10
Security Policy
From Chapter 4, Understanding the Cybersecurity Kill Chain, to Chapter 9, Privilege Escalation, we covered attack strategies, and how the Red Team could enhance an organization’s security posture by leveraging common attack techniques. Now it is time to switch gears and start looking at things from an exclusively defensive perspective. There is no other way to start talking about defense strategies other than by starting with security policies. A good set of security policies is essential to ensure that the entire company follows a well-defined set of ground rules that will help to safeguard its data and systems.
In this chapter, we are going to cover the following topics:
- Reviewing your security policy
- Educating the end user
- Policy enforcement
- Monitoring for compliance
Let’s start by highlighting the importance of reviewing your security policy, and the best ways to go about this task.
Reviewing your security policy
Perhaps the first question should be—”Do you even have a security policy in place?” Even if the answer is “Yes,” you still need to continue asking these questions. The next question is—”Do you enforce this policy?” Again, even if the answer is “Yes,” you must follow up with—”How often do you review this security policy, looking for improvements?” OK, now we’ve got to the point where we can safely conclude that a security policy is a living document—it needs to be revised and updated.
Security policies should include industry standards, procedures, and guidelines, which are necessary to support information risks in daily operations. These policies must also have a well-defined scope.
It is imperative to understand the scope of applicability of the security policy. The policy should state the area(s) to which it can be applied.
For example, if it applies to all data and systems, this must be clear to everyone reading it. Another question that you must ask is: “Does this policy also apply to contractors?” Regardless of whether the answer is “Yes” or “No,” it must be stated in the scope section of the policy.
The foundation of the security policy should be based on the security triad (confidentiality, integrity, and availability). Ultimately, the users are required to protect and ensure the applicability of the security triad in the data and systems, which is independent of how that data was created, shared, or stored. Users must be aware of their responsibilities, and the consequences of violating these policies. Make sure that you also include a section that specifies the roles and responsibilities, since this is very important for accountability purposes.
It is also important to make it clear which documents are involved in the overall security policy, since there are more than one. Make sure all users understand the difference between the following documents:
- Policy: This is the basis of everything; it sets high-level expectations. It will also be used to guide decisions and achieve outcomes.
- Procedure: As the name suggests, this is a document that has procedural steps that outline how something must be done.
- Standard: This document establishes requirements that must be followed. In other words, everyone must comply with certain standards that were previously established.
- Guidelines: Although many would argue that guidelines are optional, they are in fact recommended guidance. Having said that, it is important to note that each company has the freedom to define whether the guidelines are optional, or if they are recommended.
- Best practices: As the name says, these are best practices to be implemented by the entire company, or just some departments within the company. This can also be established per role—for example, all web servers should have security best practices from the vendor applied prior to being deployed in production.
To make sure that all these points are synchronized, managed, and have the upper management sponsorship, you need to create an organization-wide security program. The NIST 800-53 publication suggests the following organization security control objective relationships:
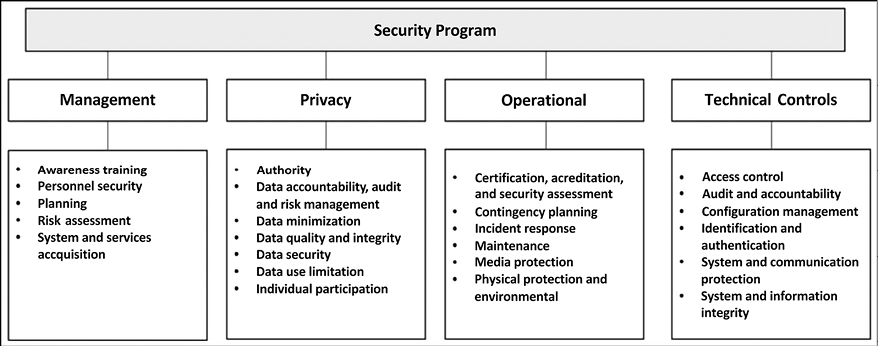
Figure 10.1: Organization security control objectives, from the NIST 800-53 publication
We would need an entire book just to discuss all the elements that are in this diagram. Therefore, we strongly recommend that you read the NIST 800-53 publication if you want more information on these areas.
Shift left approach
We hear a lot of people saying that they are shifting left, when it comes to adding guardrails to their deployment. But what does this really mean for the overall security policy? The shift left approach continues to grow due the cloud computing adoption, as most of the shift left implementations are using cloud computing-based technology. The goal of ‘shifting left’ is to ensure that the security policies are added as guardrails in the beginning of the pipeline to avoid workloads being provisioned without using the company standards.
A classic example is when users are trying to provision a storage account to use, and they just perform the default selection without taking security in consideration and hardening that deployment. If you have your policies well established in the beginning of the pipeline, that attempt of provisioning a resource that is not in compliance with company’s standard will fail, and the resource will not be deployed in production.
This approach is becoming extremely important as companies continue to embrace cloud computing workloads. It is important to add all necessary guardrails to avoid deploying resources that are not secure by default.
It is very important to also mention that when we state that security is shifting left, it is because the goal is to also include security early on the development lifecycle. So from the developer’s standpoint, they should not think about security only after they deploy their app, they need to think of security in each stage of the development process, from beginning to the end.
Nowadays Developers are using automations in various steps of the application development, and they use continuous integration/continuous delivery (CI/CD) to accomplish that. With this model and the idea that security must shift left, what we have at the end looks like the diagram below:
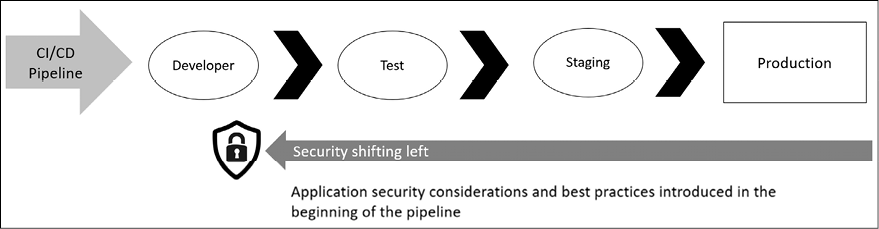
Figure 10.2: Security is shifting left
While the diagram above is more a representation of how developers are leveraging automation to continuous deliver their software, the same rationale applies to policies, because in cloud computing you can also use automation to continuously deploy resources, and security policies must shift left to ensure that you are not allowing resources to be deployed if they are not compliant with your security policy.
But, as you can imagine, this new approach requires everyone to be on the same page when it comes to security practices, and that’s why the very first step is to ensure that you are educating the user to think about security in every single operation.
Educating the end user
As shown in Figure 10.1, the end user’s education is part of the management security control, under awareness training. Perhaps this is one of the most important pieces of the security program, because a user who is uneducated in security practices can cause tremendous damage to your organization.
According to Symantec Internet Security Threat Report Volume 24, spam campaigns are still increasing relative to previous years, and although nowadays they rely on a great range of tactics, the largest malware spamming operations are still mainly reliant upon social engineering techniques.
Another platform that is being used to launch social engineering attacks is social media. In 2019, Symantec reported that social media was used in many campaigns to influence people during times of decision, including elections. The extensive use of fake accounts in social media platforms to create malicious campaigns was also uncovered by Twitter, which led them to remove more than 10,000 accounts from their platform.
The problem is that many users will be using their own device to access company information, a practice known as bring your own device (BYOD), and when they are participating in false social media campaigns like this, they are easy targets for hackers. If hackers can compromise the user’s system, they are very close to gaining access to the company’s data, since most of the time they are not isolated.
All these scenarios only make a stronger case for educating users against this type of attack, and any other type of social engineering attacks, including physical approaches to social engineering.
Social media security guidelines for users
In an article titled Social Media Impact, published by the ISSA Journal and written by the coauthor of this book, Yuri Diogenes, many cases were examined where social media was the main tool for the social engineering attack. The security program must be in line with HR and legal requirements regarding how the company should handle social media posts and give guidelines to employees on how they should handle their own social media presence.
One of the tricky questions while defining a set of guidelines to employees on how to use social media is the definition of appropriate business behavior. The appropriate business behavior when using social media has a direct impact on security policy. What your employees will say can compromise your brand, your release plans, and the overall security of your assets. For example, say an employee uses social media to publish a picture of a highly secure facility and the picture includes the geolocation of the facility. This can have a direct impact on your physical security policy, since now attackers may know where this facility is physically located. An employee using social media to make inflammatory or inappropriate comments may encourage malicious attacks against the company that they are associated with, particularly if the company is perceived to be complacent regarding these actions.
Disciplinary actions against employees that cross this boundary should be very clear. In October 2017, right after the mass shooting in Las Vegas, the CBS vice president made a comment implying that “Vegas victims didn’t deserve sympathy because country music fans are often Republicans.” The result of this online comment was simple: she was fired for violating the company’s standards of conduct. While it was important for CBS to apologize rapidly for her behavior and show policy enforcement by firing the employee, the company was still hurt by this person’s comments.
With the political tensions in the world and the freedom that social media gives to individuals to externalize their thoughts, situations like this are arising every single day. In August 2017, a Florida professor was fired for tweeting that Texas deserved Hurricane Harvey after voting for Trump. This is another example of an employee using his personal Twitter account to rant online and reaping bad consequences. Often, companies base their decision for firing an employee who misbehaved online on their code of conduct.
For example, if you read the Outside Communications section in the Google Code of Conduct, you will see how Google makes recommendations regarding the public disclosure of information.
Another important guideline to include is how to deal with defamatory posts, as well as pornographic posts, proprietary issues, harassment, or posts that can create a hostile work environment. These are imperative for most social media guidelines, and it shows that the employer is being diligent in promoting a healthy social environment within the company.
The reasons these examples are relevant for properly planning the education of your users when it comes to social media is because there are many threat actors that will research an organization by leveraging social media content. During the reconnaissance phase of an attack, threat actors may scan social media to find pattern of usage and more information about a company. A company that doesn’t have a clear social media policy, and behavior guidelines when it comes to sharing information, may face scenarios where their employees are talking about sensitive information online. Social media guidelines are also usually enforced as part of the overall security awareness training, as many threat actors may engage in social media conversations to show empathy with someone and build a relationship to obtain more information. As one starts to vent more information online, they may end up revealing more information about their own preferences and political and social views. All these attributes could also be used in the future to craft phishing emails because the threat actor will know that a specific topic will entice the user to open the email.
Social media guidelines must be always updated to be aligned with current trends. One recent example is COVID-19, which added even more complexity to the existing social media guidelines challenges since it is a moving target and there are new developments happening all the time. What was considered acceptable to speak publicly about the topic may have changed and now the company needs to adjust its policy and ensure that their employees are fully aware of the new guidelines.
Security awareness training
Security awareness training should be delivered to all employees, and it should be constantly updated to include new attack techniques and considerations. Many companies are delivering such training online, via the company’s intranet. If the training is well crafted, rich in visual capabilities, and contains a self-assessment at the end, it can be very effective. Ideally, the security awareness training should contain:
- Real-world examples: Users will more easily remember things if you show a real scenario. For example, talking about phishing emails without showing what a phishing email looks like, and how to visually identify one, won’t be very effective.
- Practice: Well-written text and rich visual elements are important attributes in training materials, but you must submit the user to some practical scenarios. Let the user interact with the computer to identify spear phishing or a fake social media campaign.
At the end of the training, all users should acknowledge that they successfully finalized the training, and that they are aware not only about the security threats and countermeasures covered in the training, but also about the consequences of not following the company’s security policy.
It is also important to ensure that security awareness training is updated at least once a quarter to include new attacks and scenarios. Even if there are not new attacks from the technical perspective, there are always new scenarios of exploitation that everyone can learn from. One place that you can visit on a monthly basis to learn about the new attacks and techniques being used is the MITRE ATT&CK website https://attack.mitre.org and from there navigate through the ATT&CK Matrix for Enterprise.
Policy enforcement
Once you finish building your security policy, it is time to enforce it, and this enforcement will take place by using different technologies according to the company’s needs. Ideally, you will have an architecture diagram of your network to understand fully what the endpoints are, what servers you have, how the information flows, where the information is stored, who has and who should have data access, and the different entry points to your network.
Many companies fail to enforce policies fully because they only think of enforcing policies at endpoints and servers.
What about network devices? That’s why you need a holistic approach to tackle every single component that is active in the network, including switches, printers, and IoT devices.
If your company has Microsoft Active Directory, you should leverage the Group Policy Object (GPO) to deploy your security policies. These policies should be deployed according to your company’s security policy. If different departments have different needs, you can segment your deployment using organizational units (OUs) and assign policies per OU.
For example, if the servers that belong to the HR department require a different set of policies, you should move these servers to the HR OU and assign a custom policy to this OU.
If you are unsure about the current state of your security policies, you should perform an initial assessment using the PowerShell command Get-GPOReport to export all policies to an HTML file. Make sure that you run the following command from a domain controller:
PS C:> Import-Module GroupPolicy
PS C:> Get-GPOReport -All -ReportType HTML -Path .GPO.html
The result of this command is shown here:
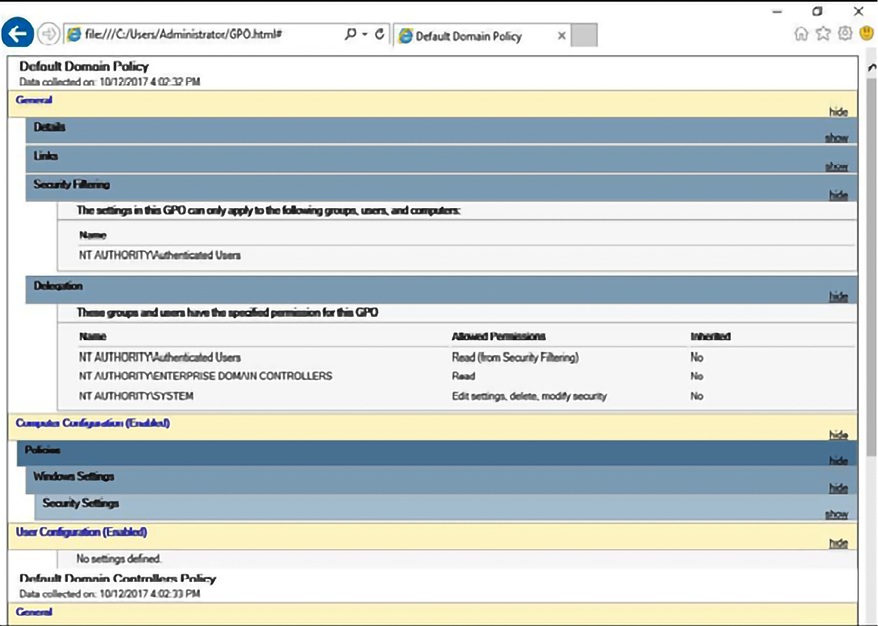
Figure 10.3: Results of the Get-GPOReport command
It is also recommended that you perform a backup of the current configuration and make a copy of this report before making any change to the current group policies. Another tool that you can also use to perform this assessment is the policy viewer, part of the Microsoft Security Compliance toolkit:
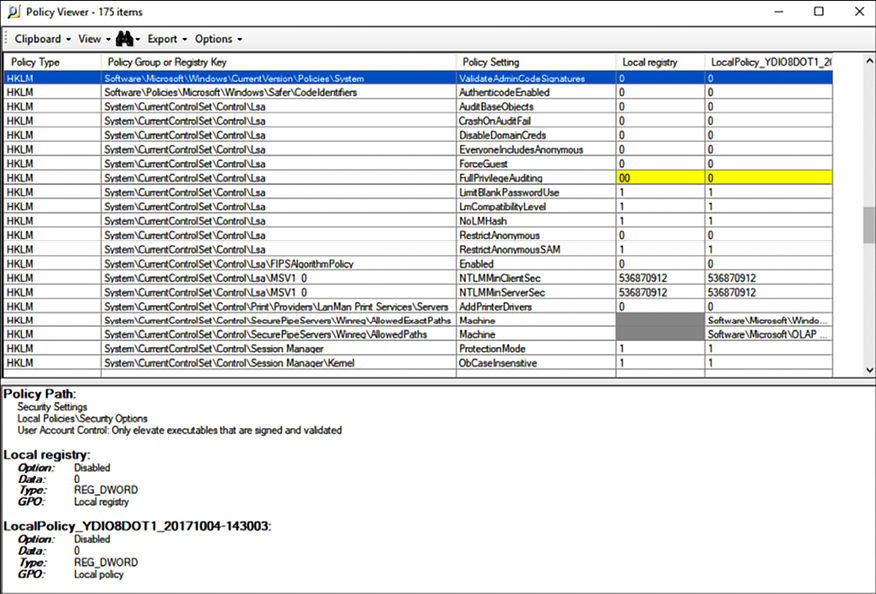
Figure 10.4: Screenshot of the Policy Viewer, part of the Microsoft Security Compliance Toolkit
The advantage of this tool is that it doesn’t just look into the GPOs, but also into the correlation that a policy has with a registry’s key values. This is a great advantage because you will immediately know what changes will be done in the registry based on those policies. Having this knowledge can help you later on to troubleshoot an issue, and even investigate a security incident where changes were made to those registry keys. You will immediately know what the threat actor was trying to achieve, since you know the policy that they were trying to change.
Policies in the cloud
If you have a hybrid environment with workloads on-premises and in the cloud, you also want to ensure that you have policies in place for your cloud-based resources. In Azure this can be done using Azure Policy:
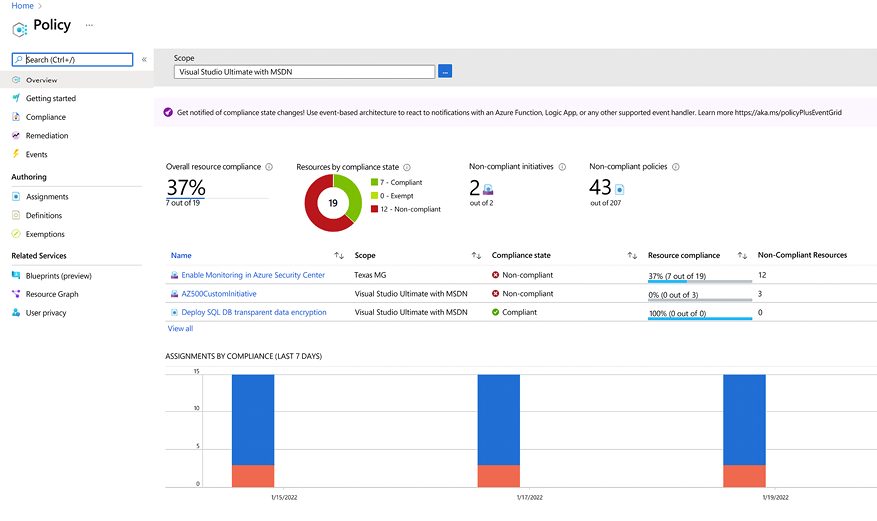
Figure 10.5: Azure Policy main dashboard
In Azure Policy you can easily see the policies that are assigned and the scope of that policy. As you can see in Figure 10.5, there are some policies that are assigned to the Management Group level and others that are assigned to the entire subscription. The decision if a policy will be assigned to a Management Group level or the entire subscription varies according to how your resources are organized and the overall architecture of your organization. In the example shown in Figure 10.6 we have an organization that has one Azure AD Tenant, but multiple subscriptions. However, they want to ensure that all branches in each region of the globe will have similar policies, so they created a Management Group that reflect the global region and are assigning the policy to the management that contains the subscriptions. As a result, the subscriptions will inherit the policies that were established in the management group level.
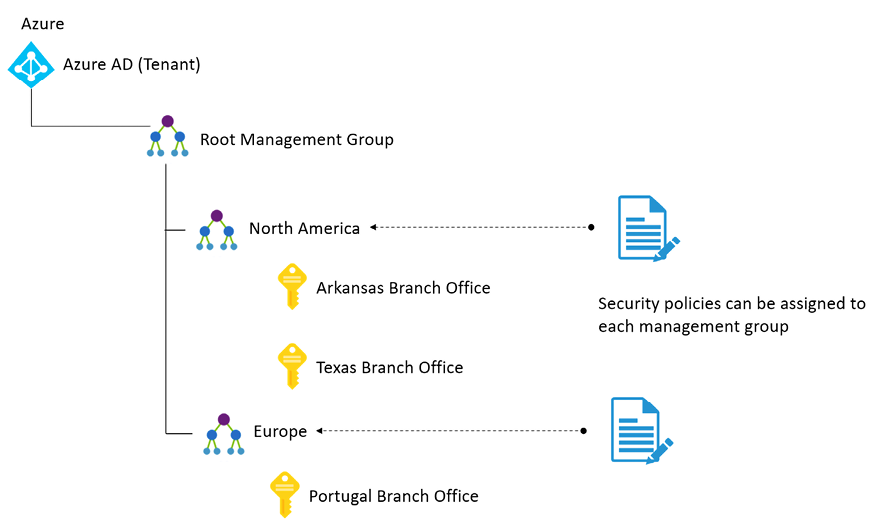
Figure 10.6: Designing management groups and policies
While the designing of how the management groups and subscriptions will be distributed, it is even more important to understand which policies are going to be used as audit only and which ones you want to enforce. In cloud computing we want to ensure that users are able to provision resources on their own, but we also need to ensure that security is in place to prevent the deployment of resources that are not secure. That’s the balance that you will need to fine tune.
Application whitelisting
If your organization’s security policy dictates that only licensed software is allowed to run in the user’s computer, you need to prevent users from running unlicensed software, and restrict the use of licensed software that is not authorized by IT. Policy enforcement ensures that only authorized applications will run on the system.
Important: We recommend that you read NIST publication 800-167 for further guidance on application whitelisting. Download this guide from http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-167.pdf.
When planning policy enforcement for applications, you should create a list of all apps that are authorized to be used in the company. Based on this list, you should investigate the details about these apps by asking the following questions:
- What’s the installation path for each app?
- What’s the vendor’s update policy for these apps?
- What executable files are used by these apps?
The more information you can get about the app itself, the more tangible data you will have to determine whether or not an app has been tampered with. For Windows systems, you should plan to use AppLocker and specify which applications are allowed to run on the local computer.
In AppLocker, there are three types of conditions to evaluate an app, which are:
- Publisher: This should be used if you want to create a rule that will evaluate an app that was signed by the software vendor
- Path: This should be used if you want to create a rule that will evaluate the application path
- File hash: This should be used if you want to create a rule that will evaluate an app that is not signed by the software vendor
These options will appear in the Conditions page when you run the Create Executable Rules wizard. To access this, use the steps below:
- Click the Windows button, type
Run, and click on it. - Type
secpol.mscand click OK. - Expand Application Control Policies and expand AppLocker.
- Right click Executable Rules, select Create New Rule and follow the wizard:
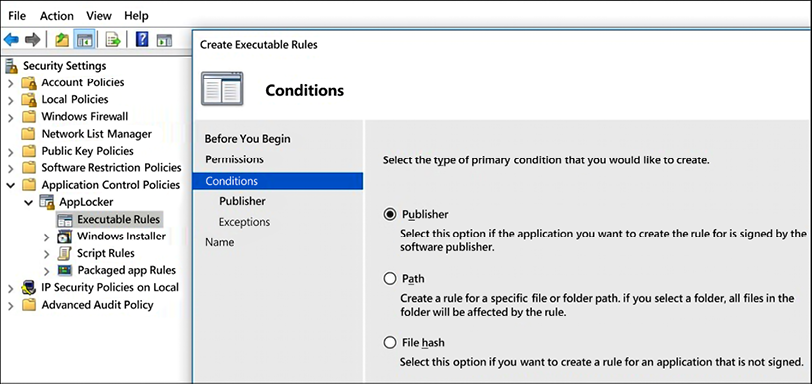
Figure 10.7: The Conditions page that appears when running the Create Executable Rules wizard
Which option you choose will depend on your needs, but these three choices should cover the majority of the deployment scenarios. Keep in mind that, depending on which option you choose, a new set of questions will appear on the page that follows.
Make sure that you read the AppLocker documentation at https://docs.microsoft.com/en-us/windows/device-security/applocker/applocker-overview.
To whitelist apps in an Apple OS, you can use Gatekeeper (https://support.apple.com/en-us/HT202491), and in a Linux OS you can use SELinux.
Another option to whitelist an application is to use a platform such as Microsoft Defender for Cloud that leverages machine learning capabilities to learn more about the apps, and automatically create a list of apps that you should whitelist. The advantage of this feature is that it works not only for Windows, but also for Linux machines.
The machine learning usually takes two weeks to learn about the applications, and after that a list of apps is suggested and at that point you can enable as is, or you can make customizations to the list. The figure below shows an example of the application control policy in Microsoft Defender for Cloud:
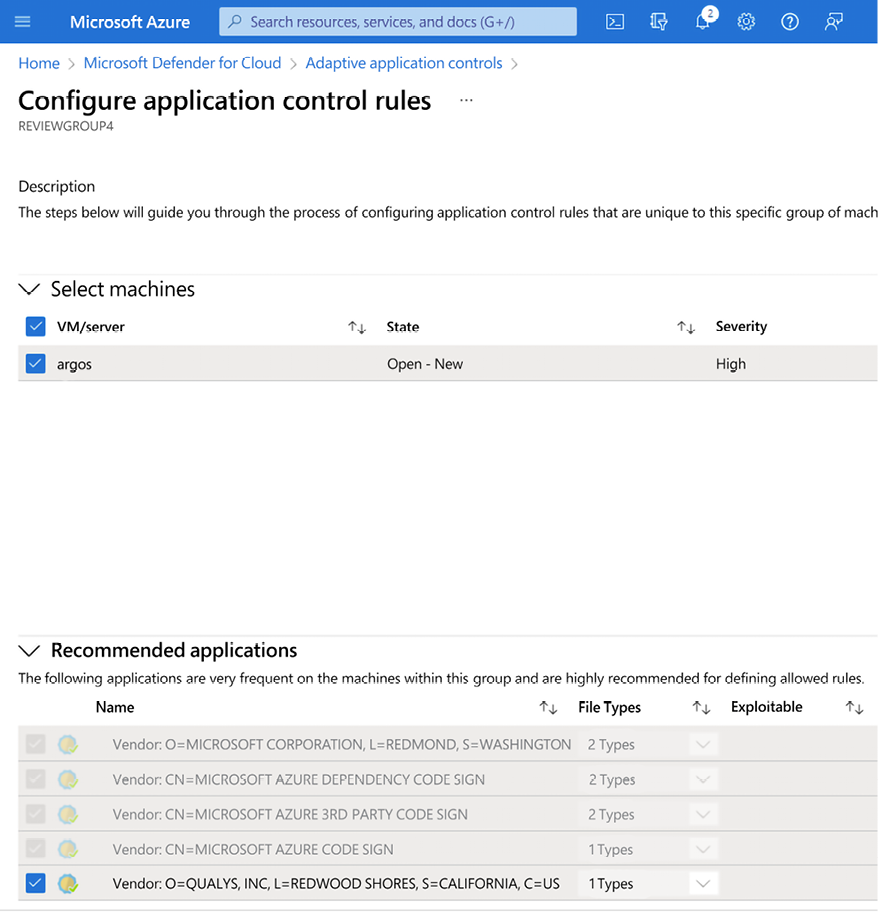
Figure 10.8: An example of the application control policy, found in Microsoft Defender for Cloud
The adaptive application control works for Azure VMs, and for computers located on-premises and in other cloud providers. For more information on this feature, access https://docs.microsoft.com/en-us/azure/defender-for-cloud/adaptive-application-controls.
When a user executes an application that is not covered by the Adaptive Application Control policy, you will receive an alert similar to the one shown in Figure 10.9:
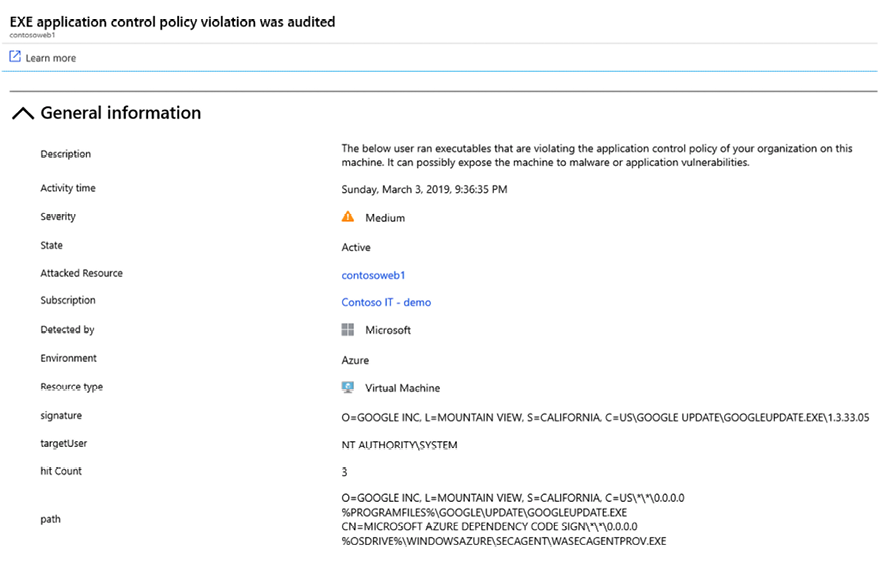
Figure 10.9: Alert triggered for an application not covered by Adaptive Application Control policy
As you can see, there are many different ways you can whitelist applications. Regardless of which method you choose, it is important to ensure you whitelist the right applications for your organization, and prevent access to any applications that could cause harm. This is an important step in making sure that only the necessary people have access to the necessary apps within your organization, but it is also well worth employing guardrails and hardening your defenses in other areas as well.
Hardening
As you start planning your policy deployment and addressing which setting should be changed to better protect the computers, you are basically hardening them to reduce the attack vector. You can apply Common Configuration Enumeration (CCE) guidelines to your computers. For more information about CCE, visit https://nvd.nist.gov/config/cce/index.
Important: Do not confuse CCE with Common Vulnerability and Exposure (CVE), which usually requires a patch to be deployed in order to mitigate a certain vulnerability that was exposed. For more information about CVE, visit https://cve.mitre.org/.
To optimize your deployment, you should also consider using security baselines. This can assist you in better managing not only the security aspect of the computer, but also its compliance with company policy. For the Windows platform, you can use the Microsoft Security Compliance Manager. You need to download this tool from the Microsoft website (https://www.microsoft.com/en-us/download/details.aspx?id=53353) and install it on your Windows system.
While CCE is a good alternative to get start hardening your system, you should also take in consideration the compliance requirements that your organization must be in alignment. For example, if you organization has workloads that handle branded credit cards from the major card schemes, these workloads will need to be compliant with the Payment Card Industry Data Security Standard (PCI DSS).
You can leverage Cloud Security Posture Management platforms such as Microsoft Defender for Cloud to get better visibility if your workloads are compliant to this standard, as shown in the example of Figure 10.10:
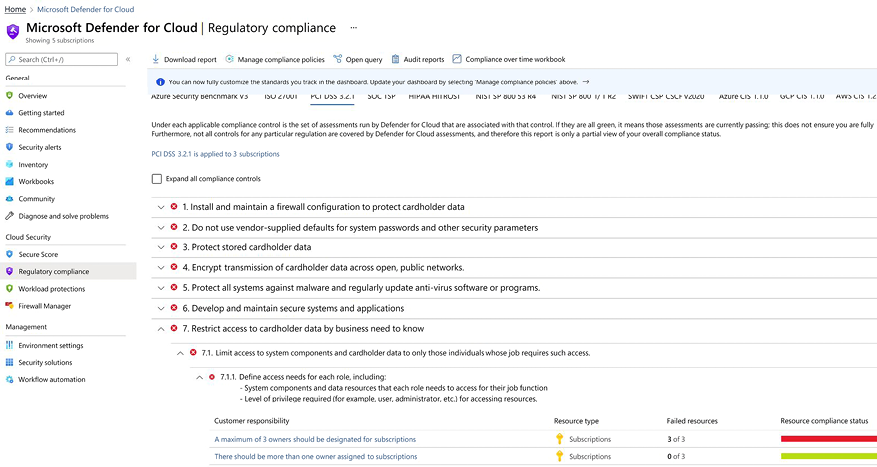
Figure 10.10: An example of the Defender for Cloud Regulatory Compliance dashboard
In the example shown in Figure 10.10, you have the clear description of the security recommendation that must be remediated in order to be compliant with PCI DSS 3.2.1, item 7.1.1, which specifies security control requirements for system components and data resources that each role needs to access for their job function, and the level of privilege required for accessing resources.
Notice also in Figure 10.10 that there are different tabs for different industry standards, which can also help to measure your current compliance state if you have different workloads that need to be compliant with different industry standards.
Once you understand the type of baseline you will utilize, you can deploy guardrails at the beginning of the pipeline that will enforce those standards and avoid creating workloads that are not following the requirements. This is an important step to keep all new provisioned workloads secure by default, in other words: with the necessary level of hardening to comply with the standard that was selected.
Monitoring for compliance
While enforcing policies is important to ensure that the upper management’s decisions are translated into real actions towards optimizing the security state of your company, monitoring these policies for compliance is also indispensable.
Policies that were defined can be easily monitored using tools such as Microsoft Defender for Cloud, which not only monitor Windows VMs and computers, but also those operating with Linux software. The example shown in Figure 10.11 is for Windows machines:
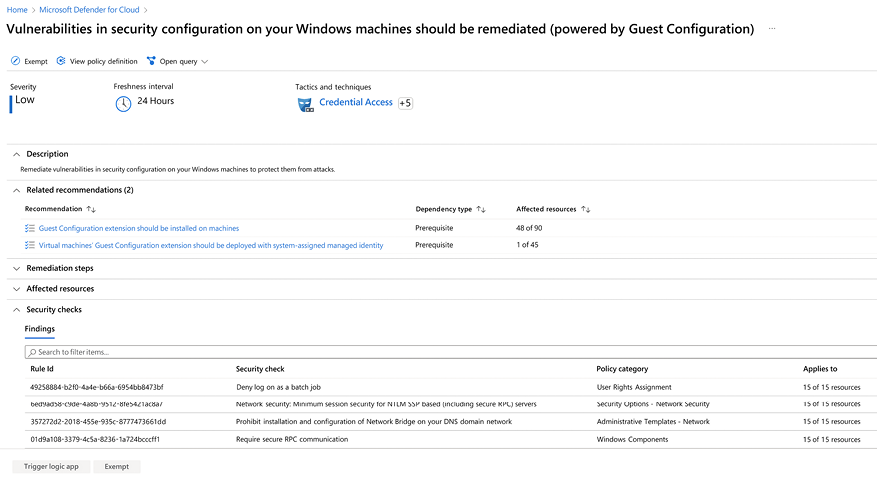
Figure 10.11: Monitoring security policies
This dashboard shows the security recommendation called Vulnerabilities in security configuration on your Windows machines should be remediated (powered by Guest Configuration). This recommendation looks across many security policies to identify if the machine is using the recommended configuration to mitigate a potential threat. For example, one rule that is part of this policy is the Minimum session security for NTLM SSP based (including secure RPC) servers.
When expanding this rule (by clicking in the Rule ID located in the bottom of the page – see Figure 10.11 as an example), you will have another page that shows more details, as shown in Figure 10.12:
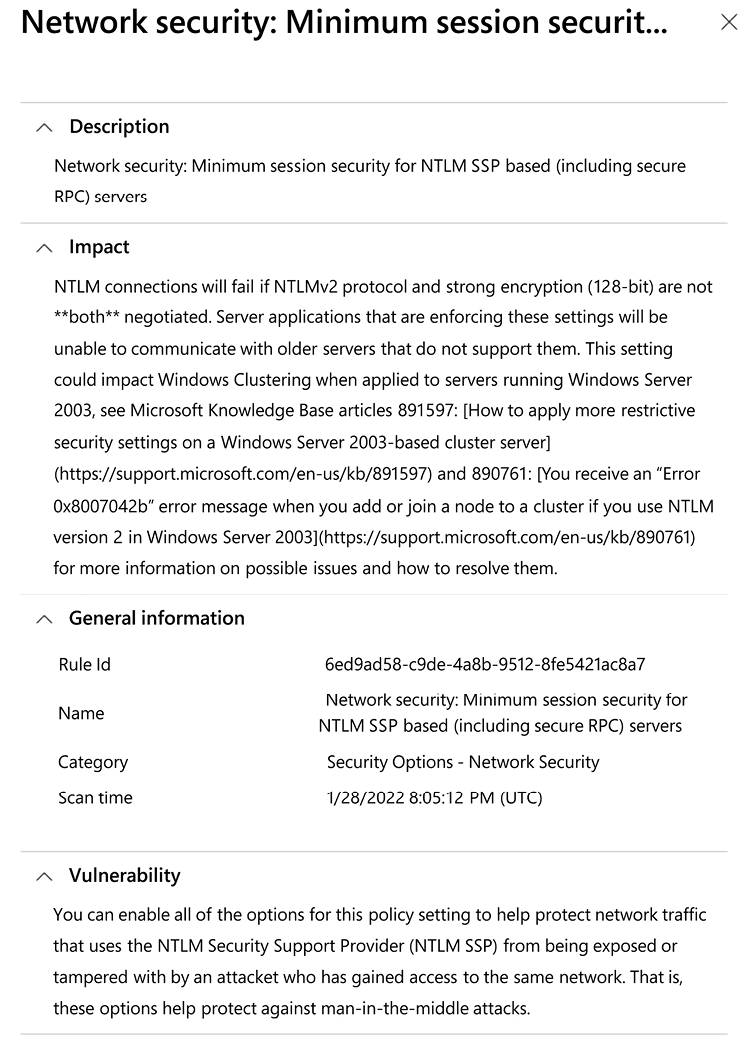
Figure 10.12: Network policy rule
It is important to emphasize that Microsoft Defender for Cloud will not deploy the configuration for you. This is a monitoring tool, not a deployment tool, which means that you need to get the suggested countermeasure and deploy it using other methods, such as GPO or Azure Policy with in-guest configuration.
Automations
When monitoring for compliance you also need to take in considerations automating certain tasks to facilitate the response and remediation. You may want to open a ticket on your ITSM tool to bring visibility about resources that failed to comply with a specific standard. In Microsoft Defender for Cloud you have a feature called Workflow Automation (see Figure 10.13) that can trigger the execution of an Azure Logic App, which is another built-in Azure service that enables you to programmatically perform a series of actions based on certain input.
Figure 10.13: Workflow automation
Automating certain enforcement tasks this way will not only save your IT department a lot of time, but will also ensure that basic cybersecurity policies are enforced across the board.
Continuously driving security posture enhancement via security policy
In the agile world that we live in, having policy enforcement is important, but you must be continuously vigilant to understand the changes that are happening in the environment, and many changes will happen, mainly when you are managing a hybrid environment where you have resources on-premises and also in the cloud. In order for you to have the right level of visibility of new resources that are added to your infrastructure, you need a Cloud Security Posture Management (CSPM) platform, which we briefly mentioned in Chapter 1, Security Posture.
Having a CSPM platform in place will help you to discover the addition of new workloads and understand the security state of those workloads. Some CSPM tools are able to scan to identify new resources and enumerate the security best practices that these resources are missing. Using Azure Security Center as an example of a CSPM platform, you also have a capability that can be used as your security Key Performance Indicator (KPI), which is called Secure Score.
Microsoft Defender for Cloud will calculate the total score based on the assumption that all security recommendations will be acted upon, in other words, the total number you can get assuming everything is in a secure state (green state) is a 100% Secure Score. The current number is a reflection of the number of resources that are in a secure state, and how it can be improved towards the green state. Below you have an example of a Secure Score:

Figure 10.14: Example of a Secure Score
To drive the Secure Score up, you need to start addressing the security recommendations. In Microsoft Defender for Cloud, under the Secure score recommendations page, you can see that the recommendations are organized by security controls, and within each control you have the set of recommendations that you need to put in place, as shown in Figure 10.15:
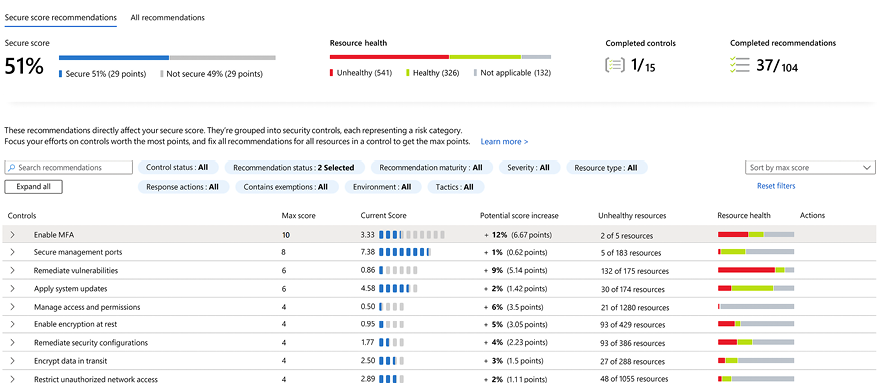
Figure 10.15: Security recommendations for different workloads
Notice that each security control has a Max score, which gives you an idea of how much you will gain once you act upon all recommendations within the security control. The Current Score column reflects your current state in your journey to earn all points in that security control.
You also have the Potential score increase column, which represents the percentage that your score will increase by once you remediate the entire security control.
To continuously drive security posture enhancement, you need to measure your progress over time, and Secure Score can be used for that as shown in the diagram below:
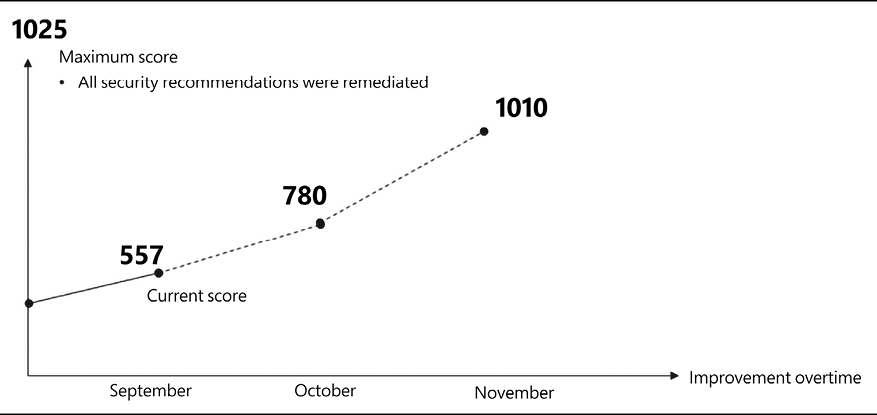
Figure 10.16: Tracking Secure Score over time
This diagram shows the Secure Score improvement over time, where improvement basically means that you have a stronger security posture, and you have fewer security recommendations to remediate. One tool available in the Microsoft Defender for Cloud dashboard that can also help you with that is the Secure Score Over Time workbook, as shown in Figure 10.17:
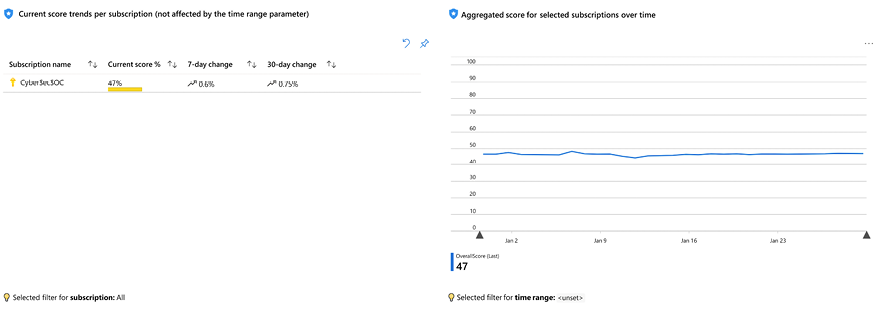
Figure 10.17: Secure Score Over Time workbook
Besides being able to track your improvement over time, this workbook can also be utilized to track potential decreases in the Secure Score and find out what caused that decrease.
Summary
In this chapter, you learned about the importance of having a security policy and driving this policy through a security program. You understood the importance of having a clear and well-established set of social media guidelines that give the employee an accurate view of the company’s view regarding public posts, and the consequences of violating these guidelines.
Part of the security program includes security awareness training, which educates the end user on security-related topics. This is a critical step to take, since the end user is always the weakest link in the security chain.
Later in this chapter, you learned how companies should enforce security policies using different sets of tools. Part of this policy enforcement includes application whitelisting and hardening systems. Lastly, you learned the importance of monitoring these policies for compliance, and learned how Microsoft Defender for Cloud can help monitor those items.
In the next chapter, we will continue talking about defense strategies, and this time you will learn more about network segmentation and how to use this technique to enhance your protection.
References
- Security and Privacy Controls for Federal Information Systems and Organizations: http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-53r4.pdf
- NIST 800-53 Written Information Security Program (WISP) security policy example: http://examples.complianceforge.com/example-nist-800-53-written-information-security-program-it-security-policyexample.pdf
- Internet Security Threat Report Volume 22: https://www.symantec.com/content/dam/symantec/docs/reports/istr-22-2017-en.pdf
- Uncovering a persistent diet spam operation on Twitter: http://www.symantec.com/content/en/us/enterprise/media/security_response/whitepapers/uncovering-a-persistent-diet-spam-operation-ontwitter.pdf
- Social Media Security: https://blogs.technet.microsoft.com/yuridiogenes/2016/07/08/social-media-security/
- Florida professor fi red for suggesting Texas deserved Harvey after voting for Trump: http://www.independent.co.uk/news/world/americas/us-politics/florida-professor-fired-trump-harvey-comments-texas-deserved-hurricane-storm-a7919286.html
- Microsoft Security Compliance Manager: https://www.microsoft.com/enus/download/details.aspx?id=53353
- Red Hat Enterprise Linux 6 Security Guide: https://access.redhat.com/documentation/en-US/Red_Hat_Enterprise_Linux/6/pdf/Security_Guide/Red_Hat_Enterprise_Linux-6-Security_Guide-en-US.pdf
- AppLocker - Another Layer in the Defense in Depth Against Malware: https://blogs.technet.microsoft.com/askpfeplat/2016/06/27/applocker-another-layer-in-the-defense-in-depth-against-malware/
- Enhanced Mitigation Experience Toolkit (EMET) 5.5: https://www.microsoft.com/en-us/download/details.aspx?id=50766
- Social Media Security: https://blogs.technet.microsoft.com/yuridiogenes/2016/07/08/social-media-security/
- Twitter deletes over 10,000 accounts that sought to discourage U.S. voting: https://www.reuters.com/article/us-usa-election-twitter-exclusive/exclusive-twitter-deletes-over-10000-accounts-that-sought-to-discourage-u-s-voting-idUSKCN1N72FA
- Symantec Internet Security Threat Reports Volume 24 – Feb 2019: https://www.symantec.com/content/dam/symantec/docs/reports/istr-24-2019-en.pdf
Join our community on Discord
Join our community’s Discord space for discussions with the author and other readers:

