CHAPTER 15
Network Security
In this chapter, you will learn about
• Common network vulnerabilities, threats, and risks
• Tools for helping secure networks
• The importance of user authentication
• Secure transmission protocols and virtual private networks
• Wireless networking security
As an AV professional, you are not necessarily in the network security business. Many IT professionals aren’t either. In lots of organizations, network security has grown into a practice all its own.
But as you probably know, security is pretty important to the people who use and operate enterprise networks. It’s important to your Internet-connected personal computer. Which is why, when you introduce AV systems to a network, someone will want to know about the security ramifications. Understanding network security risks, and the ways in which IT and network professionals protect their enterprise networks, is critical to ensuring not only a secure AV system design but a cooperative relationship between AV and IT.
Let’s face it—networks are wonderful things. They make resources accessible. You no longer have to be physically present at a device to use, configure, or troubleshoot it. The problem is, unless a network is properly secured, neither does anyone else. And if the wrong people gain access to network resources, they can do a lot of damage.
Security is often cited as the number one reason why IT professionals are concerned about attaching AV devices to an enterprise network. What are they so concerned about? In this chapter, you’ll find out about common security risks and the solutions network administrators use to mitigate them.
Vulnerabilities and Threats
Securing a network is a complex task. There are so many variables to worry about. You have to ensure that external attackers can’t gain access to the network. You also have to consider what authorized users might do (purposely and inadvertently). Most organizations have resources that must be protected even from their own employees. Network attacks can originate in the virtual world (aka cyberspace) or the physical world. Someone unplugging a switch can bring a network down just as surely as a virus.
Every network has vulnerabilities—outdated protocols, underdeveloped hardware and software, poor system design—that leave gaps through which attackers can sneak. And every network faces threats—hackers, malicious software, other intruders—that will harm the network or its systems given the chance. Vulnerabilities + threats = risks. Risks are the potential problems that network engineers must mitigate if they want assurance that the network will function reliably.
Security is a major concern for networking professionals, which often leads to the perception that an organization’s IT staff wants as few people as possible to have access to any network resource. It’s a security best practice to limit network access only to those who need it. The only truly secure system is one that’s turned off, but that’s no good to anyone. So networking professionals must balance security and integrity against availability. They must constantly ask, “Where do security risks come from? And what common vulnerabilities do threats look to exploit?”
Network Vulnerabilities
You know that old horror movie plot? The babysitter calls the police because she keeps getting scary phone calls and the police tell her, in essence (close-up on her terrified face), “The calls are coming from inside the house!” Some network vulnerabilities originate in the network itself, the result of poor configuration and device setup. Let’s review several of these problem areas.
Unprotected Network Shares
An unprotected network share, also referred to as an unprotected shared resource, is a network share that is open to all users without constraint—essentially, without security. For example, a file server that doesn’t require a password or user-account credentials in order to gain access is an unprotected network share. There are many unprotected network shares on enterprise networks and across the Internet. If you upload a folder of media clips and allow anyone to view and edit them, you’ve created an unprotected network share.
Such shares are an open invitation to intruders. Anyone can destroy the integrity of the data kept there, and sophisticated attackers may be able to use the unprotected share as a launching point to attack other resources on the network. There is no good reason to leave a share unprotected.
Open Ports
Physical and logical ports should be protected. Physical ports include wall jacks for connecting to the local network, console ports on critical network components, and common interface access ports on computer systems, such as universal serial bus (USB) ports. If an intruder can gain access to the network through any of these ports, he can wreak havoc.
In a highly secure environment, such as a government installation, these ports should be dead or disabled until needed. You can usually shut down or disable USB ports and other media access ports at a hardware level to provide better security.
A wireless access point (WAP) is another physical port through which bad guys can access a network. Some intruders try to get to a network by adding rogue access points to existing wireless networks. Wireless networks require regularly scheduled monitoring and surveying to ensure that only permitted WAPs are present.
Finally, intruders can also access a network through logical ports, those Transport Layer ports through which applications send and receive data (see Chapter 9). In general, you want to disable ports that a networked device doesn’t use or need. That way, intruders won’t be able to send unwelcome packets via those ports. For example, port 80 (HTTP) is used by web servers so browsers can access information. If a device isn’t functioning as a web server, then port 80 should be disabled.
Zero Configuration
Zero configuration (zeroconf) is a networking strategy that allows devices to join a network without requiring configuration at the user’s end. It distributes IP addresses, provides name resolution, finds and lists available network services, and distributes multicast addresses without the help of traditional DHCP, DNS, directory, or multicast servers.
Zeroconf is a link-local technology—it’s only used to distribute private addresses within a LAN. It is intended for home, small office, and ad hoc networks, not for enterprise networks or high-security environments. It’s also not recommended for wireless networks because it could allow unwelcome devices to easily join the LAN.
Zeroconf provides a “better-than-nothing” level of security, but the addresses and names it hands out don’t persist. It doesn’t play well with other security protocols that require administration because there’s no way to reliably identify zeroconf devices. That means there’s no way to administer access controls for devices that join a network using zeroconf. Long story short, zeroconf should not be allowed on enterprise networks because it weakens other security measures.
Social Vulnerabilities
Even the most locked-down network is only as secure as the people who use it. When all system patches are up to date, strong antivirus and antimalware solutions activated, and a diligent security management policy enacted, the users and administrators are the weakest security links left. Every person has a role in security. Without their diligence and cooperation, a security program will fail and systems will be exploited.
Social Engineering
Companies spend billions of dollars annually to train their users on network security awareness. Still, intruders can obtain crucial network information just by asking. Social engineering is a broad term used to refer to gaining access to network resources through human interaction. For example, to gain access to a facility, an intruder might walk up to a door with his arms full. A helpful employee with an access card then opens the door. To discover a password, the intruder might watch someone type or might simply ask a user for his or her password. Have you ever written a password down on a piece of paper and then thrown it away? Dumpster diving is a form of social engineering that only requires access to someone’s trash.
Protecting a network from social engineering requires constant vigilance. Clearly, though, some organizations and users face a greater risk from social engineering than others. Administrators have more access than other users, so they must protect their passwords more carefully. Sites that house classified or legally protected data should have stricter physical access requirements than other sites.
Email Attachments
The ability to send and receive attachments in email is invaluable but potentially dangerous. Email attachments are commonly used to create an indirect attack against a computer system. Often, malicious email attachments rely on social engineering to encourage users to download them and execute the programs within (e.g., a message that reads “You won’t believe this amazing video!”). Email filtering catches most malicious content, but the best defense is awareness training for users. Users should not open emails with or without attachments from unknown and unsolicited sources.
For some organizations, email attachments present enough of a risk that they are forbidden on the organization’s email server. Most organizations find them too useful to block, though. These organizations take a more relaxed approach. For example, they may limit attachments above a certain size but allow others.
Network Threats
There are many ways to gain unauthorized access to a network, through both network and social vulnerabilities. Who does this? What threats might exploit these vulnerabilities? Networks must protect themselves from threats both without and within.
External Intruders
External intruders come in many flavors—technically skilled hackers and crackers, curious individuals, amateur computer vandals, and so on. In the past, breaking into or disrupting a system required advanced skills that most computer users didn’t have. Not so today. Untrained intruders—sometimes called script kiddies or script bunnies—use premade applications to execute attacks against networks. Little expertise is required to attack a network. All they have to do is download a script, enter some simple parameters, and click OK. Then the attack begins. External intruders may specifically target an organization’s network, looking for potentially valuable data like credit card numbers or details on new products. They may also target networks at random, though, looking to get lucky and find something interesting or useful. Some network attacks are nothing more than random acts of network vandalism—destruction for destruction’s sake. External intruders have a wide variety of motives and methods, making protecting against them a significant challenge.
Internal Threats
Not every malicious attack originates outside a company’s network. Some of the most dangerous risks to the network are those that originate within. Authorized users may intentionally steal or destroy network data. A disgruntled, desperate, careless, or uninformed user can do a lot of damage on a network. They may also accidentally or intentionally give their account credentials to an unauthorized user. You can protect against carelessness and ignorance through training: make sure users know what information they should not share and what damage might result if they do. You can only guard against employee malice so much, however. This is why users are given access only to those network resources they need for their jobs—it limits the damage a malicious employee can do. Network administrators also monitor employees’ network activities, looking for suspicious or potentially damaging behavior.
Common Network Risks
Threats and vulnerabilities come together to form risks. Network threats are very creative—intruders are constantly devising new methods of attack. However, the most common network attacks fall into a few broad categories.
Denial of Service
One of the most common risks to a network is the denial-of-service (DoS) attack. Most DoS attacks come from external attackers, and they are designed to deny access to a network resource such as a website.
DoS attacks are typically accomplished by transmitting more data packets than a network device can manage. They tend to target perimeter routers—an organization’s gateway to the Internet—and come in many varieties, depending on the target. Internet Control Message Protocol (ICMP) attacks target routers; “email bombs” go after email servers; and “fraggle” attacks send fragmented packets to a target host.
Say an attacker wants to disable a perimeter router. The attacker chooses what’s called a “smurf” attack (named for the source code this type of attack originally used). The smurf attacker sends an ICMP broadcast to the address of the targeted network device. To intensify the attack, the attacker chooses several “reflector” devices at random. The ICMP message looks as if it came from these reflector devices instead of the actual source. Devices typically won’t respond to unsolicited messages. Because these reflectors never actually contacted the router, they won’t respond to messages from the router. When the router attempts to respond to the ICMP messages, the reflectors will reflect—bounce—the router’s traffic back to it, overloading it even more.
 CAUTION If you suspect your network is under a DoS attack, keep in mind that DoS attacks are often used as a diversion to shift focus from the actual target.
CAUTION If you suspect your network is under a DoS attack, keep in mind that DoS attacks are often used as a diversion to shift focus from the actual target.
Masquerade Attacks
There are several types of attacks based on the idea of users or devices pretending to be someone or something they’re not. These are known as masquerade attacks. Here are some of them.
Man in the Middle
A man-in-the-middle (MiM) attack is an eavesdropping attack. The goal of this attack is to intercept interesting traffic and, if possible, change the data in transit for malicious purposes. A MiM attack might also be an information collection effort for perpetrating fraud.
For a MiM attack to work, an attacker must convince a recipient computer that he is a sending computer, and he must convince the sending computer that he is the recipient computer. This is accomplished by “spoofing” the media access control (MAC) and Internet Protocol (IP) addresses of the actual devices.
Network spoofing is normally conducted at the Network Layer—the attacker imitates the Internet Protocol (IP) address of the intended device. However, spoofing can also take place at Layer 2, the Data Link Layer. Hackers can modify a system’s MAC address to mirror that of another device. Changing an IP or MAC address is not a complex task. Modern networking devices now use flash memory, which can be manipulated with the correct software. Flash memory makes it easier for a trained intruder to change both the MAC and IP addresses of the attack device used to penetrate the network, making it seem like an authorized device.
Phishing
In a MiM attack, the attacker is a passive listener. If the attack is successful, authorized users may never know it happened. Phishing is a more active attack, in which users are directly solicited for information. The goal of a phishing attack is to collect critical information, such as user credentials, passwords, or credit card details, which can be exploited for financial gain. In a phishing attack, the attacker masquerades as someone who should have access to this information—for example, your system administrator, bank, or credit card company.
Most phishing attacks are initiated through email. However, an increasing number of phishing attacks are accomplished through web redirects. For instance, you might type www.infocomm.com (incorrect) instead of www.infocomm.org (correct), and end up at a phishing site that wants to steal your InfoComm login information. The best defenses against phishing are user awareness and email spam filters.
Malware
Many attacks require that a program be downloaded to and/or executed on an authorized network device. These malicious programs are commonly known as malware. Malware is a generic term used to describe a class of computer contaminants, including adware, spyware, viruses, and worms. Malware is generally categorized by one of the following goals:
• Information collection
• Information theft
• Misinformation
• Monetary gain
• Damage infliction
We highlight some common malware to look out for.
Viruses
As you probably know, a virus is a piece of software code written to cause harm to a computer system. Viruses attach themselves to a larger file in order to activate. Once active, a virus is self-replicating. The ideal virus enters a system unnoticed and attacks before anyone can respond. The best defense against viruses is maintaining an active antivirus management policy.
Viruses need some kind of attack vector to gain access to your network—in other words, they need a way to get in. There are several types of viruses, categorized by their attack vector or their method of concealment. Table 15-1 lists some basic virus types, along with their descriptions and attack vectors.
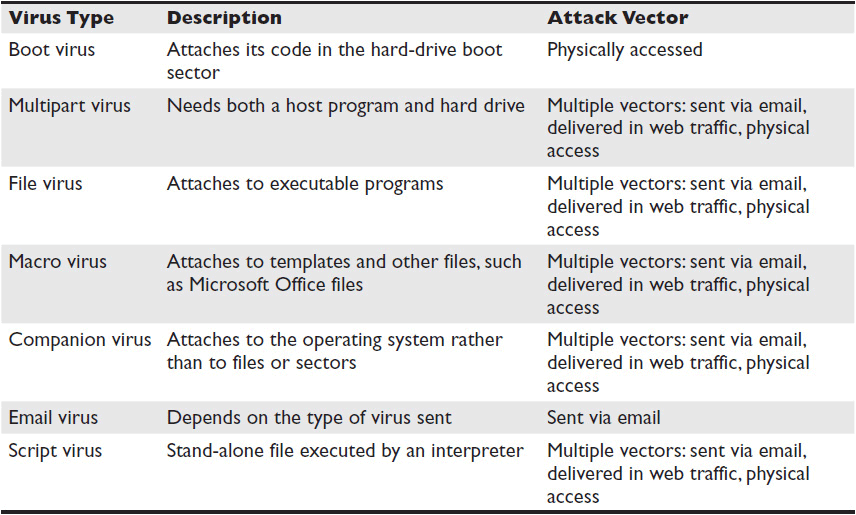
Table 15-1 Common Virus Types and Attack Vectors
 NOTE An attack vector is the means by which a malicious program or unauthorized user gains access to a system.
NOTE An attack vector is the means by which a malicious program or unauthorized user gains access to a system.
Viruses use different approaches to propagate and avoid detection. Table 15-2 shows a few of the technologies that a virus developer might program into the virus so it can replicate itself and continue attacking without being stopped.
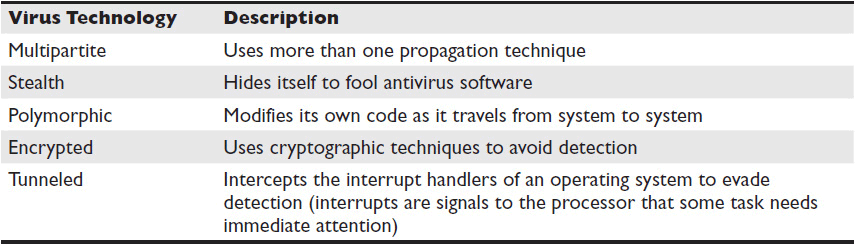
Table 15-2 Virus Technologies
Trojan Horses
A Trojan horse is a combined virus and masquerade attack in one. It is an infected application or suite of applications that masquerades as a legitimate program. Trojan horses can take many attack vectors, but they are typically bundled with normal web traffic. The Trojan horse then uses unauthorized access to gain administrative privileges on a target system. Once the Trojan horse has established itself, it can capture personal information, steal data, and/or allow a hacker to gain access or conduct other activities meant to harm the host system. The best defense against Trojans is to regularly conduct system scans and update antivirus and antimalware software.
Worms
Like viruses, worms are self-replicating malicious programs. Unlike viruses, worms do not need to attach to another program to activate or gain access to a system. Most worms gain access to systems by exploiting errors or vulnerabilities in the application or operating system code. Correcting such errors and vulnerabilities is one of the reasons software manufacturers regularly send out patches.
Once a worm enters a user’s unpatched system, it immediately looks for other networked systems. The worm simultaneously attacks the existing system and searches for other similar systems to attack. Worms can spread very quickly in this manner. A new worm can spread to Internet-connected computers worldwide in a matter of hours. The best defense against worms is system patch management.
Security Tools
The risks a network faces can seem overwhelming. Fortunately, there are many tools for mitigating those risks. These tools range from sophisticated devices and protocols to simple preventive measures.
Firewalls
When it comes to keeping external intruders away from a network, more times than not, an organization will use a web of dedicated hardware and/or software technologies known as firewalls. A firewall protects a network by preventing intrusion of unauthorized users and/or regulating traffic that is permitted to enter or exit the network. Firewalls control access across any network boundaries, including between an enterprise network and the Internet or between LANs within an enterprise.
A firewall is really a set of policies, implemented across a range of networked devices. In essence, firewall policy in an enterprise can be distilled to one of two approaches:
• All network traffic is allowed unless it’s specifically forbidden (default allow).
• All network traffic is forbidden unless it’s specifically allowed (default deny).
The former policy emphasizes ease of use but forces network administrators to try to predict how the network may be attacked. The latter policy is more secure but makes new systems more difficult to configure. In either case, the AV designer’s responsibility is the same: document system ports and protocols and coordinate those needs with the network manager.
 TIP It’s important to remember that a firewall can’t protect you from traffic you invite onto the network. For example, it won’t stop a virus or malware that you download. This is why user awareness training is always the front line of network defense.
TIP It’s important to remember that a firewall can’t protect you from traffic you invite onto the network. For example, it won’t stop a virus or malware that you download. This is why user awareness training is always the front line of network defense.
The number of firewalls you need, and where you need them, is a critical network design decision. There will be firewalls protecting gateways to the Internet. Firewalls may also be deployed within an organization’s private network to protect certain areas from internal intruders.
Many organizations layer several firewalls between their internal network and the Internet to increase reliability and security. Using two identical firewalls in parallel—a primary and a standby— is a great idea, in case the primary firewall fails. However, using several identical firewalls in a series doesn’t do much. If an attacker manages to penetrate the first firewall, he or she can use the same methods to get through the second. When using several firewalls in series, it’s a good idea to use different types from different vendors.
Firewalls use several different strategies to protect a network. A firewall may employ one or many approaches; let’s take a look at some of them.
Port Address Translation
Port address translation (PAT) is a method of network address translation (NAT; see Chapter 7) whereby devices with private, unregistered IP addresses can access the Internet through a device that has a registered IP address. Unregistered clients send datagrams to a NAT server with a globally routable address (typically a firewall). The NAT server then forwards the data to its destination and relays responses back to the original device.
 NOTE Port address translation is also known as one-to-many NAT, network-and-port translation (NAPT), or IP masquerading.
NOTE Port address translation is also known as one-to-many NAT, network-and-port translation (NAPT), or IP masquerading.
By enabling multiple devices to access the Internet without globally routable addresses, PAT conserves address space, which is a concern in IPv4 implementations. IPv6 networks also use PAT, even though the number of available global addresses in IPv6 is virtually unlimited. Why? Because PAT hides the original source of the data.
From outside the network, all data appears to originate from the NAT server. Any data that arrives at the NAT server without a client’s request has nowhere else to go—it has the address of the building, but not the apartment number. As result, the data can’t get past the doorman. PAT-based firewalls block all unrequested data. A malicious intruder can’t trace the data’s path beyond the edge of the network.
Packet Filtering
Packet filtering is a firewall technique that uses rules to determine whether a data packet will be allowed to pass through the firewall. Rules are configured by the network administrator and implemented based on the protocol header of each packet.
Packet-filtering rules instruct the firewall to inspect each incoming (and sometimes outgoing) packet for a combination of factors, including
• Source and destination address
• Source and destination port
• Application protocol
• Packet contents
The network administrator can combine these rules to reject or allow traffic based on very specific conditions.
Port Forwarding
Port forwarding combines PAT and packet filtering. The firewall inspects the packet based on rules. It is also configured to translate certain ports to private addresses on the network.
By combining PAT and packet filtering, a network administrator can allow incoming, unrequested traffic under controlled conditions. For example, a computer with a specific IP address may be allowed to send Telnet commands over port 23 to AV devices, but port 23 packets from any other address would be rejected. The firewall detects the IP address and the port and translates that port to an address, automatically forwarding the Telnet command to the designated device.
Application Layer Gateways and Session Border Controllers
Depending on the network, you may find other dedicated devices that work in concert with a firewall to provide network security. These devices can be especially helpful in the case of applications that require someone from outside the network to be able to access devices inside the network, which sounds a lot like networked AV systems.
Normally, firewalls block traffic that isn’t sent in response to a request from inside the network. However, for certain applications, such as conferencing, you want a device outside the network to be able to initiate communication. How else can someone call your organization’s videoconferencing unit?
An Application Layer gateway (ALG) works in parallel with a firewall. It acts as a proxy server because it sits between the client device and the actual server in order to exchange data (see Figure 15-1). The ALG device examines each packet before forwarding it to the far end. If your firewall employs NAT, the ALG converts the IP address information found inside each packet to the addresses acceptable by the hosts on either side of the firewall. An ALG can also support videoconferencing-related services, such as global address books. In an enterprise, an ALG has to be placed at each firewall.
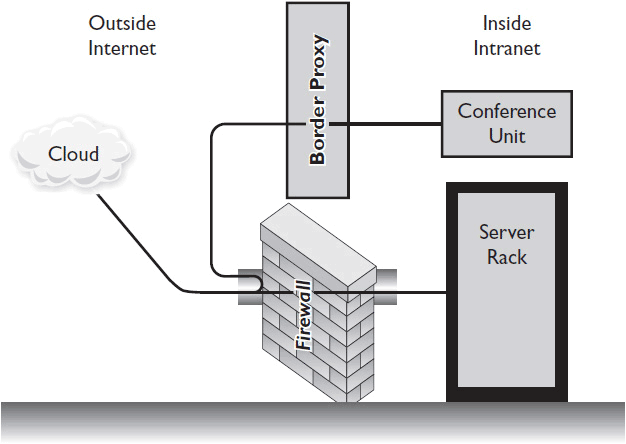
Figure 15-1 An Application Layer gateway working with a firewall.
A session border controller (SBC) funnels videoconferencing calls through a small number of ports that are open on a firewall. The SBC consists of two parts: the border controller and the client. The border controller sits outside the firewall while the client sits inside, as shown in Figure 15-2. The SBC client may exist within a conferencing endpoint or reside on another device. In an enterprise, one SBC can provide traversal for multiple firewalls.
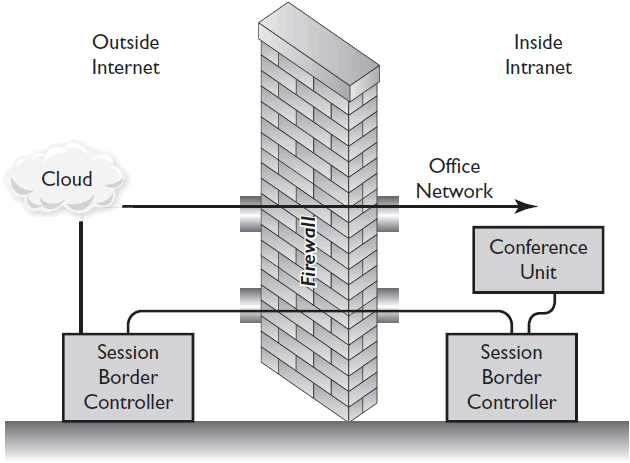
Figure 15-2 How session border controllers work.
When using an SBC, you typically set aside a public IP address at each site for conferencing traffic. All traffic sent to that address is automatically sent to the SBC, which then forwards the call-signaling information through the few permanently open ports.
Third-Party Security Tools
There are suites of third-party security tools available to anyone who needs to protect a network or networked devices. They are primarily software based and run the gamut from free to expensive. Quick note about free security software, however: it can be great for system administrators and hackers. For example, a network administrator might use a password-cracking tool to assess password strength. An intruder could use the same tool to gain access to a forbidden part of the network. For this reason, administrators sometimes forbid the use of free security programs on an enterprise network.
Still, building a toolbox of trusted security tools is essential to protecting network resources. Let’s examine a few.
Audit Tools
Audit tools are software applications used to gather logs from multiple sources and process the data into usable information. The Event Viewer built into the Windows operating system is an example of an auditing tool.
Getting data about what events have taken place on a system—unauthorized login attempts, password changes—is not a problem. Every operating system and network device can generate audit logs. The challenge is collecting data from different devices and analyzing it for potential security risks.
The default logging that network devices and operating systems automatically perform is not, by itself, very useful. These programs often log every event whether it matters or not. But a critical problem may be buried under thousands of routine actions. Logs can also be quite cryptic, leaving the network administrator to figure out what he or she is looking at. A good audit tool allows the administrator to easily identify noteworthy events, such as system errors. Without a dedicated audit tool, an administrator will be overcome by the massive accumulation of event logs from multiple sources.
Protocol Analyzer
Protocol analyzers (also known as network analyzers, packet sniffers, Ethernet sniffers, and other names) are essential to a network administrator’s toolbox. Protocol analyzers collect, monitor, and analyze network traffic. They can tell you how much of what kind of traffic is present on the network, which helps IT find traffic that doesn’t belong, or trace problematic traffic to its source.
Some protocol analyzers can also generate their own data traffic and inject it into the network. Network administrators use this function to test connectivity, firewall settings, and more. The protocol analyzer can tell the administrator whether the traffic went where it was supposed to go or got stopped along the way.
Protocol analyzers are also a good example of a useful security tool that can be dangerous in the wrong hands. Some powerful protocol analyzers are free. Hackers can use them to monitor network traffic, intercept it, or even inject malicious code. For this reason, network administrators sometimes encrypt traffic even on private LANs. They also conduct regular software inventories to make sure there are no unauthorized protocol analyzers running on the network.
Antivirus and Antimalware
Antivirus software is designed to detect viruses or worms once they enter a system. Viruses usually have a signature, which is a unique string of code that acts like a fingerprint. Typically, antivirus software uses a signature database from previously identified viruses and worms to detect malicious programs. However, this system can’t detect new viruses.
A virus doesn’t have a signature until it contaminates a system. Some antivirus software now uses a combination of signature and anomaly detection. Anomaly detection identifies software that displays certain traits or characteristics on known viruses. The problem is, some legitimate software might display virus-like behavior, leading to false positives from the antivirus software. Moreover, one of the first targets of malware is often a system’s antivirus defenses. If ever compromised, antivirus software provides zero protection.
The antivirus software industry does not consider Trojan horses, spyware, phishing attacks, or adware to be viruses or worms. Most antivirus solutions do not detect these threats. That’s left to antimalware software (which the same companies will also sell you). Antimalware software takes up where antivirus programs stop, detecting and protecting systems against known Trojans, spyware, and adware.
 NOTE Many networking professionals use the acronym “AV” to refer to antivirus software. Be sure to clarify your meaning when you use AV to refer to audiovisual.
NOTE Many networking professionals use the acronym “AV” to refer to antivirus software. Be sure to clarify your meaning when you use AV to refer to audiovisual.
Vulnerability Analysis Tools
Vulnerability analysis tools are sometimes referred to as self-hacking tools. They’re used to look for weaknesses in networks and devices—routers, switches, firewalls, computers, and so on. Basically, they attack the network as a malicious intruder might, initiating a denial-of-service, masquerade, or other type of attack to see how the network responds.
Such vulnerability testing is important, but it involves a certain amount of risk. If a network is particularly vulnerable, the tool could accidentally generate a successful attack. It takes caution and planning to conduct an effective vulnerability analysis.
User Authentication
User authentication and authorization are fundamental to the security of an enterprise network. The network’s known users, including administrators, should have a user profile. This profile identifies the user’s email account, access privileges, group memberships, and more. When users log on to the network, they have to prove their identity to gain access to their user profiles. This is usually accomplished with a username and password, although more secure networks have additional authentication requirements, such as physical access cards or biometric scans.
The guiding philosophy of user access is “least privilege.” That is, users should have the least number of network privileges they can get by with and still do their jobs. From time to time, administrators scan the network and systems to verify user access. If users need additional access, they can go through a formal approval process.
Network Access Control
Permission to enter a network—and the rights that a user enjoys once logged on—is governed by a group of technologies and policies known collectively as network access control (NAC). NAC is based on an idea that’s easy to understand, but challenging to implement: When you log on to a network, who you are determines what you can do.
In a robust NAC environment, who is determined by more than just a username. Identification and authentication are key to NAC—the right to access certain VLANs, files, or programs may be directly associated with a specific login. However, NAC may also evaluate other factors to determine what rights a user should have. For instance, a NAC system may remotely examine the endpoint that a person is using to access network resources and limit that person’s rights if the endpoint is not sufficiently secure. For example, if an endpoint is running out-of-date antivirus software, the NAC system may block the user from sensitive areas of the network, or even the entire network, until the user updates the antivirus program.
A NAC system may also weigh the type of connection a person is using. Wi-Fi? Remote VPN? A cable connected to an on-site wall port? A NAC system may be configured to grant more access to network resources if it knows the user is connected via a physical, on-site port rather than a remote or wireless one.
User Authentication Protocols
A NAC solution usually starts with one of several authentication protocols. Regardless of the technology used or the specific implementation, an authentication protocol has one purpose—to authenticate the user to the target system. While some of the following protocols are more secure than others, they all accomplish basic authentication.
Password Authentication Protocol
Password Authentication Protocol (PAP) is a simple authentication protocol. It was developed in the early 1970s—long before security was a main concern in networking. PAP is considered unsecure since it passes both the user identification and password unencrypted.
Challenge Handshake Authentication Protocol
Challenge Handshake Authentication Protocol (CHAP) is another authentication scheme used in the early days of networking. Like PAP, it is mostly used with Point-to-Point Protocol (PPP) for remote authentication. But in the case of CHAP, a user’s name and password are encrypted using a digital signature or private key. CHAP also includes a hash for integrity purposes. The sender’s hash value is compared to an existing hash value on the recipient system. If the values match, then the connection is established.
Kerberos
Kerberos was developed at the Massachusetts Institute of Technology. It’s a trusted third-party authentication method used in networked environments to implement what’s known as single sign-on (SSO). SSO allows users to access multiple protected resources with just one username and password or other authentication method. Kerberos uses private key encryption for end-to-end security.
A Kerberos system utilizes a key distribution center (KDC), which contains all the shared security keys. Unfortunately, a KDC presents a single point of failure that is vulnerable to brute-force attacks. It’s also difficult to maintain. Changing a single user’s password requires updating the entire KDC. And keep in mind, the only security feature Kerberos offers is authentication; all other network traffic remains unsecure.
 NOTE Kerberos is a network authentication protocol used in the United States to encrypt data exchanges. This software is subject to US export control.
NOTE Kerberos is a network authentication protocol used in the United States to encrypt data exchanges. This software is subject to US export control.
Extensible Authentication Protocol (EAP)
Extensible Authentication Protocol (EAP) is an authentication framework used primarily for wireless networking. The standards for implementing EAP over local area networks are defined by IEEE standards 802.1x. There are more than 40 different implementations of EAP. For example, in a wireless LAN environment, 802.1x authentication and encryption may be provided by Wired Equivalent Privacy (WEP).
Access Control List
Once a user is granted access to a network, his rights within the network may be governed by an access control list (ACL). ACLs are typically configured on network routers. An ACL specifies what can travel through the router, based on the type of traffic, source, and/or destination. An ACL may also spell out network privileges regarding who can access what parts of the network. If your audiovisual system will require special access rights, be sure the network security personnel create an ACL for the system and add the appropriate end users.
Secure Transmission
There are many steps you can take and tools you can use to secure a private network from intruders and snoops. But chances are—especially when it comes to popular networked AV systems—your data will sometimes travel over the Internet, where you have no control. Encryption is the key to sending private traffic across a public network like the Internet.
Encryption is the process of making data unreadable before transmitting or storing it. Data that’s encrypted must be decrypted when it reaches its destination. By encrypting data, you ensure that only authorized users can view it. There are a few common ways of implementing encryption:
• Digital signatures With digital signatures, each user is associated with a unique signature, or key. The key identifies who sent the encrypted data. Only a device with another authorized key can decrypt the data. Digital signatures can only be used by devices that “know” each other, that is, that belong to the same organization.
• Digital certificates Digital certificates help secure communications between “strangers,” such as a consumer and an online store. An independent organization called a certificate authority sends each device a certificate, which identifies the sender and allows the recipient to decrypt the data.
• Private key encryption Private keys are often used to allow remote access to an enterprise network. Both sender and recipient possess the same private key, which must be exchanged securely, usually in advance. The key identifies the devices as authorized to view or send data and performs the encryption and decryption. Each pair of communicating devices needs a separate private key.
• Public key encryption Public keys also allow remote access to an enterprise network. However, in this scheme, keys are sent over the Internet (private keys sit on devices behind firewalls). Multiple devices can use the same public key. The private and public keys are partners. Each can encrypt and decrypt information sent by its partner key.
Encryption can also help ensure integrity, making certain that data arrives intact and unadulterated. Some encryption algorithms attach a “hash” value or “message digest” to data before transmission. It’s basically a calculation based on the 1s and 0s of the data itself. When the data arrives, the destination device performs the same calculation. If it comes up with the same hash value as the sending device, the data is unaltered.
Secure Sockets Layer and Transport Layer Security
Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are standard security technologies for creating encrypted links over the Internet. SSL and TLS are similar almost to the point of interchangeability. They are often referred to as one thing: TLS/SSL.
SSL combines certificate and public key encryption. An organization with a web server applies to a certificate authority for an SSL certificate. The certificate lets other devices know that the organization is legitimate. It contains identifying information about the organization and the issuing certificate authority, as well as an expiration date. The organization then receives public and private keys. The public key is sent out to any device that requests secure communication with the organization’s web server.
TLS is an open standard developed by the IETF as a successor to SSL. The main difference is that TLS communication begins with an unsecured “hello” message. Secure communications are only established if this initial “handshake” is successful. TLS is backward-compatible with SSL.
 NOTE TLS/SSL is commonly used to secure web communication between unknown devices. HTTP traffic that has been encrypted in this manner is known as Hypertext Transfer Protocol Secure (HTTPS). This process is transparent to the end user. When TLS/SSL is engaged to encrypt HTTP traffic, the only sign the user typically sees is a lock symbol.
NOTE TLS/SSL is commonly used to secure web communication between unknown devices. HTTP traffic that has been encrypted in this manner is known as Hypertext Transfer Protocol Secure (HTTPS). This process is transparent to the end user. When TLS/SSL is engaged to encrypt HTTP traffic, the only sign the user typically sees is a lock symbol.
Secure Shell and Secure Copy Protocol
Secure Shell (SSH) is an encryption method used to provide remote access to enterprise resources. The underlying encryption technology varies. SSH is a client-server architecture; remote devices are SSH clients that contact an SSH server on the enterprise network to access resources. The client logs in to the server using a command-line interface or some other secure code execution. All SSH traffic is encrypted; therefore, it provides excellent confidentiality and data integrity while limiting availability to authorized users. SSH is often used to provide secure remote access to systems for off- site monitoring, configuration, and troubleshooting.
Similarly, Secure Copy Protocol (SCP) is a method of sending files securely between two systems over an unsecure network. The SCP application uses SSH to provide confidentiality of data in transit and authentication of users. Unlike File Transfer Protocol (FTP), SCP allows users to securely transmit and receive files from remote hosts. SCP is a client-server architecture that relies on the implementation of an SSH server and an SCP client application.
Virtual Private Networking
Most large or physically dispersed organizations will require some way to hold managed communication between their LANs. Network services that are particularly necessary for AV applications, such as QoS, low latency, managed routing, and multicast transmission, are impossible over the open Internet. Most customers and service providers also need a secure means of accessing systems remotely for monitoring, troubleshooting, and control purposes. Virtual private networks (VPNs) provide a way.
A VPN uses the Internet to create a secure tunnel between two or more LANs, in essence forming a virtual WAN. Each host requires the proper software, access rights, and password to log in to the client network.
VPN functionality is often built into security devices such as firewalls. Organizations that use VPNs a lot may require dedicated VPN devices. It is important to understand that using a VPN increases bandwidth overhead because it adds encryption and a tunneling “wrapper” to each packet—that’s what makes communication secure over the public Internet. This overhead may not be significant enough to require additional bandwidth, but it can increase the Ethernet frame size to the point where packets must be fragmented before they can be sent across the network. When it comes to networked AV systems, this can be a major design consideration. Packet fragmentation can be disastrous for the quality of streamed video or conferences. If a networked AV system must traverse the Internet via VPN, be sure the frame size is set low enough to account for the VPN overhead.
There are a few common VPN types, based on the protocols they use and the OSI layers at which they operate.
• Layer 2 Tunneling Protocol (L2TP) Operates at the Data Link Layer. Client devices must have the right client software installed to establish secure communications. An L2TP-based VPN can transport both IP and non-IP data, but it can also introduce significant latency. It’s not commonly used in newer systems.
• Internet Protocol Security (IPsec) Operates at the Network Layer. IPsec has been standardized by the IETF. Again, client devices must have client software installed. As its name implies, an IPsec VPN provides security for any IP transport protocol, such as TCP, UDP, and ICMP. It can authenticate users and encrypt traffic, or just authenticate, based on need. An IPsec VPN assigns remote devices an internal address when they connect, effectively incorporating them into the LAN and giving them access to the same resources they’d be able to access on premise. It’s common for site-to-site connections. You’re likely to encounter IPsec VPNs in your work, so it will be important to get familiar with the technology’s overhead requirements, which vary from system to system.
• Secure Sockets Layer (SSL) Operates at the Application Layer. It doesn’t require any special client software because users access an SSL VPN via their web browsers. This makes things easy on the endpoints, but it does require that the organization install and operate a dedicated SSL VPN server. SSL VPNs make sense when supporting a mobile workforce. They secure TCP-based communications and act as proxies, allowing only authorized users access to approved resources. Access can be configured on an individual user basis.
Many of the protocols used to transport AV data over Layer 2 (the Data Link Layer) cannot be routed over Layer 3 (the Network Layer). This limits their scalability and prevents them from taking advantage of important Network Layer functions, such as data prioritization. Enter Multiprotocol Label Switching (MPLS), which is in essence a “Layer 2.5” technology that combines Layer 2 flexibility with IP network functionality.
MPLS allows any combination of Data Link Layer protocols to be transported over any type of Network Layer. MPLS routes data by examining each packet’s MPLS label without examining packet contents, thereby improving interoperability and routing speed. MPLS is used frequently to allow access to IP services over ATM networks and vice versa. It incorporates QoS class-of-service tags and network tunneling technologies, leading MPLS service providers to offer MPLS-based VPNs as a service. Many small to medium organizations choose to purchase VPN services directly from their MPLS ISP.
MPLS-based VPNs put the burden of WAN design and maintenance on the ISP. They also provide some degree of QoS. Certain types of MPLS VPNs, including virtual leased lines (VLLs) and virtual private LAN services (VPLSs), allow users to transport a variety of data link frames, not just IP packets, over the MPLS core network. MPLS VPNs require a permanent connection between the customer’s network edge and the provider’s routers. They can’t be used by mobile clients.
Wireless Security
The idea of a wireless Internet was rushed to market with little thought for security. Early versions of wireless networking (commonly known as Wi-Fi and based on IEEE 802.11 standards) included some pseudosecurity measures, but they were easily thwarted. Consequently, the early days of wireless networking were rife with security breaches.
Despite an evolution in the technologies and best practices for securing wireless networks, IT administrators are often hesitant to add new access points to their wireless networks. This poses an issue when it comes to an increasing number of AV solutions, such as wireless presentation systems, which can use an organization’s wireless LAN to ease collaboration and access to networked-based AV resources. Understanding what makes IT nervous and how wireless networks should be secured is an important starting point for AV/IT negotiations.
Weak Wireless Security Measures
Wireless access points (WAPs) can be configured to require different levels of authentication. By default, however, most WAPs require no authentication—system owners have to establish a higher level of authentication.
Many manufacturers have tried to overcome this issue by implementing one-click security—basically zero-configuration wireless security. If all the wireless clients and WAPs can negotiate an acceptable security posture, zeroconf can be a great help. Unfortunately, it often fails, in which case wireless users go unprotected. Other less-than-perfect solutions to wireless security include the following:
• Hiding SSIDs In wireless networking, the service set identification (SSID) is used to identify a WAP. It’s the name of the WAP as displayed on the client in a list of available wireless networks. You can attempt to hide an WAP by configuring it not to broadcast the SSID. This makes it more difficult for both authorized and unauthorized users to connect to the WAP. Still, a determined attacker can use a wireless network detection tool to acquire the SSID within a few minutes.
• MAC address filtering MAC address filtering is a security measure whereby a WAP is configured to grant access to devices with preapproved MAC addresses. This is like giving a list of names to a security guard. It presents a couple of challenges, however: the MAC addresses of permitted devices are manually configured on the WAP—a potential administrative headache—and MAC address filtering is a weak approach to wireless security because MAC addresses are easy to spoof. Attackers can monitor the target network and collect all the associated MAC addresses. They can then pick one with a low signal-to-strength ratio and modify their MAC address to match the weakest signal. The attacker can then use a bigger antenna with more power, join the network, and initiate an attack.
Wireless Security Protocols
It almost goes without saying that any wireless network—whether in your home or in a business—needs to be locked down. And as the 802.11 standards developed over time, so did the security algorithms that can protect WAPs from unauthorized access. Not all wireless protocols are created equal, however. Here are the most common options.
Wired Equivalent Privacy
Wired Equivalent Privacy (WEP) is a security algorithm introduced as part of the original IEEE 802.11 standards. Today, WEP is considered extremely weak. When under attack, WEP connections can be breached in a matter of minutes. Still, you’ll find that WEP is an option on wireless network routers and modems.
WEP provides two authentication methods—open-system authentication and private key authentication. Open-system authentication isn’t much authentication at all. All it requires is access to the SSID of the wireless access point. Any client seeing the SSID can join the wireless network. Private key authentication requires knowledge of a secret key to join the wireless network. Unfortunately, the algorithm used to share the key is so weak that an intruder need only wait patiently and collect the relevant packets in order to break the key. Not that we’re condoning it, but if an access point is especially active, a hacker can get the key after about a minute of traffic analysis. WEP is better than nothing, but it’s not good enough for enterprise security.
Wi-Fi Protected Access
Wi-Fi Protected Access (WPA) was drafted by the Wi-Fi Alliance as a stopgap measure to improve wireless security until new standards could be developed. WPA uses longer private keys than WEP, making them harder to crack. WPA also implements Temporal Key Integrity Protocol (TKIP) and Advanced Encryption Standards (AES) for improved security.
Still, a dedicated attacker can attack a WPA-protected access point. Depending on the capability of the attacker and the complexity of the shared key, WPA can be broken in a couple of hours.
Wi-Fi Protected Access 2
Wi-Fi Protected Access 2 (WPA2) is the preferred security protocol for wireless LANs. It, too, was developed by the Wi-Fi Alliance to improve wireless security. As of 2006, the Wi-Fi Alliance mandated that all new wireless technologies that carry the Wi-Fi trademark must be WPA2 compliant.
WPA2 increased the security requirements of WPA to include something called Counter Cipher Mode with Block Chaining Message Authentication Code Protocol (CCMP). Basically, CCMP is an enhanced version of AES. Use WPA2 for all networked AV systems that require Wi-Fi connectivity.
Chapter Review
If you want to know why IT departments sometimes cast a wary eye on networked AV systems, it pays to understand what keeps them up at night. Security is the number one concern of most networking professionals, in part because networks are so vulnerable to attack. And if a network is compromised, enterprises can grind to a halt.
In this chapter, you learned about the risks networks face and how they can be mitigated. Now you should know what to look for in terms of secure transmission protocols. You also know what kinds of authentication and remote access options you may need to discuss with IT personnel. In the case of conferencing applications, you may even need to discuss purchasing additional security devices, like an Application Layer gateway or session border controller.
Security is the IT professional’s main concern. If you can demonstrate that you understand that concern and are working to accommodate it, your coordination efforts will be much more successful.
Now that you’ve completed this chapter, you should be able to
• Identify common network vulnerabilities and threats, along with the potential risks associated with them
• Describe the functions of the devices and software used to provide network security
• Summarize the process and purpose of user authentication
• Identify encryption protocols used for public and private Internet traffic
• Explain the functionality of VPN technologies
• Distinguish between weak and strong wireless network security measures
Review Questions
1. In general, it is considered best practice to grant users the right to access system resources on the basis of ____.
A. open access—granting full access to all system resources to all verified system users
B. least access—granting access only to the resources users need in order to do their jobs
C. access requests—granting access only to the resources that users request by name
D. priority access—granting widespread access to the most important systems, with limited access to less used systems
2. As a security best practice, TCP/UDP ports should be ____.
A. disabled unless the device has a globally routable IP address
B. disabled unless the device needs to use them
C. left open unless an attack is detected
D. left open for monitoring and maintenance purposes
3. A ____ attack is a network attack wherein a network resource is bombarded with data packets, making it unavailable to users.
A. denial-of-service (DoS)
B. phishing
C. virus
D. man-in-the-middle (MiM)
4. ____is the process of imitating the IP address and/or MAC address of an authorized device in order to gain access to a network.
A. Denial of service (DoS)
B. Phishing
C. Spoofing
D. Trojaning
5. ____are small chunks of malicious code that must be attached to a larger file in order to activate.
A. Masquerades
B. Worms
C. Viruses
D. Man-in-the-middles (MiMs)
6. A firewall policy in which all network traffic is forbidden unless it is specifically allowed is known as ____.
A. default allow
B. session border controller
C. border proxy
D. default deny
7. When data that has not been requested by a network client arrives at a gateway router, the firewall typically ____.
A. broadcasts the packets out of all ports except the receiving port
B. forwards the packets to the network administrator
C. forwards the packets back to the sending device
D. blocks the unsolicited packets
8. A network administrator can allow unrequested incoming traffic, such as remote Telnet commands from a particular device, using ____.
A. port forwarding
B. network address translation (NAT)
C. port address translation (PAT)
D. packet filtering
9. One ____ device can provide videoconferencing call traversal through multiple firewalls.
A. Application Layer gateway (ALG)
B. port forwarding
C. session border controller (SBC)
D. border proxy
10. When using ____ to forward incoming videoconference traffic past a firewall, you need a separate device for each firewall.
A. Application Layer gateways (ALGs)
B. session border controllers (SBCs)
C. packet filtering
D. port address translation (PAT)
11. ____allow network administrators to attack their own networks on purpose to test their security measures.
A. Vulnerability analysis tools
B. Network protocol analyzers
C. Packet sniffers
D. Session border controllers (SBCs)
12. Network access control (NAC) may grant users rights to access system resources based on ____. Select all that apply.
A. the make and model of peripherals attached to the endpoint
B. the state of antivirus software on the endpoint
C. username and password
D. the type of connection being used to access the network
13. Which of the following authentication protocols is unencrypted?
A. Extensible Authentication Protocol (EAP)
B. Challenge Handshake Authentication Protocol (CHAP)
C. Kerberos
D. Password Authentication Protocol (PAP)
14. ___is a client-server–based encryption method used to provide remote access to enterprise resources.
A. Transport Layer Security (TLS)
B. Password Authentication Protocol (PAP)
C. Secure Sockets Layer (SSL)
D. Secure Shell (SSH)
15. Which of the following virtual private network (VPN) technologies assigns remote devices an internal IP address upon connection, putting them virtually on the LAN?
A. Layer 2 Tunneling Protocol (L2TP)
B. Multiprotocol Label Switching (MPLS)
C. Internet Protocol Security (IPsec)
D. Secure Sockets Layer (SSL)
16. Which of the following virtual private network (VPN) technologies requires neither client software nor a permanent connection for remote access?
A. Multiprotocol Label Switching (MPLS)
B. Secure Sockets Layer (SSL)
C. Internet Protocol Security (IPsec)
D. Layer 2 Tunneling Protocol (L2TP)
17. The current preferred security protocol for wireless LANs is ____.
A. Wired Equivalent Privacy (WEP)
B. Wi-Fi Protected Access 2 (WPA2)
C. Wi-Fi Protected Access (WPA)
D. MAC address filtering
Answers
1. B. In general, it is considered best practice to grant users the right to access system resources on the basis of least access—granting access only to the resources users need in order to do their jobs.
2. B. As a security best practice, TCP/UDP ports should be disabled unless the device needs to use them.
3. A. A denial-of-service (DoS) attack is a network attack wherein a network resource is bombarded with data packets, making it unavailable to users.
4. C. Spoofing is the process of imitating the IP address and/or MAC address of an authorized device in order to gain access to a network.
5. C. Viruses are small chunks of malicious code that must be attached to a larger file in order to activate.
6. D. A firewall policy in which all network traffic is forbidden unless it is specifically allowed is known as default deny.
7. D. When data that has not been requested by a network client arrives at a gateway router, the firewall typically blocks the unsolicited packets.
8. A. A network administrator can allow unrequested incoming traffic, such as remote Telnet commands from a particular device, using port forwarding.
9. C. One session border controller (SBC) device can provide videoconferencing call traversal through multiple firewalls.
10. A. When using Application Layer gateways (ALGs) to forward incoming videoconference traffic past a firewall, you need a separate device for each firewall.
11. A. Vulnerability analysis tools allow network administrators to attack their own networks on purpose to test their security measures.
12. B, C, D. Network access control (NAC) may grant users rights to access system resources based on the state of antivirus software on the endpoint, username and password, and the type of connection used to access the network.
13. D. Password Authentication Protocol (PAP) is unencrypted.
14. D. Secure Shell (SSH) is a client-server–based encryption method used to provide remote access to enterprise resources.
15. C. Internet Protocol Security (IPsec) assigns remote devices an internal IP address upon connection, putting them virtually on the LAN.
16. B. Secure Sockets Layer (SSL) requires neither client software nor a permanent connection for remote access.
17. B. The current preferred security protocol for wireless LANs is Wi-Fi Protected Access 2 (WPA2).
