cost saving. However, it seems that the database format and rule sets that have been created can't be transferred to the rival CSP. What term would best describe this situation?
- Vendor risk
- Vendor lock-in
- Third-party liability
- Vendor management plan
- A major retailer works with a small, highly regarded, third-party development team. They intend to invest significant resources into a new customer-facing set of APIs. The retailer is concerned about the financial stability of the development company and worries that they may need to start the development project from scratch if the developers go bust. What could be used to allay the fears of the retailer?
- Change management
- Staff turnover
- Peer code review
- Source code escrow
- Andy is the CSO within a department of the United Kingdom's HM Revenue and Customs (HMRC). All new systems that will require government funding must be assessed concerning cost savings by working with a CSP. Andy is overseeing a proposed new system that will reduce the workload of the Inland Revenue HMRC employees. What must a government agency consider when planning to store sensitive data with a global CSP?
- Data sovereignty
- Data ownership
- Data classifications
- Data retention
- A Privacy Impact Assessment is being conducted on behalf of a private healthcare provider. A consultant is assessing regulatory requirements for the hospital's employee and patient data (within Europe). The data that is currently being held includes the following:
- Patient's address
- Patient's bank account details
- Patient's medical history
- Patient's X-ray records
- Employee bank account details
What type of information will need to be protected and which regulations are the most important? (Choose two)
- COPPA
- Personally identifiable information (PII)
- Financial records
- Intellectual property
- GDPR
- A regional bank intends to work with a CSP to harness some of the benefits associated with cloud computing. The bank wants the assurance that data will not be accessible when their contract with a CSP expires. What technology would be most applicable?
- Crypto erase
- Pulping
- Shredding
- Degaussing
- A company manufactures medical devices, including instruments and scanners. The company intends to sell and market its devices to a global customer base. The company must ensure its products are compatible with its worldwide customer base. What regulations or standards will be the most important?
- Export Control Regulations
- General Data Protection Regulation (GDPR)
- International Organization for Standardization (ISO)
- National Institute of Standards and Technology (NIST)
- A startup software development company is trying to win a US Federal Government contract to provision an Enterprise Resource Planning (ERP) application. They must assure the customer that they have a robust security framework for delivering software and services. What is the most relevant accreditation?
- Open Web Application Security Project (OWASP)
- Capability Maturity Model Integration (CMMI)
- National Institute of Standards and Technology (NIST)
- Cloud Security Alliance (CSA) Security Trust Assurance and Risk (STAR)
- A large US-based retailer is transitioning toward an online selling platform. While customer details and payment card details will be stored in-house, a CSP will be used to host the e-commerce site, including the online shop. What compliance will be most important to the retailer concerning storing cardholder data and electronic transactions?
- Payment Card Industry Data Security Standard (PCI DSS)
- General Data Protection Regulation (GDPR)
- Interconnection security agreement (ISA)
- Non-disclosure agreement (NDA)
- Eva is the CISO for a global stocks and shares trading site. She is performing a risk assessment that focuses on customer data being stored and transmitted. Customers are mainly based in North America with a small percentage based globally, including Europe. When it comes to considering regulatory and legal requirements, which of the following will be the most important?
- General Data Protection Regulation (GDPR)
- Payment Card Industry Data Security Standard (PCI DSS)
- International Organization for Standardization (ISO)
- Federal Information Security Management Act (FISMA)
- A US smartcard manufacturer needs to sell its products in a global market. They need to ensure that the technology is not sold to countries or governments that are hostile to the US. What guidance or regulations should they consult?
- Due care
- Export controls
- Legal holds
- E-discovery
- A government department has data privacy requirements and they need to have employees and service providers sign this agreement. They should be made aware of the strict terms of this agreement and the penalties that may be forthcoming if these requirements/standards are not met. What type of agreement will be important?
- Service-level agreement (SLA)
- Master service agreement (MSA)
- Non-disclosure agreement (NDA)
- Memorandum of understanding (MOU)
- A large multinational company intends to purchase multiple products on a rolling contract from a CSP. They need to document, payment terms, dispute resolution, intellectual property ownership, and geographic operational locations within the scope of the contract. What type of contract would be the most suitable?
- Service-level agreement (SLA)
- Master service agreement (MSA)
- Memorandum of understanding (MOU)
- Operational-level agreement (OLA)
- A global pharmaceutical company would like to build resiliency into its network connections. They are working with an ISP, who proposes a highly available MPLS solution. To ensure the vendor can deliver the service at 99.999% uptime, what documentation will be important?
- Service-level agreement (SLA)
- Memorandum of understanding (MOU)
- Interconnection security agreement (ISA)
- Operational-level agreement (OLA)
- A software development company and a mobile phone manufacturer have entered a business partnership. The business partners need to share data during a series of upcoming projects. This agreement will stipulate a timeline for the information exchange to be supported, security requirements, data types that will be exchanged, and the actual sites that will be part of the data interchange. What documentation best details these requirements?
- SLA
- MSA
- MOU
- ISA
- A regional healthcare provider needs to address ever-escalating costs. They propose to host some of the information systems with a CSP. The healthcare provider needs assurances that any sensitive data will be protected by the service provider, and that agreed-upon steps are in place if data breaches or any adverse action were to occur. What document would address these requirements?
- Non-disclosure agreement (NDA)
- Memorandum of understanding (MOU)
- Interconnection security agreement (ISA)
- Operational-level agreement (OLA)
- Privacy-level agreement (PLA)
- A government agency begins an investigation on an employee suspected of stealing company intellectual property (IP). What must be done first to ensure the data is not deleted?
- Due care
- Export controls
- Legal holds
- E-discovery
- A company has several internal business units. The business units are semi-autonomous but need to support each other for the business to be efficient. To ensure the business units can work together, it is important to document responsibilities for each business unit. This document will not be written by lawyers and is intended to formalize previous verbal agreements. What documentation would best suit this requirement?
- Service-level agreement (SLA)
- Master service agreement (MSA)
- Memorandum of understanding (MOU)
- Interconnection security agreement (ISA)
- An aerospace sub-contractor supplies parts to a major commercial aircraft manufacturer. The SLAs are very strict, with financial penalties for transgressions. Mission-critical processes must be identified within the subcontractor's plant to avoid any lengthy production delays. What metric can be used by the company to ensure a critical service will be operational within the specified timeframe?
- Recovery point objective
- Recovery time objective
- Recovery service level
- Mission essential functions
- A public transportation provider has recently completed a BIA and has determined that the Continuity of Operations Plan (COOP) will require an alternative site to be available in the event of a major incident at the main operational site. The planning team has identified a requirement for a site, housing equipment, and facilities ready for the business to use. Personnel and data will need to be moved to the site to become operational. What have they identified?
- Cold site
- Warm site
- Hot site
- Mobile site
- A CISO for a cellular telephony provider is working with a Cloud Service Provider (CSP) to define expected day-to-day computing needs. The company wants to be able to choose a plan where spikes in demand result in additional compute resources being automatically provisioned. What technology would best meet this requirement?
- Autoscaling
- Caching
- Bootstrapping
- Clustering
- A company wants to be more flexible concerning employee work/life balance. To allow for this cultural change, remote access and working from home will become widespread. Senior management has concerns about data security, as most of the company information systems are now cloud-based. The concerns that were discussed include the following:
- Data loss prevention
- Control over native features of cloud services, such as collaboration and sharing
- User and entity behavior analytics (UEBA)
- Configuration auditing
- Malware detection
- Data encryption and key management
- Context-based access control
As employees will not be connected to the company network, various management concerns must be addressed. What solution would best address these concerns?
- NGFW
- CASB
- DLP
- SWG
- What form of testing uses stakeholder involvement to assess the effectiveness of the plan? Scenarios can be discussed and actions that need to be performed can be evaluated. This exercise ensures the Disaster Recovery Team (DRT) or Cyber Security Incident Response Team (CSIRT) do not need to perform exhaustive testing until the plans are fine-tuned.
- Checklist
- Walk-through
- Tabletop exercises
- Full interruption test
- A cloud customer needs workloads to be rapidly deployed to support a large and diverse customer base. One important requirement is to allow virtualized infrastructure to be deployed, where configuration is applied to a compute node or cluster as it boots up from a standard image (such as Linux, Unix, or Windows). What technology would best suit this requirement?
- Autoscaling
- Distributed allocation
- Bootstrapping
- Replication
- A news delivery platform provider needs to deliver content in the form of web pages, media, and images to worldwide consumers. The requirement is for geographically dispersed servers using caching to ensure that data is available on the edge of the network, where users or customers will benefit from lower latency. What technology would best suit this requirement?
- Autoscaling
- Distributed network
- Content delivery network
- Replicated network
- A medical instrument manufacturer is currently experiencing problems in the production plant. The company is using a mix of Industrial Control Systems (ICS) on a common network backbone to operate the plant. Some of the manufacturing processes are time-critical and occasionally, bottlenecks occur at peak times during the day. To ensure that the time-critical processes are not impacted by bottlenecks, what technology would most likely mitigate these problems?
- Safety Instrumented System (SIS)
- Data Distribution Service (DDS)
- Operational Technology (OT)
- Controller Area Network (CAN)
- A utility company is following industry guidelines to harden its server systems. One of the first steps that the guidelines suggest is to identify all the available and unneeded services. What tool would best suit this requirement?
- Binary analysis tools
- Port scanner
- HTTP interceptor
- Protocol analyzer
- A well-known developer's content sharing portal has been targeted by a DDoS attack. Although it's the web application servers that are being targeted, the effect of all the traffic flooding the network has made all the services unavailable. Security experts are looking to implement protection methods and implement blackhole routing for the web application servers. What has this mitigation achieved?
- Traffic is inspected for malicious payloads
- Traffic intended for the systems is dropped
- Traffic to the systems is inspected before it reaches the destination
- Rules restrict the amount of traffic throughput
- Security analysts are responding to SIEM alerts that are showing a high number of IOC events. The analysts have a reason to suspect that there may be APT activity in the network. Which of the following threat management frameworks should the team implement to better understand the TTPs of the potential threat actor?
- NIST SP 800-53
- MITRE ATT&CK
- The Cyber Kill Chain
- The Diamond Model of Intrusion Analysis
- National Dynamics, an aerospace company, is looking to strengthen its cybersecurity posture by focusing on its network defenses. The company is concerned about the availability of the company's services to its B2B partners. Many manufacturing processes use JIT techniques to optimize production and false positives mustn't drop legitimate traffic. Which of the following would satisfy this requirement?
- NIDS
- NIPS
- WAF
- Reverse proxy
- A small law firm is looking to reduce its operating costs. Currently, vendors are proposing solutions where the CSP will host and manage the company's website and services. Due to legal and regulatory requirements, the company requires that all the available resources in the proposal must be dedicated. Due to cost constraints, the company does not want to fund a private cloud. Given the company requirements, which of the following is the best solution for this company?
- Community cloud service model
- Multi-tenancy SaaS
- Single-tenancy SaaS
- An on-premises cloud service model
- A company that uses Active Directory Services (ADS) is migrating services from LDAP to secure LDAP (LDAPS). During the pilot phase, the server team has been troubleshooting connectivity issues from several different client systems. Initially, the clients would not connect as the LDAP server had been assigned a wildcard certificate, *.classroom.local. To fix these problems, the team replaced the wildcard certificate with a specific named certificate, win2016-dc.classroom.local. Further problems are causing the connections to fail. The following screenshot shows the output from a troubleshooting session:

Figure 17.1 – LDAPS client troubleshooting session
Which of the following best explains why the LDAPS service failed initially and still fails client connection attempts? (Select two)
- The clients do not support the LDAP protocol by default.
- The LDAPS service has not been started, so the connections will fail.
- Classroom.local is under a DDoS attack and cannot respond to OCSP requests.
- The clients may not trust the issuing CA-classroom.classroom.local by default.
- LDAPS should be running on UDP rather than TCP.
- The company is using the wrong port. It should be using port 389 for LDAPS.
- LDAPS does not support wildcard certificates.
- A sales team relies on a CRM application to generate leads and maintain customer engagement. The tool is considered a mission-essential function to the company. During a business impact assessment, the risk management team indicated that data, when restored, cannot be older than 2 hours before a system failure. What planning objective should be used when the restoration will also require data to be restored?
- Recovery point objective
- Recovery time objective
- Recovery service level
- Mission-essential functions
- A large defense contractor has recently received a security advisory documenting the activities of highly skilled nation-state threat actors. The company's hunt team believes they have identified activity consistent with the advisory. Which of the following techniques would be best for the hunt team to use to entice the adversary to generate malicious activity?
- Perform audits on all firewall logs.
- Implement a bug bounty program.
- Increase security using isolation and segmentation schemes.
- Deploy decoy files on the host's systems on the same network segment.
- A new online retailer must ensure that all the new web servers are secured in advance of a PCI DSS security audit. PCI DSS requirements are strict and define acceptable cipher suites. Deprecated cipher suites should not be used as they offer weak encryption and are vulnerable to on-path attacks. In preparation for the audit, a security professional should disable which of the following cipher suites?
- TLS_RSA_WITH_AES_128_CCM_8_SHA256
- TLS_RSA_WITH_RC4_128_SHA
- TLS_RSA_WITH_AES_128_CBC_SHA256
- TLS_ECDHE_ECDSA_WITH_CHACHA20_POLY1305_SHA256
- A distribution company is attempting to harden its security posture regarding mobile devices. To secure the dedicated Android devices that are used in the warehouse, the company has developed SELinux policies. Security engineers have compiled and implemented the policy. Before deploying the Android devices to the warehouse staff, which mode should the devices be configured for?
- Disabled
- Permissive
- Enforcing
- Preventing
- A software development company is concerned as it has discovered that company intellectual property is circulating on social media. The CISO wants to implement a solution that will allow the company to determine the source of these leaks. Which of the following should be implemented to identify the internal source for any future exposures?
- Digital rights management
- Hashing
- Watermarking
- Identity proofing
- A company has recently undertaken a project to move several services into the cloud. A cloud service provider now hosts the following services:
- Corporate intranet site
- Online storage application
- Email and collaboration suite
The company must ensure that the data is protected from common threats, including malware infections, exfiltration of PII and healthcare data.
To be more proactive, an additional requirement is that SOC staff must receive alerts when there are any large transfers of corporate data from the company's hosted storage. Which of the following would best address the company's cyber-security requirements?
- NIDS
- CASB
- DLP agent
- Containers
- Vulnerability scanner
- A CISO is reviewing the current security of an electricity supply company. The company has many operational sites and must connect the sites securely to the company headquarters, which is where the company's data center is located. The technology that's supported within these sites includes industrial control systems and PLCs. The technology is legacy and uses the Modbus protocol across the networks. A VPN solution is being proposed to securely connect all the sites to the company's data center.
The CISO is concerned that a recent security advisory, concerning certain asymmetric algorithms, may impact the company's operations. Which of the following will be most likely impacted by weak asymmetric encryption?
- Modbus
- VPN links
- Industrial control systems
- Datacenter equipment
- Security administrators have run a scan on a network segment to detect vulnerabilities. They are trying to discover any protocols that may be running on host computers that may expose user passwords or sensitive data. The following screenshot shows the output from the scan:
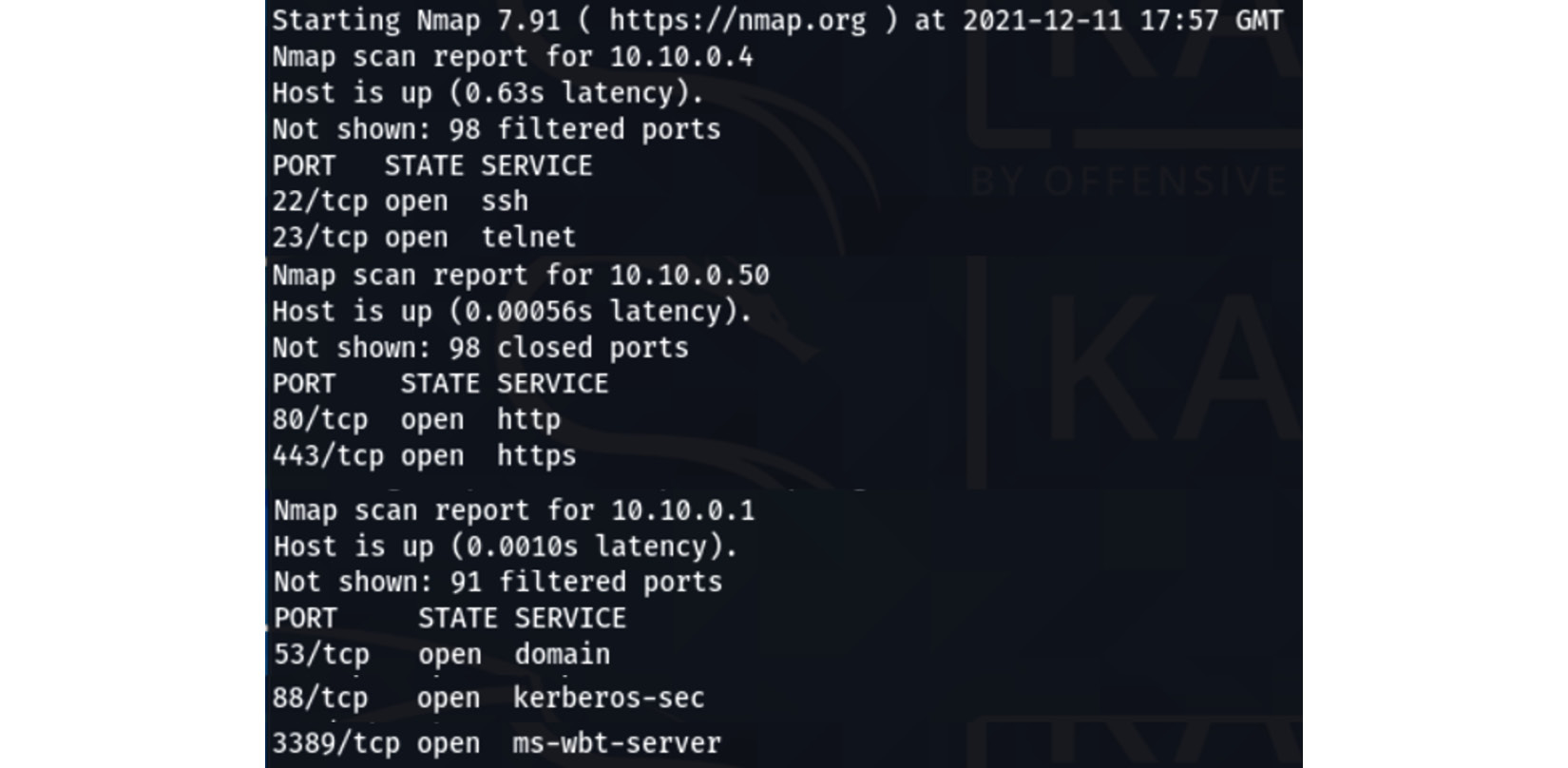
Figure 17.2 – Security scan output
To secure the network segment, additional rules must be enabled on the network firewall. Which rules should be added to meet this security requirement? Choose two.
- SRC Any DST 10.10.0.1 PORT 53 PROT TCP ACTION Deny
- SRC Any DST 10.10.0.4 PORT 23 PROT TCP ACTION Deny
- SRC Any DST 10.10.0.4 PORT 22 PROT TCP ACTION Deny
- SRC Any DST 10.10.0.50 PORT 80 PROT TCP ACTION Deny
- SRC Any DST 10.10.0.1 PORT 88 PROT TCP ACTION Deny
- SRC Any DST 10.10.0.50 PORT 443 PROT TCP ACTION Deny
- A systems administrator has deployed all updated patches for Windows-based machines. However, the users on the network are experiencing exploits from various threat actors, which the patches should have corrected. Which of the following is the most likely scenario here?
- The machines were infected with malware.
- The users did not reboot their computers after the patches were deployed.
- The systems administrator used invalid credentials to deploy the patches.
- The patches were deployed on non-Windows-based machines.
- A penetration tester is trying to gain access to a remote system. The tester can see the secure login page and knows one user account and email address but has not discovered a password yet. Which of the following would be the easiest method of obtaining a password for the known account?
- Man-in-the-middle
- Reverse engineering
- Social engineering
- Hash cracking
- An external hacker has managed to exploit an unpatched vulnerability in a web application server. They were able to use the web application service account to download malicious software. The attacker tried (unsuccessfully) to gain root privileges to install the software and was subsequently discovered. The server admin team rebuilt and patched the server. Which of the following should the team perform to prevent a similar attack in the future?
- Remove the application service account
- Air gap the web application server
- Configure SELinux and set it to enforcing mode
- Schedule regular restarts of the service to terminate sessions
- Use Nmap to perform regular uncredentialed vulnerability scans
- A manufacturing company is deploying loT locks, sensors, and cameras, which operate wirelessly. The devices will be used to allow physical access by locking and unlocking doors and other access points. Recent CVEs have been listed against the devices, for which the vendor has yet to provide firmware updates. Which of the following would best mitigate this risk?
- Connect the loT devices directly to ethernet switches and create a segmented VLAN.
- Require sensors to digitally sign all transmitted control messages.
- Add all the IoT devices to an isolated wireless network and use WPA2 and EAP-TLS.
- Implement a wireless intrusion detection system.
- A forensics investigator is following up on an incident where suspicious images have been stored on an employee's computer. The computer is currently powered off in the employee's workspace. Which of the following tools is best suited to retrieving full or partial image files from the storage device, which have been deleted so that the attacker evades detection?
- memdump
- foremost
- dd
- nc
- An aerospace company is adding promotional material to a public-facing web application server. The server will host a website containing many images, highlighting a production plant and test facilities. The CISO is concerned that the images may contain geographic coordinates in the metadata, and some of the physical locations need to remain secret. What tool can be used to ensure that the images will not contain sensitive data within the metadata?
- grep
- ExifTool
- Tcpdump
- Wireshark
- A critical service on a production system keeps crashing at random times. The systems administrator suspects that the code has not been adequately tested and may contain a bug. When the service crashes, a memory dump is created in the /var/log directory. Which of the following tools can the systems administrator use to reproduce these symptoms?
- DAST
- Vulnerability scanner
- Core dump analyzer
- Hex dump
- Ontario Outdoors Inc is expecting major disruptions due to a winter weather warning. The CISO has been reviewing company policies to ensure adequate provisions are in place to deal with these environmental impacts and finds that some are missing or incomplete. The CISO must ensure that a document is immediately drafted to move various personnel and equipment to other locations to avoid downtime in operations. What is this an example of?
- A disaster recovery plan
- An incident response plan
- A business continuity plan
- A risk avoidance plan
- Acme corporation operates a nuclear power station and relies on a legacy ICS to perform equipment monitoring functions. Regulatory compliance requires that this monitoring is mandatory. Penalties for non-compliance could be costly. The ICS has known vulnerabilities but cannot be updated or replaced. The company has been refused cyber-liability insurance. Which of the following would be the best option to manage this risk in the company's production environment?
- Avoid the risk by removing the ICS from production
- Transfer the risk associated with the ICS vulnerabilities
- Mitigate the risk by restricting access to the ICS
- Accept the risk and upgrade the ICS when possible
- Following a security incident, forensics has handed over a database server to the server admin team to begin the recovery phase. The team is looking to deploy an automated build by running a script. When accessing the Bash shell, they observe the following command as the most recent entry in the server's shell history:
dd if=dev/sda of=dev/sdb
Which of the following most likely occurred?
- Forensics have used binary analysis tools to search the metadata.
- The drive was cloned for forensic analysis.
- The hard drive was formatted after the incident.
- There is evidence that the forensics team may have missed.
- A software engineer is looking to implement secure code while the code is still in the development environment. The goal is to deploy code that meets stability and security assurance goals. Which of the following code analyzers will produce the desired results?
- SAST
- DAST
- Fuzzer
- Peer code review
Answers
- B. Vendor lock-in. This makes it difficult to switch providers as the technology is often proprietary. See Chapter 13, Applying Appropriate Risk Strategies.
- D. Source code escrow. External developers represent third-party risk. This can be mitigated by storing the code with an escrow service. This protects the IP of the developers but also protects the customer. See Chapter 13, Applying Appropriate Risk Strategies.
- A. Data sovereignty. The type of data that's stored by a government department would typically have strict regulatory controls. A global CSP may store the data offshore. See Chapter 13, Applying Appropriate Risk Strategies.
- B and E. This type of data would be labeled as PII and GDPR regulatory controls would be important as the patients and employees may be EU citizens. See Chapter 14, Compliance Frameworks, Legal Considerations, and Their Organizational Impact.
- A. Crypto erase. The customer will not have physical access to the data, so they will not be able to ensure other methods of destruction can be implemented. Crypto Erase will render the data unrecoverable. See Chapter 13, Applying Appropriate Risk Strategies.
- C. International Organization for Standardization (ISO). This will ensure that the products will be suitable across international boundaries. See Chapter 14, Compliance Frameworks, Legal Considerations, and Their Organizational Impact.
- B. Capability Maturity Model Integration (CMMI). This accreditation is required to tender for US government software contracts. See Chapter 14, Compliance Frameworks, Legal Considerations, and Their Organizational Impact.
- A. Payment Card Industry Data Security Standard (PCI DSS). Storage and processing of customer card details will be subject to PCI DSS compliance. See Chapter 14, Compliance Frameworks, Legal Considerations, and Their Organizational Impact.
- A. General Data Protection Regulation (GDPR). As this is not government or payment card data, then the focus will be on customers based in the EU. See Chapter 14, Compliance Frameworks, Legal Considerations, and Their Organizational Impact.
- B. Export controls. This is important when you're exporting technology. See Chapter 14, Compliance Frameworks, Legal Considerations, and Their Organizational Impact.
- C. Non-disclosure agreement (NDA). This is legally enforceable and protects intellectual property. See Chapter 14, Compliance Frameworks, Legal Considerations, and Their Organizational Impact.
- B. Master service agreement (MSA). This is useful when it is necessary to set baseline terms for future services. See Chapter 14, Compliance Frameworks, Legal Considerations, and Their Organizational Impact.
- A. Service-level agreement (SLA). This will allow the customer and the service provider to agree upon delivered services and the metrics that will be used to measure performance. See Chapter 14, Compliance Frameworks, Legal Considerations, and Their Organizational Impact.
- D. Interconnection security agreement (ISA). This is important for documenting the details when a connection is made between two or more parties. See Chapter 14, Compliance Frameworks, Legal Considerations, and Their Organizational Impact.
- E. Privacy-level agreement (PLA). This is very important when you're looking to assure customers who must adhere to strict regulatory compliance. See Chapter 14, Compliance Frameworks, Legal Considerations, and Their Organizational Impact.
- C. Legal holds. This ensures that the data will be retained for any legal process. See Chapter 14, Compliance Frameworks, Legal Considerations, and Their Organizational Impact.
- C. Memorandum of understanding (MOU). This is not a legal document but it can be very useful when there needs to be co-operation between two or more parties. See Chapter 14, Compliance Frameworks, Legal Considerations, and Their Organizational Impact.
- B. Recovery time objective. A recovery time objective is a planning objective that is set by stakeholders within the business. It may be cost-driven and requires careful consideration. See Chapter 15, Business Continuity and Disaster Recovery Concepts.
- B. Warm site. A warm site will not be as costly as a hot site but will not be operational until data is restored and staff are available to operate the site. See Chapter 15, Business Continuity and Disaster Recovery Concepts.
- A. Autoscaling. This allows the company to access additional computing power using automation. See Chapter 15, Business Continuity and Disaster Recovery Concepts.
- B. CASB. The company data must be protected in the cloud. Not all users will originate from a company network, so NGFW and SWG will not work. DLP does not address all the requirements. See Chapter 15, Business Continuity and Disaster Recovery Concepts.
- C. Tabletop exercises. Stakeholders will discuss how they will act when dealing with a presented scenario. See Chapter 15, Business Continuity and Disaster Recovery Concepts.
- C. Bootstrapping. This allows the automated deployment of customized workloads from a standard base image. PowerShell Desired State Configuration (DSC) is an example of this technology. See Chapter 15, Business Continuity and Disaster Recovery Concepts.
- C. Content Delivery Network. This allows the timely delivery of time-sensitive services and reduces latency. See Chapter 15, Business Continuity and Disaster Recovery Concepts.
- B. Data Distribution Service (DDS). DDS has built-in provisions for Quality of Service (QoS). See Chapter 10, Security Considerations Impacting Specific Sectors and Operational Technologies.
- B. Port Scanner. Nmap is a good choice for the following:
Scanning www.comptia.org (52.165.16.154) [1000 ports]
Discovered open port 443/tcp on 52.165.16.154
Discovered open port 80/tcp on 52.165.16.154
Completed SYN Stealth Scan at 15:36, 9.18s elapsed (1000 total ports)
See Chapter 5, Threat and Vulnerability Management.
- B. Traffic intended for the systems is dropped. A good example of this technique is Remote Triggered Black Hole (RTBH) routing. See Chapter 1, Designing a Secure Network Architecture.
- B. MITRE ATT&CK. MITRE receives government funding to carry out research and is well known for its published attack frameworks and tactics. The matrices are created to understand the tactics and techniques that attackers will use against operating systems, cloud network mobility, and industrial control systems. See Chapter 5, Threat and Vulnerability Management.
- A. NIDS. Such systems protect an organization from inbound threats across the network. The technology is primarily passive, generating alerts that must be actioned by SOC staff. See Chapter 1, Designing a Secure Network Architecture.
- C. Single-tenancy SaaS. As the CSP will be hosting and managing the company services, then the service that the customer is paying for will be Software as a Service (SaaS) to isolate the workloads. They can pay a premium to have a single tenancy. See Chapter 3, Enterprise Data Security, Including Secure Cloud and Virtualization Solutions.
- D and G. The clients may not trust the issuing CA-classroom.classroom.local by default. LDAPS does not support wildcard certificates.
The first issue that the server team solved was the problem that LDAPS does not support wildcard certificates. The second problem is most likely that the certificate authority (CA) is not trusted. If this is an internal CA, then the root CA certificate will need to be installed in the trusted enterprise store of all client computers. See Chapter 12, Implementing Appropriate PKI Solutions, Cryptographic Protocols, and Algorithms for Business Needs.
- A. Recovery point objective. When data must be available to service a mission-critical service, then the recovery point objective metric must be used. See Chapter 15, Business Continuity and Disaster Recovery Concepts.
- D. Deploy decoy files on hosts systems on the same network segment. If an APT has access to the network, then a decoy file will be a good test to observe any malicious activity. See Chapter 7, Risk Mitigation Controls.
- B. TLS_RSA_WITH_RC4_128_SHA. RC4 is weak encryption and will not be used in any regulated industries. See Chapter 11, Implementing Cryptographic Protocols and Algorithms.
- C. Enforcing. To run an SElinux policy and make Mandatory Access Control (MAC) effective, the systems must be powered up in enforced mode. See Chapter 9, Enterprise Mobility and Endpoint Security Controls.
- C. Watermarking. If an organization wants to detect theft or exfiltration of sensitive data, then documents can be checked out from an information system, but an automatic watermark will be applied to the document using the identity of the user who checked out the document. See Chapter 3, Enterprise Data Security, Including Secure Cloud and Virtualization Solutions.
- B. CASB. A CASB is often referred to as a gatekeeper that protects the enterprise data from inbound threats into the cloud and outbound threats such as data exfiltration. Another benefit of CASB is to ensure regulatory compliance, by labeling and monitoring the use of the data, to ensure compliance. See Chapter 15, Business Continuity and Disaster Recovery Concepts.
- B. VPN links. A VPN allows traffic to be secured when it's passing through untrusted networks. If the external traffic uses weak encryption, then it could be accessed by an adversary. See Chapter 1, Designing a Secure Network Architecture.
- B and D.
SRC Any DST 10.10.0.4 PORT 23 PROT TCP ACTION Deny
SRC Any DST 10.10.0.50 PORT 80 PROT TCP ACTION Deny
Port 23 supports the telnet protocol; this allows unsecured traffic to be sent when you're configuring equipment across a network. Port 80 allows for unsecured web traffic. Port 53 is for DNS traffic; this does not transmit passwords or sensitive data. Port 88 is Kerberos; this encrypts the transmission of user login traffic. Port 22 is SSH, encrypting traffic is used to access a console session on another host system. See Chapter 1, Designing a Secure Network Architecture, for more information on firewall rules.
- B. The users did not reboot the computer after the patches were deployed. Certain patches may not be effective until the operating system is rebooted. See Chapter 9, Enterprise Mobility and Endpoint Security Controls.
- C. Social engineering. Once an attacker has access to credentials, the most likely exploit to reveal a password is social engineering. See Chapter 6, Vulnerability Assessment and Penetration Testing Methods and Tools.
- C. Configure SELinux and set it to enforcing mode. SELinux enforces mandatory access control, allowing for strict enforceable policies to be deployed. This would further restrict a compromised account from accessing other resources on the system. See Chapter 9, Enterprise Mobility and Endpoint Security Controls.
- C. Add all the IoT devices to an isolated wireless network and use WPA2 and EAP-TLS. As all the devices connect wirelessly, they must be connected to a wireless segment. It is important to separate the network as there are vulnerable systems. See Chapter 10, Security Considerations Impacting Specific Sectors and Operational Technologies.
- B. Foremost. This is a forensics tool that can search for complete or partial files that have been deleted or hidden in some way. See Chapter 8, Implementing Incident Response and Forensics Procedures.
- B. ExifTool. The following screenshot shows the partial output from ExifTool:
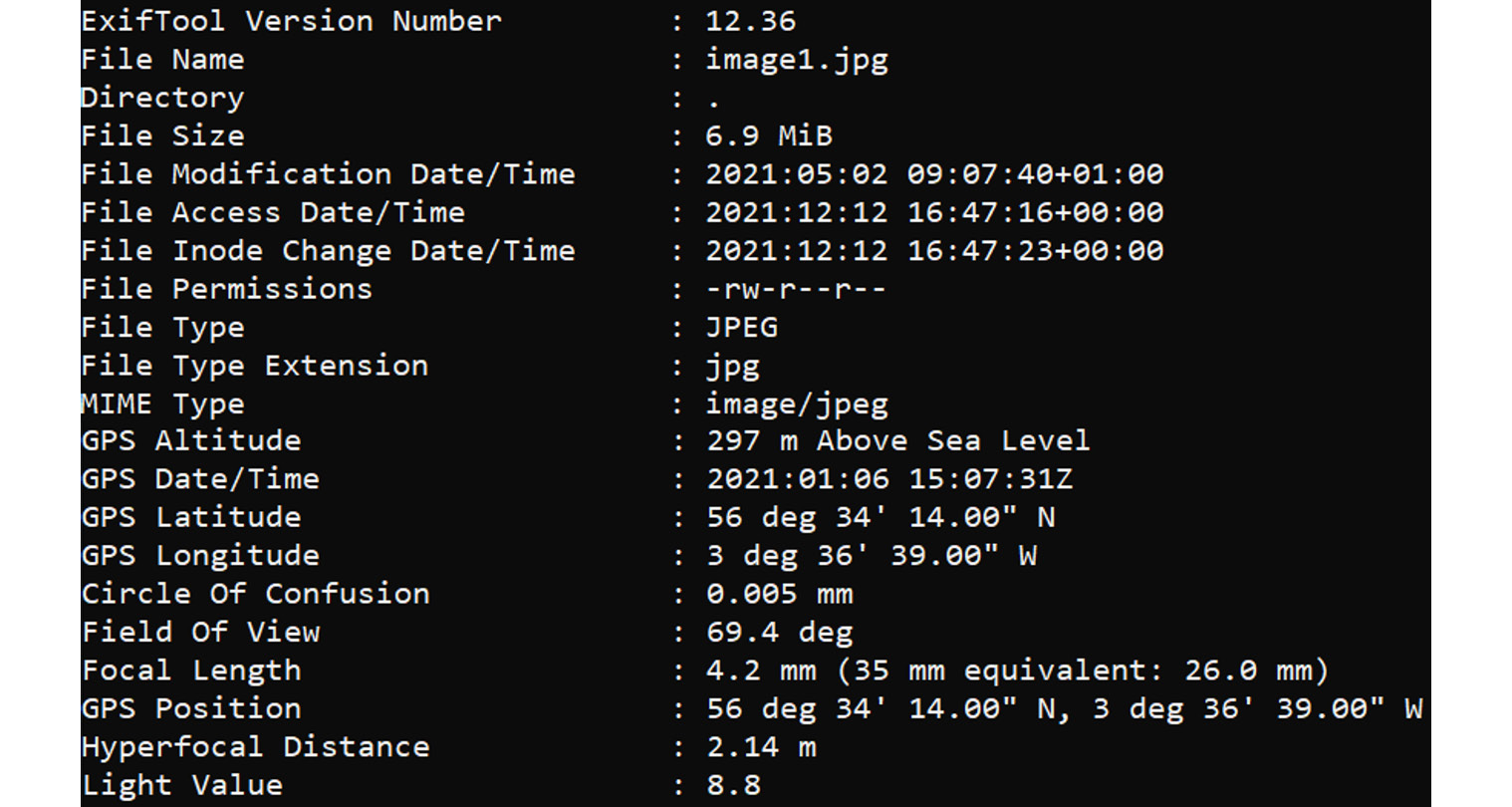
Figure 17.3 – The GPS data from an image file
Using ExifTool allows an analyst to determine the location the image was taken from.
- A. DAST. DAST tools allow a tester to recreate the error. See Chapter 2, Integrating Software Applications into the Enterprise.
- C. A business continuity plan. A business continuity plan allows the organization to identify potential problems and have alternative plans of action. See Chapter 15, Business Continuity and Disaster Recovery Concepts.
- C. Mitigate the risk by restricting access to the ICS. The only available course of action is to segment the network that contains the legacy equipment. This is a common approach when it comes to dealing with operational technology. See Chapter 10, Security Considerations Impacting Specific Sectors and Operational Technologies.
- B. The drive was cloned for forensic analysis. See Chapter 8, Implementing Incident Response and Forensics Procedures.
- A. SAST. The code is still in the development environment, so SAST will be the most appropriate option here. See Chapter 2, Integrating Software Applications into the Enterprise.
Hopefully, you enjoyed testing yourself with a typical mix of CASP questions. For more exam resources and extra content please visit https://www.casp.training.
