Secure migration to the cloud—In and out
Thomas Kemmericha; Vivek Agrawala; Carsten Momsenb a Norwegian Information Security Laboratory (NISLab), Gjøvik university College, Norway
b Leibniz University Hanover, Hanover, Germany
Abstract
This chapter describes the aspects to be considered for a small enterprise to transfer in-house computing to a Cloud Service Provider (CSP). The migration strategy and the accompanying measures are described citing an example of a small lawyer-office. This includes the security aspects and policy, privacy concerns, interoperability and strategic and legal aspects. Moving in-house computing to a CSP leads to a strong dependability of the customer to the CSP (Vendor lock-in). The issue of lock-in is described, and a 5-Phase-Migration-Model into the cloud is introduced to avoid lock-in and keep the flexibility for the customer.
Abbreviations
ADSL Asymmetric Digital Subscriber Line (commonly used Internet access technology)
BDSG Bundes Datenschutz Gesetz
BGB German Civil Law (Bürgerliches Gesetzbuch)
BSI Bundesamt für Sicherheit in der Informationstechnik https://www.bsi.bund.de/EN/Home/home_node.html
CSP Cloud Service Provider
ISMS Information Security Management System
ISO International Organization for Standardization
ISP Internet Service Provider
MSC Migration Security Concept
SANS SANS Institute, SysAdmin, Audit, Networking, and Security, www.SANS.org
SME Small and medium enterprise
UrhG Urheberrechtsgesetz (Germany)
VPN Virtual private network
1 Introduction
The decision of outsourcing the internal IT-Processes and IT-Services is mostly based on economic considerations today. Very often, the strategic and innovative role of “IT” for the cloud customer will be overseen. Taking this into account and considering the high dependency of more or less all companies according to their IT-Services, the migration of the local IT-Services to a Cloud Service Provider (CSP) has to be planned and realized very carefully. A rollback or change of the CSP is essential not to be locked-in to the chosen CSP or the need of large investments in money and manpower to change the current situation. It is important to detect and avoid the lock-in issue in any typical cloud-based service scenario. The Cloud Customer instead of the CSP should be interested to set up an IT-Service environment that could be very flexible developed and moved. This includes the avoidance of lock-in effects, which are often hidden details, and services of CSPs.
Proposed in this chapter is the description of factors that has to be concretely considered before and during the decision to move the IT-Services to a CSP along with the measures that have to be setup to be flexible in changing the conditions of delivering the IT-Services. This chapter also offers a discussion on the legal requirements of outsourcing IT-Processes since there are many obstacles and problems occurring using a CSP that are not visible at a glance. The legal consideration is mainly based on German and European legal systems in order to give a comprehensive overview. In practice, the local conditions and local legal systems and requirements have to be taken into consideration. This chapter also gives a brief overview on the requirement and challenges of cloud migration. Furthermore, this chapter concentrates on the cloud migration of small and medium enterprises (SMEs). For big companies and corporates, some other rules and boundary conditions are valid. Therefore, a separate consideration is necessary and the according measures will be in some fields different from these for SMEs.
2 Who are cloud consumer and CSP?
A cloud consumer or cloud customer is the entity that maintains a business relationship with, and uses services from, CSPs (Armour et al., 2012). A cloud consumer selects a set of service according to its need and sets up service contracts with the CSP. The cloud consumer is charged for the services being provided. Consumers use SLAs to mention its requirements to the CSP. A cloud consumer can use application/service for business process operations (SaaS); develop, tests, deploys, and manages application hosted in a cloud environment (PaaS); create/installs, manages, and monitors services for IT infrastructure operations (IaaS) (Hogan et al., 2011).
A CSP is the entity responsible for making a service available to cloud consumers (Armour et al., 2012). It is the responsibility of the CSP to acquire and manage the computing infrastructure required for providing the cloud services to the cloud consumers. The role of a CSP is to install, manage, maintain, and support the software application on a cloud infrastructure (SaaS); to provide development, deployment, and administration tools (PaaS); manage physical processing, storage, networking, and the hosting environment (IaaS) (Hogan et al., 2011).
3 IT-Service of a small lawyer office migrates into the cloud
In this chapter, the motivation and realization of a small law office to move almost all its IT-Services and IT-Application to a CSP is described as an example. The following sections will refer to this scenario at various points to make the discussion simpler. The term “consumer,” “cloud consumer,” and “law office” will be used interchangeably.
During the separation process from a big law office to a small, four people, law office the question raised up, how to organize the IT-Services in a way, which is efficient and economically arguable. A business process analysis and a clear risk assessment were the kernels of this process.
The first and most important obstacle was the complete lack of IT-Knowledge of the lawyer combined with a common view of private usage of IT. Here appears an important aspect of serving information processing in SMEs. A private developed, auto-didactic experienced knowledge of IT comes into a professional environment where confidentiality, integrity, and availability play an important role, especially for lawyers and service-oriented business dealing with private data.
The primary IT-Applications the law office is using are (see Figure 1):
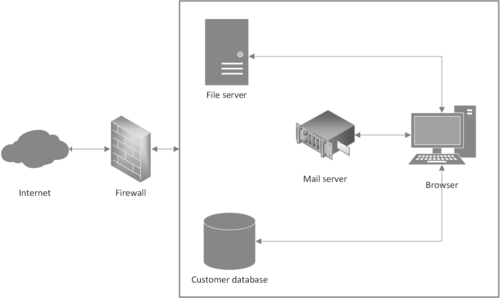
• Customer database → Processing
• Communication services (e-mail, …)
• Telephone services
• Office applications (word processing, etc.)
• Internet access
• Access to databases of relevant laws and cases
• Access to court applications
• Storage of files (containing mostly confidential and/private data)
Before starting the migration, an evaluation of the required information processing was fulfilled. The evaluation starts with the business process of the lawyer. This results in the appraisal, which business process needs what kind of IT-Support. The next step was the mapping of the business processes to the IT-Applications. Based on this information, the planning was possible to determine the required IT-Systems and the essential services for installation and management of the IT-Systems and IT-Applications. It was important at this stage to clearly define the required amount of services for IT-Systems and IT-Applications. Three scenarios were considered:
• Complete transferring of all IT-Services and IT-Applications to the CSP (this means a total terminal-based application—no relevant IT-Services locally)
• Essential IT-Applications will be served locally and the rest will be transferred to the CSP (relevant IT-Power at the end-devices must be provided locally)
• Local delivering of IT-Services using an external IT-Service Provider (relevant IT-Power at the end-devices must be provided locally)
Independently from the technological aspects, a simplified risk analysis based on International Organization for Standardization (ISO) 27001 was done using the methodology of BSI Base Protection (BSI-Standard100-3, 2008) for all scenarios.
In this case, here the lawyer had contact to a CSP, who offered this kind of services. An offer for the first two scenarios was available.
A separate scenario for leaving the cloud service was also developed. There were two possibilities under consideration:
- delivering the IT-Service with own staff and local IT-Systems,
- moving to another CSP.
An emergency case was considered in case that the actual provider would not cooperate.
During the comparison of the three solutions and the CSP change scenario, a long discussion was opened on requirements of legal contracts and the different impacts according to the risk management. This discussion leads to the development of a legal contract including service-level agreements, conditions for service provisioning, costs, penalties, and responsibilities.
Before migration, a detailed test using the cloud environment in real work cases was conducted, and an evaluation took place after the test together with the lawyer. Several processes were adapted and a local service for one application was planned and established.
The new cloud environment was set up before the lawyer and his employees moved to a new office. In other cases, if the business goes on during the cloud migration process, a dedicated migration scenario has to be developed, tested, and fulfilled. This includes also a roll-back scenario at each point of the migration phase.
A Security Policy was developed and verified with the lawyer. The business process analysis was relatively simple but the discussion about the risk analysis was complex. Since data are mostly sensitive (case data, confidential information from the clients, etc.), a strong protection is essential. During the discussion of potential loss of reputation and, therefore, a public loss of trust, cryptographic measures to protect the integrity, and confidentiality were implemented.
A yearly audit of the cloud environment and service provisioning (local, at the law office) by an independent expert/auditor shall take place to check the functionality and security and propose measures to improve the services, security, or identify possibilities for savings.
4 Requirements for cloud migration
Cloud computing is becoming a well-known solution to offer IT-Services and IT-Applications. However, it is necessary to assess all requirements before migrating to the cloud solution. There are essential factors and aspects related to the planning of the cloud migration. In this section, an overview of the most essential requirements is discussed.
4.1 Security policy
The information security policy describes how information security has to be developed in an organization, for which purpose and with which resources and structures. A security policy describes information security objectives and strategies of an organization. The basic purpose of a security policy is to protect people and information, set the rules for expected behaviors by users, define, and authorize the consequences of violation (Canavan, 2006). There are many standards available to keep the information secure and establish security policy. ISO/IEC 27001 (ISO/IEC27001:2005, 2005), ISO/IEC 27002 (ISO/IEC27002:2005, 2005), ISO 13335 (ISO/IEC13335–1:2004, 2004), ISO 17799 (ISO/IEC17799:2005, 2005) are the best-known standards for providing requirements for an Information Security Management System (ISMS). A security policy for the law office is developed according to the BSI standard 100-1 (BSI-Standard100-1, 2008). The information security policy contains statements on the following issues:
• Information security objectives of the institution (e.g., a public agency or private company),
• relationship between the information security objectives and the business objectives or functions of the institution,
• aspired level of information security,
• guiding statements on how the aspired level of information security should be achieved,
• guiding statements whether and by what means the level of information security should be verified,
• the policy is approved by the management and made public in the company.
4.2 Policy development
BSI-Standards 100-1, 100-2 (BSI-Standard100-2, 2008) and SANS institute (Institute, 2008; Canavan, 2006) describe the details of creation of a policy for information security. It is important that as many departments as possible should be involved in the development of a security policy. The security policy must be designed in such a way that all organizational units can be represented with its contents. The general composition of the policy development team varies according to the policy being developed and it is the task of an organization to decide which departments and hierarchical levels will be participated in the policy development. BSI standard 100-1 suggested a life cycle of a policy for information security. This model is known as PDCA cycle as it is based on four phases, i.e., (P)lan, (D)o, (C)heck, (A)ct. The life cycle starts with the Planning and Conception (P) phase to develop a strategy for handling risks in an organization, Implementation (D) phase to implement the plan for the security concept and safeguards, Performance (C) review and monitoring phase to monitor the performance of safeguards and security operations during operation, Optimization and Improvement (A) phase to correct any defects and improve the safeguards.
4.3 Security and Privacy
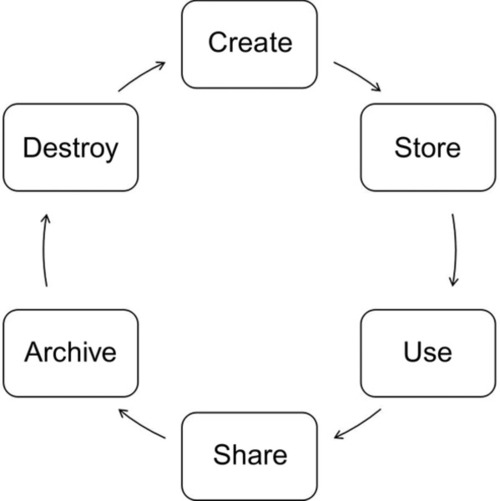
The loss of confidentiality, integrity, or availability of data of law office can have a negative impact on the business of the company. The company has an access to court application and database of sensitive information of its customers. Similarly, any breach in the information privacy is also an important concern. Privacy refers to an individual’s ability to control how his or her information is collected, used, and disclosed. CSPs must protect consumer’s assets from internal and external threats, maintain the privacy of the data, remain available and reliable, and perform consistently. A system must ensure that subjects cannot manipulate the protected data unnoticed or in an unauthorized way. CSPs store data on a virtual hard drive, which must be protected against unauthorized manipulation. A minute must be reliably assigned to the sender, and it can be proved that this information has not been changed since it was created or distributed. The Cloud Security Alliance has developed a useful model of information life cycle management, with phases of Create, Store, Use, Share, Archive, and Destroy, data (see Figure 2). The life cycle is shown in a linear progression but once the data is created, it can bounce between phases, and may not pass through all stages (Simmonds et al., 2011). There are many scenarios where security and privacy requirements play an active role in the context of moving a technology to the cloud.
4.4 Detecting and preventing sensitive data migration to the cloud
Many organizations face the problem with the management of sensitive data. They reported the migration of sensitive data to the cloud services by an individual or business unit without the approval or even notification. Data needs to be pulled out from its existing repository before moving to the cloud. The law office must adopt database activity monitoring to detect any extraction of data or replication from a database.
4.5 Protecting data moving to the cloud
It is important to protect data in transit. Data can be moved from a traditional infrastructure to a CSP; data can be moved between CSPs and between instances or components within a given cloud. Data that a customer wants to upload into a cloud must be protected in transit; similarly, data that a customer wants to download from a cloud must be protected in transit.
4.6 Protecting data in the cloud
Data should be accessed only by entities that have been authorized by the concerned customer for specific access rights. CSP must enforce a mechanism to protect against access attempts by unauthorized entities or access in unauthorized modes while preserving the availability for authorized customers.
4.7 IT-Knowledge
The decision to move IT-Processes to a CSP implies by the stakeholders often to save costs for expensive, often less productive IT-Staff. However, it will be mostly forgotten that qualified IT-Knowledge is also necessary for planning and maintenance of a running business processes supported by the (outsourced) IT-Services. The law office needs to stress on the point that migration of computing and communication services into the cloud give the IT-Staff the opportunity to do strategic work in the direction of tactical and strategic business support. In most companies, IT is a strategic factor and mostly, maintenance effort and user support prevents IT-Staff from strategic development for improving the real business of the company (IT as an enabling factor).
4.8 Control and visibility
This requirement relates to the fact that cloud consumers have very limited visibility into the provider’s policy, incident alert, audit information, and security measures. CSPs are reluctant to share this information to avoid any attack on their policies and avoiding disclosing internals. It is important for the law office to monitor their workloads, keep track of any security related incident, compliance, or privacy breach, and general the status of the systems. A workload is an encapsulation of one or more of the following: application processes, data, configuration information, and state. CSP can provide distinct and effective services but consumer must not be locked-in to the provider. Cloud consumers must be able to monitor the cloud operations so that they can replicate these operations elsewhere.
Consumers have very limited control over the security policies enforced by the CSPs. A proper set of control over the information is necessary while moving IT components to the cloud. It raises an important question on the maintenance of the control by the cloud consumers over their workloads even though they may not know the protection mechanisms and the locations of workload. It is essential for the cloud customer to define in their security policy the requirements for controlling the correct application of the policy rules by the CSP.
4.9 Costs
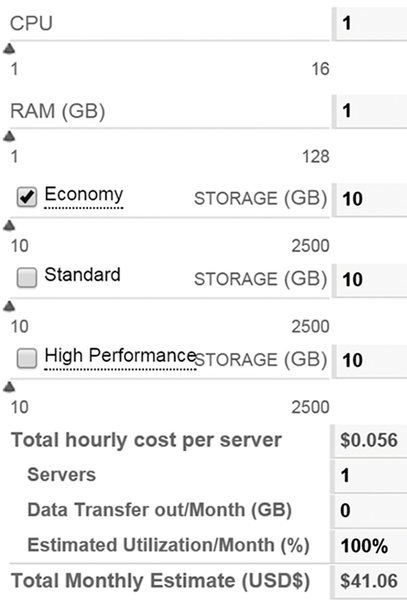
Customers must assess payment and pricing models regarding the decision to migrate to cloud environment and a particular CSP. The decision to migrate to cloud must be considered only when it would be cost effective. The payment opportunities include the possible payment method (e.g., credit card or bank transfer), the time of payment (prepaid or postpaid) and which level of granularity is priced (e.g., storage capacity of 1 MB, 100 MB, or 1 GB steps, CPU utilization, or network transfer volume/throughput) (Repschläger et al., 2012). Service charging defines how the service is charged (volume based, time-based, account based) and the available booking concept, e.g., pay per use, a subscription fee, market-based prices (spot pricing). Figure 3 shows the cost using the cloud cost estimator of DimensionData (DimensionData, n.d.). Customers need to pay only what they use. DimensionData allows consumers to customize CPU (up to 16) and RAM (up to 128 GB) for each server on the fly.
4.10 Interoperability and portability
This requirement ensures the ability to move data or services from one CSP to another, or rollback to traditional computing. It also defines the ease of ability to which application components are moved and reused regardless of provider, platform, OS, infrastructure, location, storage, the format of data, e.g., how proprietary virtual images (AMI) of Amazon are transferable to a Microsoft Azure platform (Repschläger et al., 2012). A lack of interoperability and portability can lead to being locked-in to a particular CSP. There must be adequate flexibility in the contract and renewal of contract between the law office and the CSP. The cloud computing community has not yet defined a universal set of standards, resulting in a significant risk of vendor lock-in. When a customer migrates workload from one CSP to another, it requires extracting the data from the existing cloud environment and uploading data into another cloud environment. The requirement of interoperability is necessary to ensure that any program that performing CRUD operations (create, retrieve, update, delete) on the migrated data in the original CSP continues to work with the new CSP.
4.11 Performance
Performance includes more extensive concepts such as reliability, energy efficiency, and scalability. The time required retrieving the data in cloud when it faces any error or failure will be effective on the cloud performance. CSP and cloud customer must agree on a proper network bandwidth to initiate the cloud service. The performance can be degraded if the bandwidth is too low to provide service to the customer. Organizations usually discover issues with the communication bandwidth shortly after adopting cloud services (InformationWeek, 2008). Customer must assess the communication bandwidth requirements and evaluate the performance of the applications/services before migrating to cloud (Kim et al., 2009). Customers must also discuss the possible location of data centers and their distances from their location, as it is an important factor to affect the performance. Users who are at a long distance from CSPs may experience high latency and delays (Ravanmehr and Khanghahi, 2013; Borko Furht, 2010).
5 Rollback scenarios
5.1 Vendor lock-in
The concern of vendor lock-in is often described as the “Hotel-California” syndrome. You can check-in but you can never leave.
a. What is vendor lock-in?
In the given scenario in this chapter, the law office adopts cloud computing in order to outsource its workload to a CSP. The CSP provides services in terms of processing and/or storing the data, providing platform or infrastructure to develop application, maintain database, etc. CSP configures and optimizes the given application according to own standards, protocols, and policy. This creates a risk of vendor lock-in and makes customer dependent on the current vendor. Lock-in occurs when a cloud consumer cannot move, or it costs a significant amount of money or time to do it. Cloud consumer may want to move to another CSP or to move to its own infrastructure.
Robert Jenkins, CTO of Cloud Sigma, says in an article published on GigaOm,1 “It’s not just privacy and security. It’s also—if I change my mind or it doesn’t work out, how do I move on?” There may be many reasons for the cloud consumer to change the CSP or rollback to the On-premise technology. For instance:
- an unacceptable increase in cost at contract renewal time,
- the ability to get the same service at a cheaper price,
- the CSP shuts down one or more services being used without acceptable migration plans,
- a dispute between cloud customer and CSP,
- a CSP ceases business operations.
The absence of cloud computing standards has also led to vendor lock-in, where each cloud vendor offers a proprietary cloud. When a cloud consumer writes its application using a specific API of the CSP, it will be extremely difficult for him to move to another CSP, offering a different platform.
b. How to avoid lock-in?
“When you put a lot of your resources, a lot of your data in the cloud, you want to know that you can move all that away to another CSP, or even bring that back on premises, if that’s the exit strategy,” says Thomas Erl, CEO of Arcitura Education Inc. (McKendrick, 2011).
The law office must ensure during the planning phase of cloud migration that the architecture of the IT-Business can run on multiple cloud platforms and the data can be migrated from one CSP to another. Cloud Foundry2 platform, which is Apache 2.0-licensed, is the industry’s Open PaaS and provides a choice of clouds, frameworks, and application services. Some PaaS has limited offerings in terms of language and framework support that restrict the cloud consumer to deploy its technology to a single cloud.
There have been a major research and development efforts invested into methods, tools, and standards to avoid the problem of vendor lock-in. Open-source platform is designed to avoid the problem of lock-in. For instance, TM Forum Cloud Services Initiative is an approach to increase cloud computing adoption such as common terminology, transparent movement among CSPs, security issues, and benchmarking.
c. Steps to avoid lock-in
It is indeed a challenging task to figure out whether a vendor is trustworthy or trying to lock you in. However, there are certain steps that the law office can follow as a consumer to avoid lock-in.
i. Read the Service level agreement (SLA) of the CSP carefully. Check the definition of services, performance measurement, data handling, disaster recovery, termination of agreement. Accept the SLA only if it meets your need. The management team or the team responsible for the analysis of the SLA must consult IT-Team and the legal department.
ii. Ask the CSP before the planning phase about their policies of data moving. How the CSP supports toward moving the services to another CSP?
iii. Select the architecture of the selected technology such that it can be executed on multiple cloud platforms and can be easily moved from one cloud to another.
iv. Ask your CSP to give you detailed information about their architecture so that you can investigate the technical boundary conditions. If you are going to move large section of business functionality to a CSP then demand specific architecture diagrams and get it reviewed by the system architect.
v. Ask the CSP if it is possible for you to maintain same image of the data On-premise or to export data in raw format.
vi. Check with the provider if they use any standards to ensure transparent movement among CSPs.
vii. Check with the provider if they need your application to be rewritten in their proprietary language or they are comfortable with the favorable languages for cloud application, e.g., C++, Java, Python.
6 Legal aspects
When it comes to the transfer of the IT-Systems and IT-Applications of a company into a cloud, there are many specifics according to civil law that need to be considered. These contain primarily legal issues in copyright, IT contract law, industrial property law, competition and antitrust law, data protection law, domain procurement law, the applicability of the respective local law, and last but not least the liability. The questions that been highlighted at this point should be in respect of the contractual relationship and the liability between the CSP and the cloud customer. The following aspects should be understood as a general legal paradigm. References to German law are given only to point out particular aspects of interest under European law.
The question arising at first is the one concerning the contract type between the CSP and the cloud customer. This will mostly be a mixed contract type, which will be containing aspects of lease resp. loan agreements, as well as elements of contracts for services or employment (Splittgerber/Rockstroh, 2011). As far as the transformation of a system or an upgrade of that system, which the provider owes, goes, the legal assessment is measured, for example, in Germany according to the law concerning work and services. Other countries prioritize aspects of the sales or leasing agreement. The data transport, however, is generally done on the basis of the service contract law. When it comes to the availability of the data in a particular place at a particular time, the liability also falls under the rules of the service contract law. The assignment of storage capacity in a datacenter against remuneration, however, is usually subject to the law of tenancy. Even if no item as such is left, the leave of the software must be classed with that (Hanseatisches Oberlandesgericht Hamburg, Urt. v. 15. 12. 2011, 4 U 85/11). Regarding the rent it has to be noted that the rental object has to be kept, by the landlord, in a suitable condition for use. In the case of cloud services, whose content constitutes the continuous/permanent availability and retrievability would be tantamount to a guarantee. A provider must, therefore, bear in mind that his description of services in the “Terms and Conditions” also provides realistic system availability.
On this basis, it has to be assessed which rights and obligations emerge for the respective contract partner. Essentially it deals with ensuring data security. On the one hand, this may mean that the CSP has to protect the data of the cloud user from outsiders and must not misuse it himself. On the other hand, this may bring up the question for the cloud user, on which condition he is allowed to transfer data to a cloud. This is particularly relevant in sectors where confidential information (law firms, doctors, pharmacies) is affected.
This raises the question of who owns all the data within a cloud. First, the “ownership” of data from a legal point of view cannot be justified, insofar as data are - under the relevant law—not treated as items. However, data can be protected from accessing or the exploitation by third parties under different legal conditions. Primarily copyright, data protection law and criminal law protect the right on data. In principle, the right over data vests with the one who has the power of disposition regarding the data (e.g., §§ 87a/b Urheberrechtsgesetz (Germany)). There is no mandatory link between the originator of the data or the person on whose IT-System the data is stored and who has the power of disposition of the data. If the person authorized for the data has lawfully stored the data on the external IT-System (cloud), he becomes the beneficiary of the data. This also applies in relation to the operator of the (relevant) cloud. Therefore, it will be essential for a breach of the Copyright Act, whether the access to foreign databases has intruded database rights by illegitimate methods.
In addition, the producer of a database usually has the exclusive right to reproduce the database as a whole or at least a crucial part of the database, to distribute and to reproduce it publicly. However the CSP, as such, is the owner of the data, so that he does not intervene in the data inventory illegally, but on the basis of a contract. As soon as private files (not personal data) are sent to a third person or company for storing in a cloud, only the official agreement between the CSP and the cloud customer applies. Therefore, this agreement asks to regulate the legal relations between the two parties in detail and by taking into account the foreseeable conflict scenarios.
In this regard, at least in Germany, the data protection law does not help, because it usually requires the existence of private, data concerning a person (in Germany: § 1 Bundesdatenschutzgesetz (BDSG). In the act of outsourcing the data from a law office into the cloud (i.e., data of legal entities) this protection does not apply (Splittgerber/Rockstroh, 2011).
The question of data protection probably becomes relevant when it comes to the transfer of client data into the cloud. The loss or nonscheduled publication could trigger a liability of the firm in relation to the clients and other parties. It is important that the firm outsources the data and IT-Infrastructure to the cloud and undertakes an ordered-data processing (Nägele/Jacobs, 2010; Weichert, 2010). Therefore, the cloud user of such a cloud must be convinced before the start of the data processing by a CSP, which he complies with the technical and organizational measures. This means that the user must carry out a check (pre-control). This control can already be carried out within the scope of the supplier selection and must be completed no later than the beginning of the data processing. Even when in practice, the client must not perform this control Himself. The client should still be able to demonstrate by submission of appropriate certifications (e.g., ISO 27001/IT-Risk Management) from the CSP’s compliance with data protection legislation. The same applies to the expressly by law required control in the course of the duration (current control) any duration or current control, as required by the local law. Furthermore, the German law prescribes explicitly that henceforth the pre- and the current control must be documented in writing. In Germany, therefore, all the rights and obligations of the data protection law do not apply toward the CSP, but the law firm. You must draft the cloud contract in writing and therefore necessarily regulate the following in it: subject and duration of the order, the nature, the scope and the purpose of the collection, processing, use of data, the possibility of cancelation and rectification of data, and the personal controlling rights of the client. The cloud customer is, therefore, liable for privacy violations.
But even this “pre-control” and the agreement of cancelation-conditions and corrections do not fully ensure the protection of data. For reasons of operational safety, the operator shall regularly backup copies of the files. Deleting a file will, therefore, not bring the necessary security. The obligations of the CSP are to be defined once again. The question arising for cloud users is whether the CSP is liable if he has fallen victim to a hacker attack and the data of the cloud user is affected. For claiming (civil) damages, it is crucial, in regard of hacked cloud data, to find out, whether the seller can be held responsible for the breach of the duty of care (culpability). This is the case, if the provider does not comply with recognized safety standards, and it has been the reason the hacking attack was possible in the first place (Splittgerber/Rockstroh, 2011).
Another relevant requirement for the contract is confidentiality. The cloud often contains company and business secrets or other confidential information. Therefore, in case of a breach of confidentiality there are often contractual penalties (Splittgerber/Rockstroh, 2011).
However, the essential question for the legal assessment is, which data protection law is applicable after all. For example, if data is collected anywhere in the EU (outside of Germany) but processed or used in Germany by a CSP, the “provisions of the German Data Protection Law do not apply (in Germany: § 1 “Bundesdatenschutzgesetz” (BDSG)). The idea behind this is that we assume that all Member States of the European Union would have a high level of data protection. In addition, it aims to help European companies to function easily and operate in other Member States without having to know all data protection regulations. The situation is different if the company has a subsidiary in Germany (Dammann, 2011). Then, the BSD is applicable, provided that the collection, processing, and storage are done domestically.
The territoriality principle applies for non-European companies. This is also relevant in terms of copyrights regarding the possible usage of the provided software by the CSP. In this way, it may come to licensing problems, when the cloud user uses the client software and therefore—due to the intermediate storage—duplicates (Splittgerber/Rockstroh, 2011). As a general rule: local law applies. According to Article 4 (paragraph 1 lit. c), the European Data Protection Directive (Directive 95/46/EC, 1995) finds it sufficient that the company “relies on means” that are located in the Member State. This leads to the conclusion that already uploading files through the cloud user in Germany to a non-European Server leads to the applicability of German law.
Finally, it should be said, however, that in terms of cloud contracts a clear agreement on the applicable law is recommended. This is also generally permitted under Article 3 Rome I (Regulation (EC) No. 593/2008 European Parliament and Council, 17.6.2008 (Rome I), 7.7.2008, L 177, 6). Since computerized litigation between foreign contractors often takes months and years, it should also be considered whether regulations in relation to the voluntary jurisdiction (arbitration) are useful.
7 Challenges in cloud migration
Although cloud computing seems like a trivial solution for many IT problems, there are many barriers in migrating to the cloud. A business unit will not surely move to the cloud solution if it imposes serious cost or slows down the business operation. This section discusses several aspects related to cloud migration. Each and every aspect is important for a business unit before moving to the cloud.
7.1 Latency
Latency is becoming a major challenge for the cloud customer. It represents loss of availability and slows down network performance. Users access a cloud service through a network that introduces latency into every communication. Cloud latency is a bit different from the concept of latency known before the ubiquitous Internet. The latency is the time that packets use to travel from source to destination. In the case of cloud computing, the endpoints are not static. The geographical location of the user can be anywhere. Similarly, the cloud applications can be located anywhere. It is important to know the location of the ultimate end users and the networks that connect them to the destination networks (van der Zwet and Storm, n.d.).
According to White Paper published by Internap.com (Internap, 2013), every 0.1 s in latency reduces sales by 1% of Amazon.com. According to Equation Research sanctioned by Gomez, 78% of the site visitors have gone to a competitor’s site due to poor performance during peak hours. CSPs like Amazon, Google, and Microsoft offer no better than 99.95% availability as Service Level Agreements. This signifies that the cloud service will remain down for an average time of 21.6 min per month. This can prevent enterprises from adopting IT-Services through a CSP.
7.2 Security
Security is a major concern in the adoption of cloud computing services. Most customers are unwilling to place their sensitive corporate data in the cloud as the CSPs, or other competitive customers of the same CSP could compromise the data. Customers feel the lack of transparency as they are not aware of how, why, and where their sensitive data is processed. A customer can access cloud computing services anywhere with Internet. On the connection between the CSP and cloud customer, the data may be compromised if they are not secured. A survey conducted on 800 IT-Professionals across four countries by Intel in 2012 states that 57% of the respondents accepted that they are unwilling to move their workload and data into the cloud due to security and compliance issues (Intel, 2012).
Organizations do often not have control or knowledge of the location of the data storage in the cloud. Cloud customers have very limited control over the security policies enforced by the CSPs on their behalf. In traditional IT-Environments, IT-Infrastructure is present behind the firewall of an organization. Virtualized and nonvirtualized servers serve only a fixed line of business. IT-Professionals can select advanced security tools that give them a high degree of control over the security and compliance issues related to the organization. In the case of cloud infrastructure, servers are virtualized and shared across several lines of business or even across multiple organizations. It is important to connect multiple cloud data centers to gain efficiencies. For instance, IT-Professional may want to link a public cloud data center based in UK with their private cloud-based one in Germany. If there is not an advanced tool available to secure the connection among the distant infrastructure, local IT-Staff loses a degree of control and visibility into workload and data.
7.3 Interoperability
Interoperability is still a big challenge in cloud migration. The cloud computing community does not have a universal set of standards now. Cloud interoperability might force the user to be dependent on a single CSP and causes vendor lock-in. Once an organization has selected a CSP, it is often extremely difficult to move to another CSP. It mostly incurs huge cost to change providers. It ceases the negotiation power toward the increment of service cost and service discontinuation.
The common practice to enable interoperability is the use of open standards. There are many cloud standardization projects. These projects focus on standardizing cloud computing solution such as workloads, authentication, and data access. The cloud standards coordination Wiki maintains a list of some projects (Standards, n.d.). Table 1 lists some of the projects related to standards for cloud computing interoperability (Hogan et al., 2011). The table titled “Cloud Standardization Effort” from the report “The Role of Standards in Cloud-Computing Interoperability” (http://www.sei.cmu.edu/reports/12tn012.pdf) (c) 2012 Carnegie Mellon University is used with special permission from its Software Engineering Institute.
Table 1
A List of Projects/Standards to Ensure Interoperability in Cloud Computing
| CloudAudit, also known as Automated Audit, Assertion, Assessment, and Assurance API (A6) | Open, extensible, and secure interface, namespace, and methodology for cloud computing providers and their authorized consumers to automate the audit, assertion, assessment, and assurance of their environments. As of October 2010, CloudAudit is part of the Cloud Security Alliance |
| IEEE P2301, Draft Guide for Cloud Portability and Interoperability Profiles (CPIP), IEEE | Standards-based options for application interfaces, portability interfaces, management interfaces, interoperability interfaces, file formats, and operation conventions |
| IEEE P2302, Draft Standard for Intercloud Interoperability and Federation (SIIF), IEEE | This standard creates an economy among CSPs that is transparent to users and applications, which provides for a dynamic infrastructure that can support evolving business models |
| TM Forum Cloud Services Initiative | Approaches to increase cloud computing adoption such as common terminology, transparent movement among CSPs, security issues, and benchmarking |
7.4 Internet speed
Cloud computing needs mostly a public network connection to access cloud data and applications with any computing device. To access cloud data, an Internet connection is used in the most cases. In a traditional noncloud environment, the server and client devices are connected by an internal high-speed network infrastructure. In cloud computing environment, all the access to data is done using an Internet connection. Internet speeds are on average 20 times slower than local network speeds. The download speed is in often (ADSL) not identical to upload speeds, i.e., pushing information from the cloud user device to the cloud server is slower than pulling information from the cloud to the device. Internet Service Provider (ISP) does not guarantee the Internet speed and performance. Internet bandwidth is typically shared by all users in the local office (TrinusTech, n.d.). The solution to mitigate this problem is to use an enterprise-class Internet connection (symmetric) that has better fault tolerance and repair service than a consumer-class connection. The main disadvantage of this solution is the high price of enterprise-class connection.
7.5 Cloud integration
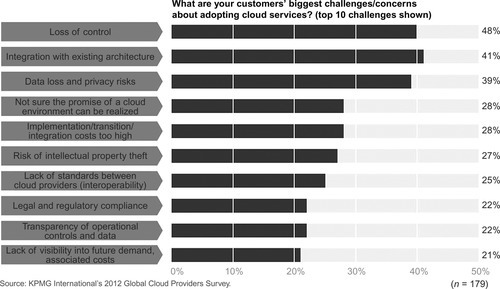
The integration of “traditional” On-premise systems with a cloud infrastructure is still a huge problem. KPMG International’s 2012 global CSPs survey (KPMG, 2012) found that the integration with existing architecture is the second biggest challenges/concerns (41%) about adopting cloud services (see Figure 4). The issue of integration takes into account the ability to connect with both source and target systems. In order to execute a smooth integration, data must be extracted from the source system, resolve all the technical and semantics differences and publish the data to the target system. In order to achieve the complete benefit of cloud computing, it is important to plan and execute integration for data, application, network, and identity:
Data—Data integration addresses the requirement to synchronize data that resides in two or more systems so that both systems always contain timely and meaningful data (SalesForce, 2014). InformaticaCloud (Cloud, n.d.) provides a solution for cloud data integration for SaaS and IaaS by integrating data between cloud-based and On-premise systems.
Application—Application integration addresses the requirement to connect business applications at a functional level. Application integration involves generation of an event in one application and triggering some activities in another application. The widely adopted application integration scenario is described by Kolluru and Mantha (2013):
• On-premise application to cloud application integration
• Cloud application to On-premise application integration
• Cloud to cloud application integration.
Network—Network integration ensures smooth and reliable communication between the On-premise and cloud server. Small size businesses often set up a Virtual private network (VPN) that connects the individual machine to the cloud network. VPN connection allows a user to access any application or database on the cloud server by using encrypted point-to-point communication.
Identity—Identity management is the aspect of cloud integration that is usually left unaddressed while planning cloud migration. IT- and management-teams pay great attention toward the integration of functionality and data. A business system comprises of many credentials to access different services. If a user can access a set of services On-premise using his credentials then, he must be able to access the same service in the cloud without any interruption. A cloud integration solution must be able to establish proper authentication and authorizing mechanism to access any resource in the cloud and On-premise.
8 Migration phases
For the migration to a CSP under consideration that a remigration to another IT-Service provisioning must be possible, a Five-Phase-Model of secure cloud migration is introduced.
The migration process to a CSP is divided into five phases that correspond to each other. It is important that an organization, intending to move its IT-Services, and IT-Processes to a CSP is aware of all phases and develops and tests a strategy to get in each step of the phases during the whole process of migration and operation. It is also essential for an organization to think about cloud migration to develop a scenario to leave the CSP without any losses of IT-Services and data and with a predictable amount of investment and manpower. Applying the Five-Phase-Model of secure cloud migration will ensure this.
The five phases of cloud migration are:
2. Contracts
3. Migration
4. Operation
5. Termination
These five phases will not follow straightward each other. It depends on the success whether the next phase can be entered or not. Under every circumstance, it is necessary to develop the light gray (left in Figure 5) and gray strategy (right in Figure 5) to leave the CSP. The way back to an internal IT-Service is the safest backup, because the customer can define all SLAs and remigration conditions. But all assumed advantages of using a CSP would be lost. The gray strategy offers, on the one hand, the possibility to negotiate regularly new condition with the actual CSP. On the other hand, it is a clear strategy available to move to another CSP if the required service, the service quality, the maintenance, or the economical conditions are not sufficient anymore. In the following section, the single phases are described according to Figure 5. This subchapter gives an overview, which subtasks during each step of the Five-Phase-Model have to be fulfilled. A detailed description of all subtasks during the migration process is not scope of this chapter because the design of the subtasks depends strongly on the required IT-Services, the kind of data which shall be processed and which legal requirements have to be applied.
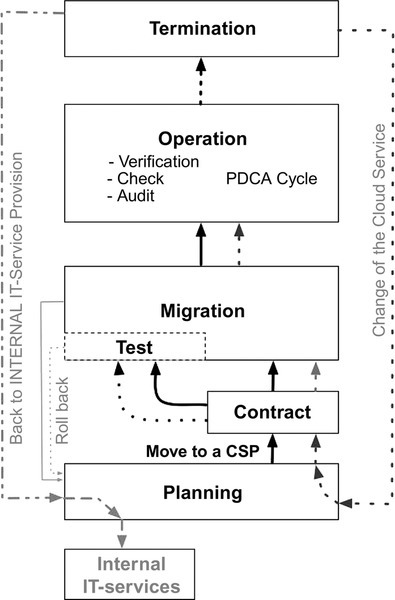
8.1 Planning
The planning phase is the most important phase because the prerequisites for all following phases and the accompanying procedures will be defined during the planning phase. Mistakes or uncertainties during this phase can affect the whole migration and operation. Especially an eventually necessary termination process could be massively disturbed or is not possible without enormous costs and may be with loss of reputation for the cloud customer.
The business analysis and the constitutive security analysis are the fundaments for all further decisions and concepts. So it is recommended to develop these two concepts very carefully and complete. From the practical experience, a comprehensive business analysis will often also give starting-points for an improvement of detailed or entire processes. So at the example of the lawyer office, we were able to detect optimization potentials in some of the internal workflows as well as in communication procedures with courts.
The subtasks of the planning phase shall include as a minimum the following points:
- Security analysis
- Definition of required SLAs
- Definition of security requirements
- Definition of required cloud services
- Definition of required cloud deployment model
- Definition of the CSP (call for tender or scan the Internet)
- Requirements for interoperability
• Virtualization software (vendor, type, version, upgrade cycle, …)
• Flexibility in upgrading or keeping the version level in accordance also to other cloud customers
- Definition of the basic rollback scenario
8.2 Contracts
Based on the strategy and the cloud policy, the contracts with the CSP as well as with the ISPs have to be negotiated. Depending on the legal situation in the country of the cloud customer, the contracts have to be negotiated and regularly adopted if necessary. Basic guidelines are described in Section 5. Because network connectivity is the basis of the successful access to the cloud services, it is essential that the ISP (mostly the CSP will be accessed via Internet) will offer the required service quality and availability. All contractual defined service levels with the CSP cannot be provisioned if the network is not available in the required condition. This often causes complex disputes.
Furthermore, it is important to describe the termination processes in the contract that includes the secure and complete erasure of all customer data and process information (including backups). The CSP has to ensure that no data can be retrieved in any way from any media after termination of the cloud service. Nondisclosure agreements also for the time after service provisioning are essential and have to be part of the contract with the CSP.
Essential subtasks for the contract design are:
- Definition of the form of the contracts (especially in international services)
- Ensure that all related law areas are involved and covered
- Description of the location, where the service are allowed to be provided (processing and storage of data)
- Definition of indicators of service provisioning and other relevant requirements (measurability and auditing)
- Definition of required certifications, quality of the certifications, and cycles to renew the certifications
- Definition of the framework for auditing processes
- Definition of Service Level Agreements and how to ensure the provisioning of the defined services (this includes the conditions and terms of termination)
- Definition of technical forms and software versions
- Definition of termination of the cloud service.
8.3 Migration
The migration phase is the most complex phase. On the basis of the former conducted business and security analysis the implementation and Migration Security Concept (MSC) has to be developed. The migration starts with a realistic test scenario, which is executed by employees of the cloud customer with real applications, but mostly as a simulation and not in real service. During this subphase, the decision to keep staying in the former situation or to migrate has to be made and necessary changes in the concept of service provisioning by the CSP can be done. During each stage of the migration phase, a rollback to the beginning must be possible.
Relevant aspects for the migration phase are:
- Implementation of the IT-Processes and IT-Services according to the business processes analysis
- Definition of the IT-Service concept
- Definition of the security concept for the migration phase (MSC) and the operation phase
- Definition of the migration concept, this includes:
• Test-concept, description, requirements, documentation, evaluation of the test
• Concept for change over (parallel service provision, consistency of services and data, rollback scenario)
• Secure transfer of the data and processes to the CSP
- Definition of a checklist for the migration process, as a basis for a necessary start of the rollback scenario
- Definition of responsibilities during the whole migration process from definition of concepts—testing—transfer—takeover, etc.
8.4 Operation
The operations phase is a more or less steady-state situation where the cloud customer mostly has to take care that the quality of the IT-Service provision is sufficient. Measures described in ISO 9000 (Quality Management) and ISO 27000 (Information Security Management) families have to be applied to guaranty the required service quality. Independent audits have to be done to guarantee the defined service quality.
Relevant aspects for the operation phase are:
- Definition of the IT-Service operation
• What services are available?
• How to access the services?
• Authentication and authorization requirements and how are they realized
• Service provisioning (e.g., based on ITIL)
- Security concept (based on ISO 27001)—follows from the planning phase
- Qualification concept for administrators and users
- Definition of the concrete auditing concept
- Emergency Handbook and test-procedure for the emergency case
- Auditing concept (see also Chapter 8)
8.5 Termination
The termination phase is necessary under the consideration that the rollback to internal IT-Service provisioning or the change of the CSP usually is not under consideration by a cloud customer in long-term planning. Often economic reasons or insufficient service provisioning leads to a decision to change the IT-Service provisioning that might lead to leaving the actual CSP. An intensive preparation makes a change of the CSP safer and more secure.
Relevant aspects for the termination phase are:
• Definition, who shall provide the IT-Services
• Ensure how to get access to all data and business processes during the whole termination process (documented guideline)
• New contract with another CSP or an internal IT-Service Provider
• Time schedule of the termination and remigration process
• SLAs for the remigration
- Definition how to secure the processes and the data
• Secure permanent access to the data during the termination process
• Secure data in transit
• Ensure secure and sustainable erasure of customer data
- Termination of the contract with the existing CSP
- Penalty rules if the CSP does not fulfill the SLAs (part of the contract)
- Definition of an emergency scenario for the case that the CSP does not cooperate
- Nondisclosure agreement for a time after service provisioning of the former CSP
9 Auditing
A regular audit process must be introduced to ensure the service quality, the level of IT-Security, and the compliance using cloud services. In Cloud Computing there is a minimum of two organizations involved, the cloud customer and the CSP. Often one or more ISPs are the third or fourth party in the ensemble taking an essential part according to the quality of the service provisioning from the view of the cloud customer. The cloud customer considers the IT-Services provided by the CSP as a support for the own, entire business process. The underlying additional services of the ISPs also have to be taken into consideration concerning the service quality.
For a successful audit, the service provisioning and policies of the cloud customer, the ISPs and the CSP have to be audited. While the internal processes of the cloud customer can be audited by himself relatively easy, the ISPs and the CSP usually do not allow the cloud customer to audit there internal systems and policies. Both service providers offer their services for several customers on the same platform. So it is not possible to audit only the services, systems, applications, and policies according to one customer without getting information about other customers of the service providers (CSP, ISP). Additionally, the ISPs as well as the CSPs usually are not willing to give third parties a view into their internal system service policies.
A complete audit of the entire service provisioning system requires to know and to prove the quality management systems and the ISMS of the cloud customer and all involved service providers. Since the ISPs and CSPs do not let the cloud customer audit their internal systems, the only possibility to guarantee a limited level of quality is (a certification according to ISO 9000 and ISO 27000) that has to be delivered by the service provider.
If the cloud customer has to fulfill additional documentation and certification requirements, it should be negotiated and fixed by a contract that additional, external audits by an independent auditor have to take place. The independent auditor has to certify that certain conditions will be realized, e.g., storage of customer data outside of the national border is prevented. In the ISMS, the fulfillment of those requirements has to be documented. Voluntary certification by independent organization like governmental privacy protection centers or similar will improve the trust of the cloud customer. Since there is no legal force to publish all procedures and protection and documentation measures an entire secure cloud service cannot be guaranteed. Some customers cooperate in a common cluster and setup or charge their own CSP who acts as a community cloud. But this is especially for SMSs like the considered lawyer office not possible.
It is additionally to prove whether the cloud customer has to document certificates like ISO 9000, ISO 27000, or others to their customers. Under this circumstance, the decisions to move IT-Services to the cloud have to be planed very careful.
10 Summary
Moving internal IT-Systems and IT-Applications to a CSP implies several requirements and should be planned very carefully. Especially, lock-in effects can become very cost intensive and lead to business problems if the lock-in effects are not detected in advance, before the migration process of IT-Services to the CSP has been started. The requirements for the migration to the cloud are security and privacy issues as well as the fact that parts of the control of the IT-Provisioning will not longer be in the hand of the cloud customer. An important aspect is that a sufficient IT-Know-How must be kept at the cloud customer, which has to be taken into account considering the economical advantages of the cloud migration (IT-Staff can not be completely substituted).
Because of the lock-in effects after migration, sufficient measures to avoid this locking-in have to be undertaken. An important part of the migration to the cloud is the legal part. The legal aspect is different according to the country and the kind of business of the cloud customer. The relevant considerations of legal requirements and contract development are described for the German legal system. For other legislation, this has to be adopted.
The challenges for using a CSP are security, network access, interoperability, and preserving IT-Know-How. An overview of the most important challenges is given and is described how to take care to deal with these challenges. In the end, a detailed Five-Phase-Model for the sustainable migration to the cloud based on planning—contracts—migration—operation—termination is described. Depending on the requirements and the economical and legal situation of a cloud customer, this model gives references what kind of aspects have to be considered while moving internal IT-Services to a CSP.
