5
Reconnaissance
The previous chapter gave you an overview of all the stages of the Cyber Kill Chain life cycle. This chapter will go into the first phase of the life cycle in depth—reconnaissance.
Reconnaissance is one of the most important stages of a threat life cycle, where attackers search for vulnerabilities that they can use to attack targets. In this stage, an attacker is interested in locating and gathering data to identify any loopholes in a target’s network, its users, or its computing systems. Reconnaissance is done both passively and actively, borrowing tactics that have been used by the military. It can be compared to sending spies into an enemy’s territory to gather data about where and when to strike. When reconnaissance is done in the right way, the target should not know that it is being done. This attack life cycle phase can be actualized in a number of ways, which are broadly classified as either external or internal reconnaissance.
This chapter is going to discuss the following topics:
- External reconnaissance
- Internal reconnaissance
- Tools used during reconnaissance (both external and internal)
- Passive vs. active reconnaissance
- Sub-phases of reconnaissance
- How to combat reconnaissance
- How to prevent reconnaissance
Let’s begin by discussing external reconnaissance and some of the attacks that are classified this way.
External reconnaissance
Also known as external footprinting, external reconnaissance involves the use of tools and techniques that help hackers find information about a target while operating outside the target’s network. This exercise is stealthy and can be quite hard to detect since some reconnaissance tools are built to be evasive to monitoring tools, and others use requests that appear to be quite normal to servers.
External reconnaissance differs from internal reconnaissance as it is conducted before a threat actor has actually infiltrated an organization (it can also be conducted as an attack of its own that doesn’t infiltrate an organization at all if the threat actor isn’t aiming to conduct an advanced persistent attack). In comparison, internal reconnaissance is conducted after a threat actor has already breached an organization, and is conducted within a target’s network to gather as much intel as possible about the organization and its members (see the Internal reconnaissance section of this chapter for more details). In advanced persistent attacks, external reconnaissance is primarily focused on finding information about a target that could give an attacker the opportunity to break into the target’s network.
Although external reconnaissance often requires less effort than internal reconnaissance, its success rates tend to be low. This is because external reconnaissance attacks are normally perimeter-focused, and the hackers have little to no information about which targets are worth exploiting. That said, threat actors can still gain some information with very little effort through external reconnaissance, which makes it attractive to them to perform the required external footprinting steps. As such, incidents where external reconnaissance does prove effective usually happen because the attack exploited the carelessness of the user.
There are many different techniques an attacker may use to conduct external reconnaissance, from scanning a target’s social media, to dumpster diving, to utilizing different social engineering techniques to extract information from a target. We will examine each of these techniques over the next sections.
Scanning a target’s social media
Social media has opened up a new hunting ground for hackers. The easiest way to find information about people is by going through their social media accounts, and hackers have found this to be one of the best places to mine data concerning specific targets as people share a lot of information on such platforms. Of particular importance is data related to the companies users work for. Other key pieces of information that can be obtained from social media accounts include details about family members, relatives, friends, and residence and contact information. As well as this, attackers have learned a new way of using social media to execute even more nefarious pre-attacks.
A recent incident involving a Russian hacker and a Pentagon official showed how sophisticated hackers have become. The Pentagon official is said to have clicked on a post put up by a robot account about a holiday package. Clicking on this link compromised his computer. The attack was targeted this way because Pentagon officials had been trained by cybersecurity experts to avoid clicking or opening attachments sent by mail.
Cybersecurity experts classified this as a spear-phishing threat; however, instead of using emails, it used a social media post. Hackers look for this type of unpredictable, and sometimes unnoticeable, pre-attack. The attacker is said to have been able to access a wealth of sensitive information about the official through this attack.
Another way that hackers exploit social media users is by going through their account posts to obtain information that could be used in passwords, or as answers to secret questions used to reset some accounts. This includes information such as a user’s date of birth, their parent’s maiden name, names of the street that they grew up in, pet names, and school names. Users are known to use weak passwords due to laziness or lack of knowledge about the threats that they face. It is, therefore, possible that some users use their birth dates as their work email passwords. Work emails are easy to guess since they use a person’s official name and end in an organization’s domain name. Armed with their full name from their social media accounts, as well as viable passwords, an attacker is able to plan how to get into a network and perform an attack.
Another danger looming in social media is identity theft. It is surprisingly easy to create a fake account bearing the identity of another person. All that is needed is access to some pictures and up-to-date details of the identity theft victim. This is all in the playbook of hackers. They track information about organizations’ users and their bosses. They can then create accounts with the names and details of the bosses. This will allow them to get favors or issue orders to oblivious users, even through the likes of social media. A confident hacker could even request network information and statistics from the IT department using the identity of a high-ranking employee. The hacker will continue to get information about the network’s security, which will then enable them to find a way to hack into it successfully in the near future.
The following screenshot is taken from one of the authors’ Facebook profiles:
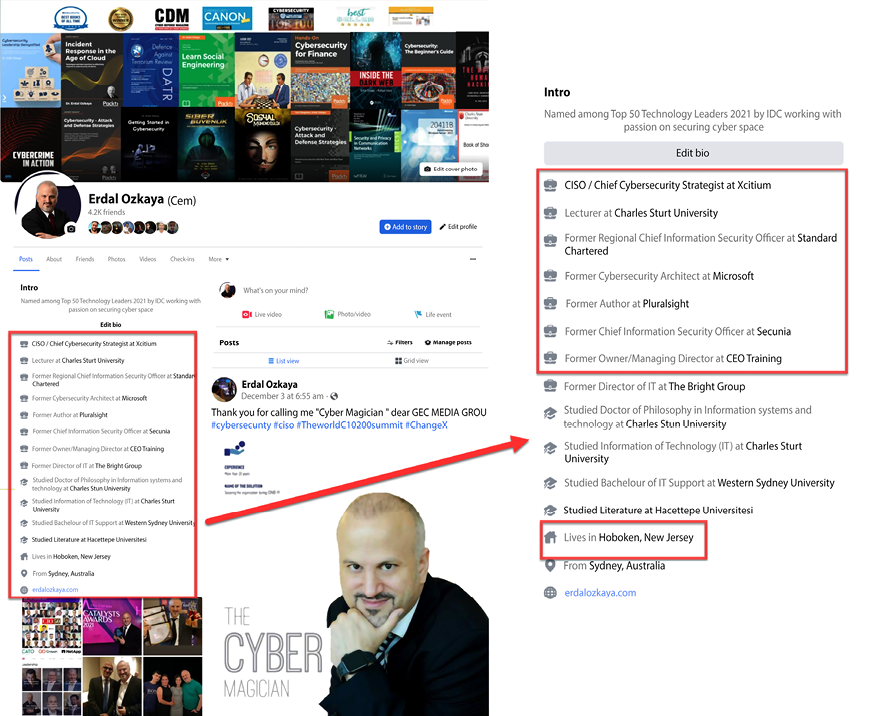
Figure 5.1: Screenshot of one of the authors’ Facebook profiles
As you can see, social media accounts can have way more information than needs to be shared. A simple search can provide a wealth of information that may be useful to a threat actor and, as such, scanning social media accounts has become a common method of conducting external reconnaissance.
Dumpster diving
Organizations dispose of obsolete devices in a number of ways, such as through bidding, sending them to recyclers, or dumping them in storage. There are serious implications for these methods of disposal. Google is one of the companies that are thorough in the way they dispose of devices that may have contained user data. The company destroys its old hard drives from its data centers to prevent the data that they contained from being accessed by malicious people. The hard drives are put into a crusher that pushes steel pistons up through the center of the disks, rendering them unreadable. This process continues until the machine spits out tiny pieces of the hard drive, which are then sent to a recycling center.
This is a rigorous and fail-proof exercise. Some other companies are not able to do this and instead opt to delete the data contained on old hard disks by using military-grade deletion software. This ensures that data cannot be recovered from old hard drives when they are disposed of.
However, most organizations are not thorough enough when handling old external storage devices or obsolete computers. Some do not even bother to delete the contained data. Since these obsolete devices may be disposed of by careless means, attackers are able to easily obtain them from their points of disposal. These obsolete storage devices can give attackers a lot of information about the internal setup of an organization. It may also allow them to access openly stored passwords on browsers, find out the privileges and details of different users, and may even give them access to some bespoke systems used in the network.
This may sound unrealistic, but even big corporations like Oracle have hired detectives to “dumpster dive” Microsoft’s trash in the past.
You can read more about it here:
Social engineering
This is one of the most feared reconnaissance acts due to the nature of the target. A company can shield itself from many types of attacks with security tools, but it cannot completely protect itself from this type of threat. Social engineering has been perfectly developed to exploit human nature—something beyond the protection of security tools. Hackers are aware that there exist very strong and powerful tools to prevent them from getting any type of information from organizational networks. Scanning and spoofing tools are easily identified by intrusion detection devices and firewalls. Therefore, it is somewhat difficult to beat today’s level of security with the usual threats since their signatures are known and can easily be thwarted. The human component, on the other hand, is still open to attacks through manipulation. Humans are sympathetic, trusting of friends, show-offs, and obedient to higher authorities; they are easy to convince provided that one can bring them around to a certain way of thinking.
There are six levers that social engineers use to get victims to talk. One of these is reciprocation, where a social engineer does something for someone who in turn feels the need to reciprocate the favor. It is part of human nature to feel obligated to return a favor to a person, and attackers have come to know and exploit this. Another lever is scarcity, where a social engineer will get compliance from a target by threatening a short supply of something that the target is in need of. It could be a trip, a mega sale, or a new release of products. A lot of work is done to find out a target’s likes in order to enable social engineers to pull this lever. The next lever is consistency, whereby humans tend to honor promises or get used to the usual flow of events. When an organization always orders and receives IT consumables from a certain vendor, it is very easy for attackers to clone the vendor and deliver malware-infected electronics.
Another lever is liking, whereby humans are more likely to comply with the requests of people they like or those that appear attractive. Social engineers are experts at making themselves sound and appear attractive to easily win the compliance of targets. A commonly used lever that has a high success rate is authority. Generally, humans are obedient to the authority of those that are ranked above them; they can therefore easily bend the rules for them and grant their wishes even if they seem malicious. Many users will give their login credentials if a high-ranking IT employee requests them. In addition, many users will not think twice if their manager or director asks them to send some sensitive data over unsecured channels. It is easy to use this lever and many people fall victim. The last lever is social validation: humans will readily comply and do something if other people are doing the same, as they do not want to seem like the odd one out. All a hacker needs to do is make something appear normal and then request an unsuspecting user to do the same.
If you want to learn more about social engineering, you can buy the following award-winning book from Dr. Erdal Ozkaya, who is a co-author of this book.

Figure 5.2: The cover of “Learn Social Engineering”
All these social engineering levers can be used in different types of social engineering attacks. Some of the most popular types of social engineering attacks include pretexting, water-holing, baiting, quid pro quo, and tailgating. All of these social engineering attacks can be used for external reconnaissance.
Pretexting
This is a method of indirectly putting pressure on targets to get them to divulge some information or perform unusual actions. It involves the construction of an elaborate lie that has been well researched so as to appear legitimate to the target. This technique has been able to get accountants to release huge amounts of money to imaginary bosses who issue an order for payment into a certain account. It is therefore very easy for a hacker to use this technique to steal the login credentials of users or to get access to some sensitive files.
Pretexting can be used to mediate an even bigger social engineering attack that will use the legitimate information to construct another lie. Social engineers that use pretexting have honed the art of impersonating other trusted individuals in society, such as police officers, debt collectors, tax officials, clergy, or investigators.
Diversion theft
This is a con game, whereby attackers persuade delivery and transport companies that their deliveries and services are requested elsewhere. There are some advantages of getting the consignments of a certain company—the attackers can physically dress as the legitimate delivery agent and proceed to deliver already-flawed products. They might have installed rootkits or some spying hardware that will go undetected in the delivered products.
Water holing
This is a social engineering attack that takes advantage of the amount of trust that users give to websites they regularly visit, such as interactive chat forums and exchange boards. Users on these websites are more likely to act in an abnormally careless manner. Even the most careful people, who avoid clicking links in emails, will not hesitate to click on links provided on these types of websites. These websites are referred to as watering holes because hackers trap their victims there just as predators wait to catch their prey at watering holes. Here, hackers exploit any vulnerabilities on the website, attack them, take charge, and then inject code that infects visitors with malware or that leads clicks to malicious pages. Due to the nature of the planning done by the attackers that choose this method, these attacks are normally tailored to a specific target and specific devices, operating systems, or applications that they use. It is used against some of the most IT- knowledgeable people, such as system administrators. An example of water holing is the exploitation of vulnerabilities on a site such as StackOverflow.com, which is often frequented by IT personnel. If the site is bugged, a hacker could inject malware into the computers of visiting IT staff.

Figure 5.3: Water holing demonstrated
Baiting
This preys upon the greed or curiosity of a certain target. It is one of the simplest social engineering techniques since all it involves is an external storage device. An attacker will leave a malware-infected external storage device in a place where other people can easily find it. It could be in the washroom of an organization, in the elevator, at the reception desk, on the pavement, or even in the parking lot. Greedy or curious users in an organization will then retrieve the object and hurriedly plug it into their machines.
Attackers are normally crafty and will leave files on the flash drive that a victim will be tempted to open. For example, a file labeled “the executive summary of salaries and upcoming promotions” is likely to get the attention of many.
If this does not work, an attacker might replicate the design of corporate thumb drives and then drop a few around the organization where they can be picked up by some of its staff. Eventually, they will end up being plugged into a computer and files will be opened.
Attackers will have planted malware to infect the computers the flash drive is plugged into. Computers configured to auto-run devices once plugged in are in greater danger, since no user action is required to initiate the malware infection process.
In more serious cases, attackers might install rootkit viruses in the thumb drive that infect computers when they boot, while infected secondary storage media is then connected to them. This will give attackers a higher level of access to the computer and the ability to move undetected. Baiting has a high success rate because it is human nature to either be greedy or curious and open or read files that are above their level of access. This is why attackers will choose to label storage media or files with tempting titles such as “confidential” or “executive” since internal employees are likely to be interested in such things.
Quid pro quo
This is a common social engineering attack that is commonly carried out by low-level attackers. These attackers do not have any advanced tools at their disposal and do not do research about the targets beforehand. These attackers will keep calling random numbers claiming to be from technical support and will offer some sort of assistance. Once in a while, they find people with legitimate technical problems and will then “help” them to solve those problems. They guide them through the necessary steps, which then gives the attackers access to the victims’ computers or the ability to launch malware. This is a tedious method that has a very low success rate.
Tailgating
This is the least common social engineering attack and is not as technically advanced as the ones we’ve discussed previously. However, it does have a significant success rate. Attackers use this method to gain entry into restricted premises or parts of buildings. Most organizational premises have electronic access control and users normally require biometric or RFID cards to be allowed in. An attacker will walk behind an employee that has legitimate access and enter behind them. At times, the attacker may ask an employee to borrow their RFID card or may gain entry by using a fake card under the guise of accessibility problems.
Phishing
This is one of the oldest tricks that hackers have used over the years, but its success rate is still surprisingly high. Phishing is mainly a technique that is used to obtain sensitive information about a company or a specific person in a fraudulent way. The normal execution of this attack involves a hacker sending emails to a target, pretending to be a legitimate third-party organization requesting information for verification purposes. The attacker normally attaches dire consequences to the lack of provision of the requested information. A link leading to a malicious or fraudulent website is also attached and the users are advised to use it to access a certain legitimate website. The attackers will have made a replica website, complete with logos and usual content, as well as a form to fill in with sensitive information. The idea is to capture the details of a target that will enable the attacker to commit a bigger crime. Targeted information includes login credentials, social security numbers, and bank details. Attackers still use this technique to capture sensitive information from users of a certain company so that they can use it to access its networks and systems in future attacks.
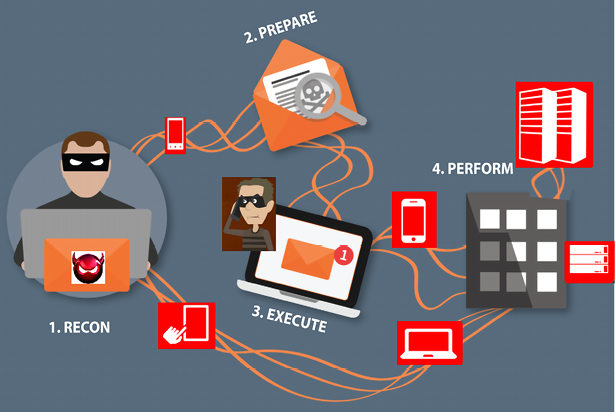
Figure 5.4: How threat actors use phishing during social engineering
Some terrible attacks have been carried out through phishing. Some time back, hackers were sending phishing emails claiming to be from a certain court and ordering the recipients to appear before the court at a certain date. The email came with a link that enabled recipients to view more details about the court notice. However, upon clicking the link, the recipients installed malware on their computers that was used for other malicious purposes, such as key logging and the collection of stored login credentials in browsers.
Another famous phishing attack was the IRS refund. Cyber attackers took advantage of the month of April, when many people were anxiously waiting for possible refunds from the IRS, and sent emails claiming to be from the IRS, attaching ransomware through a Word file. When recipients opened the Word document, the ransomware would encrypt the user’s files in the hard disk and any connected external storage device.
A more sophisticated phishing attack was used against multiple targets through a famous job board company called CareerBuilder. Here, hackers pretended to be normal job applicants, but instead of attaching resumes, they uploaded malicious files. CareerBuilder then forwarded these CVs to multiple companies that were hiring. It was the ultimate hack, which saw malware transferred to many organizations. There have also been multiple police departments that have fallen prey to ransomware. In New Hampshire, a police officer clicked on an email that appeared legitimate and the computer that he was using was infected with ransomware. This has happened to many other police departments across the world, which shows the amount of power that phishing still has.
Spear phishing
This is related to a normal phishing attack, but it does not send out high volumes of emails in a random manner. Spear phishing is specifically targeted to obtain information from particular end users in an organization. Spear phishing is more strenuous since it requires the attackers to perform a number of background checks on targets in order to identify a victim that they can pursue. Attackers will then carefully craft an email that addresses something of interest to the target, coercing him or her to open it. Statistically, normal phishing has a 3% success rate, whereas spear phishing has a 70% success rate. It is also said that only 5% of people who open phishing emails click links or download any attachments, while almost half of all people who open spear-phishing emails click on their links and download attachments.
A good example of a spear-phishing attack would be one whereby attackers are targeting a staff member in the HR department. These are employees that have to be in constant contact with the world when seeking new talent. A spear phisher might craft an email accusing the department of corruption or nepotism, providing a link to a website where disgruntled—and fictional—potential employees have been complaining. HR staff members are not necessarily very knowledgeable about IT-related issues, and therefore might easily click on such links, and as a result get infected. From one single infection, malware can easily spread inside an organization by making its way through to the HR server, which almost every organization has.
Phone phishing (vishing)
This is a unique type of phishing where the attacker uses phone calls instead of emails. It is an advanced level of a phishing attack whereby the attacker will use an illegitimate interactive voice response system that sounds exactly like the ones used by banks, service providers, and so on. This attack is mostly used as an extension of the email phishing attack to make a target reveal secret information. A toll-free number is normally provided, which when called leads the target to the rogue interactive voice response system. The target will be prompted by the system to give out some verification information. It is normal for the system to reject the input that a target gives to ensure that the target discloses several of their PINs. This is enough for the attackers to proceed and steal money from a target, be it a person or an organization. In extreme cases, a target will be forwarded to a fake customer care agent to assist with failed login attempts.
The fake agent will continue questioning the target, gaining even more sensitive information.

Figure 5.5: Obtaining login credentials via vishing demonstration
The following diagram shows a scenario in which a hacker uses phishing to obtain the login credentials of a user:

Figure 5.6: Vishing demonstrated in a cartoon
Now that we’ve examined external reconnaissance and the different types of attacks that may be used during this stage, let’s take a look at internal reconnaissance.
Internal reconnaissance
Unlike external reconnaissance attacks, internal reconnaissance is done on-site. This means that the attacks are carried out within an organization’s network, systems, and premises.
Mostly, this process is aided by software tools. An attacker interacts with the actual target systems in order to find out information about its vulnerabilities. This is the main difference between internal and external reconnaissance techniques.
External reconnaissance is done without interacting with the system, but by instead finding entry points through the people that work in an organization. That is why most external reconnaissance attempts involve hackers trying to reach users through social media, emails, and phone calls. Internal reconnaissance is still a passive attack since the aim is to find information that can be used in the future for an even more serious attack.
The main target of internal reconnaissance is the internal network of an organization, where hackers are sure to find the data servers and the IP addresses of hosts they can infect. It is known that data in a network can be read by anyone in the same network with the right tools and skill set. Attackers use networks to discover and analyze potential targets to attack in the future. Internal reconnaissance is used to determine the security mechanisms in place that ward off hacking attempts. There are many cybersecurity tools that have been made to mitigate software used to perform reconnaissance attacks. However, most organizations never install enough security tools and hackers keep on finding ways to hack through the already-installed ones. There are a number of tools that hackers have tested and have found to be effective at studying their targets’ networks. Most of them can be classified as sniffing tools.
In summary, internal reconnaissance is also referred to as post-exploitation reconnaissance since it happens after an attacker has gained access to the network. The aim of the attacker is to gather more information to move laterally in the network, identify crucial systems, and carry out the intended exploits.
Now that we’ve examined the differences between internal and external reconnaissance, let’s have a look at some of the tools that threat actors may use in these phases.
Tools used for reconnaissance
There are many recon tools available on the internet. Some of them are commercial and very expensive and some of them are totally free. In this section, we will examine some of the many tools that are used for reconnaissance. However, before we go ahead and share some useful tools here, we would like to introduce you to some comprehensive archives that are updated regularly with even more tools and exploits. As such, we recommend you visit them regularly to keep on top of the latest trends:
- Exploit-DB: The Exploit Database is a repository for exploits and proofs of concepts rather than advisories, making it a valuable resource for those who need actionable data right away. The site hosts more than 10,000 exploits and sorts them into categories based on the operating system, shellcode, and so on.
- Seebug: Seebug.org is an open vulnerability platform based on vulnerability and proof of concept/exploit sharing communities. The site has 50,000+ vulnerabilities and 40,000+ PoCs/exploits ready for use.
- Packet Storm Security: PacketStormSecurity.com has a big archive of cyber attack and defense tools, some of which we will share in this chapter. We highly recommend you visit the site regularly.
- Erdal’s cybersecurity blog: ErdalOzkaya.com has many how-to articles as well as videos on attack and defense strategies that will help you to see how you can utilize the tools covered in this book and the websites above for a better learning experience.
Now, let’s take a look at some of the new tools gaining popularity in reconnaissance.
External reconnaissance tools
There are a variety of tools that threat actors may use to conduct external reconnaissance. Some popular ones include SAINT, Seatbelt.exe, Webshag, Foca, PhoneInfoga, theHarvester, open-source intelligence, DNSdumpster, SHODAN, SpiderFoot, and Keepnet Labs. We will examine these in more detail in the following sections.
SAINT
SAINT (Security Administrator’s Integrated Network Tool) is used for scanning computer networks for security vulnerabilities, and exploiting found vulnerabilities. It can be used in scanning or reconnaissance phases. SAINT screens live systems on a network for TCP and UDP services.
For each service it finds it launches probes designed to detect anything that could allow an attacker to gain unauthorized access, create a denial-of-service, or gain sensitive information about the network.
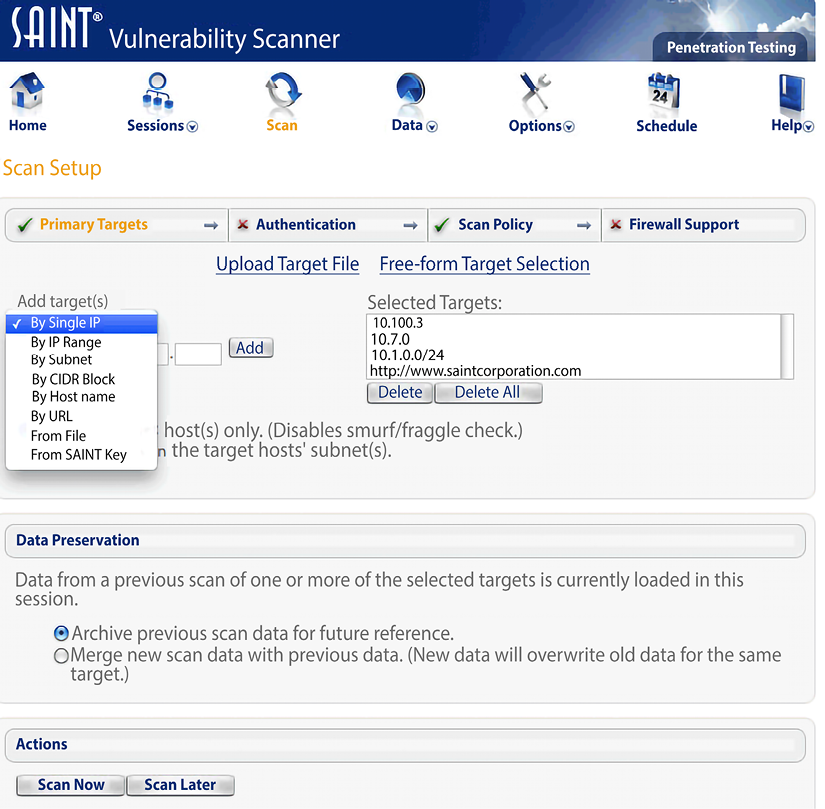
Figure 5.7: SAINT tool
You can download the tool from: https://sectools.org/tool/saint/.
Seatbelt.exe
Seatbelt is a C# project that performs a number of security-oriented host-survey safety checks relevant from both offensive and defensive security perspectives.
You can get more information about the product here: https://github.com/GhostPack/Seatbelt
Once installed, you can launch Seatbelt via the CMD line. In our case, Seatbelt is in our C drive downloads folder and so can be found through the following link: C:UsersErdaldownloadsSeatbelt.exe.
Seatbelt.exe can be used to gather really useful information: from operating system info to settings like LSA, WEF, and auditing, as well as services, RDP sessions, anti-virus information, details about registry information, and more.
Let’s have an example lab on what information we can collect via the tool. Let’s go ahead and launch the tool. Once you do that, it will look as in the screenshot below:
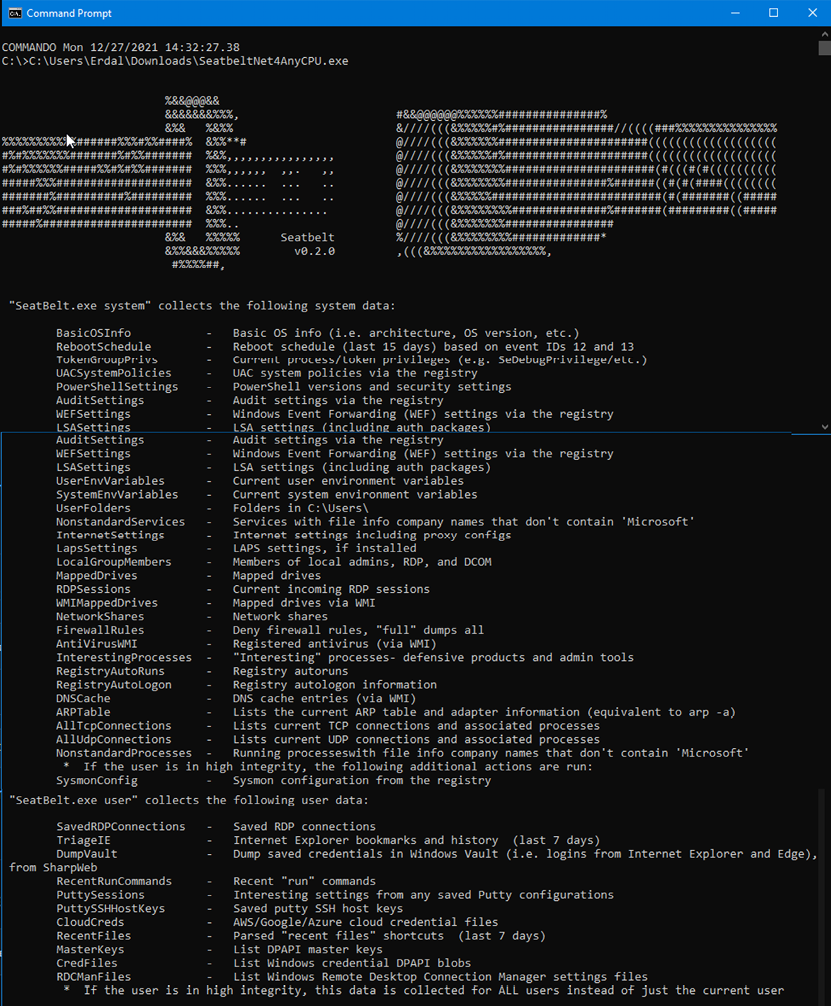
Figure 5.8: Launching Seatbelt.exe
Seatbelt can be used to gather lots of information. In this case, let’s find out what anti-virus product is installed on our target machine using the following command:
Seatbelt.exe AntiVirus
In the screenshot below, you will see that my target PC has Windows Defender installed:
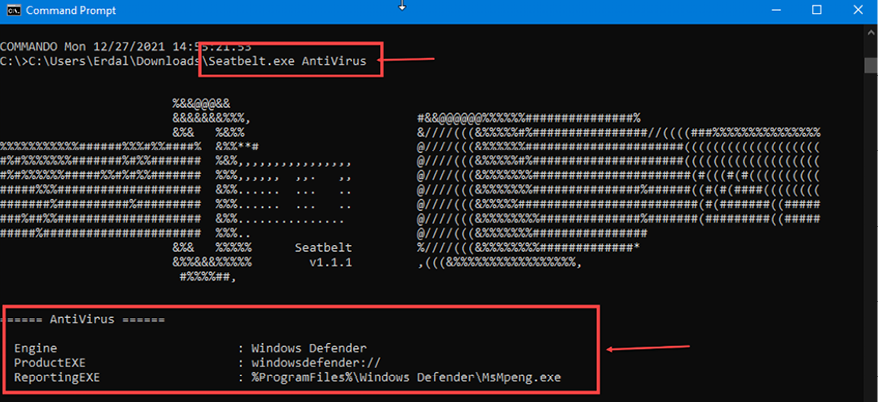
Figure 5.9: Seatbelt.exe anti-virus check
You can also find all installed products on your target machine, including the versions of the software with Seatbelt.exe InstalledProducts:
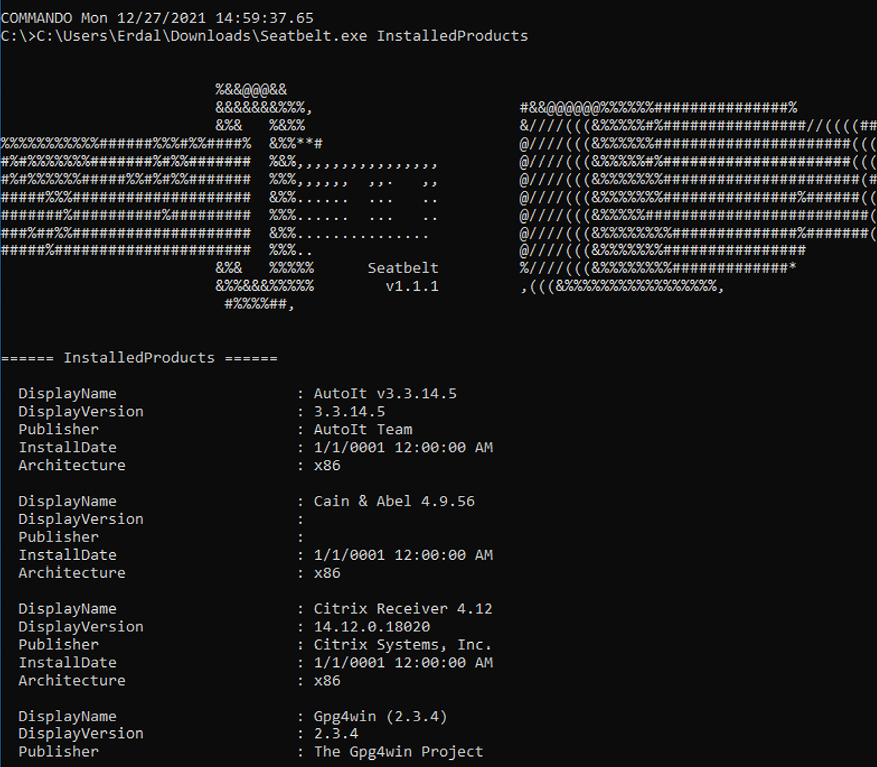
Figure 5.10: Finding installed programs on a victim’s system via Seatbelt
To find out about active TCP connections, enter the following:
Seatbelt.exe TcpConnections
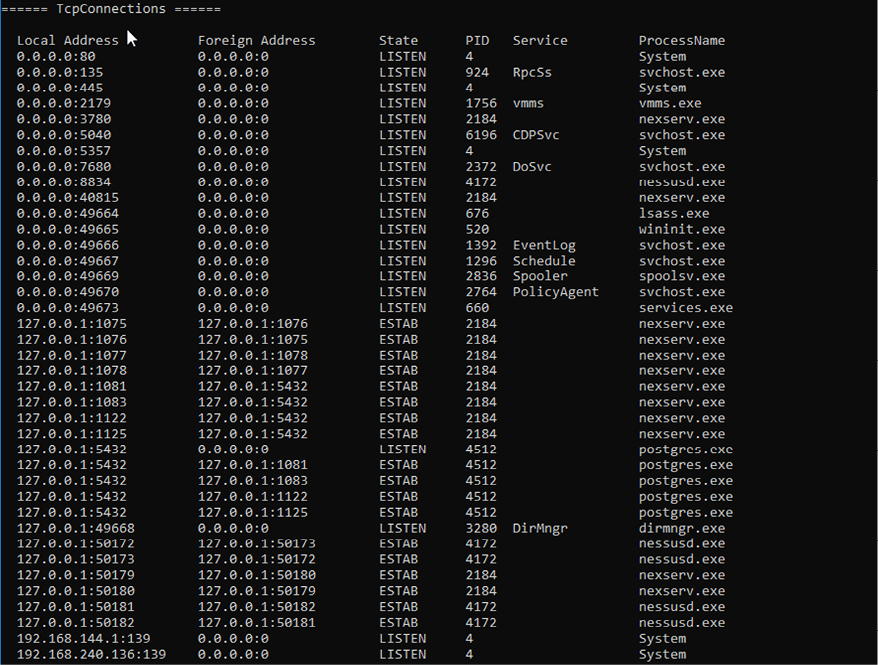
Figure 5.11: Finding active TCP connections
Additionally, Seatbelt even gives you the ability to run a group of commands:
Seatbelt.exe -group=system
This group runs nearly 50 different commands, including AMSIProviders, CredGuard, LAPS, LastShutdown, LocalUsers, WindowsDefender, and more.
The screenshot below displays one part of the command, which contains the AMSI, which can be helpful for bypassing a system’s anti-virus:
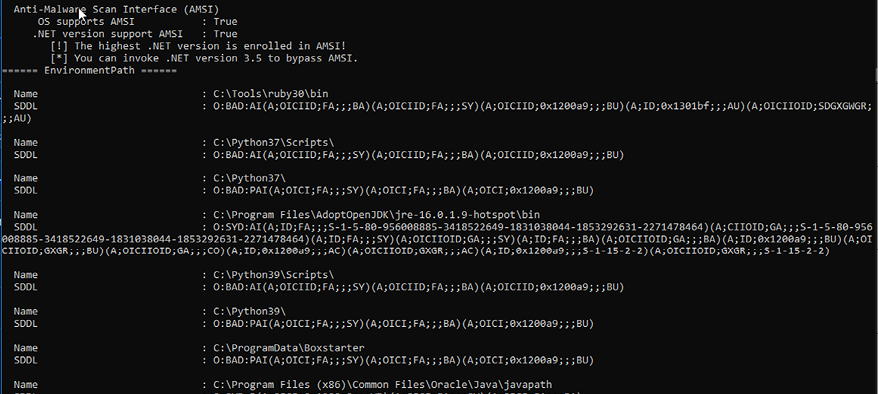
Figure 5.12: Finding active AMSI
The screenshot below displays another part of the command:
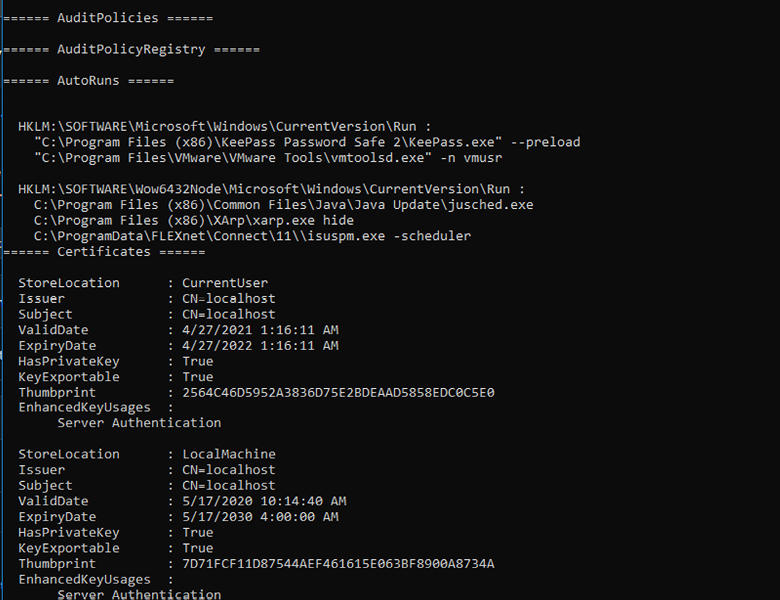
Seatbelt can also be used “remotely” where it gives us the ability to learn about the target before we attempt to exploit or laterally move within the target. Windows will automatically pass through our current user token or we can specify a username and password with -username and -password.
Here is an example:
Username: Erdal
Password: CyberBook
You will need the IP address of the target as well:
Seatbelt.exe LogonSessions -computername=192.168.241.136 -username=Erdal -password=CyberBook

Figure 5.14: Remote launch on a PC
Once the command executes you will see an output similar to the screenshot below. If you look carefully, you will see logon ID details, which could allow us to steal clear text credentials from the memory.
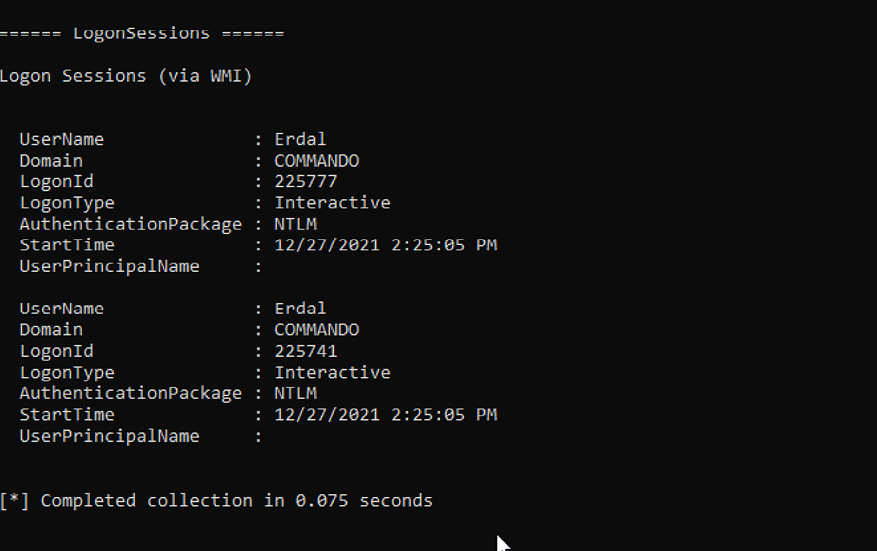
Figure 5.15: Getting information about a remote target
With this, we come to the end of this mini lab.
Webshag
This is a server scanning tool that can evade detection by intrusion detection systems. Many IDS tools work by blocking suspicious traffic from specific IP addresses. Webshag can send random requests to a server through proxies, hence evading the IP address blocking mechanism of an IDS. Therefore, the IDS will hardly be able to protect the target from being probed. Webshag can find open ports on a server and the services running on them. It has a more aggressive mode called Spider, which can list all the directories in the server to allow a hacker to dig deeper and find any loosely kept sensitive files or backups. It can also find emails and external links posted on the site. The main advantage of Webshag is that it can scan both HTTP and HTTPS protocols. It comes with Kali Linux but can still be installed on other Linux distros.
Webshag can be used in GUI or command-line versions, as in the below screenshots:
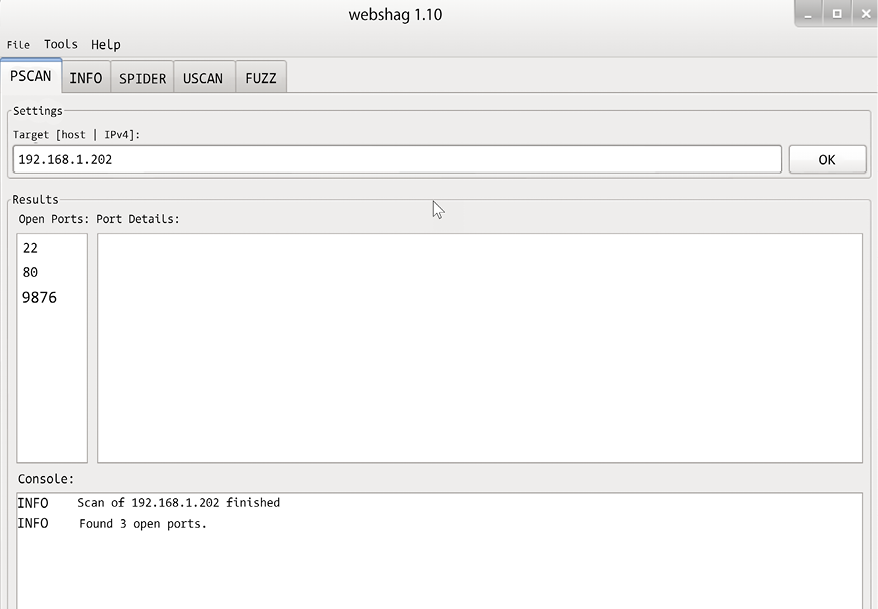
Figure 5.16: Webshag interface
And below is Webshag with the CLI in use: You can clearly see the open ports on the server and the services running on them. It also displays that the website is running on WordPress on the Apache Server, with the banner grabbed and all detected services displayed.
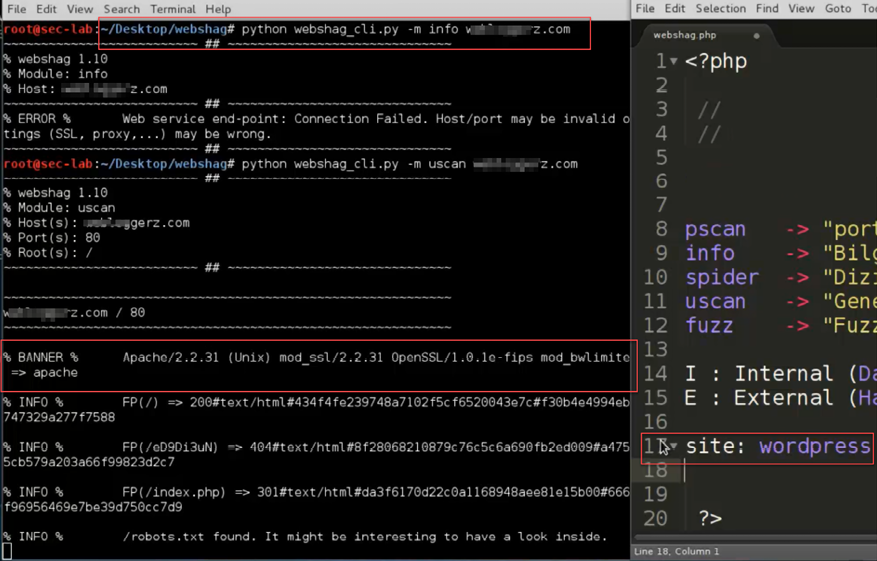
Figure 5.17: Webshag in action
FOCA
External reconnaissance involves taking information from all possible sources. At times, files can have crucial metadata that hackers can use to build an attack. FOCA (Fingerprinting Organizations with Collected Archives) is designed to help scan and extract hidden information from files and web servers. It can analyze documents and image files to find information such as authors of documents or locations in pictures. After extracting this information, FOCA uses search engines such as DuckDuckGo, Google, and Bing to collect additional information from the web that relates to the hidden metadata. Therefore, it can give social media profiles of a document author or the actual location of a place in a photo. This information is invaluable to hackers as they will start profiling some of the targets and possibly try to phish them through emails or social media.
In the screenshot below you will see FOCA in action:
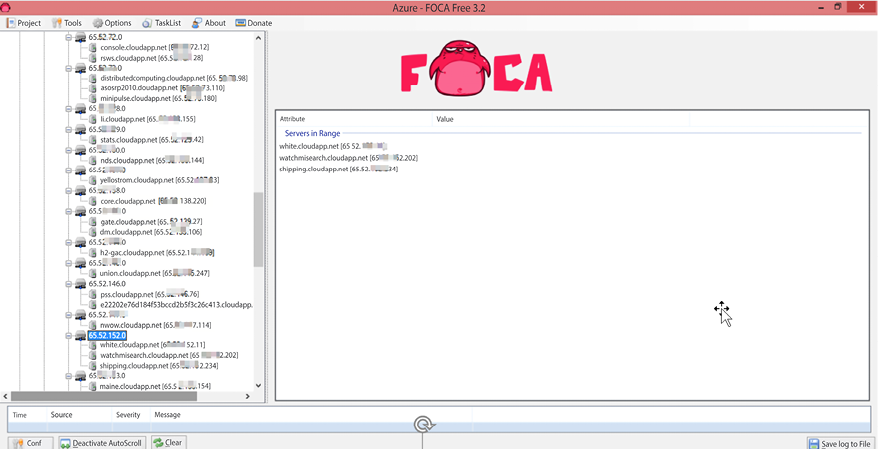
Figure 5.18: FOCA cloud recon
You can download FOCA from GitHub: https://github.com/ElevenPaths/FOCA
PhoneInfoga
PhoneInfoga is one of the tools currently used to find usable data about a target using their mobile number. The tool has a rich database and can tell whether a phone number is a throw-away or a voice-over IP number. In some cases, users that are knowledgeable about security threats might use these types of numbers to avoid leaving trails of their actual identities. This tool will simply inform a hacker in such cases so that they do not pay lots of attention to chasing such a target. PhoneInfoga can also reliably tell the carrier that a phone number operates on. All a hacker needs to do is tell the tool to do an OSINT scan of the number. The tool uses local network scans, third-party number verification tools, and web scans to find any footprints of the number. The tool runs on any OS, provided that one has installed its dependencies, which are Python 3 and pip3.
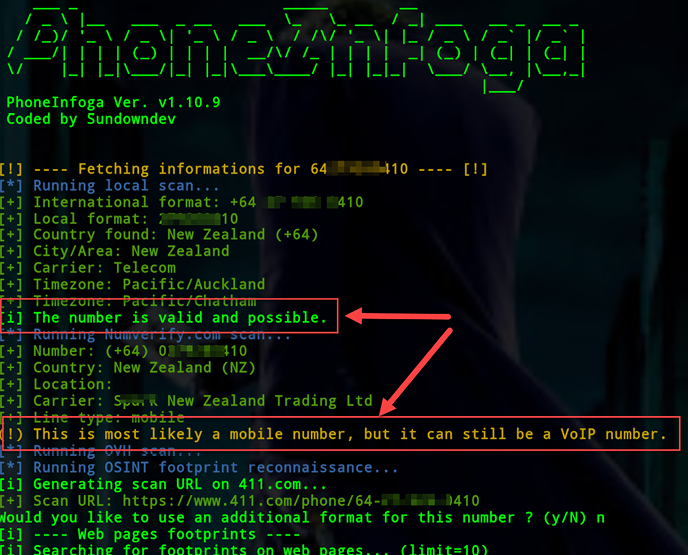
Figure 5.19: Verifying a mobile number with PhoneInfoga
You can download the tool here: https://github.com/sundowndev/PhoneInfoga
theHarvester (email harvester)
theHarvester is a relatively new external reconnaissance tool that is used to gather domain email addresses. Attackers may use this tool for reconnaissance if they wish to perform actual exploitation using phishing attacks. theHarvester allows hackers to specify the domains or company names to search from and the data source to use. The data sources the hacker has to choose from include Google, Bing, DuckDuckGo, Twitter, LinkedIn, Indeed, or just all the data sources the tool can query. The tool also allows the hacker to limit the number of results and do referential checks of any discovered emails with Shodan. theHarvester is highly effective and can obtain email addresses scattered all over the internet. Hackers can profile users with these email addresses and carry out social engineering attacks or send them malicious links.
The below screenshot showcases the abilities of the tool:
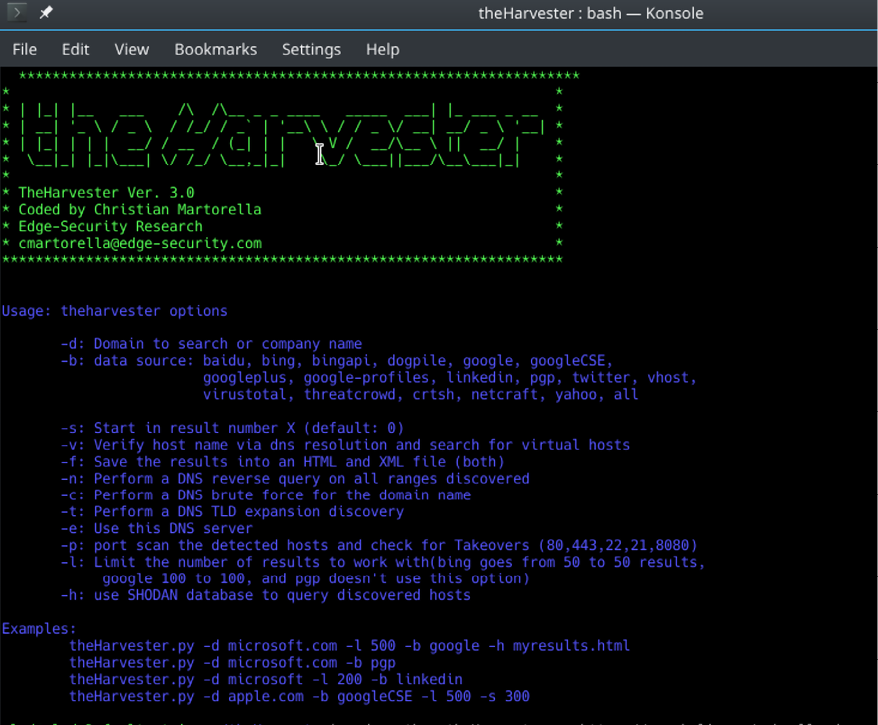
Figure 5.20: theHarvester usage options
Open-source intelligence
Open-source intelligence (OSINT) is an intelligence discipline where data is gathered from open sources such as websites, to produce actionable intelligence. OSINT Framework is a collection of OSINT tools for different OSINT objectives, as can be seen in the following image:
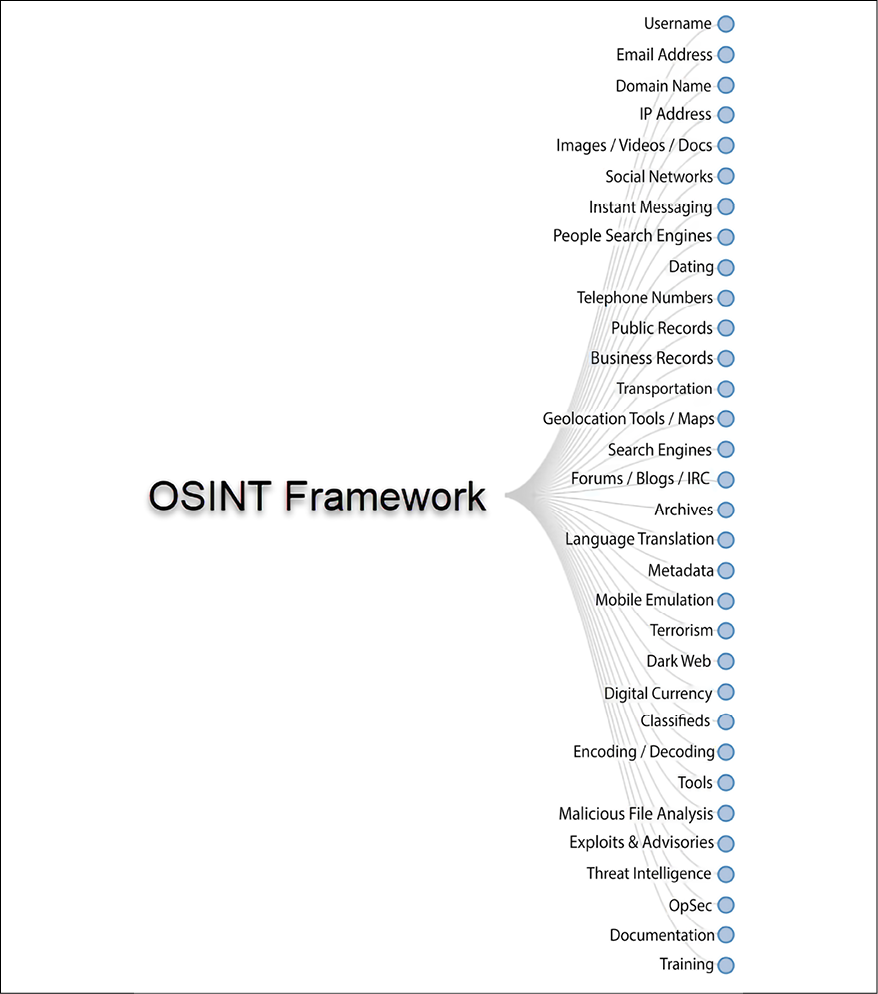
Figure 5.21: OSINT Framework
You can get more information about OSINT via https://osintframework.com/.
Let’s have some small labs on how OSINT can help us to find information from public websites.
Mini labs on OSINT
Select the target you want to collect information from. In our case, I will use www.ErdalOzkaya.com.
We will look for:
- What domains are used by your target
- If your target has some new items, press releases, or any info that you might use in a social engineering attack
Let’s collect as much information about our target as possible.
First, navigate to https://search.arin.net/ and search for your target, in our case, erdalozkaya.com.
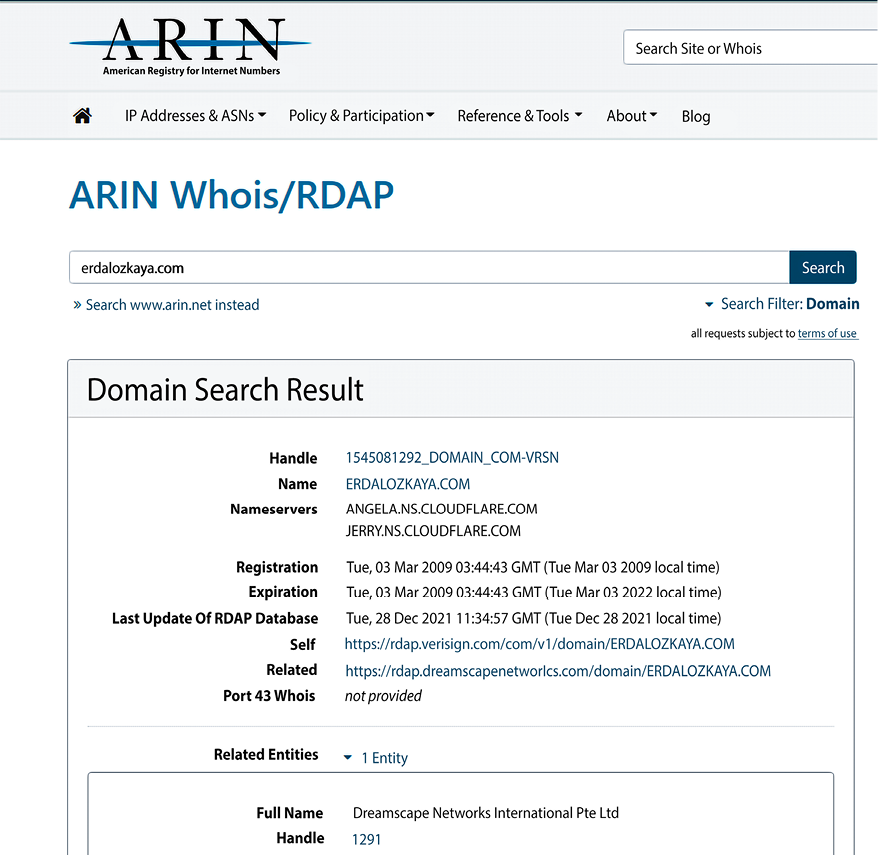
Figure 5.22: Search results with ARIN
Now let’s see if we can perform DNS reconnaissance based on the information gathered from ARIN. To do this, we will use the DNSRecon tool.
DNSRecon can perform a variety of functions ranging from security assessments to basic network troubleshooting by allowing users to check DNS-related data. The tool is preinstalled on Kali Linux.
Once you launch the DNSRecon tool in Kali, execute the command below:
dnsrecon -d erdalozkaya.com -n 8.8.8.8
-d will help you specify your target (microsoft.com in our case).
-n will specify the name of the server to use—in our case, we used Google (8.8.8.8).
You should get a similar result to the screenshot below. Please be aware you can use any domain name, and here we changed the domain name from Erdal’s blog to Microsoft.
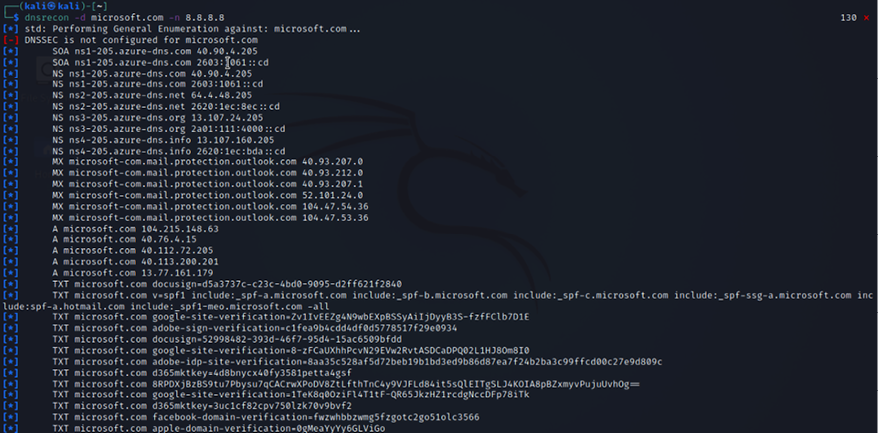
Figure 5.23: Using DNSRecon
MX records can help you to craft phishing attacks.
If you want to ensure that the DNS records are relevant to your target, then you can put a -w at the end of your search, which will perform a deep record analysis and reverse lookup of IP ranges found through WHOIS.

Once the query is done, press n to exit.
If you want to run a reverse lookup, then you can use the following command:
dnsrecon -d microsoft.com -n 8.8.8.8 -r "IP address"
Your result may vary, so here is a guide as to what each message means:
PTR vpn: VPN servers are allowed remote accessPTR dropbox: May be an opportunity for you to find access to their storagePTR admin: Yes, “admin,” so a great opportunity to explore the network as an admin
DNSdumpster
Another tool that can be used for OSINT is the website DNSdumpster (https://dnsdumpster.com/). We will use this to check for the DNS:
- Navigate to the DNSdumpster website
- Enter the domain that you want to get info on—in our case, microsoft.com—and you should get a similar response to the below screenshot:
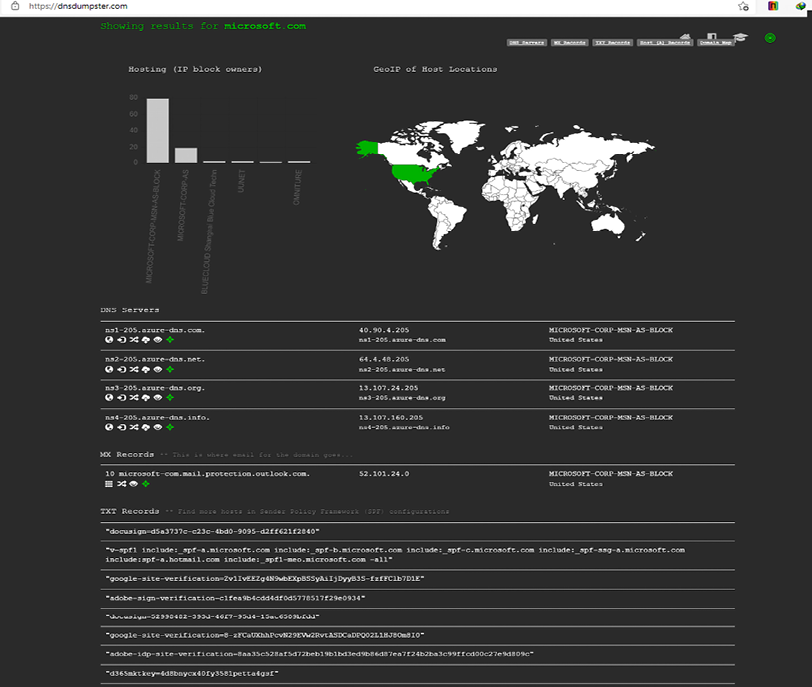
Figure 5.25: Using DNSdumpster
If you look carefully, you can see the list of DNS servers and IP addresses.
Shodan
Shodan is the world’s first search engine for internet-connected devices and enables you to discover how internet intelligence can help you make better decisions. Web search engines are for finding websites, but if you want to know which version of Microsoft IIS is the most popular and where you can find it, then Shodan is the place to search. Additionally, Shodan can even help you to find control servers for malware, new vulnerabilities related to IP addresses, exploits, and more.
We highly recommend spending much more time playing with this search engine than in this little exercise: https://www.shodan.io/.
Let’s search our example domain, and look at any interesting targets or information on the technology being used:
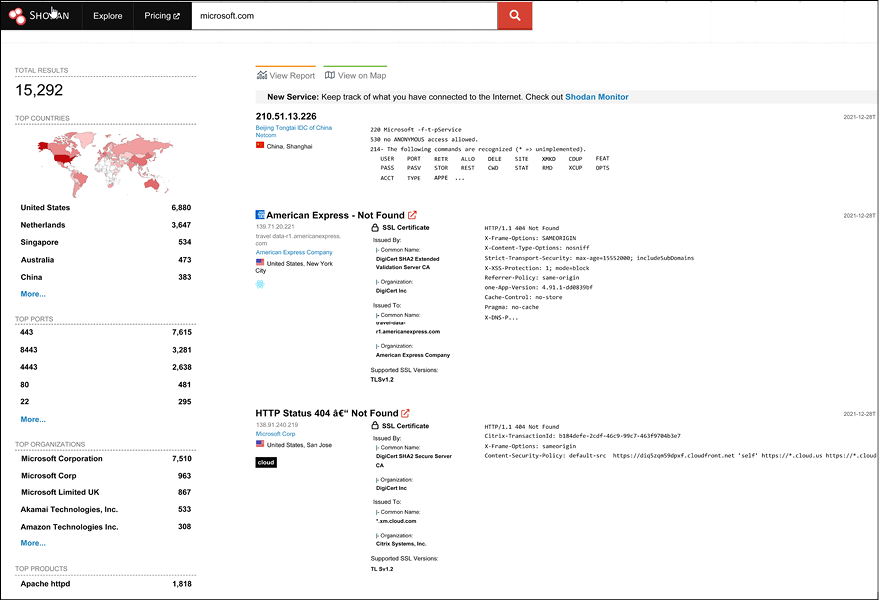
Figure 5.26: Shodan in action
SpiderFoot
Another tool is SpiderFoot, which can automate OSINT for threat intelligence, asset discovery, attack surface monitoring, or security assessments. SpiderFoot automates the process of gathering intelligence about a given target, which may be an IP address, domain name, hostname, network subnet, ASN, email address, or a person’s name.
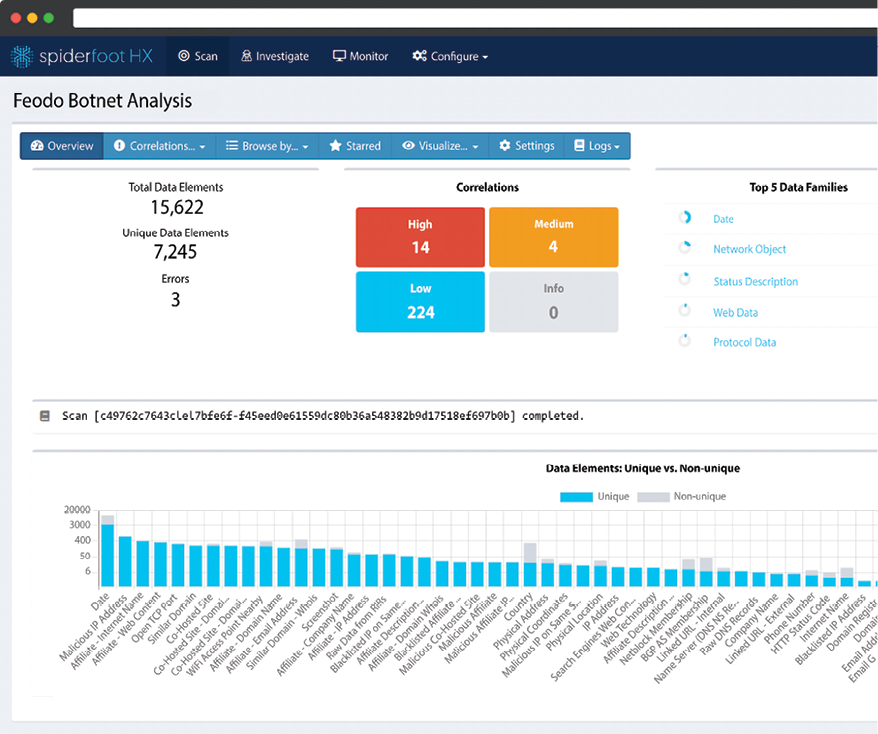
Figure 5.27: SpiderFoot scan
You can use SpiderFoot via Kali Linux, which is already preinstalled, or you can download it from their website: https://www.spiderfoot.net/.
Keepnet Labs
While the tools listed above can be used by organizations to emulate external reconnaissance, Keepnet Labs provides a tool that is expressly designed for this purpose. Keepnet Phishing Simulator is an excellent tool that can also be used as part of a security awareness training program, especially to fight against different social engineering attacks. No matter how secure your network or computer system and software, the weakest link in security posture, the people element, can be exploited. Via phishing techniques, the most common social engineering techniques used in cyber attacks, it is easy to impersonate people and get the information needed. Thus, traditional security solutions are not enough to reduce these attacks. Simulated phishing platforms send fake emails to test whether users and line employees interact with the emails.
Keepnet Labs allows you to run various phishing scenarios to test and train your employees. Keepnet also has different modules, such as Incident Responder, Threat Intelligence, and Awareness Educator.
The below screenshot displays all those modules and more.
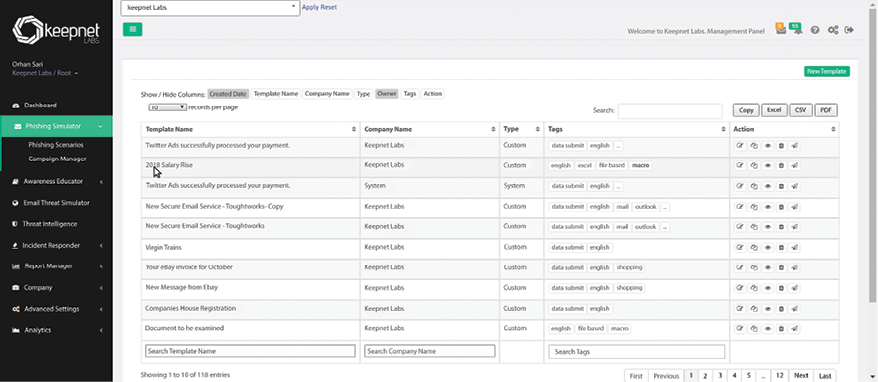
Figure 5.28: Modules in Keepnet Labs
You can learn more about Keepnet and also sign up for a free demo on their website: https://www.keepnetlabs.com/.
Internal reconnaissance tools
There are also several tools that threat actors may utilize for internal reconnaissance. Some of the most popular include Airgraph-ng; sniffing and scanning tools such as Prismdump, tcpdump, Nmap, and Wireshark; Scanrand; Masscan; Cain and Abel; Nessus; Metasploit; Hak5 Plunder Bug; CATT; canary token links; and Aircrack-ng. We will look at these in more detail in the following sections.
Airgraph-ng
When attacking corporate networks and public WiFi hotspots, commonly used scanners such as Nmap might bring confusing results due to the large number of hosts connected to a single network. Airgraph-ng is meant to specifically handle this challenge by visualizing network scan results in a more appealing way. Airgraph-ng comes as an add-on to Aircrack-ng, which was discussed in the previous chapter. It, therefore, borrows the scanning abilities of Aircrack-ng and combines them with aesthetic outputs that help hackers get a better view of the devices in a network. When connected to a network or within range of a WiFi network, Airgraph-ng can list the Mac addresses of all the devices in the network and other details such as the type of encryption used and the rate of data flow. The tool can write this information to a CSV file for further processing to come up with an output that is more understandable and easier to read. Using the data on the CSV file, Airgraph-ng can create two types of graphs. The first one is the CAPR (Client to AP Relationship) graph, which shows all the networks scanned and the clients connected to them. In addition, the tool will show the manufacturers of the devices detected. However, the CAPR graph is limited to showing information about devices that are connected to the scanned networks. To dig deeper into a device of interest, it might be worth looking into networks that devices have connected to in the past. The second type of graph that Airgraph-ng can produce is called CPG (Common Probe Graph). The CPG graph shows the MAC address of a device and the networks that the device has connected to in the past. Therefore, if you scan a hotel WiFi network, you can see the devices connected to it and the networks they were previously connected to. This could be very helpful when isolating targets of interest such as staff working in certain types of organizations. This information is also useful in the exploit phase since the attacker can create their own wireless network with an SSID similar to a previously connected network. The target device might try to connect to the spoofed network giving an attacker more access to the device.
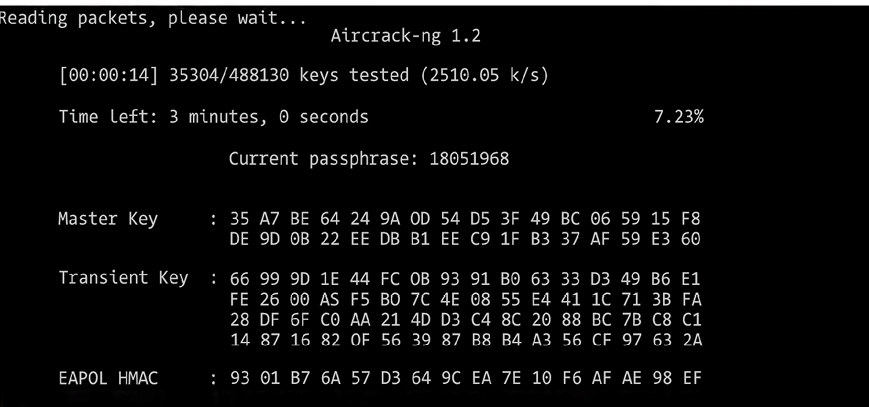
Figure 5.29: Aircrack-ng cracking a system’s wireless password
The above screenshot from Aircrack-ng, which works in Windows 10, shows it busy cracking the wireless password.
You can download the tool here: https://www.aircrack-ng.org/doku.php?id=airgraph-ng.
Sniffing and scanning
These are terms used in networking that generally refer to the act of eavesdropping on traffic in a network. They enable both attackers and defenders to know exactly what is happening in a network. Sniffing tools are designed to capture the packets being transmitted over a network and to perform analysis on them, which is then presented in a human-readable format. In order to perform internal reconnaissance, packet analysis is more than essential. It gives attackers a lot of information about the network to a level where it can be compared to reading the logical layout of the network on paper.
Some sniffing tools go to the extent of revealing confidential information, such as passwords from WEP-protected WiFi networks. Other tools enable users to set them up to capture traffic over a long period of time on wired and wireless networks, after which the users can analyze the output of the network traffic at their own convenience.
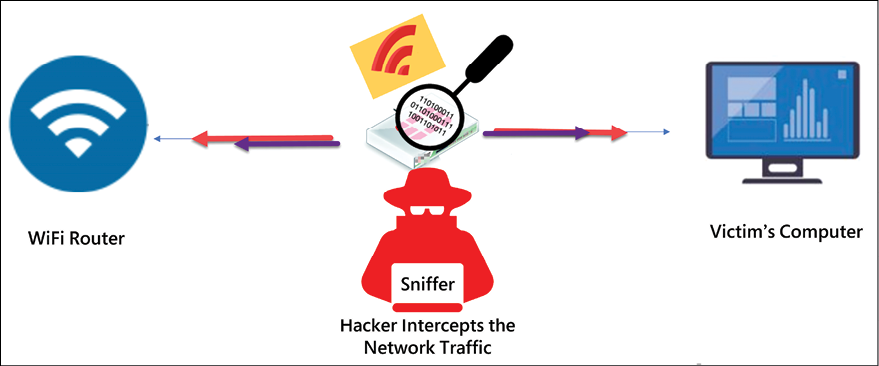
Figure 5.30: Sniffing demonstrated
There are a number of sniffing tools available today that hackers commonly use.
Prismdump
Designed only for Linux, this tool allows hackers to sniff with Prism2 chipset-based cards. This technology is only meant to capture packets, and therefore leaves analysis to be performed by other tools; this is the reason why it dumps the captured packets in the pcap format, which is widely used by other sniffing tools. Most open-source sniffing tools use pcap as the standard packet capture format.
Since this tool is only specialized to capture data, it is reliable and can be used for long reconnaissance missions. The following is a screenshot of the Prismdump tool:

Figure 5.31: Prismdump in action
tcpdump
This is an open-source sniffing tool that is used for packet capture and analysis. tcpdump runs using a command-line interface. tcpdump has also been custom-designed for packet capturing as it does not have a GUI that enables the analysis and display of data. It is a tool with one of the most powerful packet-filtering capabilities and can even selectively capture packets. This differentiates it from most other sniffing tools that have no means of filtering packets during capture. The following is a screenshot of the tcpdump tool. In the screenshot, it is listening to the ping commands being sent to its host:
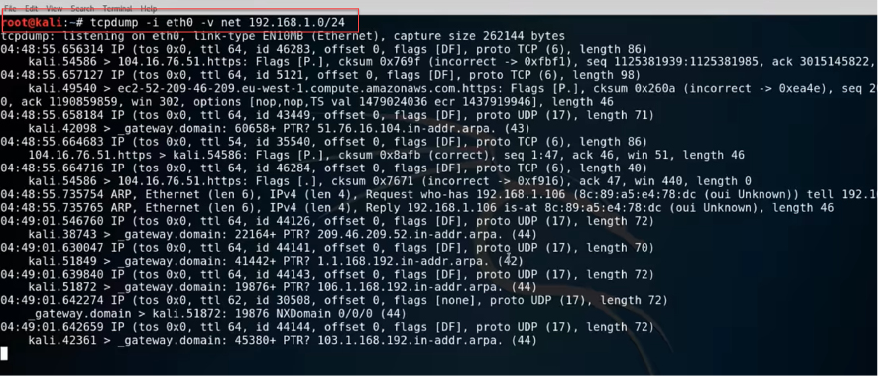
Figure 5.32: tcpdump in action
You can download the tool here: https://www.tcpdump.org/.
Nmap
This is an open-source network sniffing tool that is commonly used to map networks. The tool records IP packets entering and leaving a network. It also maps out fine details about a network, such as the devices connected to it and also any open and closed ports. The tool can go as far as identifying the operating systems of the devices that are connected to the network, as well as the configurations of firewalls. It uses a simple text-based interface, but there is an advanced version of it called Zenmap that also has a GUI. The following is a screenshot of the Nmap interface. The command being executed is:
#nmap 192.168.12.3
This command is executed to scan the ports of the computer on the IP address 192.168.12.3:
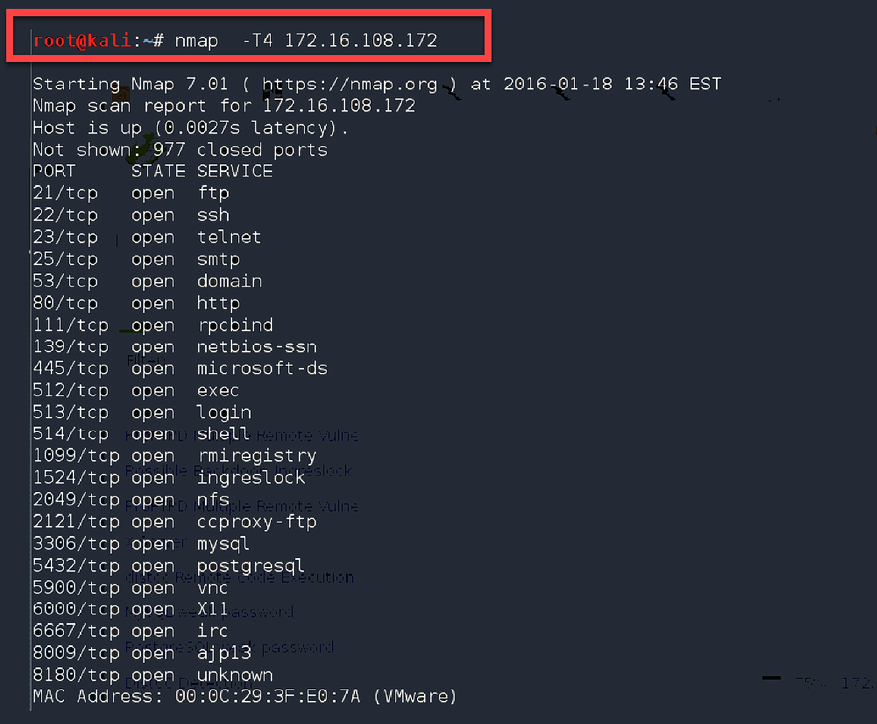
Figure 5.33: Nmap in action
You can download the latest version of Nmap here: https://nmap.org/.
Nmap functionalities
The Nmap tool is a popular tool in the cybersecurity world. The tool is popular both with ethical hackers as well as malicious hackers. The reason for the tool’s popularity lies in its flexibility and power. Nmap’s main function is to do port scanning. However, it also enables users to perform a host of other functionalities. These include:
- Network mapping: The Nmap tool can help identify all the devices that are on the target network. This process is also referred to as host discovery. During network discovery, other devices identified include servers, switches, routers, and how they are physically connected.
- Service discovery: The Nmap tool can also identify the kind of services that the hosts identified in the network do. It can tell whether hosts are offering such services as mail provision, acting as web servers, or as name servers. In addition, Nmap can determine the applications used by these devices, including the versions of software they are running.
- OS detection: Nmap can help determine the kind of operating systems that are running on network devices. This process is also referred to as OS fingerprinting. In addition, you can identify details such as the devices’ vendors, the software applications that run on all the devices, and the uptime for all these devices.
- Security auditing: Nmap will help network managers in determining the versions of the operating systems that are running on the devices that are connected to the network along with the applications running on these devices. This kind of information lets the network managers determine the vulnerability that is inherent to the specific versions of the software and applications that have been identified. Scripts can be used with the Nmap tool to help identify vulnerabilities as well.
The advantages of the Nmap tool
The Nmap tool is a favorite tool among both hackers and penetration testers. The reason for the popularity of the tool is the many advantages it offers its users. Some of these benefits include:
- The Nmap tool is easy to use: It can be used by people with limited programming or network skills.
- The Nmap tool is fast: The tool is very fast and provides scanning results pretty quickly.
- The tool has a wide range of features enabling network managers to perform a myriad of other functions.
- The Nmap tool is usable in multiple operating systems. It can be used for both Windows and Linux platforms.
- The Nmap tool can be used with multiple interfaces: It can be used comfortably with both graphical user interfaces and the command line.
- The Nmap tool enjoys a big user community that has helped improve the features of the tool and addresses the weaknesses it has in addition to helping expand the features it offers.
- The Nmap tool has many extensible features that allow it to perform several functions.
Wireshark
This is one of the most revered tools used for network scanning and sniffing. The tool is so powerful that it can steal authentication details from the traffic sent out of a network. This is surprisingly easy to do, such that one can effortlessly become a hacker by merely following a few steps. On Linux, Windows, and Mac, you need to make sure that a device, preferably a laptop, installed with Wireshark is connected to a network. Wireshark needs to be started so that it can capture packets. After a given period of time, you can stop Wireshark and proceed to perform the analysis. To get passwords, you need to filter the data captured to show only the POST data. This is because most websites use the POST method to transfer authentication information to their servers. It will list all the POST data actions that were made. Then right-click on any of these and select the option to follow the TCP stream. Wireshark will open a window showing a username and password. At times, the captured password is hashed, and this is common with websites. You can easily crack the hash value and recover the original password using other tools.
Wireshark can also be used for other functions, such as recovering WiFi passwords. Since it is open-source, the community continually updates its capabilities and therefore will continue to add new features. Its current basic features include capturing packets, importing pcap files, displaying protocol information about packets, exporting captured packets in multiple formats, colorizing packets based on filters, giving statistics about a network, and the ability to search through captured packets. The file has advanced information, and this makes it ideal for hacking. The open-source community, however, uses it for white hacking, which discovers vulnerabilities in networks before black hats do.
The following is a screenshot of Wireshark capturing network packets:

Figure 5.34: Wireshark capturing network packets
You can download Wireshark from here: https://www.wireshark.org/#download.
Scanrand
This is a scanning tool that has been specifically made to be extremely quick but effective. It tops most other scanning tools with its fast speeds, which it achieves in two ways. The tool contains a process that sends multiple queries at once and another process that receives the responses and integrates them. The two processes do not consult and therefore the receiving process never knows what to expect—just that there will be response packets.
There is, however, a clever hash-based way that is integrated into the tool that allows you to see the valid responses that it receives from scanning.
Masscan
This tool operates like Scanrand (which is harder to find today because of the lack of support from developers), Unicornscan, and ZMap, but it’s much faster, transmitting 10 million packets per second. The tool sends multiple queries at once, receives the responses, and integrates them. The multiple processes do not consult each other and therefore the receiving process will receive only response packets. Masscan is part of Kali Linux.
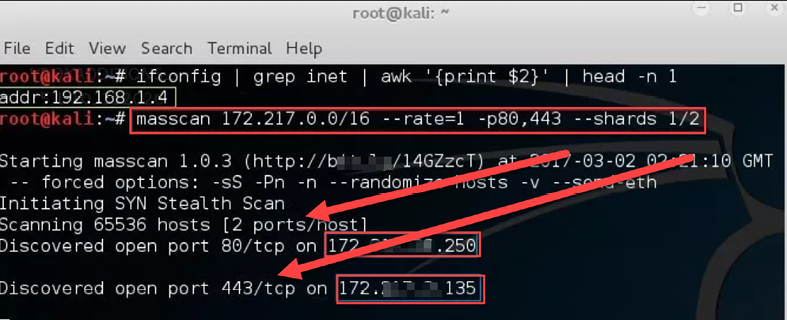
Figure 5.35: Masscan in action
Cain and Abel
This is one of the most effective tools for cracking passwords made specifically for the Windows platform. The tool recovers passwords by cracking them using dictionary, brute force, and cryptanalysis attacks. It also sniffs from the network by listening in to voice-over IP conversations and uncovering cached passwords. The tool has been optimized to work only with Microsoft operating systems.
The following is a screenshot of the Cain and Abel tool:

Figure 5.36: The old but gold tool “Cain and Abel”
This tool is now outdated, does not work with up-to-date operating systems like Windows 10, and is not available on the developer’s website anymore. But saying that, knowing that there are many Windows 7 or even Windows XP systems still on the market, it’s good to know what the tool can do. As a result, we decided to keep the tool in the new version of this book.
Nessus
This is a free scanning tool made and distributed by Tenable Network Security. It is among the best network scanners and has bagged several awards for being the best vulnerability scanner for white hats. Nessus has several functionalities that may come in handy for an attacker doing internal reconnaissance. The tool can scan a network and show connected devices that have misconfigurations and missing patches. The tool also shows devices that are using their default passwords, weak passwords, or have no passwords at all.
The tool can recover passwords from some devices by launching an external tool to help it with dictionary attacks against targets in the network. Lastly, the tool is able to show abnormal traffic in the network, which can be used to monitor DDoS attacks. Nessus has the ability to call external tools to help it achieve extra functionality. When it begins scanning a network, it can call NMap to help it scan for open ports and will automatically integrate the data that NMap collects. Nessus is then able to use this type of data to continue scanning and find out more information about a network using commands scripted in its own language.
The following screenshot is of Nessus displaying a scan report:
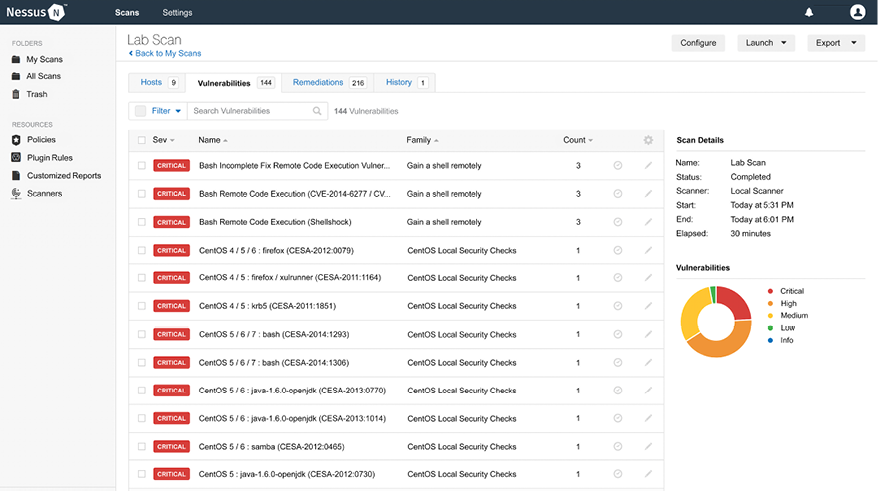
Figure 5.37: Nessus scan result
Wardriving
This is an internal reconnaissance technique used specifically for surveying wireless networks and is commonly done from an automobile. It is targeted mostly at unsecured WiFi networks. There are a few tools that have been made for the purpose of wardriving, and the two most common are NetStumbler and MiniStumbler. NetStumbler is Windows-based and it records the SSIDs of unsecured wireless networks before using GPS satellites to record the exact location of the wireless network. The data is used to create a map used by other wardrivers to find unsecured or inadequately secured wireless networks. They can then exploit the networks and their devices since the network is not secure.
MiniStumbler is a related tool but has been designed to run on tablets and smartphones. This makes wardrivers look less suspicious when identifying or exploiting a network. The functionality of the tool will simply find an unsecured network and record it in an online database. Wardrivers can then later exploit the network using a simplified map of all the identified networks. As for Linux, there is a tool called Kismet that can be used for wardriving. The tool is said to be very powerful as it lists unsecured networks and details of the clients on networks such as BSSIDs, signal levels, and IP addresses. It can also list the identified networks on maps, allowing attackers to come back and attack the network using the known information. Primarily, the tool sniffs the 802.11 layer 2 traffic of a WiFi network and uses any WiFi adapter on the machine it has been installed on.
The screenshot below displays a wardriving result that has been produced with Kismet.
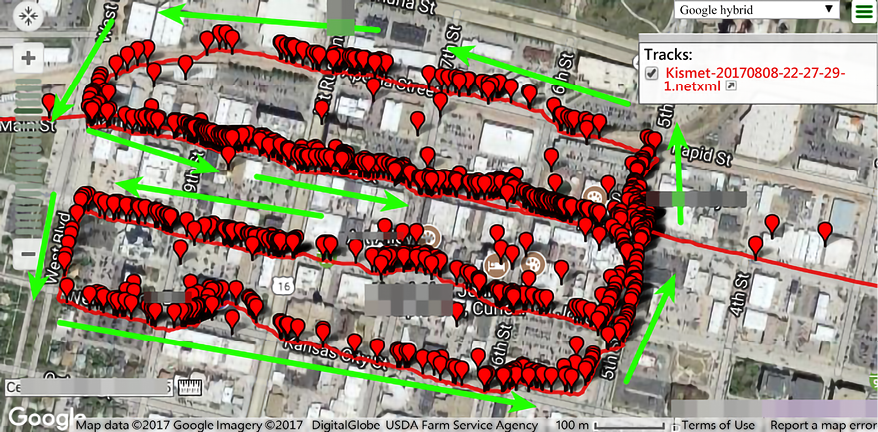
Figure 5.38: Collecting information via wardriving
Hak5 Plunder Bug
This tool is meant to specifically help hackers intercept CCTV camera footage in networks. There are many cameras that connect to networks using PoE (Power over Ethernet) connections. This allows them to get powered by the same cable that gives them network access. However, LAN connections expose the footage captured to the threat of being intercepted. The Hak5 Plunder Bug is a physical device that connects to Ethernet cables allowing hackers to intercept security camera footage. The device has a USB port that connects to computers or phones. In addition to this, the box has two Ethernet ports to allow traffic to pass directly through it. The device should be connected between the router and the computer used to monitor the CCTV footage. This allows the device to intercept communication from the CCTV camera flowing to the computer that has been configured to receive the footage. To make the best use of the device, a hacker needs Wireshark. Wireshark will capture traffic flowing through the box and identify continuous streams of JPG images, which is the norm with many CCTV cameras. Wireshark can isolate and export all the JPG files that it has captured. These can be saved and the hacker can simply view the images intercepted on the network. Other than intercepting traffic, a hacker can use this box together with other tools to manipulate the traffic flow from the CCTV camera. It is possible for the hacker to capture enough frames, block the new stream of images from the CCTV, and inject a looped stream of the captured image frames into the network. The computer monitoring the footage will show the looped stream and will not be able to access live images from the CCTV. Lastly, the hacker can just block all streams of images from the CCTV cameras from reaching the monitoring device, hence blinding the computer that monitors the live footage.
While this tool is powerful for internal reconnaissance, it can be quite challenging to use. This is because, unlike WiFi, Ethernet transmits data directly to the destination device. This means that after the footage from the CCTV camera has been routed by a router through a certain cable, the Plunder Bug needs to be placed exactly on this cable to be able to intercept footage just before it reaches the destination. The tool uses Ethernet ports, which means that the hacker will have to find a way of connecting the cable from the router to the box and another cable from the box to the destination computer. This whole process might prove to be complex and it is possible that anyone attempting to do it might be identified.
Figure 5.39: Photo of an Hak5 Plunder Bug
You can visit the website to see what else they have in their online shop: https://shop.hak5.org/.
CATT
There has been concern over the weak security controls in many IoT devices. Chromecasts, like many other IoT devices, are controllable by any user in the same network. This implies that if a hacker gets into a network with Chromecasts, they can play their own media files on the connected screens. CATT (Cast All The Things) is a Python program meant to help hackers interface with Chromecasts and send them commands. These commands tend to be more powerful than those issued using the normal Chromecast interface. One can write scripts that can instruct Chromecast to repeatedly play a certain video, play a video from a remote device, and even alter subtitles to play text files from the hacker. CATT also gives hackers a means of sending messages to a Chromecast user or disrupting what they are watching. CATT does not require the user to know where a Chromecast device is. This is because it can automatically scan and find all the Chromecast devices on a certain network.
Once a device has been discovered, CATT can cast the following:
- Video clips from video streaming sites such as YouTube among many others
- Any website
- Video clips from a local device
- Subtitles from any
.srtfile
Other commands that come with the tool include:
- Viewing the status of a Chromecast
- Pausing any playing video
- Rewinding through a video
- Skipping videos in a queue
- Adjusting the volume
- Stopping any playing video clip
Therefore, CATT is useful as a reconnaissance tool to scan Chromecasts. It also comes with functionalities that one can use to subtly exploit any Chromecast device.
Visit GitHub at https://github.com/skorokithakis/catt to download the tool.
Canary token links
These are links that can track anyone that clicks on them. The link can notify a hacker when the link has been shared and the platforms on which it has been shared. To generate a token, one has to visit the site http://canarytokens.com/generate and select the type of token they want. The available tokens include:
- Web URLs – a tracked URL
- DNS – tracks when a lookup has been done for a certain site
- Email addresses – a tracked email address
- Images – a tracked image
- PDF documents – a tracked PDF document
- Word documents – a tracked word document
- Cloned sites – a tracked clone site of an official site
Once a token has been generated, you have to provide an email address to receive notifications when an event occurs on the tokens, for instance, when a link is clicked. In addition to this, you are given a link to view the incidents list. Since most hackers will tend to use URL links, the following is the information they receive once someone has clicked on them:
- The city they have clicked from
- The browser used
- The IP address
- Information on whether the user is using an exit node (a Tor browser)
- The computing device they are using
- The OS they are using
Canary links are powerful since they can even detect instances where a link is shared on a social media platform and a snippet of it is created. For instance, if a URL is pasted on Skype, the platform will get a preview of the actual web page. By doing so, it makes a connection through the tracked link and canary will record it. Therefore, it is possible for one to know that their link is being shared on social media if they get pings from social media companies.
Passive vs. active reconnaissance
While there are two different types of reconnaissance (internal and external) there are also two different ways a threat actor may approach reconnaissance—by actively engaging with a target/system themselves (active reconnaissance), or by passively allowing tools to gather intel about a target (passive reconnaissance).
Active reconnaissance entails a situation where the hacker directly interacts with the system. The hackers use such tools as automated scanners, manually testing the system, and other tools such as Netcat and ping. The aim of the active reconnaissance process is to obtain information about the system used by an organization. Active recon is known to be faster and more accurate compared to passive recon. However, it is also known to be much riskier for the hacker compared to the passive category as it tends to make more noise within the system, significantly increasing the chances of the hacker being detected within the system.
On the other hand, passive reconnaissance is a process of gathering information about a system that uses indirect means that involve employing tools such as Shodan and Wireshark. Methods used with passive recon include such methods as OS fingerprinting to obtain information about that particular system.
How to combat reconnaissance
Stopping the success of the attacker during the reconnaissance stage is crucial to stopping attacks before they develop further. If an attacker does not gain access to critical details about a system, they will end up using either trial and error methods or basing their plans on guesswork. For major attacks, such as advanced persistent attacks that cost huge sums of money to plan, the attackers cannot afford to use uncertain information to make major plans that may end up costing them a lot of money in the end. Therefore, thwarting attacker efforts at the beginning will help to either delay the attacks happening or stop the attacks altogether.
The best way to combat the successful completion of reconnaissance by attackers is to completely understand your network as an organization. You need to know details such as:
- All the technologies that are used in the system and the network
- Any possible cracks within the system
The best way to obtain all this information is for the system to have a log collection point where messages about logs and activities in the system are centrally collected. Information about the network hardware should also be collected. The available options and tools to help you achieve this include:
- Using the Graylog tool: With the Graylog tool, you will have a visual of all network communications within the system and how the network communications have been done. The information is obtained from the log files, which will reveal all the network connections that were rejected and those that were established.
- The hiring of a red team: This is the hiring of a team to perform ethical hacking of your system. The red team results will help you identify the vulnerability in the system infrastructure. If the red team is successful in gaining access to the system, then they will be able to pinpoint the areas they exploited to gain entry as well as other areas they would recommend need additional protection.
How to prevent reconnaissance
The process of reconnaissance is the first stage of an attack that hackers will use to determine what kind of effort or tools they will need to access the system. A successful reconnaissance stage allows the hackers to effectively plan their attacks. Without the information the hackers obtain at this stage, it will force them to use trial and error methods, which will greatly increase their noise within the system or increase their chances of triggering alerts of the security systems in place to keep out attackers. Therefore, it is critical for an organization to find ways to prevent hackers from successfully carrying out reconnaissance procedures and determining essential details about the system that can help them better prepare to attack it.
Penetration testing is the solution that organizations can use to determine what an attacker can determine about the system during reconnaissance. Penetration testing is an ethical hacking procedure that is carried out by the security team to determine loopholes in the system such as open ports and other vulnerabilities that an attacker can then take advantage of to gain entry into the system. During the penetration testing exercise, the security team utilizes port scanning tools that are capable of scanning large networks to determine all hosts related to the network, the ones that are up and the ones that are not. Other tools that can be used at this stage include vulnerability scanners that are designed to scan and identify any vulnerability in the system that is likely to be exploited by potential attackers. Additional tools include SIEM solutions, which help in detecting the source IP addresses that are active in a network and are running scanning tools at that given time. If you find that external IP addresses are running scanning tools on the network, then attackers are trying to collect information about the system in preparation for a potential attack.
Summary
The reconnaissance stage of a cyber attack is a key determinant of the overall attack process. At this stage, hackers are normally seeking to find a lot of information about their targets. This information is used in the later stages of the attack process. There are two types of reconnaissance, external and internal. External reconnaissance, also referred to as external footprinting, involves finding as much information as possible about a target while outside its network.
The new tools used here include Webshag, FOCA, PhoneInfoga, and theHarvester. Internal reconnaissance, also referred to as post-exploitation reconnaissance, involves finding more information about a target within their network. Some of the new tools used include Airgraph-ng, Hak5 Plunder Bug, CATT, and canary token links. It is noteworthy that some of these tools have additional functionalities that go beyond doing basic scans. Internal reconnaissance tools will mostly yield richer information about a target. However, it is not always feasible for a hacker to be within a target’s network. Therefore, most attacks will begin with external footprinting and then proceed to internal reconnaissance. The information obtained in both types of reconnaissance helps the attacker to plan for a more effective breach and exploitation of the target’s network and systems. In the next chapter, we will discuss current trends in strategies to compromise systems and explain how to compromise a system.
References
- M. de Paula, One Man’s Trash Is... Dumpster-diving for disk drives raises eyebrows, U.S. Banker, vol. 114, (6), pp. 12, 2004. Available: https://search.proquest.com/docview/200721625.
- J. Brodkin, Google crushes, shreds old hard drives to prevent data leakage, Network World, 2017. [Online]. Available: http://www.networkworld.com/article/2202487/data-center/google-crushes--shreds-old-hard-drives-to-prevent-data-leakage.html. [Accessed: 19- Jul- 2017].
- Brandom, Russian hackers targeted Pentagon workers with malware-laced Twitter messages, The Verge, 2017. [Online]. Available: https://www.theverge.com/2017/5/18/15658300/russia-hacking-twitter-bots-pentagon-putin-election. [Accessed: 19- Jul- 2017].
- A. Swanson, Identity Theft, Line One, Collector, vol. 73, (12), pp. 18-22, 24-26, 2008. Available: https://search.proquest.com/docview/223219430.
- P. Gupta and R. Mata-Toledo, Cybercrime: in disguise crimes, Journal of Information Systems & Operations Management, pp. 1-10, 2016. Available: https://search.proquest.com/docview/1800153259.
- S. Gold, Social engineering today: psychology, strategies and tricks, Network Security, vol. 2010, (11), pp. 11-14, 2010. Available: https://search.proquest.com/docview/787399306?accountid=45049. DOI: http://dx.doi.org/10.1016/S1353-4858(10)70135-5.
- T. Anderson, Pretexting: What You Need to Know, Secur. Manage., vol. 54, (6), pp. 64, 2010. Available: https://search.proquest.com/docview/504743883.
- B. Harrison, E. Svetieva, and A. Vishwanath, Individual processing of phishing emails, Online Information Review, vol. 40, (2), pp. 265-281, 2016. Available: https://search.proquest.com/docview/1776786039.
- Top 10 Phishing Attacks of 2014 - PhishMe, PhishMe, 2017. [Online]. Available: https://phishme.com/top-10-phishing-attacks-2014/. [Accessed: 19- Jul- 2017].
- W. Amir, Hackers Target Users with ‘Yahoo Account Confirmation’ Phishing Email, HackRead, 2016. [Online]. Available: https://www.hackread.com/hackers-target-users-with-yahoo-account-confirmation-phishing-email/. [Accessed: 08- Aug- 2017].
- E. C. Dooley, Calling scam hits locally: Known as vishing, scheme tricks people into giving personal data over phone, McClatchy - Tribune Business News, 2008. Available: https://search.proquest.com/docview/464531113.
- M. Hamizi, Social engineering and insider threats, Slideshare.net, 2017. [Online]. Available: https://www.slideshare.net/pdawackomct/7-social-engineering-and-insider-threats. [Accessed: 08- Aug- 2017].
- M. Hypponen, Enlisting for the war on Internet fraud, CIO Canada, vol. 14, (10), pp. 1, 2006. Available: https://search.proquest.com/docview/217426610.
- R. Duey, Energy Industry a Prime Target for Cyber Evildoers, Refinery Tracker, vol. 6, (4), pp. 1-2, 2014. Available: https://search.proquest.com/docview/1530210690.
- Joshua J.S. Chang, An analysis of advance fee fraud on the internet, Journal of Financial Crime, vol. 15, (1), pp. 71-81, 2008. Available: https://search.proquest.com/docview/235986237?accountid=45049. DOI: http://dx.doi.org/10.1108/13590790810841716.
- Packet sniffers - SecTools Top Network Security Tools, Sectools.org, 2017. [Online]. Available: http://sectools.org/tag/sniffers/. [Accessed: 19- Jul- 2017].
- C. Constantakis, Securing Access in Network Operations - Emerging Tools for Simplifying a Carrier’s Network Security Administration, Information Systems Security, vol. 16, (1), pp. 42-46, 2007. Available: https://search.proquest.com/docview/229620046.
- C. Peikari and S. Fogie, Maximum Wireless Security, Flylib.com, 2017. [Online]. Available: http://flylib.com/books/en/4.234.1.86/1/. [Accessed: 08- Aug- 2017].
- Nmap: the Network Mapper - Free Security Scanner, Nmap.org, 2017. [Online]. Available: https://nmap.org/. [Accessed: 20- Jul- 2017].
- Using Wireshark to Analyze a Packet Capture File, Samsclass.info, 2017. [Online]. Available: https://samsclass.info/106/proj13/p3_Wireshark_pcap_file.htm. [Accessed: 08- Aug- 2017].
- Secureworks Counter Threat Unit’s Threat Intelligence Research: https://www.secureworks.com/research
- Nessus 5 on Ubuntu 12.04 install and mini review, Hacker Target, 2017. [Online]. Available: https://hackertarget.com/nessus-5-on-ubuntu-12-04-install-and-mini-review/. [Accessed: 08- Aug- 2017].
- Metasploit Unleashed, Offensive-security.com, 2017. [Online]. Available: https://www.offensive-security.com/metasploit-unleashed/msfvenom/]. [Accessed: 21- Jul- 2017].
- Hacking in a nutshell: https://www.youtube.com/c/erdalozkaya
Join our community on Discord
Join our community’s Discord space for discussions with the author and other readers:

