CHAPTER
3
Malware Deployment
Before malware can do any real damage, it must reach the target system. To reach a target system, the attackers use or abuse different technologies, some of which are legitimate while others are designed purely to deploy malware.
Malware deployment is just as important as the actual capabilities of malware. Without the deployment technology, malware, no matter how sophisticated, will be rendered useless. Think of malware as soldiers. For them to reach their target site, they must be deployed effectively and oftentimes under stealth. This is why capable countries invest in air, land, and sea deployment vehicles for the purpose of successfully carrying soldiers to their target destinations. This is the same concept when it comes to malware deployment technologies. The attackers invest heavily in the most effective and stealthy deployment technology to deliver their malware. One example of this is the exorbitant price of a newly discovered, zero-day vulnerability.
Malware deployment does not concern itself with the execution of malware, although some deployment technology has that capability. It is mostly concerned about malware reaching its intended target. For instance, in the early days of computer viruses, the often-used technology to deploy or spread malware was the floppy disk. The disk carried infected host files, and an infected disk, once placed inside a disk drive, was considered a successful deployment. The malware had reached its target. Infection of the target system was possible because the infected files reached the target, and if a user executed these infected files, the result was a compromised system.
As previously stated, some deployment technology has the capability of automatically executing malware, resulting in deployment and infection. Going back to the disk example, if a disk is infected with a boot sector virus, simply accessing the disk will execute the boot sector virus, causing system compromise. There is no need for a user to execute any infected files to infect the target system.
NOTE
Successful malware deployment does not equal successful malware infection.
The computer virus was successfully deployed using physical media, the disk, to reach its target. The ability to execute the malware once it reaches a target is an added bonus, especially if a deployment technology has this capability. The physical media, and other techniques or technology used to deploy malware are called malware infection vectors.
In this chapter, I will discuss what a malware infection vector is and how it is used by attackers to deploy malware to their targets. I will identify the different dimensions of a malware infection vector that serve as a guide to attackers on which specific infection vector to use in their attack campaigns. And most importantly, I will enumerate the most common malware infection vectors that are being used by attackers regardless of whether their campaign of attack is opportunistic or targeted. I will then conclude the chapter by identifying the different characteristics that make a technology suitable for becoming a malware infection vector.
Malware Infection Vectors
An infection vector (or a combination of several infection vectors) is what is behind the spread of malware. It is responsible for the distribution and proliferation of malware. In a threat ecosystem, having the right infection vector is what separates success from failure of malware deployment.
LINGO
A threat ecosystem is a collection of different technologies that attackers use to conduct attack campaigns. Each of these technologies supports the malware and each other. If one fails, so does the attack campaign.
There are a lot of infection vectors at the disposal of attackers. I will enumerate these different infection vectors later in the chapter. To help attackers choose which one is best for their specific needs, they consider the different dimensions of each malware infection vector.
Infection vectors are chosen based on the different dimensions they offer. The following are the important dimensions of an infection vector:
![]() Speed
Speed
![]() Stealth
Stealth
![]() Coverage
Coverage
![]() Shelf life
Shelf life
Speed
The speed by which infection occurs is important to the attackers. Depending on the attacker’s intent, she might choose the slow physical media infection vector that relies on physical transport by humans or the faster e-mail infection vector that relies on the speed of different network connections to reach a target. If time is of the essence, the faster infection vector is always chosen. If there is no rush and the target system to be compromised is not connected to any network systems, the physical media might be the better alternative.
The speed by which a malware can reach a target is quite scary. Before everybody was connected to the Internet and everyone had e-mail, malware infection was slow. Almost all malware relied on physical media, and malware infection was not a big thing. A well-known researcher and a personal idol of mine once said in an interview that computer viruses are an urban legend, like the crocodiles in the New York sewers, and one U.K. expert claimed that he had proof that computer viruses were a figment of the imagination.1 Systems still get infected, but the impact is not as big to garner any attention. There were infections that are well known during those times but not as impactful as the infections that occur when everybody got on the World Wide Web.
With the advent of e-mail and so many computers and devices connected to the Internet, malware now has a faster infection vector in e-mail. This means malware has the ability to reach targets in an instant. With this speed, a malware coming from the East Coast can reach a target on the West Coast, or in any part of the world for that matter, in mere seconds.
The speed and coverage of an e-mail infection vector make it possible to have a worldwide malware outbreak.
Stealth
A successful infection vector is one that cannot be detected easily and can bypass most security solutions. The stealthiest infection vector by far is vulnerable software. A well-crafted exploit can easily bypass most security hurdles and take advantage of the vulnerable software’s permissions and privileges. It is always a challenge to detect a zero-day vulnerability. In most cases, it takes a long time to detect the vulnerability and even more time to fix it. This is why zero-day vulnerabilities fetch a big chunk of change in the underground market. Software publishers would rather pay researchers who discover zero-day vulnerabilities rather than know about the zero-day after a massive infection has hit.
LINGO
Zero-day vulnerabilities or zero-days are vulnerabilities that have been discovered but are still unknown to the software publisher and to the information security industry at large.
In some cases, physical media can prove to be the stealthiest infection vector of all. For example, a target company that does not have any security policy in its endpoints to prevent the use of unauthorized universal serial bus (USB) sticks or external hard drives can easily fall victim to a malware delivered through infected physical media. No matter how state-of-the-art or best-of-breed security solutions are used to guard the network from infiltration and infection, the lowly physical media can easily infect an endpoint, which can serve as the staging ground for further infections within the network.
Coverage
Coverage means the number of targets an infection vector can reach. Is it a single target? Is it in the tens of thousands? Is it in the millions across geopolitical borders? All of these are possible depending on the infection vector chosen.
In an opportunistic attack, the desired coverage is as many as possible. Therefore, an e-mail spam carrying the malware or linking to the malware is often used as the infection vector. Think of the worldwide malware outbreaks that the world saw in the nineties and early part of the 21st century such as the Melissa worm, the ILOVEYOU worm, and MYDOOM, among others. Most of the malware was delivered by e-mail. Anybody who has an e-mail address is a potential target.
LINGO
An opportunistic attack is an attack targeting everybody. Whoever stumbles upon the infection vector and becomes compromised becomes the attacker’s victim.
In a targeted attack, the desired coverage can range from a single person to a handful of targets. If the target is a specific person or position within a target entity, the malware infection vector needs to deliver the malware to only one target. If the target is a group of employees, the malware infection vector might be crafted to deliver malware to only this small group. For example, an attacker who wants to compromise a small subsidiary that has ten employees will target only those ten employees. In most targeted attacks, the smaller the number of compromised systems, the higher the chance that the malware will stay hidden and not raise any suspicion.
LINGO
A targeted attack is an attack focusing on a specific entity chosen specifically by the attacker. Targets are usually executives or important people within an organization.
Shelf Life
Some malware infection vectors have an expiration. Take, for instance, software vulnerability. A patch that closes the software vulnerability can render all exploits that take advantage of it useless. The software vulnerability will not be as successful in deploying malware as it was before the patch was applied.
An e-mail that is captured that delivers malware loses its freshness immediately after a solution to block it gets released.
This is why time is always of the essence when it comes to deploying malware. It is a race between the attackers and the researchers. Once a vector is found out, it is only a matter of time before that specific infection vector is rendered useless, and it is up to the attackers to come up with a new one.
Types of Malware Infection Vectors
An attacker can deploy malware using one or a combination of different infection vectors that includes, but is not limited to, the following:
![]() Physical media
Physical media
![]() E-mails
E-mails
![]() Instant messaging and chat
Instant messaging and chat
![]() Social networking
Social networking
![]() Universal resource locator (URL) links
Universal resource locator (URL) links
![]() File shares
File shares
![]() Software vulnerabilities
Software vulnerabilities
In analyzing malware, it is also important to determine the infection vector the malware used to deploy itself because it completes the story of how the malware reached the target and it answers the most important question of how a system got infected. This information is valuable to security professionals who are in charge of securing a network or establishing a network perimeter defense. Sometimes this is evident based on the behavior that will be extracted from the analysis, but sometimes it is not, especially if the deployment technology is completely decoupled from the malware. A decoupled deployment technology is an infection vector that is not initiated by the malware but controlled by the actors behind an attack.
A decoupled infection vector is a deployment technology separate from the malware itself. Decoupled infection vectors can be used to deploy different kinds of malware and are not dependent on any malware that they deploy.
For example, an e-mail carrying a malware in the initial stages of infection is considered a decoupled infection vector if the malware does not initiate the sending of that e-mail. Since the malware does not initiate the e-mail, the e-mail won’t be part of the analysis because it’s not possible to know it was involved. This is similar to how a person carrying an infected disk to a computer won’t be seen by analysts after the fact. But if the malware when active sends out more e-mail carrying itself, then that e-mail infection vector is not decoupled because you can see that behavior once the malware is analyzed.
NOTE
Sometimes it is a challenge to determine how a system got infected from the malware alone, especially if the malware was deployed using a decoupled infection vector.
Physical Media
Physical media are the main infection vectors of computer viruses. Since computer viruses are mostly file infectors, the only way they can reach another system is to be manually carried to that system through the use of a disk.
A malware with no capabilities of spreading through any other means than file infection usually uses this infection vector. It is already assumed that the infection vector is physical media since there is no other way for this type of malware to get into another system. But if a malware infects physical media such as the boot sector or sets itself up in the physical media to take advantage of the autorun capabilities of the target OS, then that is clear evidence the malware uses physical media as its infection vector. But what if the malware does not exhibit these capabilities? Is it still possible to use physical media as an infection vector? The answer is yes.
There have been cases where malware that has no routine to infect files or boot sectors is deployed using physical media. For example, someone giving away USB sticks outside of an office building, a school, or anywhere for that matter, can simply put a sophisticated malware on the USB stick hoping that somebody will put it in a system and start the infection process. In this case, the USB stick is a decoupled infection vector because the malware did not put itself on the USB stick; therefore, no traces of this activity will be found during analysis.
Be wary of free USB sticks even at security conferences; they might be carrying more than what they’re supposed to be carrying.
E-mails
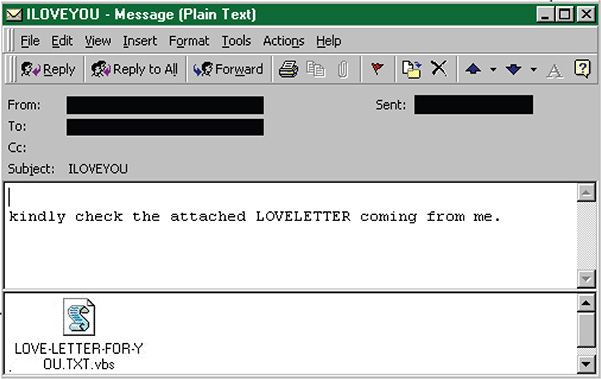
One of the fastest ways to reach someone is through e-mail. The same thing goes for malware. Anyone with an e-mail address is a potential target. Lots of noteworthy malware went on to produce worldwide outbreaks because of e-mail; among them are the ILOVEYOU worm, as shown in Figure 3-1, and the Melissa worm.
Figure 3-1 ILOVEYOU worm.
If during analysis it becomes evident that a malware accesses the default mail client, accesses the user’s address book, or uses Simple Mail Transfer Protocol (SMTP), chances are that malware uses e-mail as its main infection vector to spread to other systems.
Even with lots of e-mail security solutions available, the use of e-mail as an infection vector is still popular with attackers because most solutions can be easily bypassed and the e-mail vector is cheap and fast. Plus, there are still lots of users who are easily fooled by simple social engineering tactics. Figure 3-2 shows an example of a socially engineered e-mail vector created for an opportunistic attack.
Figure 3-2 Socially engineered e-mail vector for opportunistic attack.
There are two types of attacks: targeted and opportunistic. A targeted attack is geared toward a specific company, individual, or entity and usually takes ample preparation from the attackers before it is executed. An opportunistic attack, on the other hand, is a form of attack that is waged to as many potential victims as possible. It does not have a specific target. The main goal is to have as many system infections as possible.
Instant Messaging and Chat
Instant is the magic word when it comes to IM and chat. It’s real time. Although e-mail is fast, slow e-mail servers can delay the delivery of a malware or drop the infected message altogether because of non-compliance with e-mail policies or being blocked by mail security products. This is not good for the attacker.
Like e-mail, IM and chat have the capability of sending not only text but also files. But when used as infection vectors, IM and chat usually deliver malicious links pointing to a malware-serving domain or a drive-by download site. In this case, the malware does not necessarily send a copy of itself to propagate. It can be setting up a new malware to be installed on a target PC. It depends on what malware is being served by the malicious link.
LINGO
A malware-serving domain is a domain that links to a network resource that hosts malware. A drive-by download site installs malware once a victim visits that site.
Instant messaging and chat take advantage of trust. A compromised system can make use of the victim’s IM account to send malicious links or files to that victim’s entire list of friends. The receiving friend will think that the link or file is legitimate because it came from their friend. Some of the target friends won’t think twice about clicking the link or downloading and executing the transferred file.
The two popular ways a malware uses IM and chat to spread is by hijacking a user’s IM account once the machine is infected and by disguising itself as an IM client.
Social Networking
Social networks are popular. They not only are used to connect with someone but also are used to promote products. The more registered users a social network has, the more valuable it is, and the number of users is directly proportional to its popularity. Some social networks are so popular that the number of registered users actually exceeds the population of some countries, as shown in Figure 3-3.
Figure 3-3 Population size of social networks relative to countries. (Source: www.pingdom.com.)
Social networks offer features that are desirable to attackers. Among them is the ability to send instant messages and post updates in the form of feeds. The feeds can be visible to friends only or to the public. The feeds are desirable to the attackers because the links remain posted until they are taken down; they are just there waiting for unsuspecting users to click them.
Social networks also take advantage of trust. Attackers can post malicious links to the compromised account’s wall, and posts can be made to a friend’s feed wall. That friend will think it’s legitimate, and chances are he will click that link.
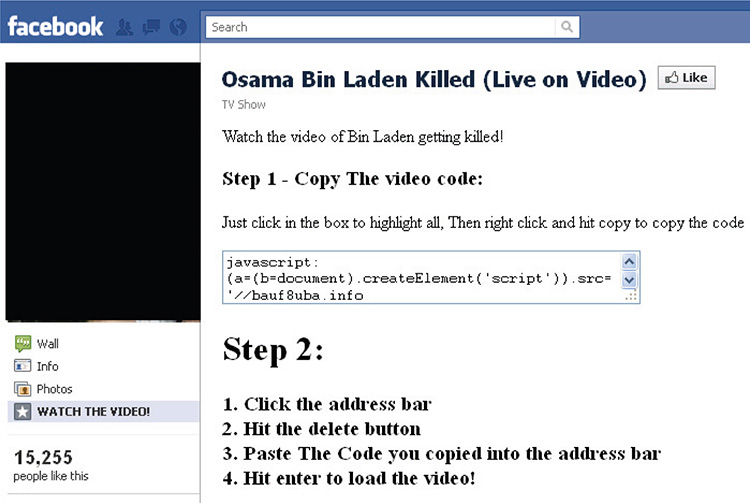
A malware that looks for social network accounts or requires a certain user to be logged in to a social network for it to function as intended usually uses social networks to spread. But not all malware that uses social networks to spread will show this feature, especially if the social network is used as a decoupled infection vector. One example of this is when the attackers create a social network page about a celebrity, a new movie, a new product, or breaking news. These pages will often attract users to it. The more relevant the subject of the page is, the more users will be drawn to it. Chances are, some of these potential victims will click a link or download a file from that page. Figure 3-4 shows a social network page created by attackers to lure visitors to do what the page says. The result of course is infection.
Figure 3-4 Fake Osama Bin Laden video page on a social network site.
TIP
Be wary of clicking supposed videos in social network feeds. The malicious ones are not videos but graphic files pretending to be videos with play icons in the middle. They can lead to infection.
URL Links
Another way of delivering malware to a target system is through URL links. Attackers use URLs to point to a webpage containing malware or even directly to the malware itself. In the case of the latter, the malware is saved to the file system. In the worst-case scenario, it gets executed immediately, a classic example of a drive-by download site.
A URL link is a special kind of infection vector. It is both an infection vector and a payload of another infection vector. Infection vectors that have URL links as their payload are called infection-vector-hosting (IVH) infection vectors and include e-mail, instant messaging, social network feeds, and documents with links.
TIP
When investigating malware that uses IVH infection vectors, be on the lookout for links. These links usually contains new version of the malware or some of its components.
Sometimes static analysis can reveal some of these URL links, especially if the malware is not encrypted. Otherwise, dynamic analysis with network monitoring tools is the only way to reveal these malicious URL links.
File Shares
Peer-to-peer (P2P) file sharing is commonly taken advantage of by malware to get into the system of other users. A malware will drop a copy of itself in the public-facing file share folders. This makes the malware available to all peers that are downloading files. To make sure that other users will download and execute the files, the malicious files use enticing names such as MSOfficeCrack. EXE, DOTAFullVersionNoAccountNeeded.EXE, and more. The idea is to social engineer its way into a target user system by making itself desirable for download.
A malware that looks for common P2P file share folders and drops itself there during execution uses this kind of infection vector.
Software Vulnerabilities
No software is perfect. All software has bugs, and some have flaws. Some are known, while others are not. Some are critical, while others are minor. Depending on the severity of the bug, it can have unpredictable and unintended results. The attackers, with some of them being software developers themselves, recognize the value of an unknown or undiscovered critical bug waiting to be exploited in certain software.
It is important to know the difference between a software bug and a software flaw. A software bug is an issue with a feature that is not functioning as intended, while a software flaw is an error in the design and architecture of the software. A bug can be fixed by a patch, but a flaw can be fixed only by a complete redesign of the software.
The advantage of using software vulnerabilities as an infection vector over other infection vectors is that it significantly lowers, if not totally eliminates, the need for human interaction. Typically, it results in the automated execution of malware, which is what is considered the most effective way of infecting a system. It also takes advantage of software that is whitelisted in the system, thus evading any sort of application control security products.
LINGO
Application control is also known as whitelisting. The concept of this security product or feature is to let only known whitelisted applications to run in a system.
Lots of material covers software vulnerabilities already. With this in mind, I will focus on those that are used to install malware on a system.
To take advantage of software vulnerabilities, the attackers use an exploit. An exploit can be a piece of code or a chunk of malformed data that causes the target software to behave in a way not intended by the software manufacturer. The most common exploit is the one that takes advantage of buffer overflow.
NOTE
An exploit is not a vulnerability. An exploit is something that takes advantage of a vulnerability.
Buffer Overflow
Software consists of two distinct components: code and data. Code is the set of instructions that makes use of data. During data manipulation, software often makes use of a temporary data storage called a buffer. A buffer is created to hold data and nothing more. But sometimes, because of programmatic error, more data is written to the allocated buffer. This results in data overflowing to adjacent buffers. This condition is called a buffer overflow. Attackers take advantage of this by overflowing the buffer with code instead of data. The buffer is overflowed in such a way to transfer the control to that code, thus executing it. The often-used buffer overflows are
![]() Stack overflow
Stack overflow
![]() Heap overflow
Heap overflow
It is important to note that a buffer overflow can be triggered using a malformed file. The malformed file is the one that is deployed by the attacker. Once this file is opened using the vulnerable application, the data from the malformed file overflows the buffer. Getting hold of a malformed file during malware hunting helps in understanding how the vulnerable application is being exploited.
Stack Overflow The stack is a last-in first-out (LIFO) data structure. This means the data that is pushed last onto the stack is what is popped out first. It is aptly called a stack because it is stacking data on top of one another. Think of it like a stack of plates. The last plate that is put on the top of the stack is the one that is used first. Because of its LIFO nature, the stack is often used to store temporary variables, making it efficient to use with program functions.
Stack overflow is the result of overflowing the buffers on the stack to get control of the execution flow of the program. This is made possible by overflowing the buffer enough to overwrite the value stored in the return address (RET). To understand this concept, let’s look at how program functions use the stack.
A program function is like a small program within a program. It’s independent, compartmentalized code that performs specific operations using data passed to it and then returns the result to the main program. Since a function has to manipulate data, it utilizes the stack as a temporary storage for this data. When a function is called within a program, it pushes all the data into the stack, including the return address. To understand what the stack looks like, see Figure 3-5.
Figure 3-5 What the stack looks like during a function call.
The return address is where the instruction pointer is currently pointing when the function is called. This is important because after the function has finished processing, the execution flow has to go back to that return address so the main program can continue its execution flow. This value is stored in RET. When the function finishes, the value stored in RET is passed to the instruction pointer so the main program can go back to its execution flow before the function was called. So if the attacker is able to overflow the buffer and as a result overwrite the value stored in RET with an address value that points to malicious code, the instruction pointer will point directly to the malicious code, resulting in the malicious code being executed.
Heap Overflow The heap is dynamically allocated memory space. The logic behind this is that the amount of memory needed by a program is not known in advance; therefore, memory has to be allocated as needed and freed up when not needed. The difference between a heap and a stack is that a heap does not have a return address like a stack does. This makes the technique used to control execution flow in stack overflow useless. Overflowing a heap instead results in data and pointers to other data or program functions being overwritten. As a result, the attacker can overwrite these pointers to point to malicious code instead of the original location.
Privilege Escalation
The ability of a software vulnerability to deliver and install malware in a system depends on its getting privilege escalation. Privilege escalation is the process of gaining access to system resources that are accessible only to a superuser or system administrator. With this, the attacker can do pretty much anything with the system, including installing malware.
Privilege escalation is achieved when the exploited, vulnerable software (or some of its components) is already running on escalated privilege or it has access to system resources or functions running on escalated privileges.
Zero-Day Vulnerabilities
The knowledge of a program’s vulnerabilities that can be exploited is often kept private by the attacker. This is known as a zero-day vulnerability. A zero-day vulnerability is an exploitable hole in an operating system, software, or even hardware that has no solution and has been discovered by those other than the manufacturers or publishers of the vulnerable object. If an independent researcher has discovered a zero-day vulnerability, the next step is to report this to the manufacturer or publisher so a patch or a new minor version can be released that fixes the vulnerability. Some software manufacturers even pay for this kind of information, making vulnerability discovery a good independent business for software hobbyists. But it’s a different story if an attacker discovers it. It is usually kept secret to be used in future attacks or to be sold to other cybercrime groups. Keeping it a secret creates immense value because this vector’s shelf life depends on how long it is kept a secret and how long before a patch is released to fix it.
There have been cases where a vulnerability has been public already but the patch to fix it was pending release; thus, any malware that utilized this vulnerability still enjoyed some level of success. Unfortunately, the only way to prevent vulnerable software with no available patch or fix from being exploited is to uninstall or not use it, but in cases where the software is vital to an enterprise’s operation, this is usually out of the question.
A good way to stay abreast of the latest vulnerabilities is by visiting http://cve.mitre.org.
Potential Infection Vectors
It is important to note that any technology can be used as a malware infection vector as long as that technology possesses one or a combination of the following:
![]() The ability to process data from an external source
The ability to process data from an external source
![]() The ability to move data to a chosen destination
The ability to move data to a chosen destination
![]() The ability to share data
The ability to share data
Who knows? In the span of your research and analysis, you might discover a new malware infection vector.
Recap
Malware deployment is an important part of the threat ecosystem. As stated previously, it is as important as the actual capabilities of malware. Without the deployment technology, malware, no matter how sophisticated it is, would be rendered useless.
Having familiarity with the different malware infection vectors enables analysts to determine how the malware spreads. This answers the important question of how the victim got infected and also helps security professionals in securing networks.
In this chapter, I discussed what an infection vector is and how attackers use it to deploy their malware. I enumerated the four dimensions of a malware infection vector, which are the following:
![]() Speed
Speed
![]() Stealth
Stealth
![]() Coverage
Coverage
![]() Shelf life
Shelf life
Depending on the attacker’s needs, an infection vector is chosen based on these dimensions. It serves as a guide for the attacker on which appropriate infection vector should be chosen to deploy their malware.
I then enumerated the most common infection vectors that are used by the attackers to deploy their malware.
![]() Physical media
Physical media
![]() E-mails
E-mails
![]() Instant messaging and chat
Instant messaging and chat
![]() Social networking
Social networking
![]() URL links
URL links
![]() File shares
File shares
![]() Software vulnerabilities
Software vulnerabilities
An infection vector can be coupled with or decoupled from the malware. A coupled infection vector can easily be revealed during malware analysis because the malware initiates the use of the vector. A decoupled vector is much more challenging to discover; because it is not initiated by the malware, no evidence of it will appear during analysis. The attackers usually initiate the use of a decoupled vector.
It is important to note that most infection vectors used by attackers are legitimate services that are essential to the operation of any network system. These services cannot be blocked simply for the purpose of stopping malware. The key here is to understand how these technologies are being used by attackers to deliver their malware and then find a solution.
Any technology can be used by attackers to deploy malware, which is why I concluded this chapter by discussing the potential of any technology to be used as an infection vector. It actually depends on the following characteristics:
![]() The ability to process data from an external source
The ability to process data from an external source
![]() The ability to move data to a chosen destination
The ability to move data to a chosen destination
![]() The ability to share data
The ability to share data
Finding out which infection vector an attacker used to deploy malware completes the story of system compromise. And most of the time, it is important to complete the story.
1 1988 The Game Begins by DaBoss: http://www.cknow.com/cms/vtutor/1988-the-game-begins.html.