Chapter 2
Analyzing Potential Indicators to Determine the Type of Attack
This chapter covers the following topics related to Objective 1.2 (Given a scenario, analyze potential indicators to determine the type of attack) of the CompTIA Security+ SY0-601 certification exam:
Malicious Software (Malware)
Ransomware
Trojans
Worms
Potentially unwanted programs (PUPs)
Fileless virus
Command and control
Bots
Cryptomalware
Logic bombs
Spyware
Keyloggers
Remote access Trojan (RAT)
Rootkit
Backdoor
Password attacks
Spraying
Dictionary
Brute force (Offline and Online)
Rainbow tables
Plaintext/unencrypted
Physical attacks
Malicious universal serial bus (USB) cable
Malicious flash drive
Card cloning
Skimming
Adversarial artificial intelligence (AI)
Tainted training data for machine learning (ML)
Security of machine learning algorithms
Supply-chain attacks
Cloud-based vs. on-premises attacks
Cryptographic attacks
Birthday
Collision
Downgrade
To combat the various security threats that can occur on a computer system, you first need to classify them. Then you need to define how these threats can be delivered to the target computer. Afterward you can discuss how to prevent security threats from happening and troubleshoot them if they do occur. In this chapter, let’s start with the most common computer threat and probably the deadliest—malicious software.
“Do I Know This Already?” Quiz
The “Do I Know This Already?” quiz enables you to assess whether you should read this entire chapter thoroughly or jump to the “Chapter Review Activities” section. If you are in doubt about your answers to these questions or your own assessment of your knowledge of the topics, read the entire chapter. Table 2-1 lists the major headings in this chapter and their corresponding “Do I Know This Already?” quiz questions. You can find the answers in Appendix A, “Answers to the ‘Do I Know This Already?’ Quizzes and Review Questions.”
Table 2-1 “Do I Know This Already?” Section-to-Question Mapping
Foundation Topics Section |
Questions |
|---|---|
Malicious Software (Malware) |
1–5 |
Password Attacks |
6–7 |
Physical Attacks |
8 |
Adversarial Artificial Intelligence (AI) |
9 |
Supply-Chain Attacks |
10 |
Cloud-based vs. On-premises Attacks |
11 |
Cryptographic Attacks |
12 |
Caution
The goal of self-assessment is to gauge your mastery of the topics in this chapter. If you do not know the answer to a question or are only partially sure of the answer, you should mark that question as wrong for purposes of the self-assessment. Giving yourself credit for an answer you correctly guess skews your self-assessment results and might provide you with a false sense of security.
1. You logged in to your laptop and noticed a message saying that all your files have been encrypted and to recover them you need to pay $1,000 in Bitcoins. What has your system been infected with?
Ransomware
Worm
Keylogger
None of these answers are correct.
2. What type of malware can look like legitimate software but then performs negative actions to manipulate your system?
Trojan
Ransomware
Worm
None of these answers are correct.
3. Which malware type can allow an attacker to gain administrator privileges?
Keylogger
Rootkit
Ransomware
All of these answers are correct.
4. What type of malware does not reside on the hard drive of a computer?
Ransomware
Botnets
Fileless malware
None of these answers are correct.
5. Bots in a botnet typically receive instructions from which of the following?
A command-and-control (C2) server
A zombie system
A malvertising site
All of these answers are correct.
6. An attacker using John the Ripper, which uses a wordlist, is an example of which of the following?
Social engineering attack
Dictionary password attack
Buffer overflow attack
Cross-site request forgery attack
7. An attacker using a large number of usernames with a few commonly used passwords is considered what kind of attack?
Password spraying
Credential harvesting
Password cracking
None of these answers are correct.
8. What type of attack occurs when an attacker captures credit card information or information from other similar cards (gift cards, loyalty cards, identification cards, and so on)?
Skimming
Shimming
SIM cloning
None of these answers are correct.
9. Which of the following techniques are used to attack machine learning (ML) implementations?
Tainting of data to cause errors in the outcome of the ML solution
Overfitting attacks
ML transfer attacks
All of these answers are correct.
10. You purchased a brand-new Internet of Things (IoT) device and noticed that it started collecting personal information (PI) and attempted to send your data by communicating with random IP addresses. You noticed that an implant could have been installed during the manufacturing of the product. What type of attack might this be?
Supply-chain attack
Cross-site scripting
Return to libc attack
Masquerading attack
11. Which of the following attacks are made against cloud implementations?
API attacks
DNS attacks
VM escape attacks
All of these answers are correct.
12. An attacker attempts to force an application to roll back the version of TLS (from TLS version 1.3 to 1.0). What is the name of this type of attack?
Privilege escalation
Downgrade attack
Cracking
Fuzzing
Foundation Topics
Malicious Software (Malware)

Malicious software, or malware, is software designed to infiltrate a computer system and possibly damage it without the user’s knowledge or consent. Malware is a broad term used by computer professionals to include viruses, worms, Trojan horses, spyware, rootkits, adware, and other types of undesirable software.
Of course, as a security professional, you don’t want malware to infect your systems, but to defend against it, you first need to define it and categorize it. Then you can put preventive measures into place. It’s also important to locate and remove or quarantine malware from a computer system in the case that it does manifest itself.
For the exam, you need to know about several types of malware. Over the past several years, an emphasis shift from viruses to other types of malware, such as spyware and ransomware, has occurred. Most people know about viruses and have some kind of antivirus software running. However, many people are still confused about the various other types of malware, how they occur, and how to protect against them. As a result, computer professionals spend a lot of time fixing malware issues (that are not virus related) and training users on how to protect against them in the future. However, viruses are still a valid foe, so let’s start by discussing them.
A computer virus is code that runs on a computer without the user’s knowledge; it infects the computer when the code is accessed and executed. For viruses to do their dirty work, they first need to be executed by the user in some way. A virus also has reproductive capability and can spread copies of itself throughout the computer—if it is first executed, by the user or otherwise. By infecting files accessed by other computers, the virus can spread to those other systems as well. The problem is that computers can’t call in sick on Monday; they need to be up and running as much as possible, more than the average human.
Ransomware and Cryptomalware

Some less than reputable persons use a particularly devious malware known as ransomware—a type of malware that restricts access to a computer system and demands that a ransom be paid. Ransomware informs the user that in order to decrypt the files or unlock the computer to regain access to the files, a payment would have to be made to one of several banking services (typically crypto currencies like Bitcoin). It often propagates as a Trojan or worm, and usually makes use of encryption to cause the user’s files to be inaccessible. This use of encryption is also known as cryptoviral extortion. Examples of ransomware include WannaCry, NotPetya, Nyetya, SamSam, BadRabbit, and others. One of the most common infection methods of ransomware is via phishing and spear phishing attacks. You learned about phishing and spear phishing in Chapter 1, “Comparing and Contrasting Different Types of Social Engineering Techniques.”

Ransomware is also often referred to as cryptomalware. Today’s cryptomalware leverages advanced encryption techniques to prevent files from being decrypted without a unique key.
Figure 2-1 shows a message displayed to the victim of a ransomware attack. The ransomware illustrated in this figure is the well-known ransomware called WannaCry.

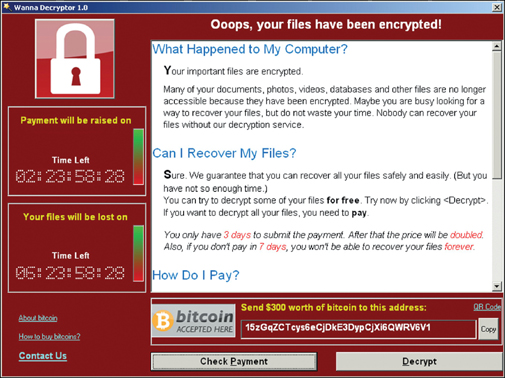
FIGURE 2-1 A Ransomware Attack
Note
Sometimes a user will inadvertently access a fraudulent website (or pop-up site) saying that all the user’s files have been encrypted and payment is required to decrypt them; some imposing government-like logo will accompany the statement. But many of these sites don’t actually encrypt the user’s files. In this case, we are talking about plain old extortion with no real damage done to the computer or files. These types of sites can be blocked by pop-up blockers, phishing filters, and the user’s common sense when clicking searched-for links.
Trojans

Trojan horses, or simply Trojans, appear to perform desirable functions but are actually performing malicious functions behind the scenes. They are not technically viruses and can easily be downloaded without being noticed. They can also be transferred to a computer by way of removable media, especially USB flash drives. One example of a Trojan is a file that is contained within a downloaded program such as a key generator—known as a keygen used with pirated software—or another executable. If users complain about slow system performance and numerous antivirus alerts, and they recently installed a questionable program from the Internet or from a USB flash drive, their computers could be infected by a Trojan.
Remote Access Trojans (RATs) and Rootkits

Remote access Trojans (RATs) are the most common type of Trojan. Examples include Back Orifice, NetBus, and SubSeven. Their capability to allow an attacker higher administration privileges than those of the owner of the system makes them quite dangerous. The software effectively acts as a remote administration tool, which happens to be another name for the RAT acronym. These programs have the capability to scan for unprotected hosts and make all kinds of changes to a host when connected. They are not necessarily designed to be used maliciously but are easy for an average person to download and manipulate computers with. Worse, when a target computer is controlled by an attacker, it could easily become a robot, or simply a bot, carrying out the plans of the attacker on command. We discuss bots later in this chapter.
RATs can also be coded in many programming languages (such as PHP, Ruby, and Python) to allow remote access to websites. An example of this is the web shell, which has many permutations. It allows an attacker to remotely configure a web server without the user’s consent. Quite often, the attacker will have cracked the FTP password in order to upload the RAT.
RATs are often used to persistently target a specific entity such as a government or a specific corporation. One example is the PlugX RAT. Malicious software such as this is known as an advanced persistent threat (APT). Groups that have vast resources at their disposal might make use of these APTs to carry out objectives against large-scale adversaries. APT groups could take the form of large hacker factions, and even some corporations and governments around the globe.

A rootkit is a type of software designed to gain administrator-level control over a computer system without being detected. The term is a combination of the words root (meaning the root user in a UNIX/Linux system or administrator in a Windows system) and kit (meaning software kit). Usually, the purpose of a rootkit is to perform malicious operations on a target computer at a later date without the knowledge of the administrators or users of that computer. A rootkit is a variation on the virus that attempts to dig in to the lower levels of the operating system—components of the OS that start up before any antimalware services come into play. Rootkits can target the UEFI/BIOS, boot loader, kernel, and more. An example of a boot loader rootkit is the Evil Maid Attack, which can extract the encryption keys of a full disk encryption system, as discussed later. Another (more current) example is the Alureon rootkit, which affects the master boot record (MBR) and low-level system drivers (such as atapi.sys). This particular rootkit was distributed by a botnet and affected over 200,000 (known) Microsoft operating systems.
Rootkits are difficult to detect because they are activated before the operating system has fully booted. A rootkit might install hidden files, hidden processes, and hidden user accounts. Because rootkits can be installed in hardware or software, they can intercept data from network connections, keyboards, and so on.
A successfully installed rootkit enables unauthorized users to gain access to a system and act as the root or administrator user. Rootkits are copied to a computer as a binary file. This binary file can be detected by signature-based and heuristic-based antivirus programs; however, after the rootkit is executed, it can be difficult to detect. The reason is that most rootkits are collections of programs working together that can make many modifications to the system. When subversion of the operating system takes place, the OS can’t be trusted, and it is difficult to tell if your antivirus programs run properly or if any of your other efforts have any effect. Although security software manufacturers are attempting to detect running rootkits, it is doubtful that they will be successful. The best way to identify a rootkit is to use removable media (a USB flash drive or a special rescue disc) to boot the computer. This way, the operating system is not running, and therefore, the rootkit is not running, making it much easier to detect by the external media.
Sometimes, rootkits will hide in the MBR. Often, operating system manufacturers recommend scrubbing the MBR (rewriting it, for example, within System Recovery Options or another recovery environment) and then scanning with antivirus software. This solution depends on the type of rootkit. The use of GPT in lieu of MBR helps to discourage rootkits. I suggest using GPT whenever possible.
Unfortunately, because of the difficulty involved in removing a rootkit, the best way to combat rootkits is to reinstall all software (or reimage the system). Generally, an IT technician, upon detecting a rootkit, will do just that because reinstalling usually takes less time than attempting to fix all the rootkit issues; plus, it can verify that the rootkit has been removed completely.
Worms

A worm is much like a virus except that it self-replicates, whereas a virus does not. It does this in an attempt to spread to other computers. Worms take advantage of security holes in operating systems and applications, including backdoors, which we discuss later. They look for other systems on the network or through the Internet that are running the same applications and replicate to those other systems. With worms, the user doesn’t need to access and execute the malware. A virus needs some sort of carrier to get it where it wants to go and needs explicit instructions to be executed, or it must be executed by the user. The worm does not need this carrier or explicit instructions to be executed.
Going back in history, a well-known example of a worm is Nimda (admin backward), which propagated automatically through the Internet in 22 minutes in 2001, causing widespread damage. It spread through network shares, mass emailing, and operating system vulnerabilities.
Sometimes, the worm does not carry a payload, meaning that in and of itself, it does not contain code that can harm a computer. It may or may not include other malware, but even if it doesn’t, it can cause general disruption of network traffic and computer operations because of the very nature of its self-replicating abilities.
In the late 2010s, different types of ransomware (including WannaCry) propagated like a worm by scanning and infecting vulnerable systems leveraging a known Windows SMB vulnerability.
Fileless Virus

Malware doesn’t have to reside on the hard drive of a computer. It can also reside within RAM (and possibly other locations). Fileless malware—also known as non-malware—functions without putting malicious executables within the file system and instead works in a memory-based environment. Sound potent? It can be, but the attacker will usually need to have remote access to the system—via SSH, a RAT, or otherwise—in order to deploy the malware. The term fileless is somewhat of a misnomer because the attack may actually contain files. The systems affected, such as ATMs, often suffer from weak endpoint security, and the organization that owns those systems might also have ineffective access control policies.
Command and Control, Bots, and Botnets

I know what you’re thinking: the names of these attacks and delivery methods are getting a bit ridiculous. But bear with me; they make sense and are deadly serious. Allow me to explain—malware can be distributed throughout the Internet by a group of compromised computers (bots), known as a botnet, and controlled by a master computer (command-and-control [C2] server). The individual compromised computers in the botnet are called bots and also often called zombies because they are unaware of the malware that has been installed on them. These compromises can occur in several ways, including automated distribution of the malware from one zombie computer to another. Now imagine if all the zombie computers had a specific virus or other type of attack loaded, and a logic bomb (defined a bit later) was also installed, ready to set off the malware at a specific time. If this were done to hundreds or thousands of computers, a synchronized attack of great proportions could be enacted on just about any target. Often, this is known as a distributed denial-of-service (DDoS) attack and is usually perpetuated on a particularly popular server, one that serves many requests. If a computer on your network is continually scanning other systems on the network, is communicating with an unknown server, and/or has hundreds of outbound connections to various websites, chances are the computer is part of a botnet. But botnets can be used for more than just taking down a single target. They can also be used to fraudulently obtain wealth and even crypto mining.
Figure 2-2 shows a botnet controlled by a command-and-control server. The attacker (via the C2) sends instructions to the bots in the botnet. A botnet could be composed of any compromised system. These could be user endpoints, as well as Internet of Things (IoT) devices (such as cameras, sensors, and industrial control systems).

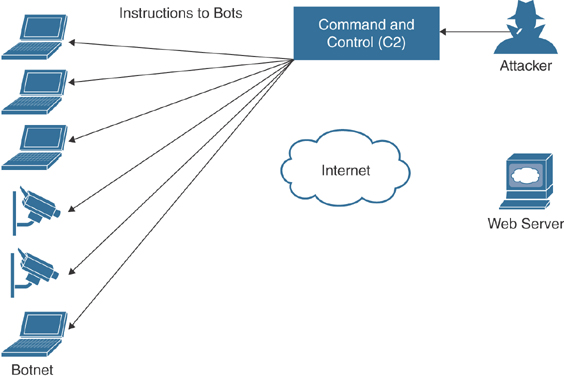
FIGURE 2-2 A Botnet and C2 Example
After the bots receive the instructions from the C2, they perform a given action. In the example illustrated in Figure 2-3, the bots start sending numerous IP packets to a web server (the victim) to perform a DDoS attack. The purpose of this attack is to consume system resources and prevent authorized users from accessing the web server. You will learn additional details about DDoS attacks in Chapter 4, “Analyzing Potential Indicators Associated with Network Attacks.”


FIGURE 2-3 The Botnet Performing a DDoS Attack
Logic Bombs

A logic bomb is code that has, in some way, been inserted into software; it is meant to initiate one of many types of malicious functions when specific criteria are met. Logic bombs blur the line between malware and a malware delivery system. They are indeed unwanted software but are intended to activate viruses, worms, or Trojans at a specific time. Trojans set off on a certain date are also referred to as time bombs. The logic bomb ticks away until the correct time, date, and other parameters have been met. So, some of the worst bombs do not incorporate any explosion whatsoever. The logic bomb could be contained within a virus or loaded separately. Logic bombs are more common in the movies than they are in real life, but they do happen—and with grave consequences. But more often than not, they are detected before they are set off. If you, as a security administrator, suspect that you have found a logic bomb or a portion of the code of a logic bomb, you should notify your superior immediately and check your organization’s policies to see if you should take any other actions. Action could include placing network disaster recovery processes on standby, notifying the software vendor, and closely managing usage of the software, including, perhaps, withdrawing it from service until the threat is mitigated. Logic bombs are the evil cousin of the Easter egg.
Easter eggs historically have been platonic extras added to an OS or application as a sort of joke; often, they were missed by quality control and subsequently released by the manufacturer of the software. Easter eggs are not normally documented (being tossed in last minute by humorous programmers) and are meant to be harmless, but nowadays they are not allowed by responsible software companies and are thoroughly scanned for. Because an Easter egg (and who knows what else) can possibly slip past quality control, and because of the growing concerns about malware in general, many companies have adopted the idea of trustworthy computing, which is a newer concept that sets standards for how software is designed, coded, and checked for quality control. Sadly, as far as software goes, the Easter egg’s day has passed.
Potentially Unwanted Programs (PUPs) and Spyware

Spyware is a type of malicious software either downloaded unwittingly from a website or installed along with some other third-party software. Usually, this malware collects information about the user without the user’s consent. Spyware could be as simple as a piece of code that logs what websites you access, or it could go as far as a program that records your keystrokes (known as a keylogger). Spyware is also associated with advertising (those pop-ups that just won’t go away!) and is sometimes related to malicious advertising, or malvertising—the use of Internet-based advertising (legitimate and illegitimate) to distribute malicious software.
Spyware can possibly change the computer configuration without any user interaction—for example, redirecting a browser to access websites other than those wanted. One example (of many) of spyware is the Internet Optimizer, which redirects Internet Explorer error pages out to other websites’ advertising pages. Spyware can even be taken to the next level and be coded in such a way to hijack a user’s computer. Going beyond this, spyware can be used for cyber espionage, as was the case with Red October, which was installed to users’ computers when they unwittingly were redirected to websites with special PHP pages that exploited a Java flaw, causing the download of the malware.

Adware usually falls into the realm of spyware because it pops up advertisements based on what it has learned from spying on the user. Grayware is another general term that describes applications that are behaving improperly but without serious consequences. It is associated with spyware, adware, and joke programs. Very funny…not. Adware and grayware are types of potentially unwanted programs (PUPs).
Preventing spyware and PUPs works in much the same manner as preventing other types of malware when it comes to updating the operating system and using a firewall. Also, because spyware is as common as viruses, antivirus companies and OS manufacturers add antispyware components to their software. Here are a few more things you can do to protect your computer in the hopes of preventing spyware:
Use (or download) and update built-in antispyware programs such as Windows Defender. Be sure to keep the antispyware software updated.
Adjust web browser security settings. For example, disable (or limit) cookies, create and configure trusted zones, turn on phishing filters, restrict unwanted websites, turn on automatic website checking, disable scripting (such as JavaScript and ActiveX), and have the browser clear all cache on exit. All of these things can help filter out fraudulent online requests for usernames, passwords, and credit card information, which is also known as web-page spoofing. Higher security settings can also help fend off session hijacking, which is the act of taking control of a user session after obtaining or generating an authentication ID.
Uninstall unnecessary applications and turn off superfluous services (for example, Remote Desktop services or FTP if they are not used).
Educate users on how to surf the web safely. User education is actually the number one method of preventing malware! Access only sites believed to be safe, and download only programs from reputable websites. Don’t click OK or Agree to close a window; instead press Alt+F4 on the keyboard to close that window, or use the Task Manager to close out of applications. Be wary of file-sharing websites and the content stored on those sites. Be careful of emails with links to downloadable software that could be malicious.
Consider technologies that discourage spyware. For example, use a browser that is less susceptible to spyware, and consider using virtual machines.
Verify the security of sites you visit by checking the certificate or by simply looking for HTTPS in the URL.
Here are some common symptoms of spyware:
The web browser’s default home page has been modified.
A particular website comes up every time you perform a search.
Excessive pop-up windows appear.
The network adapter’s activity LED blinks frequently when the computer shouldn’t be transmitting data.
The firewall and antivirus programs turn off automatically.
New programs, icons, and favorites appear.
Odd problems occur within windows (slow system, applications behaving strangely, and such).
The Java console appears randomly.
To troubleshoot and repair systems infected with spyware, first disconnect the system from the Internet (or simply from the local-area network). Then try uninstalling the program from the Control Panel or Settings area of the operating system. Some of the less malicious spyware programs can be fully uninstalled without any residual damage. Be sure to reboot the computer afterward and verify that the spyware was actually uninstalled! Next, scan your system with the AV software to remove any viruses that might have infested the system, which might get in the way of a successful spyware removal. In Windows, do this in the recovery environment (for example, Safe Mode) if the AV software offers that option.
Keyloggers

An attacker may use a keylogger to capture every keystroke of a user in a system and steal sensitive data (including credentials). There are two main types of keyloggers: keylogging hardware devices and keylogging software. A hardware (physical) keylogger is usually a small device that can be placed between a user’s keyboard and the main system. Software keyloggers are dedicated programs designed to track and log user keystrokes.
Tip
Keyloggers are legal in some countries and designed to allow employers to oversee the use of their computers. However, recent regulations like the General Data Protection Regulation (GDPR) in the European Union (EU) have made keyloggers a very sensitive and controversial topic. Threat actors use keyloggers for the purpose of stealing passwords and other confidential information.
There are several categories of software-based keyloggers:
Kernel-based keylogger: With this type of keylogger, a program on the machine obtains root access to hide itself in the operating system and intercepts keystrokes that pass through the kernel. This method is difficult both to write and to combat. Such keyloggers reside at the kernel level, which makes them difficult to detect, especially for user-mode applications that don’t have root access. They are frequently implemented as rootkits that subvert the operating system kernel to gain unauthorized access to the hardware. This makes them very powerful. A keylogger using this method can act as a keyboard device driver, for example, and thus gain access to any information typed on the keyboard as it goes to the operating system.
API-based keylogger: With this type of keylogger, compromising APIs reside inside a running application. Different types of malware have taken advantage of Windows APIs, such as GetAsyncKeyState() and GetForeground Window(), to perform keylogging activities.
Hypervisor-based keylogger: This type of keylogger is effective in virtual environments, where the hypervisor could be compromised to capture sensitive information.
Web form–grabbing keylogger: Keyloggers can steal data from web form submissions by recording the web browsing on submit events.
JavaScript-based keylogger: Malicious JavaScript tags can be injected into a web application and then capture key events (for example, the onKeyUp() JavaScript function).
Memory-injection-based keylogger: This type of keylogger tampers with the memory tables associated with the browser and other system functions.
Backdoors

Backdoors are pieces of software, malwar, or configuration changes that allow attackers to control a victim’s system remotely. For example, a backdoor can open a network port on the affected system so that the attacker can connect and control the system.
A backdoor can be installed by an attacker to either allow future access or to collect information to use in further attacks. When the threat actor gains access to a system, the attacker usually wants future access so he or she can control the system and can carry out other attacks. The attacker wants that access to be really easy. Many backdoors are installed by users clicking something without realizing that the link that they clicked or the file that they opened is actually a threat. A backdoor can be implemented as a result of malware, a virus, or a worm.
Malware Delivery Mechanisms
Malware is not sentient (…not yet) and can’t just appear out of thin air; it needs to be transported and delivered to a computer or installed on a computer system in some manner. This can be done in several ways. The simplest way would be for attackers to gain physical access to an unprotected computer and perform their malicious work locally. But because obtaining physical access can be difficult, this can be done in other ways, as shown in the upcoming sections. Attackers can use some of these methods to simply gain access to a computer, make modifications, and so on, in addition to delivering the malware.
The method that a threat uses to access a target is known as a threat vector. Collectively, the means by which an attacker gains access to a computer in order to deliver malicious software is known as an attack vector. Probably the most common attack vector is via software.
Malware can be delivered via software in many ways. A person who emails a zipped file might not even know that malware also exists in that file. The recipients of the email will have no idea that the extra malware exists unless they have software to scan their email attachments for it. Malware could also be delivered via FTP. Because FTP servers are inherently insecure, it’s easier than you might think to upload insidious files and other software. Malware is often found among peer-to-peer (P2P) networks and bit torrents. Great care should be taken by users who use these technologies. Malware can also be embedded within, and distributed by, websites through the use of corrupting code or bad downloads. Malware can even be distributed by advertisements. And of course, removable media can victimize a computer as well. Optical discs, USB flash drives, memory cards, and connected devices such as smartphones can easily be manipulated to automatically run malware when they are inserted into the computer. (This is when AutoPlay/AutoRun is not your friend!) The removable media could also have hidden viruses or worms and possibly logic bombs (discussed earlier) configured to set that malware off at specific times.
Potential attackers also rely on user error. For example, if a user is attempting to access a website but types the incorrect domain name by mistake, that user could be redirected to an altogether unwanted website, possibly malicious in nature. This type of attack is known as typo squatting or URL hijacking.
Note
You learned details about typo squatting in Chapter 1.
URL stands for Uniform Resource Locator, which is the web address that begins with http or https. The potential attacker counts on the fact that millions of typos are performed in web browsers every day. These attackers “squat” on similar (but not exact) domain names. Once the user is at the new and incorrect site, the system becomes an easy target for spyware and other forms of malware. Some browsers come with built-in security such as antiphishing tools and the capability to autocheck websites that are entered, but the best way to protect against this issue is to train users to be careful when typing domain names.
Another way to propagate malware is to employ automation and web attack-based software “kits,” also known as exploit kits. Exploit kits are designed to run on web servers and are usually found in the form of PHP scripts. They target client computers’ software vulnerabilities that often exist within web browsers. One example of an exploit kit is the Blackhole exploit kit. It is used (and purchased) by potential attackers to distribute malware to computers that meet particular criteria, while the entire process is logged and documented.
Note
The automating of cybercrime, and the software used to do so, is collectively referred to as crimeware.
Active interception normally includes a computer placed between the sender and the receiver to capture and possibly modify information. If a person can eavesdrop on your computer’s data session, then that data can be stolen, modified, or exploited in other ways. Examples include session theft and man-in-the-middle (MITM) attacks. For more information on these attacks, see Chapter 4.
You Can’t Save Every Computer from Malware!
On a sad note, sometimes computers become so infected with malware that they cannot be saved. In this case, the data should be backed up (if necessary by removing the hard drive and slaving it to another system), and the operating system and applications reinstalled. The UEFI/BIOS of the computer should also be flashed. After the reinstall, the system should be thoroughly checked to make sure that there are no residual effects and that the system’s hard drive performs properly.
Password Attacks
There are many different ways that attackers can steal passwords, crack passwords, and perform other credential-based (password-based) attacks. The following sections describe the most common password-based attacks.
Dictionary-based and Brute-force Attacks

A dictionary-based attack pulls words from the dictionary or word lists to attempt to discover a user’s password. A dictionary attack uses a predefined dictionary to look for a match between the encrypted password and the encrypted dictionary word. Many times, a dictionary attack will recover a user’s password in a short period of time if simple dictionary words are used.
A hybrid attack uses a dictionary or a word list and then prepends and appends characters and numbers to dictionary words in an attempt to crack the user’s password. These programs are comparatively smart because they can manipulate a word and use its variations. For example, take the word password. A hybrid password audit would attempt variations such as 1password, password1, p@ssword, pa44w0rd, and so on. Hybrid attacks might add some time to the password-cracking process, but they increase the odds of successfully cracking an ordinary word that has had some variation added to it.
A brute-force attack uses random numbers and characters to crack a user’s password. A brute-force attack on an encrypted password can take hours, days, months, or years, depending on the complexity and length of the password. The speed of success depends on the speed of the CPU’s power. Brute-force audits attempt every combination of letters, numbers, and characters.
Tip
Tools such as 0phtCrack, LCP, Cain and Abel, and John the Ripper can all perform dictionary, hybrid, and brute-force password cracking.
Password Spraying

Password spraying is a type of attack in which an attacker attempts to compromise a system using a large number of usernames with a few commonly used passwords. Traditional brute-force attacks attempt to gain unauthorized access to a single account by guessing the password. This can quickly result in the targeted account getting locked out because commonly used account-lockout policies allow for a limited number of failed attempts (typically three to five) during a set period of time. During a password-spraying attack (also known as the “low-and-slow” method), the malicious actor attempts a single commonly used password (such as Password1, COVID19, or asdasd) against many accounts before moving on to attempt a second password, and so on. This technique allows the actor to remain undetected by avoiding rapid or frequent account lockouts.
Offline and Online Password Cracking

Weak passwords are the bane of today’s operating systems and networks. This could be because no policy for passwords was defined, and people naturally gravitate toward weaker, easier-to-remember passwords. Or it could be that a policy was defined but is not complex enough or is out of date. Whatever the reason, it would be wise to scan computers and other devices for weak passwords with an online or offline password cracker, which uses comparative analysis to break passwords and systematically guesses until it cracks the password. And, of course, a variety of password-cracking programs can help with this. Examples are John the Ripper and hashcat. These programs have a bit of a learning curve but are quite powerful. They can be used to crack all kinds of different passwords on a local system or on remote devices and computers. They sniff out other hosts on the network the way a protocol analyzer would. They are excellent tools to find out whether weak passwords are on the network or to help if users forget their passwords (when password resets are not possible). Attackers can discover hashed passwords on a compromised Windows, Linux, or macOS system and then crack the password on the same system (online) or on a separate dedicated system (offline). The goal is to obtain the original plaintext version of the password.
Figure 2-4 shows how an attacker steals the password hash of a compromised system and then uses that hash to crack the password “offline” in another system with superior compute resources.

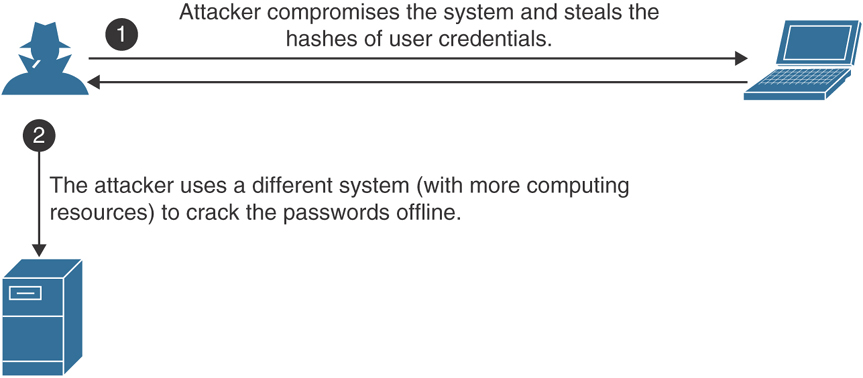
FIGURE 2-4 Offline Password Cracking
Rainbow Tables

A rainbow table is a precomputed table used to reverse engineer a cryptographic hash function and crack passwords. Attackers can perform cryptanalysis attacks a lot easier using these rainbow tables (as a form of a lookup table). Rainbow tables can be used with the L0phtCrack (https://sectools.org/tool/l0phtcrack/) and RainbowCrack applications.
Note
This attack can be defeated by implementing salting, which is the randomization of the hashing process.
Plaintext/Unencrypted

If your attempts to guess passwords have not been successful, sniffing or keystroke loggers might offer hope. Think about how much traffic passes over a typical network every day. Most networks handle a ton of traffic, and a large portion of it might not even be encrypted. Password sniffing requires that you have physical or logical access to the device. If that can be achieved, you can sniff the credentials right off the wire as users log in.
One such technique is to pass the hash. Passing the hash enables the hacker to authenticate to a remote server by using the underlying NT LAN Manager (NTLM) and/or LAN Manager (LM) hash of a user’s password, instead of using the associated plaintext password. Plaintext is the term used to describe unencrypted data (in this case an unencrypted password). Mimikatz is a pass the hash application that enables an attacker to authenticate to a remote server using the LM/NTLM hash of a user’s password, eliminating the need to crack/brute-force the hashes to obtain the clear-text password. Because Windows does not salt passwords, they remain static in the Local Security Authority Subsystem Service (LSASS) from session to session until the password is changed. If the password is stored in LSASS and the attacker can obtain a password hash, it can be functionally equivalent to obtaining the clear-text password. Rather than attempting to crack the hash, attackers can simply replay them to gain unauthorized access. You can download this pass the hash toolkit at https://github.com/gentilkiwi/mimikatz.
Physical Attacks
An organization’s building is one of its greatest assets and as such it should be properly protected. The following sections detail door access, biometric readers, access logs, and video surveillance to teach you some of the ways to protect the building, its contents, and its inhabitants and to ensure proper authentication when a person enters a building.
Malicious Flash Drives

Malware can be transferred to a computer by way of removable media, especially USB malicious flash drives. For example, an attacker could install a Trojan or ransomware by using a malicious flash drive, if he or she has physical access to the targeted system. Alternatively, the attacker could place the USB flash drive somewhere and use some aspects of social engineering to fool the user into inserting it in his or her system and getting infected. For example, the attacker may attach a key chain or pictures of a dog or a cat. This approach makes the attack a little more personal. The victim may try to find out who those keys and USB flash drive belong to. When he or she inserts the USB flash into a machine, the system is compromised.
Malicious Universal Serial Bus (USB) Cables

In a similar way to malicious USB flash drives, attackers can use malicious USB cables to compromise systems. Different USB cables are designed to infect connected devices with malware. These malicious USB cables work by injecting keystrokes onto the victim’s system when plugged into a USB-capable device.
Card Cloning Attacks

Attackers can perform different card cloning attacks. For example, an attacker can clone a credit card, a smartphone SIM card, or even the badges/cards used to access a building. Specialized software and hardware can be used to perform these cloning attacks.
For instance, a traditional attack on smartphones is SIM cloning (also known as phone cloning), which allows two phones to utilize the same service and allows an attacker to gain access to all phone data. V1 SIM cards had a weak algorithm that made SIM cloning possible (with some expertise). However, V2 cards and higher are much more difficult (if not impossible) to clone due to a stronger algorithm on the chip. Users and administrators should be aware of the version of SIM card being used and update it (or the entire smartphone) if necessary.
There are techniques available to unlock a smartphone from its carrier. Users should be advised against this, and as a security administrator, you should create and implement policies that make unlocking the SIM card difficult if not impossible. Unlocking the phone—making it SIM-free—effectively takes it off the grid and makes it difficult to track and manage. When the SIM is wiped, the international mobile subscriber identity (IMSI) is lost, and afterward the user cannot be recognized. However, you can attempt to blacklist the smartphone through its provider by using the International Mobile Equipment Identity (IMEI), electronic serial number (ESN), or mobile equipment identifier (MEID). The ID used will vary depending on the type and age of smartphone. Regardless, as a security administrator, you should avoid that tactic altogether because the damage has already been done, so protection of the SIM becomes vital.
Skimming

Skimming is a type of attack in which an attacker captures credit card information or information from other similar cards (gift cards, loyalty cards, identification cards, and so on) from a cardholder surreptitiously. Attackers use a device called a skimmer that can be installed at strategic locations such as ATMs and gas pumps to collect card data.
Attackers can also perform radio frequency identification (RFID) attacks to steal information. RFID has many uses, but it all boils down to identifying and tracking tags that are attached to objects. In the security world, that generally means authentication. As with any wireless technology, RFID is susceptible to attack. For example, some RFID tags can be affected by skimming, MITM attacks, sniffing, eavesdropping/replaying, spoofing, and jamming (DoS).
From an authentication standpoint, the attacker is using these attacks to try to find out the passcode. An RFID tag can also be reverse-engineered if the attacker gets possession of it. Finally, power levels can be analyzed to find out passwords. On some RFID tags, correct passcodes emit a different level of power than incorrect passcodes. To prevent these attacks, you, as the security administrator, or your team should consider newer-generation RFID devices, encryption, chip coatings, filtering of data, and multifactor authentication methods. Encryption is one of the best methods. Included in this prevention method are rolling codes, which are generated with a pseudorandom number generator (PRNG) and challenge-response authentication (CRA), where the user (or user’s device) must present the valid response to the challenge.
RFID ranges vary depending on the EM band used—from 10 cm up to 200 meters. Many authentication readers can be as much as 1 meter, which is enough to facilitate skimming of information by attackers. One way to avoid this is to use newer RFID proximity readers and keys—ones that use lower frequencies—from respectable companies.
Another way is to utilize the set of protocols called near-field communication (NFC). NFC generally requires that communicating devices be within 4 cm of each other, which makes skimming of information difficult. If an employee uses a smartphone to enter a building instead of an RFID device, then NFC should be implemented. NFC has obvious benefits for contactless payment systems or any other non-contact-oriented communications between devices. However, for optimal security, you should use contact-oriented readers and cards.
Adversarial Artificial Intelligence
Attackers have developed new ways to attack artificial intelligence (AI) and machine learning (ML) implementations. Examples of these adversarial techniques are tainting training data for ML and leveraging insecure implementations of machine learning algorithms.
Tainted Training Data for Machine Learning

Machine learning is being implemented in many solutions in use today (even in security products and solutions). Attackers can manipulate (taint) training data used for machine learning implementations to cause errors in the outcome of the ML solution. They can either change the integrity and modify the training data, or they can inject incorrect data in the training set.
Tip
If you are not familiar with the concepts of artificial intelligence and machine learning, the following article provides a good overview: https://vas3k.com/blog/machine_learning.
Security of Machine Learning Algorithms

Securing machine learning algorithms involves protecting the basis of security: confidentiality, integrity, and availability. The CIA concepts that apply to non-ML implementations also apply here with a few specific techniques. To protect ML implementations, you must classify malicious events in order to prevent them from interfering with algorithms and system operations. You need to prevent attackers from reaching ML system assets and from interfering with normal operations. You also need to prevent the attacker from reading critical data, as well as injecting any malicious or erroneous data in the training set.
Data poisoning attacks can be carried out by attackers to fool the machine learning system to produce incorrect errors. Another attack against machine learning implementations is the overfitting attack. When a machine learning system starts the learning process and “memorizes” its training data set, it will not generalize to new data. This process is referred to as overfitting. Overfitting and overfit models are very easy to attack because adversarial examples need only be a short distance away from the input space in the ML system.
Many ML systems are implemented by tuning a base model that is already trained to enhance the learning process. ML transfer attacks can be launched by an attacker in this scenario. When the pretrained model is widely available, an attacker may be able to formulate attacks using this pretrained model that will be robust enough to succeed against your tuned task-specific model (which is typically unavailable to the attacker). In addition, the ML system you are fine-tuning could possibly be a Trojan injected by the attacker that includes devious ML behavior that is unanticipated.
Supply-Chain Attacks
A supply-chain attack is a type of attack in which attackers target security weaknesses in the supply network. Attackers have successfully launched supply-chain attacks against many different types of industries (including manufacturing plants, financial services companies, energy and oil companies, technology companies, and more). Attackers can modify products or software during or right after the manufacturing process of a product by installing a rootkit or hardware-based spying components.
Cybersecurity experts recommend strict control of your supply network to prevent potential damage from today’s attackers. The supply chain is a complex network of interconnected stakeholders governed by supply and demand.
Tip
An example of a supply-chain attack is the manipulation of system maintenance software called CCleaner. This software was manipulated in the supply chain including implants designed to spy and steal sensitive information from many large technology companies. You can obtain more information about this attack at https://blog.talosintelligence.com/2017/09/ccleaner-c2-concern.html.
Cloud-based vs. On-premises Attacks
Many organizations are moving to the cloud or deploying hybrid solutions to host their applications. Organizations moving to the cloud are almost always looking to transition from capital expenditure (CapEx) to operational expenditure (OpEx). Most Fortune 500 companies operate in a multicloud environment. It is obvious that cloud computing security is more important than ever. Cloud computing security includes many of the same functionalities as traditional IT security, which includes protecting critical information from theft, data exfiltration, and deletion, as well as privacy.
Note
You will learn details about cloud computing architectures in Chapter 10, “Summarizing Virtualization and Cloud Computing Concepts.”
Cloud Security Threats
There are many potential threats when organizations move to a cloud model. For example, although your data is in the cloud, it must reside in a physical location somewhere. Your cloud provider should agree in writing to provide the level of security required for your customers. The following are questions to ask a cloud provider before signing a contract for its services:

Who has access? Access control is a key concern because insider attacks are a huge risk. Anyone who has been approved to access the cloud is a potential hacker, so you want to know who has access and how they were screened. Even if it was not done with malice, an employee can leave, and then you find out that you don’t have the password, or the cloud service gets canceled because maybe the bill didn’t get paid.
What are your regulatory requirements? Organizations operating in the United States, Canada, and the European Union must abide by many regulatory requirements (for example, ISO/IEC 27002, EU-U.S. Privacy Shield Framework, ITIL, and COBIT). You must ensure that your cloud provider can meet these requirements and is willing to undergo certification, accreditation, and review.
Do you have the right to audit? This particular item is no small matter in that the cloud provider should agree in writing to the terms of the audit. With cloud computing, maintaining compliance could become more difficult to achieve and even harder to demonstrate to auditors and assessors. Of the many regulations touching on information technology, few were written with cloud computing in mind. Auditors and assessors might not be familiar with cloud computing generally or with a given cloud service in particular.
Division of compliance responsibilities between cloud provider and cloud customer must be determined before any contracts are signed or service is started.
What type of training does the provider offer its employees? This is a rather important item to consider because people will always be the weakest link in security. Knowing how your provider trains its employees is an important item to review.
What type of data classification system does the provider use? Questions you should be concerned with here include what data classification standard is being used and whether the provider even uses data classification.
How is your data separated from other users’ data? Is the data on a shared server or a dedicated system? A dedicated server means that your information is the only thing on the server. With a shared server, the amount of disk space, processing power, bandwidth, and so on is limited because others are sharing this device. If it is shared, the data could potentially become comingled in some way.
Is encryption being used? Encryption should be discussed. Is it being used while the data is at rest and in transit? You will also want to know what type of encryption is being used. For example, there are big technical differences between DES and AES. For both of these algorithms, however, the basic questions are the same: Who maintains control of the encryption keys? Is the data encrypted at rest in the cloud? Is the data encrypted in transit, or is it encrypted at rest and in transit?
What are the service-level agreement (SLA) terms? The SLA serves as a contracted level of guaranteed service between the cloud provider and the customer that specifies what level of services will be provided.
What is the long-term viability of the provider? How long has the cloud provider been in business, and what is its track record? If it goes out of business, what happens to your data? Will your data be returned and, if so, in what format?
Will the provider assume liability in the case of a breach? If a security incident occurs, what support will you receive from the cloud provider? While many providers promote their services as being “unhackable,” cloud-based services are an attractive target to hackers.
What is the disaster recovery/business continuity plan (DR/BCP)? Although you might not know the physical location of your services, it is physically located somewhere. All physical locations face threats such as fire, storms, natural disasters, and loss of power. In case of any of these events, how will the cloud provider respond, and what guarantee of continued services is it promising?
Even when you end a contract, you must ask what happens to the information after your contract with the cloud service provider ends.
Insufficient due diligence is one of the biggest issues when moving to the cloud. Security professionals must verify that issues such as encryption, compliance, and incident response are worked out before a contract is signed.
Cloud Computing Attacks
Because cloud-based services are accessible via the Internet, they are open to any number of attacks. As more companies move to cloud computing, look for hackers to follow. Some of the potential attack vectors that criminals might attempt include the following:

Session hijacking: This attack occurs when the attacker can sniff traffic and intercept traffic to take over a legitimate connection to a cloud service.
DNS attack: This form of attack tricks users into visiting a phishing site and giving up valid credentials.
Cross-site scripting (XSS): This type of attack is used to steal cookies that can be exploited to gain access as an authenticated user to a cloud-based service.
SQL injection: This attack exploits vulnerable cloud-based applications that allow attackers to pass SQL commands to a database for execution.
Session riding: This term is often used to describe a cross-site request forgery (CSRF) attack. Attackers use this technique to transmit unauthorized commands by riding an active session using an email or malicious link to trick users while they are currently logged in to a cloud service.
Distributed denial-of-service (DDoS) attack: Some security professionals have argued that the cloud is more vulnerable to DDoS attacks because it is shared by many users and organizations, which also makes any DDoS attack much more damaging.
Man-in-the-middle cryptographic attack: This attack is carried out when the attacker places himself or herself in the communication path between two users. Any time the attacker can do this, there is the possibility that he or she can intercept and modify communications.
Side-channel attack: An attacker could attempt to compromise the cloud by placing a malicious virtual machine in close proximity to a target cloud server and then launching a side-channel attack.
Authentication attack: Authentication is a weak point in hosted and virtual services and is frequently targeted. There are many ways to authenticate users, such as based on what a person knows, has, or is. The mechanisms used to secure the authentication process and the method of authentication used are frequent targets of attackers.
API attacks: Often APIs are configured insecurely. An attacker can take advantage of API misconfigurations to modify, delete, or append data in applications or systems in cloud environments.
Regardless of the model used, cloud security is the responsibility of both the client and the cloud provider. These details will need to be worked out before a cloud computing contract is signed. The contracts will vary depending on the given security requirements of the client. Considerations include disaster recovery, SLAs, data integrity, and encryption. For example, is encryption provided end to end or just at the cloud provider? Also, who manages the encryption keys: the cloud provider or the client? Overall, you need to ensure that the cloud provider has the same layers of security (logical, physical, and administrative) in place that you would have for services you control.
Cryptographic Attacks
Attackers can launch different cryptographic attacks against weak cryptography (crypto) implementations. The following sections describe three common crypto attacks: collision, birthday, and downgrade attacks.
Collision

A collision occurs when two different files end up using the same hash. Message Digest Algorithm 5 (MD5) is a legacy hashing algorithm that is used to attempt to provide data integrity. By checking the hash produced by the downloaded file against the original hash, you can verify the file’s integrity with a level of certainty. However, MD5 hashes are susceptible to collisions. Due to this low collision resistance, MD5 is considered to be harmful today. MD5 is also vulnerable to threats such as rainbow tables and preimage attacks. The best solution to protect against these attacks is to use a stronger type of hashing function such as SHA-2 or higher. The Secure Hash Algorithm (SHA) is one of a number of hash functions designed by the U.S. National Security Agency (NSA) and published by NIST. These functions are used widely in the U.S. government. Because MD5 and SHA-1 have vulnerabilities, government agencies and the private sector started using SHA-2 and newer implementations.
Note
You will learn more about hashing algorithms in Chapter 16, “Summarizing the Basics of Cryptographic Concepts.”
It is important that a hashing algorithm be collision-resistant. If it has the capability to avoid the same output from two guessed inputs (by an attacker attempting a collision attack), it is collision-resistant. When it comes to cryptography, “perfect hashing” is not possible because usually unknowns are involved, such as the data to be used to create the hash and what hash values have been created in the past. Though perfect is not possible, it is possible to increase collision resistance by using a more powerful hashing algorithm.
Birthday

A birthday attack is an attack on a hashing system that attempts to send two different messages with the same hash function, causing a collision (similarly to the concept explained in the preceding section). It is based on the birthday problem in probability theory (also known as the birthday paradox). It can be summed up simply as the following: a randomly chosen group of people will have a pair of persons with the same calendar date birthday. Given a standard calendar year of 365 days, the probability of this occurring with 366 people is 100 percent (367 people on a leap year). So far, this makes sense and sounds logical.
The paradox (thoughtfully and mathematically) comes into play when fewer people are involved. With only 57 people, there is a 99 percent probability of a match (a much higher percentage than one would think), and with only 23 people, there is a 50 percent probability. Imagine that and blow out your candles! And by this, I mean use hashing functions with strong collision resistance. Because if attackers can find any two messages that digest the same way (use the same hash value), they can deceive a user into receiving the wrong message. To protect against a birthday attack, you should use a secure transmission medium, such as SSH, or encrypt the entire message that has been hashed.
Downgrade

A downgrade attack is a type of cryptographic attack that forces the rollback of a strong algorithm in favor of an older, lower-quality algorithm or mode of operation. Attackers leverage systems that have legacy crypto algorithms typically enabled for backward compatibility with older systems. Downgrade attacks can be performed by attackers in combination with an MITM attack.
Downgrade attacks can take many forms. However, they can target the crypto algorithm itself (such as downgrading from AES to DES or RC4) or the version of an algorithm (such as downgrading from TLS 1.3 to 1.0).
Chapter Review Activities
Use the features in this section to study and review the topics in this chapter.
Review Key Topics
Review the most important topics in the chapter, noted with the Key Topic icon in the outer margin of the page. Table 2-2 lists a reference of these key topics and the page number on which each is found.

Table 2-2 Key Topics for Chapter 2
Key Topic Element |
Description |
Page Number |
|---|---|---|
Paragraph |
Description of malware |
33 |
Paragraph |
Description of ransomware |
33 |
Paragraph |
Description of cryptomalware |
34 |
A ransomware attack |
34 |
|
Paragraph |
Description of Trojan horses |
35 |
Paragraph |
Description of remote access Trojans |
35 |
Paragraph |
Description of rootkits |
35 |
Paragraph |
Description of worms |
36 |
Paragraph |
Description of fileless malware |
37 |
Paragraph |
Description of Command and Control, bots, and botnets |
37 |
A botnet and C2 example |
38 |
|
The botnet performing a DDoS attack |
39 |
|
Paragraph |
Description of logic bombs |
39 |
Paragraph |
Description of spyware |
40 |
Paragraph |
Description of potentially unwanted programs (PUPs) |
40 |
Paragraph |
Description of keyloggers |
42 |
Paragraph |
Description of backdoors |
43 |
Paragraph |
Description of dictionary-based and brute-force attacks |
45 |
Paragraph |
Description of password spraying |
46 |
Paragraph |
Description of password cracking |
46 |
Offline password cracking |
47 |
|
Paragraph |
Description of rainbow tables |
47 |
Paragraph |
Description of password hacking via pass the hash technique |
47 |
Paragraph |
Description of malicious flash drives |
48 |
Paragraph |
Description of malicious USB drives |
48 |
Paragraph |
Description of card cloning attacks |
48 |
Paragraph |
Description of skimming |
49 |
Paragraph |
Description of tainted training data used for machine learning |
50 |
Paragraph |
Description of securing machine learning algorithms |
50 |
List |
Questions to ask a cloud provider before signing a contract for its services |
52 |
List |
Attack vectors against cloud-based services |
54 |
Paragraph |
Description of collisions and hashing algorithm security vulnerabilities |
55 |
Paragraph |
Description of birthday attacks |
56 |
Paragraph |
Description of downgrade attacks |
56 |
Define Key Terms
Define the following key terms from this chapter, and check your answers in the glossary:
Review Questions
Answer the following review questions. Check your answers with the answer key in Appendix A.
1. What is a group of compromised computers that have software installed by a worm or Trojan?
2. What term is often used to describe a compromised system that can be updated automatically and remotely?
3. What is a common symptom of spyware?
4. You noticed that your DHCP server is flooded with information. After analyzing this condition, you found that the information is coming from more than 100 computers on the network. What is most likely the reason?
5. Which type of malicious software encrypts sensitive files and asks the user to pay in order to obtain a key recover those files?
6. What is a malicious attack that executes at the same time every week?
7. What is still one of the most common ways that attackers spread ransomware?
8. What is a type of malware that appears to a user as legitimate but actually enables unauthorized access to the user’s computer?
