10
Exploring Wireless Standards and Technologies
Wireless networking has been around for many years, and it’s continuously being improved to support new technologies and capabilities for efficiently delivering messages over a non-wired network. It provides the convenience of mobility, allowing employees to use laptops, smartphones, and tablets within the vicinity of their company’s wireless network. Moreover, wireless networking allows network professionals to create a metaphorical bridge between wired networks and wireless devices by using access points. It also allows wireless routers to allow these wireless clients to access the resources on a wired network. Therefore, users with a wireless network adapter can roam around the office or building while staying connected to the corporate network.
During the course of this chapter, you will be exploring various wireless communication standards that are commonly used within the industry and how each standard differs from the other. You will gain a solid understanding of various wireless networking concepts, such as discovering various wireless frequencies, how wireless devices communicate, and the types of antennas that are used to transmit messages. Lastly, you will dive into understanding various wireless security standards that are used to provide privacy using data encryption algorithms between clients and access points on a wireless network.
In this chapter, we will cover the following topics:
- Exploring wireless networking
- Delving into wireless security
- Exploring cellular technologies
Let’s dive in!
Exploring wireless networking
When designing a wireless network for an organization, it’s important to consider the components needed, the number of wireless clients that need access to the wireless network, and the location of these clients within an organization. The components needed are access points or wireless routers based on the size of the organization and the number of users on the wireless network.
For instance, wireless routers are common wireless networking devices that are commonly found within Small Office Home Office (SOHO) networks. This type of wireless networking device is simply a router, switch, and access point within a single unified device. A wireless router is suitable for small wireless networks such as those within homes and small office environments.
The following snippet shows the back of a Cisco Linksys 160N wireless router:
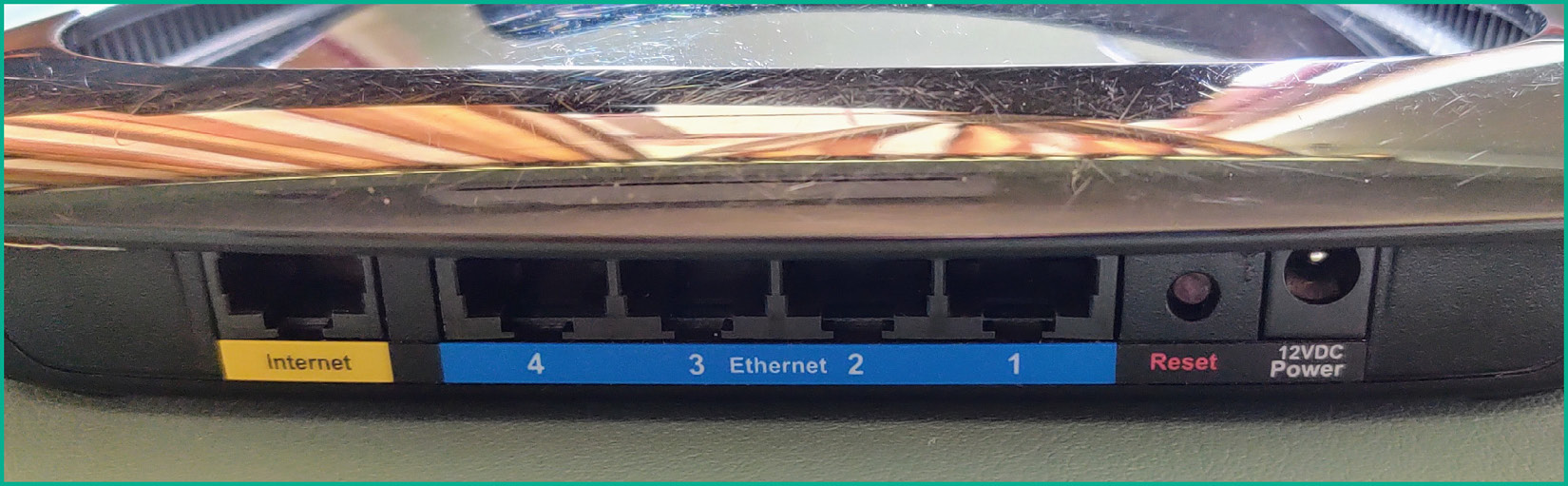
Figure 10.1 – Wireless router
As shown in the preceding snippet, there are five interfaces that allow wired ethernet connections. The Internet port, sometimes referred to as the Wide Area Network (WAN) port, allows a network professional to establish a wired connection from the internet modem to the wireless router for the purpose of providing internet access to devices that are connected to the wireless router. Without internet access on the wireless router, wireless clients will be able to communicate with each other but won’t be able to access any resources on the internet.
The following diagram shows the connection between an internet modem and a wireless router:

Figure 10.2 – Providing internet to a wireless router
Additionally, the wireless router has one or more ethernet ports that operate like a typical network switch, allowing network professionals to interconnect clients with each other using a wired connection. The built-in switch within the wireless routers functions like a typical network switch that forwards frames between devices on the wired and wireless networks. Therefore, all devices that are connected to the wireless router, whether on the wireless or wired network, will be able to communicate and exchange messages with each other.
Furthermore, the wireless router leverages the built-in access point feature to generate radio frequencies within the 2.4 GHz and/or 5 GHz band to create a wireless network, allowing wireless clients to connect to the device. The router functionality allows devices that are connected to the wired and wireless network types to intercommunicate with each other. Additionally, the router feature allows network professionals to create a Dynamic Host Configuration Protocol (DHCP) server within the wireless router to provide IP addresses, subnet mask, default gateway, and Domain Name System (DNS) server addresses to all connected clients.
The following diagram shows different networks that exist when using a wireless router:

Figure 10.3 – Wireless networking
As shown in the preceding diagram, clients that are connected to the wireless network that’s generated by the wireless router use IP addresses on the 172.16.1.0/24 network, whereas the network that exists between the modem and the internet port of the wireless router is in the 192.168.1.0/24 network range. Hence, the router function is used to forward packets between these different IP subnets and to the internet.
In medium-sized to large organizations, access points are commonly implemented to provide wireless coverage to all areas within a building. Access points simply generate a radio frequency that is supported by wireless devices, allowing wireless clients, such as mobile devices, to establish a connection to the access point and access the resources on the wired network. Unlike wireless routers, access points do not have any routing or switching functionality; they are simply used to create a wireless network and forward frames to the wired network and vice versa. This is a thin-client access point, one that has no configuration capability. They are connected to a wireless controller. Fat-client access points, on the other hand, can be individually configured and don’t require a controller.
Clients that are connected to access points receive an IP address that is provided to the clients on the wired network. Hence, access points are simply used to allow wireless clients to access resources on the organization’s network seamlessly as if they were connected to the wired network.
Up next, you’ll learn how a wireless router and access points advertise themselves to nearby wireless clients within the vicinity while wireless clients search for previously associated wireless networks.
Beacons, probes, stations, and SSIDs
The Service Set Identifier (SSID) is simply the name of the wireless network that allows wireless clients to identify one wireless network from another. Imagine if setting an SSID was not an option on the wireless router or access point, it’ll be quite challenging for users to identify their wireless network from another network. Home users and organizations usually change the default SSID that’s configured by the vendor of the device to a name that’s recognizable. However, as a good security practice, organizations should not set an SSID that can easily identify the organization’s network or lure a hacker.
For instance, many IT professionals usually configure their wireless networks with SSIDs that are easily identifiable such as using their company’s name. While this concept provides a lot of convenience in allowing the employees of an organization to easily discover the wireless network within the vicinity, it also helps a hacker to easily identify a target wireless network. When a wireless router or access point is powered on, the firmware and configurations are loaded in memory and the device begins to broadcast its presence within the vicinity.
Wireless routers and access points continuously broadcast beacons that contain specific information about themselves such as the SSID, wireless encryption standard, operating channel, and even their Media Access Control (MAC) address. The beacons are detected and inspected by any device that has a supported wireless network adapter such as smartphones, tablets, Internet of Things (IoT) devices, and laptops, therefore allowing a user to identify wireless networks within the vicinity.
The following diagram shows a wireless router broadcasting beacons:

Figure 10.4 – Wireless beacons
As shown in the preceding diagram, as wireless clients move into the range of the wireless signal that’s generated by the wireless router or access points, they will be able to capture the beacons and inspect them to determine the wireless network that’s close by.
Wireless routers and access points provide the capability of disabling the SSID broadcast as a technique of hiding your wireless network from wireless clients. However, this technique does not add any layer of security as a seasoned hacker or cybersecurity professional can discover a hidden wireless network within a few seconds using very specialized skills, such as performing wireless reconnaissance by capturing beacons and probes. By analyzing the data within the captured beacons and probes, a seasoned hacker will be able to determine the type of clients and wireless routers within the area, hidden wireless networks, type of security configurations applied to the networks, and even the approximate distance between the attacker’s machine and the target wireless router and clients.
If an IT professional chose to disable the SSID broadcast feature, the wireless router will not insert the SSID but still include all other information within each beacon that will be broadcasted.
The following snippet shows the basic configuration page of a wireless router:
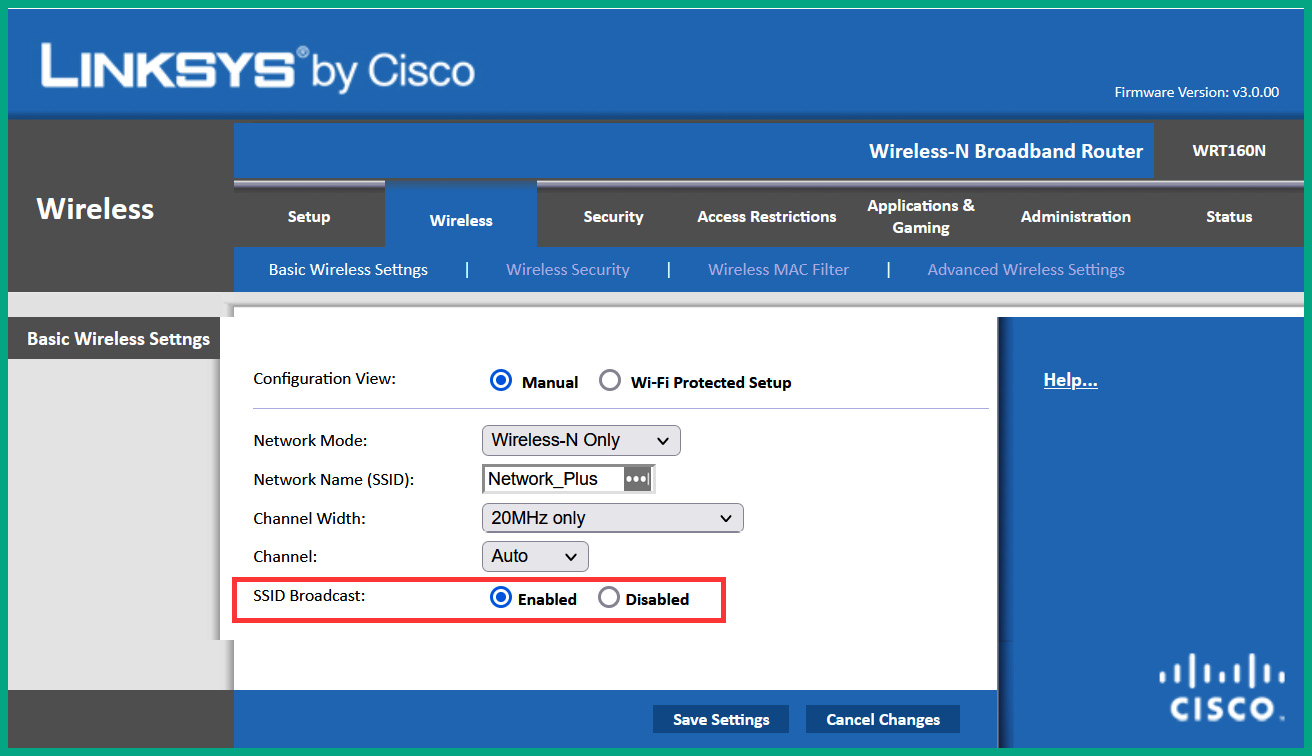
Figure 10.5 – Wireless router basic configuration page
As shown in the preceding snippet, the basic wireless configuration page allows a user to configure the wireless operating standard, SSID, channel width, channel number, and whether to enable or disable the SSID broadcast on the device.
When a wireless client (station) establishes a connection to a wireless router or access point, it’s referred to as an association. When a client joins a wireless network, the client saves both the SSID and password into a Preferred Network List (PNL) that allows the user to easily re-join the same wireless network in the future. This enables the wireless network adapter on a client to begin sending probes for each entry within the PNL on the device. The probes allow the client to seek any of the wireless networks via their SSIDs that are stored within the PNL. Once a wireless network is found within the signal range, the client will attempt to create an association with the wireless network.
Important note
Wireless clients, such as laptops, smart TVs, and IoT devices, are examples of stations on a wireless network. The terms wireless clients and stations are used interchangeably during discussions and literature.
A seasoned hacker or cybersecurity professional can capture the probes to determine the wireless networks that are stored on a client and attempt to perform an AP-less attack to retrieve the password/passphrase of an organization’s wireless network. However, many newer devices are now allowing IT professionals to prevent the client from automatically connecting to a saved wireless network that’s within range.
Frequencies, ranges, and channels
The Institute of Electrical and Electronics Engineers (IEEE) is the governing body that created and currently maintains the standards and frameworks for both electrical and electronics specifications that include computers and wireless networking. The 802 committee of the IEEE holds the responsibility of creating and maintaining many common standards that are used by both computing and networking devices, such as Ethernet, Bluetooth, and Wi-Fi. The .11 working group of the 802 committee is specifically responsible for the wireless networking standard such as the IEEE 802.11 wireless networking standard within the industry.
The following tables show the different IEEE 802.11 wireless standards:
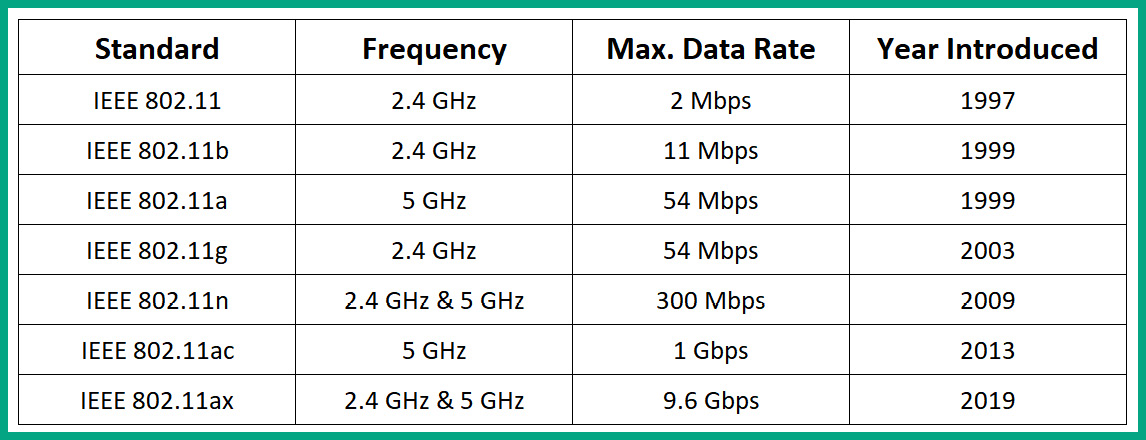
Figure 10.6 – Wireless standards
As shown in the preceding table, there are many generations of IEEE 802.11 within the wireless networking industry. The original IEEE 802.11 standard was designed to operate on a 2.4 GHz frequency and supported a maximum data transfer rate of 2 Megabits per second (Mbps), however, this original standard was not implemented on any device. IEEE 802.11b became the first official wireless standard that was implemented on devices that operated on 2.4 GHz and provided a maximum data transfer rate of 11 Mbps.
IEEE 802.11a operates on the 5 GHz frequency and provides a maximum data transfer rate of 54 Mbps. The IEEE 802.11g standard operates at 2.4 GHz and supports maximum transfer rates of 54 Mbps. However, IEEE 802.11n (Wi-Fi 4), also known as Wi-Fi 4, operates on both the 2.4 GHz and 5 GHz frequencies and supports Multiple In Multiple Out (MIMO), which improves the maximum data transfer rate up to 300 Mbps. Later wireless standards, such as IEEE 802.11ac (Wi-Fi 5), operate on the 5 GHz frequency and provide a maximum data transfer rate of 1 Gigabit per second (Gbps).
The latest version of the wireless standard, IEEE 802.11ax (Wi-Fi 6), uses both 2.4 GHz and 5 GHz frequencies and provides a maximum data transfer rate of 9.6 Gbps. Overall, the speed and bandwidth that are supported on wireless networks are aligning with the speeds on wired networks, allowing users to exchange messages very quickly.
The IEEE 802.11 standards use the 2.4 GHz range, which has a total of 14 channels that range from 2.400 GHz to 2.490 GHz, with each individual channel having a width size between 20 MHz to 22 MHz for transporting messages between devices on the wireless network. Since these individual channels are very close to each other, it’s recommended to configure the wireless routers and access points with non-overlapping channels, such as channels 1, 6, and 11.
The following diagram shows a representation of the non-overlapping channels:

Figure 10.7 – Non-overlapping channels
As shown in the preceding diagram, channels 1, 6, and 11 are the only channels within the 2.4 GHz range that do not overlap with each other. However, channel 14 on the 2.4 GHz is restricted for usage in many countries, hence you will commonly discover wireless networks are using channels 1 to 13. It’s important to ensure your organization’s access points aren’t using any channels that are overlapping with other access points within the vicinity as it will create interference and affect the performance of the wireless network.
However, the earlier generations of IEEE 802.11 use the 2.4 GHz range and as a result, many organizations and home users who already have an existing wireless network are using the 2.4 GHz range. Therefore, if you were to implement a new wireless router or access point within your network, there’s a high possibility that another access point within the same vicinity is using an overlapping channel as your wireless network. This issue is due to the limited number of available channels in the 2.4 GHz range for the IEEE 802.11 wireless network.
Tip
Using a Wi-Fi analyzer tool, such as inSSIDer from Metageek or the Wi-Fi Analyzer app from Microsoft Store, allows network professionals to view all nearby wireless networks, their operating frequencies and channels, SSIDs, vendors, and much more. Additionally, Wi-Fi analyzers help determine whether your wireless network is using an overlapping channel with another nearby Access Point.
The 5 GHz range supports a lot more channels compared to the 2.4 GHz band that ranges from channels 36 to 165. Unlike the 2.4 GHz band, the 5 GHz band allows devices to use channels 20 MHz, 40 MHz, 80 MHz, and 160 MHz using a technology known as channel bonding. Using channel bonding in the 5 GHz band allows wireless devices to transport more data over the wireless network, hence the 5 GHz band supports more bandwidth compared to the 2.4 GHz band.
The following table shows a comparison between the 2.4 GHz and 5 GHz bands:
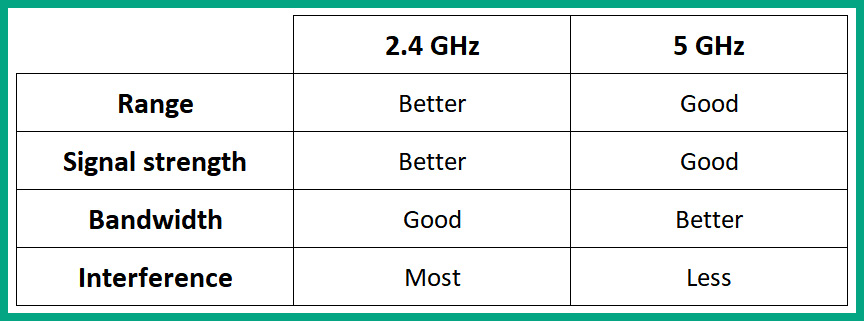
Figure 10.8 – Wireless band comparison
As shown in the preceding table, the 2.4 GHz band provides better signal strength, allowing the radio frequency signal to travel further away from the wireless router or access point, overall providing better range. The 5 GHz band, on the other hand, operates on a higher frequency and does not provide the same signal strength or range. However, the 5 GHz band supports more channels and channel bonding to provide greater bandwidth and less interference compared to the 2.4 GHz band.
SSID
The SSID allows network professionals to create a network name that’s 32-bits in length, which helps users easily identify their preferred wireless network. When implementing a wireless network infrastructure within a building, office space, or home, it’s important to understand the characteristics of various types of wireless network infrastructure deployment.
The topology of a wireless network can be infrastructure, ad hoc, or mesh modes. In infrastructure mode, a wireless Access Point is used as the network intermediary device to allow wireless clients to connect and share resources. While the ad hoc mode does not use any wireless intermediary devices, a wireless device such as a laptop can directly connect to another laptop to share resources. Lastly, in mesh mode, all wireless devices establish a connection with each other, hence creating a mesh topology.
A Basic Service Set (BSS) is the most common type of wireless infrastructure that contains a single wireless router or access point, allowing wireless clients within the vicinity to connect to it. The wireless router or access point is simply the intermediary wireless networking device that’s used to forward WLAN frames between wireless clients and onto the wired network known as a Distributed System Service (DSS).
The following diagram shows a typical wireless network that’s configured as a BSS:

Figure 10.9 – BSS wireless infrastructure
Important note
Any wireless network that uses a wireless router or access point as the wireless network intermediary device is commonly referred to as infrastructure mode.
The Extended Service Set (ESS) is commonly found within medium-sized to large organizations with multiple access points connected to the same DSS (wired network). This wireless network exists when network professionals implement two or more access points that are connected to the same wired network. Each access point is configured with the same SSID, allowing a user with a laptop to roam between different access points within the office space or building of the organization. Roaming allows a user to automatically connect to another access point with the same SSID when moving out of range from one access point that has a weaker signal and closer to another that is broadcasting a stronger signal with the same SSID.
The following diagram shows a typical ESS wireless infrastructure:
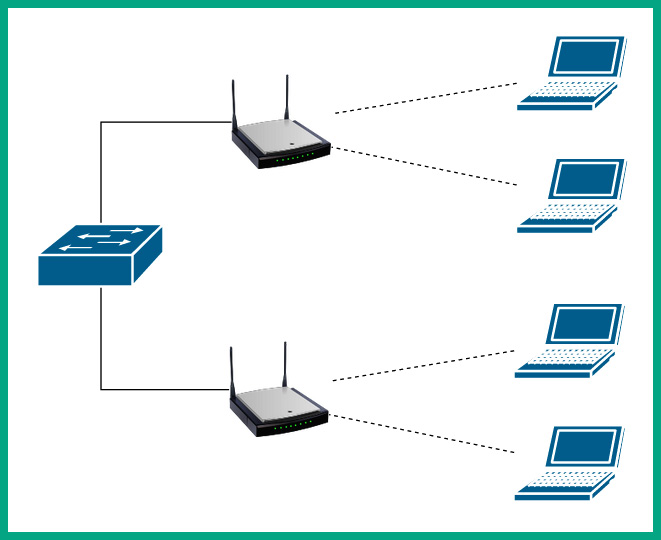
Figure 10.10 – ESS wireless infrastructure
As shown in the preceding diagram, there are two access points that are configured with the same SSID that allows wireless clients to automatically connect to the access point with the better signal. When a wireless client is disconnecting from one access point and connecting to another, the user will experience a temporary drop in wireless network connectivity until the wireless client re-establishes an association with the new access point.
An Independent Basic Service Set (IBSS) is a wireless network that does not use a wireless router or access point. In an IBSS, each wireless client is connected to every other wireless client within the vicinity, creating a wireless mesh network. This type of wireless network allows clients to share their resources directly with another client and it’s commonly referred to as ad hoc mode.
The following diagram shows a typical IBSS wireless network:

Figure 10.11 – IBSS wireless network
As shown in the preceding diagram, each wireless client, such as a laptop, can be configured to operate as an access point, allowing other wireless clients to connect and share resources with each other without the need for a dedicated wireless router.
Antenna types
When implementing a wireless infrastructure within an organization, the placement of wireless routers and access points is important to ensure there is proper coverage of the wireless signal for all wireless clients within a building or office space. If a wireless client is unable to receive an acceptable quality of signal from a wireless router, the transmission speeds for exchanging data between the wireless router and the wireless client is affected. Hence, it’s important for network professionals to perform a wireless LAN (WLAN) survey to determine the number of access points needed and the placement of each access point to ensure there’s full coverage of the organization.
There are various types of antennas that are installed on wireless routers and access points; each type of antenna determines how the signal is focused in a direction. For example, omnidirectional antennas do not focus the signal in a specific direction but emit the signal all around the antenna in any direction. Dipole antennas are an example of omnidirectional antennas; these are commonly within wireless radio devices and mobile cellular towers to send and receive signals in all directions.
The following is a picture of an omnidirectional antenna with an external network adapter:

Figure 10.12 – Omnidirectional antenna
While omnidirectional antennas work great to provide signal coverage within a home, office space, or building, it’s not efficient in focusing a wireless signal in a specific direction. Directional antennas are better at radiating their signal more efficiently in a single direction. The following are examples of common directional antennas:
- Yagi antenna
- Dish antenna
- Parabolic antenna
Some of the wireless signals may radiate the signal to the sides of a focal point of a directional antenna while still focusing most of the signal in a specific direction.
MIMO concepts
Older wireless routers, access points, and wireless network adapters on clients were designed with a single antenna, which allowed the device to send and receive WLAN frames on the same antenna. This concept was referred to as Single In Single Out (SISO).
The following diagram shows an example of SISO communication between an access point and a client:
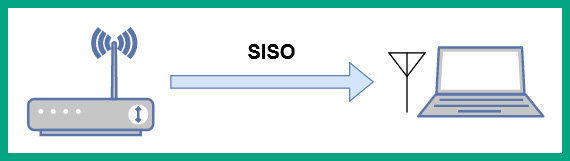
Figure 10.13 – Observing SISO
As shown in the preceding diagram, both the wireless client and wireless router are using the same antenna on their devices to send and receive messages. While this SISO allowed devices to communicate with each other, it was not efficient for sending more traffic on the wireless network.
Wireless device manufacturers began implementing multiple antennas on wireless routers, access points, and clients, allowing multiple antennas to send and receive messages simultaneously with the intention of increasing the throughput of the wireless network. This concept is referred to as Multiple In Multiple Out (MIMO).
The following diagram shows an access point and client using MIMO to exchange messages:
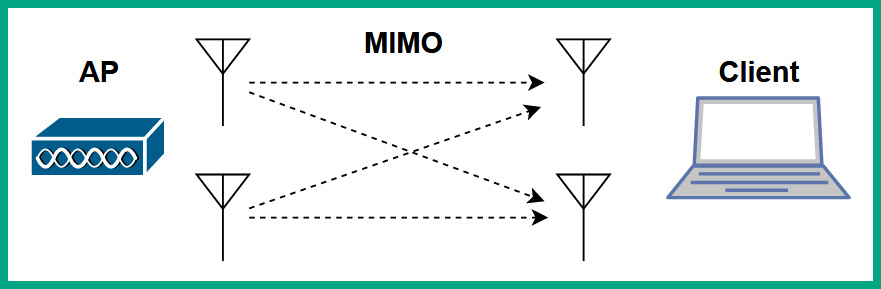
Figure 10.14 – Observing MIMO
On a wireless network with multiple wireless clients connected to the same wireless router, the wireless router can only transmit a stream of messages to one wireless client at a time, then to another client, and so on. Therefore, all wireless clients that are associated with the same wireless router or access point do not receive messages at the same time. This is referred to as Single User Multiple In Multiple Out (SU-MIMO).
The following diagram shows a representation of SU-MIMO on a wireless network:

Figure 10.15 – Observing SU-MIMO
As shown in the preceding diagram, the access point has multiple streams for each wireless client but is unable to send the streams to each client at the same. Therefore, the access point will forward the stream for each client one at a time, ensuring messages are delivered to their destinations as quickly as possible.
However, wireless networks that use SU-MIMO have the limitation of forwarding a data stream to one wireless client at a time. The implementation of Multi-User Multiple Input Multiple Out (MU-MIMO) allows a wireless router or access point to forward all data streams to all wireless clients at the same time.
The following diagram shows a representation of MU-MIMO on a wireless network:

Figure 10.16 – Observing MU-MIMO
As shown in the preceding diagram, the access point is distributing multiple data streams to each wireless client at the same time.
Having completed this section, you have learned about the fundamentals of wireless networking and infrastructure that are commonly implemented within organizations. In the next section, you will learn about various wireless security standards and the need for proper security on wireless networks.
Delving into wireless security
As an aspiring network professional, it’s essential to gain a solid understanding of wireless security concepts and techniques that are used to improve the security posture of a wireless network within organizations. Wireless security helps network professionals prevent unauthorized users from accessing the resources and prevent threat actors, such as a hacker, from capturing sensitive data that’s exchanged between devices on the wireless network.
As more organizations implement wireless networks to support their mobile workforces, such as those who are using laptops and tablet computers, hackers are always looking for the low-hanging fruit such as the weakest points that can be easily compromised within an organization; wireless networks can be compromised as long as the hacker is within the vicinity of the wireless signal emitting from the access point. Hence, network professionals need to implement proper security solutions and best practices to reduce the risk of a potential cyber-attack on their systems and network.
Wireless encryption standards
Wired Equivalent Privacy (WEP) was one of the first generations of wireless security standards that were implemented on IEEE 802.11b wireless networks. The WEP security standard used the Rivest Cipher 4 (RC4) encryption algorithm to ensure confidentiality between the access point and wireless clients. However, many unresolved security vulnerabilities were found within the RC4 encryption algorithm that allow threat actors to easily compromise IEEE 802.11 wireless networks that used the WEP wireless security standard.
The following are key points about WEP:
- Uses a weak encryption algorithm
- Uses a small Initialization Vector (IV), which is static and does not change, therefore increasing the likelihood of a threat actor determining the IV value that’s exchanged between devices
- Uses 64-bit and 128-bit key sizes during the data encryption process
- Uses the RC4 stream cipher for data encryption
- Provides a 24-bit Cyclic Redundancy Checksum (CRC) for integrity checking
The Wi-Fi Protected Access (WPA) wireless security standard became the successor and replacement for the WEP security standard for wireless networks. WPA used a 128-bit key to perform data encryption on each WLAN frame by using the RC4 encryption algorithm with Temporal Key Integrity Protocol (TKIP). TKIP ensures each WLAN frame was encrypted with a unique key before transmitting the frame over the wireless network. This technique simply inserted a sequence counter within each WLAN frame that prevented a threat actor, such as a hacker, from performing a replay attack on the wireless network. While WPA is using RC4 with TKIP, there are security vulnerabilities within both algorithms that allow hackers to easily compromise WPA wireless networks. Additionally, WPA provides a 48-bit CRC with a Message Integrity Check (MIC) for integrity checking for each WLAN frame that’s transmitting over the network.
The following are key points of WPA:
- Uses a weak encryption algorithm
- Uses TKIP to encrypt each WLAN frame with a unique key
- Uses 128-bit keys during the data encryption process
- Uses the RC4 data encryption algorithm
- Provides a 48-bit CRC for data integrity
Wi-Fi Protected Access 2 (WPA2) is the successor and replacement for the WPA wireless security standard. WPA2 uses the Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP) that is implemented within the Advanced Encryption Standard (AES) data encryption algorithm. CCMP allows AES to encrypt data within 128-bit blocks with a 128-bit key size. AES with CCMP prevented hackers from decrypting any messages that were exchanged over wireless networks that use WPA2 as the preferred wireless security standard.
Wi-Fi Protected Access 3 (WPA3) is currently the strongest and latest wireless security standard that uses Simultaneous Authentication of Equals (SAE) for data encryption. When WPA3 is implemented on personal networks, it uses a 128-bit key for data encryption and a 192-bit key on enterprise networks. Many new wireless routers and access points are supporting WPA3, however, there are many wireless clients supporting up to WPA2 standards. WPA3 supports backward compatibility for wireless clients that support WPA2, however, the wireless router or access point will scale down its wireless security standard from WPA3 to WPA2 to support older wireless clients. As a result, once the wireless router or access point uses WPA2, it inherits all of the security vulnerabilities of the older wireless security standard, such as brute force attacks, to retrieve the password/passphrase for the wireless network.
Authentication methods
After configuring the wireless security standard on a wireless router or access point, it’s important to configure the authentication method for the wireless network. The authentication method simply defines how the wireless router or access point is going to validate an authorized wireless client before allowing access to the resources on the wireless network.
The Pre-Shared Key (PSK) allows the network professional to configure a password or passphrase on the wireless router or access point and it’s shared with authorized users. When using PSK, all authorized users will know and share the same key for the network. However, if the key was shared with someone who is no longer authorized, the user will be able to access the wireless network provided that the network professional has not changed the key on the wireless router or access point.
Enterprise is another authentication method that allows network professionals to implement IEEE 802.1X for Network Access Control (NAC) using an Authentication, Authorization, and Accounting (AAA) server. The AAA server allows network professionals to create a user account for each authorized user for the wireless network on the centralized AAA server. Additionally, the network professional can configure authorization security policies on each user account that defines the user’s privilege on the network. Furthermore, a AAA server has the capabilities of creating a log message for each activity performed by an authenticated user on the network for accountability purposes.
The following diagram shows an enterprise network topology including an AAA server:
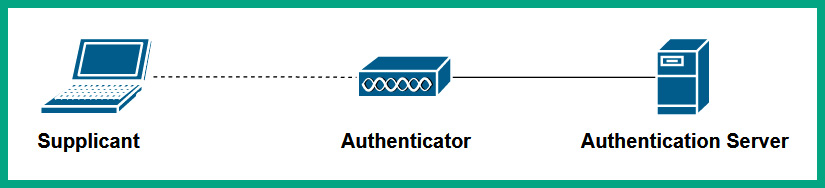
Figure 10.17 – AAA on an enterprise network
As shown in the preceding diagram, the Supplicant is simply the wireless client that wants to join the wireless network, the Authenticator is the wireless router or Access Point, and the Authentication Server is the centralized AAA server on the network. In this wireless infrastructure, each authorized user is assigned unique user credentials on the AAA server, therefore allowing better user management on the entire wireless network.
Important note
The authentication server can use either the Remote Authentication Dial-In User Service (RADIUS) or Terminal Access Controller Access Control System+ (TACACS+) authentication protocol. RADIUS is an open authentication protocol that is interoperable with different vendor devices while TACACS+ is a Cisco proprietary protocol that works with Cisco devices only.
Open authentication is the default authentication method on many wireless routers and access points. This method does not provide any authentication and allows any wireless device to connect and access resources on the wireless network. Additionally, this method does not provide any data encryption between the wireless client and the wireless router or access point. Many public wireless networks use open authentication that allows anyone in public to access the internet, however, this authentication method is not recommended for organizations as anyone can connect to it.
Wi-Fi Protected Setup (WPS) is an unsecure authentication method that eliminated the need to manually configure a password or passphrase on the wireless network. WPS simply provides an easy method to allow a wireless client authentication to a wireless network without the need for entering any credentials. Wireless routers or access points that are configured with WPS allow the network professional to simply press the physical WPS button of the wireless router and enable the WPS feature on the wireless client when a user needs to join the wireless network. Both devices will exchange a mutual 8-digit key, allowing the client to be authenticated to the wireless network. While WPS seems to be a convenient authentication method, it’s highly unsecure as the 8-digit pin that’s generated by the wireless router can be easily retrieved by hackers. Hence, it’s recommended to disable WPS whenever possible on wireless networks.
A captive portal is simply a web-based portal that prompts a user on a wireless client to provide their user credentials when connected to a wireless network. Captive portals are commonly implemented by network professionals within hotels and coffee shops.
Having completed this section, you have learned about the types of wireless security standards and the importance of ensuring a wireless network is secure from threat actors and unauthorized users. In the next section, you will explore various cellular technologies that are used by mobile telecommunication service providers around the world.
Exploring cellular technologies
Cellular technologies have been around for quite some time and telecommunication providers are continuously improving the quality of service provided to their customers. Cellular technologies simply allow us to intercommunicate with each other using a cellular phone by connecting to a mobile telecommunication provider’s network. While a mobile telecommunication service provider allows registered devices to connect to their network, the service provider has the ability to both track the geo-location of a connected mobile device and monitor the traffic types on their cellular networks.
2nd Generation (2G) is one of the most common generation cellular technologies within many countries around the world as it introduced both voice and text communication between mobile devices. 2G uses the Global System for Mobile Communications (GSM) technology that allows supported cellular devices to connect to the service provider’s network and exchange voice and text messages with other users. Additionally, mobile telecommunication service providers used both Enhanced Data rates for GSM Evolution (EDGE) and General Packet Radio Service (GPRS) to provide data services of a 2G cellular network to mobile devices.
On the 2G network, Time-Division Multiple Access (TDMA) was a very common access method that divides the available bandwidth into different or separate time slots, allowing each device to be allocated a specific amount of bandwidth at a time to exchange messages over the service provider’s network. The Code-Division Multiple Access (CDMA) is another common access method that ensures both the sender and receiver are transmitting messages using a mutually unique code pattern. This technique ensures both the sender and receiver are able to interpret the messages that are being exchanged between those devices over the service provider’s network.
The 3rd Generation (3G) is the successor of 2G that provides faster data services using both High Speed Packet Access (HSPA) and HSPA+. 3G used two technologies that are created from CDMA as the access method: the Universal Mobile Telecommunications Systems (UTMS) that introduced the High Speed Packet Access (HSPA) and HSPA+ that supports better data services over the mobile network. Additionally, 3G used CDMA2000 that introduced the Evolution Data Optimized (EVDO) technologies for better data rates.
The following are important key points about 3G data rates:
- Uses UMTS with Wideband Code Division Multiple Access (WCMDA) that supports up to 2 Mbps, HSPA with download speeds of 14.4 Mbps and upload speeds of 5.57 Mbps, and HSPA+ that provides 42 Mbps download speeds and 11.5 Mbps upload speeds.
- Uses CDMA2000 that supports both upload and download speeds of 153 Kbps and uses EVDO that has 14.7 Mbps download speeds and 5.4 Mbps upload speeds.
The 4th Generation (4G) is the successor of 3G that provides very high data rates using two technologies: Worldwide Interoperability for Microwave Access (WiMAX) that’s defined by IEEE 802.16 and Long-Term Evolution (LTE). These mobile technologies provide an upgrade migration path for systems and devices on both the UMTS and GSM networks.
The following are important key points about 4G data rates:
- WiMax operates at 70 Mbps while WiMax 2.1 operates at 1 Gbps
- LTE supports 300 Mbps, LTE-A support 1 Gbps, and LTE-Pro support 3 Gbps
Currently, the 5th Generation (5G) is the latest cellular technology within the mobile telecommunication industry. 5G still uses some of the existing 4G technologies within the mobile service provider’s network but provides huge gigabit speeds with very low latency between devices. However, 5G technologies use MIMO with beamforming to boost/concentrate the signal in a specific direction to ensure a mobile device has coverage to access the cellular network.
Having completed this section, you have learned about various types of cellular technologies such as 2G, 3G, 4G, and 5G.
Summary
Over the course of this chapter, you have learned the fundamentals of various wireless networking technologies, such as wireless infrastructure within organizations and the importance of understanding operating frequencies and channels. Additionally, you have learned about the difference between various wireless network topologies such as BSS, ESS, and IBSS. Furthermore, you have gained a solid understanding of the characteristics of various wireless security standards and the importance of using strong data encryption algorithms to improve the confidentiality of wireless networks. Lastly, you have explored various cellular networking technologies and how they are used within the mobile telecommunication industry.
We hope this chapter has been informative for you and is helpful in your journey towards learning networking and becoming a network professional. In the next chapter, Chapter 11, Assuring Network Availability, you will learn about the importance of network operations such as monitoring a network to ensure the availability of services and resources.
Questions
The following is a short list of review questions to help reinforce your learning and help you identify areas that require some improvement.
- Which of the following contains the SSID from an Access Point?
A. IBSS
B. Beacon
C. Probe
D. ESS
- Which of the following frequencies provides greater distance for Wi-Fi networks?
A. 5 GHz
B. 6 GHz
C. 2.4 GHz
D. All of the above
- Which of the following wireless network topologies allows network professionals to configure two or more Access Points with the same SSID that’s connected to the same wired network?
A. ISS
B. BSS
C. DSS
D. ESS
- Which of the following wireless security standards uses static, weak initialization vectors?
A. TKIP
B. WPS
C. WEP
D. WPA
- Which of the following wireless security standards uses TKIP to improve security?
A. WPA
B. WPS
C. WPA3
D. WEP
- Which of the following wireless security standards is not susceptible to a brute-force attack?
A. WPA
B. WPS
C. WPA3
D. WEP
- Which of the following authentication methods uses IEEE 802.1X?
A. Open Authentication
B. PSK
C. Enterprise
D. Captive portal
- When using AAA on a wireless network, which of the following devices has the role of the authenticator?
A. Laptop
B. Access point
C. RADIUS server
D. None of the above
- Which of the following cellular technologies uses EDGE for data services?
A. 2G
B. 4G
C. 5G
D. 3G
- Which of the following frequencies on an IEEE 802.11 network has the most interference?
A. 5 GHz
B. 6 GHz
C. 2.4 GHz
D. All of the above
Further reading
To learn more on the subject, check out the following links:
- What is a Wi-Fi or wireless network: https://www.cisco.com/c/en/us/solutions/small-business/resource-center/networking/wireless-network.html
- What is a Wi-Fi Router: https://www.linksys.com/us/r/resource-center/wifi-router/
- What is an Access Point: https://www.linksys.com/us/r/resource-center/what-is-a-wifi-access-point/
- Wireless Network Standard: https://www.technology.pitt.edu/help-desk/how-to-documents/wireless-network-standard
