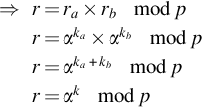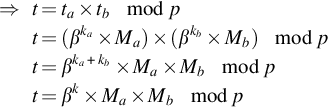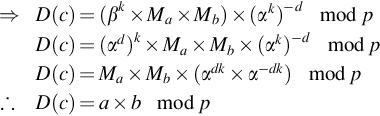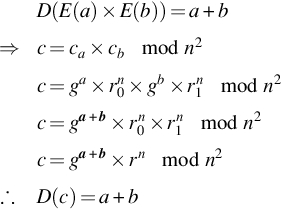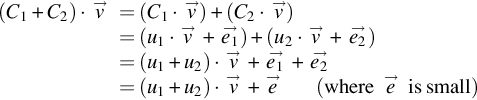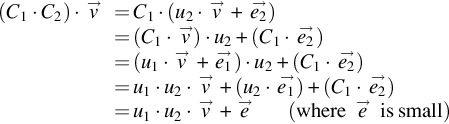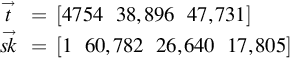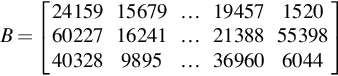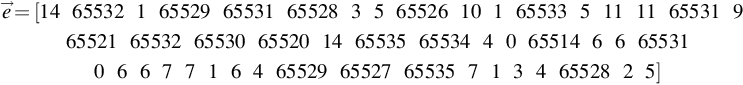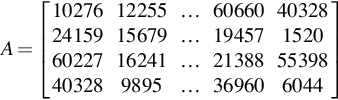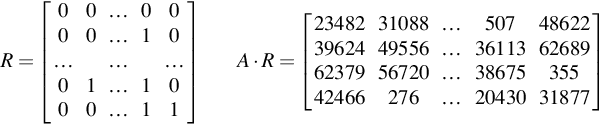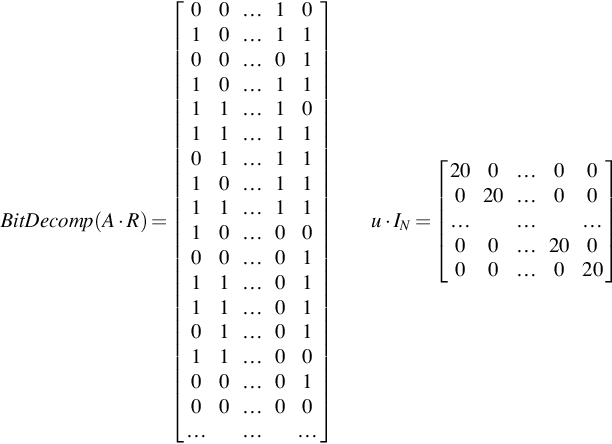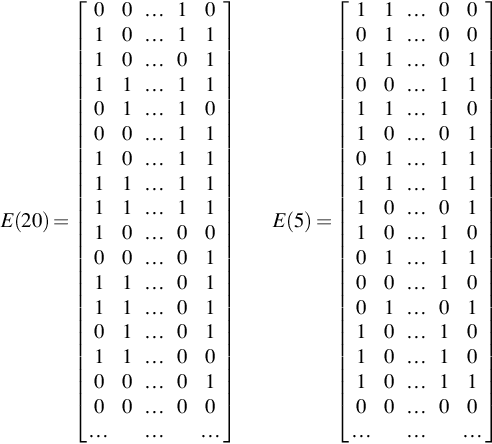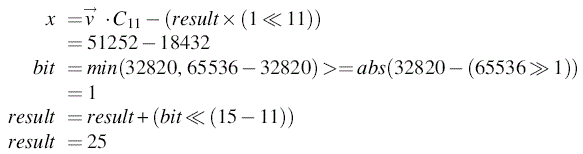A guide to homomorphic encryption
Mark A. Will; Ryan K.L. Ko Cyber Security Lab, Department of Computer Science, University of Waikato, Hamilton, New Zealand
Abstract
Traditional cryptography techniques require our data to be unencrypted to be processed correctly. This means that at some stage on a system we have no control over, our data will be processed in plaintext. Homomorphic encryption or specifically, fully homomorphic encryption is a viable solution to this problem. It allows encrypted data to be processed as if it were in plaintext and will produce the correct value once decrypted. While many know that homomorphic encryption promises to be an ideal solution to trust, security, and privacy issues in cloud computing, few actually knows how it works and why it is not yet a practical solution despite its promises. This chapter serves as a much needed primer on current homomorphic encryption techniques, discusses about several practical challenges, and introduces workarounds proposed by practitioners and researchers to overcome these challenges.
1 Introduction
In cloud computing, fully homomorphic encryption (FHE) is commonly touted as the “holy grail” (Gentry, 2009a; Micciancio, 2010; Van Dijk and Juels, 2010) of cloud security. While many know this potential, few actually understands how FHE works and why it is not yet a practical solution despite its promises. Homomorphic encryption schemes allow users’ data to be protected anytime it is sent to the cloud, while keeping some of the useful properties of cloud services like searching for strings within files. This is because it can allow operations and functions to be preformed over encrypted data, meaning that the data is never unencrypted outside the users’ environment. It prevents malicious employees of cloud service providers from accessing private data. A report (Chen, 2010) of an employee at Google in 2010 described a former engineer abusing his privileges to view private information. He used this information to stalk teenage girls and spy on their chat sessions. Many employees of cloud services have the required privileges to view our data, and we need to prevent such incidents from happening again.
There are two flavors of homomorphic encryption: partially and fully. Partially Homomorphic Encryption (PHE) is where only a single operation can be performed on cipher text, for example, addition or multiplication. Schemes for PHE exist and are usable today, with two being described in Section 4. However, many cloud services require more functionality than just addition or multiplication. This is where FHE, also known as the “holy grail” of encryption, can start to play a huge role in securing cloud services. FHE can support multipliable operations (currently addition and multiplication), allowing more computation to be performed over encrypted data.
Looking at an example, Alice runs an accounting firm, which stores all of her customers balances on the cloud. By utilizing the cloud, it means that she does not have to manage the underlying infrastructure of the cloud. Instead it is managed by a third-party cloud service provider. The problem Alice faces is that in order to keep her customers accounts secure, she encrypts them when they are in the database/storage. This prevents a malicious outsider gaining direct access to the information, while also stopping the cloud service employees from being able to see the data. But when she needs to make a change to an account balance, she has to either transfer the encrypted account back to the her trusted environment, or decrypt the account data in the cloud, update the account, then encrypt it again before storage. This creates a risk where the data has to be decrypted at a point before it can be used. Because homomorphic encryption can process data while encrypted, Alice can simply apply changes to the encrypted account balance by sending encrypted data to the cloud and have the account updated without it ever being in decrypted form (i.e., plaintext). This allows Alices’ cloud accounting firm to keep its customers secure, while having the added benefits of using the cloud.
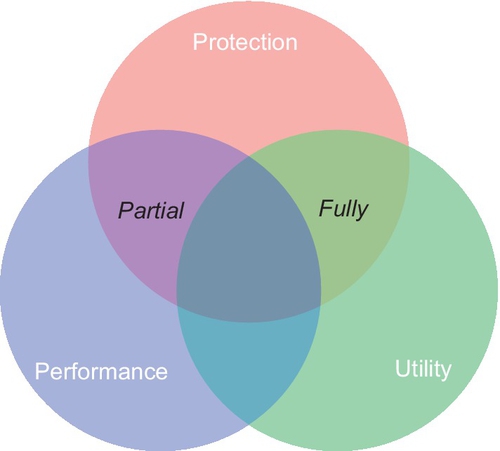
There is however a catch with this example. The performance of FHE is currently quite inefficient, where simple operations can take anywhere from seconds to hours depending on security parameters (Gentry and Halevi, 2011). Therefore, homomorphic encryption is currently a balancing act between utility, protection, and performance. FHE has good protection and utility, but poor performance. Where PHE has good performance and protection, but is very limited in its utility. This is illustrated in Figure 1, where the perfect solution would be in the center of the Venn diagram.
This chapter will give an in-depth overview of homomorphic encryption, and why it is so important for the cloud. We start with why homomorphic encryption is needed in the cloud, and some basic background information on the history of homomorphic encryption. In Section 4, we will describe and provide examples of two PHE schemes, El Gamal and Paillier. This leads into FHE where the Approximate Eigenvector Algorithm will be given, with details of how it works, the mathematical properties, and an example. From Section 6, some examples of homomorphic encryption in use today will be shown, followed by the some thoughts about the future of homomorphic encryption. For businesses requiring the protection of their data, homomorphic encryption is not the only answer available today, and Section 8 will give another methodology for storing encrypted data in the cloud.
2 Current industry work-arounds and their gaps
The cloud is built upon many technologies and ideas, but none more important than trust. As uses of cloud services, we have to trust that the providers will not misuse our data and information, but on top of that, we have to trust that their security defences will prevent malicious users from gaining access it as well.
Dropbox is one of the most widely used cloud storage services today, producing equivalent to one-third of the traffic that YouTube produces (Drago et al., 2012). On a help page titled How secure is Dropbox? (Dropbox Inc, 2014), is some useful information on how Dropbox is trying to protect its users. Analyzing a couple of these points: Dropbox uses modern encryption methods to both transfer and store your data (Secure Sockets Layer and AES-256 bit encryption) and Dropbox employees are prohibited from viewing the content of files you store in your account (Dropbox Inc, 2014). It is clear that even though your data is encrypted when stored, it is still possible for someone other than you to view the data in the unencrypted form. Be it a rogue Dropbox employee or a malicious attacker.
Then there are cloud storage services such as Mega Limited (Mega ltd, 2014), which provide privacy and protection by only having the end users device encrypt and decrypt their data. This ensures that only the user can access the unencrypted data, even if the service is compromised. This does however come with a cost, because only you can view your files. Therefore, it is difficult for Mega to provide advanced features such as searching for strings within files or sharing files with others. These features are still possible to implement, for example, having the client build and use a search index which can be encrypted and stored in the cloud, or for sharing files, encrypt with a different key allowing the user to give it to whomever needs access.
The problem is that Dropbox can perform the same tasks automatically, faster, and more efficiently. So the trade-off between utility, protection, and performance is a key problem for cloud service providers. This is where homomorphic encryption can play such a huge role in the cloud, because it can help combine the features of both Dropbox and Mega. Allowing the creation of more secure and trustworthy cloud services, by bridging the gap between utility and protection. Note that the algorithms for how homomorphic encryption will be able to actually search files is still unknown. However it could be done in a similar manner as encryption gateways described in Section 8 or using another encrypted search technique (Li et al., 2014; Kuzu et al., 2012; Li et al., 2010; Wang et al., 2014). But once FHE becomes more practical, these algorithms will start to be developed.
Even though homomorphic encryption cannot currently easily support searching, it is ideal for computing mathematical functions on encrypted data. For example, computing statistics, such as the mean or average value in a large dataset. Other application groups that can benefit are banking and data mining. So, therefore, homomorphic encryption is very important for the cloud, and once it matures, it will be widely used.
3 History and related work
To the best of our knowledge, the idea of using homomorphic encryption for protecting data has been around for decades, with Rivest et al. proposing special encryption functions called “privacy homomorphisms” in 1978 (Rivest et al., 1978b). The authors discuss the use of hardware to process data securely, with the data only ever decrypted on a physically secure processor. This way, any time the data leaves the processor (i.e. to memory) it is encrypted, similar to the AEGIS chip we see today (Suh et al., 2003, 2005). However, the issue with these types of chips is that because it is custom hardware, costly to implement, and still requires a decryption key for the data. Rivest el al. then mention a solution where the data is not decrypted, but standard hardware can still process the data correctly, and the concept of homomorphic encryption was born. They present some proof-of-concept examples that are not practical for use, but importantly show that this idea of processing encrypted data is possible, finishing off with two open questions:
• Does this approach have enough utility to make it worthwhile in practice? (Rivest et al., 1978b)
• For what algebraic systems U does a useful privacy homomorphism exist? (Rivest et al., 1978b)
In the same year, the RSA encryption scheme was made public by the same two authors of Rivest et al. (1978b), Rivest and Adleman, with the addition of Shamir (Note: RSA actually stands for the initials of the authors) (Rivest et al., 1978a). The original paper has no mention of homomorphic encryption; however, it was later proved that RSA does support multiplication over encrypted data (Denning, 1982). This is due to the mathematical properties of RSA, where by raising a message to e in modulo n, allows the two encrypted messages to be multiplied correctly once the e’s are removed at the decryption stage. Therefore, PHE has been conceptually supported for some time now.
In 1985, Blakley et al. proposed a database encryption scheme which supports computing some statistical operations over encrypted data stored in the database. Even though the paper does not specifically mention homomorphism, this is a step in showing that homomorphic encryption can be worthwhile in practice. In 1987 Ahituv et al. (1987) provides some more example algorithms that can support homomorphic operations, however have very weak security. In the following year Brickell and Yacobi (1988) evaluated the security of the first proposed homomorphic algorithms in Rivest et al. (1978b) and proposed an additive homomorphic algorithm where there was a maximum number of additions that could occur before it would break.
It was not until 1996 that we saw the first homomorphic algorithm to support both addition and multiplication (Ferrer, 1996). Domingo-Ferrer provided a needed breakthrough in the field, and later showed in 2002 that the proposed scheme was secure against known clear-text attacks; however, the scheme was broken a year later by Wagner (2003).
The problem up until this point was developing a scheme that was secure, without losing its homomorphic properties, able to support the repeating of operations many times, or being incredibly inefficient. Armknecht et al. proposed a solution which supported arbitrary number of additions and a fixed number of multiplications (Armknecht and Sadeghi, 2008), while remaining secure under a known decoding problem.
However, the real breakthrough occurred in 2009 when Gentry proposed a scheme that could support an arbitrary number of additions and multiplications and based the security on the hardness of lattice problems (Gentry, 2009a). Since then, Gentry has been involved in many different schemes (Gentry, 2009b; Van Dijk et al., 2010; Gentry et al., 2013) for FHE, gradually improving the schemes, but still to this day are not efficient enough to be used in the real world. The brief history given in this section is summarised in Table 1.
Table 1
Historic Overview of Homomorphic Encryption
| 2013 | Homomorphic encryption from learning with errors: Conceptually simpler, asymptotically faster, attribute-based (Gentry et al., 2013) |
| 2010 | Fully homomorphic encryption over the integers (Van Dijk et al., 2010) |
| 2009 | A fully homomorphic encryption scheme (Gentry, 2009a) |
| Fully homomorphic encryption using ideal lattices (Gentry, 2009b) | |
| 2008 | A new approach for algebraically homomorphic encryption (Armknecht and Sadeghi, 2008) |
| 2002 | A provably secure additive and multiplicative privacy homomorphism (Domingo-Ferrer, 2002) |
| 1996 | A new privacy homomorphism and applications (Ferrer, 1996) |
| 1988 | On privacy homomorphisms (Brickell and Yacobi, 1988) |
| 1987 | Processing encrypted data (Ahituv et al., 1987) |
| 1985 | A database encryption scheme that allows the computation of statistics using encrypted data (Blakley and Meadows, 1985) |
| 1982 | Signature protocols for RSA and Other Public-Key Cryptosystems (Denning, 1982) |
| 1978 | On data banks and privacy homomorphisms (Rivest et al., 1978b) |
4 Overview of partial homomorphic encryption schemes
Algorithms supporting the idea of homomorphic encryption have been around for quite some time, as discussed by Section 3. In this section, two PHE schemes, ElGamal (1985) and Paillier (1999), will be covered. These were chosen so that an addition and a multiplication scheme were shown. This section will first introduce the idea of public key encryption, since both of these schemes fall into that category. Before describing El Gamal and Paillier in detail, examples of addition and multiplication are included.
4.1 Public key encryption
Diffie and Hellman (1976) introduced the concept of public key encryption, also known as asymmetric cryptography in 1976. Like FHE today, practical implementations of public key encryption were limited. However they are now widely used, including the El Gamal and Paillier schemes. Both of these schemes use a large prime number for a modulus operation, which is a security parameter. It is important to note however that even though these schemes can provide homomorphic operations, because of the nature of modulus operation, if the input or output values are greater than the modulus, results may not be as expected.
Looking at an example of public key encryption, Alice, Bob and Claire are good friends who send each other online chat messages at night after school. However, Alice and Bob would like to throw Claire a surprise birthday party. The problem is that neither Alice or Bob can figure out how to remove Claire from the chat session. But they do not want Claire to be able to see their conversion because it will ruin the surprise. One solution to this problem is for them both to create a private and public key, known as public key encryption. Then they can send their public key to everyone in the chat session. This allows Bob to encrypt a secret message to Alice using her public key, before broadcasting it in the chat session. Only Alice will be able to decrypt and read the message, meaning Claire is unable to read any messages about her surprise party.
However looking at the bigger picture, it also prevents malicious users from reading the messages as well. For example, the chat services’ administrators can only see the public key and encrypted messages. The same applies for any user sniffing the network, and finally this means that even if the chat service gets compromised, Alice and Bobs chat history is safe. This is not to say that the encrypted chat is 100% guaranteed to be safe and secure, but it adds another layer of protection to their data.
Therefore, public key encryption proves a means to encrypt data that only the holder of the private key can read. Anyone can gain access to the public key, which is used to encrypt the data. But ideally, only one person/system has the private key to decrypt the data. Everyone using the Internet would have experienced public key encryption, but probably without knowledge. For example, Hypertext Transfer Protocol Secure (HTTPS) sets up a secure tunnel using public key encryption within a browser. The client sends data to the server using the servers public key, and the server sends data back to the client using the clients public key. The setup of the keys is a bit more complicated than the example before, but it all happens in the background.
When designing and setting up a cloud service, it is important to consider how public key encryption will play a role in making the service more secure. Providing secure channels for authentication is a must today, and HTTPS is a viable solution. However, there are other ways to make the service more secure, like the use of PHE. Some real-world examples of homomorphic encryption will be covered in Section 6, but now El Gamal and Paillier’s scheme will be described to show how simple it is to implement PHE.
4.2 El Gamal
The security strength of El Gamal is based on the hardness of solving discrete logarithms, which was first proposed in 1985 by ElGamal (1985). Conceptually, El Gamal supports homomorphic multiplication operations on encrypted data. The key generation algorithm is given in Algorithm 1.
Now that the keys are generated, the algorithms to encrypt E(x) and decrypt D(x) are given in Algorithms 2 and 3, respectively.
Line 2 in Algorithm 2 allows us to hide k, so that it can be removed from t when we are decrypting the message. We discard k so that it remains a secret and cannot be leaked. This is necessary because the strength of this algorithm is based upon solving for k is hard. Therefore, if a malicious user gains access to k, they can decrypt the message without the private key.
It is important to understand the proof of encryption and decryption as it shows how the public and private keys cancel each other out, leaving the original message. This allows an appreciation of the mathematics behind El Gamal. Even though to implement an encryption algorithm does not require knowledge of how they work, security holes found are often in the implementation, and not the algorithm itself.
Because the algorithm only uses multiplication operations on the message value, it is quite easy to see how it supports homomorphic multiplication operations. Given a and b, we want to show that encrypting them, multiplying, then decrypting gives a × b.
D(E(a)×E(b))modp=ta×tb×(ra×rb)−dmodp
First, when the r values are multiplied, because the k values are random, then adding them still gives a random k.
⇒r=ra×rbmodpr=αka×αkbmodpr=αka+kbmodpr=αkmodp
The multiplication of the t values also involves random ks, which can be combined in the same manner. This leaves the a and b values multiplied together, along with βk.
⇒t=ta×tbmodpt=(βka×Ma)×(βkb×Mb)modpt=βka+kb×Ma×Mbmodpt=βk×Ma×Mbmodp
Now by substituting the t and r values into the decryption equation, the αs cancel themselves out, resulting in the decrypted value equaling a × b.
⇒D(c)=(βk×Ma×Mb)×(αk)−dmodpD(c)=(αd)k×Ma×Mb×(αk)−dmodpD(c)=Ma×Mb×(αdk×α−dk)modp∴D(c)=a×bmodp
To this point, the mathematics show that El Gamal supports homomorphic multiplications. However to conclude, an example of El Gamal in operation will be shown. Given 6 and 5, we want to solve E(6) × E(5) where p = 47, α = 7, d = 35, and β = 735 mod 47 = 17. Also this example will show that addition is not supported.
Encrypt 6 Encrypt 5
k=41r=741mod47=42mod47t=1741×6mod47=14mod47E(6)=(42,14)k=29r=729mod47=8mod47t=1729×5mod47=23mod47E(5)=(8,23)
Calculate E(6) × E(5) Calculate E(6) + E(5)
=E(6)×E(5)=(42×8,14×23)=(7,40)=E(6)+E(5)=(42+8,14+23)=(3,37)
Decrypt (7,40) Decrypt (3,37)
=7−35×40mod47=30mod47=3−35×37mod47=7mod47
4.3 Paillier cryptosystem
Proposed in 1999 by Paillier (1999), the Paillier cryptosystem is based on the problem that computing nth residue classes is computationally intensive. The nature of the algorithm allows for homomorphic addition operations to produce the current answer once decrypted. The key generation for Paillier Cryptosystem given in Algorithm 4, is a bit more complicated than El Gamal.
To encrypt a message, the message is used as the exponent for g, then a random value is raised to the other public key value n, as shown in Algorithm 5. This produces a cipher value in modulo n2. Decryption is again a simple equation, like El Gamal, and is given in Algorithm 6. Note that the definition for L(x) was given with key generation.
The proof of the encryption and decryption will be now given to show how the public and private key values cancel each other out. This is important because it will help to show why the Paillier Cryptosystem can support homomorphic addition operations.
If an addition operation is desired to be computed on the encrypted data, it is actually a multiplication operation that needs to be used. This is because the message is encrypted as an exponent. Therefore to add exponents, a multiplication operation needs to be computed on two values of the same base, which in this case is g. Note that because the r0 and r1 values are random, they can be combined to form another random value r.
D(E(a)×E(b))=a+b⇒c=ca×cbmodn2c=ga×rn0×gb×rn1modn2c=ga+b×rn0×rn1modn2c=ga+b×rnmodn2∴D(c)=a+b
5 Fully homomorphic encryption
There are many schemes being introduced today that claim to support FHE (Armknecht and Sadeghi, 2008; Gentry, 2009a,b; Van Dijk et al., 2010; Brakerski and Vaikuntanathan, 2011; Gentry et al., 2013; Brakerski and Vaikuntanathan, 2014). In this chapter, we will focus on just one which uses the Learning With Errors (LWE) problem for FHE as described by Gentry et al. (2013). They call their method the approximate eigenvector method, which allows homomorphic addition and multiplication computation. This is achieved by using matrix addition and multiplication operations and without the need for bootstrapping user keys.
This section will cover some of the ideas that the approximate eigenvector algorithm is based upon. Lattices are a key building block and are explained first, before the problems that help make this algorithm hard to break are covered. Finally, the algorithm will be described, including a small example of homomorphic encryption.
5.1 Lattices
In order to understand why lattices are useful for FHE, we must first understand the basic properties of a lattice.
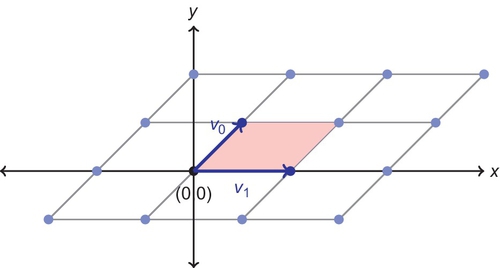
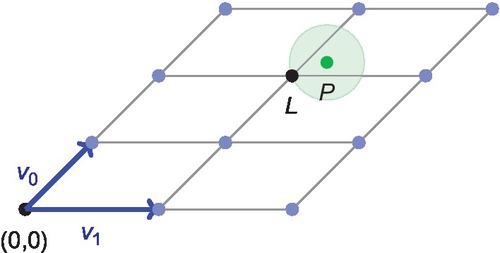
It is important to note that the same lattice can be formed from different basis vectors; therefore, it is said that a lattice is made up of an unique set of vectors which are the closed to the origin.
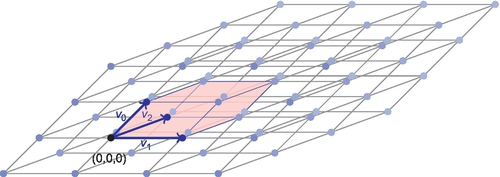
Any point that is the result of combining these vectors is known as a lattice point, and the region that can be translated by a lattice point while repeating the pattern is known as the fundamental region. The fundamental region is used to calculate the determinate of a lattice, which is the volume of the fundamental parallelepiped and represents the reciprocal of the density. Looking at the example in Figure 2, we are given the basis vectors v0 and v1, and combining these vectors together in many different ways gives a grid pattern of lattice points. The fundamental region is shown in red (dark gray in the print version), and with this simple 2D example it is easy to see how to repeat the fundamental region to continue the pattern.
Now imagine adding a basis vector v2 which is on the z-axis, making the lattice three dimensions as shown in Figure 3. The square fundamental region is replaced with a cubic one. As humans, lattices beyond three dimensions can be difficult to picture, but larger dimensions are simple for a computer to compute over as the input it receives is a matrix. In August 2010, IBM held a competition (IBM, 2010) for contestants to break FHE keys. The “toy” challenge used for testing had a dimension of 512, and the hardest problem had 32,768 dimensions. This shows that the number of dimensions is directly related to the strength of the key.
5.2 Lattice problems
A couple of hard lattice problems which cryptography can be built upon is the Closest Vector Problem (CVP) and Shortest Vector Problem (SVP).
In Figure 4, it is easy to see the closest lattice point in pictorial form. However because a computer is only given a matrix, and the dimensions are much larger, it makes finding the closest lattice point much more computationally intensive.
Non zero is important because every lattice technically has a zero vector. In Figure 4, this is simply v0 because the example lattice is only showing the basis vectors. However, if larger vectors are given, there may exist a smaller vector which can make up the fundamental region. Note that CVP is actually a generalization of SVP, because if you are given an oracle (function) for CVP, it is possible to find the shortest vector by querying the oracle (Micciancio and Goldwasser, 2002; Goldreich et al., 1999). Therefore because CVP is a NP-Hard problem, so is SVP (van Emde-Boas, 1981; Micciancio, 2001).
5.3 Learning with errors
The LWE problem was introduction by Regev (2010) and is widely used for a range of cryptographic functions, such as public key encryption (Peikert, 2009). This is because it claims to be as hard as worst-case lattice problems (Regev, 2010), implying that any functions built upon LWE are secure. This was briefly discussed in Section 5.2. It is also currently assumed that worst-case lattice problems are even secure against the likes of quantum computers.
Relating this back to lattices, the definition means distinguishing vectors that are created from a set of noisy (contains some error) linear equations between uniformly random vectors. Looking at an example from Regev (2010), we are given the set of linear equations shown in Figure 5 where in this case each equation has an error of approximately ± 1, then all we have to do is solve for x. But by introducing the error it makes solving x more difficult. If you were to try and solve the set of equations using Gaussian elimination (row reduction), for example, the errors would accumulate making the result invalid.
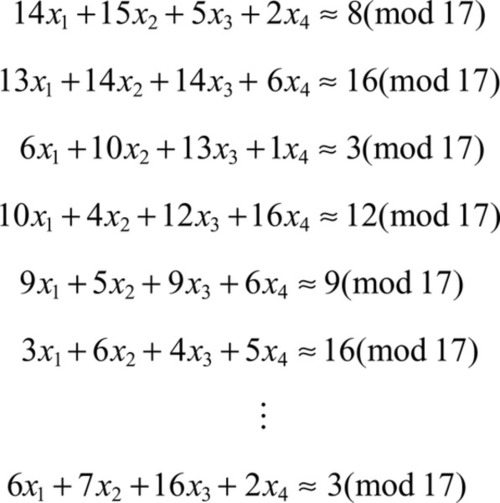
Given 2O(nlogn)![]() equations we can deduce the secret x in 2O(nlogn)
equations we can deduce the secret x in 2O(nlogn)![]() time but this approach is based more around luck than sense. A simpler technique is the Maximum Likelihood algorithm, which only requires O(n) equations and computes the only value for x that can satisfy the equations. This is achieved with brute force by computing all possible values, resulting in a run time of 2O(nlogn)
time but this approach is based more around luck than sense. A simpler technique is the Maximum Likelihood algorithm, which only requires O(n) equations and computes the only value for x that can satisfy the equations. This is achieved with brute force by computing all possible values, resulting in a run time of 2O(nlogn)![]() (Regev, 2010). Currently, the best, known algorithm for solving LWE is by Blum et al. and requires 2O(n) equations and time (Blum et al., 2003), which relates to the fact that the best algorithms for solving lattice problems need 2O(n) time (Ajtai et al., 2001; Micciancio and Voulgaris, 2013).
(Regev, 2010). Currently, the best, known algorithm for solving LWE is by Blum et al. and requires 2O(n) equations and time (Blum et al., 2003), which relates to the fact that the best algorithms for solving lattice problems need 2O(n) time (Ajtai et al., 2001; Micciancio and Voulgaris, 2013).
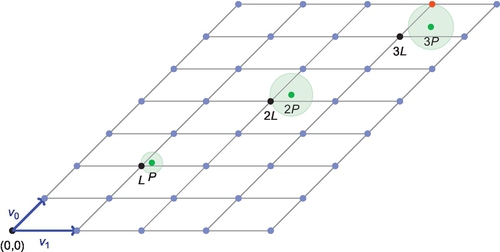
Therefore, homomorphic schemes built on the LWE problem need to keep the errors relatively small otherwise results can become invalid. For example, Figure 6 shows a lattice point L, and the point P which has some error added so that by solving CVP, L will be the result. If P is doubled, 2L is still the closest lattice point, however by adding P again giving 3P, the closest lattice point is not 3L, but instead 3L + v0; therefore, the result is now invalid. Managing this error is one of the key challenges to homomorphic encryption in general and is a contributing factor to the performance limitations of current FHE schemes, such as the Approximate Eigenvector algorithm.
5.4 Approximate eigenvector algorithm
The Approximate Eigenvector scheme for FHE was proposed by Gentry et al. (2013) in 2013, which uses the LWE problem previously described in Section 5.3. This scheme allows for addition and multiplication homomorphic operations to be computed the same as matrix addition and multiplication operations, for most cases. Gentry et al. claim this makes the scheme asymptotically faster and easier to understand (Gentry et al., 2013), which is why we chose it for this chapter. The formal definition of an eigenvector is given below, where T is a square matrix and λ is a scale. Essentially for →v![]() to be classified as an eigenvector for the matrix T, the result must be equivalent to multiplying →v
to be classified as an eigenvector for the matrix T, the result must be equivalent to multiplying →v![]() by some scale factor. In this scheme, →v
by some scale factor. In this scheme, →v![]() is an approximate eigenvector, not a perfect one.
is an approximate eigenvector, not a perfect one.
To make this a leveled scheme (i.e. it will work up to a certain depth), the error must be controlled. As seen in Figure 6, controlling the size of the error is extremely important, so that the decrypted value will be correct. This is achieved by flattening the cipher matrix so that it contains values in {0,1}. Flattening uses bit decomposition operations, which does not affect dot product operations on the matrices. This allows homomorphic operations still be computed correctly, while keeping the errors small.
We will now cover the scheme, starting with the security parameters and function definitions. Before giving the key generation, encryption and decryption algorithms. We will then prove that the scheme does in fact support homomorphic addition and multiplication operations, which will be followed by an example.
Key generation
Given the security parameters, the secret key generation is shown in Algorithm 7, where →s![]() is the secret key. The vector →t
is the secret key. The vector →t![]() is randomly generated with integer values in modulo q (no values are larger than q) and has the length n. The length is the same as the number of lattice dimensions so that a dot product can be computed over the lattice matrix. The secret key →s
is randomly generated with integer values in modulo q (no values are larger than q) and has the length n. The length is the same as the number of lattice dimensions so that a dot product can be computed over the lattice matrix. The secret key →s![]() has one more value than →t
has one more value than →t![]() (i.e., n + 1), which appends 1 to the front of →t
(i.e., n + 1), which appends 1 to the front of →t![]() multiplied by − 1. Vector →v
multiplied by − 1. Vector →v![]() is the result of the Powersof2 function defined earlier.
is the result of the Powersof2 function defined earlier.
Once the secret key is generated, we can generate the public key matrix A, as shown in Algorithm 8. We start by randomly generate a matrix B with integer values in modulo q, with the size n × m. Now we must generate an error vector →e![]() of size m using the error distribution χ. To link together the public and secret key, the vector →b
of size m using the error distribution χ. To link together the public and secret key, the vector →b![]() must be calculated using random vector →t
must be calculated using random vector →t![]() from the secret key generation step, with some error added. Finally, the public key matrix A can be created by joining together the vector →b
from the secret key generation step, with some error added. Finally, the public key matrix A can be created by joining together the vector →b![]() and the matrix B, such that the first column of A is the →b
and the matrix B, such that the first column of A is the →b![]() , with the remaining columns being B. This will be easier to understand in the example given in Section 5.4.1.
, with the remaining columns being B. This will be easier to understand in the example given in Section 5.4.1.
5.4.1 Encryption and decryption
Now that the public and secret keys can be generated, we will show how they can be used to encrypt and decrypt data. The algorithm for encrypting an integer u in modulo q is given in Algorithm 9. In order to make cipher values different even if the input message u is the same, first we must generate a random matrix R. The matrix R is then multiplied (dot product) by the public key matrix A before applying the bit decomposition function. This result will vary each time which helps hide the message. The message u is multiplied by an identity matrix I of size N × N (u is diagonally added to a square matrix of zeros), before being added to the result of the bit decomposition function. The message u becomes the scale value λ in the eigenvector definition shown earlier.
Decrypting a cipher matrix can be achieved using a couple of different techniques, depending on the value chosen for q. If q is a power of 2, then the MPDec function can be used for decryption. Otherwise the standard Decrypt function will have to be used. First, we will describe the standard Decrypt function given in Algorithm 10, where C is the encrypted cipher matrix. Once a value for i has been chosen which meets the conditions shown, compute the inner product (scalar product) of the ith row in matrix C, and →v![]() . Now the message u can be recovered.
. Now the message u can be recovered.
The description of the MPDec function shown in Algorithm 11 is better shown in Section 5.4.1 and in Micciancio and Peikert (2012). However to summarize, we can recover the least significant bit of the message u from the ℓ − 2 column of the cipher matrix C. Then process the columns back to the 0th column, which will contain the most significant bit. Whether the bit should be high or low, given the column Ci, and the current result will now be described. Note that the result should be initialized to 0 when computing Cℓ−2.
Proof for homomorphic addition and multiplication
Now that the algorithm has been described, we will now prove that homomorphic addition and multiplication operations are supported.
Given:
Cn⋅→v=un⋅→v+→en(where→eis small)
Addition:
(C1+C2)⋅→v=(C1⋅→v)+(C2⋅→v)=(u1⋅→v+→e1)+(u2⋅→v+→e2)=(u1+u2)⋅→v+→e1+→e2=(u1+u2)⋅→v+→e(where→eis small)
Multiplication:
(C1⋅C2)⋅→v=C1⋅(u2⋅→v+→e2)=(C1⋅→v)⋅u2+(C1⋅→e2)=(u1⋅→v+→e1)⋅u2+(C1⋅→e2)=u1⋅u2⋅→v+(u2⋅→e1)+(C1⋅→e2)=u1⋅u2⋅→v+→e(where→eis small)
Example
To help make this algorithm easier to understand, a simple example will now be explained for the addition of 5 and 20. Due to the large sizes of the matrices that are generated, they will be shown in a compressed form. The following parameters have been chosen for this example in order to keep the sizes of the vectors and matrices small.
q=65,536n=3χ=8m=48ℓ=17N=68
Now we need to generate the secret key. First, →t![]() is randomly generated with values in modulo q. The secret key vector can then be created, be simpling joining 1 and the negative values of →t
is randomly generated with values in modulo q. The secret key vector can then be created, be simpling joining 1 and the negative values of →t![]() . For example, →t0=4754
. For example, →t0=4754![]() , becomes −4754, then find the modulus in q, −4754 + 65,536 which results in 60,782.
, becomes −4754, then find the modulus in q, −4754 + 65,536 which results in 60,782.
→t=[475438,89647,731]→sk=[160,78226,64017,805]
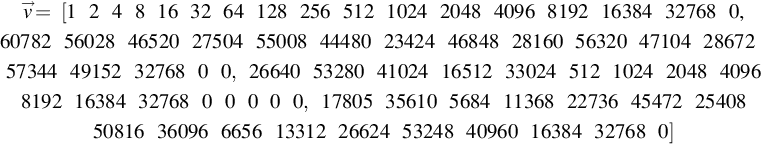
Calculating →v![]() involves computing the Powersof2 function on →sk
involves computing the Powersof2 function on →sk![]() . The first 17 values are powers of 2 from 20 to 216, because they are multiplied by →sk0
. The first 17 values are powers of 2 from 20 to 216, because they are multiplied by →sk0![]() which is 1. Note that these are the modulus values in q, hence 1 × 216 = 0. Now we do the same but instead multiply 20 to 216 by →sk1
which is 1. Note that these are the modulus values in q, hence 1 × 216 = 0. Now we do the same but instead multiply 20 to 216 by →sk1![]() . Therefore, the next value is 20 × 60,782 = 60,782, followed by 21 × 60,782 = 121,564 = 56,028 (mod q).
. Therefore, the next value is 20 × 60,782 = 60,782, followed by 21 × 60,782 = 121,564 = 56,028 (mod q).
→v=[1248163264128256512102420484096819216384327680,60782560284652027504550084448023424468482816056320471042867257344491523276800,26640532804102416512330245121024204840968192163843276800000,1780535610568411368227364547225408508163609666561331226624532484096016384327680]
The public key now needs to be generated. We randomly generate the matrix B and vector →e![]() .
.
B=[2415915679…1945715206022716241…2138855398403289895…369606044]
→e=[146553216552965531655283565526101655335111165531965521655326553065520146553565534406551466655310667716465529655276553571346552825]
Compute the vector →b![]() .
.
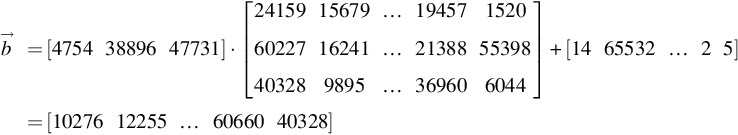
→b=[47543889647731]⋅[2415915679…1945715206022716241…2138855398403289895…369606044]+[1465532…25]=[1027612255…6066040328]
Now we can join the vector →b![]() with the matrix B, to form the matrix A.
with the matrix B, to form the matrix A.
A=[1027612255…60660403282415915679…1945715206022716241…2138855398403289895…369606044]
That concludes the key generation, so we can start encrypting an integer value. The encryption process for 20 will be shown now, and the cipher matrix for 5 will be given. So first we randomly generate the matrix R. It is important to note that the random matrix R will be different for the encryption of 20 and 5. Then we multiple this random matrix by the public key (matrix A).
R=[00…0000…10………01…1000…11]A⋅R=[2348231088…507486223962449556…36113626896237956720…3867535542466276…2043031877]
Because we want values in {0,1} to keep errors small, we must now bit decompose A ⋅ R. If we take the first value 23,482, converted to a 17 bit value it becomes 001011011101110102. This is then put into a matrix vertically, from the least significant bit. Only the values 23,482, 31,088, 507 and 48,622 are shown. We must also calculate the identity matrix and multiply it by the value u we are encrypting, which is 20.
BitDecomp(A⋅R)=[00…1010…1100…0110…1111…1011…1101…1110…1111…1110…0000…0111…0111…0101…0111…0000…0100…00………]u⋅IN=[200…00020…00………00…20000…020]
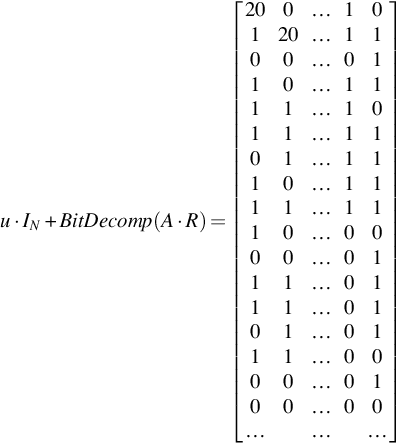
These two matrices now have to be added together. Note that in the example, only the top 17 rows are shown, hence only two additions of 20 appear.
u⋅IN+BitDecomp(A⋅R)=[200…10120…1100…0110…1111…1011…1101…1110…1111…1110…0000…0111…0111…0101…0111…0000…0100…00………]
After the addition, we must get the values small again. This involves using the Flatten function, which performs an inverse bit decomposition, then a regular bit decomposition. Taking the values in the 0th column [20, 1, 0, 1, 1, 1, 0, 1, 1, 1, 0, 1, 1, 0, 1, 0, 0], performing an inverse bit decomposition becomes the value 001011011101110102 + 20, resulting in 23,502. This value is then represented in bits from least to most significant bits 01110011110110100 and stored in the cipher matrix vertically. Note than when undecomposing column 1, the 20 is added as 20 ![]() 1. The final cipher matrix is given as E(20), and the cipher matrix for 5 is also given.
1. The final cipher matrix is given as E(20), and the cipher matrix for 5 is also given.
E(20)=[00…1010…1110…0111…1101…1000…1110…1111…1111…1110…0000…0111…0111…0101…0111…0000…0100…00………]E(5)=[11…0001…0011…0100…1111…1010…0101…1111…1110…0110…1001…1100…1001…0110…1010…1010…1100…00………]
With the encryption done, we can now perform the addition of the two cipher matrices. This is just a simple matrix addition operation. Note that if many operations are required, the result matrix will need to be flattened. If multiplication is performed on two cipher matrices. The result matrix will also need to be flattened. In this example, we do not require a flatten operation because the values are still small.
E(20)+E(5)=[11…1011…1121…0211…2212…2010…1211…2222…2221…1220…1001…1211…1112…0211…1121…1010…1200…00………]
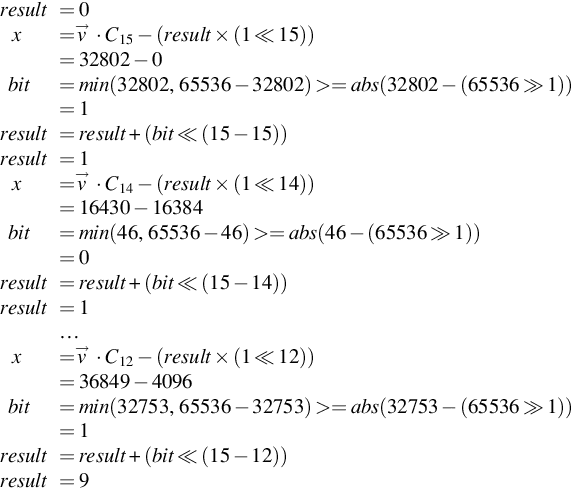
Because the q in this example is a power of 2, we can use the MPDec function to decrypt. Using MPDec allows us to start at column 15 and work back to column 0 to give the 16-bit answer. Column 15 contains the value for the 0th bit, and column 0 has the value for the 15th bit.
result=0x=→v⋅C15−(result×(1≪15))=32802−0bit=min(32802,65536−32802)>=abs(32802−(65536≫1))=1result=result+(bit≪(15−15))result=1x=→v⋅C14−(result×(1≪14))=16430−16384bit=min(46,65536−46)>=abs(46−(65536≫1))=0result=result+(bit≪(15−14))result=1…x=→v⋅C12−(result×(1≪12))=36849−4096bit=min(32753,65536−32753)>=abs(32753−(65536≫1))=1result=result+(bit≪(15−12))result=9
x=→v⋅C11−(result×(1≪11))=51252−18432bit=min(32820,65536−32820)>=abs(32820−(65536≫1))=1result=result+(bit≪(15−11))result=25
6 Homomorphic encryption in the cloud
Today real-world applications of FHE in the cloud are nigh-on impossible to find, due to the severe performance limitations of currently proposed schemes making them unattractive for cloud services to employ. Research for practical implementations of FHE are currently pursued by organizations such as IBM Research and Microsoft. But also by universities across the global, for example, Stanford and The University of Waikato (CROW, 2014). Until schemes are made practical, we will not see them in services exposed to the public. On the other hand, PHE has enabled some cloud services and systems to reap benefits. Some examples are:
• CryptDB (Popa et al., 2011) is a database privacy layer that explored the use of FHE for performing queries over encrypted data but opted do use a selection of techniques to perform different types of queries. For basic addition operations over integers, the Paillier cryptosystem (Paillier, 1999) was implemented, which offers PHE. When using Paillier, to perform the addition of two values x and y, the encrypted values are multiplied together, which when decrypted, is the equivalent of adding the unencrypted values together.
• Helios (Adida, 2008) is a cloud-based open-audit voting system, which as off version 2.0 uses homomorphic encryption to tally the votes (Adida et al., 2009). This allows all the votes to be submitted and tallied in an encrypted form, then only once the final votes have been cast and added to the tallies, is the result decrypted. The PHE scheme used is a variant of El Gamal, which was described in Section 4.2, Exponential El Gamal.
• Porticor (2014a), which was founded in 2010, is to the best of our knowledge one of the first commercial implementations of homomorphic encryption, which provides a secure cloud key management platform using PHE. The company states that FHE isn’t yet feasible for a real-world system (Porticor, 2014b), and that by only supporting a few computational operations you benefit from fast, reliable performance for your business-critical applications (Porticor, 2014b) while keeping the keys secure.
7 Future of homomorphic encryption and open issues
Homomorphic encryption in the cloud is still relatively young and is only being adopted at a slow rate. Even though FHE is currently not plausible to implement for real-world scenarios, there is no reason why PHE cannot offer cloud providers an extra level of security right now. Then in time migrate to FHE when schemes offer better performance. The cloud requires an increased level of security, and homomorphic encryption is a viable answer. Some cloud solutions have already realized this, like the samples in Section 6, but in the near future this will be more common across a far more diverse group of cloud applications and services.
As discussed throughout this chapter, there are still some problems with homomorphic encryption which will impact its future. For example, FHE can support more than a single operation. However, an open issue is that FHE also has limitations on supporting a wide range of operations/functions, even though this is the very definition of FHE. This is because two operations could be used to cancel each other out and make the security pointless. Supporting subtractions by an unencrypted value and comparing the encrypted value with zero would be one case. Because a malicious user can just subtract 1 until the encrypted value is zero, giving the answer. This leads to another issue, currently FHE is thought of as the perfect solution; however, it needs to be considered on an application by application basis. A one size fits all solution is not going to be as secure as a scheme which is designed for the application in mind. And finally, by having homomorphic encryption protect user information/data, it stops cloud services from learning information about them. This can stop targeted ads, selling anonymous user data and many other ways cloud services make money even though there is no cost to the end user. The issue is that even though users want to be more secure online, will they be willing to pay for the cloud service, or will they prefer the free, unsecured service instead? These are just some of the current issues that homomorphic encryption faces as it tries to become the future of security in the cloud.
8 Alternatives to homomorphic encryption
Cloud adoption by businesses handling sensitive data is slow because they cannot afford their data to be leaked. Be it their private cooperate data, or their customers data. This could be to protect their image, or because they are contractible obliged to keep the data confidential. While homomorphic encryption is a viable answer, there are other solutions which target this problem, and for some businesses could be a perfect fit for their business model or infrastructure.
A model widely adopted for securing cloud data is to provide a gateway between the cooperate network and the cloud (Salehi et al., 2014), which encrypts data before it leaves the network, and decrypts data from the cloud. This is similar to the Mega cloud service (Mega ltd, 2014) described early, however it is designed for enterprise, where Mega is intended more for personal use. That is not to say Mega cannot be used for enterprise, in fact it is perfect for small businesses, but the gateway solution is more powerful and flexible.
The general idea of using an encryption gateway is shown in Figure 7. This shows two computers within the company, used by Alice and Bob, that are connected to the companies internal network. Then any traffic leaving the internal network exists through what is known as the border router. However, there is a gateway that any data heading for the cloud service must go through. For example, Bob creates a files and wants to save it to the cloud. When the file is being saved, before it goes out onto the Internet, it must go through the gateway appliance. This gateway encrypts the file and forwards it to the cloud service via the border router. Then Alice wants to view this file, so she requests it from the cloud service. The encrypted file then goes back through the gateway appliance and is decrypted before reaching Alice. This guarantees that files are always encrypted before leaving the internal network to be stored on the cloud service. It also means that the company manages its own keys, unlike services like Dropbox. Alice and Bob are not affected by the encryption gateway, yet the companies data remains secure.
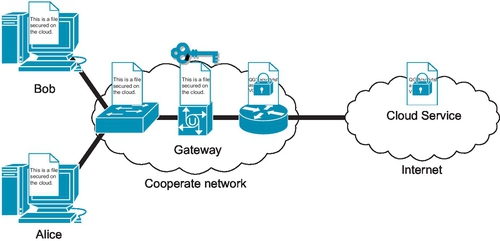
Encryption gateways can do more than just encrypting and decrypting data. RESeED (Salehi et al., 2014) allows searching over encrypted files in the cloud using regular expressions, by creating an index from the unencrypted files before they are encrypted and saved to the cloud. This device still has some limitations, such as the keys cannot be recovered off the device. So if the device has a fault and stops working, the encrypted data stored in the cloud is not recoverable. CipherCloud (2014) is another example of an encryption gateway, which supports cloud services such as Amazon Web Services, Gmail, and Office 365. These encryption gateway devices can be implemented into networks now, unlike solutions involving homomorphic encryption which are still years away from full-scale use.
9 Summary
This chapter has given an in-depth overview of homomorphic encryption schemes. It has provided proofs to show that the schemes can support homomorphic operations, while also providing examples to help make the mathematics and algorithms easier to understand. Homomorphic encryption will become more essential for cloud services as the performance of the schemes improves, allowing for more secure and trust worthy applications. Some cloud services are already benefiting from homomorphic encryption, and hopefully many more will follow.