Chapter 20
Physical Security
Over the years, I've visited lots of different companies, large and small, public and private, and analyzed, advised, troubleshot, designed, and implemented their networks. Without fail, the system administrators I've met along the way have been really eager to tell me all about the security systems they have in place. “Look at this awesome firewall setup!”, “Check out the cool Group Policy structure we have!” “Watch how quickly our fault tolerance springs into action!” They're very proud, and rightly so, of what they've worked so hard to set up, because doing that isn't easy.
But interestingly, one of the things few people brag about is physical security—like it's some kind of afterthought. Maybe the server room has a locked door, maybe it doesn't. Maybe the badges that open that door are owned by the right people, or maybe they aren't. I guess that on a subconscious level, we tend to inherently trust the people working within the walls and focus our fears, suspicions, and ammo on mysterious outside forces that we're sure are incessantly trying to break in, steal data, or totally murder our networks. Some of the sharpest, most talented, and savvy system administrators I've ever met still have a tendency to neglect inside security and fail to reasonably monitor things going on within the building.
And there are some seriously vital things to nail down on the inside. For instance, does it really matter if your network has a secured subnet for the servers, with its own dedicated internal firewall? Definitely—I've actually found servers in racks like sitting ducks in a hallway right across from the lunch room. When I pointed out the fact that this was not so good, I was assured that it was only temporary until the server room construction was complete. I don't know about you, but for some reason, that didn't cut it and didn't make me feel anywhere near okay with the situation. At another company, I found the door to the server room propped open because otherwise “it got too hot in there.” Because that toasty server room didn't exactly have a guard posted, anyone could just walk in and do whatever; the backup tapes were clearly marked and sitting there on a shelf—yikes! And don't even get me started about the heat. The bottom line is that if your system is not physically secured, you're basically sending out an open invitation to a Pandora's box of problems without even realizing it.
Detection Methods
You can't react to and address a security issue if you don't even know its occurring. As one fellow security expert once said, “if you're going to get hacked, at least realize you've been hacked.” Detection technologies and procedures are designed to alert you when bad things might be occurring. In the following sections, we'll look at some of the most common detection mechanisms.
Cameras
In many high-security scenarios it may be advisable to visually monitor the area 24 hours a day. When this is the case, it will make sense to deploy video monitoring. We'll look at two options, IP cameras and CCTV systems.
IP Cameras
IP video systems are a good example of the benefits of networking applications. These systems can be used both for surveillance of the facility and for facilitating collaboration.
CCTVs
While an IP camera is a type of digital video camera commonly employed for surveillance, analog closed-circuit television (CCTV) cameras are unable to send their images across IP networks. CCTV cameras record directly to a medium such as video tape or hard drive. It is possible to convert the signal to digital in cases where you need to send it across an IP network.
Cameras should cover all entrances to the building and the entire parking lot. Be sure that cameras are in weather-proof and tamper-proof housings and review the output at a security-monitoring office. Record everything on extended-length tape recorders.
Motion Detection
In areas that require constant attention to security, it may be advisable to install motion detectors of some sort. Server rooms, wiring closets, and other critical areas may need these. Let's look at a few types.
Infrared Sensors
Passive infrared (PIR) systems operate by identifying changes in heat waves in an area. Because the presence of an intruder would raise the temperature of the surrounding air particles, the system alerts or sounds an alarm when this occurs.
Electromechanical Systems
Electromechanical systems operate by detecting a break in an electrical circuit. For example, the circuit might cross a window or door, and when the window or door is opened, the circuit is broken, setting off an alarm of some sort. Another example might be a pressure pad placed under the carpet to detect the presence of individuals.
Photoelectric Systems
Photometric or photoelectric systems operate by detecting changes in the light and thus are used in windowless areas. They send a beam of light across the area and if the beam is interrupted (by a person, for example), the alarm is triggered.
Acoustical Detection Systems
Acoustical systems use strategically placed microphones to detect any sound made during a forced entry. These systems only work well in areas where there is not a lot of surrounding noise. They are typically very sensitive, which would cause many false alarms in a loud area, such as a door next to a busy street.
Wave Motion Detector
These devices generate a wave pattern in the area and detect any motion that disturbs the wave pattern. When the pattern is disturbed, an alarm sounds.
Capacitance Detector
These devices emit a magnetic field and monitor that field. If the field is disrupted, which will occur when a person enters the area, the alarm will sound.
Asset Tags
Proper asset management is not rocket science. It boils down to knowing exactly what you have, when you got it, where it is, and where the license to use it is. The devil as they say is in the details. Most server administrators don't set out to intentionally exercise poor asset management; they simply don't give it the importance it requires to be done correctly.
Labeling or tagging servers, workstations, printers, ports on infrastructure devices (routers and switches), and other items is another form of asset documentation that often doesn't receive enough attention. Not only does this make your day-to-day duties easier, it makes the process of maintaining accurate records simpler and supports a proper asset management plan. When periodic inventories are taken (you are doing that, right?), having these items labeled makes the process so much quicker. This goes for cables in the server room as well.
Tamper Detection
Tamper detection refers to any method that alerts you when a device or the enclosure in which it resides has been opened or an attempt has been made to open it. A good example is computer chassis intrusion detection.
You should use settings in the BIOS/UEFI to alert you when the case has been opened. These settings are shown in Figure 20.1. In this case, the open case warning has not been enabled yet.
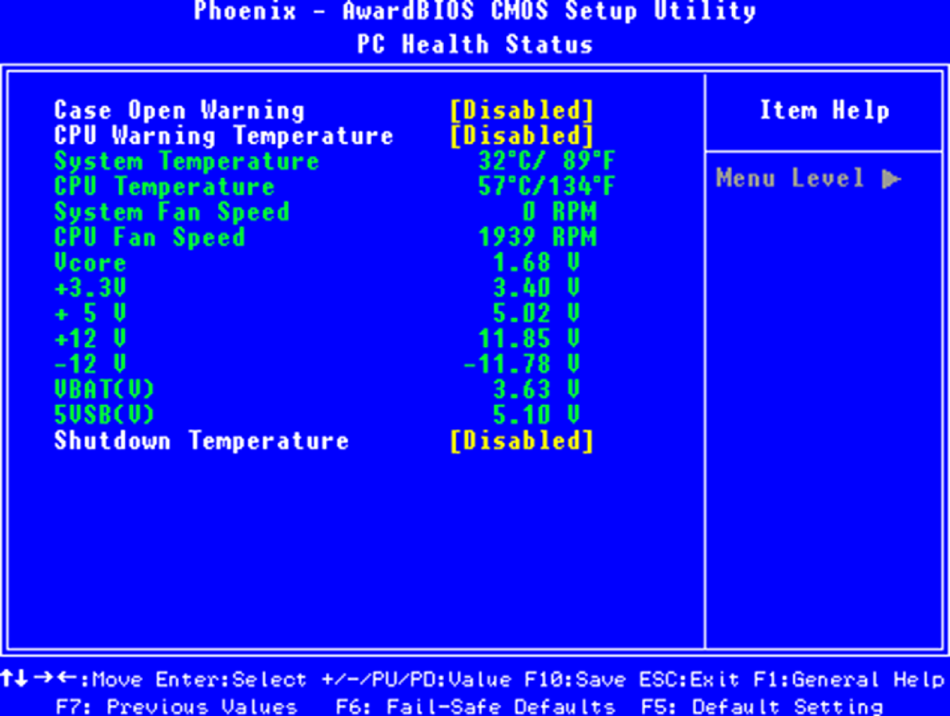
FIGURE 20.1 Open case warning in the BIOS
Prevention Methods
While detection mechanism are great, wouldn't it be even better if we could just avoid the issue altogether? There are some measures we can take to prevent some of the issues that detection mechanisms are designed to identify. In the following sections, you'll learn about some of the more common methods.
Employee Training
This brings us to the human element of network security. It's true that most of your users want to do the right thing to protect the company from the prying eyes of hackers (and in the process protect their jobs), but the problem is that people don't always know the right thing to do. That's why training is so vital. It can include classroom sessions and/or web-based training, but experience has shown me that actual classroom-based instruction works the best. It's also a good idea to have separate training classes for IT personnel and end users.
End-User Training
End-user training is pretty easy—it can take just an hour or so to bring employees up to speed. The “keep it short and simple” rule applies here or you'll just end up with nap time. This is a great time to include detailed security protocol training. But if you see eyes beginning to glaze over or hear anyone snoring, you might want to make security protocol training a separate session because, as I said, it's really important to the effectiveness of your security policy for everyone to know about and understand it. You can even use a year-end bonus or something else cool as a motivational reward for the employees who complete their training and test well on it.
And you have to back up your training by providing your end users with hard-copy, printed reference manuals in case they forget something (which they will). Include things like the following items:
- Recommended policies for creating safe passwords
- The number to call if they've locked themselves out of their accounts
- What to do if they think someone is phishing for information
- What to do if they think their computer has a virus
Clearly, new employees to the company or division should be required to go through training, but requiring that everybody attend refresher courses is also a good idea. And don't hesitate to call a meeting if new threats arise or any sudden changes occur to keep everyone up to date.
Administrator Training
Obviously, training sessions for your IT personnel have to be a lot more in depth because they'll be the ones who set up and configure policies, and they'll also be the first responders to any security emergency.
It's important to cover every aspect of your security policy with these people. And be sure they understand the correct ways to escalate issues in case of an emergency. Reacting to a security emergency is pretty stressful, and you don't want your administrators to panic or feel isolated if one occurs. Making sure they know where their lifelines are and how to reach them quickly if they need backup will relieve a lot of pressure when something nasty happens.
Access Control Hardware
Access control hardware comprises a category of devices that are used to identify and authenticate users. They combine a technical physical control (the device) and administrative controls (password policies and procedures) to create an access control system.
While access control vestibules/mantraps may justify their cost in some high-security scenarios, not all situations require them. Door controls should be used to prevent physical access to important infrastructure devices such as routers, switches, firewalls, and servers.
Proximity or badge readers are door controls that read a card from a short distance and are used to control access to sensitive rooms. These devices can also provide a log of all entries and exits. Usually, a card contains the user information required to authenticate and authorize the user to enter the room.
Biometrics
Biometric systems are designed to operate using characteristic and behavioral factors. While knowledge factors (password, PIN, or something you know) are the most common authentication factors used, characteristic factors represent something you are (fingerprint, iris scan), while behavioral factors represent something you do (signature analysis).
Multifactor authentication is achieved by combining authentication factors. When two factors are combined, such as a retina scan (characteristic factor) and a password (knowledge factor), dual-factor authentication is required. When three factors are combined, such as a retina scan (characteristic factor), a password (knowledge factor), and signature analysis (behavioral factor), then multifactor authentication is in effect.
One of the issues with biometrics is the occurrence of false positives and false negatives. A false positive is when a user that should not be allowed access is indeed allowed access. A false negative, on the other hand, is when an authorized individual is denied passage by mistake.
Locking Racks
Rack devices should be secured from theft. There are several locking systems that can be used to facilitate this. These locks are typically implemented in the doors on the front of a rack cabinet:
- Swing handle/wing knob locks with common key
- Swing handle/wing knob locks with unique key
- Swing handle with number and key lock
- Electronic locks
- Radio-frequency identification (RFID) card locks
Locking Cabinets
There are many items that should not be left just lying around a facility. These items include laptops, smartphones, and sensitive documents. A good example of a locking cabinet is shown in Figure 20.2. Each drawer is secured by a lock.
FIGURE 20.2 Locking cabinet
Access Control Vestibule (Previously Known as a Mantrap)
A mantrap or vestibule is used to control access to the vestibule of a building. It is a series of two doors with a small room between them. The user is authenticated at the first door and then allowed into the room. At that point, additional verification will occur (such as a guard visually identifying the person) and then they are allowed through the second door. These doors are typically used only in very high-security situations. They can help prevent tailgating. A mantrap design is shown in Figure 20.3.
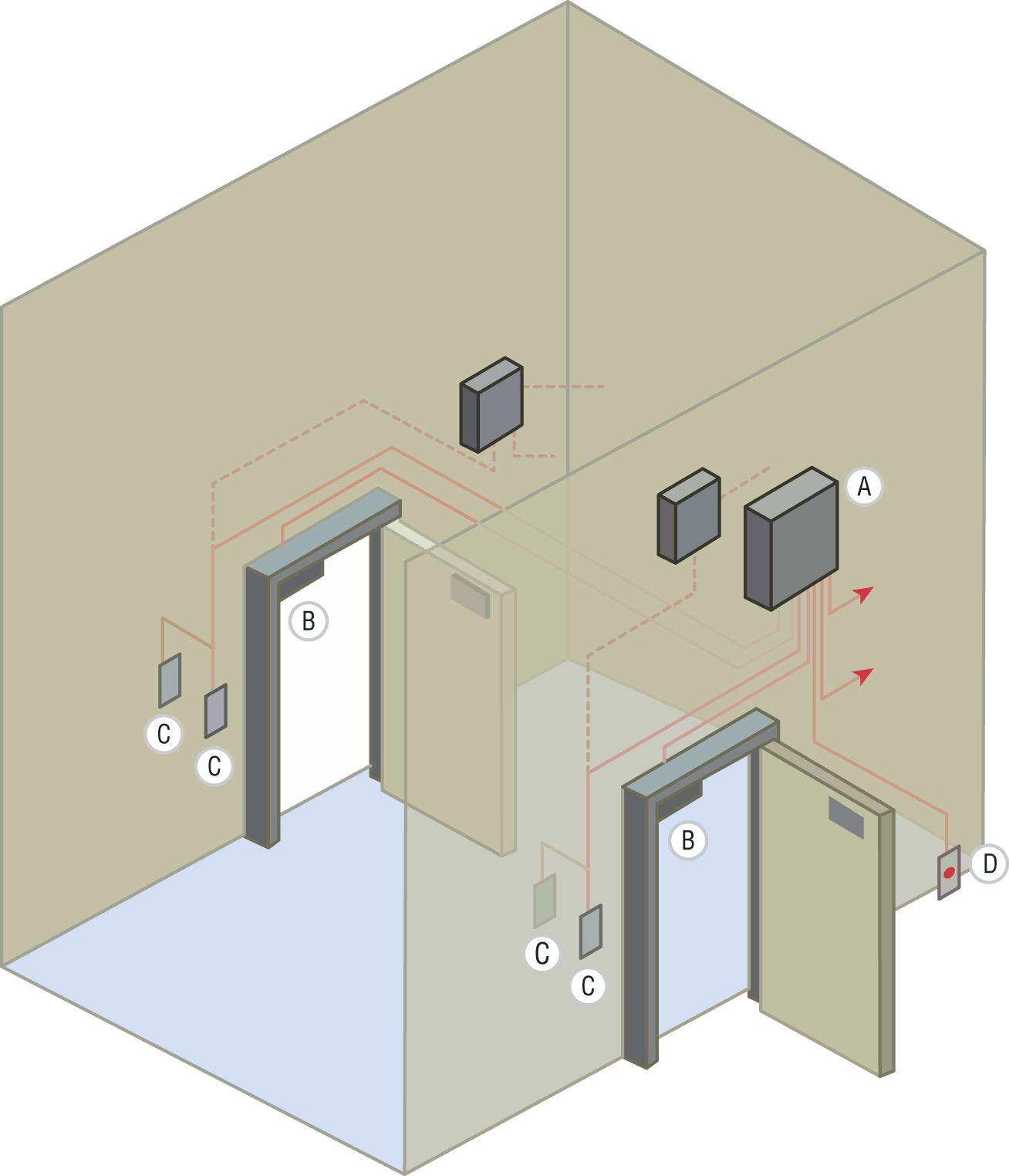
FIGURE 20.3 Access Control Vestibule/Mantrap
Smart Lockers
Smart lockers comprise a new storage locker option born in the last decade. A smart lock is an electromechanical lock that is designed to perform locking and unlocking operations on a door when it receives such instructions from an authorized device using a wireless protocol and a cryptographic key to execute the authorization process. With smart locks, lockers can be assigned on-the-fly, reset, audited, and reassigned using simple desktop or mobile software. They can utilize many lock choices (RFID or NFC, others with digital touch pads).
Asset Disposal
The final steps in the asset life cycle is the disposal of the asset when it is no longer of use or when it is replaced with a better alternative. Whether you intend to donate, throw away, or repurpose the asset, you must consider what data is on the device. In the following sections, you'll learn some of the considerations and techniques involved.
Factory Reset/Wipe Configuration
Many device vendors offer a factory reset that is mostly used to clear out the accumulated gunk and start over, thus improving performance. Yes, it does appear to remove all data, but not really. This is not a technique on which to rely if there is sensitive data involved.
You also hear quite often about the remote wipe feature that can be used to remove data when a device is stolen. While these wipe processes are different, it is not generally accepted to get rid of sensitive data. Moreover, if the device is turned off or the battery has run down, remote wipe does not work.
Sanitize Devices for Disposal
When the time comes to decommission an asset such as a server or a hard drive, the handling of any data that remains is a big security issue. Whenever data is erased or removed from a storage media, residual data can be left behind. This can allow data to be reconstructed when the organization disposes of the media, resulting in unauthorized individuals or groups gaining access to the data. Media that security professionals must consider include magnetic hard disk drives, solid-state drives, magnetic tapes, and optical media, such as CDs and DVDs. When considering data remanence, security professionals must understand the following methods:
- Clearing includes removing data from the media so that the data cannot be reconstructed using normal file recovery techniques and tools. With this method, the data is only recoverable using special forensic techniques.
- Purging, also referred to as sanitization, makes the data unreadable even with advanced forensic techniques. With this technique, data should be unrecoverable.
- Overwriting is a technique that writes data patterns over the entire media, thereby eliminating any trace data.
- Degaussing exposes the media to a powerful, alternating magnetic field, removing any previously written data and leaving the media in a magnetically randomized (blank) state.
- Encryption scrambles the data on the media, thereby rendering it unreadable without the encryption key.
- Physical destruction involves physically breaking the media apart or chemically altering it. For magnetic media, physical destruction can also involve exposure to high temperatures.
Most of the countermeasures given work for magnetic media. However, solid-state drives present unique challenges because they cannot be overwritten. Most solid-state drive vendors provide sanitization commands that can be used to erase the data on the drive. Security professionals should research these commands to ensure that they are effective. Another option for these drives is to erase the cryptographic key. Often a combination of these methods must be used to fully ensure that the data is removed.
Data remanence is also a consideration when using any cloud-based solution for an organization. Security professionals should work with their organization when negotiating any contract with a cloud-based provider to ensure that the contract covers data remanence issues, although it is difficult to determine that the data is properly removed. Using data encryption is a great way to ensure that data remanence is not a concern when dealing with the cloud.
Summary
In this chapter you learned the basic concepts, terms, and principles that all network professionals should understand to physically secure a network.
You learned about detection methods such as cameras and motion detection systems. We also discussed prevention methods such as training, locking cabinets, and rack locks. Finally you learned about the proper way to dispose of assets in a secure manner.
Exam Essentials
- Explain detection methods. These include cameras, motion-detection systems, asset tags, and tamper-detection software.
- Describe common prevention methods. This includes the employee training, access control hardware, badge readers, biometrics, locking racks, locking cabinets, access control vestibules/mantraps, and smart lockers.
- Identify asset disposal issues. These consist of proper identification and application of the proper destruction method, including factory reset, remote wipe, purging, degaussing, and overwriting.
Written Lab
Complete the table by filling in the appropriate definition for each term.
You can find the answers in Appendix A.
| Term | Definition |
|---|---|
| Purging | |
| Clearing | |
| Destruction | |
| Overwriting |
Review Questions
You can find the answers to the review questions in Appendix B.
- Which of the following would not be considered a detection method?
- Camera
- Motion sensor
- Tamper alert software
- Employee training
- Which motion detection system operates by identifying changes in heat waves in an area?
- Infrared
- Electromechanical
- Photelectric
- Acoustical
- Which motion-detection system operates by emitting a magnetic field and monitoring that field?
- Infrared
- Capacitance
- Wave motion
- Acoustical
- An open case warning is an example of which of the following?
- Motion detection
- Asset tagging
- Tamper detection
- Dynamic alert
- Which of the following is the most effective way to stop social engineering attacks?
- Policies
- Penalties
- Training
- Auditing
- Which of the following uses a characteristic factor for authentication?
- Biometrics
- Secondary authentication
- Identity proofing
- Hybrid authentication
- Which of the following is not an example of multifactor authentication?
- Password and PIN
- Password and iris scan
- Retina scan and USB fob
- USB fob and smart card
- Which of the following occurs when a legitimate user is denied authentication in a biometric system?
- False negative
- True negative
- True positive
- False positive
- Which of the following is also known as an access control vestibule?
- Trapdoor
- Mantrap
- Smart door
- Turnstile
- Which of the following is managed using simple desktop or mobile software?
- Proximity door
- Smart locker
- Faraday cage
- Black box
