13
Threat Intelligence
By now, you’ve been through a number of different phases in your journey toward a better security posture. In the last chapter, you learned about the importance of a good detection system, and now it’s time to move to the next level. The use of threat intelligence to better know the adversary and gain insights into the current threats is a valuable tool for the Blue Team. Although threat intelligence is a domain that has been gaining traction over the last few years, the use of intelligence to learn how the enemy is operating is an old concept. Bringing intelligence to the field of cybersecurity was a natural transition, mainly because, now, the threat landscape is so broad and the adversaries vary widely, from state-sponsored actors to cybercriminals extorting money from their victims.
In this chapter, we are going to cover the following topics:
- Introduction to threat intelligence
- Open-source tools for threat intelligence
- Microsoft threat intelligence
Let’s begin with an introduction to threat intelligence and examine why it is so important to improve your threat intelligence capabilities.
Introduction to threat intelligence
It was clear in the last chapter that having a strong detection system is imperative for your organization’s security posture. One way to improve this system would be to reduce the noise and number of false positives that are detected. One of the main challenges that you face when you have many alerts and logs to review is that you end up randomly prioritizing – and in some cases, even ignoring – future alerts because you believe it is not worth reviewing them. According to Microsoft’s Lean on the Machine report, an average large organization has to look through 17,000 malware alerts each week, taking on average 99 days for an organization to discover a security breach.
Alert triage usually happens at the Network Operations Center (NOC) level or Security Operations Center (SOC), and delays to triage can lead to a domino effect. This is because if triage fails at this level, the operation will also fail, and in this case the operation will be handled by the incident response team.
Let’s step back and think about threat intelligence outside of cyberspace. How do you believe the Department of Homeland Security defends the United States against threats to border security?
They have the Office of Intelligence and Analysis (I&A), which uses intelligence to enhance border security. This is done by driving information sharing across different agencies and providing predictive intelligence to decision makers at all levels. Now, use the same rationale toward cyber threat intelligence, and you will understand how effective and important this is. This insight shows that you can improve your detection by learning more about your adversaries, their motivations, and the techniques that they are using. Using this threat intelligence toward the data that you collect can bring more meaningful results and reveal actions that are not detectable by traditional sensors.
In a news briefing in February 2002, the United States Secretary of Defense, Donald Rumsfeld, responded to a question with a phrase that continues to be used even today by the intelligence community. He said:
”As we know, there are known knowns; there are things we know we know. We also know there are known unknowns; that is to say, we know there are some things we do not know. But there are also unknown unknowns—the ones we don’t know we don’t know.”
While this was widely propagated by the mainstream media during that time, this concept was created in 1955 by two American psychologists who developed the Johari window.
Why is this important in the context of cyber intelligence? Because when you are collecting data to be used as your source of cyber intel, you will determine that some data will lead you to results that you already know (threats that are known – known knowns), others you will conclude that you know that there is something out of pattern, but you don’t know what it is (known unknowns), and others that you have no idea what it is and if it is out of pattern (unknown unknowns). Often, you will also see the use of the term Cyber Threat Intelligence (CTI) when referring to threat intelligence for the cybersecurity domain.
It is important to mention that the attacker’s profile will be directly related to their motivation. Here are some examples of an attacker’s profile/motivation:
- Cybercriminal: The main motivation is to obtain financial results or steal sensitive data.
- Hacktivist: This group has a broader scope of motivation—it can range from an expression of political preference to just an expression for a particular cause.
- Cyber espionage: Although you can have cyber espionage without it being state-sponsored (usually in the private sector), a growing number of cyber espionage cases are happening because they are part of bigger state-sponsored campaigns.
The question now is: which attack profile is most likely to target your organization? It depends. If your organization is sponsoring a particular political party, and this political party is doing something that a hacktivist group is totally against, you might be a target.
If you identify yourself as a potential target, the next question is: what assets do I have that are most likely desired by this group? Again, it depends. If you are a financial group, cybercriminals will be your main threat, and they usually want credit card information, financial data, and so on.
Another advantage of using threat intelligence as part of your defense system is the ability to scope data based on the adversary. For example, if you are responsible for the defense of a financial institution, you will want to obtain threat intel from adversaries that are actively attacking this industry. It really doesn’t help much if you start receiving alerts related to attacks that are happening in education institutions. Knowing the type of assets that you are trying to protect can also help to narrow down the threat actors that you should be more concerned about, and threat intelligence can give you that information.
It is important to understand that threat intelligence is not always available from a single location; you can have different data feeds that will be leveraged as the source to compose your threat intelligence.
Let’s use the WannaCry ransomware as an example. The outbreak happened on Friday, May 12, 2017. At the time, the only indicators of compromise (IoCs) available were the hashes and filenames of the ransomware sample. However, even before WannaCry existed, the EternalBlue exploit was already available, and as you know, WannaCry used the EternalBlue exploit. EternalBlue exploited Microsoft’s implementation of the Server Message Block (SMB) protocol v1 (CVE-2017-0143). Microsoft released the patch for this vulnerability on March 14, 2017 (almost two months prior to the WannaCry outbreak).
Are you following? Well, let’s contextualize this with the following diagram:

Figure 13.1: The events leading up to the WannaCry outbreak
Note that threat intelligence was receiving relevant information about this threat in the early stages, even when the EternalBlue exploit (originally discovered by the NSA) was leaked online (April 2017) by a hacker group calling itself The Shadow Brokers (TSB). The group was not new, which means there was intel related to the work they had done in the past and their previous motivations. Similarly, there will often be intel on your adversary’s work in the past that can help predict their next move. By having this information, and knowing how EternalBlue works, it was just a matter of waiting for the vendor (Microsoft, in this case) to send out a patch, which happened in March 2017. At this point, the Blue Team had enough information to determine the criticality of this patch to the business that they were trying to protect.
Many organizations didn’t fully realize the impact of this issue, and instead of patching, they just disabled SMB access to the internet. While this was an acceptable workaround, it didn’t fix the root cause of the issue. As a result, in June 2017, another ransomware outbreak happened—this time it was Petya. This ransomware used EternalBlue for lateral movement. In other words, once it compromised one machine inside the internal network (see, the firewall rule doesn’t matter anymore), it was going to exploit other systems that were not patched with MS17-010. As you can see, there is a level of predictability here, since part of the Petya operation was implemented successfully after using an exploit similar to the one used by previous ransomware.
The conclusion to all this is simple: by knowing your adversaries, you can make better decisions to protect your assets. Having said that, it is also fair to say that you can’t think of threat intelligence as an IT security tool—it goes beyond that. You have to think of threat intelligence as a tool to help make decisions regarding the organization’s defense, help managers to decide how they should invest in security, and help CISOs to rationalize the situation with top executives. The information that you obtain from threat intelligence can be used in different areas:
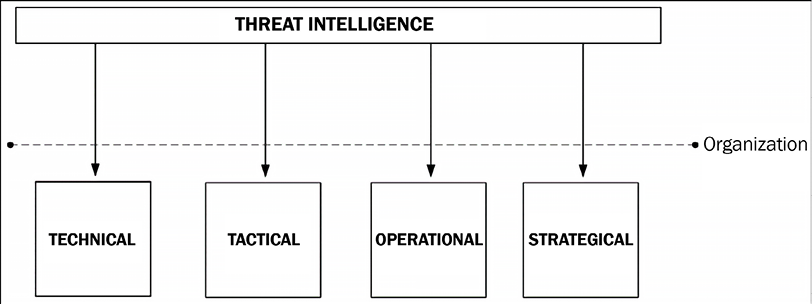
Figure 13.2: Threat intelligence feeding into different areas across an organization
As shown in the preceding diagram, there are different areas of the organization that can benefit from threat intelligence. Some will have more benefit in the long-term use, such as strategical and tactical. Others will be more for short-term and immediate use, such as operational and technical. Examples of each are as follows:
- Technical: When you obtain information about a specific IoC. This information will usually be consumed by your SOC analysts and the incident response (IR) team.
- Tactical: When you are able to determine the tactics, techniques, and procedures (TTP) used by attackers. Again, this is critical information that is usually consumed by SOC analysts.
- Operational: When you are able to determine the details about a specific attack, which is important information to be consumed by the Blue Team.
- Strategic: When you can determine the high-level information about the risk of an attack. Since this is more high-level information, this information is usually consumed by executives and managers.
There are different use cases for threat intelligence; for example, it can be used during an investigation to uncover the threat actors who were involved in a particular attack. It can also be integrated with the sensors to help reduce false positives.
Open-source tools for threat intelligence
As mentioned earlier, DHS partners with the intelligence community to enhance its own intelligence, and this is pretty much standard in this field. Collaboration and information sharing are the foundations of the intelligence community. There are many open-source threat intelligence tools out there that can be used. Some are commercial tools (paid), and some are free. You can start consuming threat intelligence by consuming TI feeds. OPSWAT MetaDefender Cloud TI feeds have a variety of options that range from free to paid versions, and they can be delivered in four different formats: JSON, CSV, RSS, and Bro.
For more information about MetaDefender Cloud TI feeds, visit https://www.metadefender.com/threat-intelligence-feeds.
Another option for quick verification is the website https://fraudguard.io. You can perform a quick IP validation to obtain threat intel from that location. In the example that follows, the IP 220.227.71.226 was used as a test (the test result is relative to the day that it was done, which was 10/27/2017), and the result shows the following fields:
{
"isocode": "IN",
"country": "India", "state": "Maharashtra", "city": "Mumbai",
"discover_date": "2017-10-27 09:32:45", "threat": "honeypot_tracker", "risk_level": "5"
}
A complete screenshot of the query is shown here:
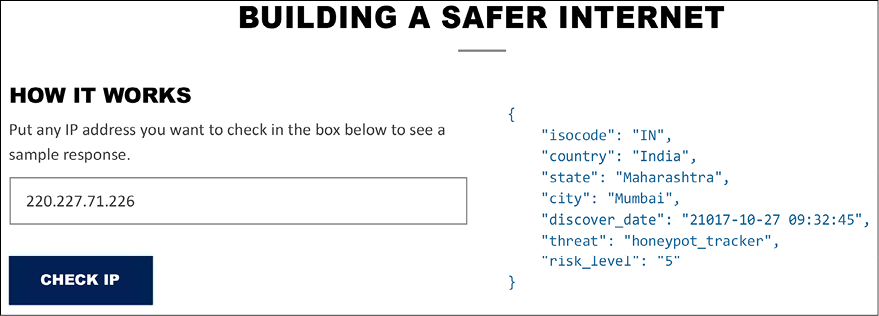
While this is just a simple example, there are more capabilities available that will depend on the level of the service that you are using. It also varies across the free and the paid versions. You can also integrate threat intelligence feeds into your Linux system by using the Critical Stack Intel Feed (https://intel.criticalstack.com/), which integrates with the Bro Network Security Monitor (https://www.bro.org/). Palo Alto Networks also has a free solution called MineMeld (https://live.paloaltonetworks.com/t5/MineMeld/ct-p/MineMeld) that can be used to retrieve threat intelligence.
Visit this GitHub location for a list of free tools, including free threat intel: https://github.com/hslatman/awesome-threat-intelligence.
In scenarios where the incident response team is unsure about whether a specific file is malicious or not, you can also submit it for analysis at https://malwr.com. They provide a decent amount of detail about IoCs and samples that can be used to detect new threats.
As you can see, there are many free resources, but there are also open-source initiatives that are paid, such as AlienVault Unified Security Management (USM) Anywhere (https://www.alienvault.com/products/usm-anywhere). To be fair, this solution is way more than just a source of threat intelligence. It can perform vulnerability assessment, inspect the network traffic, and look for known threats, policy violations, and suspicious activities.
On the initial configuration of AlienVault USM Anywhere, you can configure the Open Threat Exchange (OTX). Note that you need an account for this, as well as a valid key, as shown here:
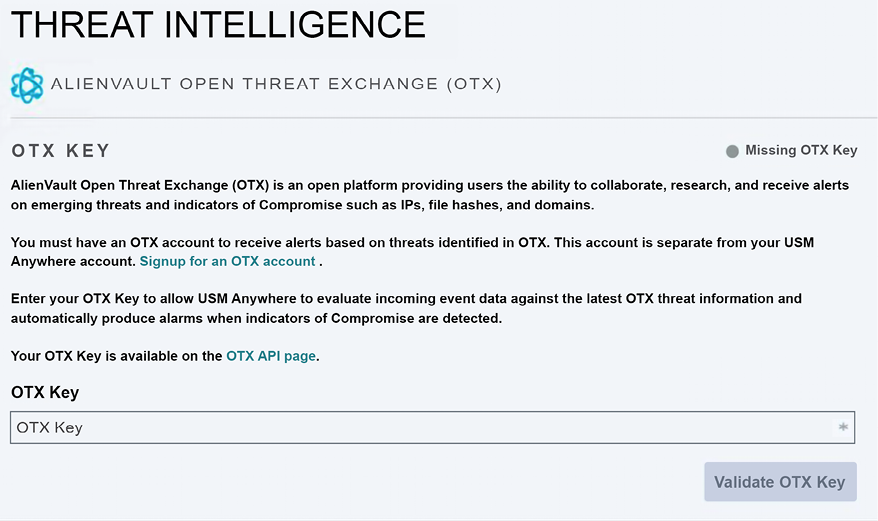
Figure 13.4: Use of the AlienVault Open Threat Exchange (OTX) platform
After you finish configuring, USM will continuously monitor your environment, and when something happens, it will trigger an alarm. You can see the alarm status, and most importantly, which strategy and method were used by this attack, as shown here:
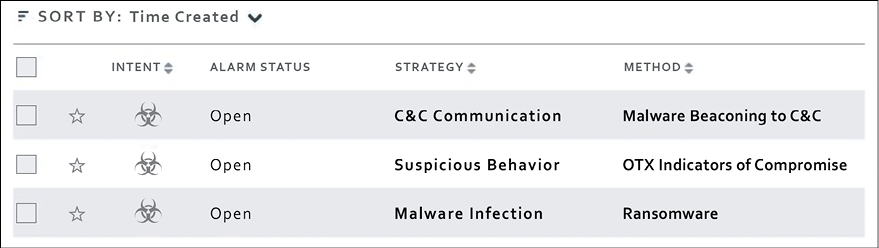
Figure 13.5: Alarm status, strategy, and method, shown in USM
You can dig into the alert and look for more details about the issue; that’s when you will see more details about the threat intelligence that was used to raise this alarm. The image that follows has an example of this alarm; however, for privacy, the IP addresses are hidden:
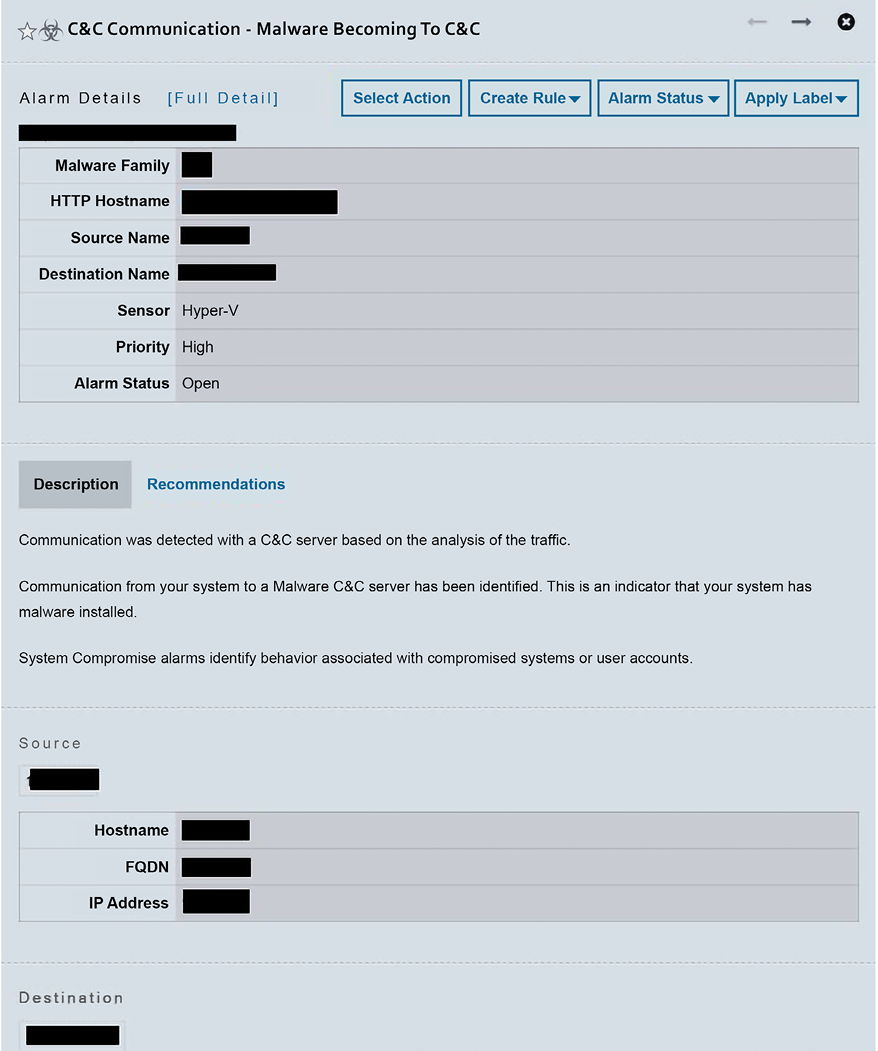
Figure 13.6: Example of a specific USM alarm
The threat intel that was used to generate this alert can vary according to the vendor, but usually it takes into consideration the destination network, the traffic pattern, and potential IoCs. From this list, you have some very important information—the source of the attack, the destination of the attack, the malware family, and a description, which gives you a lot of details about the attack. If you need to pass this information over to the incident response team to take action, you can also click on the Recommendations tab to see what should be done next. While this is a generic recommendation, you can always use it to improve your own response.
At any moment, you can also access OTX Pulse from https://otx.alienvault.com/pulse, and there you have IT information from the latest threats, as shown in the following example:
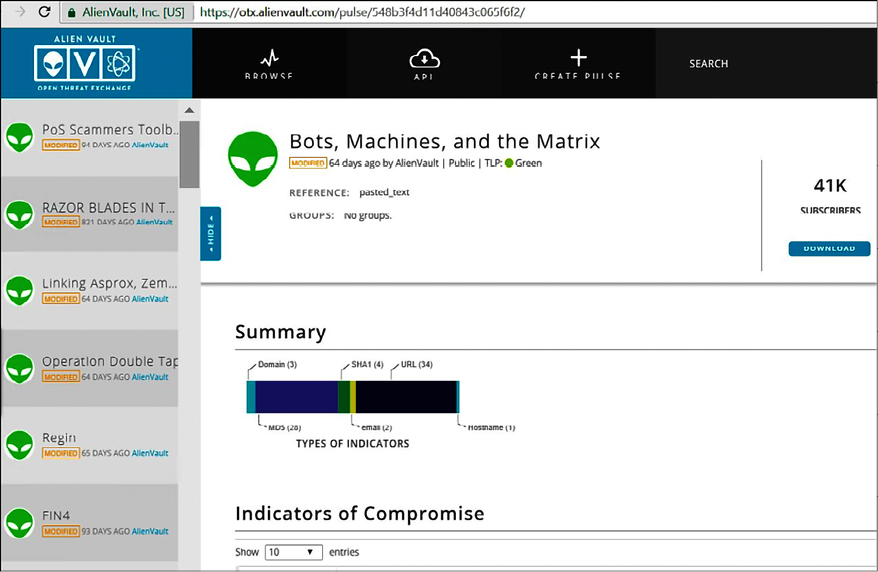
Figure 13.7: A screenshot of the OTX Pulse dashboard
This dashboard gives you a good amount of threat intel information, and while the preceding example shows entries from AlienVault, the community also contributes. Using the search capability on this dashboard to look for more information about a threat (for the example, it was Bad Rabbit) can lead you to get many other insights.
Here is one example of some important data that can be useful to enhance your defense system:
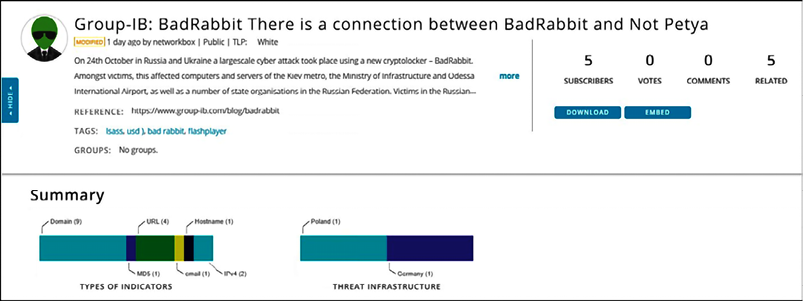
Figure 13.8: Important information for enhancing your defense system from a community contribution
In addition to tools that can be used for verification and analyzing specific issues, there are also a number of free threat intelligence feeds that can be used to keep up to date on threat information.
Free threat intelligence feeds
You can also leverage some free threat intelligence feeds available on the web. Here you have some examples of websites that can be used as your source of threat information:
- Ransomware Tracker Indicators: This site (https://otx.alienvault.com/pulse/56d9db3f4637f2499b6171d7/related) tracks and monitors the status of domain names, IP addresses, and URLs that are associated with ransomware:
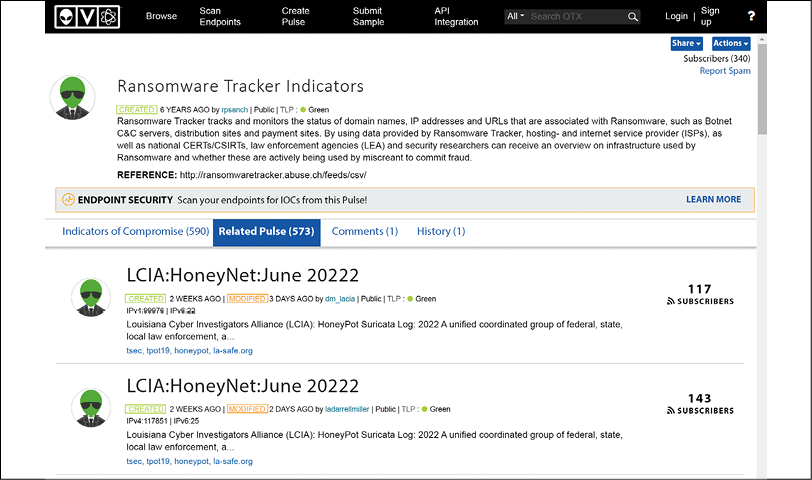
Figure 13.9: A screenshot of Ransomware Tracker Indicators
- Automated Indicator Sharing: This site (https://www.cisa.gov/ais) is from the Department of Homeland Security (DHS). This service enables participants to connect to a DHS-managed system in the Department’s National Cybersecurity and Communications Integration Center (NCCIC), which allows bidirectional sharing of cyber threat indicators:
Figure 13.10: A screenshot from the Homeland Security website, on a page discussing AIS
- Virtus Total: This site (https://www.virustotal.com/) helps you to analyze suspicious files and URLs to detect types of malware:
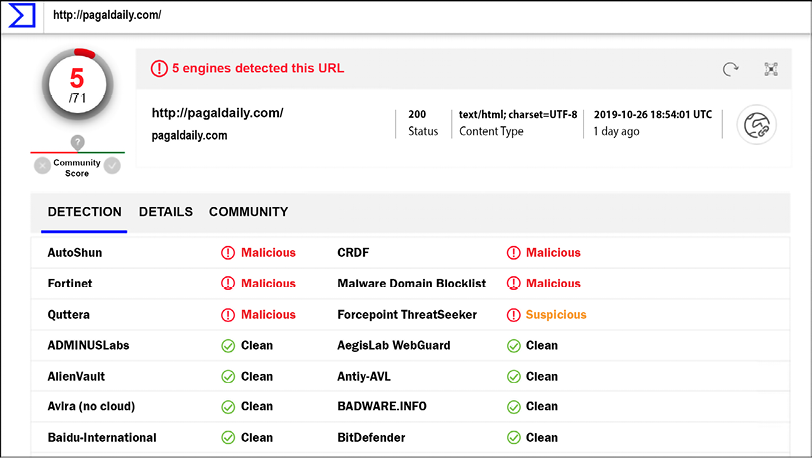
Figure 13.11: Detecting suspicious or malicious files and URLs using Virus Total
- Talos Intelligence: This site (https://www.talosintelligence.com/) is powered by Cisco Talos and it has multiple ways to query threat intel, including URL, file reputation, email, and malware data:
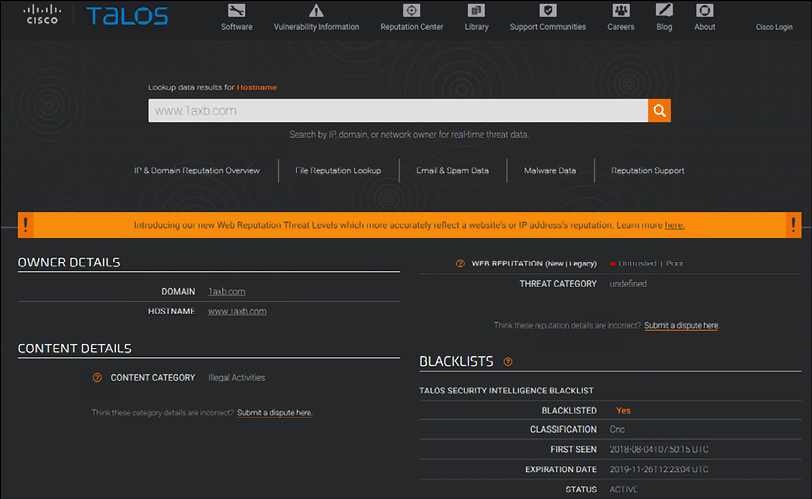
Figure 13.12: A screenshot of Talos Intelligence
- The Harvester: Available on Kali Linux, this tool will gather emails, subdomains, hosts, open ports, and banners from different public sources, including the SHODAN database:
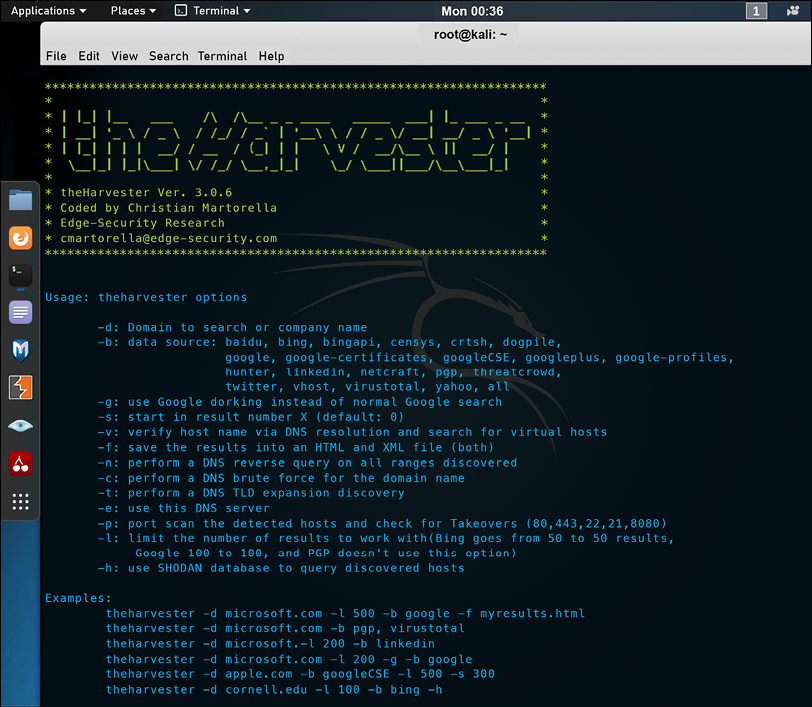
Figure 13.13: A screenshot of The Harvester in action
Using MITRE ATT&CK
According to the MITRE ATT&CK®: Design and Philosophy e-book, “MITRE ATT&CK is a curated knowledge base and model for cyber adversary behavior, reflecting the various phases of an adversary’s attack lifecycle and the platforms they are known to target.” You can leverage this knowledge base to better understand how adversaries are compromising systems and which techniques they are using. This can be beneficial in many scenarios, including when you need to enrich your threat intelligence.
Note: You can download the MITRE ATT&CK®: Design and Philosophy e-book for free at https://attack.mitre.org/docs/ATTACK_Design_and_Philosophy_March_2020.pdf.
Most of the scenarios with Windows and Linux in a corporate environment will be using the ATT&CK Matrix for Enterprise, which is composed of the following phases (in this order):
- Reconnaissance https://attack.mitre.org/tactics/TA0043/
- Resource Development https://attack.mitre.org/tactics/TA0042/
- Initial Access https://attack.mitre.org/tactics/TA0001/
- Execution https://attack.mitre.org/tactics/TA0002/
- Persistence https://attack.mitre.org/tactics/TA0003/
- Privilege Escalation https://attack.mitre.org/tactics/TA0004/
- Defense Evasion https://attack.mitre.org/tactics/TA0005/
- Credential Access https://attack.mitre.org/tactics/TA0006/
- Discovery https://attack.mitre.org/tactics/TA0007/
- Lateral Movement https://attack.mitre.org/tactics/TA0008/
- Collection https://attack.mitre.org/tactics/TA0009/
- Command and Control https://attack.mitre.org/tactics/TA0011/
- Exfiltration https://attack.mitre.org/tactics/TA0010/
- Impact https://attack.mitre.org/tactics/TA0040/
Note: To see the entire matrix in a table representation, go to https://attack.mitre.org/matrices/enterprise.
When reviewing information that can be useful to understand how adversaries are operating, you will be able to map the behavior with a specific phase of the matrix. The raw data collected by event systems, such as security information and event management (SIEM) platforms, will give you a lot of indication of what is happening in the environment. Let’s use an example where the incident response team received a ticket that reported a system that was presenting suspicious behavior, and upon reviewing the raw logs, you noticed that the following commands were utilized in the system:
ipconfig /all
arp -a
tasklist /v
sc query
net group "Domain Admins" /domain
net user /domain
net group "Domain Controllers" /domain
netsh advfirewall show allprofiles
netstat -ano
Notice that all these are built-in Windows commands, so by nature, they are not only benign, but legitimate administrative commands. So why is this suspicious? Because of two indications: the system is behaving suspiciously, and the execution order of these commands may indicate a malicious operation. This information is gold, and you can use MITRE ATT&CK to help you understand the scenarios in which these commands are used.
The first step is to visit the MITRE ATT&CK website https://attack.mitre.org; from there, you can click on the Search button as shown below:
Figure 13.14: Using the Search capability on the MITRE ATT&CK website
In the Search floating window, type ipconfig and you will see that among the results, ipconfig, Software S0100 appears, as shown below:
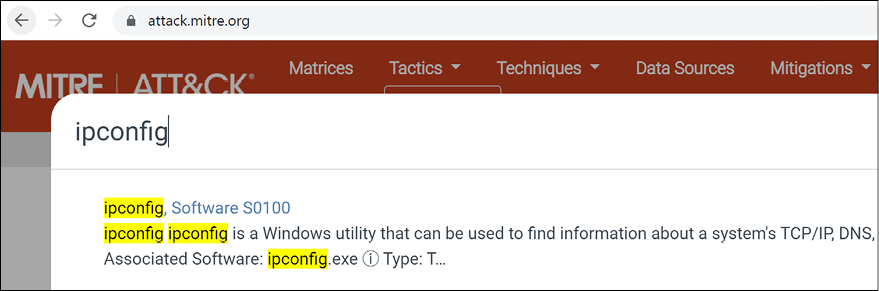
Figure 13.15: Selecting the search result
On the ipconfig page, you will see the details about this command and the mapping for the technique and the groups (adversaries) that use this software. Notice that the technique in which this software is used is mapped to System Network Configuration Discovery, as shown in the figure below (which is part of the page that you visited):
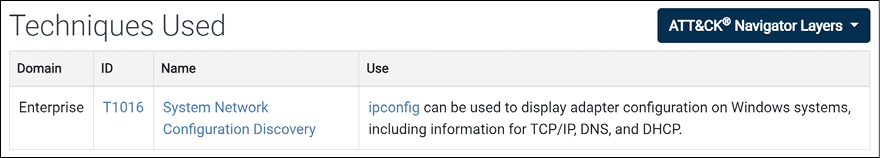
Figure 13.16: Technique that leverages this software
If you click on this technique (T1016), you will see that this is actually a sub-technique from Discovery. What does this tell you? It tells you that in the discovery phase, the adversary is still trying to understand the environment. This indicates that the threat actor is still at the beginning of their mission.
Another important piece of information available in this page is the Procedures Examples, which shows examples of the usage of this software for malicious activities by different adversaries. To better understand how to use it, let’s do the following exercise:
- Search for Cobalt Strike on this page.
- Click on it and you should be redirected to this page: https://attack.mitre.org/software/S0154.
- On this page, search for System Network Configuration Discovery.
- Now read the description on how Cobalt Strike uses this sub-technique.
Another way to visualize this is by leveraging the MITRE ATT&CK Navigator. To start using this tool, access the website https://mitre-attack.github.io/attack-navigator. On the first page, click the Create New layer option and then select Enterprise, as shown below:

Figure 13.17: Technique that leverages this software
This will launch the MITRE ATT&CK Navigator; from there, click on the Search button, as shown in Figure 13.18:
Figure 13.18: Search button
Now type Cobalt Strike, and on the result, expand Software, click Cobalt Strike, and click the Select button. You will notice that different phases got highlighted, but to make it easier to see, let’s change the color by changing the scoring number. Click on the Scoring button, type 1, and then click on the button again to hide the floating menu:
Figure 13.19: Scoring button
Now you can clearly see where Cobalt Strike has techniques mapped to, as shown below:
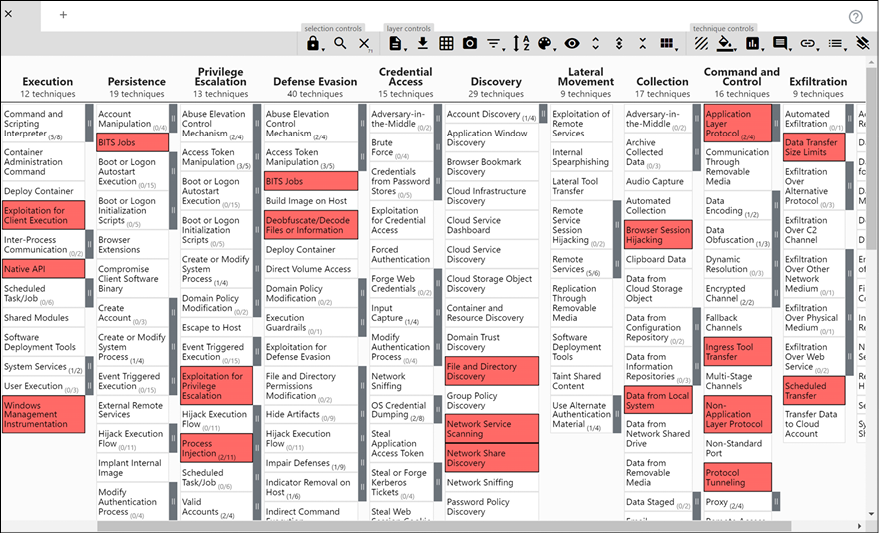
Figure 13.20: MITRE ATT&CK Navigator
This is critical information to have as part of your investigation. From there, you can pivot back to the page for more information. For example, under Execution, you will see that Windows Management Instrumentation was highlighted. This means that Cobalt Strike uses that, and if you need more information on how to mitigate this, you can right-click on Windows Management Instrumentation and select View Technique. This will lead you to the https://attack.mitre.org/techniques/T1047/ page, and there you can search for Mitigations.
The steps below summarize the use of this tool to help during your investigation:
- Find the behavior: This can come from your raw logs or the description of an incident.
- Research the behavior: Try to better understand the scenario, the overall behavior of the attack. Maybe here you need to pull logs from other data sources. Also, take notes of things you don’t know, for example, if you see a TCP connection on an unknown port to you, research more about that port.
- Convert the behavior into a MITRE ATT&CK tactic: Here is where you will leverage the MITRE ATT&CK website (as we did in this section).
- Identify techniques and sub-technique: As you continue to explore the MITRE ATT&CK tactic, you will land on more details about the techniques and sub-techniques in use. Keep in mind that not every behavior is a technique or subtechnique. You always need to take into consideration the context.
Microsoft threat intelligence
For organizations that are using Microsoft products, whether on-premises or in the cloud, they consume threat intelligence as part of the product itself. That’s because, nowadays, many Microsoft products and services take advantage of shared threat intelligence, and with this, they can offer context, relevance, and priority management to help people take action.
Microsoft consumes threat intelligence through different channels, such as:
- The Microsoft Threat Intelligence Center, which aggregates data from:
- Honeypots, malicious IP addresses, botnets, and malware detonation feeds
- Third-party sources (threat intelligence feeds)
- Human-based observation and intelligence collection
- Intelligence coming from consumption of their service
- Intelligence feeds generated by Microsoft and third parties
Microsoft integrates the result of this threat intelligence into its products, such as Microsoft Sentinel, Microsoft Defender for Cloud, Office 365 Threat Intelligence, Microsoft Defender for Cloud Apps, Microsoft Defender for Identity, and others.
Visit https://aka.ms/MSTI for more information about how Microsoft uses threat intelligence to protect, detect, and respond to threats.
Microsoft Sentinel
In 2019, Microsoft launched its first SIEM tool, which was initially called Azure Sentinel, and in 2021, it changed its name to Microsoft Sentinel. This platform enables you to connect with Microsoft Threat Intelligence and perform data correlation with the data that was ingested.
You can use the Threat Intelligence Platforms connector to connect to Microsoft Threat intelligence, shown as follows:
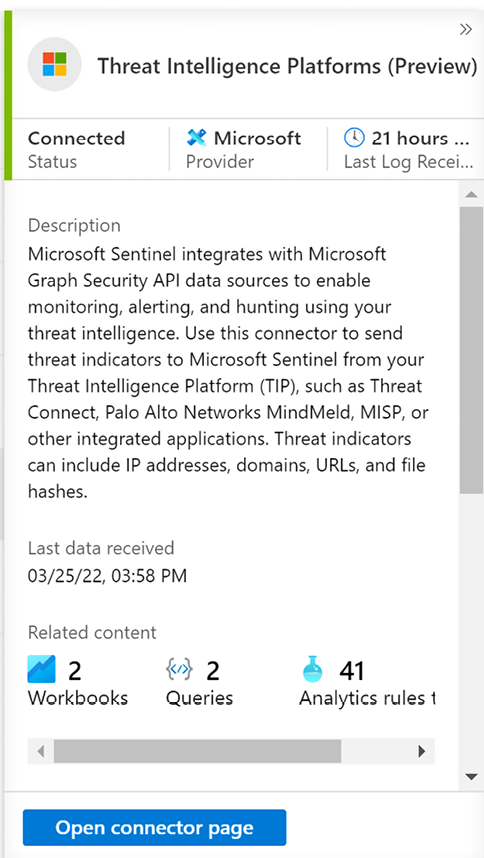
Figure 13.21: A screenshot of the Threat Intelligence Platforms connector
Microsoft Sentinel aggregates all the threat intelligence information in a page that summarizes all the activities, as shown below:
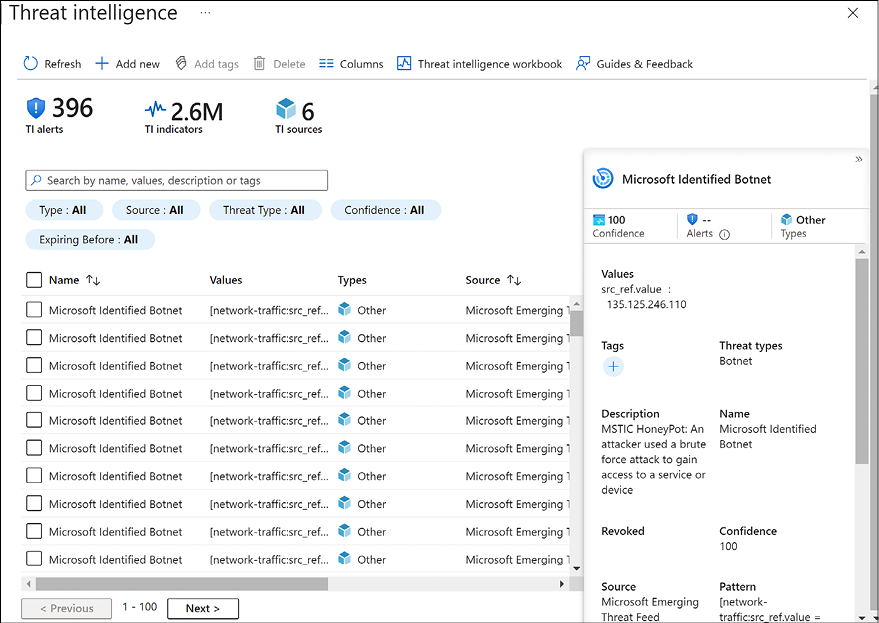
Figure 13.22: A screenshot of the Threat intelligence page in Microsoft Sentinel
If you need to get more details, statistics, and a more robust overview across all your CTIs, you can use the Threat Intelligence workbook, which can be accessed by clicking on the Threat intelligence workbook button on the page shown in Figure 13.22.
Once you click, you will see the workbook, as shown in the following figure:
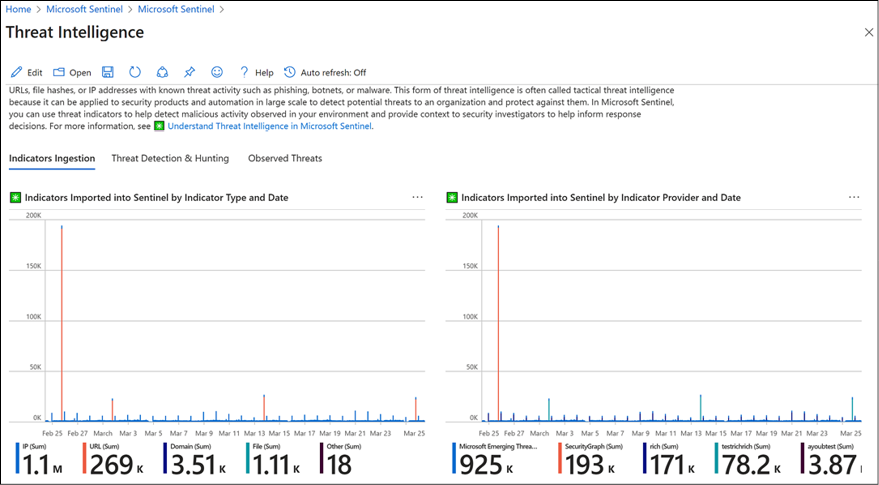
Figure 13.23: A screenshot of the Threat Intelligence workbook
It is well worth taking advantage of the intelligence provided by Microsoft Sentinel, particularly for organizations that already use Microsoft products in their daily activities.
Summary
In this chapter, you learned about the importance of threat intelligence and how it can be used to gain more information about current threat actors and their techniques and, in some circumstances, predict their next step. You learned how to leverage threat intelligence from the open source community based on some free tools, as well as commercial ones.
You learned how to use the MITRE ATT&CK framework and the MITRE ATT&CK Navigator to understand adversaries’ behavior and how they are leveraging different techniques and subtechniques for their operations.
Next, you learned how Microsoft integrates threat intelligence as part of its products and services, and how to use Microsoft Sentinel not only to consume threat intelligence, but also to visualize potentially compromised features of your environment based on the threat intel acquired, compared to your own data.
In the next chapter, we will continue talking about defense strategies, but this time, we will focus on response, which is a continuation of what we started in this chapter. You will learn more about the investigation, both on-premises and in the cloud.
References
- Microsoft Lean on the Machine Report: http://download.microsoft.com/download/3/4/0/3409C40C-2E1C-4A55-BD5B-51F5E1164E20/Microsoft_Lean_on_the_Machine_EN_US.pdf
- Wanna Decryptor (WNCRY) Ransomware Explained: https://blog.rapid7.com/2017/05/12/wanna-decryptor-wncry-ransomwareexplained/
- A Technical Analysis of WannaCry Ransomware: https://logrhythm.com/blog/a-technical-analysis-of-wannacry-ransomware/
- New ransomware, old techniques: Petya adds worm capabilities: https://blogs.technet.microsoft.com/mmpc/2017/06/27/new-ransomware-oldtechniques-petya-adds-worm-capabilities/
- MITRE ATT&CK https://attack.mitre.org/
Join our community on Discord
Join our community’s Discord space for discussions with the author and other readers:

