16
Vulnerability Management
In the previous chapters, you learned about the recovery process and how important it is to have a good recovery strategy and the appropriate tools in place. Oftentimes, the exploitation of a vulnerability might lead to a disaster recovery scenario. Therefore, it is imperative to have a system in place that can prevent the vulnerabilities from being exploited in the first place. But how can you prevent a vulnerability from being exploited if you don’t know whether your system is vulnerable? The answer is to have a vulnerability management process in place that can be used to identify vulnerabilities and help you mitigate them. This chapter focuses on the mechanisms that organizations and individuals need to put in place to make it hard to be hacked. It might be impossible for a system to be 100% safe and secure; however, there are some measures that can be employed to make it difficult for hackers to complete their missions.
This chapter will cover the following topics:
- Creating a vulnerability management strategy
- Elements of a vulnerability strategy
- Differences between vulnerability management and vulnerability assessment
- Best practices for vulnerability management
- Vulnerability management tools
We’ll begin with strategy creation.
Creating a vulnerability management strategy
To have a healthy security program and reduce organizational risk, it’s important for organizations to effectively identify, assess, and remediate weaknesses. Vulnerability management aims to reduce organizational exposure, harden attack surface areas, and increase organizational resilience.
The optimal approach to creating an effective vulnerability management strategy is to use a vulnerability management life cycle. Just like the attack life cycle, the vulnerability management life cycle schedules all vulnerability mitigation processes in an orderly way.
This enables targets and victims of cybersecurity incidents to mitigate the damage that they have incurred or might incur. The right counteractions are scheduled to be performed at the right time to find and address vulnerabilities before attackers can abuse them.
The vulnerability management strategy is composed of six distinct phases. This section will discuss each of them and what they are meant to protect against. It will also discuss the challenges that are expected to be met at each of those stages.

Figure 16.1: The six stages of a vulnerability management strategy
We begin with the asset inventory stage.
Asset inventory
The first stage in the vulnerability management strategy should be the making of an inventory. An asset inventory serves as a register of all the hosts in a network and also of the software contained in them. It should, at the very least, show the hardware and software assets owned by an organization and their relevant license details. As an optional addition, the inventory should also show the vulnerabilities present in any of these assets.
Many organizations lack an effective asset register and, therefore, have a hard time when securing their devices. An up-to-date asset inventory will come in handy when the organization has to respond to vulnerabilities with fixes to all its assets, as security administrators can use it to go through the devices an organization has and highlight the ones that need to be covered by security software.
An organization should start by giving one employee the responsibility of managing an asset inventory to ensure that all devices are recorded and that the inventory remains up to date. The asset inventory is also a great tool that network and system admins can use to quickly find and patch devices and systems.
Without the inventory, some devices could be left behind when new security software is being patched or installed. These are the devices and systems that attackers will target. There are hacking tools that can scan the network and find out which systems are unpatched, as we saw in Chapter 6, Compromising the System.
The lack of an asset inventory may also lead to the organization underspending or overspending on security. This is because it cannot correctly determine the devices and systems that it needs to purchase protection for. The challenges that are expected at this stage are many. IT departments in today’s organizations are often faced with poor change management, rogue servers, and a lack of clear network boundaries. Organizations also lack effective tools for maintaining the inventory in a consistent manner.
Tools like the Comodo Dragon platform can be used for asset management as well, as per the screenshot below:
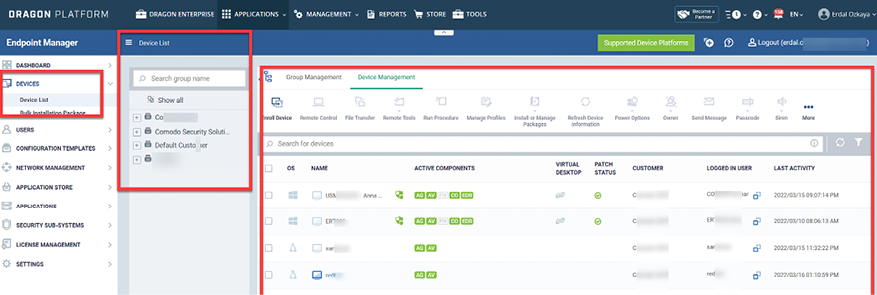
Figure 16.2: You can use many different commercial tools to manage your assets
Information management
The second stage in the vulnerability management strategy is controlling how information flows into an organization. The most critical information flow is internet traffic coming from an organization’s network. There has been an increase in the number of worms, viruses, and other malware threats that organizations need to guard against. There has also been an increase in traffic flow both inside and outside of local networks. The increased traffic flow threatens to bring more malware into an organization. Therefore, attention should be paid to this information flow to prevent threats from getting in or out of a network.
The goal should be the setting up of an effective way to get information about vulnerabilities and cybersecurity incidents to the relevant people within the shortest time possible. At the end of this stage, there should be an elaborate communication channel between incident responders and other users when there has been a breach of systems.
Other than the threat of malware, information management is also concerned with the organization’s data. Figure 16.3 below displays one of many tools that can help you to view network traffic:
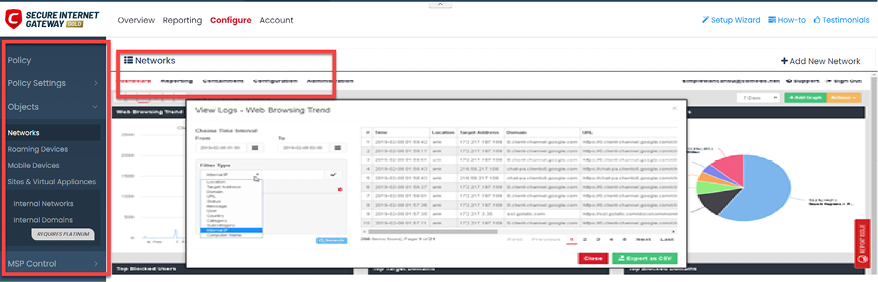
Figure 16.3: Monitoring internet traffic via Comodo Secure Internet Gateway
Organizations store different types of data, and some of it must never get into the hands of the wrong people. Information, such as trade secrets and the personal information of customers, could cause irreparable damage if it is accessed by hackers. An organization may lose its reputation, and could also be fined huge sums of money for failing to protect user data. Competing organizations could get secret formulas, prototypes, and business secrets, allowing them to outshine the victim organization. Therefore, information management is vital in the vulnerability management strategy.
In order to achieve this, an organization could deploy a computer security incident response team (CSIRT) to handle any threats to its information storage and transmission. This team will not just respond to hacking incidents but will also inform management when there are intrusion attempts to access sensitive information and the best course of action to take.
Apart from this team, an organization could adopt the policy of least privilege when it comes to accessing information. This policy ensures that users are denied access to all information apart from that which is necessary for them to perform their duties. Reducing the number of people accessing sensitive information is a good measure toward reducing the avenues of attack.
Lastly, in the information management strategy, organizations could put in place mechanisms to detect and stop malicious people from gaining access to files. These mechanisms can be put in place in the network to ensure that malicious traffic is denied entry and suspicious activities such as snooping are reported. They could also be put in place on end user devices to prevent the illegal copying or reading of data.
There are a few challenges in this step of the vulnerability management strategy. To begin with, over the years, information has grown in breadth and depth, making it hard to handle and also control who can access it. Valuable information about potential hackings, such as alerts, has also exceeded the processing capabilities of most IT departments. It is not a surprise for legitimate alerts to be brushed off as false positives because of the number of similar alerts that the IT department receives daily.
There have been incidents where organizations have been exploited shortly after ignoring alerts from network monitoring tools. The IT department is not entirely to blame as there is a huge amount of new information that such tools are generating per hour, most of which turn out to be false positives. Traffic flowing in and out of organizational networks has also become complex. Malware is being transmitted in nonconventional ways. There is also a challenge when it comes to conveying information about new vulnerabilities to normal users who do not understand technical IT jargon. All these challenges together affect the response times and actions that an organization can take in the case of potential or verified hacking attempts.
Risk assessment
This is the third step in the vulnerability management strategy. Before risks can be mitigated, the security team should do an in-depth analysis of the threats and vulnerabilities that it faces (Figure 16.4). In an ideal IT environment, the security team would be able to respond to all vulnerabilities since it would have sufficient resources and time. However, in reality, there are a great many limiting factors when it comes to the resources available to mitigate risks. That is why risk assessment is crucial. In this step, an organization has to prioritize some vulnerabilities over others and allocate resources to mitigate against them.
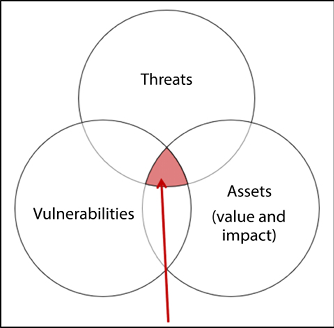
Figure 16.4: Risks can be found by assessing threats and vulnerabilities
ISO 27001, clause 4.2.1, and ISO 27005, clause 7.4, set up the main objectives of the selection process of the approach to, and the methodology for, risk assessment. In the figure below (Figure 16.5), ISO recommends selecting and defining an approach to risk assessment that is aligned with the management of the organization and with a methodology that fits the organization.
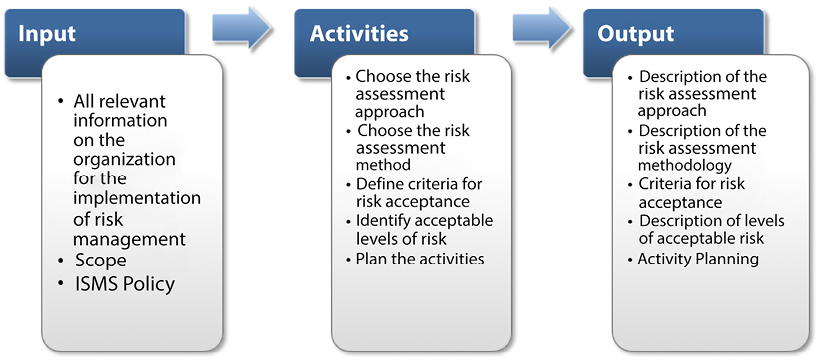
Figure 16.5: ISO risk assessment methodology
Risk assessment is comprised of six sub-stages:
- Scope
- Collecting data
- Analysis of policy and procedures
- Vulnerability analysis
- Threat analysis
- Analysis of acceptable risks

Figure 16.6: The six stages of risk assessment
We will cover each of these six sub-stages in the following subsections.
Scope
Risk assessment starts with scope identification. An organization’s security team only has a limited budget. It, therefore, has to identify the areas that it will cover and those that it will not. It determines what will be protected, its sensitivity, and to what level it needs to be protected.
The scope needs to be defined carefully since it will determine where internal and external vulnerability analyses will occur.
Collecting data
After the scope has been defined, data needs to be collected about the existing policies and procedures that are in place to safeguard the organization from cyber threats. This can be done through interviews, questionnaires, and surveys administered to personnel, such as users and network administrators. All the networks, applications, and systems that are covered in the scope should have their relevant data collected. This data could include the following: service packs, OS versions, applications running, locations, access control permissions, intrusion-detection tests, firewall tests, network surveys, and port scans. This information will shed more light on the type of threats that the networks, systems, and applications are facing.
Analysis of policies and procedures
Organizations set up policies and procedures to govern the usage of their resources. They ensure that they are put to rightful and safe use. It is, therefore, important to review and analyze the existing policies and procedures. There could be inadequacies in the policies. There could also be impracticalities in some policies. While analyzing the policies and procedures, one should also determine the level of compliance on the part of the users and administrators. Just because the policies and procedures are formulated and disseminated does not mean that they are complied with. The punishments set for noncompliance should also be analyzed. In the end, it will be known whether an organization has sufficient policies and procedures to address vulnerabilities.
Vulnerability analysis
After the analysis of the policies and procedures, vulnerability analysis must be done in order to determine the exposure of the organization and to find out whether it has enough safeguards to protect itself. Vulnerability analysis is done using the tools that were discussed in Chapter 5, Reconnaissance. The tools used here are the same tools that hackers use to determine an organization’s vulnerabilities so that they can decide which exploits to use. Commonly, organizations will call in penetration testers to conduct this process. The biggest setback in vulnerability analysis is the number of false positives that are identified that need to be filtered out. Therefore, various tools have to be used together in order to come up with a reliable list of the existing vulnerabilities in an organization.
The penetration testers need to simulate real attacks and find the systems and devices that suffer stress and get compromised in the process. At the end of this, the vulnerabilities identified are graded according to the risks that they pose to the organization.
Vulnerabilities that have less severity and exposure usually have low ratings. There are three classes in a vulnerability grading system. The minor class is for vulnerabilities that require lots of resources to exploit, yet have very little impact on the organization. The moderate class is for those vulnerabilities that have moderate potential for damage, exploitability, and exposure. The high-severity class is for vulnerabilities that require fewer resources to exploit but can do lots of damage to an organization if they are exploited.
Threat analysis
Threats to an organization are actions, code, or software that could lead to the tampering, destruction, or interruption of data and services in an organization. Threat analysis is done to look at the risks that could happen in an organization. The threats identified must be analyzed in order to determine their effects on an organization. Threats are graded in a similar manner to vulnerabilities but are measured in terms of motivation and capability. For instance, an insider may have low motivation to maliciously attack an organization but could have lots of capabilities because of their inside knowledge of the workings of the organization. Therefore, the grading system may have some differences to the one used in the vulnerability analysis. In the end, the threats identified are quantified and graded.
Below, you will see an example from ISO 27001, which shows the relationship between assets, vulnerabilities, and threats:

Figure 16.7: Relationship between assets, vulnerabilities, and threats
Analysis of acceptable risks
An analysis of the acceptable risks is the last thing done in risk assessment. Here, the existing policies, procedures, and security mechanisms are first assessed to determine whether they are adequate. If they are inadequate, it is assumed that there are vulnerabilities in the organization. Corrective actions are taken to ensure that they are updated and upgraded until they are sufficient. Therefore, the IT department will determine the recommended standards that the safeguards should meet. Whatever is not covered is categorized as an acceptable risk. These risks might, however, become more harmful with time; therefore, they have to be analyzed. It is only after it is determined that they will pose no threat that the risk assessment will end.
If they might pose a threat, safeguard standards are updated to address them.
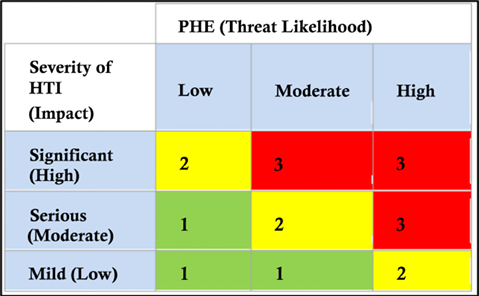
Figure 16.8: Sample risk matrix
The biggest challenge in this stage is the lack of availability of information. Some organizations do not document their policies, procedures, strategies, processes, and security assets. It might, therefore, be difficult to obtain the information needed in order to complete this stage. It might be easier for small- and medium-sized companies to keep documentation of everything, but it is a complex task for big companies. Big companies have multiple lines of business, departments, a lack of enough resources, a lack of disciplined documentation, and overlapping duties. The only solution to ready them for this process is by conducting regular housekeeping activities to ensure that everything important is documented and that staff clearly understand their duties.
This sub-stage marks the end of the risk assessment phase of the vulnerability management strategy.
Vulnerability assessment
Vulnerability assessment closely follows risk assessment in the vulnerability management strategy. This is because the two phases are closely related. Vulnerability assessment involves the identification of vulnerable assets. This phase is conducted through a number of ethical hacking attempts and penetration tests. The servers, printers, workstations, firewalls, routers, and switches on the organizational network are all targeted by these attacks. The aim is to simulate a real hacking scenario with the same tools and techniques that a potential attacker might use. The majority of these tools were discussed in Chapter 5, Reconnaissance, and Chapter 6, Compromising the System. The goal of this step is not only to identify vulnerabilities but also to do so in a fast and accurate manner. The step should yield a comprehensive report of all the vulnerabilities that an organization is exposed to.
The challenges faced in this step are many. The first one to consider should concern what the organization should assess. If the asset inventory step was not completed well, an organization will not be able to identify which devices they should focus on. It will also become easy to forget to assess certain hosts, and yet they may be key targets for a potential attack. Another challenge has to do with the vulnerability scanners used. Some scanners provide false assessment reports and guide the organization down the wrong path. Of course, false positives will always exist, but some scanning tools exceed the acceptable percentage and keep on coming up with nonexistent vulnerabilities.
These may lead to the wasting of the organization’s resources when it comes to mitigations. Disruptions are another set of challenges that are experienced at this stage. With all the ethical hacking and penetration-testing activities going on, the networks, servers, and workstations suffer. Networking equipment such as firewalls also gets sluggish, especially when denial of service attacks are being carried out.
Sometimes, strong attacks will actually bring down servers, disrupting the core functions of an organization. This can be addressed by conducting these tests when there are no users using them, or by coming up with replacements when core tools are being assessed. There is also the challenge of using the tools themselves. Tools such as Metasploit require you to have a solid understanding of Linux and be experienced with using command-line interfaces. The same is true for many other scanning tools. It is difficult to find scanning tools that offer a good interface and, at the same time, offer the flexibility of writing custom scripts. Lastly, sometimes scanning tools do not come with a decent reporting feature, and this forces the penetration testers to manually write these reports. Their reports may not be as thorough as those that would have been generated directly by the scanning tools.
There are a variety of different vulnerability assessments that can be done in an organization, including:
- External assessments: these identify vulnerabilities from the outside inward
- Internal assessments: these identify vulnerabilities within a network
- Social engineering: this is used to identify training gaps and vulnerabilities in human resources
- Wireless assessments: these are conducted to identify vulnerabilities within wireless networks
- Physical security assessments: these identify vulnerabilities related to people and facilities
- Application and database: this identifies software vulnerabilities
The scope of this book does not allow us to cover these in much detail, but knowing the different types of vulnerability assessments can help to build your scope in Red Teaming better.
Reporting and remediation tracking
After the vulnerability assessment comes the reporting and remediation stage. This phase has two equally important tasks: reporting and remediation. The task of reporting helps the system admins to understand the organization’s current state of security and the areas in which it is still insecure, and it points these out to the person responsible. All the risks and vulnerabilities identified must be reported back to the stakeholders of the organization. The reports should be comprehensive and touch on all hardware and software assets belonging to the organization. The reports should also be fine-tuned to meet the needs of various audiences. There are audiences that might not understand the technical side of vulnerabilities, and it is, therefore, only fair that they get a simplified version of the reports. Reporting also gives something tangible to the management so that they can associate it with the future direction of the organization. Reporting normally comes before remediation so that all the information compiled in the vulnerability management phase can seamlessly flow to this phase.
Remediation starts the actual process of ending the cycle of vulnerability management. The vulnerability assessment phase, as was discussed, comes to an end after analyzing the threats and vulnerabilities as well as outlining the acceptable risks.
Remediation complements this by coming up with solutions to the threats and vulnerabilities identified. After the risks and vulnerabilities that the organization faces have been identified, the appropriate people to remedy them should be stated. They should be assigned the responsibility for ensuring that all the risks and vulnerabilities are resolved in totality.
There should be an elaborate way of tracking the progress of the resolution of the identified threats. All the vulnerable hosts, servers, and networking equipment should be tracked down and the necessary steps should be established to remove the vulnerabilities and protect them from future exploits. This is the most important task in the vulnerability management strategy, and if it is well executed, the vulnerability management is deemed to be a success. Activities in this task include identifying missing patches and checking for available upgrades to all systems in an organization. Solutions are also identified for the bugs that were picked up by scanning tools. Multiple layers of security, such as antivirus programs and firewalls, are also identified at this stage. If this phase is unsuccessful, it makes the whole vulnerability management process pointless.
As expected, this phase sees a coming together of a great many challenges since it is the phase where all vulnerabilities have their solutions identified. The first challenge arises when reporting is partial and does not contain all the required information about the risks that the organization faces. A poorly written report may lead to poor remediation measures and, thus, leave the organization still exposed to threats. The lack of software documentation may also bring about challenges in this phase. The vendors or manufacturers of software often leave documentation that includes an explanation of how updating is to be done.
Without it, it may prove hard to update bespoke software. Poor communication between software vendors and the organization may also bring about challenges when the patching of a system needs to be done. Lastly, remediation can be compromised by a lack of cooperation from end users. Remediation may introduce downtimes to end users, something that they never want to experience.
Response planning
Response planning can be thought of as the easiest, but nevertheless a very important, step in the vulnerability management strategy. It is easy because all the hard work will have been done in the previous five steps. It is important because, without its execution, the organization will still be exposed to threats.
In response planning, the organization should come up with a means of patching, updating, or upgrading the systems that were identified as possessing some risks or vulnerabilities. The hierarchy of severity identified in the risk and vulnerability assessment steps should be followed. This step should be implemented with the aid of the asset inventory so that the organization can confirm that all its assets, both hardware and software, have been attended to. However, by far the most important thing in this phase is the speed of execution. Large organizations face major hurdles when it comes to executing it because of the large number of devices that require patches and upgrades.
An incident happened when Microsoft announced the existence of the MS03-023 and released a patch for it. Smaller organizations that have short response plans were able to patch their operating systems with an update shortly after the announcement.
However, larger organizations (which either lacked or had long response plans for their computers) were heavily attacked by hackers. Hackers released the MS Blaster worm to attack the unpatched operating systems barely 26 days after Microsoft gave a working patch to its users. That should have been enough time for even big companies to patch their systems in totality. However, the lack of response plans or the use of long response plans caused some to fall victim to the worm. The worm caused network sluggishness or outages on the computers it infected.
Another famous incident that happened quite recently was that of the WannaCry ransomware. It is the largest ever ransomware attack in history caused by a vulnerability allegedly stolen from the NSA called EternalBlue. The attack started in May 2017, but Microsoft released a patch for the EternalBlue vulnerability in March. However, it did not release a patch for older versions of Windows, such as XP. From March until the day the first attack was recognized, there was enough time for companies to patch their systems. However, most companies had not done so by the time the attack started because of poor response planning. If the attack had not been stopped, even more computers would have fallen victim.
This shows just how important speed is when it comes to response planning. Patches are to be installed the moment that they are made available.
The challenges faced in this phase are many since it involves the actual engagement of end users and their machines. The first of these challenges is getting the appropriate communications out to the right people in time. When a patch is released, hackers are never slow in trying to find ways to compromise the organizations that do not install it. That is why a well-established communication chain is important.
Another challenge is accountability. The organization needs to know who to hold accountable for not installing patches. At times, users may be responsible for canceling installations. In other instances, it may be the IT team that did not initiate the patching process in time. There should always be an individual that can be held accountable for not installing patches.
The last challenge is the duplication of efforts. This normally occurs in large organizations where there are many IT security personnel. They may use the same response plan, but because of poor communication, they may end up duplicating each other’s efforts while making very little progress.
Elements of a vulnerability strategy
There are several elements that have to work in unison and that are integral to the success of your vulnerability management system. These elements include:
- People: The team working on the security issues and the employees involved in the processes and plans should have extensive knowledge and expertise on matters dealing with vulnerabilities. In addition, they need to have great communication abilities that can help them coordinate with all other business people that may be affected by the security issues they may uncover, as well as the processes they will set up to address the identified issues.
- Process: The process of conducting assessments can be done by anyone. However, for value addition, the process needs to have additional features such as a setup that will allow for follow-ups on the assessment data and that can make the data usable. The process also needs to be precise and reproducible to allow other people to repeat the process as well.
- Technology: The technology being used by security experts plays a huge role in how effective the vulnerability management system will be. The technology should be simple enough to help in carrying out effective scans and to enable additional features such as creating asset databases and creating ticketing systems whenever an issue is raised with the system. This will enable easier recording of issues and make follow-ups more effective.
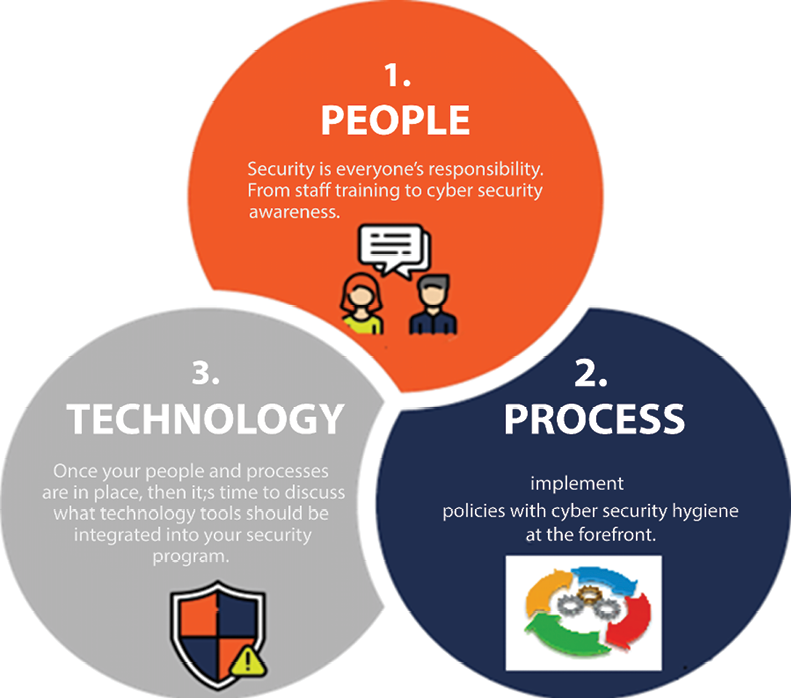
Figure 16.9: People, process, and technology
Differences between vulnerability management and vulnerability assessment
The term vulnerability management can often be confused with vulnerability assessment. The discussion of vulnerability management is not possible without mentioning vulnerability assessment repeatedly. Vulnerability assessment is a subset of vulnerability management. However, there are clear differences between the two, and they will be highlighted in detail in this section:
- As already mentioned, vulnerability assessment is a subset of vulnerability management. In the pursuit of effective vulnerability management, vulnerability assessment helps organizations determine the weaknesses in the system before they can come up with a comprehensive vulnerability management plan to address the identified issues. Therefore, it starts with organizations assessing the system using experts such as external security consultants who are hired to specifically assess the system for vulnerabilities and the risks they present to the company.
- While vulnerability management is a many-faceted, continuous process, vulnerability assessment is a one-time project. The assessment has a fixed time period in which the security experts will scan the system to identify potential vulnerabilities. After a successful scan, the experts will be able to identify the weaknesses in the system. This marks the end of the vulnerability assessment phase of the exercise. Vulnerability management doesn’t stop here though. All the subsequent activities after the assessment has been done comprise vulnerability management.
- Apart from the process of assessment that has just been highlighted, vulnerability management also includes other processes such as the identification of vulnerabilities, treatment of the identified vulnerabilities, and the reporting of these vulnerabilities to the relevant stakeholders such as the executive branch of the business and cybersecurity experts in the industry, such as vendors who may use that information to upgrade their security products. The entire process of vulnerability management is more important than just assessment, which only helps identify the issue without providing treatment processes for the identified issues.
- Vulnerability assessment does not provide cures for the weaknesses in the system. It can only help by recommending solutions for the weaknesses. However, vulnerability management goes a step further by ensuring that the solutions are implemented and the security problem solved. Assessment does not help improve the system. It only helps in alerting you of the dangers that you face from the system.
Best practices for vulnerability management
Even with the best tools, execution is all that matters in vulnerability management. Therefore, all the actions that have been identified in the implementation section must be carried out flawlessly. There is a set of best practices for each step of the implementation of the vulnerability management strategy.
Starting with the asset inventory, the organization should establish a single point of authority. There should be one person that can be held responsible if the inventory is not up to date or has inconsistencies. Another best practice is to encourage the use of consistent abbreviations during data entry. It may become confusing to another person trying to go through the inventory if the abbreviations keep on changing.
The inventory should also be validated at least once a year. Lastly, it is advisable to treat changes in inventory management systems with the same degree of care as any other change in a management process.
In the information management stage, the biggest achievement that the organization can get is a fast and effective dissemination of information to the relevant audience. One of the best methods for doing this is allowing employees to make a conscious effort of subscribing to mailing lists. Another one is to allow the incident response team to post its own reports, statistics, and advice on a website for the organization’s users. The organization should also hold periodic conferences to discuss new vulnerabilities, virus strains, malicious activities, and social engineering techniques with users. It is best if all the users are informed about the threats that they may face and how to deal with them effectively. This has more impact than mailing lists telling them to do technical things that they are not knowledgeable of. Lastly, the organization should come up with a standardized template of how all the security-related emails will look. It should be a consistent look that is different from the normal email format that users are used to.
The risk assessment step is one of the most manually demanding stages of the vulnerability management life cycle. This is because there are not many commercial tools that can be used here. One of the best practices is to document the ways to review new vulnerabilities as soon as they appear. This will save a lot of time when it comes to mitigating them since the appropriate countermeasures will already be known. Another best practice is to publish the risk ratings to the public or at least to the organizational users. That information may spread and ultimately reach a person that will find it more useful. It is also recommended that you ensure that asset inventories are both available and updated at this stage so that all hosts in a network can be combed through during risk analysis. The incident response team in every organization should also publish a matrix for each tool that the organization has deployed to secure itself. Lastly, the organization should ensure that it has a strict change management process that ensures that incoming staff are made aware of the security posture of the organization and the mechanisms in place to protect it.
The vulnerability assessment step is not so different from the risk assessment step; therefore, the two might borrow from each other’s best practices (which we discussed previously). In addition to what has been discussed in risk assessment, it is good practice to seek permission before extensively testing the network. This is because we saw that this step might introduce serious disruptions to an organization and might do actual damage to the hosts. Therefore, a lot of planning ahead needs to happen. Another best practice is to create custom policies for specific environments—that is, the different operating systems of the organization’s hosts. Lastly, the organization should identify the scanning tools that are best for its hosts. Some methods may be overkill where they do too much scanning and to an unnecessary depth. Other tools are too shallow and do not discover the vulnerabilities in a network.
There are a few tips that may be used in the reporting and remediation tracking stage. One of these is to ensure that there is a reliable tool for sending reports to asset owners concerning the vulnerabilities they had and whether they have been fixed completely. This reduces the number of unnecessary emails received from users whose machines were found to contain vulnerabilities. The IT staff should also meet with management and other stakeholders to find out the type of reports that they want to see. The level of technicality should also be agreed upon.
The incident response team should also agree with the management of the remediation time frames and the required resources, and make known the consequences of non-remediation. Lastly, remediation should be performed following the hierarchy of severity. Therefore, the vulnerabilities that pose the most risk should be sorted first.
The response planning step is the conclusion of the whole vulnerability management process. It is where the responses to different vulnerabilities are implemented. There are several best practices that can be used in this step. One of them is to ensure that the response plans are documented and well known by the incident response team and the normal users. There should also be fast and accurate information flow to the normal users concerning the progress of fixing the vulnerabilities identified. Since there is a chance of failure after machines are updated or patches are installed, contact information should be provided to the end users so that they can reach out to the IT team when such cases arise. Lastly, the incident response team should be given easy access to the network so that they can implement their fixes faster.
Strategies to improve vulnerability management
Vulnerability management is now a common thing among most organizations. A quick survey will reveal that most organizations actually have a vulnerability management system in place. The reason for this is simple: people recognize the importance of having one. The absence of a system has consequences that organizations would rather avoid.
While most organizations will boast of being security conscious and having some sort of vulnerability management system in place, cases of security breaches have also been on the increase. These cases affect even companies that have a vulnerability management system in place. Clearly, it is one thing to have a vulnerability management system in place and another for the system to work effectively to keep attackers at bay. Most of the breaches that occur in organizations that already have this system in place occur because of some ignored vulnerability or a yet-to-be-identified vulnerability. However, it is possible to significantly improve the quality of the vulnerability management at your organization using the following strategies meant to improve the vulnerability management strategy’s effectiveness:
- Making executive support the main priority: The executive branch of an organization is the one that makes strategic decisions as well as important decisions such as those related to finance. Issues such as risk management affect them directly and they are required to have a thorough understanding of the risks affecting their organization at any given time. Therefore, ensuring you have a vulnerability management system that can provide executives with an exhaustive report on all aspects of the organization at a glance means the system is effective. Therefore, the aim is to have a vulnerability management strategy that satisfies the executive branch of the organization. Such a system will undoubtedly be an effective one. The more concrete the report the system can generate for the use of the executive, the better it is.
- Ensure that you prioritize asset visibility: The aim is to ensure you have comprehensive asset visibility at any given time. Asset discovery is a major factor in vulnerability management. You cannot conduct vulnerability management without having the ability to check all the assets an organization has and to review their status.
Therefore, the vulnerability management program should be able to afford you the ability to check all assets linked to the organization to ensure the program covers them. The vulnerability management system should be able to conduct actions such as agentless scanning, agent-based scanning, endpoint scanning, scanning of BYOD devices, and cloud asset scanning. Additionally, the scanning should be done regularly to ensure that new vulnerabilities are identified on time and sorted out.
- Ensure that you align your scans with the remediation processes: Remediation exercises are the deliberate actions that you take to ensure that the identified vulnerabilities are solved. You should ensure that the scanning efforts and the remediation efforts align in such a way that they are done at the same frequency. For instance, if you scan your system once a week, the remediation should also be done once a week. If you scan every day but remediation is done weekly, then the two do not align and will not be effective. Scanning and identifying vulnerabilities without doing anything about them is inconsequential as far as protecting your system from attackers is concerned. The key idea here is to ensure that the scanning is done regularly and that the remediation is done promptly. This will ensure an efficient vulnerability management system.
- All risk assessments should be given a business context: Bringing in the business context entails analyzing the business impact of the risks and vulnerabilities in the system. Your vulnerability management program should not place equal weight on all the vulnerabilities in the system. Each of the identified vulnerabilities should be analyzed, and the impact of their exploitation on the business will allow you to prioritize what vulnerabilities need sorting out first. The risk with the most business impact can lead to the collapse of a business if exploited or can bring about major financial losses to the enterprise. The identified vulnerabilities also need strategic management, which means that they need to be analyzed based on the business impact perspective before acting on the remediation processes.
- Ensure that you minimize exceptions in your vulnerability management system: Exceptions in the system are those devices that have been exempted from scanning processes. Organizations will often exempt one device or another for organizational reasons. However, huge enterprises creating exceptions in several localities where they operate eventually have a situation in which they have a huge attack surface that is unknown and whose vulnerabilities remain unknown to the vulnerability management program. These exceptions present unknown risks to the organizations and the more exceptions there are, the higher the likelihood that an attacker will find one and exploit it.
- Focusing your efforts on the right metrics: Metrics play a critical role in determining whether your vulnerability management program is successful or not. For instance, you may be keeping track of all the vulnerabilities you identify in your system but fail to keep a record of the prioritization of these vulnerabilities. In this case, the metrics you keep will not be of much use to you. The metrics need to be properly used. After scanning and gathering information, it is important to determine the metrics that are crucial to your organization and consistently use these records to improve your vulnerability management program. The shift of mentality, in this case, is to go for quality metrics and not quantity. Do not keep huge amounts of data you do not use. It will just take up more resources and reduce the efficiency of your efforts.
- Ensuring that there is a clear connection between the risk assessment and remediation workflows: Scanning will lead to huge chunks of information regarding your system. The information is not important without actual remediation actions that will seek to address the identified vulnerabilities. The process of linking the assessment and remediation is what we are referring to as workflows. Every organization will have unique workflows that include specific predetermined processes through which it initiates remediation efforts after assessments. Also, ensure that you regularly review the vulnerability management program to ensure that it works as expected. The regular review of the strategies in use is crucial, as they help you avoid the complacency that may creep in and cause you to not update the strategy in use to keep up with evolving trends.
Vulnerability management tools
The available vulnerability management tools are many, and for the sake of simplicity, this section will discuss tools according to the phase they are used in. Therefore, each phase will have its relevant tools discussed and their pros and cons given. It is worth noting that not all the tools discussed may deal with the vulnerabilities themselves. Their contributions are, however, very important to the whole process.
Asset inventory tools
The asset inventory phase is aimed at recording the computing assets that an organization has so as to ease their tracking when it comes to performing updates. The following are some of the tools that can be used in this phase.
Peregrine tools
Peregrine is a software development company that was acquired by HP in 2005. It has released three of the most commonly used asset inventory tools. One of these is the asset center. It is an asset management tool that has been specifically fine-tuned to meet the needs of software assets. The tool allows organizations to store licensing information about their software. This is an important piece of information that many other asset inventory systems leave out. This tool can only record information about the devices and software in the organization. However, sometimes there is a need for something that can record details about the network.
Peregrine created other inventory tools specifically designed for recording assets on a network. These are the network discovery and desktop inventory tools, which are commonly used together. They keep an updated database of all computers and devices connected to an organization’s network. They can also provide extensive details about a network, its physical topology, the configurations of the connected computers, and their licensing information.
All these tools are provided to the organization under one interface. Peregrine tools are scalable, can be easily integrated, and are flexible enough to cater to changes in a network. Their disadvantage shows itself when there are rogue desktop clients in a network since the tools will normally ignore them.
LANDesk Management Suite
The LANDesk Management Suite is a vigorous asset inventory tool that is commonly used for network management. The tool can provide asset management, software distribution, license monitoring, and remote-based control functionalities over devices connected to the organizational network.
The tool has an automated network discovery system that identifies new devices connected to the network. It then checks against the devices that it has in its database and adds the new devices if they have never been added. The tool also uses inventory scans running in the background on clients, and this enables it to know information specific to the client, such as license information. The tool is highly scalable and gives users a portable backend database.
Figure 16.10: LANDesk Management Suite dashboard
The cons of this tool are that it cannot be integrated with other tools used in command centers and that it also faces the challenge of locating rogue desktops.
Foundstone’s Enterprise (McAfee)
Foundstone’s Enterprise is a tool by FoundScan Engine that performs network discovery using IP addresses. The tool is normally set up by the network administrator to scan for hosts assigned a certain range of IP addresses. The tool can be set to run at scheduled times that the organization deems to be most appropriate. The tool has an enterprise web interface where it lists the hosts and services it has found running on the network. The tool is also said to scan intelligently for vulnerabilities that the hosts may have and give periodic reports to the network admin. However, the tool is seen as falling short of being the ideal asset inventory tool since it only collects data related to vulnerability scanning:

Figure 16.11: McAfee Enterprise Security Manager dashboard view
This tool can be accessed at https://www.mcafee.com/enterprise/en-us/home.html
Information management tools
The information management phase concerns the control of the information flow in the organization. This includes the dissemination of information about intrusions and intruders to the right people who can take the recommended actions. There are a number of tools that offer solutions to help with the dissemination of information in organizations. They use simple communication methods such as emails, websites, and distribution lists. Of course, all of these are customized to fit an organization’s security incident policies.
During security incidents, the first people that have to be informed are those in the incident response team. This is because their speed of action may determine the impacts that security vulnerabilities have on an organization. Most of the tools that can be used to reach them are web-based.
One of these tools is the CERT Coordination Center. It facilitates the creation of an online command center that alerts and periodically informs a select number of people via email (for more information, visit https://www.kb.cert.org/vuls/). Another tool is Security Focus, which uses a similar strategy to the CERT tool. It creates mailing lists to inform the incident response team when a security incident has been reported.
The Comodo Dragon platform is also another information management tool. There are many advantages of this tool, one of which is that it keeps the incident response team informed. Comodo Cybersecurity is renowned globally for its in-depth internet security threat reports. These annual publications are great for learning how cybercriminals are evolving each year. The report also gives meaningful attack statistics. This allows the incident response teams to adequately prepare for certain types of attacks based on the observable trends. As well as this publication, the tool also provides you with the threat intelligence report and security white papers. The tool also provides threat spotlights for some types of attacks that organizations must prevent. Finally, the tool provides remediation steps via Comodo AEP, which can be used to remove malware and treat infected systems. This tool is well rounded in information management and is, therefore, highly recommended.
Figure 16.12: Comodo Dragon Enterprise Platform dashboard view
In the figure below, you will see a comparison between the usual managed endpoint detection and response services and Comodo:
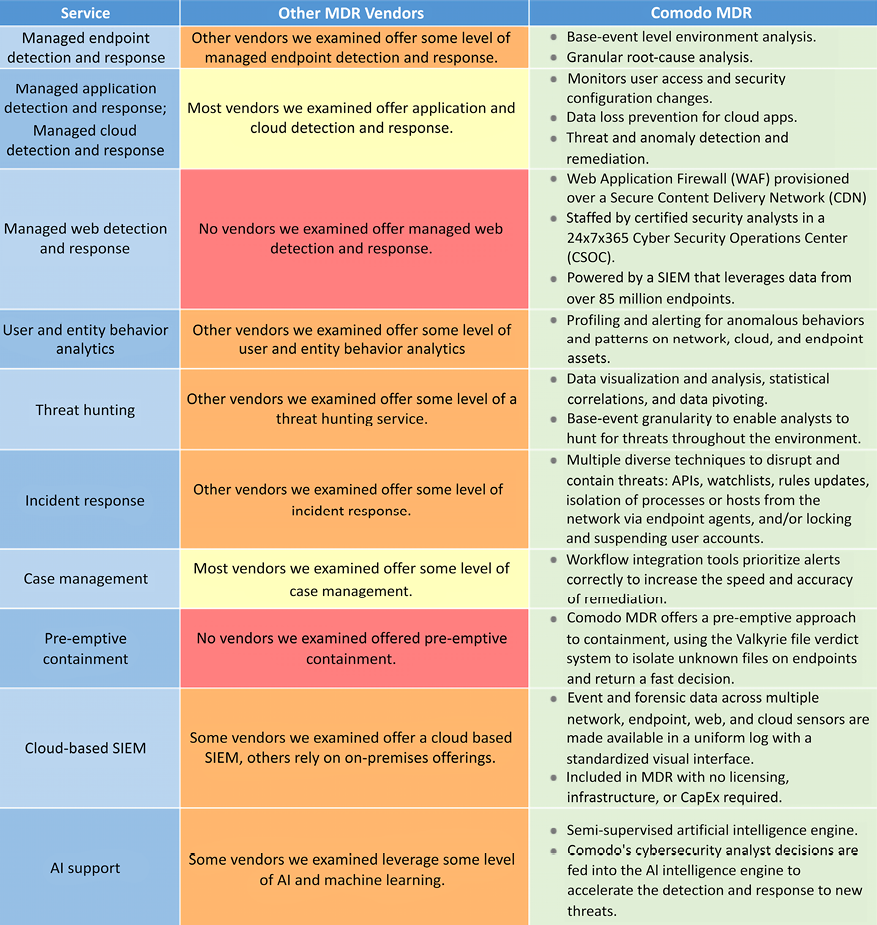
Figure 16.13: Comodo MDR vs others
The most obvious similarity in all these tools is the use of email alerts through mailing lists. The mailing lists can be set up so that incident responders get the alerts from an organization’s security monitoring tools first, and once they have verified a security incident, the rest of the users in an organization can be informed. The appropriate actions that stakeholders ought to take should also be communicated via the mailing lists.
Organizational security policies are, at times, good tools that complement these online tools. During an attack, the local security policies can guide users as to what they can do and who they should contact.
Risk assessment tools
Most risk assessment tools are developed in-house since all organizations do not face the same risks at the same time. There are many variations in risk management, and that is why it might be tricky to use only one choice of software as the universal tool to identify and assess the risks that an organization faces. The in-house tools that organizations use are checklists developed by the system and network administrators. The checklist should be made up of questions about potential vulnerabilities and threats that the organization is exposed to. These questions will be used by the organization to define the risk levels of the vulnerabilities identified within its network. The following is a set of questions that can be put on the checklist:
- How can the identified vulnerabilities impact the organization?
- Which business resources are at risk of being compromised?
- Is there a risk for remote exploitations?
- What are the consequences of an attack?
- Is the attack reliant on tools or scripts?
- How can the attack be mitigated?
To complement the checklist, organizations can acquire commercial tools that perform automated risk analysis. One of these tools is ArcSight Enterprise Security Manager (ESM), which is available at https://www.microfocus.com/en-us/cyberres/secops/arcsight-esm. It is a threat-detection and compliance-management tool used to detect vulnerabilities and mitigate cybersecurity threats. The tool gathers a lot of security-related data from a network and the hosts connected to it. From the event data that it records, it can make real-time correlations with its database to tell when there are attacks or suspicious actions on the network. It can correlate a maximum of 75,000 events per second. This correlation can also be used to ensure that all events follow the internal rules of the organization.
It also recommends methods of mitigating and resolving vulnerabilities.

Figure 16.14: ArcSight Command Center dashboard
Vulnerability assessment tools
Because of the increase in the number of cybersecurity threats that organizations face, there has been a corresponding growth in the number of vulnerability scanning tools. There are many freeware and premium tools for organizations to choose from. Most of these tools were discussed in Chapter 5, Reconnaissance, and Chapter 6, Compromising the System. The two most commonly used vulnerability scanners are Nessus and Nmap (the latter of which can be used as a basic vulnerability tool via its scripting function). Nmap is highly flexible and can be configured to address the specific scanning needs of the user. It quickly maps a new network and provides information about the assets connected to it and their vulnerabilities.
Nessus can be thought of as an advancement of the Nmap scanner. This is because Nessus can perform an in-depth vulnerability assessment of the hosts connected to a network. The scanner will be able to determine the hosts’ operating systems’ versions, missing patches, and the relevant exploits that can be used against the system.
The tool also sorts the vulnerabilities according to their threat levels. Nessus is also highly flexible such that its users can write their own attack scripts and use them against a wide range of hosts on the network. The tool has its own scripting language to facilitate this (we will cover Nessus in more detail later in this chapter). It is a great feature since, as was stated when we discussed the challenges faced in this step, many scanners do not find the perfect balance between a good interface and a high level of flexibility.
There are other related tools that can also be used for scanning, such as Harris STAT, Rapid7’s tools, and Zenmap. Their functionalities are, however, similar to those of both Nessus and Nmap.
Reporting and remediation tracking tools
This step of the vulnerability management strategy allows incident responders to come up with appropriate ways to mitigate the risks and vulnerabilities faced by an organization. They need tools that can tell them the current security state of the organization and to track all the remediation efforts. There are many reporting tools, and organizations tend to prefer the ones that have in-depth reporting and can be customized for several audiences. There are many stakeholders in an organization and not all of them can understand technical jargon. At the same time, the IT department wants tools that can give them the technical details without any alterations. Therefore, the separation of audiences is important.
Two tools with such capabilities are Qualisys (https://www.qualisys.com/) and Intruder (https://www.intruder.io/ – we will discuss Intruder’s various features further in a dedicated section later in this chapter). They both provide reporting features that can be customized to the different needs of users and other stakeholders. Both come with a customizable dashboard. This dashboard enables its users to retrieve long-term reports and reports that are custom-made for specific people, operating systems, services, and regions. Different regions will affect the language of the report, and this is particularly useful for global companies. The reports generated by these tools will show vulnerability details and their frequency of occurrence.
The two tools also provide remediation tracking functionalities. Intruder has an option to assign vulnerabilities to a specific system administrator or IT staff member. It can then track the remediation process using tickets. Intruder also has the option where it can assign certain vulnerabilities to certain people that are responsible for remedying them. It will also track the progress that the assigned parties make. Upon completion, Intruder will perform a validation scan to ascertain that the vulnerability was solved. This is particularly useful as remediation tracking is normally aimed at ensuring that someone takes responsibility for addressing a certain vulnerability until it is resolved.
Response planning tools
Response planning is the step where most of the resolution, eradication, cleansing, and repair activities take place. Patches and system upgrades also occur at this stage. There are not many commercial tools made to facilitate this step. Mostly, response planning is done through documentation. Documentation helps system and network administrators with the patching and updating process for systems that they are not familiar with. It also helps during changeovers where new staff may be put in charge of systems that they have never used before. Lastly, documentation helps in emergency situations to avoid skipping some steps or making mistakes.
Now that we have discussed tools that are useful for each stage of a vulnerability management strategy, we will look at some tools that are useful for vulnerability management at large.
Intruder
This tool addresses the growing need for security teams to scan for vulnerabilities on both on-premises and cloud platforms. The tool itself is cloud-based and can integrate with the leading cloud solution providers such as Amazon AWS, Google Cloud, and Microsoft Azure. Since it is cloud-based, the tool is always running and, thus, does real-time external scans to ensure that an organization is not exposed to known weaknesses that can be exploited by attackers.
Intruder can scan computer networks, systems, and cloud apps, identify the flaws, and send alerts to the IT security team to fix them. The tool is perimeter-specific and keeps track of exposed ports and services on networks. It also scans for weaknesses in configurations that might impact the security stature of an organization. Some of the weaknesses that it checks for include default passwords and weak encryption. Intruder scans applications to determine their susceptibility to attacks such as cross-site scripting or brute-force attacks.
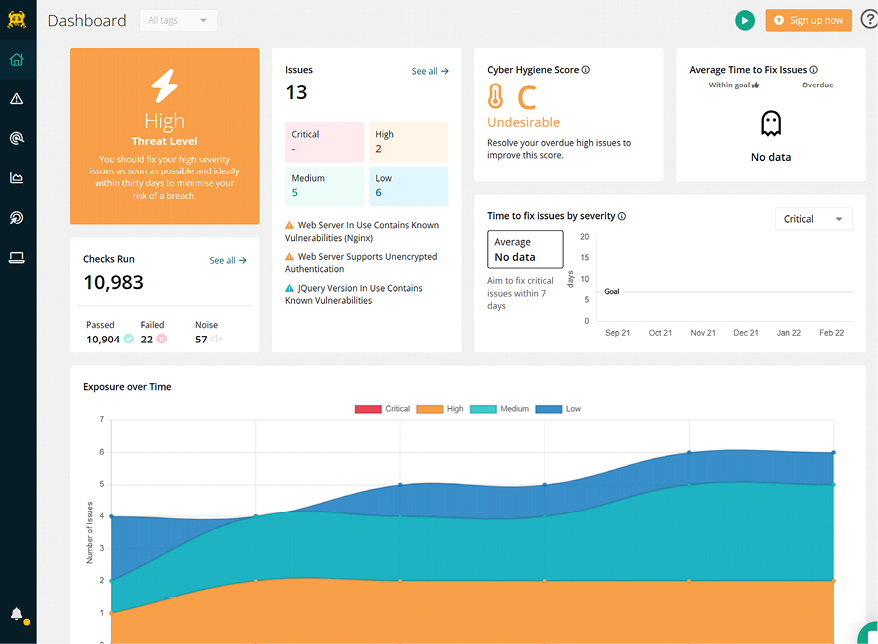
Figure 16.15: The Intruder dashboard displays a summary of a scan detecting 13 issues and mapping the system’s exposure to them over time
To ensure that the IT team gets a full external view of their IT infrastructure, the tool also scans for software patches on servers and hosts and informs the IT team when some patches have not been applied.
Lastly, the tool uses several techniques to ensure that it does not report false positives, a common weakness with many other vulnerability scanners. The tool issues monthly reports to users to provide them with intelligence for managing vulnerabilities.
Patch Manager Plus
There have been many cases of hackers breaching into systems that missed some patches from manufacturers. With the increase of zero-day attacks, many software vendors are providing users with patches for any discovered vulnerabilities. However, not all users are notified about the availability of patches and many more do not take the initiative to install available patches.

Figure 16.16: ManageEngine’s Patch Manager Plus can display not just the patch status, but also the network status
The Patch Manager Plus tool has been specifically developed to take up the burden of vulnerabilities in unpatched systems. The tool scans unpatched systems in a network and automatically deploys patches.
It currently supports Windows, Mac, and Linux operating systems as well as 300 commonly used third-party software. The tool works as follows:
- Detection – it scans the hosts on a network to discover the missing OS and third-party software patches
- Testing – since patches might at times cause unanticipated behaviors in systems, the tool first tests the patches before deployment to ensure that they are secure and work correctly
- Deployment – the tool automatically starts patching the operating systems and the supported third-party applications
- Report – the tool provides a detailed report of the audit done on the network and the patches that have been applied
Windows Server Update Services (WSUS)
Windows Server Update Services (WSUS) is another commonly used patch management tool. WSUS is free to use and allows you to fully manage the distribution of Microsoft updates to computers on your network. WSUS cannot be used to deploy third-party patches, which is probably the only downside of the product.
The WSUS service can be enabled via any Windows Server.
Figure 16.17: WSUS dashboard
Comodo Dragon platform
As explained before, the Comodo Dragon platform is a great tool to secure your corporate environments. This tool has the ability to patch your computers for Microsoft Windows updates and any third-party application updates, including firmware updates of any computer brand.
Figure 16.18: Dragon platform Patch Management
InsightVM
Created by Rapid7, InsightVM uses advanced analytics to discover vulnerabilities in a network, pinpoint which devices are affected, and prioritize the critical ones that need to be attended to. The tool first discovers all the devices that are connected to the network. It then assesses and categorizes each device based on types such as laptops, phones, and printers. Afterward, it scans the devices for vulnerabilities.
InsightVM can import penetration test results from Metasploit since they are all developed by Rapid7. Likewise, Metasploit Pro can initiate vulnerability scans on networked devices using InsightVM. It assigns the vulnerabilities that it detects on devices a score that is based on the CVE and CVSS base scores and other factors such as exposure and vulnerability duration. This helps the IT security team to prioritize the vulnerability management process more accurately.
The tool also comes with inbuilt templates for compliance audit purposes.
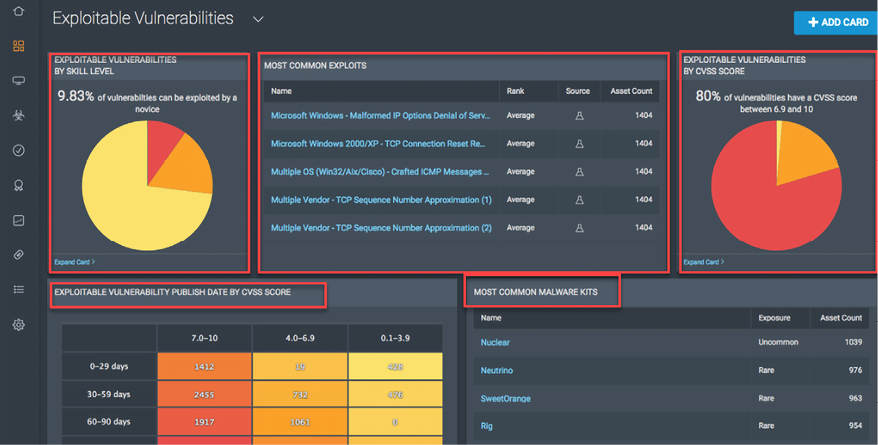
Figure 16.19: Rapid7 uses the benefits of owning Metasploit; when it comes to vulnerabilities, this is one of the best products on the market
Azure Threat and Vulnerability Management
If you are using the Microsoft cloud, then Azure Threat and Vulnerability Management can be a valuable tool for your organization. It’s a solution to bridge the gap between security administration and IT administration during the remediation process. It does so by creating a security task or ticket through integration with Microsoft Intune and Microsoft System Center Configuration Manager. Microsoft is promising real-time device inventory, visibility into software and vulnerabilities, application runtime context, and configuration posture.
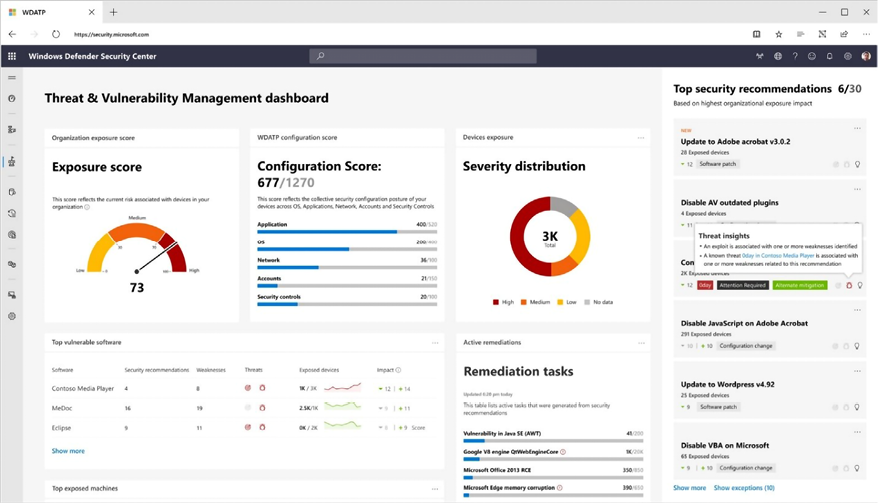
Figure 16.20: Azure Threat and Vulnerability Management dashboard view
This tool assists you by exposing emerging attacks in the wild, pinpointing active breaches, and protecting high-value assets, while giving you seamless remediation options.
Implementing vulnerability management with Nessus
Nessus is one of the most popular commercial network vulnerability scanners, developed by Tenable Network Security. It is designed to automate the testing and discovery of known vulnerabilities before a hacker takes advantage of them. It also suggests solutions for the vulnerabilities identified during the scan. The Nessus vulnerability scanner products are annual subscription-based products. Luckily, the home version is free of charge, and it also offers plenty of tools to help explore your home network.
Nessus has countless capabilities and is fairly complex. We will download the free home version, and cover only the basics of its setup and configuration, as well as creating a scan and reading the report. You can get the detailed installation and user manual from the Tenable website.
Download the latest version of Nessus (appropriate to your operating system) from its download page (https://www.tenable.com/products/nessus/select-your-operating-system). In our example, I downloaded the 64-bit Microsoft Windows version, Nessus-7.0.0-x64.msi. Just double-click on the downloaded executable installation file and follow the instructions along the way.
Nessus uses a web interface to set up, scan, and view reports. After the installation, Nessus will load a page in your web browser to establish the initial settings. Click on the Connect via SSL icon. Your browser will display an error indicating that the connection is not trusted or is unsecure. For the first connection, accept the certificate to continue configuration. The next screen (Figure 16.21) will be about creating your user account for the Nessus server:
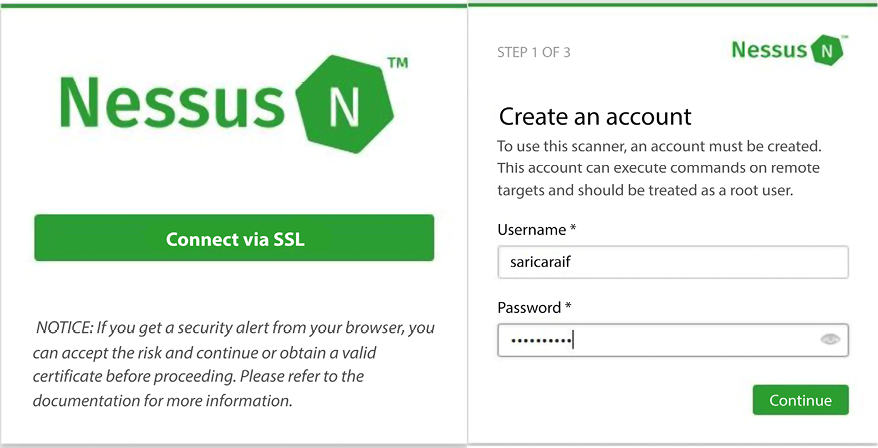
Figure 16.21: Account creation
Create your Nessus system administrator account with a Username and Password that you will use for future logins, then then click on the Continue button. On the third screen choose Home, Professional, or Manager from the drop-down menu.
After that, go to https://www.tenable.com/products/nessus-home in a different tab and register for the activation code, as shown in the figure below:
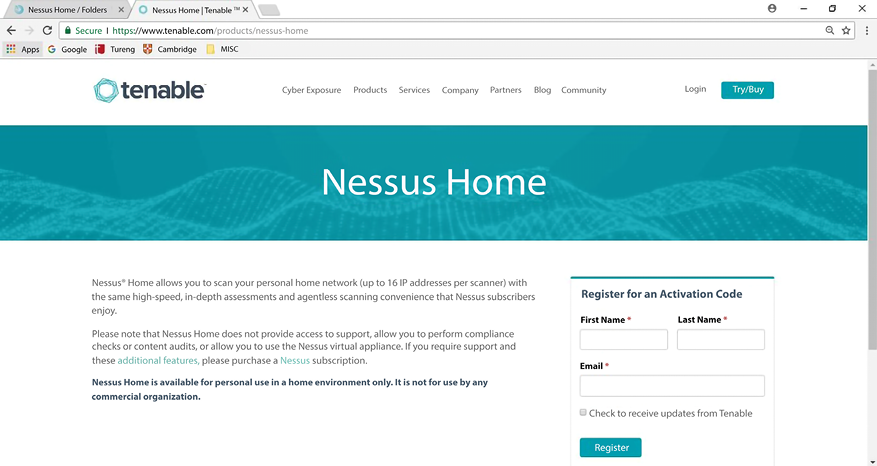
Figure 16.22: Registration and plugin installation
Your activation code will be sent to your email address. Type your activation code in the Activation Code box. After registration, Nessus will start downloading plugins from Tenable. This may take several minutes depending on your connection speed.
Once the plugins have been downloaded and compiled, the Nessus web UI will initialize and the Nessus server will start, as shown in the figure below:

Figure 16.23: Nessus web UI
To create a scan, click on the New Scan icon in the upper-right corner. The Scan Templates page will appear, as shown in the following screenshot:

Figure 16.24: Scan Templates
You can choose any template listed on the Scan Templates page. We will choose Basic Network Scan for our test. The Basic Network Scan performs a full system scan that is suitable for any host. For example, you could use this template to perform an internal vulnerability scan on your organization’s systems. As you choose Basic Network Scan, the Settings page will be launched, as shown in Figure 16.25.
Name your scan “TEST” and add a description. Enter IP scanning details on your home network. Keep in mind that Nessus Home allows you to scan up to 16 IP addresses per scanner. Save the configuration and, on the next screen, click the Play button to launch the scan. Depending on how many devices you have on your network, the scan will take a while.

Figure 16.25: Scan configuration
Once Nessus finishes scanning, click on the related scan; you’ll see a bunch of color-coded graphs for each device on your network. Each color on the graph refers to different results, starting from a low level and ranging to critical.
In Figure 16.26, we have four hosts (192.168.0.25, 192.168.0.21, 192.168.0.1, and 192.168.0.24):

Figure 16.26: Test results
After the Nessus vulnerability scan, the results will be shown, as displayed in Figure 16.26.
Click on any IP address to display the vulnerabilities found on the selected device, as shown in Figure 16.27. I chose 192.168.0.1 to see the details of the vulnerability scan:

Figure 16.27: Vulnerabilities
When an individual vulnerability is selected, it displays more details of that particular vulnerability. My UPnP Internet Gateway Device (IGD) Protocol Detection vulnerability is shown in Figure 16.27. It gives lots of information about related details, such as the Description, Solution, Plugin Details, Risk Information, and Vulnerability Information:

Figure 16.28: Details of the vulnerability
Lastly, scan results can be saved in several different formats for reporting purposes. Click on the Export tab in the upper-right corner to pull down a menu with the formats Nessus, PDF, HTML, CSV, and Nessus DB:

Figure 16.29: Exporting results
In my case, I chose a PDF format and saved the vulnerability scan results. As shown in Figure 16.30, the report gives detailed information based on the IP addresses scanned. The Nessus scan report presents extensive data about the vulnerabilities detected on the networks. The report can be especially useful to security teams. They can use this report to identify vulnerabilities and the affected hosts in their network, and take the required action to mitigate vulnerabilities:

Figure 16.30: Results in PDF format
Nessus provides a lot of functionality and ability in one tool. Compared to other network scanning tools, it is fairly user-friendly, has easy-to-update plugins, and has nice reporting tools for upper management. Using this tool and seeing the vulnerabilities will help you gain knowledge of your systems and also teach you how to protect them. New vulnerabilities are released almost daily, and in order to keep your systems consistently secure, you have to scan them regularly.
Keep in mind that finding the vulnerabilities before hackers take advantage of them is a great first step in keeping your systems safe.
OpenVAS
OpenVAS is a vulnerability scanner that can do unauthenticated and authenticated testing, with some other customizable options. The scanner is accompanied by vulnerability test feeds and daily updates.

Figure 16.31: HostedScan powered by OpenVAS
Qualys
Qualys offers different security products with different scopes, including Cloud Platform, cloud-hosted assets management, IT security, compliance, and web app security products. They provide continuous monitoring of your network to detect and protect against attacks, alerting their customers in real time of threats and system changes.

Figure 16.32: Qualys Vulnerability Management dashboard view
As you can see in the screenshot above, vulnerability management can be scheduled based on different scopes. Qualys not only detects vulnerabilities, but also provides you with options to remediate them.
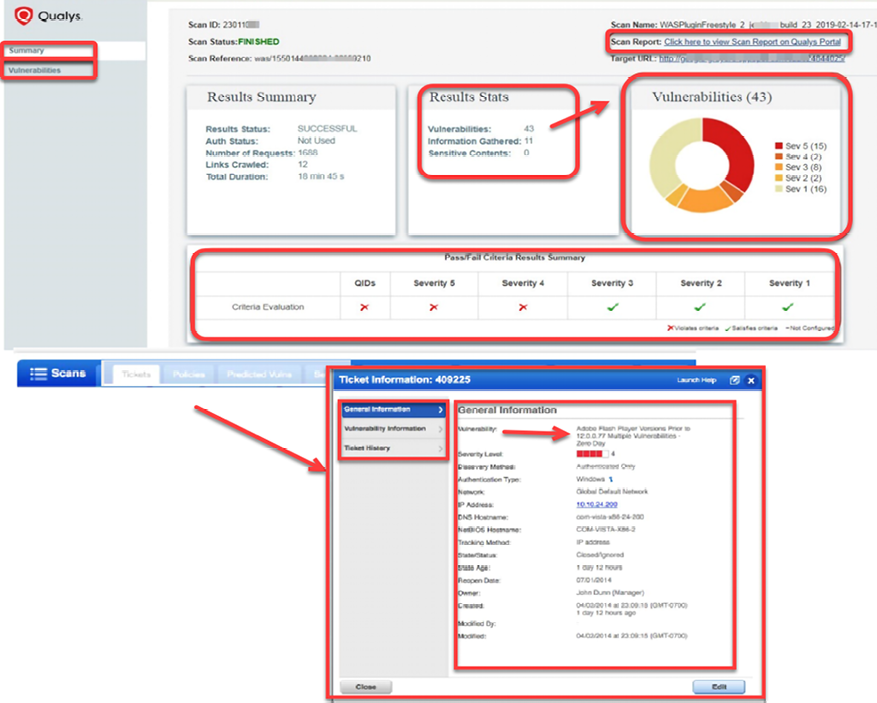
Figure 16.33: Detailed view of the Qualys software
Acunetix
The Acunetix vulnerability scanner tests the network perimeter for more than 50,000 known vulnerabilities and misconfiguration.
Acunetix leverages the OpenVAS scanner to provide comprehensive network security scans. It’s an online scanner, so scan results are available on the dashboard where you can drill down into the report to access the risks and threats.

Figure 16.34: Acunetix dashboard view
Risk items are associated with the standard threat score and actionable information, so it’s easy for you to remediate.
Some of the following checks are done.
- Security assessment for routers, firewalls, load balancers, switches, etc.
- Auditing weak passwords on network services
- Testing DNS vulnerabilities and attacks
- Checking the misconfiguration of proxy servers, TLS/SSL ciphers, and web servers
Conclusion
Organizations are finding themselves under the pressure of being forced to react quickly to the dynamically increasing number of cybersecurity threats. Since attackers have been using an attack life cycle, organizations have also been forced to come up with a vulnerability management life cycle. The vulnerability management life cycle is designed to counter the efforts made by the attackers in the quickest and most effective way.
The previous chapters have discussed the attack life cycle and outlined the tools and techniques that attackers normally come packed with. From these tools and techniques, a life cycle capable of mitigating them was designed. This chapter has discussed an effective vulnerability management life cycle composed of six steps. Each of the steps is aimed at making the life cycle effective and thorough in mitigating the vulnerabilities that may be in an organization and that attackers may exploit. The well-planned life cycle ensures that not a single host of an organizational network is left exposed to attackers. The life cycle also ensures that the organization ends up with a fully secured IT environment and that it is hard for attackers to find any vulnerabilities to exploit. This chapter has given a set of best practices for each step of the life cycle. These best practices are aimed at ensuring that the incident response teams and the IT staff members make exhaustive use of each step to secure the organization. In the lab section, we looked at two software options that can help you to understand vulnerability management better.
Summary
This chapter has outlined the types of responses that organizations are expected to provide against attackers. This chapter has discussed the vulnerability management life cycle in terms of the vulnerability management strategy. It has gone through the steps of asset inventory creation, the management of information flow, the assessment of risks, the assessment of vulnerabilities, reporting, and remediation, and finally the planning of the appropriate responses. It has explained the importance of each step in the vulnerability management phase and how each should be carried out.
The asset inventory has been described as crucial to the strategy because it is the point where all the details about the hosts are listed to assist in a thorough sanitization of all machines that may have vulnerabilities. The critical function of the information management step in disseminating information in a fast and reliable way has also been highlighted, as well as the tools commonly used to achieve it. The risk identification and classification functions of the risk assessment step have also been discussed. The chapter has also discussed the identification of vulnerabilities in hosts in the vulnerability assessment phase. The roles played by reporting and remediation tracking to inform all stakeholders and follow up on remediation have also been touched upon. The chapter has also discussed the final execution of all responses in the response planning step. The best practices for completing each of the steps successfully have also been discussed.
In the next chapter, you will learn about the importance of logs and how you can analyze them.
Further reading
- Incident Response in the Age of Cloud, by Dr. Erdal Ozkaya, Packt Publishing: https://www.packtpub.com/product/incident-response-in-the-age-of-cloud/9781800569218
- Microsoft Digital Defense Report: https://www.microsoft.com/en-au/security/business/security-intelligence-report
- Comodo Valkyrie: https://threatmap.valkyrie.comodo.com/#/
- Risk management guides: https://www.erdalozkaya.com/?s=risk+management
References
- K. Rawat, Today’s Inventory Management Systems: A Tool in Achieving Best Practices in Indian Business, Anusandhanika, vol. 7, (1), pp. 128–135, 2015. Available: https://search.proquest.com/docview/1914575232?accountid=45049
- P. Doucek, The Impact of Information Management, FAIMA Business & Management Journal, vol. 3, (3), pp. 5–11, 2015. Available: https://search.proquest.com/docview/1761642437?accountid=45049
- C. F. Mascone, Keeping Industrial Control Systems Secure, Chem. Eng. Prog., vol. 113, (6), pp. 3, 2017. Available: https://search.proquest.com/docview/1914869249?accountid=45049
- T. Lindsay, LANDesk Management Suite / Security Suite 9.5 L... | Ivanti User Community, Community.ivanti.com, 2012. [Online]. Available: https://community.ivanti.com/docs/DOC-26984. [Accessed: 27-Aug-2017]
- I. Latis Networks, “Latis Networks, Bloomberg.com, 2017. [Online]. Available: https://www.bloomberg.com/research/stocks/private/snapshot.asp?privcapId=934296. [Accessed: 27-Aug-2017]
- The CERT Division, Cert.org, 2017. [Online]. Available: http://www.cert.org. [Accessed: 27-Aug-2017]
- SecurityFocus, Securityfocus.com, 2017. [Online]. Available: http://www.securityfocus.com. [Accessed: 27-Aug-2017]
- IT Security Threats, Securityresponse.symantec.com, 2017. [Online]. Available: http://securityresponse.symantec.com. [Accessed: 27-Aug-2017]
- G. W. Manes et al., NetGlean: A Methodology for Distributed Network Security Scanning, Journal of Network and Systems Management, vol. 13, (3), pp. 329–344, 2005. Available: https://search.proquest.com/docview/201295573?accountid=45049. DOI: http://dx.doi.org/10.1007/s10922-005-6263-2
Join our community on Discord
Join our community’s Discord space for discussions with the author and other readers:

