9
Handling Data Responsibly
Today, data and analytics are present in every aspect. As a result, data and analytics play a huge part in our daily lives. As stated in Chapter 1, The Beginning – The Flow of Data, we constantly generate and collect data. It has been estimated that we generate more than 2.5 quintillion bytes of data every day (https://www.vpnmentor.com/blog/data-privacy-security-stats/), sometimes in ways that we cannot control or see.
Companies use our data on the internet, on websites, on our watches and phones, and even on our smart devices at home for a variety of purposes. Our information is used to improve customer service, provide a better customer experience, send us personalized advertisements, and more. However, we are not even aware of the potential risks that may arise. What should we think about our privacy? Or do you not wonder what others might do with your data, and whether it is used safely and ethically when, for example, algorithms and/or business rules are used? Do you know whether your data is safe? Do you know what others do with your data?
There are some obstacles that we must overcome and identify. This chapter will cover a variety of topics, with the goal of providing you with food for thought about how to handle data in a correct and ethical manner, as well as how to care for personal data, identify personal data at the start of a project, and more. We do not claim to be ethics, privacy, or security experts, but we have witnessed how our data world has evolved over the last few decades. In addition, we have seen an increase in the number of potential risks that we must address at the start of our projects.
In this chapter, we will cover the following topics:
- Introducing the potential risks of data and analytics
- Identifying data security concerns
- Identifying data privacy concerns
- Identifying data ethics concerns
Introducing the potential risks of data and analytics
Over the years, we’ve seen a lot of movies with artificial intelligence elements. We’ve seen Mr. Arnold Schwarzenegger in the movie Terminator, where computers took over the world and the movie ended with things returning to how they were. What do you think of the Matrix movies starring Keanu Reeves? The Matrix is a computer simulation of the world in 1999, designed specifically to control people on the planet. Or what about the Sandra Bullock film The Net? Angela Bennet (Bullock) used to be a systems analyst. When a coworker sends her a floppy disk with a game on it, she looks at it on her system and the trouble begins, and her entire identity is erased. There are many more movies such as this, with programs, computers, and more describing the world and telling humanity what to do, or, in the best-case scenario, saving the world. Sometimes, the movies and series that were made depicted rather dark and bad scenarios. Some are even worse than others when it comes to using data in a bad way, using virtual worlds, and more.
Looking back in time, what should we think about East Germany? For four decades, until the Berlin Wall fell (November 9, 1989), the Stasi spied on millions of people. They even forced loved ones to spy on their own families and friends. They amassed an incredible amount of information about their inhabitants. They are said to have collected and stored 111 kilometers of documents in their previous archives (https://www.pieterjanssen.eu/2020/06/15/transitieproces-van-de-stasi-documenten-in-volle-gang/). We do know that people are working on restoring and digitizing those documents. In this way, history is saved and preserved for future generations. Can you imagine what kind of analysis can be done when documents, films, and other media are digitized? When this project is completed, it is possible that amazing, interesting, or harmful things will be discovered.
It’s all here: data, analytics, big data, artificial intelligence, machine learning, deep learning, natural language processing, neural networks, and more. It is used in many ways; we even described some solutions in Chapter 2, Unfolding Your Data Journey. But what will happen when we use that data to classify people? For example, consider that a university only wants students with grades higher than 8 out of 10 to enter that particular university. As they say, to influence the level of entrants at that university to have better-qualified students (that is, a better success rate).
Think about sorting resumes based on algorithms, where women above 40 will be dismissed for a job at a certain company. Or that your data is stolen and your credit card is used to purchase expensive goods.
Nonetheless, as a result of various ethical, security breaches, or privacy issues, people have been robbed, injured, banned, or labeled as fraudulent. The question here is whether we need to protect data and protect people from unethical use of our data. The answer is yes! During our discussions, it occurred to us that we needed to consider data privacy, data security, and data handling in an ethical manner before beginning our data and analytics projects. This is why we felt it was important to address how to handle your data responsibly, and we chose to write a chapter about it. Figure 9.1 depicts three specific data concerns when it comes to handling data responsibly:
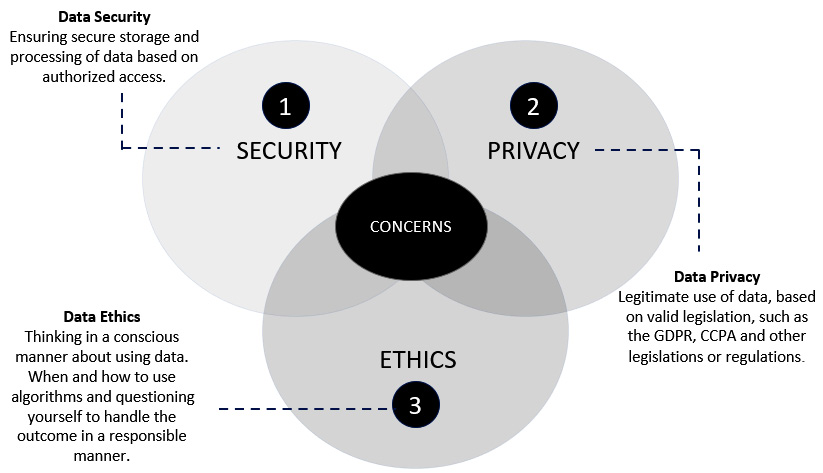
Figure 9.1 – Three important data concerns
When we look at those three concerns, we are able to define them a bit further in more detail:
- Data security: Data security is the process of protecting data and ensuring that the data in your organization is secure. It is concerned with the security of infrastructure, software, and procedures. It also handles data access with the necessary permissions that you are authorized to look at specific data.
- Data privacy: Data privacy, also known as privacy management, is concerned with the protection of data through legislation and regulations. With the assistance of these laws and regulations, everyone can take privacy regulations into consideration so that personal and confidential data is properly collected, shared, and used.
- Data ethics: Data ethics is about managing information in a transparent, fair, and respectful manner, which is required for responsible data handling.
According to the Internet Society (https://www.internetsociety.org/policybriefs/responsible-data-handling/), when we want to handle data responsibly, we should not ask ourselves, can we do this? The question that needs to be answered here is should we do this?
The concerns of data security, data privacy, and data ethics will be discussed in the following sections. We address those concerns from a more pragmatic standpoint, and we are well aware that those are not the only concerns that could exist. They simply mean that you will be able to address questions about security, privacy, and ethical data handling earlier in your project initiatives (such as an intake).
Intermezzo – a retailer uses buying history and artificial intelligence to personalize coupons
A United States retailer was interested in doing more personalized marketing for its customers. It had previously sent out monthly coupon books in the mail but had an idea to try and send out personalized coupons that each shopper might be more likely to use.
To start the project, the retailer looked at all the historical purchases to analyze what items are commonly purchased together. Once it figured this out, it then planned to find customers who may have purchased one of those items recently, but not the others, and then send them coupons for those other products.
It was able to accomplish this and launch the project. A few months later, the organization received a complaint from a father saying that his 16-year-old daughter was being sent coupons for items that relate to pregnancy. While the father was upset that his daughter was being sent coupons for pregnancy, what he did not know at the time was that his daughter was, in fact, pregnant and in the first trimester. The organization’s personalized marketing project had correctly identified the daughter was pregnant, even before her father was aware.
Did the organization violate the privacy of the girl? Had the organization done its due diligence to ensure these ethical dilemmas would not happen?
Identifying data security concerns
When a security breach occurs, sensitive, private, personal, or confidential information is exposed to untrustworthy or unsecured parties. This is exactly why we are of the opinion that data security (just like privacy and ethics) should be at the forefront of our minds and that we need to pinpoint it.
Intermezzo – data security facts
In the United States, 1,767 data breaches were reported in the first 6 months of 2021, with over 1,000 data leaks exposing more than 155.8 million records containing sensitive data (https://www.vpnmentor.com/blog/data-privacy-security-stats/).
The Dutch Data Protection Authority (AP) published the Data Breach report for 2021 on May 24, 2022. The number of Data Breach notifications was 24,866, a 4% increase from the previous year. Malware, phishing, or hacking were the sources of those breaches.
Data breaches can occur unintentionally or intentionally. When this occurs and there is no control over the use of that data, that data can be used to cause harm to persons in question, such as spending on their credit, identity theft, and selling personal data on the dark web for other bad guys. When a security breach occurs, it can be extremely painful and cause significant harm.
We should always consider data security elements, especially when we work with data and share insights. Therefore, we should identify them upfront, for example, during the initial data and analytics project initiatives. We can do this by using checklists in our project intake forms or adding a checklist to a project plan.
An example of such an intake form with included checklists is available in Appendix A:
|
Data security check A data security incident is a serious security breach. When protected, sensitive, or confidential data is stolen, used, viewed, stored, or transmitted by someone who is not authorized, a breach occurs. Other security concerns include data leaks, information leaks (who can see what), sensitive information leaks, and data spillage. As a result, when it comes to data and information usage, we must identify some specific elements. | |
|
Application/model/app Dashboards and reports are critical for any organization, team, or department. The work cannot be completed without this information. |
Essential | Important | Desirable | Unclassified |
|
Confidentiality The dashboards and reports are private and only available to a select group of managers and employees. |
Essential | Important | Desirable | Unclassified |
|
Access control What type of access control is required when confidentiality is required? What are the rules that we must follow? (For example, the manager of team A can see information about team A and so on.) |
Add information: |
|
Integrity Incorrect information will not be tolerated (accountable environment). The organization suffers significant damage if the information is incorrect, incomplete, or late. Inaccurate data, such as financial transactions, undermines trust in the organization. |
Essential | Important | Desirable | Unclassified |
|
Availability Dashboards and reports are essential. The organization will suffer severe consequences if the information is not available. |
Essential | Important | Desirable | Unclassified |
|
Additional information and/or explanation | |
Intermezzo – a data leak at an airplane carrier
The Dutch Data Protection Authority (AP) fined an airline carrier 400.000 Euro for failing to secure personal data. In 2019, a hacker was able to penetrate the systems of this airplane carrier due to a poor security process. The hacker gained access to systems and was able to view the personal information of over 25 million people. It has been determined that the hacker downloaded the personal information of approximately 83,000 people.
According to the AP, when you book a flight and enter personal information, the airliner must use that information correctly. Because you cannot book a flight without providing your personal information, you must be able to trust that an organization will handle your data with care and protect it thoroughly. In this case, it was discovered that the airliner did not adequately protect the data.
In 2019, the hacker gained access to systems by using two IT department accounts. That proved to be far too simple.
The airline failed to address the following three data security issues:
- The password was simple to figure out. Only one easy-to-guess password was sufficient to gain access to the airline’s systems.
- There was no use of multi-factor authentication (for example, using a password and a code received via text message).
- Once the hacker gained control of the two accounts, they were able to access a large number of the airline’s systems.
The hacker gained access to the systems in September 2019 and retained access until the airliner closed the leak at the end of November 2019. They promptly reported the breach to the authorities (AP) and informed those who were involved. The airliner took immediate action and measures to better protect passengers. The press release is available at https://autoriteitpersoonsgegevens.nl/nl/nieuws/ap-beboet-transavia-om-slechte-beveiliging-persoonsgegevens.
This previous section described the elements of data security and how important it is to address them at the start of data and analytics projects. We’ve provided an overview of a checklist and added stories from real life to support the importance of data security. In the next section, we will discuss the concerns of data privacy.
Identifying data privacy concerns
When it comes to data usage and data privacy, some countries have special legislation and regulations in place. For example, in European Union countries, there is a law known as the General Data Protection Regulations (GDPR). Regulations in the United States are a patchwork of rules. Except in the case of children, there is no specific privacy law; but the state of California has implemented the California Consumer Privacy Act (CCPA).
Data privacy is the process of handling personal data in accordance with data protection regulations, laws, and common data privacy best practices. We can define who has unrestricted access to what data or information with the help of data privacy, and who has restricted access to data (see also Identifying data security concerns). One example of sharing data (as we described in Chapter 2, Unfolding Your Data Journey) is the usage of smart devices such as a smartwatch for monitoring sports activities. What if the home address of a military member could be found by sharing data from their smartwatch, which poses a potential threat to the personnel and their family? This is exactly why we should take care of privacy concerns at the start of our data and analytics initiatives.
We will address some concerns that we should take care of when we work with data for our data-informed decision-making processes:
- Designed-in privacy (using a clear framework, a written and internal data protection policy, and described organizational and technical measures). Privacy needs to be at the forefront of our minds!
- Processing registers (describe the processes, type, purpose, data security, users, and retention period).
- Is it necessary to do a privacy impact assessment with our Privacy Officer or responsible privacy staff member?
- Take care of procedures and processes in place for the right of access, right to transfer data, and right to be forgotten for data (typically done by the Privacy Office or other departments responsible for data privacy).
- Have a register to report data leaks. When an authority is in place, we should report the data leak within the given regulations.
- Larger organizations, such as healthcare organizations, banks, and governments, should have a Privacy Officer and data privacy processes in place.
To be able to identify data privacy elements, the preceding concerns/elements must be verified and checked during the initial project initiatives (for example, via an intake form). A checklist example can be found in the data privacy check table (the complete intake form and checklist are available in Appendix A):
|
Data privacy check When it comes to using personal data, we should take precautions or be aware from the start of our project that we must adhere to privacy regulations. We need to identify and categorize several categories. For example, in the Netherlands, we handle the following criteria:
Note here that simply moving, copying, or linking data is already a process of digesting or assimilating data. | |
|
Name, Address, and City data (Name, Address, Postal Code, and City of Residence) Yes No | |
|
Identification data (Passport, Driver’s license, or Social Security number) |
Yes No |
|
Application details (Application letters, Resume) |
Yes No |
|
Contact details (E-mail address, Phone or Fax number) |
Yes No |
|
Salary details (Salary details, Social Payments, Income Taxes, Expense reimbursement) |
Yes No |
|
Social Media accounts (LinkedIn, Twitter, WhatsApp, Facebook) |
Yes No |
|
Image and sound recordings (Video, Photos, Passport photographs) |
Yes No |
|
Payment details (Bank name, Account Number, Name of Account holder) |
Yes No |
|
Addition and or explanation When a checkbox is answered with “yes,” it is advised that you arrange a legislation and regulations check with your Privacy Officer. | |
|
Legislation – Regulations check | |
|
Privacy Impact Analysis (PIA) needed? |
Essential | Important | Desirable | Unclassified |
|
Register of Data needed? |
Essential | Important | Desirable | Unclassified |
|
Addition and/or explanation | |
Data privacy regulations are governed by national or state regulations or laws. To ensure that we work in a correct, legal, and ethical manner it is necessary to address privacy concerns like we described in this section. This especially is important when it comes to processing personal data. It is a fact that some (the bigger ones) European organizations face a significant administrative burden to do so, they have to set up their Data Registers, perform Privacy Assessments and act responsibly based on the regulations that are set. If they don't they could face significant problems and fines from the controlling authorities.
Intermezzo – it is unavoidable; companies are using our private data
There are over 100 data and security statistics displayed on the vpnMentor website (https://www.vpnmentor.com/blog/data-privacy-security-stats/). One of the issues here is determining what the percentage of data collection is for some large companies. These are companies that we most likely use every day. For example, did you know that Facebook collects 79.49%, Instagram collects 69.23%, Tinder collects 61.54%, and Airbnb collects 33.33%?
It’s impossible to hide from this phenomenon. If you don’t want your data to be collected through your interest behavior, you should not go on the net! As Edward Snowden once said, the NSA knows it all – you are not aware of it, but you are being monitored! To be honest, it’s hard to control our data. Do we really read all the information of an agreement when using an app or using a website for purchases and more? No, we don’t think so, and once companies have our data, they are able to sell it to other companies. Those companies can use your data to sell more products or services. But what happens when our data falls into the hands of someone who doesn’t have the right intentions?
This previous section described the concerns of data privacy and how important it is to address them at the start of data and analytics projects. We’ve provided an overview of a checklist and added stories from real life to support the importance of data privacy. In the next section, we will discuss data ethical concerns.
Identifying data ethical concerns
When it comes to ethical concerns about data, we see that this topic has grown in prominence in recent years. This is because, in our digital big data era, we create masses more data every day, as discussed in previous chapters. But this data, whether pertaining to an individual or a business, can often be personal or sensitive, and open to exploitation by cybercriminals or others looking to exploit or use this information for negative gain.
Initially, this was a kind of gray area as there were no particular rules defined. People just did amazing things, such as predicting when a website visitor booked an airplane ticket online that they also would buy insurance (a sort of classification was used here). Wherever we could lay our hands on data from an internal and external perspective, we could do amazing things without even worrying about rules or ethical concerns.
But today, the data ethics landscape is different. Issues such as the ownership, privacy, and transparency of data now come into play. In this chapter, we’ll discuss a few examples. We’ll begin by exploring how ethics pertains to algorithms and business rules.
Algorithms and business rules are a set of instructions that can be used to solve specific problems, connect data, and connect logic. While they are commonly used interchangeably, for the purposes of this book, we will define business rules as any logic that you might use to run your business processes, whether those processes are automated or not. For example, a store’s return policy can be an example of a business rule.
An algorithm is a rule or procedure that can be used for solving problems, or when a computation is needed. When we think of algorithms, we think of them as coded formulas. Once the rule and process are automated, it is typically a set of instructions that can run automatically. Like using an algorithm to recognize the faces of people, or identify outliers in data sets and correct them, and so on. With both algorithms and business rules, they take in data and information, apply some logic or math to it, and provide data or information as an output. The output of the business rule or algorithm is the knowledge that aids in the formulation of a solution to a problem.
When viewed in this way, business rules and algorithms are nothing more than a recipe or a detailed set of instructions. Because of technological advancements, particularly in our data field, business rules and algorithms are increasingly capable of learning based on the knowledge they generate.
With the help of Figure 9.2, we give you a definition of ethics and the essence of behaving ethically:
Figure 9.2 – What is ethics?
To be able to identify data ethical elements, they must be verified and checked during the initial project initiatives (for example, via an intake form). We have an example of a checklist in the data ethics check table (the complete intake form and checklist are available in Appendix A), which you could use when performing an intake for your data and analytics projects.
When it comes to data ethics, we simply mean that you should think about what you create from data and how you handle data. Following a number of incidents involving data, algorithms, and business rules, an algorithm supervisor has been established to monitor transparency in the use of algorithms as well as the implementation of effective European regulations. Some industries are developing frameworks and standards for ethical data handling, such as The Council on the Responsible Use of AI by Harvard Kennedy School’s Belfer Center for Science and International Affairs and the Bank of America Corporation. Singapore is also working on ethical data use in the financial sector. Last but not least, Meta, Microsoft, Apple, Amazon, IBM, and Google are all working on the ethical side of data usage. Europe is also working on new legislation and regulations when it comes to handling data in an ethical manner.
When it comes to handling data ethically, businesses must have a transparent, structured data strategy that includes the data ethics strategy. When we use algorithms or business rules that affect decisions that then affect people, organizations, and more, the following three elements must be present:
- Trust: Organizations must apply key data ethics principles to their models, such as transparency, fairness of use, accountability, and privacy. For example, creating risk models in which people are classified as risky based on data from others while they themselves have not done anything to get that label.
- Fairness: Bias, most likely unintended and unknown, can have a negative impact on data-informed decisions. Organizations can provide documentation of fairness when the fairness of use is in place and ethical processes are followed. For example, Amazon was recommended to hire white male applicants based on data from the past, because the data showed that IT professionals had those characteristics (https://amp.theguardian.com/technology/2018/oct/10/amazon-hiring-ai-gender-bias-recruiting-engine).
- Compliance: When it comes to data, we must adhere to privacy legislation and regulations such as the GDPR in Europe and the CCPA in California, USA. Beyond legislation and regulations, organizations have a moral obligation to implement ethical rules. When organizations (or countries) do not have specific ethical rules, it could be a rather scary world. For example, in China, a massive amount of data is collected. Some people call it Big Brother 2.0. Your social score determines your life. When your social score is low, it will affect your complete life. And when this is the case, it could be that people have to face inequality, discrimination, and get hurt.
As mentioned earlier, addressing data ethical concerns, especially when we work with data and share insights, is important. We should do so upfront, for example, during the initial data and analytics project initiatives. We can do so by using checklists in our project intake forms or adding a checklist to a project plan. An example of a checklist is in the following table which is also available in, Appendix A- Templates:
|
Data ethics checklist Data generation, use, collection, analysis, and dissemination are all aspects of working with data. We can do this with both unstructured and structured data. When we do so, there is a chance that the decisions we make will have an impact on individuals and the world. As a result, we must be open about how we use data in our projects. | ||
|
1 |
Do we have to take care of laws and regulations in this data and analytics project? The first critical step is to determine whether any legalizations or regulations are applicable to the project. |
Yes No Write extra/additional information here: |
|
2 |
Is the data that we want to use available in an ethical manner and is that data suitable for usage? We must be mindful of who owns the data and ensure that it is used in the manner intended by the owner! |
Yes No Write extra/additional information here: |
|
3 |
Is it possible to identify and check bias in the data that we have collected or used for our models? People can be biased by their origin, and the same is true for data and the application of algorithms and business rules. The data we collect and store is not as objective as we believe! When using algorithms and business rules, we should be aware that the data we use to train the models can have an impact on people and possible human bias magnifies, which results in undesirable outcomes. To conclude, we must be able to identify, test, verify, and discuss the results. |
Yes No Write extra/additional information here: |
|
4 |
Can we identify and demonstrate bias in our created model or in the used data? When we use data and apply various models, we may have used data that is biased. When we use that specific dataset and apply the learning models, the model produces biased results; for example, a bias based on gender, age, equality, or racial elements. We must be aware that we must consider documenting, discussing, and evaluating our data usage choices. The message here is to avoid doing things simply because you can! |
Yes No Write extra/additional information here: |
|
5 |
Can the legal rights of individuals be impinged by the use of data? When individuals’ legal rights are at stake, the organization must have permission and the right to use data for specific purposes. For example, suppose an organization provides data to its direct partners, but privacy conditions other than the internal data usage may be addressed here. In the event of an incident, for example, they know address details and more detailed information about people, but certain data is not shared to protect those people’s privacy (such as names, address details, and other things by which someone can be individually identified). It could also happen internally, for example, through logging information that is known at the employee level but is shared with users at the department or concern level. We should be aware of this in order to protect the privacy of each individual employee. |
Yes No Write extra/additional information here: |
|
6 |
Are we able to understand that the data that we want to use is suitable for the purposes of our project? When we begin an analytics or data science project, we must understand and ensure that the data we intend to use is appropriate for the purpose of our projects. Following that, we should be able to verify and validate the data for our project. For example, when records or values are missing, the outcome or our algorithms and business rules can have a significant impact on the results, potentially producing a biased result. |
Yes No Write extra/additional information here: |
|
7 |
Do we have a multi-disciplinary team present to discuss the apparent dilemmas regarding the possible usage of algorithms and the possible outcomes? When it comes to assessing and discussing our own work, we need to discuss the dilemmas and outcomes that can occur with a multi-disciplinary team. |
Yes No Write extra/additional information here: |
|
8 |
Explainable AI by Design. Are we able to define the role of the algorithm used and what processes are being followed (procedural transparency)? It is critical for data engineers and data scientists who train models to understand the model’s behavior in order to detect errors or weaknesses. This is why we must correctly describe the used algorithms or business rules. When data scientists and data engineers train a model, it is critical to understand the model’s behavior. They must identify any flaws or errors. |
Yes No Write extra/additional information here: |
|
9 |
Explainable AI. Are we able to explain the algorithm or business rules to the guardians, stakeholders, and others with whom they are concerned? Explainable AI is defined as the ability of a person to comprehend the reason for a decision. The decision is influenced by algorithms and business rules. To be able to understand the model’s decision, we must be able to explain the decision. We can do so by design, but we can also do it post hoc by using an algorithm to understand the black-box model. |
Yes No Write extra/additional information here: |
|
Addition and/or explanation | ||
Intermezzo – tax office profiles ethnically
This is a translation of news articles and reports published in the Netherlands and beyond. We’ve cut those articles and news flashes down to the essentials of the story.
The Tax and Customs Administration was already aware, at the start of 2019, that a selection was made based on non-Dutch ancestry in fraud investigations involving childcare allowance. Despite repeated questions from the House of Representatives and the media about possible ethnic profiling by the service, the tax authorities continued to deny this for more than a year.
Several organizations performed an investigation into how this situation could occur. Amnesty International concluded (just like the other investigators) that a majority of things went wrong in this particular case. Therefore, thousands of people were affected wrongly. Above 30,000 people were accused of fraud and they had to repay the received allowances back to that tax office. As a result of this situation, people lost their homes as they could not pay their mortgages or rent anymore and their jobs. The children's protection organization got also involved and due to the earlier-mentioned issues, children were displaced from their parents and homes..
The risk model was used to estimate the risks of fraud or improper benefit utilization. For example, in the algorithms, Dutch citizenship was used to identify and estimate the possible risk. However, having Dutch nationality is not a condition (or business rule) for receiving a childcare allowance. The model was also used by a special team within the allowances department. This team assessed signs of abuse and then determined whether additional investigations by special fraud teams were required. The Tax and Customs Administration determined which applications for rent or childcare allowance had to be processed manually using the contentious risk model. Employees of the Tax and Customs Administration examined nationality, family composition, and income level, among other things. But using a nationality (or a second nationality) is discrimination and, therefore, prohibited. The Authority previously found the Tax and Customs Administration to be discriminatory. The good action here is that the model has not been used since July 2020.
The key message here is that using algorithms for classifying people is an ethical concern. When those initiatives are planned or discussed, we should take the mentioned concerns and potential risks into account. Determining the danger of risks when using personal data, outdated data and lack of control are key elements to consider, and by all means, be vigilant.
Here is a list of the websites we’ve used for this intermezzo:
- https://www.amnesty.nl/actueel/toeslagenaffaire-is-mensenrechtenschending-zegt-amnesty-international
- https://autoriteitpersoonsgegevens.nl/nl/nieuws/werkwijze-belastingdienst-strijd-met-de-wet-en-discriminerend
- https://nos.nl/artikel/2364658-nooit-meer-een-toeslagenaffaire-wat-moet-er-nu-gebeuren
Let’s move on and summarize the chapter next.
Summary
After reading this chapter, you should have a better understanding of data security, data privacy, and data ethics. We’ve discussed the various topics from a more pragmatic standpoint.
We took the three topics and created tables with questions that you can use when you are about to begin a data and analytics project. It is prudent to address and answer these types of questions because incorrectly applied outcomes can cause harm to individuals.
Additionally, we included some real-life stories that were published online by newspapers or other news sites to help you understand what can go wrong when you use data incorrectly.
As we need to act on the created insights (see Chapter 7, Designing Dashboards and Reports), we will help you understand how to turn insights into decisions. We will do so in the following chapter. We will cover a seven-step framework to help you to turn insights into decisions.
