An employee who earns $60,000 a year and wastes five minutes a day (dealing with version control, file formats and other document related problems) costs an organisation $635 per year in lost productivity.
Osterman Research, 2009
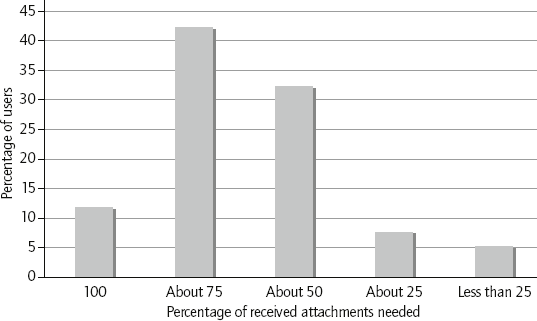
How much are you costing yourself and your business by behaving thoughtlessly with attachments? Email seduces us into circulating huge volumes of attachments, very few of which are really needed by the recipient, as shown by the results of our research in Figure 15.1.
This chapter covers patrolling your use of attachments as a sender to:
- improve the chance of your email being well received by the recipient
- increase security and confidentiality
- raise the probability of everyone working with the correct version of the file (spreadsheet, document, etc).
Email limits – a necessary evil?
There are several reasons why organisations impose restrictions on attachment sizes.
- Attachments use valuable bandwidth as they are transmitted (sent/received). To preserve your email system’s reliability (especially speed and stability), most businesses need to restrict the size of attachments that can be transmitted during normal working hours: this is usually between 5 and 20 MB. Emails over the limit are held for sending/delivery until after normal working hours.
- Network bandwidth and speed is directly proportional to cost.
- Carbon footprints are directly related to mailbox sizes, because more bandwidth and storage consumes more energy.
Is there scope to save time in the way I handle attachments as a sender?
Attachment dumping is the fastest way to annoy people and waste everyone’s time. These are the top seven attachment time thieves for recipients, all of which are caused by the sender:
- Missing attachments.
- Large attachments that do not reach the recipient on time.
- Sending multiple attachments in a single email.
- Not working with the most current version of the file.
- Not saving attachments so they can be found quickly and easily.
- Sending/receiving attachments containing hidden confidential metadata (changes made by the originator such as revisions, by whom and when).
- Sending/receiving attachments containing viruses and malware.
Improving how you manage attachments both as a sender and as a recipient will help you and others recoup further time from the email thieves.

Always attach your file first, then write your email. This reduces the likelihood of another round of email ping-pong to resolve the missing attachment dilemma.
Keeping attachment sizes within limits
Here are four simple ways to check and reduce the size of the attachments you send to ensure you stay within the limit for transmission during working hours.
- Find out about both your own and the recipient’s limit for transmitting emails during the working day.
- Check the file size either from the folder list (in Explorer) or right-click on the file itself. Microsoft (PC) users should pick ‘Properties’ from the drop-down menu; Apple users should pick ‘Get Info’.
- Compress (zip) large attachments (over 5 MB) using proprietary software like WinZip and Stuffit.
- If the compressed file is still large, either split the contents and send the files in separate emails or compress the original file. For example, reduce the resolution of images.
The actions outlined above increase the likelihood of your email being delivered on time and promote a more professional image by sparing you the embarrassing ‘Where is it?’ email chain/phone call.
Efficient ways to send multiple attachments
Often several files need to be attached to single emails (for example, for board meetings, sales presentations, budget and personnel reviews). The main challenge facing recipients of multiple attachments are:
- being sure that they have them all
- the reading order
- which attachment, if any, specifically requires their attention.
Time is then squandered by email dialogues while recipients clarify what has been sent and what is required of them.

Include a ‘Read me first’ file that lists how many files are attached and their reading order.
Five more tips to make friends not enemies and impress recipients when sending multiple attachments are:
- Limit the total number in a single email to seven.
- Zip the files into one main file (again using proprietary software such as WinZip and Stuffit).
- Label each file with an intelligent and self-explanatory name.
- Where there are multiple recipients, draw individuals’ attention to files (and sections) that require their specific scrutiny.
- If some recipients only need to see certain pages tell them which ones.
These tips raise the likelihood of everyone reading the files properly, being better briefed and generally able to work more productively. You also reduce the carbon footprint of attachments: as there is nothing more annoying and wasteful than printing a large document only to find you needed only one page. Plus patrolling your use of attachments continues to enhance your email dress code.
Sharing to reduce the volume of unnecessary attachments and data leakage
The uncontrolled circulation of attachments gives rise to a number of challenges:
- Files become out of date almost as soon as they are sent: a revised version has to then be sent immediately after. This seems to happen often with meeting papers and budgets.
- Everyone keeps their own copy (copies).
- People work from different versions of the file.
- There is a high risk of breach of compliance, because attachments are sometimes retained which by law should be deleted. (For example, under the Data Protection Act personal data such as CVs should be deleted once they are no longer relevant.)
- Copies are printed ‘just in case’.
File sharing (either through the network or collaborative tools like Notes or Microsoft SharePoint) substantially reduces the unnecessary drain on resources, from your personal time to your server space and carbon footprint. It also increases the probability of everyone working from the correct file version and minimises the risk of a breach of compliance and security as you can control access to the file.
Securing the content from being distorted
While attachments are not quite as vulnerable as the body of an email, they are not tamper-proof. Furthermore, the contents can still reveal hidden confidential information in the form of metadata (track changes, number of revisions, etc.). Many organisations have found themselves put at significant financial and reputational risk through employees leaving metadata in files, as outlined in the introduction to this part.
![]()
The ‘Dodgy Dossier’ incident (2002) was created through the metadata left in the UK government files. Analysis of the metadata revealed that files had been plagiarised from other non-government sources (a postgraduate thesis) and that the edits had been made to make the case for Iraq’s ability to produce nuclear weapons.
Do
- Clean up attachments before sending them – for example, remove track changes, comments and hidden columns.
- Use a function like the ‘Inspector’ in Word 2007 or a specialist product like Workshare™ and ConfidentSend™.
- Unless you are expecting the recipient to work on them, convert and send the file as a pdf.
- Password-protect (or encrypt) the files if they contain highly sensitive and confidential information.
- Send an original hand copy if you have any concerns that the recipient might alter an electronic version and then present their version as the authentic one.
Don’t
- Assume that because you have sent the document as a pdf, the recipient cannot change the contents. Using Acrobat Professional, any pdf file can be opened and changed. (Sadly, even if you encrypt the pdf, there is software which lets the recipient decrypt it and tamper with it.)
For more information on this subject see ‘A Guide to Document Comparison and Security for Corporate Legal’ from Osterman Research – www.ostermanresearch.com.
Cleaning up attachments not only improves productivity but also protects your reputation and minimises the risk of leaking confidential information.
Attachments and handheld email devices
Attachments can present a problem to those accessing their emails on a handheld email device such as a BlackBerry or iPhone, as older models often do not download and display attachments satisfactorily. This is changing. Nonetheless, it is always worth checking first with the recipient.

If the recipient is working on a handheld email device, paste just the critical part/executive summary of the attachment into the body of the email.
Microsoft Office 2007 lets you send the file you are working on directly from within the application without opening the email application. Go to the ‘Office’ button and pick ‘Send’. This will open up your email software and you can either attach or insert the file automatically.
![]()
Patrolling your use of attachments as a sender and recipient will help you reclaim further time from email time thieves, reduce your carbon footprint and further enhance your email dress code.
- Send a link rather than the actual file wherever possible.
- When sending more than five files in one email, attach a ‘Read me first’ note telling the recipient how many files to expect, what they are about and the reading order. Draw to their attention to sections/pages that require their specific attention.
- Viewing attachments on handheld email devices can be difficult. Copy and paste key information into the body of the email.
- Clean attachments before sending to remove any potentially damaging metadata.
- Protect and secure the contents of attachments which are sensitive, confidential and may be regarded as legally binding.