4
Understanding the Cybersecurity Kill Chain
In the last chapter, you learned about the incident response process and how it fits into the overall enhancement of a company’s security posture. Now it is time to start thinking like an attacker and understand the rationale, the motivation, and the steps of performing an attack. We call this the Cybersecurity Kill Chain, which is something that we briefly covered in Chapter 1, Secure Posture. Today, the most advanced cyber-attacks are reported to involve intrusions inside a target’s network that last a long time before doing damage or being discovered. This reveals a unique characteristic of today’s attackers: they have an astounding ability to remain undetected until the time is right. This means that they operate on well-structured and scheduled plans. There have been studies carried out on the precision of their attacks, which have revealed that most cyber attackers use a series of similar phases to pull off successful attacks.
To enhance your security posture, you need to ensure that all phases of the Cyber Kill Chain are covered from a protection and detection perspective. But the only way to do that is to ensure that you understand how each phase works, the mindset of an attacker, and the tolls that are taken during each phase.
In this chapter, we’re going to cover the following topics:
- Understanding the Cyber Kill Chain
- Security controls used to stop the Cyber Kill Chain
- Threat life cycle management
- How the Kill Chain has evolved
- Concerns about the Cyber Kill Chain
- Tools used during different phases of the Cyber Kill Chain
- Comodo AEP via Dragon Platform
Let’s start by looking at what the Cyber Kill Chain actually is in a little more detail.
Understanding the Cyber Kill Chain
The Cyber Kill Chain is attributed to Lockheed Martin, who derived it from a military model used to effectively neutralize targets by anticipating their attacks, engaging them strategically, and stopping them. Despite how fancy it sounds, in reality the Cyber Kill Chain is just a step-by-step description of how hackers attack. The model describes the steps of adversaries from the beginning phases of attack until a system is exploited, these steps include:
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command and Control (C2)
- Actions on Objectives
Organizations use this model to better understand threat actors so they can track and prevent cyber intrusions at their different stages. This has been done with varying degrees of success against ransomware, hacking attempts, and APTs (advanced persistent threats). As a defense strategist your goal will be to understand the attacker’s actions, and of course the intelligence. If you look at the kill chain from the attacker’s perspective, then you need to succeed in all steps to complete the attack successfully.
The sections that follow will discuss each of the steps in the Cyber Kill Chain: Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command and Control, Actions on Objectives, and (an optional eighth step) Obfuscation. Some of these steps are more complex than others, so we will also detail various subphases within some of these main steps.
Reconnaissance
This is the first step of the kill chain, where hackers gather as much information as they can about a target, to identify any weak points that may be vulnerable to attack. The main focus areas of reconnaissance are:
- Network information: Details about the type of network, security weaknesses, domain name, and shared files (among others)
- Host information: Details about the devices connected to a network including their IP addresses, MAC addresses, operating system, open ports, and running services (among others)
- Security infrastructure: Details about the security policies, security mechanisms employed, and weaknesses in the security tools and policies (among others)
- User information: Private information about a user, their family, pets, social media accounts, hangout spots, and hobbies (among others)
There are three subphases that a threat actor will go through during reconnaissance: footprinting, enumeration, and scanning.
Footprinting
Footprinting is a critical step in the reconnaissance stage of the kill chain. Maximum possible time is spent at this stage of reconnaissance. This stage entails the collection of data about the target system, which can then be used to hack the target system. Some examples of information that is gathered at this point include:
- asmiServer configurations
- IP addresses
- VPN
- Network maps
- URLs
The threat actor will utilize various tools and techniques to achieve footprinting.
Enumeration
Enumeration is used to extract details such as client names, machine names, network assets, and different administrations used within the target systems. The data that is collected at this point is essential as it enables the hacker to identify and then distinguish between the various weaknesses in the assets of an organization. It also helps to identify information such as the kind of security that the organization employs to protect its informational assets. At this point, the focus is on points where the organization employs frail security practices that can later be exploited.
Scanning
This is the most popular methodology that is used by attackers (and ethical hackers replicating the kill chain) at the reconnaissance stage. This methodology is used to identify services within the target system that can be exploited or misused. The scanning process helps reveal details such as all the machines connected to a network, all open ports, and any other informational assets connected to a network.
Other important details that are revealed using scanning include:
- Services that are executed by the system
- The clients that own various administrations within the system
- Whether the system holds any incognito logins
- Validation requirements for the organization
Scanning can be done using various techniques, but there are three main types of scanning:
- Port scanning: This kind of scanning helps to reveal information about the system such as live ports, open ports, live frameworks, and the different administrations that are used in the system.
- Network scanning: This kind of scanning aims at revealing details about the network in use by the system. The information gathered at this point includes network switches, routers, the network topology, and network firewalls in use (if a firewall is used at all). The accessed data can then be used to draw an organizational graph.
- Vulnerability scanning: This type of scanning helps ethical hackers or attackers to determine the target system’s shortcomings, which they can then use to exploit the system. This kind of scanning is normally done using automated software.
When footprinting, enumeration, and scanning have been conducted, a threat actor is ready to move on from reconnaissance to the next stage in the kill chain.
Weaponization
After an attacker has conducted reconnaissance and found their target’s weaknesses, they will have a much better sense of which weapon will work best on their particular target. Weaponization is the phase where tools are built or used to attack their victims, for example, creating an infected file to send to the victim.
Depending on the target and the attacker’s intent, the weapon a threat actor chooses can differ greatly. Weaponization can include anything from writing malware that focuses strictly on a specific zero-day exploit to exploiting multiple vulnerabilities within an organization.
Delivery
As it sounds, delivery is just delivering the weapon to the victim. To be able to gain access to the victim’s systems the attackers usually inject “malware” into their content to gain access and then the malicious content will be “delivered” to the victim in different ways such as phishing, compromising the systems, or even using insiders.
Exploitation
This is the stage where the cyber-attack is initiated by the malware that was created in the weaponization phase. The malware will be activated on the victim’s system to exploit the target’s vulnerability/vulnerabilities.
This is the phase where the main attack starts. Once an attack has reached this phase, it is considered successful. The attacker normally has unobstructed freedom to move around a victim’s network and access all its systems and sensitive data. The attacker will start extracting sensitive data from an organization. This could include trade secrets, usernames, passwords, personally identifiable data, top-secret documents, and other types of data.
Additionally, many corporations nowadays keep sensitive access credentials in shared files. This is intended to help staff members to easily gain access to shared accounts such as call center records. However, once an attacker has breached a network, they can navigate to shared files and find out whether the employees have shared any sensitive files.
Threat actors will also often conduct privilege escalation during exploitation in order to further the impact of this phase.
Privilege escalation
During their initial breach, hackers will only get direct access to computers or systems with the admin privileges assigned to their target. Therefore, they will often use various privilege escalation techniques to gain admin rights and extract even more data from the same organization. Therefore, in the exploitation phase, hackers may attempt privilege escalation.
Privilege escalation can be done in two ways, vertical and horizontal:

Figure 4.1: Vertical and horizontal privilege escalation
The differences between the two are outlined in the following table:
|
Vertical privilege escalation |
Horizontal privilege escalation |
|
The attacker moves from one account to another that has a higher level of authority. |
Attacker uses the same account, but elevates its privileges. |
|
Tools are used to escalate privileges. |
The original target’s user account is used to escalate privileges. |
Table 4.1: A comparison of vertical and horizontal privilege escalation
Both forms of privilege escalation are conducted to give the attacker access to admin-level functionalities or sensitive data in a system.
Vertical privilege escalation
Vertical privilege escalation is where an attack that starts from a point of lower privilege, then escalates privileges until it reaches the level of the privileged user or process it targets. It is a complex procedure since the user has to perform some kernel-level operations to elevate their access rights.
Once the operations are done, the attacker is left with access rights and privileges that allow them to run any unauthorized code. The rights acquired using this method are those of a super user that has higher rights than an administrator.
Due to these privileges, an attacker can perform various harmful actions that not even an administrator can stop.
Horizontal privilege escalation
Horizontal privilege escalation, on the other hand, is simpler since it allows a user to use the same privileges gained from the initial access.
A good example is where an attacker has been able to steal the login credentials of an administrator of a network. The administrator account already has high privileges that the attacker assumes immediately after accessing it.
Horizontal privilege escalation also occurs when an attacker is able to access protected resources using a normal user account. A good example is where a normal user is erroneously able to access the account of another user. This is normally done through session and cookie theft, cross-site scripting, guessing weak passwords, and logging keystrokes.
At the end of this phase, the attacker normally has well-established remote access entry points into a target system. The attacker might also have access to the accounts of several users. The attacker also knows how to avoid detection from security tools that the target might have.
Examples of attacks that used exploitation
There have been some ugly incidents faced by big companies whose data has been stolen. In 2015, a hacker group breached and stole 9.7 GB of data from a site called Ashley Madison, which offered spouse-cheating services. The hackers told Avid Life Media, the company that owned the website, to take it down or they would release some user data. The mother company threw out the claims, but the hackers soon dumped the data on the dark web. The data included real names, addresses, phone numbers, email addresses, and login credentials of millions of users. The hackers encouraged the people affected by the leak to sue the company and claim damages.
There is an ongoing trend of hackers specifically targeting data stored in systems. Once they breach any corporate network, they move laterally to the data storage locations. They then exfiltrate this data to other storage locations from where they can read, modify, or sell it. In April 2018, SunTrust Banks was breached and the attackers managed to steal data belonging to 1.5 million people. Another attack happened on Facebook’s platform in October of the same year and attackers were able to steal data belonging to 50 million accounts.
In the first half of 2021 more than 98.2 million individuals were impacted by the 10 biggest data breaches, where 3 of the 10 largest breaches occurred at technology companies.
In 2016, Yahoo came out and said that data belonging to over a billion user accounts had been stolen by hackers back in 2013. The company said that this was a separate incident from the one where user data of half a million accounts had been stolen by hackers in 2014. Yahoo said that in the 2013 incident, hackers were able to exfiltrate names, email addresses, dates of birth, and security questions and answers, as well as hashed passwords.
The hackers allegedly used forged cookies that allowed them to gain access to the company’s systems without a password. In 2016, LinkedIn was hacked and the user data of over 160 million accounts was stolen.
The hackers soon put the data on sale for any interested buyers. The data was said to contain the email addresses and encrypted passwords of the accounts. These three incidents show how serious an attack becomes after the attacker is able to get to this stage. The victim organizations’ reputations suffer, and they have to pay huge sums of money as fines for not securing user data.
Attackers at times do more than just exfiltration of the data. They could erase or modify the files stored in the compromised computers, systems, and servers. In March 2017, hackers demanded ransom from Apple and threatened to wipe the data belonging to 300 million iPhones on iCloud accounts. Although this was soon rubbished as a scam, such an action is within the realm of possibility. In this case, a big company such as Apple was put in the spotlight when hackers tried to extort money from it. It is possible that another company would have hurriedly paid the hackers in order to prevent the data of its users from being wiped out.
An example of an attack that utilized vertical privilege escalation, in particular, can be found in the WannaCry attack that happened in May 2017. WannaCry, a ransomware, caused devastation by encrypting computers in over 150 countries and demanding a ransom of $300 to decrypt that would double after the second week. The interesting thing about it is that it was using a vulnerability called EternalBlue, allegedly stolen from the NSA. EternalBlue allowed the malware to escalate its privileges and run any arbitrary code on Windows computers.
All of these incidents that were faced by Apple, Ashley Madison, LinkedIn, and Yahoo show the significance of this stage. Hackers that manage to reach this stage are virtually in control. The victim might still not be in the know that data has already been stolen. The hackers may decide to remain silent for a while.
Installation
During installation, attackers roam freely within a network, copying all data that they think is valuable while ensuring they remain undetected. There is an option to end the attack in the previous stage when data has already been stolen and can either be publicized or sold. However, highly motivated attackers that want to completely finish off a target choose to continue with the attack. Attackers install a backdoor, which gives them access to the victim’s computers and systems whenever they want.
The main aim of entering this stage is to buy time to perform another, and even more harmful, attack than exploitation. The attacker is motivated to move past data and software and attack the hardware of an organization. The victim’s security tools are, at this point, ineffective at either detecting or stopping the attack from proceeding. The attacker normally has multiple access points to the victims, such that even if one access point is closed, their access is not compromised.
Command and Control
This phase builds on the backdoor established in the installation phase. In the Command and Control stage, the attacker uses their backdoor into the system to manipulate their target remotely. The threat actor waits until the victim is away from their computer and performs actions that will aid them in their assault.
Actions on Objectives
Actions on Objectives is the most feared stage of any cyber-attack. It is where the attacker does damage exceeding the data and software. An attacker might disable or alter the functioning of the victim’s hardware permanently. The attacker focuses on destroying hardware controlled by the compromised systems and computing devices.
A good example of an attack that got to this phase is the Stuxnet attack on Iran’s nuclear station. It was the first recorded digital weapon to be used to wreak havoc on physical resources. Just like any other attack, Stuxnet followed the previously explained phases and had been residing in the facility’s network for a year. Initially, Stuxnet was used to manipulate valves in the nuclear facility, causing the pressure to build up and damage a few devices in the plant. The malware was then modified to attack a larger target, the centrifuges. This was achieved in three stages.
The malware was transmitted to the target computers through USB thumb drives, since they were not connected to the internet. Once it infected one of the target computers, the malware replicated itself and spread to the other computers. The malware proceeded to the next stage where it infected some software by Siemens called Step7 that was used to control the programming of logic controllers. Once this software was compromised, the malware finally gained access to the program logic controllers. This allowed the attackers to directly operate various machinery in the nuclear plant. The attackers caused the fast-spinning centrifuges to spin out of control and tear apart on their own.
The Stuxnet malware shows the heights that this phase can reach. The Iranian nuclear facility stood no chance of protecting itself as the attackers had already gained access, escalated their privileges, and stayed out of sight of security tools. The plant operators said that they were receiving many identical errors on the computers, but all virus scans showed that they had not been infected. It is clear that the attackers did a few test runs of the worm within the compromised facility with the valves. They found out that it was effective, and decided to scale up to attack the centrifuges and crash Iran’s nuclear weaponry prospects.
Essentially, this stage is where the hacker does actual harm to a compromised system. Actions on Objectives includes all activities aimed at compromising the confidentiality, integrity, and availability of networks, systems, and data. For example, one kind of attack that may be conducted during the Actions on Objectives stage is data exfiltration.
Data exfiltration
Data exfiltration occurs when a threat actor steals an organization’s data. This can happen in any of the following ways:
- Outbound email – one of the convenient methods that hackers use for exfiltration where they just send it over the internet via email. They could quickly log into throw-away email accounts on the victim’s machine and send the data to another throw-away account.
- Downloading – when the victim’s computer is connected remotely to the hacker’s computer, they can download the data directly to their local devices.
- External drives – when hackers have physical access to the compromised system, they can exfiltrate data directly to their external drives.
- Cloud exfiltration – data from the cloud can be exfiltrated via downloads if a hacker gains access to a user’s or organization’s cloud storage space. On the other hand, cloud storage spaces can also be used for exfiltration purposes. Some organizations have strict network rules such that hackers cannot send data to their email addresses. However, most organizations do not block access to cloud storage spaces. Hackers can use them to upload data and later download it to their local devices.
- Malware – this is where a hacker infects a victim’s computer with malware specifically designed to send data from a victim’s computer. This data could include keystroke logs, passwords stored in browsers, and browser history.
Attackers normally steal huge chunks of data during exfiltration. This data can either be sold off to willing buyers or leaked to the public.
Obfuscation
This is the last stage of the attack, which some attackers may choose to ignore. The main aim here is for the attackers to cover their tracks for various reasons. If the attackers do not want to be known, they use various techniques to confuse, deter, or divert the forensic investigation process that follows a cyber-attack. Some attackers may, however, opt to leave their trails unmasked if they operated anonymously or want to boast of their exploits.
Obfuscation is done in a number of ways. One of the ways that attackers prevent their adversaries from catching up with them is by obfuscating their origins; another is by hiding their trails after the fact. Some common techniques used by threat actors in this stage are:
- Encryption – to lock all evidence related to cyber intrusions, hackers may choose to encrypt all the systems they accessed. This effectively renders any evidence, such as metadata, unreadable to forensic investigators. In addition to this, it becomes significantly harder for the victim to recognize the malicious actions that hackers performed after compromising a system.
- Steganography – in some incidents, the hackers are insider threats in the victim organizations. When sending sensitive data outside a network, they may opt to use steganography to remain undetected when exfiltrating data. This is where secret information is concealed in non-secret data such as images. Images can be freely sent into and outside organizations since they appear inconsequential.
Therefore, a hacker can send lots of sensitive information through steganography without raising any alarms or being caught.
- Modifying logs – attackers can opt to erase their presence in a system by modifying system access logs to show that there were no suspicious access events captured.
- Tunneling – this is where hackers create a secure tunnel through which they send data from the victim’s network to another location. Tunneling ensures that all data is encrypted from end to end and cannot be read in transit. Therefore, the data will pass through security tools such as firewalls unless the organization has set up monitoring for encrypted connections.
- Onion routing – hackers can secretly exfiltrate data or communicate with each other through onion routing. Onion routing involves multiple layers of encryption and data is bounced from one node to another till it gets to the destination. It is hard for investigators to follow data trails through such connections as they would need to break through each layer of encryption.
- Wiping drives – the last method of obfuscation is by destroying the evidence. Hackers could wipe the hard drive of a system they have breached to make it impossible for the victims to recognize the malicious activities performed by the hackers. Clean wipes are not done by simply deleting data. Since hard drive contents can be recovered, hackers will overwrite the data several times and wipe the disk clean. This will make it hard for the contents of the drive to be recovered.
As you can see, there are many different methods hackers can use to cover their tracks.
Examples of attacks that used Obfuscation
There are many examples of real-world attacks that used a variety of obfuscation techniques. For example, at times, hackers attack outdated servers in small businesses and then laterally move to attack other servers or targets. Therefore, the origins of the attacks will be tracked down to the servers of an innocent small business that does not regularly perform updates. This type of obfuscation was recently witnessed in a university where the IoT lights were hacked into and used to attack the university’s servers. When forensic analysts came to investigate the DDoS attack on the servers, they were surprised to see that it originated from the university’s 5,000 IoT lights.
Another origin obfuscation technique is the use of public school servers. Hackers have repeatedly used this technique where they hack into vulnerable web applications of public schools and move laterally into the schools’ networks, installing backdoors such as rootkit viruses on the servers. These servers are then used to launch attacks on bigger targets since forensic investigations will identify the public schools as the origin.
Lastly, social clubs are also used to mask the origins of attacks by hackers. Social clubs offer their members free Wi-Fi, but it is not always highly protected. This provides hackers with an ideal ground for infecting devices that they can later use to execute attacks without the knowledge of the owners.
Another obfuscation technique that hackers commonly use is the stripping out of metadata. Metadata can be used by law enforcement agencies to catch up with perpetrators of some crimes.
In 2012, a hacker by the name of Ochoa was charged with hacking the FBI database and releasing the private details of police officers.
Ochoa, who used the name “wormer” in his hacks, was caught after he forgot to strip metadata from a picture that he placed on the FBI site after hacking it. The metadata showed the FBI the exact location of the place where the photo was taken and this led to his arrest. Hackers have learned from this incident that it is irresponsible to leave any metadata in their hacking activities as it could be their downfall, just as it was for Ochoa.
It is also common for hackers to cover their tracks using dynamic code obfuscation. This involves the generation of different malicious code to attack targets, but prevents detection from signature-based antivirus and firewall programs through metamorphism.
The pieces of code can be generated using randomizing functions or by changing some function parameters. Therefore, hackers make it significantly harder for any signature-based security tool to protect systems against their malicious codes. This also makes it difficult for forensic investigators to identify the attacker as most of the hacking is seemingly done by random code.
At times, hackers will use dynamic code generators to add meaningless code to their original code. This makes a hack appear very sophisticated to investigators, and it slows down their progress in analyzing the malicious code. A few lines of code could be made to be thousands or millions of meaningless lines. This might discourage forensic investigators from analyzing code deeper to identify some unique elements or hunt for any leads toward the original coder.
Now that we’ve examined the Cyber Kill Chain and its phases, the question remains: how can organizations use their knowledge of the kill chain to improve their security posture? Understanding how threat actors plan attacks is a critical step, but we still need to explore how organizations can use this information to plan effective defenses.
Security controls used to stop the Cyber Kill Chain
There are several methods that an organization can use to stop the different stages of the cyber kill chain. It can do this by implementing various security controls. Some of the effective security controls that have been identified include:
- Detect: In this security control, an organization will determine all attempts by attackers to gain access to the system. This includes attempted scans of the system by outsiders to determine a system’s potential vulnerabilities.
- Deny: Thwarting attacks while they are in progress. The security team should move swiftly to stop any attacks when they get information regarding any possible attack.
- Disrupt: This includes efforts by the security team to intercept any communication between the attackers and the system and interrupt this communication. Communication may be feedback on queries done by attackers on the system to determine various elements of the system before they can carry out their attacks.
- Degrade: This includes developing and implementing various measures that are meant to reduce the potency of attacks to limit the damage of these attacks.
- Deceive: This includes implementing various measures that will deliberately mislead attackers by providing them with false information about the assets in the organization.
In each of the cyber kill chain stages, security tools can be used to apply these aforementioned security controls. This is shown below:
- Reconnaissance stage: Detection is done via web analytics, network intrusion detection systems, and threat intelligence. Denying is done via firewall access control lists and the implementation of information-sharing policies.
- Weaponization stage: Detection is made possible through the use of threat intelligence and network intrusion detection systems. Denying is done by using network intrusion prevention systems.
- Delivery stage: At the delivery stage, detection is done using endpoint malware protection; denying is done using proxy filters and host-based intrusion prevention; disruption is done with an inline antivirus; degrading is done by queuing; containing is done by app-aware firewalls and inter-zone network intrusion detection systems.
- The exploitation stage: Detection is done by endpoint malware protection; denying is done by patch management; disruption is possible by data execution prevention; containing is done by trust zones and inter-zone network intrusion detection systems.
- The installation stage: Detection is done by the use of security information and event management systems; denying is done by the use of strong passwords and privilege separation; disruption is done by router access control lists; containing is done by trust zones and inter-zone network intrusion detection systems.
- The command and control stage: Detection is done using host-based intrusion detection systems; denying is done by use of firewall access control lists and network segmentation; disrupting is done by host-based intrusion prevention systems; degrading is done by a tarpit; deceiving is done by a Domain Name System redirect; containing is done by Domain Name System sinkholes.
- The actions on objectives stage: Detection is possible via the use of endpoint malware protection and Security Information and Event Management (SIEM); denying is done by data-at-rest encryption and through egress filtering; disrupting is done by endpoint malware protection and the use of a data loss prevention system; degrading is done through quality of service; deceiving is achieved by the use of a honeypot; containing is made possible by using incident response programs and firewall access control lists.
In addition to these security controls, organizations may also use other methods for thwarting attackers using the kill chain, such as UEBA and security awareness training for staff.
Use of UEBA
UEBA is an acronym for User and Entity Behavior Analytics. This methodology is critical and effective in the fight against APTs. The cyber kill chain is mainly focused on APT attacks since they are the most destructive attacks an attacker can carry out on your organization. APT attacks are advanced forms of attacks that may take years of planning. In many cases, the attackers want to get into the system, camouflage themselves in the system, and spend long periods within the system to enable them to carry out their attacks. With the modern advanced and automated tools in use, camouflaging within the system has become more difficult, hence requiring APT attackers to be more creative to achieve their plans.
UEBA are security tools that make use of analytics technology including the use of machine learning to identify abnormal and risky behavior among users of a particular system. UEBA achieves this by learning the normal behavior of users of the system and creating a profile that it considers normal. Based on the normal user behavior, the security solution can then identify any risky behavior when a user appears to deviate from normal behavior. Any deviations or risky behavior can alert the security team and subsequent investigations are done to determine the reasons for the deviations in behavior. UEBA is an extremely effective technique for fighting APTs because of the inability of attackers to mimic normal user behavior. It proves even more effective when the machine learning model that trains the analytics tool has a huge database to learn from. As the UEBA tool gets more data, it becomes more effective and it becomes easier for the tool to identify any anomalies in the system, hence increasing security against advanced persistent attacks.
Figure 4.2: Areas that UEBA can help with
This image highlights various areas that UEBA can help with, in particular.
Security awareness
Security awareness among ordinary staff plays a critical role in many organizations. However, many organizations do not seem to understand the actual potential of having the staff members at their disposal being included in the cybersecurity strategies to help safeguard their organizations from potential attackers.
The potential of using ordinary employees in an organization as vital elements of cybersecurity strategies is exemplified by the many reported cases of ordinary employees thwarting cyber-attacks. Many ordinary employees have identified anomalies in the systems and reported these anomalies, leading to the security teams in various organizations being alerted of actual attacks in progress. This shows that ordinary staff in an organization, who may have little to do with the information technology department, can play a crucial role in helping to safeguard an organization from attacks. The solution to this is security awareness. Increasing awareness among these employees will immensely benefit an organization. Some of the benefits that can accrue from increasing security awareness of ordinary staff include:
- Identifying attacks in progress and alerting the security teams of any anomalies in the system: In many cases, an organization will install automated tools that are designed to identify any suspicious activities within the systems and alert the security team of potential attacks. However, if an attacker gets to learn about the systems and the kind of transactions done within the system, they are likely to get into the system and try to replicate these kinds of transactions. If these attacks are done during production time, the system may not be able to identify and differentiate between the actual transactions and suspicious ones. In this case, the ordinary staff may be able to identify any anomalies in the system while working. For instance, if employees notice unnecessary delays in the system, they can inform the security team of them for an investigation to determine the cause of the delays.
- Human users are one of the biggest flaws and potential vulnerabilities in any system. Even for systems that are deemed impenetrable, the human factor in the form of human users will always present the system with weaknesses that can be exploited. For instance, a user who is authorized to access a system can be used to gain access to the system. In such a case, the impenetrable system can do little about such a situation. Also, users can be deceived into revealing passwords or information about the system that attackers cannot gain from hacking the system. They can also be coerced into revealing information or passwords that hackers can use to gain access into the system. Therefore, it is in the best interests of an organization to increase the security awareness of the users to enable them to play a critical role in enhancing the security posture of an organization.
- Some of the cybersecurity strategies include the development of policies and the implementation of these policies. Examples of a policy may be rules on the handling of personal client data by staff members to ensure the integrity and privacy of the data in question. Staff members are responsible for handling client data. Without the required security awareness, employees can put the data at risk of access from attackers. It is critical, therefore, to ensure that ordinary employees are equipped with knowledge that will enable them to improve the security of the data they handle and the informational assets they manage while at work.
- Focusing only on the technological aspects of cybersecurity strategies is not enough. The human element is just as crucial to cybersecurity strategies as technology is. Targeted and personalized attacks have been identified as the main methods that attackers are using to infiltrate systems. Therefore, when attackers target employees of an organization and find a group of workers that are not technologically savvy but have access to the organization’s systems, then the ease of gaining access to the system is increased.
Organizations need to ensure that the efforts that are put into safeguarding an organization in this day and age include all elements of an organization inclusive of the users of the systems. Any element of the system that is ignored will work as a weakness in the security aspects of the organization. Attackers are always attempting to gain entry into the system and testing the company for any vulnerability in its systems. Any weakness is a potential exploit that attackers can potentially use. An effective system ensures that all potential vulnerabilities are identified and sealed before they can be exploited.
As you can see, the cyber kill chain can be incredibly useful for informing an organization’s cybersecurity practices. The tasks of detect, deny, disrupt, degrade, and deceive can be directed at different areas of the kill chain, depending on which stage of attack is being used against an organization. Additionally, UEBA can be used to disrupt the APTs that follow the kill chain, and increasing staff members’ security awareness around areas such as the cyber kill chain can lead to great results for the company’s security stance.
While all of these are useful techniques for thwarting attacks that use the kill chain, the aim of threat life cycle management, in particular, is to stop an attack in its earliest possible phases, which can be particularly useful for preventing the kill chain from progressing.
Threat life cycle management
An investment in threat life cycle management can enable an organization to stop attacks as early as possible in the cyber kill chain. It is a worthy investment for any company today since statistics show that the cyber breaches being witnessed are not slowing down. There was a 760% increase in cyber-attacks from 2014 to 2016. Cybercrimes are increasing because of three things. To begin with, there are more motivated threat actors. Cybercrime has become a low-risk, high-return business for some people. Despite the increase in the number of breaches, there has been a very low conviction rate, which shows that very few cybercriminals get caught.
At the same time, organizations are losing billions to these motivated attackers. Another reason for the increase in the number of breaches is the maturity of the cybercrime economy and supply chain. Cybercriminals are today able to access numerous exploits and malware that are for sale, provided that they can pay commensurate amounts of money. Cybercrime has become a business that has sufficient suppliers and willing buyers. The buyers have been multiplying since the advent of hacktivism and cyberterrorism. This is, therefore, leading to an unprecedented increase in the number of breaches.
Lastly, breaches are on the rise because of the expansion of attack surfaces by organizations. New technologies have been adopted, bringing new vulnerabilities and therefore widening the surface area that cybercriminals can attack.
The Internet of Things (IoT), one of the latest additions to organizational technologies, has already caused a number of companies to be hacked. The future is bleak if organizations do not take the required precautions to protect themselves.
The best investment that they can make now is in threat life cycle management to allow them to respond appropriately to attacks based on the phase that they are in. In 2015, an investigation report by Verizon claimed that, out of all attacks, 84% left evidence in the log data.
This means that with the appropriate tools and mindset, these attacks could have been mitigated early enough to prevent any damage.
Now that we’ve seen why investing in threat life cycle management is worthwhile, let’s examine what threat life cycle management actually looks like. LogRhythm proposed six phases to their threat life cycle management framework, forensic data collection, discovery, qualification, investigation, neutralization, and recovery, which we will discuss in the following sections.
Forensic data collection
The first phase in the threat life cycle management framework is forensic data collection. Prior to the detection of a full-blown threat, some evidence is observable in the IT environment. Threats can come through any of the seven domains of IT. Therefore, the more of the IT infrastructure the organization can see, the more threats it can detect.
There are three applicable events at this phase. To start off, organizations should collect security event and alarm data. Today, organizations use countless security tools to help them nab attackers and prevent their attacks from being successful. Some of these tools only give warnings and, therefore, simply generate events and alarms. Some powerful tools may not sound alarms for small-level detections, but they will generate security events.
However, tens of thousands of events may be generated daily, thus confusing an organization about which ones to focus on. Another applicable event in this phase is the collection of log and machine data. This type of data can provide deeper visibility of what actually goes on in an organizational network on a per-user or per-application basis. The last applicable thing in this stage is the collection of forensic sensor data. Forensic sensors, such as network and endpoint forensic sensors, are even more in depth, and they come in handy when logs are not available.
Discovery
The next phase in threat life cycle management is the discovery phase. This comes after the organization has established visibility and thus can detect attacks early. This phase can be achieved in two ways.
The first of these is search analytics. This is where IT employees in the organization carry out software-aided analytics. They are able to review reports and identify any known or reported exceptions from network and antivirus security tools. This process is labor-intensive and therefore should not be the sole analytics method that a whole organization should rely on.
The second way of achieving this phase is by using machine analytics. This is analytics that is purely done by machines/software. The software normally has machine learning capabilities and, therefore, artificial intelligence, enabling them to autonomously scan large amounts of data and give brief and simplified results to people to further analyze. Machine learning simplifies the threat discovery process since it is automated and continually learns new threats on its own.
Qualification
Next is the qualification phase, where the threats discovered in the previous phase are assessed to find out their potential impact, urgency of resolution, and how they can be mitigated. The phase is time-sensitive, as an identified attack may mature faster than expected.
To make matters worse, it is not simple, and consumes a lot of manual labor and time. In this phase, false positives are a big challenge, and they must be identified to prevent the organization from using resources against nonexistent threats. Inefficient qualification may lead to true positives being missed and false positives being included. Legitimate threats could, therefore, go unnoticed and unattended. As you can see, this is a sensitive phase in the threat management process.
Investigation
The next phase is the investigation phase where threats categorized as true positives are fully investigated to determine whether or not they have caused a security incident.
This phase requires continuous access to forensic data and intelligence about very many threats. It is mostly automated, and this simplifies the lookup process for a threat among millions of known threats. This phase also looks at any potential damage a threat might have done to the organization before it was identified by the security tools. Based on information gathered from this phase, the IT team of an organization can proceed accordingly against a threat.
Neutralization
Next comes the neutralization phase. Here, mitigations are applied to eliminate or reduce the impact of an identified threat to an organization. Organizations strive to get to this stage as quickly as possible since threats involving ransomware or privileged user accounts might do irreversible damage in a short period.
Therefore, every second counts when eliminating identified threats. This process is also automated to ensure a higher throughput of deleting threats and to also ease information sharing and collaboration between several departments in an organization.
Recovery
The last phase is recovery, which only comes after an organization is sure that its identified threats have been neutralized and that any risks that it faced are put under control. This phase aims to restore the organization to a position it enjoyed before being attacked by threats. Recovery is less time-critical, and it highly depends on the type of software or service being made available again. This process, however, requires care to be taken; changes that might have been made during an attack incident or during the response need to be backtracked. These two processes may cause undesired configurations or actions to have been taken to either compromise a system or prevent it from sustaining further damage. Systems must be brought back to the exact state that they were in before being attacked. There are automated recovery tools that can return systems automatically to a backed-up state. Due diligence must, however, be carried out to ensure that no backdoors are introduced or left behind.
As you can see, this framework gives organizations an effective plan to respond to APTs in their early stages, which allows the organization to stop a threat actor’s progression through the Cyber Kill Chain before they reach the most damaging phases.
Now that we have seen how organizations can utilize their understanding of the cyber kill chain to better their security, it is worth calling into question a few concerns about the kill chain model itself.
Concerns about the Cybersecurity Kill Chain
The kill chain has been in use since the year 2011. While it has obvious benefits, it has also presented numerous flaws that organizations need to be aware of. Some of the flaws that have been identified include:
- Perimeter security: Perimeter security involves using security solutions such as malware prevention and firewalls. While these two solutions have been known to be very effective in the past, recent times have seen organizations shift to cloud technologies where perimeter security and malware detection are largely handled by third-party companies while an organization focuses on service delivery or product improvement. This means that there is an increasing need for the kill chain to evolve to accommodate new challenges and to fit the new market needs where technologies such as IoT are increasingly playing integral roles in business operations.
- Attack vulnerabilities: The kill chain has also been criticized in terms of the number of attacks that can be stopped using this methodology. There is a limited range of attacks that can be stopped using the methodology. The best example of attacks that have been identified includes insider attacks. Insider attacks are among the most dangerous attacks an organization can face and will often have difficulty detecting. The original kill chain framework is also inconsequential when facing compromised credentials and attackers getting into the system without needing to use techniques such as brute force that will alert the security systems. While the framework is built to help secure organizations from sophisticated attacks such as advanced persistent attacks, less sophisticated attacks have been known to avoid detection. For instance, in 2017, the infamous Equifax breach went undetected for a long period and the kill chain was ineffective in that case.
As you can see, while the Cyber Kill Chain has numerous benefits, there are certain areas where it can fall short. Additionally, our understanding of the kill chain is not static and is constantly evolving to respond to changes in the cybersecurity landscape. While this helps to ensure the kill chain is responding to the current landscape, it can also make the model itself a bit less predictable.
How the Cyber Kill Chain has evolved
The cyber kill chain has evolved over time. The cyber kill chain model was first released in the year 2011. Since then, the kill chain model has evolved tremendously. The main reason for the big changes in the kill chain is the rapid evolution of the attackers and attack methodologies. Attackers are continually evolving their methods of attack. Since the kill chain is based on the methodologies used by attackers, it is also bound to evolve to accommodate the changes in the threat actors’ methods and abilities.
At its inception, the cyber kill chain was very predictable with the step-by-step stages clearly defined and the activities in each of the stages clearly outlined. However, in recent periods, the kill chain has become far less predictable owing largely to the unpredictability of attacks. Attackers, in their efforts to become harder to stop, have been known to combine some of the steps of the attack. This means that the kill chain can no longer afford to be fixed, but needs to be flexible as well. An additional result of this is that there are now multiple versions of the kill chain that have variations in how they define steps, so it is important to ensure that employees are referencing the same version of the model when planning a response.
The preference for use of the kill chain as a major security solution for cybersecurity has also presented organizations with newer security challenges as attackers are well aware of the steps the organizations will use to secure their systems. Attackers are now opting to either avoid some steps or combine steps to benefit them by helping them to avoid detection. All these changes in the attack systems have led to changes and evolution in the kill chain, making it far less predictable than it was during its inception in 2011.
As a result of this evolution and the concerns around the model at large, the kill chain should not be treated as a catch-all that can be applied to every attack but, rather, as a jumping-off point for improved understanding of an attacker’s methods and motivations.
Tools used during the Cyber Kill Chain
Now that we have examined the kill chain in depth and can understand a threat actor’s motivations at each stage, let’s examine some of the tools they may use during different phases of the kill chain. By taking the time to examine how these tools are used, we can gain a better understanding of the process threat actors go through when planning and staging an attack, and thus can better prepare ourselves for when they strike. In addition, these tools can be incredibly useful for Red Teams to utilize in mock attacks.
Metasploit
Metasploit is a legendary, Linux-based hacking framework that has been used countless times by hackers. This is because Metasploit is made up of numerous hacking tools and frameworks that have been made to effect different types of attacks on a target. So far, the framework has over 1,500 exploits that can be used against browsers, Android, Microsoft, Linux, and Solaris operating systems, and various other exploits applicable to any platform. Because of its vastness, Metasploit is a tool that can be used during all stages of the cyber kill chain.
The tool has received attention from cybersecurity professionals and is also used to teach ethical hacking. The framework provides its users with vital information about multiple vulnerabilities and exploitation techniques. As well as being used by cybercriminals, this framework is also commonly used for penetration testing to assure organizations that they are protected from penetration techniques that attackers commonly use.
Metasploit is run from a Linux terminal, which offers a command-line interface console from which exploits can be launched. The framework will tell the user the number of exploits and payloads that can be used. The user has to search for an exploit to use based on the target, or what is to be scanned on a target’s network. Normally, when one selects an exploit, they are given the payloads that can be used under that exploit.
The following figure shows a screenshot of the Metasploit interface. This screenshot shows the exploit being set to target the host on IP address 192.168.1.71:

Figure 4.3: Metasploit interface
This screenshot shows the compatible payloads that can be deployed on the target:

Figure 4.4: Compatible payloads in Metasploit
To download Metasploit and gather more information, visit https://www.metasploit.com/.
Twint
A common trend with cyber-attacks is that hackers are increasingly focusing on phishing attacks that use social engineering. Therefore, it is common to find that some reconnaissance targets are the online profiles of key personnel working at organizations of interest to hackers. Targeted information is gathered about these individuals during the reconnaissance stage of the kill chain, and one of the best ways to mine this information is through Twitter. Twint is meant to make this task simpler by allowing one to scrape tweets made by a certain person, containing a certain phrase, from verified profiles, containing email addresses, and within a certain geographic location, among other things.
Twint is effective when one is gathering information to be used for a social engineering attack among other types of phishing attacks. It is open source and runs on Linux platforms only.
Figure 4.5: Twint dashboard
You can download Twint from GitHub: https://github.com/twintproject/twint.
Nikto
During the reconnaissance stage, threat actors will search for exploitable weaknesses wherever they can, even in an organization’s website. Nikto is a Linux-based website vulnerability scanner that hackers use to identify any exploitable loopholes in organizational websites. The tool scans web servers for over 6,800 commonly exploited vulnerabilities. It also scans for unpatched versions of servers on over 250 platforms. The tool also checks for errors in the configurations of files in web servers. The tool is, however, not very good at masking its tracks, and thus almost always gets picked up by any intrusion detection and prevention system.
Nikto works through a set of command-line interface commands. Users first give it the IP address of the website that they wish to scan. The tool will do an initial scan and give back details about the web server.
From there, users can issue more commands to test for different vulnerabilities on the web server.
Figure 4.6 shows a screenshot of the Nikto tool scanning a web server for vulnerabilities. The command issued to give this output is:
Nikto -host 8.26.65.101
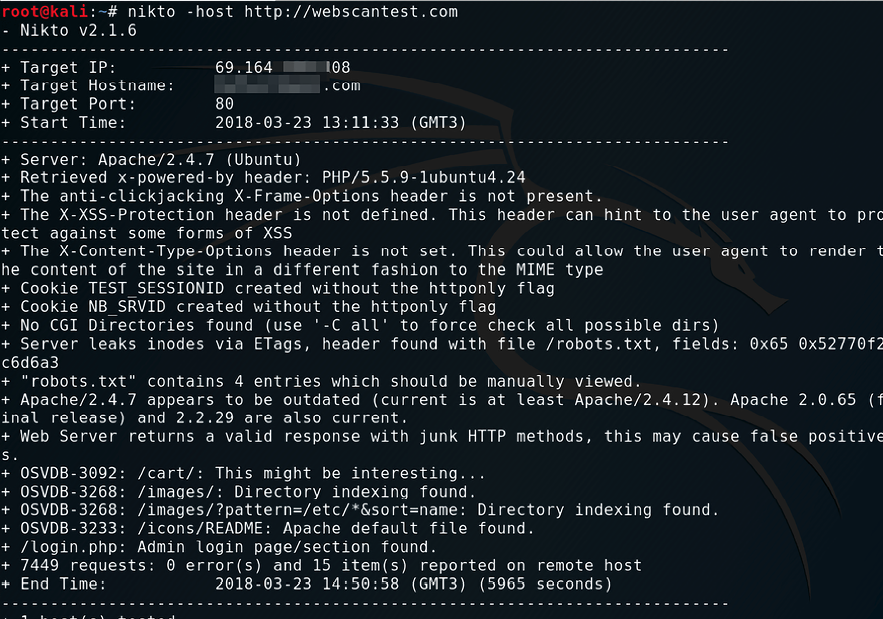
Figure 4.6: Screenshot of the Nikto tool looking for vulnerabilities in an Ubuntu server
To download Nikto, visit https://cirt.net/Nikto2.
Kismet
Kismet is a wireless network sniffer and intrusion detection system. It normally sniffs through 802.11 layer 2 traffic, which includes 802.11b, 802.11a, and 802.11g. The tool works with any wireless card available on the machine that it runs on in order to sniff out sensitive information.
Unlike other tools that use a command-line interface, Kismet is operated using a graphical user interface that pops up after a user opens the program. The interface has three sections that users use to make requests or view the status of an attack. When the tool scans a Wi-Fi network, it will detect whether it is secured or unsecured. Because of this, it is a useful tool for reconnaissance.
If it detects that a Wi-Fi network is secured, it will then detect whether the encryption used is weak. Using a number of commands, the user can instruct the tools to crack into the identified Wi-Fi networks. Figure 4.7 shows a screenshot of the Kismet GUI. The graphical user interface is well laid out and a user interacts with the program using well-defined menus, as shown in the screenshot:
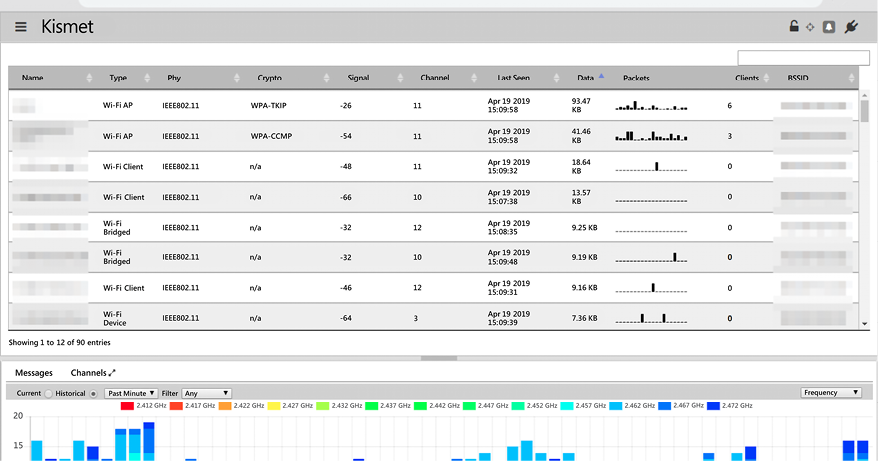
Figure 4.7: Screenshot of Kismet
To download Kismet, go to https://www.kismetwireless.net/.
Sparta
Sparta is a new network exploit tool that now comes pre-installed with Kali Linux. The tool combines the functionalities of other web attack tools that usually offer fragmented services. Conventionally, hackers use Nmap to do network scans and then execute attacks using other tools since Nmap is not designed to carry out any attack (we have already discussed a few reconnaissance tools in this chapter, but we will discuss Nmap and other tools used specifically for reconnaissance in detail in Chapter 5, Reconnaissance).
However, Sparta can conduct reconnaissance by scanning a network and identifying the hosts and services running on it, and then execute attacks against the hosts and services itself:

Figure 4.8: Sparta conducting a brute-force attack
Because of this, Sparta can be used in multiple stages of the kill chain. The tool, however, works when one is already connected to the network they wish to carry the attacks on.
John the Ripper
This is a powerful password-cracking tool available on Linux and Windows operating systems that is used by hackers to perform dictionary attacks. The tool is used to retrieve the actual user passwords from encrypted databases of desktop- or web-based systems and applications. The tool works by sampling commonly used passwords and then encrypting them with the same algorithm and key used by a given system. The tool does a comparison between its results and those that have been stored in the database to see if there are matches.
The tool cracks passwords in only two steps. First, it identifies the encryption type of a password. It could be RC4, SHA, or MD5, among other common encryption algorithms. It also looks at whether the encryption is salted.
Salted means that extra characters have been added to the encryption to make it more difficult for hackers to go back to the original password.
In the second step, the tool attempts to retrieve the original password by comparing the hashed password with many other hashes stored in its database. Figure 4.9 shows a screenshot of John the Ripper recovering a password from an encrypted hash:

Figure 4.9: Screenshot of John the Ripper recovering an encrypted password
To download John the Ripper, visit https://www.openwall.com/john/.
Hydra
Hydra is similar to the previously discussed tool, the only difference being that Hydra works online while John the Ripper works offline. Hydra is, however, more powerful and thus more popular among hackers. It is available for Windows, Linux, and Mac OS X. The tool is commonly used for fast network login hacking. It uses both dictionary and brute-force attacks to attack login pages.
Brute-force attacks may raise alarms on the target’s side if there are some security tools put in place, and thus hackers are extremely careful with the use of the tool.
Hydra has been found to be effective against databases, LDAP, SMB, VNC, and SSH.
The workings of Hydra are quite simple. The attacker gives the tool the login page to any of the target’s online systems. The tool then tries all possible combinations for the username and password fields. Hydra stores its combinations offline, making it faster to do the matching process.
The following screenshot shows the options of Hydra. The installation is being done on a Linux machine, but the process is the same for Windows and Mac. The user is required to type make install during the installation. The setup handles the rest until the completion of the installation:

Figure 4.10: A screenshot showing THC Hydra
To download THC Hydra, visit https://sectools.org/tool/hydra/.
Aircrack-ng
Aircrack-ng is a dangerous suite of tools that is used for wireless hacking and has become legendary in today’s cyberspace. The tools are available for both Linux and Windows operating systems. It is important to note that Aircrack-ng relies on other tools to first get some information about its targets. Mostly, these programs discover potential targets that can be hacked. Airdump-ng is the commonly used tool to do this, but other tools, such as Kismet, are reliable alternatives. Airdump-ng detects wireless access points and the clients connected to them. This information is used by Aircrack-ng to hack the access points.
Today, most organizations and public places have Wi-Fi, and this makes them ideal hunting grounds for hackers in possession of this suite of tools. Aircrack-ng can be used to recover the keys of secured Wi-Fi networks, provided that it captures a certain threshold of data packets in its monitoring mode. The tool is being adopted by white hats that are focused on wireless networks. The suite includes attacks such as FMS, KoreK, and PTW, which makes its capabilities incredible.
The FMS attack is used to attack keys that have been encrypted using RC4. KoreK is used to attack Wi-Fi networks that are secured with WEP-encrypted passwords. Lastly, PTW is used to hack through WEP- and WPA-secured Wi-Fi networks.
Aircrack-ng works in a number of ways. It could be used to monitor the traffic in a Wi-Fi network by capturing packets to be exported in formats that can be read by other scanning tools. It can also attack a network by creating fake access points or injecting its own packets into a network to get more information about the users and devices in a network.
Finally, it can recover passwords for Wi-Fi networks using the aforementioned attacks to try different combinations.
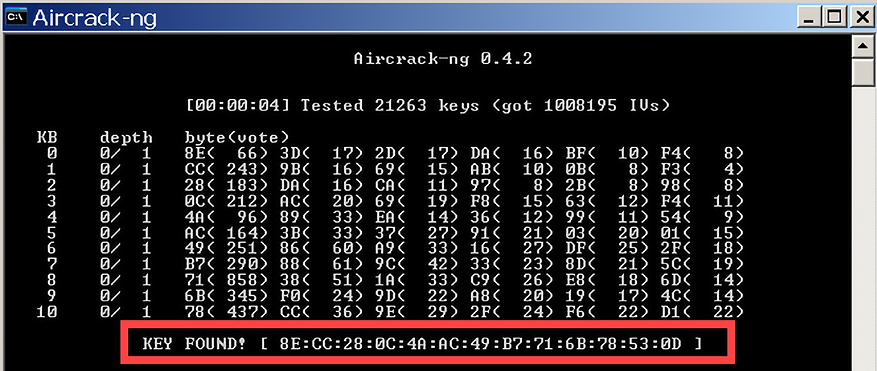
Figure 4.11: Aircrack-ng interface
Aircrack-ng can be used with Windows or Linux.
Airgeddon
This is a Wi-Fi hacking tool that can be used to give hackers access to a password-protected Wi-Fi connection. The tool capitalizes on the tendencies of network admins of setting weak passwords on Wi-Fi networks. Airgeddon requires a hacker to get a wireless network card that can listen to networks. The tool scans all the wireless networks that are in the range of the adapter and finds out the number of hosts connected to them. It then allows the hacker to select the desired network to attack. Once selected, the tool can go into monitor mode to “capture handshakes,” that is, the authentication process between clients on the network by the wireless access point. The tool first sends de-authentication packets to the WAP, hence disconnecting all the clients on a wireless network. It will then capture the handshake between clients and the AP when they try to reconnect. The handshake will be saved in a .cap file. The tool then allows the hacker to go into a WPA/WPA2 decryption mode to attempt and decrypt the handshake captured in the .cap file. This is done through a dictionary attack whereby Airgeddon will try several of the commonly used passwords in its decryption attempts. Eventually, the tool will find the password code and display it in plain text. The hacker can then join the network and execute tools such as Sparta to scan for vulnerable devices.

Figure 4.12: Airgeddon
There are only three commands required to install and run Airgeddon on Kali Linux.
To download the tool, enter:
git clone
https://github.com/v1s1t0r1sh3r3/airgeddon.git
To go to the newly created directory that contains the tool after downloading, enter:
cd airgeddon/
To run the tool itself, enter:
sudo bash airgeddon.sh
After this, Airgeddon should be up and running.
Deauther Board
This is an unconventional attack tool since it is not just a software but rather a plug-and-play board that can be connected to any computer. The Deauther board is specifically meant to attack Wi-Fi networks through de-authentication. De-authentication attacks have so far proven to be very powerful and can disconnect all devices connected to a wireless access point. During an attack, the Deauther board scans for wireless networks within range. The board has the ability to find networks within a wide range. The hacker has to select the network that the attack is to be carried out on and the board will execute a de-authentication attack. Effectively, all hosts on the network will be disconnected and will begin trying to reconnect. The board creates confusion by creating Wi-Fi networks with similar SSIDs as the one attacked. Therefore, some of the disconnected devices will try to connect to the board and give their authentication details (BSSIDs). It will attempt to capture the BSSIDs and attempts to decrypt them through brute-force or dictionary attacks. If the Wi-Fi password is weak, it is highly likely that either of these attacks will be successful in finding it. Once the hacker has the key, they can access the network and listen to the communication to and from different devices in the hope of finding exchanged login credentials.
Once sensitive credentials have been captured, the hacker can use them to gain access to systems used in organizations such as call centers or email systems.
Figure 4.13: A Deauther board
You can easily buy a Deauther board from Amazon.
HoboCopy
Windows-based systems use LM hashes to store passwords. However, it is possible to retrieve these hashes and further process them to get plain text admin passwords. HoboCopy is one of the tools that can be used in this process. HoboCopy makes use of the Volume Shadow Service to create a snapshot of a computer’s disk and then copies the contents. This technique allows it to copy all files on the disk, including the LM hashes. One can navigate through the copied contents to find the LM hashes and try to crack them using easily accessible tools such as CrackStation. Once the credentials for the admin account are known, the hacker could log out of a low-level user account on the attacked Windows computer and log in to the admin profile where they will have access to more privileges.
You can download HocoCopy from GitHub here:
https://github.com/candera/hobocopy/downloads
EvilOSX
It has long been claimed that the Apple OS ecosystem is impenetrable to hackers. Therefore, Mac users are less likely to be concerned about their security. Apple built the OS for convenience. Users normally have privileges to use apps such as Find My iPhone or My Mac to locate their devices. They are also able to view their files in iCloud across multiple devices. However, this level of integration of devices and files comes at a cost. If a hacker succeeds in breaching an Apple computer, they can have access to a lot of sensitive data and functionalities.
One of the few ways that hackers can harm a Mac computer is by acquiring remote access through a tool called EvilOSX. The only challenge with this tool is that the hacker will need to either have physical access to the victim’s computer or use social engineering to convince the target to run the payload on their system. The reason for this will be discussed in further detail shortly.
After installing the tool on Linux, one is required to build the payload. The tool requires the IP address of the computer to be used to attack a target, or in other terms, the address where the tool will execute from. The next step involves specifying a port that the tool will use. Once these are successfully set, the attack server should start. The hacker needs to run the payload on the victim’s Mac computer at this stage. This is why they need access to the targeted computer or, alternatively, to use social engineering attacks to get the user to run the payload. Once the payload is run on the target’s computer, the server is able to make a remote connection to it. On the victim’s computer, the payload runs in the background to avoid detection. On the attack server, the hacker will have unfiltered access to the remote computer.
The actual assault begins with the execution of commands that allow the hacker to take control of the compromised computer remotely. There are several modules that the EvilOSX server comes with. These include:
- Access to a remote computer’s browser history
- Upload/download of files to the victim’s machine
- Phishing the victim to steal their iCloud passwords
- Executing DoS attacks on the victim’s computer
- Taking screenshots of a victim’s machine
- Retrieving Chrome passwords from the compromised machine
- Taking pictures via the victim’s webcam
- Recording audio using the victim’s microphone
- Retrieving backups from iTunes
- Stealing iCloud authorization tokens
- Stealing iCloud contacts on the victim’s computer
A well-executed attack could be devastating to the target. Within hours, a hacker can make away with lots of sensitive information without the victim’s knowledge. The tool can gather a lot of information about one’s personal life. However, the attack ends when the victim’s computer goes offline or is shut down.
Figure 4.14: EvilOSX
You can get it from GitHub at https://github.com/Marten4n6/EvilOSX.
Comodo AEP via Dragon Platform
While the tools discussed in the previous sections provide useful resources for red-teaming and testing your systems, there are also tools that can be used to stop a real attack when it happens. One such tool is Comodo Advanced Endpoint Protection’s Dragon Platform, which brings together an approach to block hackers at each phase of the kill chain.
Comodo has a default deny technology that is particularly useful for thwarting attacks as they are happening as it prevents any unknown files from creating a socket for network communication. It is only after their File Verdict System determines that a file is safe that it is allowed to create sockets and communicate with the network. This eliminates the need for decoding the protocols, identifying non-standard port usage, and protocol tunneling as files are unable to communicate until it is confirmed that they are definitely safe.
This makes Comodo unique as creating a C&C channel is not possible with any of the attack and evasion techniques stated elsewhere in this chapter.
Comodo utilizes a slightly different version of the kill chain which has just three steps: preparation, intrusion, and active breach. This version of the kill chain is derived from MITRE ATT&CK. The image below maps these phases against Lockheed Martin’s version of the kill chain:
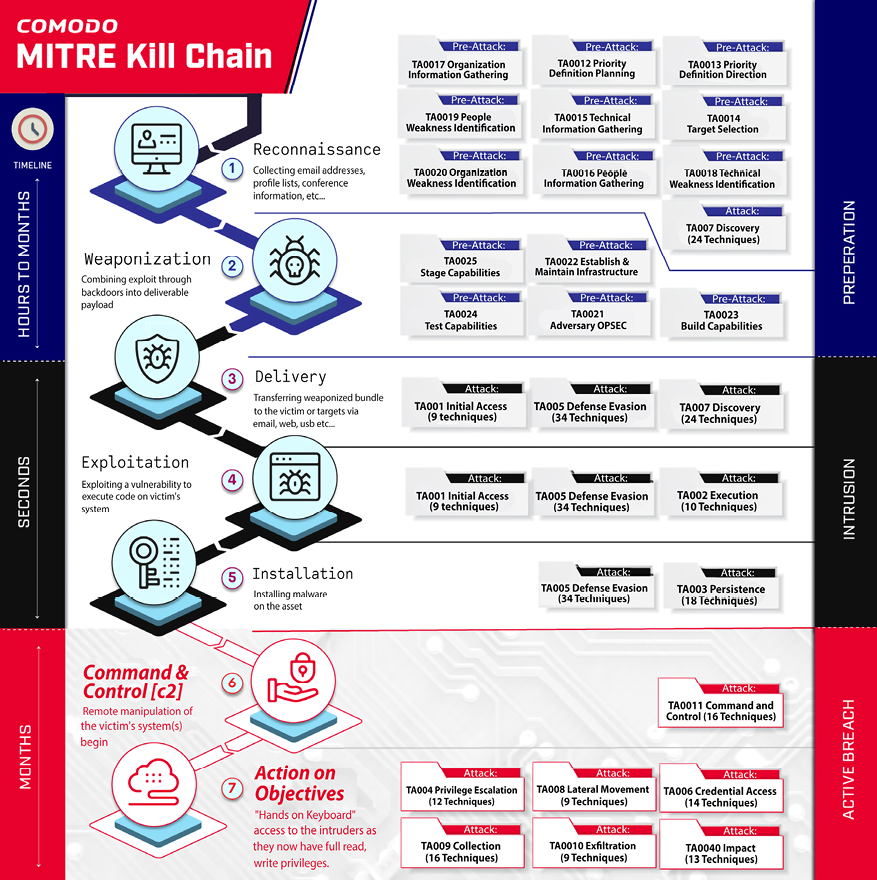
Figure 4.15: The Comodo-MITRE Kill Chain
Now let’s see how Comodo can help you build a defense against each step in the Cyber Kill Chain.
Preparation phase
Comodo has mapped the Kill Chain: Reconnaissance phase to the MITRE Pre-Attack phase. In this phase, the actions of threat actors are mostly passive, like TA0017 Organization Information Gathering, TA0019 People Weakness Identification, or TA0020 Organization Weakness Identification.
The Kill Chain: Weaponization phase is also mapped directly to the MITRE Pre-Attack phase where it essentially defines activities regarding developing the exploit and embedding it into a deliverable payload.
For defensive countermeasures against the Preparation phase, organizations should use multiple cyber threat intelligence reporting sources with varying detail to prepare policies that evaluate adversary behavior (increasing your insight into adversary activity) and assess what preventive technologies are most effective.
Figure 4.16: Tactics used against the Preparation phase
Intrusion phase
The Kill Chain: Delivery phase is where Comodo mainly starts to interact with the MITRE ATT&CK taxonomy. Starting from TA001 Initial Access to TA007 Discovery and TA005 Defense Evasion Tactics and Techniques, this stage primarily defines techniques to discover victim vulnerabilities and weaknesses regarding delivery, and uses defense evasion techniques to get initial access to a victim’s environment. These techniques include:
- Drive-by Compromise
- Exploit Public-Facing Application
- External Remote Services
- Hardware Additions
- Phishing
- Replication Through Removable Media
- Supply Chain Compromise
- Trusted Relationship
- Valid Account
The Kill Chain: Exploitation phase mainly covers TA 002 Execution Tactics. These tactics include:
- Command and Scripting Interpreter: Adversaries may abuse command and script interpreters to execute commands, scripts, or binaries. These include PowerShell, AppleScript, Unix, and the Windows shell.
- Exploitation for Client Execution: Adversaries may exploit software vulnerabilities in client applications to execute code. Adversaries can take advantage of certain vulnerabilities through targeted exploitation for the purpose of arbitrary code execution.
- Inter-Process Communication: Adversaries may abuse inter-process communication (IPC) mechanisms for local code or command execution.
- Native API: Adversaries may directly interact with the native OS application programming interface (API) to execute behaviors.
- Scheduled Task/Job: Adversaries may abuse task scheduling functionality to facilitate the initial or recurring execution of malicious code. Utilities exist within all major operating systems to schedule programs or scripts to be executed at a specified date and time.
- Shared Modules: Adversaries may abuse shared modules to execute malicious payloads. The Windows module loader can be instructed to load DLLs from arbitrary local paths and arbitrary Universal Naming Convention (UNC) network paths.
- Software Deployment Tools: Adversaries may gain access to and use third-party software suites installed within an enterprise network, such as administration, monitoring, and deployment systems, to move laterally through the network.
- System Services: Adversaries may abuse system services or daemons to execute commands or programs.
- User Execution: An adversary may rely upon specific actions by a user in order to gain execution. Users may be subjected to social engineering to get them to execute malicious code by, for example, opening a malicious document file or link.
- Windows Management Instrumentation: Adversaries may abuse Windows Management Instrumentation (WMI) to achieve execution.
The Kill Chain: Installation phase is mainly where attackers use MITRE ATT&CK Persistence tactics and, of course, defense evasion (which is present in all phases of Intrusion). Here MITRE ATT&CK Persistence tactics cover techniques after intrusion to keep access to systems across restarts, changed credentials, and other interruptions that could cut off their access. Techniques used for persistence include any access, action, or configuration changes that let them maintain their foothold on systems, such as replacing or hijacking legitimate code or adding startup code. Here is the list of full techniques related to Persistence tactics:
- Account Manipulation
- BITS Jobs
- Boot or Logon Autostart Execution
- Boot or Logon Initialization Scripts
- Browser Extensions
- Compromise Client Software Binary
- Create Account
- Create or Modify System Process
- Event Triggered Execution
- External Remote Services
- Hijack Execution Flow
- Implant Container Image
- Office Application Startup
- Pre-OS Boot
- Scheduled Task/Job
- Server Software Component
- Traffic Signaling
- Valid Accounts
When planning defenses against the Intrusion phase, network- and endpoint-based intrusion detection systems provide useful defensive countermeasures. Additionally, network-based filtering with inline-AV, proxy filters, or DNS filters can be used. Finally, next-gen AVs and EDR and EPP solutions are also key players in detecting an intrusion and eliminating it.
Active Breach phase
Things become interesting in the Active Breach phase. In this phase, the attacker has already created a persistent communication channel within the victim organization. If an attacker reaches this point that means that an organization’s countermeasures and defensive techniques have been evaded and the attacker is free to move on to their final objectives. The last two steps of the Kill Chain, Command & Control and Actions on Objectives, are regarded as active breaches.
The Kill Chain: Command and Control phase is mapped directly with MITRE ATT&CK: Command and Control tactics, which includes 16 techniques:
- Application Layer Protocol
- Communication Through Removable Media
- Data Encoding
- Data Obfuscation
- Dynamic Resolution
- Encrypted Channel
- Fallback Channels
- Ingress Tool Transfer
- Multi-Stage Channels
- Non-Application Layer Protocol
- Non-Standard Port
- Protocol Tunneling
- Proxy
- Remote Access Software
- Traffic Signaling
- Web Service
Regular defenses against C&C are based on network intrusion prevention techniques such as NIDS, NIPS, UTM, DNS filtering, etc.; however, all those techniques depend on either intrusion detection signatures or behavior-based signatures to block traffic at network boundaries. This is where Comodo AEP proves particularly useful, as it simply prevents unknown files from creating a socket for network communication, which simplifies this process significantly. As such, Comodo can be particularly useful in defending against the types of APTs that follow the cyber kill chain.
Summary
This chapter gave an overall picture of the phases commonly involved in cyber-attacks. It exposed the mindset of an attacker. It showed how an attacker gets details about a target using simple methods and advanced intrusion tools to, later on, use this information to attack users. It has discussed the two main ways through which attackers escalate their privileges when they attack systems. It has explained how cyber attackers exfiltrate data from systems that they have access to. It has also looked at scenarios where attackers proceed to attack the hardware of a victim to cause more damage. It has then discussed ways through which attackers maintain anonymity. The chapter has also highlighted ways through which users can interrupt the threat life cycle and thwart attacks. Lastly, the chapter has emphasized the need for improved security awareness in organizations as ordinary employees play a critical role in enforcing cybersecurity strategies.
The next chapter will take an in-depth look at reconnaissance to fully understand how attackers collect information about users and systems using social media, compromised websites, emails, and scanning tools.
Further reading
The following are resources that can be used to gain more knowledge about what was covered in this chapter:
- Discover & Attack Network Devices with Sparta: https://www.youtube.com/watch?v=owEVhvbZMkk
- Data exfiltration: https://www.forcepoint.com/cyber-edu/data-exfiltration
- Hacker tools for ethical hackers: https://youtu.be/X07Gc717U8E
- 15 million customer records stolen: https://www.bleepingcomputer.com/news/security/suntrust-bank-says-former-employee-stole-details-on-15-million-customers/
- Security awareness on Cyber Kill Chain: https://www.sans.org/blog/applying-security-awareness-to-the-cyber-kill-chain/
- MITRE Kill Chain: https://www.erdalozkaya.com/comodo-mitre-kill-chain/
- Cyber Kill Chain: https://www.exabeam.com/information-security/cyber-kill-chain/
References
- M. Clayton, Clues about who’s behind recent cyber attacks on US banks, The Christian Science Monitor, pp. 11, 2012. Available: https://search.proquest.com/docview/1081779990.
- B. Harrison, E. Svetieva, and A. Vishwanath, Individual processing of phishing emails, Online Information Review, vol. 40, (2), pp. 265-281, 2016. Available: https://search.proquest.com/docview/1776786039.
- M. Andress, Network vulnerability assessment management: Eight network scanning tools offer beefed-up management and remediation, Network World, vol. 21, (45), pp. 48-48,50,52, 2004. Available: https://search.proquest.com/docview/215973410.
- Nmap: the Network Mapper - Free Security Scanner, Nmap.org, 2017. [Online]. Available: https://nmap.org/. [Accessed: 20- Jul- 2017].
- Metasploit Unleashed, Offensive-security.com, 2017. [Online]. Available: https://www.offensive-security.com/metasploit-unleashed/msfvenom/. [Accessed: 21- Jul- 2017].
- R. Upadhyay, THC-Hydra Windows Install Guide Using Cygwin, HACKING LIKE A PRO, 2017. [Online]. Available: https://hackinglikeapro.blogspot.co.ke/2014/12/thc-hydra-windows-install-guide-using.html. [Accessed: 21- Jul- 2017]
- S. Wilbanks and S. Wilbanks, WireShark, Digitalized Warfare, 2017. [Online]. Available: http://digitalizedwarfare.com/2015/09/27/keep-calm-and-use-wireshark/. [Accessed: 21- Jul- 2017].
- Packet Collection and WEP Encryption, Attack & Defend Against Wireless Networks - 4, Ferruh.mavituna.com, 2017. [Online]. Available: http://ferruh.mavituna.com/paket-toplama-ve-wep-sifresini-kirma-kablosuz-aglara-saldiri-defans-4-oku/. [Accessed: 21- Jul- 2017].
- Hack Like a Pro: How to Find Vulnerabilities for Any Website Using Nikto, WonderHowTo, 2017. [Online]. Available: https://null-byte.wonderhowto.com/how-to/hack-like-pro-find-vulnerabilities-for-any-website-using-nikto-0151729/. [Accessed: 21- Jul- 2017].
- Kismet, Tools.kali.org, 2017. [Online]. Available: https://tools.kali.org/wireless-attacks/kismet. [Accessed: 21- Jul- 2017].
- A. Iswara, How to Sniff People’s Password? (A hacking guide with Cain & Abel - ARP POISONING METHOD), Hxr99.blogspot.com, 2017. [Online]. Available: http://hxr99.blogspot.com/2011/08/how-to-sniff-peoples-password-hacking.html. [Accessed: 21- Jul- 2017].
- A. Gouglidis, I. Mavridis, and V. C. Hu, Security policy verification for multi-domains in cloud systems, International Journal of Information Security, vol. 13, (2), pp. 97-111, 2014. Available: https://search.proquest.com/docview/1509582424 DOI: http://dx.doi.org/10.1007/s10207-013-0205-x.
- R. Oliver, Cyber insurance market expected to grow after WannaCry attack, FT.Com, 2017. Available: https://search.proquest.com/docview/1910380348.
- N. Lomas. (Aug 19). Full Ashley Madison Hacked Data Apparently Dumped On Tor. Available: https://search.proquest.com/docview/1705297436.
- D. FitzGerald, Hackers Used Yahoo’s Own Software Against It in Data Breach; ‘Forged cookies’ allowed access to accounts without password, Wall Street Journal (Online), 2016. Available: https://search.proquest.com/docview/1848979099.
- R. Sinha, Compromised! Over 32 mn Twitter passwords reportedly hacked Panache], The Economic Times (Online), 2016. Available: https://search.proquest.com/docview/1795569034.
- T. Bradshaw, Apple’s internal systems hacked, FT.Com, 2013. Available: https://search.proquest.com/docview/1289037317.
- M. Clayton, Stuxnet malware is ‘weapon’ out to destroy Iran’s Bushehr nuclear plant?, The Christian Science Monitor, 2010. Available: https://search.proquest.com/docview/751940033
- D. Palmer, How IoT hackers turned a university’s network against itself, ZDNet, 2017. [Online]. Available: http://www.zdnet.com/article/how-iot-hackers-turned-a-universitys-network-against-itself/. [Accessed: 04- Jul- 2017].
- S. Zhang, The life of an exhacker who is now banned from using the internet, Gizmodo.com, 2017. [Online]. Available: http://gizmodo.com/the-life-of-an-ex-hacker-who-is-now-banned-from-using-t-1700074684. [Accessed: 04- Jul- 2017].
- Busted! FBI led to Anonymous hacker after he posts picture of girlfriend’s breasts online, Mail Online, 2017. [Online]. Available: http://www.dailymail.co.uk/news/article-2129257/Higinio-O-Ochoa-III-FBI-led-Anonymous-hacker-girlfriend-posts-picture-breasts-online.html. [Accessed: 28- Nov- 2017]
Join our community on Discord
Join our community’s Discord space for discussions with the author and other readers:

