14
Network Security Concepts
As an aspiring network professional, it’s important to have a solid foundation in various network security concepts and principles. Designing, building, and maintaining networks is quite awesome within the industry, but hackers are always looking for new ways to compromise organizations and steal their data. Network professionals design a network with network security principles and technical controls to prevent and mitigate cyber-attacks and threats to help safeguard the assets of the company.
In this chapter, you will understand the need for network security principles and how they are used to help prevent various cyber-attacks and threats. Additionally, you will explore various techniques that are commonly implemented within large organizations to improve the authentication process between users and systems. Lastly, you will explore security and business risk management techniques that are used to help organizations identify and mitigate various types of risks.
In this chapter, we will cover the following topics:
- Understanding network security
- Exploring authentication methods
- Risk management
Let’s dive in!
Understanding network security
Network security focuses on the techniques, policies, and security controls that are implemented within an organization’s network infrastructure to prevent various types of malicious activities, threats, and cyber-attacks. Without network security solutions, anyone, whether it’s an employee or a guest user, can intentionally or unintentionally perform malicious activities on the network that can cause damage to systems and data loss.
While threat actors are the typical people who will perform intentional cyber-attacks on a network, the trusted employees within the organization can perform unintentional actions, such as inserting a malware-infected USB drive into their work computer/systems without knowing the USB drive contains malware. Sometimes, an employee who is unaware of various threats may click a malicious link within a phishing email that’s created by hackers. Hence, network security professionals need to consider the risks that are involved if the organization’s assets are left unprotected.
Before implementing network security solutions and countermeasures to mitigate and prevent cyber-attacks and threats, it’s important to identify the assets within the organization. Assets are simply anything that has value or is valuable to the organization. Without being able to identify the assets within a company, network security professionals will not be able to properly implement the best countermeasures and security controls to protect the asset from threats.
The following are the three categories of assets:
- Tangible: The tangible assets are simply any physical objects that have value such as networking devices, security appliances, servers, computers, and furniture.
- Intangible: These are the intellectual property and digital assets, which do not have a physical form. Intangible assets are data, software and application licenses, business processes and procedures, and intellectual property.
- People: The employees of an organization are of value as they are the ones who perform the day-to-day business processes to ensure the business continues to operate and provide services to customers. The employees need to be protected from human-based cyber-attacks and threats such as social engineering attacks.
In the field of network security, various types of security controls and countermeasures are commonly implemented to mitigate and prevent cyber-attacks and threats while protecting tangible and intangible assets, as well as people, within a company. To further understand the network security concepts, next, you will take a deep dive into exploring the pillars of information security and how they work together to protect data, systems, networks, and people.
Confidentiality, integrity, and availability
Information security focuses on protecting the most valuable asset of any organization: data. Data is created each day by users on computers, servers, networking devices, and even security appliances. Data is created in many ways such as a user creating a document on their computer to write a letter to another person, creating a spreadsheet that helps forecast future financial projections for the later months, and even creating an email message. Networking devices and security appliances generate logs, which contain important information about various transactions and causes of errors that occurred on the network that will be helpful to network and security professionals for troubleshooting issues.
Overall, data is created very often on systems, and we don’t even realize it anymore as many organizations and people around the world have adapted to using digital technologies in their everyday lives. For instance, a computer with a word processing application was used to create and help develop the contents of this book while the author typed his thoughts using his keyboard. For each new document, file, or email created on a system such as a computer or a server, new data is created and written to the storage drives of the device.
Organizations store a lot of data that contains confidential information such as details that can be used to identify people; this type of data is commonly referred to as personally identifiable information (PII). The following are examples of PII:
- A person’s name
- Date of birth
- Credit card number
- Driver’s permit/license number
- Any biological characteristics such as fingerprints, facial geometry, and more
- Mother’s maiden name
- Social security number
- Bank account details
- Email address
- Telephone number
- Physical residential address
Additionally, healthcare providers store their patients’ details on their systems, which can be used to profile a specific patient. This type of data is commonly referred to as protected health information (PHI). The following are examples of PHI:
- The patient’s name
- Telephone number
- Email address
- Residential address
- Any dates on medical records such as date of birth, date of deceased, date of administration, and discharge of the health facility
- Social security number
- Driver’s permit/license number
- Biometric information about the patient
- Information about the patient’s mental or physical health
- The health care provider’s information for the patient
Nowadays, threat actors are developing more sophisticated malware such as ransomware, a type of crypto-malware that is designed to encrypt all the data on a system except for the operating system files and presents a payment window to the victim. By encrypting all the data on the system, the threat actor is holding your data hostage and requesting a ransom to be paid within a specific time frame; otherwise, the data will be wiped from the system. This technique is quite intelligent because threat actors can simply create ransomware and unleash it on the internet to compromise any connected systems that are vulnerable. Keep in mind that when ransomware infects a system, the threat actor can exfiltrate your data and sell it on the dark web.
To better understand how data can be vulnerable, the following are the various states of data you must know about:
- Data in motion: This is any data that is being sent from one device to another, either over a network or being transported using a portable storage device. Typically, devices are continuously exchanging messages with each other on the Local Area Network (LAN) within a building or over the internet. For instance, many network protocols that transport data over a network are unsecure by default, allowing hackers to intercept and capture sensitive information such as user credentials and confidential files. There are various techniques to protect data in motion, such as using secure protocols and Virtual Private Network (VPN) solutions.
- Data at rest: This is the data that is currently stored on a local or external storage drive that’s not being used by an application or transmitted over a network. If a hacker compromises a server, the hacker will look for any confidential data that’s on the local storage drives. Using disk and file encryption applications allows users to encrypt data and entire drives on a system to protect any data at rest.
- Data in use: This is any data is that currently being used or accessed by an application. This is the most vulnerable state of data. Simply put, imagine that you have created a password-protected document on your local disk drive to prevent unauthorized persons from reading the contents of the file. Whenever you need to access the file, it has to be decrypted and then viewed within the application. While an application is accessing data in its decrypted state, a hacker can compromise the system or application to access the data. To protect data in use, it’s recommended to use trusted applications and ensure both the application and operating system are up to date.
The three pillars of information security are implemented in both administrative and technical security controls within organizations to help protect assets, including data from cyber-attacks and threats. The following are three elements are the pillars of information security:
- Confidentiality: Confidentiality ensures that only authorized users have access to resources such as systems or data on a network. Without confidentiality on a system or network, anyone, such as hackers and unauthorized people, will be able to access sensitive and confidential information. Using secure network protocols and VPN technologies protects data in motion and using file and disk encryption applications allows a user to encrypt data at rest on a storage drive. Threat actors will be able to access encrypted data – they just won’t be able to use or consume it without the decryption key if the data is at rest.
- Integrity: Integrity ensures a message is not changed, modified, or altered in any way between the source and destination. Imagine sending a message such as an email to someone and, during the delivery process, a threat actor was able to intercept the message, read its contents, and modify the message before sending it off to the destination. The recipient, on reading the email, will not identify the message was altered during transmission. Using a trusted hashing algorithm allows users to validate whether a message was altered or not between a source and a destination. Another example is if you’re downloading a file from a trusted website with a provided hash. After the download is completed, you can compare the provided hash with the hash you’ve generated for the file. If both hash values are the same, the integrity is verified, and the file’s contents were not altered.
- Availability: Availability ensures the data and resources are available to authorized users. Various types of cyber-attacks focus on disrupting the availability of network services, applications, devices, and networks. For instance, threat actors commonly use a Distributed Denial of Service (DDoS) attack to disrupt public servers on the internet while preventing legitimate users from accessing the services. Network security professionals commonly implement cybersecurity solutions that are designed to mitigate and prevent cyber-attacks that are designed to affect the availability of systems and resources.
When implementing confidentiality, integrity, and availability within an organization, it’s important to ensure there is a balance between each of the components to form the CIA triad, as shown in the following diagram:
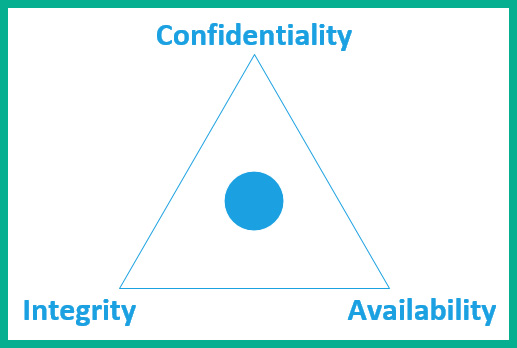
Figure 14.1 – CIA triad
As shown in the preceding diagram, the CIA triad is usually drawn using a triangle, and at the end of each angle is one of the three elements – confidentiality, integrity, and availability. At the center of the CIA triad is a dot that represents an equal balance of each element. Some organizations may focus more on confidentiality and integrity, which reduces the availability (access) of resources to users on the network, including the employees. Hence, maintaining a good balance between the components will create great harmony.
Threats, vulnerabilities, and exploits
A threat is simply defined as anything that has the potential to cause harm or damage to a system. Additionally, a threat has the potential to violate any component of the CIA triad, such as retrieving confidential data, altering a message during transmission, and even disrupting network services and resources. A vulnerability is described as a security weakness or design flaw within a system. Hackers typically use an exploit that can take advantage of the security weakness of their target, allowing the hacker to compromise the system. You can think of an exploit as code that is designed to take advantage of a security weakness on an application, firmware, or operating system. As you dive further into the field of network security, cybersecurity, and information security, you will discover many types of internal and external threats that can compromise the confidentiality, integrity, or availability of a system.
Additionally, zero-day vulnerabilities are found and exploited by threat actors before they are known by the vendor of the product. For instance, operating systems and software vendors perform continuous and rigorous security testing on their products to discover and resolve any security flaws before making them available to their customers. However, there have been times when threat actors were able to discover and exploit a security weakness on an application before the software vendor was made aware of the vulnerability and had time to resolve it. Sometimes, a software vendor may take a few days or even months to roll out a security update or patches to resolve the zero-day vulnerability, leaving their customers’ systems vulnerable and exploitable.
Whenever a new security vulnerability is discovered, it is commonly reported to the software vendor or directly to the Common Vulnerabilities and Exposures (CVE) and National Institute of Standards and Technology (NIST) National Vulnerability Database (NVD), which is assigned a unique CVE reference number that provides details about the security vulnerability, affected systems, and how it can be mitigated.
The following screenshot shows an example of the CVE details of the EternalBlue security vulnerability on the Microsoft Windows operating system:
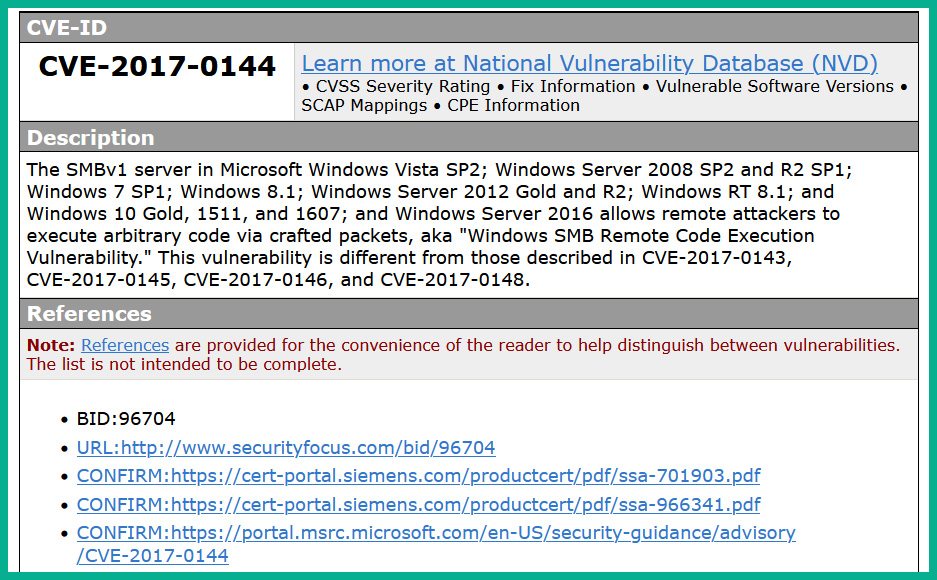
Figure 14.2 – CVE details of a known vulnerability
Tip
To learn more about the newly reported vulnerability and CVE details, be sure to check out https://cve.mitre.org/.
The NIST NVD website usually contains additional details about the security vulnerability, such as the vulnerability scoring, which is based on the Common Vulnerability Scoring System (CVSS) calculator for creating a community-recognized vulnerability score. This determines the severity level of a security weakness.
Internal threats can create a greater impact within an organization compared to external threats. While many organizations focus on implementing various security solutions to protect their corporate networks from external threats on the internet, many IT professionals do not always apply the same level of security to their internal networks. Threat actors such as hackers are aware that the internal security within many organizations is weak or does not even exist at all. Hence, it’s easier to compromise an organization from the inside than to perform an external attack.
For instance, many organizations implement a next-generation firewall at their network perimeter to filter inbound and outbound traffic between their organization and the internet. Threat actors commonly craft phishing email messages, which are designed to trick a potential victim into clicking a malicious embedded link or execute the malicious attachment within the message. While firewalls are security appliances, they are unable to inspect inbound and outbound email traffic for new and emerging threats. Hence, phishing emails can easily go undetected by firewall appliances, which is why dedicated email security solutions are needed.
Next, you will explore various types of threats and malware that are common within the cybersecurity industry.
Type of threats and malware
Malware is any type of malicious software that is designed to cause harm or data loss on a system. The following are a list of various type of malware:
- Virus: A computer virus is simply any malicious application or code that attaches itself to a program, application, file, or service on the victim’s system. Viruses are designed to infect and unleash their malicious payloads on the victim’s device. However, a virus needs human interaction, such as someone executing the virus file so that it’s activated and can begin working and infecting the system.
- Macro virus: This is a type of virus that attaches itself to Microsoft Office documents and executes when the unaware user opens the infected Microsoft office document and enables the macro feature. The macro feature within Microsoft Office allows a user to insert additional functionality into the document whenever a user opens the file. However, hackers have found methods to exploit this feature in Microsoft Office files.
- Boot sector virus: This type of virus infects the boot sector of a hard disk drive on a victim’s computer. If the boot security has a virus, whenever the system boots and the operating system is running, the virus has the potential to compromise all aspects of the victim’s computer.
- Attachments: Malicious attachments are commonly inserted and sent in phishing email messages to potential victims and organizations around the world. Email attachments may be malware-infected and are designed to compromise the unaware user’s system.
- Polymorphic virus: This type of malware is designed to consistently change its coding to evade detection by antimalware solutions on systems and networks, but the role and function of the malware do not change.
- Worm: A computer worm is self-propagating malware that can spread to any connected system on its own without user interaction. Computer worms are designed to affect a system’s usability by overwhelming or exhausting the available computing resources of the system.
- Fileless virus: This type of malware does not have a digital form compared to other traditional malware, which is usually attached to a file, service, or application. This type of malware simply does not exist as a file and does not have a virus signature, which allows it to evade threat detection systems. Additionally, fileless viruses are designed to run within the memory of the compromised system.
- Rootkits: This type of malware is designed to gain high-privilege access to the victim’s system such as root on Linux-based systems and administrator or system-level privileges on Windows-based systems, allowing the malware to perform administrative tasks. Once a system is infected with a rootkit, it operates at the kernel level of the operating system, which is inaccessible by antimalware programs.
- Keylogger: A keylogger is an application that’s commonly installed on a compromised system that captures all the keystrokes from the victim’s keyboard. Keyloggers are both software and hardware based. The hardware-based keylogger is inserted between the user’s keyboard and the computer to intercept all user input from their keyboard.
- Trojan: This type of malware is disguised to trick the potential victim into thinking it’s a legitimate file or program. A hacker usually creates a Trojan to trick their victim into installing a computer game or a trusted program. Once the victim executes the trojan on their system, the payload is unleashed in the background while the victim thinks the application is legitimate.
- Backdoor: A backdoor is usually created on a compromised system by a Trojan. Backdoors allow hackers to gain access to the compromised system, unbeknownst to the victim.
- Logic bomb: This type of malware is installed on a system and remains dormant until a predefined action is triggered, activating the logic bomb to unleash its payload on the system. Logic bombs can be triggered based on the time, date, and even the user’s actions.
- Ransomware: This is crypto-malware that encrypts all the data on a compromised system except the operating system. The operating system is left unharmed as the ransomware displays the payment window to the victim, requesting a ransom to recover the encrypted data. Since hackers are untrustworthy, it’s not recommended to pay the ransom as there is no reassurance the hacker will provide the correct decryption keys to access your data.
- Bot and botnet: Hackers install a bot (robot) on each compromised system, which allows them to remotely control the compromised system over a network, hence creating zombies. A group of infected systems with bots are commonly referred to as a botnet (robot network). A single hacker can set up a Command and Control (C2) server on the network, which allows the hacker to send instructions to the C2 server. These are then relayed to all active bots within the botnet to launch a cyber-attack on a target on the internet.
- Remote Access Trojan (RAT): Sometimes called a Remote Administration Tool (RAT), this allows a hacker to remotely control a compromised system over a network.
- Spyware: This type of malware collects data about the user’s activity on an infected system. It monitors and reports the victim’s activities and behavior back to the hacker. The hacker collects the data, which is usually sold on the dark web.
- Potentially Unwanted Program (PUP): This is usually any unwanted application or software that is installed on your system. Sometimes, when a user is installing an application, there are additional third-party applications that may be bundled and installed on the user’s device.
There are so many types of malware in the industry and being able to identify each type is beneficial in understanding whether a system is compromised by a specific malware or another type of threat.
Types of threat actors
While there are many types of threats and cyber-attacks, threat actors are the people responsible for performing the cyber-attacks and creating the threats within the industry. The following is a list of various categories of threats actors and their motives:
- Advanced Persistent Threat (APT): APTs are special hacking groups that design very sophisticated cyber-attacks and threats that are advanced and undetected by security solutions, persistent to remain on a compromised system and network while being a threat to the victim. APTs are created to remain on a compromised network while further exploiting additional systems on the network and exfiltrating data.
- Insider: Insider threats are described as the attacker already being within the organization’s network, behind the company’s security controls, and being able to attack any vulnerable systems. A disgruntled employee can be an insider threat as these are people whose intention is to disrupt the operations of the company by launching a cyber-attack.
- State actors: These are hackers who are hired by a nation’s government to focus on national security and perform reconnaissance on other nations around the world. State actors, sometimes referred to as nation-state hackers, are always well funded to acquire the best technologies, tools, and training needed to develop advanced persistent threats to compromise their targets.
- Hacktivist: This threat actor is a person who uses their hacking skills to support a political or social agenda as an activist. Their actions include website defacement, launching massive DDoS attacks, and disclosing confidential records on the internet.
- Script kiddie: This is a novice type of hacker, sometimes a beginner who is not necessarily a kid or child, but someone who does not truly understand the technical details of performing a cyber-attack and creating a threat on their own. This is someone who follows the instructions or tutorials of real hackers to perform a cyber-attack on a target without understanding what is happening in the background and the impact. However, the actions of a script kiddie can cause equal or more damage to a system compared to a seasoned hacker.
- Criminal syndicates: These are well-funded groups of hackers who focus on financial gain. Each person within the group has a specialist role during the cyber-attack, such as someone who focuses strictly on the reconnaissance of the target, while another develops an APT and another on exploitation, and so on.
- White hat hacker: These are the cybersecurity professionals within the industry who uses their hacking skills to help companies secure their systems and networks.
- Black hat hacker: This type of hacker uses their skills for malicious purposes.
- Gray hat hacker: This type of hacker uses their skills for both good and bad intentions. This person can be a cybersecurity professional during their day job and uses their hacking skills for bad intentions at night.
- Competitors: Competitors are always seeking new methods to ensure their products, services, and solutions are always the best in the industry, above their opponents in the business sector. However, competitors may look for ways to damage the reputation of their opponents to create a competitive advantage of gaining new customers and more revenue. Some competitors may even hire a hacker to compromise and exfiltrate confidential documents and leak financial records on the internet.
Now that you’re familiar with various types of threats and threat actors, next, you will learn about the importance of implementing least privilege for users on a network and how role-based access control (RBAC) can provide an additional layer of security.
Least privilege and RBAC
Imagine if, one day, all the employees within your organization had the same user privileges as each other. This would imply the customer service representatives have the same user privileges on their systems as the IT manager and senior members of staff, without any security restrictions to prevent unauthorized changes on their computers. To reduce these security risks, the principle of least privilege is applied to everyone to ensure a user has only enough user privileges on their systems to perform their daily duties while meeting the organization’s goals and objectives.
Additionally, rotation of duties helps detect and reduce any fraudulent activities within an organization. This technique ensures each employee is rotated between different job functions every few months. Therefore, if a specific employee is performing unethical or fraudulent tasks within their current job over a certain period, it may be unnoticeable. However, when the new employee assumes the role of the previous one, the unethical practices will be noticeable, and management can determine the source of the issue.
Another common strategy within large organizations is using separation of duties to ensure no single employee has all the privileges to make a major technical change to a system. Separation of duties requires two different people who can use their combined knowledge to complete a major technical change on a system. For instance, the person who is responsible for modifying the configurations on the firewall should not be the same person who is authorizing those changes; there should be two people for this. This concept prevents a single person from taking over the system or network within an organization.
Sometimes, the human resource and management team suspects an employee is performing unethical or malicious activities on the network. By enforcing mandatory vacation, the employee will need to a take leave of absence from the workplace, where they will be unable to access the systems and networks while away. This allows the organizations to determine whether the employee is responsible for unethical or malicious activities on the network.
Lastly, RBAC is a type of access control method that is based on a user’s job role and duties within the company. This access control ensures the user has the necessary privileges to perform their job efficiently and nothing more. IT professionals can implement this technical security control within their organization by leveraging the Group Policy Object (GPO) role within Active Directory Domain Service (AD DS) on Microsoft Windows Server. GPOs allow IT professionals to create security policies by indicating the permissions a user has on a company-owned system. For instance, if you want to prevent all users within the organization from accessing the Control Panel area or the Settings menu within the Microsoft Windows operating system, using a GPO allows you to configure this restriction and roll out the policy to all domain user accounts on the network. Within the enterprise versions of Microsoft Windows, IT professionals can create local GPOs on individual systems that will be applied to any user who logs into the computer.
Defense in Depth and zero trust
While cyber-attacks and threats are increasing each day and the need for cybersecurity professionals and solutions are increasing, organizations are starting to realize there are no prior warnings or indications their company is the next target until it’s too late and their systems are compromised. While many organizations are already investing in acquiring cybersecurity solutions such as threat detection and prevention application and security appliances such as firewalls, they also need to understand the importance of implementing a multi-layered approach to improve their defenses against new and emerging threats.
While many organizations think they don’t need cybersecurity solutions, hackers target anyone and any organization, despite the size of the company. For instance, if a small, private medical practitioner has a few computers within the office to perform daily business transactions and tasks, consider the network infrastructure that’s used to interconnect these systems to share resources. The business may be using a small wired or wireless network; however, does the network have any security features and solutions implemented to prevent external and internal threats?
It’s important to understand not all cyber-attacks and threats originate from the internet or externally. However, many organizations think a network-based firewall is enough to protect their assets and safeguard their systems and users from hackers and other threats. The downside is the network-based firewall is simply a single layer of security that can only filter traffic that passes through the device.
The following diagram shows a network-based firewall that’s filtering inbound and outbound traffic:

Figure 14.3 – Network-based firewall
While having a network-based firewall implemented between the internet and the internal network, it’s important to understand that there are other types of threats and attacks that cannot be prevented or mitigated by a security appliance such as a firewall. What if the organization has a wireless network? Does the wireless router or Access Point use the latest wireless standard and is configured with a complexity password? Are there any unauthorized users who are connected to the wireless network? These are just some of the many questions we need to think about when considering the security of a wireless network.
While some organizations or small businesses think their network or systems do not contain any valuable data, all data is valuable to threat actors. For instance, a small medical practitioner may be using a laptop, computer, or tablet to store patients’ information. If a threat actor were to compromise the laptop and steal the patients’ data, they may be able to identify many patients and disclose their medical history to the public. As a result, the patients will be the victim because their PHI was stolen due to a lack of security controls, meeting compliance, or a lack of diligence of security of the patients’ data by the medical provider. However, the medical provider is also the victim as their systems and networks were compromised by a threat actor.
As you may realize already, a single layer of security is not sufficient. A Defense in Depth approach is the concept of implementing multiple layers of security, which is designed to reduce the attack surface that the threat actor can exploit using a vulnerability while improving the security posture of an organization. For instance, rather than implementing only a network-based firewall to protect all the internal assets of an organization, using a Defense in Depth approach, you should implement Endpoint Detection and Response (EDR) applications on users’ computers, enforce inbound and outbound email filtering for email-based threats, implement inbound and outbound web filter for web-based attacks, best practices for wireless security, and so on.
A Defense in Depth approach ensures an organization is fortified to prevent internal and external threats, it’s resilient against new cyber-attacks and threats, reduces the attack surface, and improves the security posture of the entire organization while using a multi-layered approach.
While some organizations have a flat network, where all devices are on the same physical and logical network, implementing a Virtual Local Area Network (VLAN) within the network can help create and enforce logical network segmentation within the organization. Therefore, each organizational department, such as Sales, HR, Accounting, and so on, can be placed on their own, unique VLAN on the network. Implementing network segmentation improves not only the network performance but the network security too.
The following diagram shows the concept of VLANs on a network:

Figure 14.4 – VLANs on a network
As shown in the preceding diagram, there are many devices connected to the same physical network but the devices within their own organizational departments, such as Sales, HR, and IT, are on their own VLAN and IP subnet.
Additionally, many organizations have network-based firewalls that are filtering inbound and outbound traffic between their internal corporate network and the internet. However, the organizations may have a few servers that need to be accessible from users on the internet. Placing the servers on the internal network creates a major security risk as users from the internet will be able to access the internal network, which isn’t good. However, creating a screened subnet, previously known as a Demilitarized Zone (DMZ), allows security professionals to create a semi-trusted area on their network with strict rules to allow specific users and traffic types into the screened subnet.
The following diagram shows the concept of a screened subnet or DMZ:
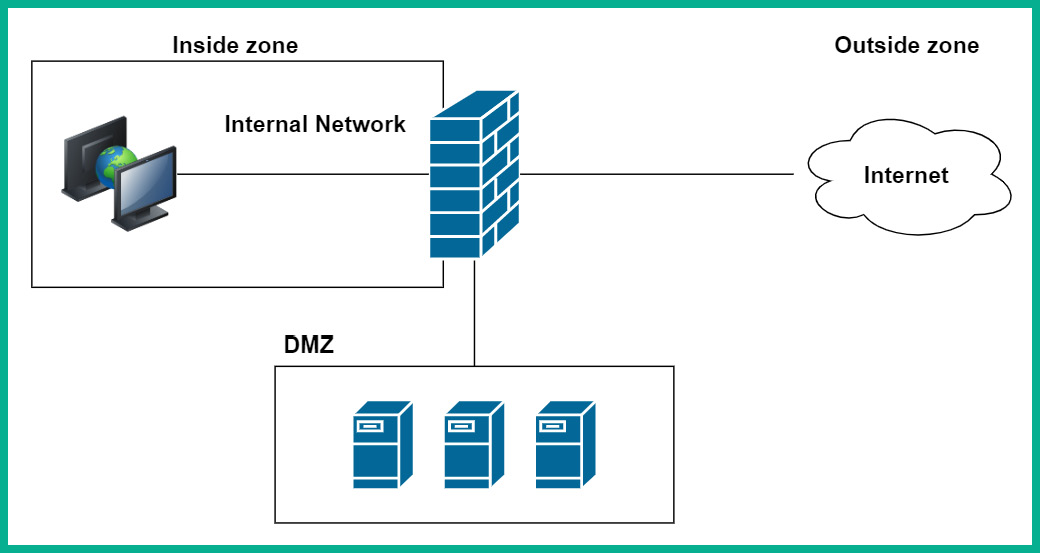
Figure 14.5 – Screened subnet
As shown in the preceding diagram, the screened subnet (or DMZ) contains all the publicly accessible servers within the organization, allowing users from the internet to access these systems. When implementing a network-based firewall, it’s important to understand the importance of security zones:
- Inside zone: The inside zone is a fully trusted zone that has a security level of 100. This security zone is typical of an internal, corporate network, so the firewall will automatically trust all traffic that’s originating from the inside zone.
- Outside zone: The outside zone is a no-trusted zone with a security level of 0. This security zone is typically a foreign network that is not owned or managed by the organization – it’s commonly the internet. Therefore, the firewall will not trust any traffic that originates from the outside zone and simply drop or block the traffic.
- DMZ: This is the semi-trusted zone, also known as the screened subnet, which typically has a security level of 50.
The security zones and security levels play an important role within the firewall as it determines how traffic is filtered by default between each of the security zones based on the security levels:
- Traffic that originates from a security zone with a higher security level will be allowed to access a security zone with a lower security level
- Traffic that originates from a security zone with a lower security level will be denied from accessing a security zone with a higher security level
- Traffic from the inside zone is allowed to the DMZ and the outside zone
- Traffic from the internet is denied from accessing the inside zone
- Traffic from the internet is selectively permitted to the DMZ if a firewall rule is created to allow the traffic type
- Traffic from the DMZ is not permitted to access the inside zone unless it’s stateful traffic
However, firewalls do not prevent an unauthorized user or device from connecting to the internal wired or wireless network as the firewall was simply designed to filter traffic between networks. Using Network Access Control (NAC), defined by IEEE 802.1X, enforces port-based access control. Therefore, whenever a user connects a device to the wired or wireless network, the NAC system prompts the user to enter valid user credentials, which will be used to validate the identity of the user and their device, assign policies that define what the user is allowed to do while on the network, and generate logs for accountability of the user’s actions while authenticated to the network.
The following shows a NAC system and its components on a network:

Figure 14.6 – NAC system
As shown in the preceding diagram, three essential components are part of a NAC solution. The supplicant is the client device that is connected to the wired or wireless network. Once the supplicant (computer) is connected to the network, the user will be prompted to enter their user credentials. The authenticator is the network switch, wireless router, or Access Point on the network, which is the intermediary device that allows the supplicant to access the network. The authentication server is the server and performs Authentication, Authorization, and Accounting (AAA) on the network. The user credentials, policies, and logs are created on the authentication server.
AAA is a framework that improves network security within an organization. AAA uses the following authentication protocols:
- Remote Access Dial-In User Service (RADIUS) is a common, open source AAA server that allows IT professionals to implement AAA within an environment with multi-vendor equipment. RADIUS operates on UDP port 1812 for authentication and UDP port 1813 for accounting. Keep in mind that RADIUS does not encrypt the entire packet on the network but only encrypts the password.
- Terminal Access Controller Access-Control System Plus (TACACS+) is a Cisco-proprietary authentication server that only operates with Cisco devices. TACACS+ operates on TCP port 49 and encrypts the entire packet, protecting the data it contains.
Wireless networks that use IEEE 802.1X NAC commonly use Extensible Authentication Protocol (EAP), a network authentication framework that is designed to securely handle the authentication messages between systems over a wireless network. EAP is commonly seen on wireless networks that use Enterprise mode with a RADIUS server compared to Personal mode with a Pre-Shared Key (PSK).
The following are variations of EAP:
- EAP Flexible Authentication via Secure Tunneling (EAP-FAST): This version of EAP was developed by Cisco as a replacement for the Lightweight EAP (LEAP) version, which was implemented in wireless networks that used the Wired Equivalent Privacy (WEP) security standard. EAP-FAST uses a Protected Access Credential (PAC) to handle the authentication process. PAC is similar to using a secure cookie between a web server and web browser; it’s stored locally on the client that’s being authenticated to the network and is used by the client to validate their authenticity to the system.
- EAP Transport Layer Security (EAP-TLS): This uses TLS to provide stronger security on a network. EAP-TLS supports mutual authentication, such that both a client and server authenticate to each other, whereby both the client and server exchange digital certificates to validate their identities to each other.
- EAP Tunnel Transport Layer Security (EAP-TTLS): This is a version of EAP that supports TLS tunneling for transporting messages between systems over a network. In EAP-TTLS, only the server needs a digital certificate, unlike in EAP-TLS, where both the client and server use certificates.
- Protected EAP (PEAP): This version of EAP encapsulates EAP messages inside a TLS tunnel.
While NAC solutions are designed to enforce port-based access control to wired and wireless networks, companies add the following types of controls within their network to improve the network security while creating a Defense in Depth approach:
- Technical controls: These are the electronic and digital systems that are implemented to prevent unauthorized activities.
- Administrative controls: These are the security policies that are created and implemented within a company that is designed to manage how employees interact with the organization’s systems. These administrative controls are usually in the form of security policies and procedures, human resource policies, and standard operating procedures.
- Physical controls: These are the physical objectives and controls such as doors, locks, fences, security guards, and so on that are used to secure a physical location such as a building or data center.
Furthermore, some organizations implement a honeypot, which is a type of computer system that is configured and implemented on a network to catch or trick threat actors into thinking it’s a real system. A honeypot intends to lure attackers using a decoy such as mimicking a real production system on the network. When the attacker attempts to compromise and exploit the honeypot, cybersecurity professionals capture the data that’s generated from specialized security monitoring tools on the honeypot, which indicates the attacker’s action – that is, what the person is trying to do.
The data collected from a honeypot provides insights into the following:
- The source of the attacker
- The severity of the threat and cyber-attack
- What type of tools the attacker is using
- If your security solutions are capable of preventing the threat or cyber-attack
By implementing Defense in Depth within organizations, they can move closer to creating a zero-trust network. Zero trust simply focuses on not trusting anything or anyone until it’s properly authenticated on the network. Can you imagine the security risks that are involved when a user connects their mobile device to a company’s network? If the company’s network does not support AAA or does not have any threat detection and prevention systems, malware on the user’s device can spread onto the network and compromise the critical servers.
Having completed this section, you have learned about various network security concepts, such as the importance of the CIA triad, various types of threats and threat actors, and the importance of Defense in Depth. Next, you will explore various authentication methods that can be implemented on a network.
Exploring authentication methods
As humans, we can simply look at someone and recognize whether a person is a relative, friend, colleague, stranger, or foe. The human mind allows us to retain memories that contain details about what we see each day, such as recognizing a co-worker entering the office building each morning and greeting you. Likewise, security guards, who are present at various entry points on a compound or building, validate whether a person is an employee or a customer. Eventually, the security guards will become familiar with the employees of an organization and recognize their faces quickly.
Computer systems and their technologies are continuously advancing to help improve the lives of many people around the world while helping organizations improve their business operations and automation. Since many organizations rely strongly on computers to help perform many business processes and procedures, IT professionals need to ensure authorized people are using company-owned systems. For instance, what if an unauthorized user within the organization gained access to a computer system that is responsible for the Heating, Ventilation, and Air Conditioning (HVAC) system for the data center? What will the impact be if the user shuts down the cooling system?
Computer systems are different from the human mind and need processes to determine and validate the identity of a user before allowing them to access the resources of the system. By implementing authentication, IT professionals can configure various key elements that are used to identify a valid user on the system, such as a username and password combination. Whenever a user attempts to access the system, they are prompted to enter something that is known only to the valid user onto the system, such as a valid username and password. If the user credentials are correct, the system allows the user to access the resources. However, if the user credentials are inaccurate, the system restricts access and does not trust the user. You can think of authentication as a set of processes that are used by a system to validate the identity of a user.
Authentication plays an important role in computer systems in today’s world, especially with the continuous increase in cybercrime that’s happening each day. It has become an industry norm to ensure authentication is enabled on all systems within organizations, simply to reduce the risk of an unauthorized user gaining access to a system.
The following are various authentication factors:
- Something you are: A user can prove their identity to a system by using biometrics such as their fingerprint, facial recognition, voice, and iris and retina scanning.
- Something you have: A user can provide a security token such as a smart card or a USB token such as a Yubikey. Additionally, the system that the user is attempting to access can send an SMS message that contains a unique authentication code that can be used once by the user.
- Something you know: This can be a password, passphrase, Personal Identification Number (PIN), or even a series of patterns such as those on the locked screen of a smartphone.
- Somewhere you are: Systems allow a user to validate their identity via their geo-location. So, when a user is attempting to log into a system, the source IP address and/or Global Positioning System (GPS) location is used as an additional attribute.
- Something you do: This is an attribute that’s personal to the user, such as their typing and handwriting patterns.
Typically, when a person acquires a new computer, laptop, or smartphone, they will enable authentication to ensure an unauthorized user is unable to access the contents and resources on the device. Similarly, network professionals will configure a local user account with a password to restrict unauthorized users from accessing their networking devices. Since the user account is created locally on the computer or networking device, whenever a user wants to access the system, they will need to enter their user credentials, which are checked against the local database. This database determines whether the account is valid. This method is commonly referred to as local authentication as the user credentials are created on the local system only.
If the same user attempts to log into another computer or a networking device, a valid user account needs to be created on the other systems too. The benefit of using local authentication is the computer system can quickly query its local database to determine whether the username and password combination exists or not. However, the downside is that the user account needs to exist on each system that the user needs access to. Therefore, if the user credential is changed on one device, it must be changed on all devices. Using AAA with NAC allows network professionals to implement a centralized authentication server that’s running RADIUS, allowing networking devices to query the authentication server whenever a user attempts to log into a system.
Next, you will learn about the importance of implementing multi-factor authentication (MFA) on systems to prevent unauthorized users from gaining access to systems and accounts.
Multi-factor authentication
Creating a user account on a computer or an online website is quite simple; fill in some identification details and create a username (identity) and password. Whenever you’re attempting to log into your online account, you’ll be prompted to enter your username and password. Once the user credentials match on the system, you’re authenticated. It’s that simple. However, configuring only a password, passphrase, or pin is one factor that’s used to validate your identity to the system. Simply put, if a hacker wants to compromise your email account, they can easily determine your username by looking at your email address. Then, the hacker will simply need to determine your password for the account. Once the password is retrieved, the hacker can access your account.
MFA is the concept of enabling additional layers of security on a user account to prevent hackers from performing account takeovers. With MFA implemented, a user will need to provide two or more authentication factors during the authentication process before the system allows the user access. For instance, when logging into your online email account, the website prompts you to enter your email address or username, as shown in the following screenshot:

Figure 14.7 – Google sign-in page
Next, the system prompts you to enter your password/passphrase to validate whether you’re the authorized user for the account, as shown in the following screenshot:

Figure 14.8 – Password page
If you’ve configured MFA, the system will prompt you to use the additional factor next. In this example, I’m using a physical security token and received the following prompt to insert the USB device:

Figure 14.9 – Additional security
With MFA enabled on a system, a user must enter more than one factor to prove their identity. This means that if a username and password of a victim are known to a hacker, the hacker is less likely to compromise the user account if MFA is turned on. Many people are also using authenticator apps on their mobile devices where the authentication code is changed every 20 to 30 seconds. Therefore, if a hacker wants to access an online account with MFA enabled that uses an authenticator code, the hacker will need to use a unique code from the app.
Kerberos, single sign-on, and LDAP
Kerberos is a network authentication that is commonly implemented on Microsoft Windows operating systems and allows client devices such as computers to authenticate to a Domain Controller on a network. Microsoft Windows Server supports the Active Directory Domain Service (AD DS) role, which allows an IT professional to create a logical security domain. This allows IT professionals to centrally manage the security privileges of all users, groups, and devices that belong to the domain.
Important note
Active Directory allows IT professionals to create users, groups, and computer accounts on Windows Server. This allows IT professionals to centrally manage the security of devices and assign policies to users on the domain.
Kerberos allows users on a Microsoft environment to authenticate once on the domain and access all the resources without the need to re-enter their user credentials whenever they need access to a new resource. This concept is commonly referred to as single sign-on (SSO). Additionally, SSO is commonly implemented on various online platforms. For instance, when a user logs into their Google account on the internet, the user can access all of Google’s products and services without having to register or re-authenticate when accessing other services from Google.
To get a better idea of how Kerberos works, let’s look at the three main components that all need to work together to ensure Kerberos provides SSO to users and systems on the network:
- Client: This is the user who logs into their client computer using their domain user credentials.
- Key Distribution Center (KDC): The KDC is the Microsoft Windows server that is running the Active Directory role and services. It’s the Domain Controller.
- Application server: The application server is simply a server that is providing a resource or service to users on the domain/network.
When a person enters their user credentials on a client computer that’s connected to a domain, the client computer converts the password into a New Technology LAN Manager (NTLM) version 2 hash. Then, it sends both the username and the NTLMv2 hash of the password within a Lightweight Directory Access Protocol (LDAP) packet to the Domain Controller. As you may recall, LDAP is a common network protocol that is used to perform operations such as read, write, and query, on a directory server for records. A common directory server is a Windows Server that is running the Active Directory role.
The following steps outline the Kerberos process:
- The user enters their credentials on their client’s computer. The username and NTLMv2 hash of the password are sent across the network in an LDAP packet to the KDC:

Figure 14.10 – Kerberos phase 1
- Next, the krbtgt account is a local account that’s automatically created on the KDC. It is responsible for creating and sending an encrypted and signed Ticket Granting Ticket (TGT) to the client:

Figure 14.11 – Kerberos phase 2
- The client keeps the TGT until the user is ready to access a resource such as the application server on the domain. The client sends the TGT to the KDC to request a Ticket Granting Service (TGS) ticket:

Figure 14.12 – Kerberos phase 3
- Next, the KDC uses the service’s NTLM hash to encrypt the TGS and sends the TGS to the client:

Figure 14.13 – Kerberos phase 4
- When the client computer connects to the application server on the domain, it provides the TGS ticket to access the services and resources on the server:

Figure 14.14 – Kerberos phase 5
As you have seen in the preceding phases, the user authenticates only once to the Windows domain using Kerberos with SSO and does not need to re-authenticate to access resources on the domain.
Having completed this section, you have learned about authentication methods on networks. Next, you will discover risk management techniques that are commonly used by organizations.
Risk management
Each day, people make decisions to mitigate and prevent various types of risks in their daily lives, workplaces, and organizations. In this context of network security, risk is defined as the likelihood/possibility that a threat actor can cause harm or damage to a system. IT professionals must be able to identify the assets that could be attacked and compromised by cyber-attacks and threats. As you may recall, assets are simply anything that has value to an organization and are usually tangible, intangible, and people (employees). By identifying the assets, security professionals will get a better idea of what needs to be safeguarded from potential threats.
Furthermore, IT professionals need to identify the various types of threats and threat actors and how they can potentially compromise the assets of the organization. A hacker will commonly perform reconnaissance to collect a lot of information about their target before launching an attack. The information that’s collected is used to create a profile about the target and determine the technical infrastructure of the target. Sometimes, during the reconnaissance phase, the threat actor may discover exposed security vulnerabilities that can be exploited. However, the hacker usually proceeds to perform various types of scanning to determine if additional security vulnerabilities exist on devices that belong to the target. A large number of vulnerabilities found during the reconnaissance and scanning phases is an indication of a large attack surface.
From a cybersecurity perspective, each vulnerability found on a system has a severity score/rating that is determined by vulnerability assessment tools using the CVSS calculator. The CVSS calculator allows cybersecurity professionals to determine the vulnerability score for any security weaknesses or flaws found on a system, helping cybersecurity professionals prioritize their focus on high-risk vulnerabilities that can have a huge impact if exploited compared to low-risk vulnerabilities. The vulnerability score provided by the CVSS calculator is acceptable within the cybersecurity industry among professionals and organizations.
Overall, the main objective of risk management is to implement processes, procedures, and controls to reduce the security risks that can impact or compromise the assets of a company.
Important note
The CVSS 3.1 calculator can be found at https://www.first.org/cvss/calculator/3.1 and https://nvd.nist.gov/vuln-metrics/cvss/v3-calculator.
The following are common risk response techniques:
- Avoidance: This technique focuses on stopping all activities that are creating risk within the organization.
- Transference: This technique involves contacting a third-party vendor such as a Managed Security Service Provider (MSSP) to both handle and manage the security risk on behalf of the organization.
- Acceptance: The organization understands its mission-critical processes and procedures that create risk. Without them, the organization cannot operate and accepts the risks.
- Mitigation: The organization implements various security controls to prevent the occurrence of risks.
Next, you will explore the importance of regular security risk assessments within organizations.
Security risk assessments
A security risk assessment helps organizations identify, assess, and even implement various security controls that are designed to prevent and resolve security vulnerabilities on their systems and networks. Can you imagine if organizations never performed security risk assessments on their infrastructure? There would be a lot of hidden security flaws in their applications, systems, and networks that can be exploited by hackers. For instance, many organizations around the world don’t realize their systems have been compromised until a few months have passed. This is why there’s a need for regular security risk assessments – to determine the current security posture with a gap analysis to indicate whether the number of security risks is reducing after each assessment and implementation of security controls.
Threat assessments allow cybersecurity professionals to research new, existing, and emerging threats in the industry to determine the future of cyber-attacks and the intention of threat actors. Since each type of threat actor has a unique motive for their attacks, it is important to understand their mindset and the type of tools being used to perform those attacks on targets. For instance, data is the most valuable asset to any organization, and it’s found everywhere. Understanding the strategies and tools that are used by hackers allows cybersecurity professionals to use the same tools and techniques with the intent to discover security vulnerabilities on their company’s systems, and then implement security controls to prevent a real cyber-attack from occurring. This involves taking a proactive approach to improving the security posture of the organization from threats.
The following are additional types of threats that can affect organizations:
- Environmental: These types of threats are natural and sometimes occur without any prior warning. Environmental threats include natural disasters such as flooding, hurricanes or cyclones, earthquakes, and so on.
- Man-made: These types of threats are created by people such as a disgruntled employee who wants to cause harm to the organization by destroying the data stored on the company’s servers or disrupting the availability of network services and resources.
- External: These are threats that can originate from outside of the organization, such as a hacker or group of hackers launching a DDoS attack on the organization’s web server on the internet.
A vulnerability assessment helps organizations identify the security vulnerabilities that exist on a system and determine their risk level. Since a security vulnerability is defined as the security weakness or flaw in a system that can be exploited by a threat actor such as a hacker, IT professionals must quickly discover these flaws and resolve them before a real hacker compromises their company. Additionally, vulnerability assessment tools help cybersecurity professionals test for specific vulnerabilities and help ensure systems are compliant with various industry security frameworks and standards. For instance, systems that are used to process payment cards must be Payment Card Industry Data Security Standard (PCI DSS)-compliant to ensure these systems meet the minimum level of security for data protection. Vulnerability assessments and tools assist in checking for compliance.
The following are common vulnerabilities in systems:
- Default settings: These are systems and devices that are deployed on a network using the same configurations as they had when they left the manufacturer.
- Weak encryption: These are systems that use insecure encryption technologies that allow a threat actor to gain unauthorized access to the system and data.
- Unsecure protocols: Unsecure protocols are network and application protocols that do not provide security features such as encryption to ensure privacy between the client and the server.
- Open permission: These are the full permissions of files and folders that are given to everyone, which can lead to security risks from users on the network.
- Unsecure root accounts: These are root accounts on Linux-based systems that do not contain complex passwords that are easy to compromise. Since root accounts are created on Linux-based systems, they’re often used to discover unsecure administrator accounts on Windows-based systems that are vulnerable to account takeovers due to weak passwords.
- Open ports and services: Many unnecessary services run on a system. Some services may open a service port to allow inbound connections from a remote system. Then, a threat actor can launch a remote exploit across the network to take advantage of the vulnerable service on a target system.
Penetration testing is the technique used by authorized cybersecurity professionals with legal permission to simulate a real-world cyber-attack on the systems and networks that belong to an organization, using the same techniques and tools used by real hackers with the intent to discover hidden security vulnerabilities. At the end of a penetration test, the cybersecurity professional submits both an executive and technical report to the organization with details of any security vulnerabilities that were found during the time of the security assessment, from most critical to least. This will include details on how a real hacker will be able to compromise the vulnerabilities, and recommendations on how to prevent and mitigate the security risk.
Organizations use a penetration testing report to improve the security posture of their systems and networks that were tested by applying patches and updates, closing unused service ports, disabling unnecessary services, improving device configurations, and using secure network protocols for communication. It’s important to perform continuous testing on systems and networks within companies to ensure all backdoors and security flaws are fixed before a real hacker compromises them.
Posture assessment helps organizations determine the security risks on mobile devices that are connecting to the corporate network. For instance, an organization with a Bring Your Own Device (BYOD) policy may be allowing their employees to connect their devices, such as smartphones, tablets, and laptops, to the company’s wireless network. Since these personal devices are not managed by the organization’s IT team, there’s no way IT professionals can regularly implement operating systems and security updates on these devices.
Therefore, network and security professionals commonly implement security solutions such as the Cisco Identity Services Engine (ISE) to help determine the security posture of any connected device. The posture assessment checks each device to determine if it is trusted, whether the operating system is up to date, whether the device has an antimalware application, and the type of operating system. If the device has not been through the posture assessment, it is assigned to an isolated logical network, preventing the user and device from accessing the resources on the network.
Important note
Process assessment focuses on examining the existing business processes and procedures within the organization. This helps determine whether these processes are performing optimally with the expenses associated with each process to achieve the expected quality and goals.
Vendor assessment focuses on understanding and reducing the risks that are involved in working with a third-party vendor such as a service provider. There are many security concerns, such as whether the vendor has certified professionals to work on your equipment such as networking devices, security appliances, and servers within your organization. Additionally, it checks whether the vendor has a privacy policy for protecting their customer’s data and whether the vendor is meeting various industry compliance and standards. For instance, an engineer may be required to be certified in a specific information security certification before working on systems that are designed to protect data. Important organizations screen each vendor and ensure they meet all the requirements before conducting any business.
In this section, you learned about various security risk assessment types and how they can be used to help organizations to identify and reduce security vulnerabilities.
Summary
In this chapter, you learned about the CIA triad and how network professionals can use it to improve data security within their organizations. Additionally, you learned about various types of security risks and threats that can cause harm to systems and networks in many companies. Furthermore, you discovered various types of authentication methods and how they can be used to reduce account takeovers while preventing unauthorized access to systems.
I hope this chapter has been informative for you and is helpful in your journey toward learning networking and becoming a network professional. In the next chapter, Chapter 15, Exploring Cyberattacks and Threats, you will learn about various types of attacks and threats, as well as how to identify them.
Questions
The following is a short list of review questions to help reinforce your learning and help you identify areas that may require some improvement:
- Which of the following is responsible for ensuring authorized users have access to data?
A. Availability
B. Integrity
C. Confidentiality
D. All of the above
- Which of the following prevents users from accessing a web server on the internet?
A. Ransomware
B. Black hat
C. Trojan
D. DDoS
- Which of the following allows a hacker to exploit and compromise a system before the vendor can resolve the issue?
A. Zero-day
B. Day one attack
C. Exploit
D. Ransomware
- Which of the following malware does not have a signature and runs in memory?
A. Rootkit
B. Fileless virus
C. Boot sector virus
D. Polymorphic virus
- Which of the following best describes an employee who uses hacking skills to cause damage to the organization’s systems?
A. APT
B. Hacktivist
C. Black hat
D. Insider
- Which of the following allows network professionals to create logically isolated networks using their existing physical network infrastructure?
A. Implementing routers
B. Implementing switches
C. Implementing VLANs
D. Implementing bridges
- Which of the following frameworks is associated with port-based access control?
A. IEEE 802.1Q
B. IEEE 802.1D
C. IEEE 802.1w
D. IEEE 802.1X
- Which of the following is an open network authentication protocol that works with mixed-vendor equipment?
A. RADIUS
B. SSO
C. TACACS+
D. Kerberos
- Which of the authentication methods grants a ticket to a user, allowing to user to provide the ticket to any server on the network to access its resource?
A. RADIUS
B. SSO
C. TACACS+
D. Kerberos
- Which of the following checks whether a device has met all the security requirements before it’s allowed access to the network resources and services?
A. Vulnerability assessment
B. Posture assessment
C. Process assessment
D. Threat assessment
Further reading
To learn more about the topics that were covered in this chapter, check out the following links:
- What is the CIA Triad?: https://www.fortinet.com/resources/cyberglossary/cia-triad
- Cyber Security Threats: https://www.imperva.com/learn/application-security/cyber-security-threats/
- Zero Trust Security Explained: Principles of the Zero Trust Model: https://www.crowdstrike.com/cybersecurity-101/zero-trust-security/
- Use these 6 user authentication types to secure networks: https://www.techtarget.com/searchsecurity/tip/Use-these-6-user-authentication-types-to-secure-networks
- What is risk management and why is it important? https://www.techtarget.com/searchsecurity/definition/What-is-risk-management-and-why-is-it-important
