Ubuntu One investigation
Detecting evidences on client machines
Mohammad Shariatia; Ali Dehghantanhaa; Ben Martinib; Kim-Kwang Raymond Choob a School of Computing, Science and Engineering, University of Salford, Greater Manchester, UK
b Information Assurance Research Group, School of Information Technology and Mathematical Sciences, University of South Australia, Adelaide, Australia
Abstract
STorage as a Service (STaaS) cloud services have been adopted by both individuals and businesses as a dominant technology worldwide. Similar to other technologies, this widely accepted service can be misused by criminals. Investigating cloud platforms is becoming a standard component of contemporary digital investigation cases. Hence, digital forensic investigators need to have a working knowledge of the potential evidence that might be stored on cloud services. In this chapter, we conducted a number of experiments to locate data remnants of users' activities when utilizing the Ubuntu One cloud service. We undertook experiments based on common activities performed by users on cloud platforms including downloading, uploading, viewing, and deleting files. We then examined the resulting digital artifacts on a range of client devices, namely, Windows 8.1, Apple Mac OS X, and Apple iOS. Our examination extracted a variety of potentially evidential items ranging from Ubuntu One databases and log files on persistent storage to remnants of user activities in device memory and network traffic.
1 Introduction
The term cloud computing refers to a model whereby a user can access computing resources via a network on an on-demand basis (Mell and Grance, 2011). Various types of resources can be shared between users and in a way that remote clients can utilize them, e.g., processing, volatile and persistent storage, and so on. This pool of resources is commonly available as a service via an internal network (private cloud) or publically via the Internet (public cloud). In addition to providing the de facto definition of cloud computing the National Institute of Standards and Technology (NIST) also defined a number of service models including: Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS) (Mell and Grance, 2011). Storage as a Service (STaaS) is an addition to these traditional service models. STaaS technologies enable users to store, download, and share their data in a very accessible manner. There are a number of STaaS service providers including Dropbox, Microsoft OneDrive, Google Drive, and Ubuntu One. These service providers commonly provide personal accounts for minimal or no cost. Cloud Service Providers (CSPs) have made significant efforts to attract customers by supporting various types of devices ranging from traditional PC platforms such as Windows, Mac OS X, and Linux to more recent smart phone operating systems such as iOS and Android. Also, CSPs generally offer access to their services via standards compliant Web browsers including Internet Explorer, Google Chrome, Mozilla Firefox, and Apple Safari. These features allow users to access their data via the majority of Internet connected devices.
However, while STaaS services provide legitimate users with significant utility and convenience, they are equally useful to criminals who utilize them for storing and sharing illicit materials. The global nature of cloud computing infrastructure contributes to the numerous technical and jurisdictional challenges in the identification and acquisition of evidential data by law enforcement and national security agencies.
Digital forensics is the process of identifying, preserving, analyzing, and presenting evidence for use in legal proceedings (McKemmish, 1999). The process of traditional forensic investigation is often impeded by some of the key characteristics of the cloud environment such as multitenancy and global data distribution. Taylor et al. (2011) highlighted that with the advent of cloud computing acquiring and analyzing digital evidence from cloud services using traditional processes is generally infeasible. One key area of difficulty is in identifying the particular service utilized by suspects and then extracting potential remnants of user activities involving that service.
In this chapter, we seek to assist forensic investigators and practitioners to detect possible evidential remnants derived from the Ubuntu One cloud storage service. The artifacts discussed in this chapter should assist in detecting the use of Ubuntu One and the associated evidential remnants stored on client devices. The focus of this study is to detect file system, RAM, and network artifacts present after utilizing Ubuntu One on the Windows 8.1, Mac OS X 10.9, and iOS 7.0.4 platforms.
In this chapter, we intend to address the following research questions:
1. What data can be found on a device’s persistent storage after using the Ubuntu One client software and the location of data remnants within Windows, Mac OS X, and iOS devices?
2. What data can be found in a device’s persistent storage after using Ubuntu One via a Web browser?
3. What data can be extracted from volatile memory on Windows and Mac OS X devices when utilizing Ubuntu One?
4. What data can be extracted from collected network traffic after Ubuntu One has been accessed on Windows, Mac OS X, and iOS devices?
The remainder of this chapter is organized as follows; in the next section, we provide a brief review of related work in the field of cloud forensics. In Sections 3 and 4, we outline both the methodology and experiment setup utilized in our experiments, respectively. In Section 5, we present our research findings, and finally in Section 6, we conclude the chapter.
2 Related work
Grispos et al. (2012) discussed a number of challenges for forensic investigations in the cloud, namely, creating valid forensic images, recovery of distributed evidence, and management of large data sources. There are a number of other research studies that highlight a number of the major issues of cloud forensics (Biggs and Vidalis, 2009; Birk and Wegener, 2011; Martini and Choo, 2012; Damshenas et al., 2012; Daryabar et al., 2013; Aminnezhad et al., 2013).
In the case of STaaS forensic research, the majority of existing research has been conducted on STaaS clients, with a smaller subset of the published materials focusing on server side STaaS investigation. Quick and Choo (2013a,b,c, 2014) have developed a forensic framework to identify, acquire, and present evidential data remnants of Dropbox, Google Drive, and Microsoft SkyDrive on the Windows 7 and iPhone platforms. Hale (2013) published a similar investigation on the Amazon Cloud Drive client on Windows XP and 7. In addition, Chung et al. (2012) analyzed Amazon S3, Google Docs, and Evernote and outlined a technique to collect data from personal computers and mobile devices. Federici (2014) described the concepts and internals of the Cloud Data Imager tool which he developed to provide read-only access to files and metadata of selected remote folders on STaaS services and currently provides access to the Dropbox, Google Drive, and Microsoft SkyDrive services. In terms of server STaaS analysis, Martini and Choo (2013) focused upon the client and server artifacts created with use of ownCloud. The analysis of the ownCloud server component, after analysis of the client component, allows the practitioner to obtain a wider range of evidential data (e.g., previous versions of files).
The numerous publications that investigate STaaS products demonstrate the need for researchers to undertake detailed analysis to guide practitioners in collecting all available evidence from cloud storage products.
3 Methodology
Using Ubuntu One as a case study, artifacts were identified that are likely to remain after the use of cloud storage, in the context of several experiments conducted on Windows, Mac OS X, and Apple iPhone 3G clients. As Ubuntu One supports accessing, uploading, and sharing data using both client software and a browser, we have undertaken experiments across multiple platforms to locate evidential data sources on different client devices.
In each experiment, the investigator first determines whether it is possible to collect volatile data on the platform being investigated. If so, the investigator acquires the contents of physical memory and captures the network traffic. Next, if nonvolatile data can be obtained, the investigator gathers data from the file system such as log files, configuration files, internet history data, databases, and directories. For the Windows and Mac operating systems, we were able to collect volatile and nonvolatile data, but in the case of iOS only network traffic was collected. This was due to the lack of opportunities for forensically sound physical memory acquisition on iOS devices. After collection, the investigator searches for traces of the Ubuntu One cloud storage service in the collected images.
4 Experiment setup
The research experiment was broken into six stages, namely, (1) preparing the Virtual Machines and iPhone, including installing the cloud applications; (2) uploading a dataset to the cloud storage provider; (3) accessing the data through the client application/Web browser on the VMs and iPhone; (4) perform various file manipulations to the dataset on both the VMs and iPhone; (5) process the VMs and iPhone to extract volatile and nonvolatile data; and (6) use numerous forensic tools to analyze the collected forensic images and present the final result.
We undertook experiments within the following four usage environments:
(1) Windows browser-based (see Section 5.1);
(2) Windows app-based (see Section 5.2);
(3) Mac OS X app-based (see Section 5.3); and
(4) iOS app-based (see Section 5.4).
We have used Ubuntu One 4.0.2 which provides users with 5 GB of free space and utilized the following three files from the Enron e-mail dataset, downloaded from the project Web site (http://bailando.sims.berkeley.edu/enron_email.html) on 15 April 2014, to conduct our experiments:
2. HANGING.DOC (22 kB),
3. HANGING.txt (2 kB)
Different file types were utilized in the experiments to determine whether any discrepancies in forensic collection were observable for the different file types.
Windows 8.1 and Mac OS X 10.9 experiments were conducted on virtualized environments utilizing VMware Player 6.0.2. An iPhone 4S with iOS 7.0.6 was used to undertake iOS investigation experiments. Each VM was configured with one CPU, 2 GB of RAM, and 20 GB of hard disk space.
Our experiments were designed to simulate common user activities on cloud platforms, namely, uploading, downloading, opening, and deleting files. For the purposes of this research, one set of credentials were used in all experiments to simplify the location of the credentials as part of forensic image examination.
Web Browser Investigation Experiments Setup: To commence our environment setup for Web browser analysis, we installed the four most popular browsers at the time of research, namely, Microsoft Internet Explorer (version 10.0.9200.16384), Mozilla Firefox (version 25.0.1), Google Chrome (version 31.0.1650.63), and Apple Safari (version 5.1.7), on four VMs. We then performed a series of upload, open, download, and delete operations with one VM for each type of operation. Table 1 outlines the list of tools that were copied to each VM for monitoring changes and detecting possible evidential data.
Table 1
Software Used on VMs for Analysis
| Software | Version | Purpose |
| Regshot | 1.9.0 | Registry monitor |
| Process Monitor | 3.05 | Process, registry, and file activity monitor |
| Nirsoft Web browser passview | 1.43 | Saved password retrieval |
| Digital detective net analysis | 1.5 | Browser cache retrieval |
Figure 1 shows the VM hierarchy for our browser-based experiments.
Windows App-Based Investigation Experiment Setup: In addition to the series of upload, download, open, and delete operations, we also experimented installing and uninstalling the Ubuntu One app to determine the artifacts that could be detected after such activities on client devices, as outlined in Figure 2.
Mac OS X App-Based Investigation Experiment Setup: Similar experiments to Windows platform were conducted on Mac OS X 10.9 Mavericks. However, the process for uninstalling applications on Mac OS X is different in comparison to uninstalling an app in the Windows environment. While most Windows programs include an uninstaller that can be run using the Add/Remove Programs tool available in Control Panel, no such feature exists in Mac OS X and therefore, most users simply move application bundles to the Trash. Assuming that the trash is not emptied, we should be able to locate significant application artifacts after an uninstallation of the Ubuntu One client on OS X client machines.
iOS App-Based Investigation Experiment Setup: For our iOS experiment, we used a jailbroken iPhone 4S running iOS 7.0.6 to conduct our experiments. iFile 2.0.1-1 was installed from Cydia to browse iOS storage directories. The directory holds the associated files and folders of apps from the Apple Store is/private/var/mobile/Applications, with each app being assigned a subdirectory name by universally unique identifier (UUID). Activating the “Applications Names” option under iFile’s Preferences (File Manager section) translates the UUIDs to the human readable names of all the subdirectories. Mobile Terminal was another application installed from Cydia enabling execution of UNIX commands in the iOS environment.
5 Discussion and analysis
In this section, we explore residual artifacts generated by Ubuntu One when cross-platform methods are used to manipulate data hosted on the cloud. Generally, collection of data remnants was conducted in two stages. The first stage is the acquisition of live data. The analysis of this live (volatile) data is regarded as significant in recovering sensitive information that is available while Ubuntu One is being accessed. The second stage is the analysis of nonvolatile data remnants that can be located on the local system. These two methods complement each other to maximize the amount of available evidential data during an investigation. In our research, forensic analysis of live data encompasses analysis of live memory and network traffic, while data remnants analysis involves the persistent files such as log files, databases, and the registry (for Windows platforms).
In all versions of the client applications, after lunching Ubuntu One, the user must enter a device name and their authentication credentials. At next launch, Ubuntu One logs-in automatically unless the user unlinks the device.
For this research, virtual hard disks, virtual memory, and forensic images of real memory and network traffic were examined using multiple forensic tools. We analyzed the VM’s VMEM file as a memory dump file and the VMDK file as an image of the hard disk using AccessData FTK (version 1.86.1). We also used Hex Workshop (version 6.7) for analysis of memory and hard disk images, which enabled searching for keywords such as the Ubuntu One credentials, files being accessed, and words such as “Ubuntu One,” “Ubuntu,” and “UbuntuOne,” The network traffic was captured and analyzed using Wireshark (version 1.10.2) and further analysis was conducted using NetworkMiner (version 1.5). SQLite DB Browser under OSForensics (version 2), PList Explorer (version 1.0), and Notepad++ (version 6.4) were employed to access and retrieve evidential data from the Ubuntu One databases and log files. AccessData Registry Viewer (version 1.7.4.2) and Regripper (version 2.8) were utilized to analyze Windows registry and NTUSER.dat files.
5.1 Windows browser based
Ubuntu One allows users to access and manipulate their data on the cloud without installing the client application, via a Web browser. From an evidence collection perspective, it can be presumed that the browser-based application leaves fewer remnants on local computer compared to the full client application. The following stages outline the results of our analysis, in a step-by-step manner, for each of the evidence sources identified such as live memory and browser cache.
5.1.1 Memory
We found live memory forensic analysis very useful for extracting important digital artifacts when Ubuntu One was being accessed via the Web interface. We utilized two methods to detect Ubuntu One user identity information in the live memory:
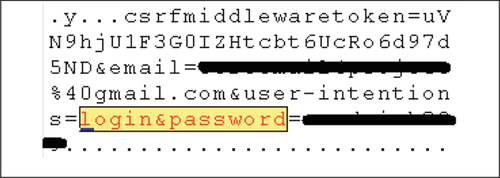
Method 1—Searching for the string “login&password=” to retrieve the user’s credentials in plain text (see Figure 3).
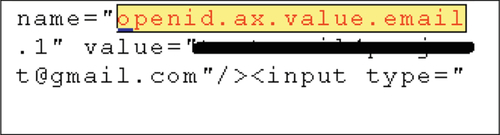
Method 2—Searching for the string “openid.ax.value.email” to retrieve the users e-mail address (see Figure 4).
We also noted that it was possible to extract the names of files that had been accessed or manipulated depending on the specific operation used. A selection of operations and the associated artifacts are outlined in Figures 5–7.
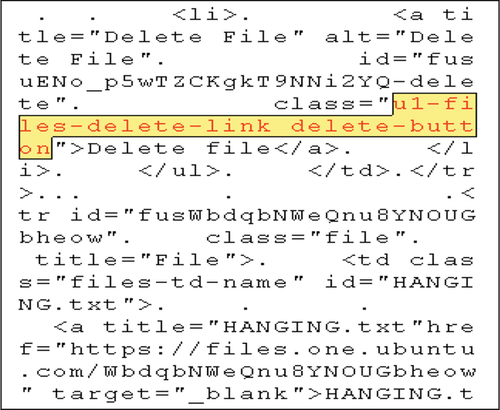
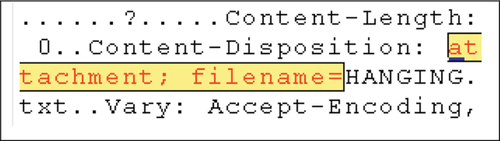
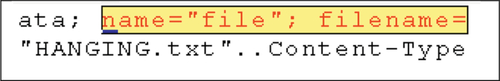
5.1.2 Browser cache and history
When a user has accessed Ubuntu One via the online interface the Web browsers cache and history may contain evidential data and should be extracted. Although it will not generally be possible to extract the Ubuntu One user credentials from the browser cache and history, numerous other evidential artifacts can often be retrieved. While we were not able to extract credentials from the cache directly, in the case of the Chrome and Internet Explorer browsers, the Nirsoft Web Browser Pass View was able to extract the stored password which we saved using the browser.
For an investigator, the first step in a cloud investigation is often to determine which cloud storage services have been used by the suspect, and URL addresses are one source of evidential data useful in determining this. In our experiments, we noted a number of Web addresses in the cache and history that relate to Ubuntu One. These addresses are listed below:
From our analysis of the cache data, we determined that there were three Web pages that we considered to be of particular importance, namely, “dashboard.htm,” “files.htm,” and “+opened.htm.”
The dashboard.htm file contains the first name and last name that has been entered by the Ubuntu One user. In our case, “Test” and “Project” were the first name and last name, respectively (see Figure 8).
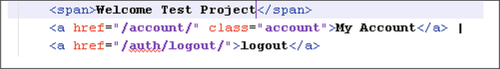
The opened.htm file stores the username as well as the full name of the Ubuntu One user (see Figure 9).

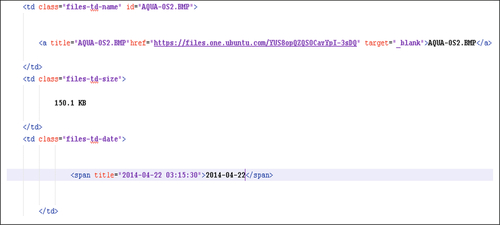
Finally, files.htm cache files often contain filenames, file size, and the date and time that an operation on the file was carried out (see Figure 10).
5.1.3 Registry
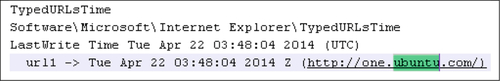
There was no information regarding Ubuntu One credentials and usage located in the registry except for a “TypedURL” entry from Internet Explorer (see Figure 11). As the name suggests, these registry entries are stored when a user types a URL in Internet Explorer (Mee et al., 2006).
5.1.4 Network traffic
Wireshark was used for collecting the network traffic from Ubuntu One usage, which was then analyzed using NetworkMiner. We found that all of the collected traffic was encrypted due to the use of SSL/TLS when communicating with the Ubuntu One servers. For this reason, we were unable to extract any data of significant evidential value. However, a number of common IP addresses were used for Ubuntu One communications, which resolve to Ubuntu.com subdomains. Table 2 shows the IP addresses and associated hostnames that were extracted from the network traffic capture file after a login to Ubuntu One and contents of the user’s account had been accessed/manipulated.
5.2 Windows App-Based
Upon installation the Ubuntu One client software creates a folder named Ubuntu One stored in the “Users<user>Ubuntu One” directory, by default. The folder only appears to be utilized while the Ubuntu One client is running, during which content can be found in the directory as discussed below. By default, this folder is used by Ubuntu One for automatic synchronization of files. In addition to this directory, the installation of Ubuntu One creates some folders on the local computer to store persistent data including log files, databases, and other related files. Utilizing Process Monitor, we detected the following folders that were used by Ubuntu One:
1) C:ProgramDataMicrosoftWindowsStart MenuProgramsUbuntu One
2) C:Program Files (x86)ubuntuone
3) C:Users[user]AppDataLocalubuntuone
4) C:Users[user]AppDataLocalxdgcache
5) C:Users[user]AppDataLocalxdgubuntuone
6) C:ProgramDataubuntuone
7) C:Users[user]Ubuntu One
We also noted three processes related to the use of the Ubuntu One client, namely, ubuntu-sso-login.exe, ubuntuone-control-panel-qt.exe, ubuntuonesyncdaemon.exe.
5.2.1 Memory
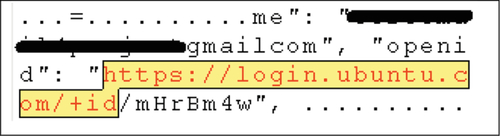
Unlike our browser-based experiments discussed above, analysis of live memory for the Windows client did not result in the location of the user’s password in plaintext. However the username was located by searching for the string “https://login.ubuntu.com/+id” (see Figure 12).
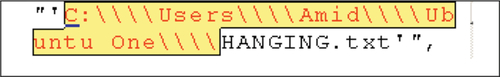
We were also able to locate filenames for files being accessed from the Ubuntu One default folder; however, this required the use of double escaped backslashes. For example, when the default path is C:UsersusernameUbuntu One, the term to search for in the image of live memory is “C:\\Users\\username\\Ubuntu One\\” (see Figure 13).
5.2.2 File system
The Ubuntu One folder in Program Files contains many files including .pem and .conf files. The .pem files are certificate files in the PEM encoding format and .conf files contain configuration values for the Ubuntu One client. There is only one log file in the folder, namely, install.log, which holds information regarding Ubuntu One’s installation process.
The Ubuntu One folder in ProgramData also stores configuration files as well log files in .xdg format. We determined that information of importance can be recovered from the “xdg” log files, including the username used for logging into Ubuntu One and the name and path of the files listed below:
C:Users[user]AppDataLocalxdgcachessosso-client.log
C:Users[user]AppDataLocalxdgcachessosso-client-gui.log
Surprisingly, no database files were located in Ubuntu One’s folders.
5.2.3 Event logs
Windows event logs store useful and valuable information about a system and its users (Do et al., 2014). Depending on the enabled logging level and the installed version of Windows, event logs may provide investigators with valuable data about application operations, login timestamps for users, and other system events of interest.
In our research, we located several logs associated with Ubuntu One within the application and services log. Searching for the keyword “Ubuntu” in the Windows event log leads to several hits as shown in Figure 14.
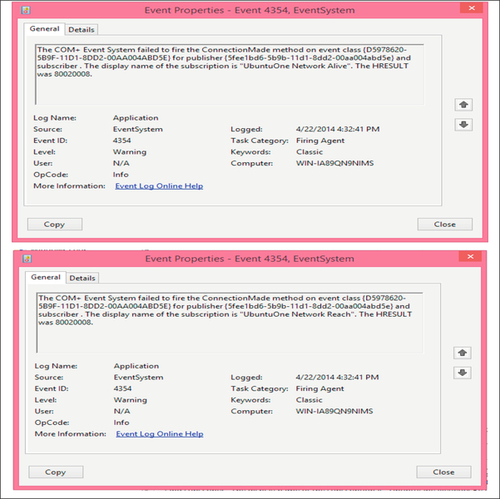
5.2.4 Registry
We noted the creation of the following keys in the registry after installation of the Ubuntu One client:
HKEY_LOCAL_MACHINESOFTWAREWow6432NodeUbuntu One
HKEY_CURRENT_USERSoftwareUbuntu One
Also, searching for the keyword “Ubuntu One” located the following results in the registry:
HK_Current_User/Software/Microsoft/Windows/Run:
C:Program Files (x86)ubuntu onedistubuntuone-syncdaemon.exe
HK_Current_User/Software/Microsoft/Windows/Current version/UFH/SHC:
HKEY_LOCAL_MACHINESOFTWAREWow6432NodeMicrosoftWindowsCurrentVersionUninstallUbuntu One 4.2
Opening files synced via the Ubuntu One, client leads to addition of entries in the RecentDocs registry subkey as expected (see Figure 15).
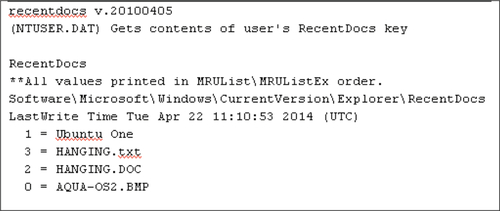
We did not locate any data regarding the files that had been uploaded or downloaded or Ubuntu One credentials in the registry.
5.2.5 Network traffic
Our results for network traffic capture when using the Ubuntu One client was similar to our findings for browser-based access as all network data is encrypted using SSL. As such, plaintext data of value could not be found. However, the captured network traffic shows some differences compared to the network capture acquired using the Ubuntu One online interface. Quick and Choo (2013a,b, 2014) observed Online Certificate Status Protocol traffic relating to the presented SSL certificate in their captured network traffic. We did not note an OSCP query in our network capture. In addition, there were no connections recorded associated with the “media.ubuntu.com” subdomain. The list of IP addresses and associated hostnames extracted from the network traffic collected is listed in Table 3.
5.2.6 Uninstallation
The uninstallation process for Ubuntu One removes all of the files located in the Ubuntu One folder in “Program Files” except for the “dist” folder. All other folders associated with Ubuntu One remain on the client machine after uninstallation, including the Ubuntu One default folder and its contents.
Uninstallation also only removes Ubuntu One artifacts from the “HKEY_CURRENT_USERSoftware” key, while the remaining registry artifacts are left intact.
5.3 Mac OS X App-Based
After installation of the Ubuntu One client on Mac OS X 10.9, we located the following directories created by the installation process:
/Users/< user >/Ubuntu One (default Ubuntu One directory)
/Users/< user >/Library/Application Support/Ubuntuone
/Users/< user >/Library/Caches/ubuntuone
/Users/< user >/Library/Caches/sso
Uninstallation of the Ubuntu One client only removes the first directory while the rest remain intact. Some of these directories contained information related to Ubuntu One credentials and sync files such as the following:
~/Library/Caches/sso/sso-client.log
~/Library/Caches/sso/sso-client-gui.log
~/Library/Caches/ubuntuone/syncdaemon.log
The username of the Ubuntu One user can be located within the first two log files as shown in Figure 16.

Files which have been synced can be found in the syncdaemon.log log file as can be seen in Figure 17.
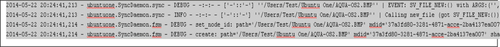
5.3.1 Memory
We were unable to locate plaintext credentials in our memory capture file (.vmem) of the Ubuntu One client on the Mac OS X platform. However, searching for the Ubuntu One default directory string in memory led to a number of filenames when we conducted upload, download, and delete operations (see Figure 18).
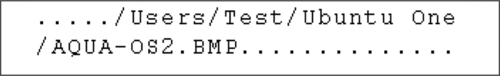
From the other keywords present in the memory capture, we were able to determine the operation that was being undertaken on the file. For example, “ubuntuone.SyncDaemon.EQ—DEBUG—push_event: FS_FILE_CREATE, kwargs: {'path':” and “EVENT: FS_FILE_DELETE:{} with ARGS” represent upload and delete operations, respectively.
5.3.2 Network traffic
The results of our network traffic capture is similar to that of the Windows client application discussed above, where we did not note any OCSP queries. Table 4 outlines the list of IP addresses (and associated hostnames) extracted from the network traffic capture file.
5.4 iOS App-Based
There does not appear to be an official Ubuntu One app available for iOS in the Apple App Store. We selected the “U1Files” (version 0.5) unofficial Ubuntu One client app for analysis on iOS. We installed the app on a jailbroken device running iOS 7.0.4. Application data for apps installed from the App Store is stored in/var/mobile/Applications on iOS. The iFile app (version 2.0.1-1) was also installed from Cydia to locate the directories created by U1Files. The directory name for U1Files in our case was EDF4B87E-CBC0-466C-2377A089DB10. The U1Files directory had five sub directories named Documents, Library, StoreKit, tmp, and U1Files.app. Ubuntu One’s default directory was located at the following path:
/var/mobile/Applications/EDF4B87E-CBC0-466C-2377A089DB10/Documents/Ubuntu One
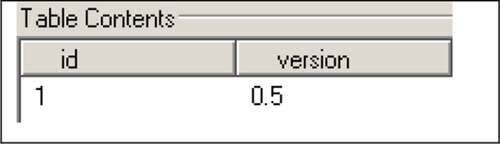
We determined that all synced files were stored in that directory. The “Documents” directory contained the “u1.db” database, which we found contains the three tables provided in Figures 19–21:


1—login_info_table (see Figure 19): These appear to be the authentication token components stored by the mobile app for authenticating to Ubuntu One services. The topic of authentication token use in mobile apps is discussed further in Martini et al. (2015a,b).
2—nodes_table (see Figure 20): Filenames, last modified date, size, and hash values are the notable values we located in this table.
3—version_table (see Figure 21): The currently installed version of the U1Files app can be retrieved from this table. We also located a file named "iTunesMetadata.plist" which contained information including the date that we purchased the U1Files app and the Apple ID that was associated with the purchase.
The results of our network traffic capture analysis on iOS did not differ significantly from our findings for Mac OS X.
6 Conclusion
Cloud storage has attracted many individuals and business users by offering cost-effective storage and services across a variety of devices. However, the prevalence of cloud storage has provided criminals with opportunities, including the ability to organize their activities in a distributed, scalable, and somewhat anonymous way. The nature of the cloud environment imposes several challenges to the traditional process of digital forensic investigation. Data of interest may be segregated on shared storage in different physical locations, where such data is subject to foreign laws and regulations (Hooper et al., 2013).
One area of difficulty in cloud forensics is in identifying the use of cloud services by suspects and, then determining the particular cloud service used and acquiring the account credentials for the service (Quick et al., 2014). The evidence sources in a digital investigation vary and may include computer hard disks and live memory, network traffic captures, and mobile devices such as the Apple iPhone and Android mobile devices. The identification and collection of suspect’s data must be carried out in timely fashion before the data can be moved to another unknown location or even permanently deleted. The legislative process for seizing data also differs between jurisdictions. Hence, forensic investigators and practitioners need to preserve suspects’ data as soon as possible after identification.
In this chapter, we carried out a number of experiments on Ubuntu One to examine the artifacts that may be left behind on client devices after use of this cloud service. First, Windows 8.1 was utilized to access Ubuntu One via its online interface using four major browsers (Internet Explorer, Mozilla Firefox, Apple Safari, and Google Chrome). We then deployed Ubuntu One’s client application to Windows 8.1, Apple Mac OS X 10.9, and an unofficial Ubuntu One client on iOS 7.0.4. During our experiments on these platforms, we simulated a user carrying out common operations on cloud storage, such as uploading, downloading, and deleting files, with a standard dataset. The evidence sources under investigation varied between on operating systems, but included sources such as the Windows registry, event logs, network traffic captures, live memory captures, and persistent file system changes. We found that it was likely that practitioners would be able to locate a range of distinct remnants in relation to Ubuntu One usage, but access to valuable evidential artifacts (such as authentication and user action logs) varied between platforms. The artifacts described in this chapter may assist forensic practitioners in detecting Ubuntu One use and hopefully assist in acquiring data of potential evidential value.
Cloud storage is likely to remain popular and even grow in usage as the dominant technology used in file hosting and transmission of files among individuals and organizations. As a result, it is recommended that those undertaking future work in this area continue to examine cloud storage including investigation of other cloud storage applications using various devices and operating systems. Future work also includes further analysis of the authentication token system used by the Ubuntu One client, which may allow for the location of authentication credentials on the PC operating systems, in addition to the token credentials located on the mobile client.
