Security as a service (SecaaS)—An overview
Baden Delamore; Ryan K.L. Ko Cyber Security Lab, Department of Computer Science, University of Waikato, Hamilton, New Zealand
Abstract
With cloud computing facilitating the migration of platforms, infrastructure and software to the cloud, security services are now following suit. Security as a service (SecaaS) is inherently a business model in which organizations can purchase on-demand security solutions to protect their data, applications, and systems, while taking advantage of what cloud computing has on offer. This chapter explores the evolution from traditional on-premise and managed security solutions to the SecaaS model, and evaluates the supporting and opposing arguments for the adoption of cloud security services. Furthermore, an overview is given for cloud security services categories with additional focus areas presented, and critical gaps identified in the literature.
1 Introduction
1.1 History repeating itself
The inception of cloud computing with respect to information technology (IT) represents a significant change in the way we process, store, and utilize data. This change has similarities with the way businesses used power at the turn of the century. In the late 1890s, every factory or business had in its basement a smoke belching, fuel consuming power generator that was tended to by gray boiler suited men who serviced it and kept it running as best as they could. This was fine when things worked nicely. But when they did not, more often than not, the machines ground to a halt, the lights went out and nothing could be done.
In the early 1900s, the Chicago-based Edison power company developed the turbine power station which could generate and distribute large-scale power to business. This provided cheaper, more reliable, and cleaner power than any factory or business base generator without many of the headaches. And by 1920 most businesses had made the switch to the grid. Business now access power simply by plugging into the wall.
Today we take virtually unlimited power for granted, and we cannot imagine it any other way. At the time of writing, a similar revolution is happening in IT called Cloud Computing. Enterprises no longer have to buy, build, and manage costly computer facilities on-site. Just as businesses learned that power provided by a specialized power company improved reliability and quality, cloud computing has been proven to be more secure, more reliable, more scalable, and ultimately more affordable than traditional on-site IT. This is why most new business applications are now deployed in the cloud.
1.2 The growth of cloud computing services
Since its introduction to the mass market, cloud computing has seen a phenomenal level of growth all over the world (Ko, 2010). It represents one of the most significant shifts in IT many of us are likely to see in our lifetimes-reaching the point where the point where computing as a utility has so much innovation potential one cannot yet imagine. Many factors such as:
• Less maintenance: Hardware, applications, and bandwidth are managed by the provider.
• Continuous availability: Public cloud services are available where you are located.
• Scalability: Pay online for the applications and data storage you need.
• Elasticity: Private clouds can be scaled to meet your changing IT systems demands.
have influenced the transition from traditional on-site management to the cloud (NIST, 2014). Despite this rapid transition to the cloud, the deployment of cloud-based security services forms important challenges that need to be addressed. Hence, an extensive overview of security as a service (SecaaS) is presented in this chapter.
1.3 Defining security as a service
At its core, SecaaS is a business model in which a security service provider integrates their security services into a corporate infrastructure, typically on a subscription basis delivered from the cloud without requiring on-premises hardware. This approach is one that is more cost effective as it does not require an individual or corporation to purchase, deploy or maintain their own infrastructure. Rather, ather businesses only need to subscribe to the service to reap SecaaS benefits.
1.4 Motivation for this chapter
SecaaS represents a new model for the deployment, management, and utilization of security services based on cloud computing principles. Although SecaaS is often considered an emerging trend in IT, the literature around it is sparse. This fact, coupled with an expected proliferation of cloud-based services over the coming years, demands that an overview of such a model is timely. Moreover, there exists a growing interest from business’ for the adoption of this model. In fact, a press release in 2013 from Gartner, a research and IT consulting company, anticipated growth over the next 2 years for cloud security services to increase by nearly 40% (Gartner, 2013).
This is exciting times for business, academia, and corporate organizations who wish to protect their intellectual property and data from traditional threats, without major overhead to the day-to-day running of their operations. As we will soon discuss in this chapter there are a myriad of benefits for shifting to cloud-based security services, but with that said, there exists skepticism around the adoption of it.
This chapter aims to demystify cloud-based security services and provide a compelling discussion with regards to traditional on-premise, managed security services (MSS) and cloud-based security models.
2 Background
This section aims to explain the background for SecaaS. This extends to the adoption of SecaaS which is defined in Section 1.3. Subsequently, an overview of related work regarding the adoption of similar technological innovations is provided in Section 2.1.
2.1 Security as a service
As mentioned, SecaaS is a business model that facilitates outsourcing of security management, engagements, and technologies to a trusted third party (cloud security service providers). It is further defined as a service-orientated approach and consequently the evolution of traditional security landscapes (Senk, 2013a; Hafner et al., 2009; Senk, 2013b). It combines managed services and security intelligence for the purpose of integrating security with traditional business processes in a cloud environment, and is arguably a cost-effective and more efficient solution with respect to previous security models.
In order to classify SecaaS, an extensive market-oriented taxonomy was undertaken by Kark which pertains to outsourced security services, specifically MSS (Kark et al., 2014). The results from the taxonomy provided Senk et al. with a sound foundation for their classification of SecaaS (see Table 1). His classification scheme was later validated by a survey of existing SecaaS offerings.
Table 1
Classification of SecaaS Applications
| Application type | Description |
| Application security | Secure operation of software applications (e.g., application firewalls, code analyzers) |
| Compliance and IT Security management (ITSM) | Support of the client organizations compliance and IT security management (e.g., automatic compliance checks, benchmarking) |
| Content security | Protection of content data from intended attacks and undesired events (e.g., e-mail encryption, filtering of network traffic) |
| Endpoint security | Protection of servers or client computers in networks (e.g., malware protection, host-based intrusion detection) |
| Identity and access management | Identification of users, provisioning of user identity attributes and assignment of necessary privileges (e.g., single sign-on, multi-factor authentication) |
| Devices management | Remote management of client-sided security systems (e.g., intrusion detection and prevention systems) |
| Security information and event management (SIEM) | Specific security-related functions for monitoring complex IT systems (e.g., archiving and analysis of log-data, forensic analysis) |
| Vulnerability and threat management (VTM) | Detection of threats apart of eminent internal security incidents (e.g., patch management, notifications on current attacks) |
In an empirical study conducted in cooperation with the German Federal Association for IT, it was discovered that statistically, there were three main drivers for the adoption of SecaaS (Senk, 2013b):
• Perceived ease of adoption: Degree to which the adopter believes that the SecaaS adoption is effortless, both technically and organizationally speaking;
• Perceived usefulness: Degree to which the adopter believes that the adoption increases its performance—this includes cost and quality-related benefits;
• Trust: Degree to which the adopter believes that the adoption is free of risks, which includes mainly security-related but also social and strategic risks.
The authors for that study also noted the majority of existing SecaaS products cover Endpoint Security or Content Security applications (Senk, 2013b). Furthermore, they outline compliance deficiency with respect to Cloud and SaaS design principles in existing systems, in particular inflexible pricing models that restrict the potential value of existent SecaaS systems (Senk, 2013b).
According to the SecaaS model (Senk, 2013a), the delivery of security services differs clearly from traditional on-premise deployments and MSS provisioning (see Figure 1). On-premise security systems are deployed, operated, and maintained on the client’s side and requires the allocation of trained IT and human resource capacities. MSS are described as services that are outsourced to another company which involve prior negotiation of Service Level Agreements (SLA) (Deshpande, 2005). Therefore, it is the MSS who is responsible for the management and operation of systems. Further, it is often required that dedicated hardware and systems are deployed within the client organization, and due to the initial effort required, clients are bound by up-front commitments and long-term relationships with providers.
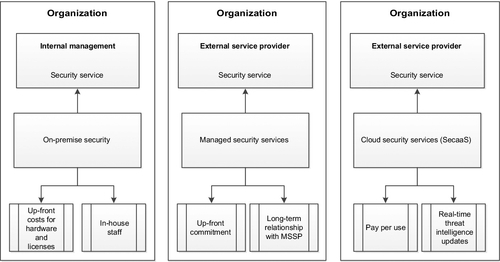
Traditional MSS provisioning follows the Application Service Provider (ASP) model (Senk, 2013b; Quirchmayr et al., 2006). In contrast, SecaaS solutions are fully operated and maintained by the cloud service provider. Thus, it is not necessary for clients to require dedicated hardware or software. Rather, services are provided to clients by means of a virtualized multi-tenant architecture that ensures the highest degree of capacity utilization. This makes the service usage highly cost-effective to the client and enables fine-grained pay-per-use models.
2.2 Outsourcing model
The SecaaS model draws similar motivations from typical outsourcing situations. Just like manufacturing and transportation outsourcing commonly found in supply chains, security is an integral component to be considered by every business even though they may not have the resources or capability to execute it to the highest level. Outsourcing models for security assessment enables companies to achieve the following: (Bill Lakenan, 2001; Quin, 1999)
• Economies of scale: From the SecaaS provider point of view, an important objective of outsourcing is to reduce operational costs through the aggregation of service contracts from many different customers. The SecaaS provider would be able to disseminate the benefits of their latest developments around security and protection, and pass them on to their customers (regardless of the number of customers).
• Risk pooling: SecaaS also allows the customers to transfer the requirements for constant knowledge updating of security risks and mitigation to the SecaaS companies. This means that the latest developments and vulnerability mitigation techniques are implicitly shared between many of the customers while there is a higher-level overview of the trends developing.
• Reduced capital investment: The costs of hiring security resources are greatly reduced through SecaaS services since the customers’ system administrators just need to ensure that the systems are regularly inspected by the SecaaS services—maximizing productivity.
• Focus on core competency: By carefully outsourcing security requirements to SecaaS suppliers, the customer can focus on its core strength without compromising on security capabilities.
• Increased flexibility: With SecaaS outsourcing models, customers can also better react to changes and developments in the rapidly developing security industry.
3 Traditional security
In this section we expand on our coverage of traditional security services (on-premise and MSS) with respect to the SecaaS model.
3.1 On-premise
On-premise security refers to the hardware and software solutions that protect businesses data from outside and inside threats. Such solutions require the hardware that houses the security infrastructure to be maintained and updated on-site. The upside of approach is that all the specialized hardware and software are managed by the businesses own internal IT department and thus does not rely on any external service providers. It is worthy to note that there are drawbacks to this solution, some of which are covered in Table 2.
Table 2
On-Premises versus SecaaS
| SecaaS | On-premises | |
| Cost | Pay as you go, per user, per month, etc. | Up-front capital costs for hardware, software licensing, lab space, air conditioning, etc. |
| Customization | Customizable and scalable services | Somewhat customizable depending on software vendor |
| Hardware | Hardware and software owned reside at provider site | Customer must provide hardware and system platforms to run apps |
| Security | Access to SecaaS apps is via Internet | Less risky because of on-premises location |
| Mobile access | Accessible via browsers running on mobile devices | Limited access to business applications via browsers running on mobile devices |
| Integration | Limited integration, even though this is an important requirement | Integration with existing software is commonplace |
| Control | SecaaS provider controls systems and is entrusted with customer data | Control of systems and data |
Our comparison between cloud-based and on-premises solutions illustrates the differences in terms of cost, control, security, and the likes. While maintaining hardware on-site is regarded as less risky, the associated costs for hardware and software are significantly higher than the “pay as you go” approach that SecaaS offers. This is exacerbated by the fact that the price of hardware is to be covered up front and the on-going cost of maintaining, upgrading, and servicing the hardware. Moreover, it is likely that on-premise training for staff is likely to be a recurring cost.
3.2 Managed security services
MSS are characterized in that a dedicated security service instance is set up for a client organization by an external service provider. This approach involves the prior negotiation of individual SLA (Senk, 2013a; Deshpande, 2005). Such a service, in the past, has been provided by a range of different entities. For example, start-ups, established companies, telecommunication and computer companies, ASPs and consulting firms are examples of businesses who have been involved in providing MSS for their customers. Listed below are some of the services that MSS provide that are discussed in the literature (Deshpande, 2005).
• Perimeter management and network boundary protection: This service usually includes installation and maintenance of virtual private networks (VPNs), IDSs / IPSs, and firewalls.
• Managed security monitoring (MSM): MSM is more focused on the monitoring of the client’s network. It deals with interpreting whether data passing through the network is malicious or benign and deals with incident response measures.
• Vulnerability assessment/penetration testing: This service deals with identifying flaws within a company’s services (e.g., web, mail, network, etc.) that could lead to exploitation by adversaries.
Although MSS covers a range of security services, there are trade-offs between this model and SecaaS. For example, consider a firewall under the MSS scheme which is outsourced to an MSSP (managed security service provider). The client who subscribes to the service need not worry about log inspection, rather it is the responsibility of the MSSP to collect, store, and review the logs and take the necessary mitigation steps. With the SecaaS model, given the same scenario, only the delivery model is outsourced—the mechanics of the collection and storage tasks including the software and hardware that enable it—but it is the clients personnel or staff that are responsible for the firewall security. Therefore, the role of log inspection, report generation is maintained by the client. This general definition is the same for any security task, whether it is e-mail security, vulnerability assessment, network intrusion, SIEM, and so forth.
4 Secaas categories of service
Based on our observations of the literature for categories of service regarding SecaaS, we have identified two main viewpoints around this topic. The first comes from Senk et al. in their paper Adoption of SecaaS (Senk, 2013a), and the second is the Cloud Security Alliance in their paper Defined Categories of Service (Cloud Security Alliance, 2011a). The CSA working group is perhaps best known for its extensive research around the adoption of cloud computing, and its guidelines for best practices within cloud environments. In their paper, the CSA notes that the following service categories were identified as most significant to experienced industry consumers and security professionals (Cloud Security Alliance, 2011a): identity and access management (IAM); data loss prevention (DLP); Web security; email security; security assessments; intrusion management; security information and event management (SIEM); encryption; business continuity and disaster recovery; network security. For the purposes of this section, we have classified the above into the four classes described by the CSA, namely protective; detective; preventive, and reactive. These are given in Table 3.
Table 3
SecaaS Categories by Class
| Category | Domain | Protective | Preventative | Detective | Reactive |
| 1 | Identity and access management | X | X | ||
| 2 | Data loss prevention | X | |||
| 3 | Web security | X | X | X | |
| 4 | Email security | X | X | X | |
| 5 | Security assessment | X | |||
| 6 | Intrusion management | X | X | X | |
| 7 | Security information and event management | X | |||
| 8 | Encryption | X | |||
| 9 | Business continuity and disaster recovery | X | X | ||
| 10 | Network security | X | X | X |
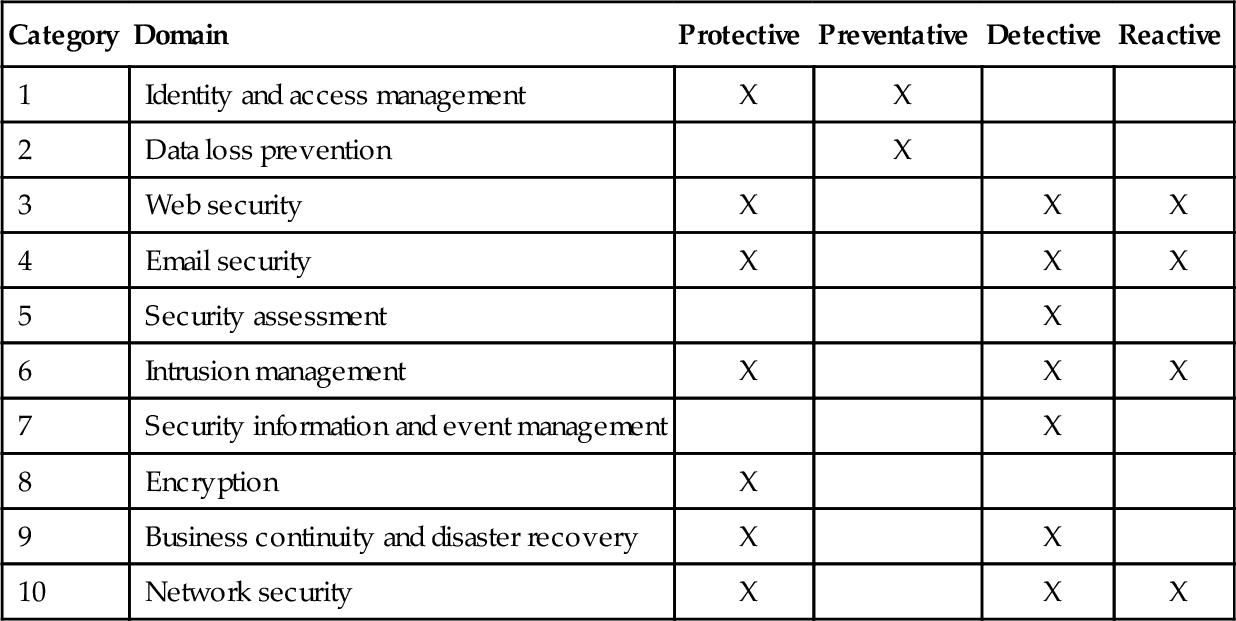
For organizations to achieve a robust security posture, all of the aforementioned classes must be addressed. Where security is paramount, it is important for organizations to be able to cover the entire class scope for events that can occur. From security assessments, to intrusion detection/prevention and monitoring of ones files and event logs, it is essential to have a security posture in place that addresses these. It is simply not enough to have measures that address security after the fact where an adversary has succeeded in infiltrating ones organization. As such, in the following subsections, we will be addressing those categories for which protective, detective, and reactive measures can be deployed via the SecaaS model. In the authors opinion, for brevity, we can condense the aforementioned categories into four subsections. These are as follows: system security, data security, Web security and network security (see Table 4).
Table 4
Defined Categories of Service by Class
| Category | Domain | Data | Web | System | Network |
| 1 | Identity and access management | X | |||
| 2 | Data loss prevention | X | |||
| 3 | Web security | X | X | X | |
| 4 | Email security | X | X | ||
| 5 | Security assessment | X | X | X | X |
| 6 | Intrusion management | X | |||
| 7 | Security information and event management | X | X | X | |
| 8 | Encryption | X | |||
| 9 | Business continuity and disaster recovery | X | |||
| 10 | Network security | X | X | X |
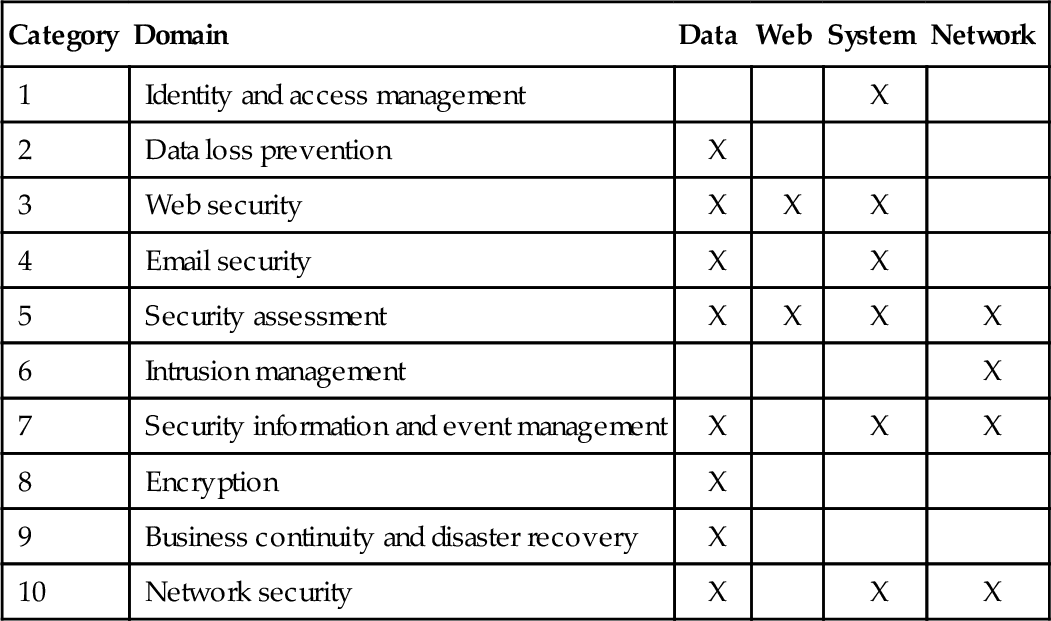
4.1 System security
System security assessments are third-party or internal audits (by an independent department of an organization) of on premise or cloud-based systems (Cloud Security Alliance, 2011c). Typically, the core functionalities for cloud-based security assessments described in the literature are as follows:
• Governance: Process by which policies are set and decision making is executed.
• Risk management: Process for ensuring that important business processes and behaviors remain within the tolerances associated with those policies and decisions.
• Compliance: Process of adherence to policies and decisions. Policies can be derived from internal directives, procedures, and requirements, or external laws, regulations, standard and agreements.
• Technical compliance audits: Automated auditing of configuration settings in devices, operating systems, databases, and applications.
• Application security assessments: Automated auditing of custom applications.
• Vulnerability assessments: Automated probing of network devices, computers and applications for known vulnerabilities and configuration issues.
• Penetration testing: Exploitation of vulnerabilities and configuration issues to gain access to an environment, network, or computer.
• Security/risk rating: Assessment of the overall security/vulnerability status of the systems being tested. This is usually based on the OWASP risk rating methodology (OWASP, 2014b).
Following the above functionalities, cloud providers can address concerns that relate to both traditional security assessment methods and cloud-related concerns. For example, the lack of continuous monitoring is a problem that can be mitigated somewhat entirely by outsourcing services such as intrusion detection/prevention systems (IDS/IPS) and WAFs (Web application firewall) to a provider. This ensures continuous availability and real-time protection from outside threats. Indeed it is possible to implement such solutions without using cloud infrastructure and services, but doing so requires more hardware and software resources, staffing and cost overhead. Web application security assessments can also be carried out using the SecaaS model. Traditional approaches include black-box testing where the Web application is tested from the vantage point of an outside attacker without prior knowledge of its architecture and source code. The Web SecaaS providers toolkit should address the most common areas of deficiencies outlined by OWASP (2014b) which include: cross-site scripting flaws (XSS), structured query language (SQL) injection flaws, file inclusion issues, direct object references, directory traversal, information leakage, and session management.
Where clients have multiple sites or domains to manage, it may be advantageous for them to assess and monitor their Web applications from a single location. In doing so, it is possible to schedule active scanning during off-peak times, while keeping a threat database up to date in a single location. Leveraging the cloud, vulnerability assessment can be carried out across an internal network systematically. In some cases, it may be desirable to install agent software on devices that require endpoint and service protection. Vulnerability assessment, in this context, may take the form of network sweeping for open ports, in combination with identifying outdated services. Where required, the assessment process might also encompass exploitation of mal-configured software, in order to gain access to the machine or an environment. It is important to note that cloud security assessment tools should support common standards and industry best practices. For example, CVE (2014) for vulnerability assessments, OWASP top 10 (OWASP, 2014a) for Web application security assessment, NIST/CIS/FDCC/SANS (NIST, 2014; CIS, 2014; FDCC, 2014; SANS, 2014) guidelines and controls for compliance assessment.
4.2 Network security
Network security, as defined by the CSA consists of security services that allocate access, distribute, monitor, and protect the underlying resource services (Cloud Security Alliance, 2011b). It addresses risks relating to the use of, and access to, enterprise networks. In a cloud environment, network security is likely to be a double prong approach comprising physical and virtual devices. Typically, the core functionalities for cloud-based network security described in the literature are as follows:
• Security gateways: This includes firewalls, WAF, SOA/API, VPN.
• Integrity monitoring: For example, IDS, IPS, Server Tier firewall, file integrity monitoring, DLP, anti-virus and anti-spam.
• Secure services: For example, DNS (domain name system) and/or DNSSEC, DHCP, NTP, RAS, OAuth, SNMP, and management network segmentation and security.
• Traffic monitoring: This includes monitoring network traffic and flows.
• Denial of service protection: For example, identifying anomalous network flows.
The above is a necessary list for network security but by no means a sufficient one. The authors would like to encourage interested readers to take a look at the CSA paper for network security deployment guidelines (Cloud Security Alliance, 2011b). In addition to the core functionalities described in the literature, there are several key network security services that are applicable to the SecaaS model that we will be addressing in this section. These are given in no particular order: network service scanning, network intrusion detection, real-time configuration and alerts.
4.2.1 Service scanning
Network service scanning is designed to probe a server or host for open ports that map to a particular service (Lyon, 2009). Not unlike traditional port scanning, cloud services provide similar functionality as traditional scanners which allow administrators to monitor services running on internal clients, with the additional benefits of the cloud delivery model. Network administrators ought to be equipped with the necessary tools to carry out these tasks. These tasks should include the ability to analyze networks and subnets for newly added machines, and the ability to recognize unauthorized services running on physical and virtual devices.
4.2.2 Intrusion detection
Network intrusion detection (IDS) and prevention (IPS) systems are systems that attempt to discover unauthorized access to an enterprise network by analyzing traffic on the network for signs of malicious activity. They are usually placed at ingress and egress points of the network to detect for anomalous traffic. These systems do this by combining signature and statistical anomaly detection and heuristic behavioral analysis (Cloud Security Alliance, 2011b). To differentiate the two, an IDS provides logging functionality and alerts to attacks, whereas an IPS takes preventative action and responds to attacks. Within a cloud providers network, the client should define specific locations to be monitored by the IDS/IPS, and agree to service and performance levels along with rules and policy management.
4.2.3 Real-time configuration and alerts
Real-time configuration and alerting are features that follow the SIEM category of service. The CSA defines SIEM as a system that accepts (via push or pull mechanisms) log and event information. This information is then correlated and analyzed to provide real-time reporting and alerting on incidents/events that may require intervention (Cloud Security Alliance, 2011d). Needless to say, SIEM deployed via the cloud provides a number of benefits that include powerful user interfaces, proactive alerting, reporting and analysis which make it easier for organizations to achieve compliance.
4.3 Web security
Web security is defined by the CSA as real-time protection offered either on-premise through software/appliance installation or via the cloud by proxying or redirecting web traffic to the cloud provider (Cloud Security Alliance, 2011e). This provides an added layer of protection on top of things like anti-virus to prevent malware from entering the organization via activities such as web browsing. Policy rules can also be enforced by this extra layer of security. For example, an administrator may set a rule such that only particular departments can access parts of the web, whereas other departments may have different web policy rules as required. Web SecaaS, in contrast to traditional security services, utilizes the cloud computing model. Following this model, users of cloud security services can take advantage of its offerings regardless of geographic location (remote and on-premise). Proposed cloud web security solutions should aim to achieve the following goals: reduce cost and complexity; provide real-time protection and provide web filtering; provide granular web application controls. In the following subsections, we will be breaking down the aforementioned goals and examining how they can be realized.
4.3.1 Reduce cost and complexity
The inherent nature of cloud computing follows the pay-per-use business model. What this means in the context of SecaaS is that an enterprise pays only for the services and resources it uses, as it uses them (ISACA, 2013). By moving services and maintenance workloads to a cloud platform, the enterprise has the ability to instantly increase or decrease resources, depending on the immediate needs of a particular workload. With SecaaS, very limited, if any, up-front capital investment is required for hardware and software, ongoing software licenses are eliminated, the need for complex technologies is limited and services can be delivered and accessed regardless of geographic location. As a result, there are fewer servers running security applications and thus yielding a smaller data center footprint. To an enterprise, this translates to direct savings on real estate, power and cooling and indirect savings on facilities maintenance (Microsoft, 2014).
4.3.2 Provide real-time protection
Following the cloud computing model, the CSA’s Web security implementation guidance paper (Cloud Security Alliance, 2011e) recognizes two capabilities which must be apart of a cloud web security solution. These are as follows: A scalable threat assessment infrastructure: Providers should have the ability to collect, classify, and correlate large quantities of security intelligence data from which zero-hour threats can be recognized. A comprehensive centralized management interface: The benefits of such a management interface will result in greater efficiencies, visibility, control, and management over combined web, data, and email security technologies from which unified content analysis and management can be delivered.
4.3.3 Web filtering
Routing traffic through a SecaaS proxy server allows for cleaning of web traffic (web content filtering) while keeping delays to a minimum (Getov, 2012). With the SecaaS model, the service receives and forwards both incoming and outgoing traffic (see Figure 2). Such an approach has several uses—URL filtering, HTTP header information screening and page content analysis. Moreover, the authors would suggest specific pattern matching analysis on content that passes through the web security service. One should be able to configure through the web interface, a simple string or regular expression match for content sensitive data, for example credit card and social security numbers.
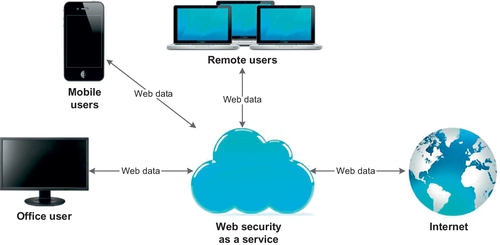
4.3.4 Granular Web application controls
Gone are the days of static HTML Web pages whereby information was delivered to the user exactly as stored. Nowadays, applications rely heavily on dynamic Web pages which are generated by Web applications. Instead of merely reading information from Web pages, users are invited to comment on published articles, create a user account or profile and thus increasing participation. This is what referred to as Web 2.0—coined by DiNucci (1999). This poses a significant challenge to traditional Web application controls wishing to impose high granularity. As a result, Web SecaaS providers are forced to adapt to these new Web technologies and provide a means for dealing with such dynamic content. For example, it may not be advantageous to block these sites entirely, rather it would be desirable for the provider to have policy control over content to be restricted (e.g., gaming, posting, viewing video, etc). This granular control over content passing through the proxy is simple to deploy, but at the same time, a powerful feature that highly configurable.
4.4 Data security
Data security, in the context of a cloud service, the authors define it as the measures put in place to track, analyze and protect information on a system, medium, and in transit. This definition encompasses data that resides on physical and virtual devices, portable devices and data that are sent across a network. Although cloud computing promises lower costs, rapid scaling, easier maintenance and service availability anywhere, anytime, a key challenge is how to build confidence in how cloud can handle user data in a secure manner (Song et al., 2012). A recent Microsoft survey found that a majority of both public and business leaders are excited about the possibilities of cloud computing. Ninety percentage of them, however, are worried about availability, privacy and security of their data as it rests in the cloud (Dwork, 2009). The survey by Microsoft highlights the need for a transparent data-centric approach. To achieve these goals, control of data must be passed back to cloud end users rather than providers. To address the concerns relating to data trust and privacy, users require assurance that their data have not been passed on to a third party or susceptible to prying eyes. Therefore, protection of data that resides on disk or in transit must be adequately secured or encrypted with keys in the users possession.
5 Gaps identified after secaas classification
Following the classification of SecaaS, it became apparent that the following issues remain to be resolved.
5.1 Gaps in secaas web technologies
There are a numerous Web technologies and frameworks that enable developers to build and configure feature rich Web applications. But in the context of SecaaS and Web integration, there are no real guidelines for the development of such an application. One must first consider which Web technologies and frameworks conform with the implementation guidelines outlined by the CSA, before any decision is made to implement a cloud security service.
5.2 Lack of true risk evaluation
Though some vendors claim that their products and services eliminate false positives entirely, to our best knowledge, this is largely unsubstantiated. This highlights the need for assessment techniques to be able to provide to its users a proof of concept for the vulnerabilities and flaws that it claims to detect. Such assessment techniques will demonstrate to users how, when, and where abouts in their services do the vulnerabilities reside. In doing so, true risk potential can be realized and appropriate action taken.
5.3 Lack of a data-centric approach
While two classifications of SecaaS have been proposed in the past, and standards for transmitting data across networks have been addressed, there is a need to address data, its integrity and provenance from a cloud-based perspective. Such an approach will enable users to track what has happened to their data across the physical and virtual infrastructure on which cloud services are built. In doing so, a relationship built on trust and transparency between the user and provider can be realized. Moreover, users ought to be able to track files and directories on their internal network and establish whether tampering has occurred.
5.4 No real classification for mapping legitimate communicating services
Applications such as intrusion detection/prevention systems and firewalls allow network administrators to monitor inbound and outbound traffic on a network (Roesch, 1999), however, there is a need to distinguish applications that communicate over common whitelisted ports such as 80 and 443. This is due to the ever-changing complexity of malware that tend to “phone home” and transfer data over these ports (which are usually whitelisted by the firewall rulesets). Such a classification needs to differentiate between benign applications, for example, browsers and cloud services/agents, and malicious ones. It is worthy to note that this is not a cloud security specific problem, and many on-premise security solutions are still grappling with this.
6 Future work
Recent studies have shown that security is regarded as the top concern for adopting cloud security services (Senk, 2013a; Al-Harthy and Al-Badi, 2014). And there are, of course, several key areas needed to be addressed for SecaaS to reach its full potential. Future work should aim at addressing the critical gaps outlined in this chapter, namely, data-centricity; web technologies for SecaaS; differentiating malicious and benign services; and true risk evaluation.
The fact that trust and perceived usefulness have been identified as the main barriers to the adoption of SecaaS (Senk, 2013b), future work on the topic ought to focus on areas in which usefulness and trust can be increased.
7 Concluding remarks
The proliferation of cloud computing has changed the way we manage our IT infrastructure and services over the Internet. It has paved the way for a new approach to the security of our infrastructure, our data and our applications. SecaaS promises to deliver the scope, scale, and sophistication of tools required to protect information, while substantially decreasing the costs and resources associated with information security. In this chapter, we have described how SecaaS can be used as a tool to protect our data, while being a cost effective, elastic, flexible, and agile asset to enterprise. Furthermore, we have compared and contrasted the SecaaS model with respect to traditional on-premise and MSS, and provided a compelling discussion for moving such services to the cloud. Our observations note that while literature around cloud security services are sparse, future predictions by Gartner and Forrester show that growth for such services is expected to increase substantially. This chapter aimed to address this gap and made sense of this burgeoning field in cloud security.
