CHAPTER 10
Information Governance and Information Technology Functions
Information technology (IT) is a core function that contributes to, and is impacted by information governance (IG) program efforts. IT departments typically have been charged with keeping the “plumbing” of IT intact—the network, servers, applications, and data. However, while the output of IT is in their custody, they have not been held to account for it; that is, the information, reports, and databases they generate have long been held to be owned by users in business units. This has left a gap of responsibility for governing the information that is being generated and managing it in accordance with legal and regulatory requirements, standards, and best practices.
Certainly, on the IT side, shared responsibility for IG means the IT department itself must take a closer look at IT processes and activities with an eye to IG. A focus on improving IT efficiency, software development processes, and data governance and quality will help contribute to the overall IG program effort. IT is an integral piece of the program.
Debra Logan, vice president and distinguished analyst at Gartner, states:
Information governance is the only way to comply with regulations, both current and future, and responsibility for it lies with the CIO and the chief legal officer. When organizations suffer high-profile data losses, especially involving violations of the privacy of citizens or consumers, they suffer serious reputational damage and often incur fines or other sanctions. IT leaders will have to take at least part of the blame for these incidents.1
Gartner predicted that the need to implement IG is so critical that significant numbers of chief information officers (CIOs) will be terminated for their inability to implement IG successfully. Data breaches, ransomware attacks, and significant system downtime all end up on the CIO's doorstep. And if serious enough, the CEO can even be held to account for IT department deficiencies and mistakes.
Aaron Zornes, chief research officer at the MDM (Master Data Management) Institute, stated: “While most organizations’ information governance efforts have focused on IT metrics and mechanics such as duplicate merge/purge rates, they tend to ignore the industry- and business-metrics orientation that is required to ensure the economic success of their programs.”2
Four IG best practices in this area can help CIOs and IT leaders to be successful in delivering business value as a result of IG efforts:
- Make the business case for IG by tying its objectives to business objectives.
To garner the resources and time needed to implement an IG program, you must develop a business case in real, measurable terms and tie it to corporate objectives. When executives see this alignment of objectives, they are more likely to support an IG program. The business case must be presented in order to gain executive sponsorship, which is an essential component of any IG effort. Without executive sponsorship, the IG effort will fail. Making the business case and having metrics to measure progress and success toward meeting business objectives are absolute musts.
- Don't focus on technology, focus on business impact.
Technology often fascinates those in IT—to the point of obfuscating the reason that technologies are leveraged in the first place: to deliver business benefit. Therefore IT needs to reorient its language, its vernacular, its very focus when implementing IG programs. IT needs to become more business savvy, more businesslike, more focused on delivering business benefits that can help the organization to meet its business goals and achieve its business objectives. “Business leaders want to know why they should invest in an information governance program based on the potential resulting business outcomes, which manifest as increased revenues, lower costs and reduced risk.”3
- Customize your IG approach for your specific business, folding in any industry-specific best practices possible.
You cannot simply take a boilerplate IG plan, implement it in your organization, and expect it to be successful. Sure, there are components that are common to all industries, but tailoring your approach to your organization is the only way to deliver real business value and results. That means embarking on an earnest effort to develop and sharpen your business goals, establishing business objectives that consider your current state and capabilities and external business environment and legal factors unique to your organization. It also means developing a communications and training plan that fits with your corporate culture. And it means developing meaningful metrics to measure your progress and the impact of the IG program, to allow for continued refinement and improvement.
- Standardize the use of business terms.
IG requires a cross-functional effort, so you must be speaking the same language, which means the business terms you use in your organization must be standardized. This is the very minimum to get the conversation started. But IG efforts will delve much more deeply into the organization of information and seek to standardize the taxonomy for organizing documents and records and even the metadata fields that describe in detail those documents and records across the enterprise.
Overall, being able to articulate the business benefits of your planned IG program will help you recruit an executive sponsor, help the program gain traction and support, and help you implement the program successfully.4
Several key foundational programs should support your IG effort in IT, including data governance, master data management (MDM), IT governance, and implementing accepted IT standards and best practices.
Data Governance
We touched on data governance in Chapter 2. In today's business environment, data is mountainous, data is growing, data is valuable, and the insights that can be gained by analyzing clean, reliable data with the latest analytics tools are a sort of new currency. This is where the principles of infonomics enter into play. There are nuggets of gold in those mountains of data. Some insights can be monetized or leveraged for economic advantage. And leveraging those discoveries can provide a sustainable competitive advantage for the organization in areas such as customer acquisition, customer retention, and customer service.
The challenge is largely in garnering control over data and in cleaning, securing, and protecting it; doing so requires effective data governance strategies. But data governance is not only about cleaning and securing data; it is also about delivering it to the right people at the right time (sometimes this means in real time) to provide strategic insights and opportunities. If a data governance program is successful, it can add profits directly to the bottom line, while improving productivity for knowledge workers.5
Data governance involves processes and controls to ensure that information at the data level—raw data that the organization is gathering and inputting—is true and accurate, and unique (not redundant). It involves data cleansing (or data scrubbing) to strip out corrupted, inaccurate, or extraneous data and de-duplication to eliminate redundant occurrences of data.
Data governance focuses on information quality from the ground up (at the lowest or root level), so that subsequent reports, analyses, and conclusions are based on clean, reliable, trusted data (or records) in database tables. Data governance is the most fundamental level at which to implement IG. Data governance efforts seek to ensure that formal management controls—systems, processes, and accountable employees who are stewards and custodians of the data—are implemented to govern critical data assets to improve data quality and to avoid negative downstream effects of poor data.
Data governance is a newer, hybrid quality control discipline that includes elements of data quality, data management, IG policy development, business process improvement, and compliance and risk management.
Good data governance programs should extend beyond the enterprise to include external stakeholders (suppliers, customers) so an organization has its finger on the pulse of its extended operations. In other words, enforcing data governance at the earliest possible point of entry—even external to the organization—can yield significant efficiencies and business benefits downstream. And combining data governance with real-time business intelligence (BI) and data analytics software not only can yield insights into significant and emerging trends but also can provide solid information for decision makers to use in times of crisis—or opportunity.
Steps to Governing Data Effectively
Nine key steps you can take to govern data effectively are listed next:
- Recruit a strong executive sponsor: As in broader IG efforts, data governance requires cross-functional collaboration with a variety of stakeholders. To drive and facilitate this sometimes contentious conversation, a strong executive sponsor is required. This is not an easy task since executives generally do not want to deal with minutia at the data level. You must focus on the realizable business benefits of improved data governance (i.e. specific applications that can assist in customer retention, revenue generation, and cost cutting).
- Assess your current state: Survey the organization to see where the data repositories or silos of data are, what problems related to data exist, and where some opportunities to improve lie. Document where your data governance program stands today and then map out your road to improvement in fundamental steps.
- Set the ideal state vision and strategy: Create a realistic vision of where your organization wants to go in its data governance efforts, and clearly articulate the business benefits of getting there. Articulate a measureable impact. Track your progress with metrics and milestones.
- Compute the value of your data. Try to put some hard numbers to it. Calculate some internal numbers on how much value data—good data—can add to specific business units. Apply some of the formulas for calculating the value of information presented in Doug Laney's groundbreaking Infonomics book. Data is unlike other assets that you can see or touch (cash, buildings, equipment, etc.), and it changes daily, but it has real value.
- Assess risks. What is the likelihood and potential cost of a data breach? A major breach? Are ransomware attacks on the rise in your industry? What factors come into play, and how might you combat these potential threats? Perform a risk assessment to rank and prioritize threats and assign probabilities to those threats so you may develop appropriate countermeasures.
- Implement a going-forward strategy. It is a significantly greater task to try to improve data governance across the enterprise for existing data, versus focusing on smaller business units, one at a time.6 Remember, you may be trying to fix years if not decades of bad behavior, mismanagement, and lack of governance. Taking an “incremental approach with an eye to the future” provides for a clean starting point and can substantially reduce the pain required to implement. A strategy where new data governance policies for handling data are implemented beginning on a certain future date is a proven best practice.
- Assign accountability for data quality to business units, not IT. Typically, IT has had responsibility for data quality, yet the data generation is mostly not under that department's control, since most data is created in the business units. A pointed effort must be made to push responsibility and ownership for data to data stewards in the business units that create and use the data.
- Manage the change. Educate, educate, educate. People must be trained to understand why the data governance program is being implemented and how it will benefit the business. The new policies represent a cultural change, and supportive program messages and training are required to make the shift.
- Monitor your data governance program. See where shortfalls might be, and continue to fine-tune the program.7
From a risk management perspective, data governance is a critical activity that supports decision makers and can mean the difference between retaining a customer and losing one. Protecting your data is protecting the lifeblood of your business, and improving the quality of the data will improve decision making, foster compliance efforts, and yield competitive advantages.
Data Governance Framework
The Data Governance Institute has created a data governance framework, a visual model to help guide planning efforts and a “logical structure for classifying, organizing, and communicating complex activities involved in making decisions about and taking action on enterprise data.”8 (See Figure 10.1.) The framework applies more to larger organizations, which have greater complexity, greater internal requirements, and greater, more complex regulatory demands. It allows for a conceptual look at data governance processes, rules, and people requirements.
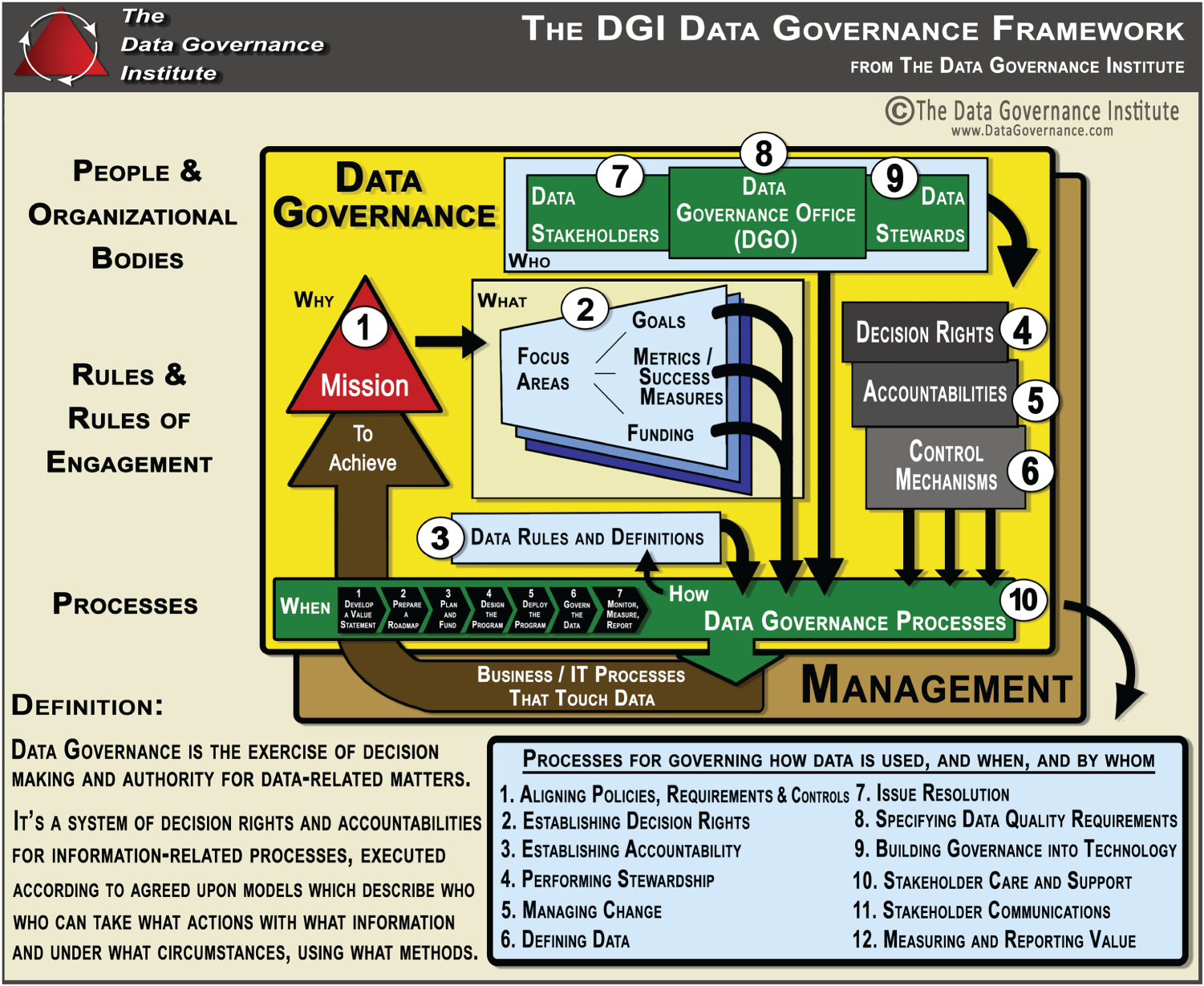
Figure 10.1 DGI Data Governance Framework™
Source: The Data Governance Institute (datagovernance.com).
Information Management
Information management is a principal function of IT. It is complex and spans a number of subdisciplines but can be defined as the “application of management techniques to collect information, communicate it within and outside the organization, and process it to enable managers to make quicker and better decisions.”9 It is about managing information, which is more than just collecting and processing data from varying sources and distributing it to various user audiences. It includes a number of subcomponent tasks, including these four key functions:
- Master data management (MDM) is a key process for IG success in the IT department, which extends to involved business units. An emerging discipline, MDM came into prominence around 2010–2012, coinciding with the Big Data trend. The goal of MDM is to ensure that reliable, accurate data from a single source is leveraged across business units. That is, a key aim is to establish a “single version of the truth”10 and eliminate multiple, inconsistent versions of data sets, which are more common than most might think, especially in larger organizations with physically distributed operations and large numbers of servers and databases. MDM gets to the core of data integrity issues, essentially asking “Is this data true and accurate? Is this the best and only, final version?” MDM grew from the need to create a standardized, “discrete discipline” to ensure there was a single version to base analytics calculations on and to base decisions on.11 According to Gartner, MDM:
is a technology-enabled discipline in which business and IT work together to ensure the uniformity, accuracy, stewardship, semantic consistency and accountability of the enterprise's official shared master data assets. Master data is the consistent and uniform set of identifiers and extended attributes that describes the core entities of the enterprise including customers, prospects, citizens, suppliers, sites, hierarchies and chart of accounts.12
What is the business impact? How are operations enhanced and how does that contribute to business goals? One set of reliable, clean data is critical to delivering quality customer service, reducing redundant efforts and therefore operational costs, improving decision making, monetizing data, and even potentially to lower product and marketing costs. A unified view of customers, products, or other data elements is critical to turning these business goals into reality.
Again, the larger the organization, the greater the need for MDM.
- Information life cycle management (ILM) is managing information appropriately and optimally at different stages of its useful life, from creation, through distribution and use, including meeting legal and regulatory requirements, and through its final disposition, which can be destruction, archiving, or transfer to another entity. Organizations historically over-retain information; however, studies show that information quickly loses its value and that once data has aged 10 to 15 days, the likelihood it will be used again is around 1%.13 Based on its use characteristics, differing storage management strategies are appropriate. It defies business logic to manage information that has little value with as much IT resource as information that is high value. Doing so is a misuse of resources. To execute ILM properly, the value of certain data sets and records must be appraised and policies must be formed to manage it, recognizing that information value changes over the life cycle, which requires varying strategies and resource levels.14 ILM conceptually includes and can begin with MDM and is linked to compliance requirements and capabilities.
- Data architecture refers to the “design of structured and unstructured information systems”15 in an effort to optimize data flow between applications and systems so that they are able to process data efficiently. Further, data architecture uses data modeling, standards, IG policies, and rules for governing data and how it populates databases and how those databases and applications are structured.16 Some key issues to uncover when researching data architecture and design include data structure, or schema, which databases are used (e.g. Oracle Database 18.1.0, IBM Db2, MS SQL Server 2017), methods of query and access (e.g. SQL), the operating systems the databases operate on, and even their hardware (which can affect data architecture features and capabilities).
- Data modeling can be complex, yet it is an important step in overall IG for the IT department. It “illustrates the relationships between data.” Data modeling is an application software design process whereby data processes and flows between applications are diagrammed graphically in a type of flowchart that formally depicts where data is stored, which applications share it, where it moves, and the interactions regarding data movement between applications. “Data modeling techniques and tools capture and translate complex system designs into easily understood representations of the data flows and processes, creating a blueprint for construction and/or re-engineering.”17 Good data models allow for troubleshooting before applications are written and implemented.
The importance of data modeling as a foundation for the application development process is depicted in Figure 10.2.
Once the data model is developed, business rules and logic can be applied through application development. A user interface is constructed for the application, followed by movement of data or e-documents through work steps using work flow capabilities, and then integration with existing applications (e.g. enterprise resource planning or customer relationship management systems). Typically this is accomplished through an application programming interface, a sort of connector that allows interaction with other applications and databases.
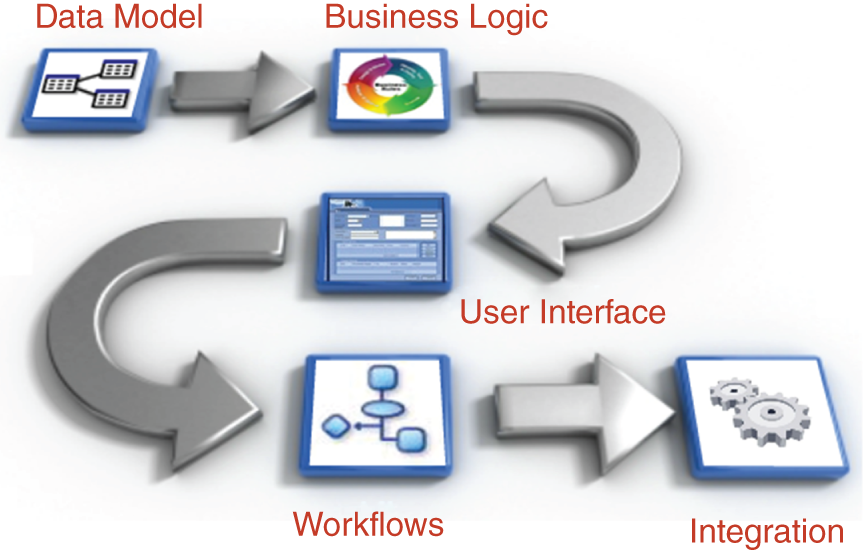
Figure 10.2 Key Steps from Data Modeling to Integration
Source: Adapted from Orangescape.com (http://www.orangescape.com/wp-content/uploads/2010/10/Application-Development-Lifecycle-OrangeScape.png).
There are six approaches to data modeling:
- Conceptual. The conceptual approach merely diagrams data relationships at the “highest level”18 showing the storage, warehousing, and movement of data between applications.
- Enterprise. The enterprise approach is a more business-oriented version of conceptual data modeling that includes specific requirements for an enterprise or business unit.
- Logical. Pertinent to the design and architecture of physical storage, logical data modeling “illustrates the specific entities, attributes, and relationships involved in a business function.”
- Physical. The physical approach depicts the “implementation of a logical data model” relative to a specific application and database system.
- Data integration. This approach is just what it says; it involves merging data from two or more sources, processing the data, and moving it into a database. “This category includes Extract, Transform, and Load (ETL) capabilities.”19
- Reference data management. This approach often is confused with MDM, although they do have interdependencies. Reference data is a way to refer to data in categories (e.g. having lookup tables— standard industry classification or SIC codes) to insert values,20 and is used only to “categorize other data found in a database, or solely for relating data in a database to information beyond the boundaries of the enterprise.”21 So reference data is not your actual data itself but a reference to categorize data.
Figure 10.3 shows different categories of data.

Figure 10.3 Categories of Data
Source: IBM.com.
IT Governance
As introduced in Chapter 2, IT governance is about efficiency and value creation. IT governance is the primary way that stakeholders can ensure that investments in IT create business value and contribute toward meeting business objectives.22 This strategic alignment of IT with the business is challenging yet essential. IT governance programs go further and aim to improve IT performance, deliver optimum business value, and ensure regulatory compliance.
Although the CIO typically has line responsibility for implementing IT governance, the chief executive officer and board of directors must receive reports and updates to discharge their responsibilities for IT governance and to see that the program is functioning well and providing business benefits.
The focus of governance in IT is on the actual software development and maintenance activities of the IT department or function, and IT governance efforts focus on making IT efficient and effective. That means minimizing costs by following proven software development methodologies and best practices, principles of data governance and information quality, and project management best practices while aligning IT efforts with the business objectives of the organization.
IT Governance Frameworks
Several IT governance frameworks can be used as a guide to implementing an IT governance program.
Although frameworks and guidance like COBIT® and ITIL have been widely adopted, there is no absolute standard IT governance framework; the combination that works best for your organization depends on business factors, corporate culture, IT maturity, and staffing capability. The level of implementation of these frameworks will also vary by organization.
COBIT 2019®
COBIT (Control Objectives for Information and Related Technology) is a process-based IT governance framework that represents a consensus of experts worldwide. It was codeveloped by the IT Governance Institute and ISACA. COBIT addresses business risks, control requirements, compliance, and technical issues.23 The latest version is COBIT 2019.24 Some changes and updates include:
- New concepts are introduced and terminology is explained—the COBIT Core Model and its 40 governance and management objectives provide the platform for establishing your governance program
- The performance management system is updated and allows the flexibility to use maturity measurements as well as capability measurements
- Introductions to design factors and focus areas offer additional practical guidance on flexible adoption of COBIT 2019, whether for specific projects or full implementation.25
COBIT offers IT controls that:
- Cut IT risks while gaining business value from IT under an umbrella of a globally accepted framework.
- Assist in meeting regulatory compliance requirements.
- Utilize a structured approach for improved reporting and management decision making.
- Provide solutions to control assessments and project implementations to improve IT and information asset control.
COBIT consists of detailed descriptions of processes required in IT and tools to measure progress toward maturity of the IT governance program. It is industry agnostic and can be applied across all vertical industry sectors, and it continues to be revised and refined.26
COBIT is broken into three basic organizational levels and their responsibilities: (1) board of directors and executive management; (2) IT and business management; and (3) line-level governance, security, and control knowledge workers.
The COBIT model draws on the traditional “plan, build, run, monitor” paradigm of traditional IT management, only with variations in semantics. There are four IT domains in the COBIT framework, which contain 40 governance and management objectives for IT processes and also control objectives that map to the four specific IT processes of:
- Plan and organize
- Acquire and implement
- Deliver and support
- Monitor and evaluate
Specific goals and metrics are assigned, and responsibilities and accountabilities are delineated.
The COBIT framework maps to ISO 17799 of the International Organization for Standardization and is compatible with Information Technology Infrastructure Library (ITIL) and other accepted practices in IT development and operations.
ValIT®
ValIT is a newer value-oriented framework that is compatible with and complementary to COBIT. Its principles and best practices focus is on leveraging IT investments to gain maximum value. Forty key ValIT essential management practices (analogous to COBIT's control objectives) support three main processes: value governance, portfolio management, and investment management. ValIT and COBIT “provide a full framework and supporting tool set” to help managers develop policies to manage business risks and deliver business value while addressing technical issues and meeting control objectives in a structured, methodic way.”
ITIL
ITIL is a set of process-oriented best practices and guidance originally developed in the United Kingdom to standardize delivery of IT service management. ITIL is applicable to both the private and public sectors and is the “most widely accepted approach to IT service management in the world.”27 As with other IT governance frameworks, ITIL provides essential guidance for delivering business value through IT, and it “provides guidance to organizations on how to use IT as a tool to facilitate business change, transformation and growth.”28
ITIL best practices form the foundation for ISO/IEC 20000 (previously BS 15000), the International Service Management Standard for organizational certification and compliance.29 ITIL 2011 is the latest revision (as of this writing). It consists of five core published volumes that map the IT service cycle in a systematic way:
- ITIL Service Strategy
- ITIL Service Design
- ITIL Service Transition
- ITIL Service Operation
- ITIL Continual Service Improvement
ISO 38500
ISO/IEC 38500:2015 is an international standard that provides high-level principles and guidance for senior executives and directors, and those advising them, for the effective and efficient use of IT.30 Based primarily on AS 8015, the Australian IT governance standard, it “applies to the governance of management processes” performed at the IT service level, but the guidance assists executives in monitoring IT and ethically discharging their duties with respect to legal and regulatory compliance of IT activities.
The ISO 38500 standard comprises three main sections:
- Scope, Application and Objectives
- Framework for Good Corporate Governance of IT
- Guidance for Corporate Governance of IT
It is largely derived from AS 8015, the guiding principles of which were:
- Establish responsibilities
- Plan to best support the organization
- Acquire validly
- Ensure performance when required
- Ensure conformance with rules
- Ensure respect for human factors
The standard also has relationships with other major ISO standards, and embraces the same methods and approaches.31
IG Best Practices for Database Security and Compliance
Although security is a topic primarily for Chapter 11, it is a technical topic that we address here as well. Best practices have been developed over the past few years and can prevent leakage of structured data from databases and Web services due to SQL injections (where hackers attack SQL databases) and other types of attacks.
An organization and its data need to be connected to its stakeholders—employees, customers, suppliers, and strategic partners. In this interconnected world that keeps expanding (e.g. cloud, mobile devices), proprietary data is exposed to a variety of threats. It is critical to protect the sensitive information assets that reside in your databases.32
Perimeter security often is easily penetrated. Web apps are vulnerable to attacks such as SQL injection (a favorite among malicious approaches). Hackers also can gain access by spear phishing (very specific phishing attacks that include personal information) to glean employee login credentials in order to get access to databases.
Streamlining your approach to database security by implementing a uniform set of policies and processes helps in compliance efforts and reduces costs. Here are some proven database security best practices:33
- Inventory and document. You must first identify where your sensitive data and databases reside in order to secure them. So a discovery and mapping process must take place. You can begin with staff interviews but also use tools such as data loss prevention (DLP) to map out data flows. Include all locations, including legacy applications, and intellectual property such as price lists, marketing and strategic plans, product designs, and the like. This inventorying/discovery process must be done on a regular basis with the assistance of automated tools, since the location of data can migrate and change.
- Assess exposure/weaknesses. Look for security holes, missing updates and patches, and any irregularities on a regular basis, using standard checklists such as the CIS Database Server Benchmarks and the DISA Security Technical Implementation Guides (STIGs). Do not forget to check OS-level parameters such as file privileges for database configuration files and database configuration options such as roles and permissions, or how many failed logins result in a locked account. (These types of database-specific checks are typically not performed by network vulnerability assessment scanners.)
- Shore up the database. Based on your evaluation of potential vulnerabilities, take proper steps and also be sure to that used database functions are disabled.
- Monitor. On a regular basis, monitor and document any configuration changes, and make sure the “gold” configuration is stable and unchanged. “Use change auditing tools that compare configuration snapshots and immediately alert whenever a change is made that affects your security posture.”
- Deploy monitoring/auditing tools. Deploy these tools to immediately detect intrusions or suspicious activity, use your database's database activity monitoring (DAM) and database auditing tools continuously and in real time. Note any anomalies, such as unusually large numbers of records being downloaded even by authorized users—this could indicate, for instance, a rogue employee gathering information. But also higher-level “privileged users—such as database administrators (DBAs), developers, and outsourced personnel” must be monitored to comply with certain regulations. Watch for attackers who have gained access through authorized credentials. DAM creates an audit trail generated in real time that can be the forensic smoking gun in investigations after attacks have occurred. Also, monitor the application layer, as well-designed DAM solutions associate specific database transactions performed by the application with specific end-user IDs, in order to deterministically identify individuals violating corporate policies. In addition, combining database auditing information with OS [operating system] and network logs via a security information and event management … system to see everything that a user has done can also provide critical information for forensic investigations.
- Verify privileged access. In your audit process, periodically review the list of privileged users and entitlement reports to ensure that superusers and those with access to sensitive information are still authorized.
- Protect sensitive data. Known sensitive data should be encrypted, so that even if attackers gain access, it is unreadable. “File-level encryption at the OS layer, combined with granular real-time monitoring and access control at the database layer, is typically accepted as a practical alternative to column-level encryption and a compensating control for Requirement 3.3 of PCI-DSS.”
- Deploy masking. Hide your live production data by masking test data. “Masking is a key database security technology that de-identifies live production data, replacing it with realistic but fictional data that can then be used for testing, training and development purposes, because it is contextually appropriate to the production data it has replaced.”
- Integrate and automate standardized security processes. To pass compliance audits, you need to show that processes and system are in place to reduce risks and detect potential intrusions, attacks, and unauthorized use. Standardizing and automating these tasks as much as possible help minimize compliance costs while protecting the organization's data.
Implementing these best practices will help keep sensitive data in your databases secure.
Tying It All Together
Multiple frameworks and standards can be applied to the IT process to more effectively govern it and focus the processes on business impact. Beginning with a robust data governance program, organizations can ensure, at the more fundamental level, that the information they are using to base decisions on is clean, reliable, and accurate. Implementing an MDM program will help larger organizations with complex IT operations ensure that they are working with consistent data from a single source. Implementing the COBIT 5 business framework for delivering IT results will help support a more efficient IT operation and include other major frameworks, standards, and best practices. Leveraging the use of the ISO 38500 standard will help senior executives to better manage and govern IT operations, and employing database security best practices will help guard against outside threats.
Notes
- 1. “Gartner Says Master Data Management Is Critical to Achieving Effective Information Governance,” January 19, 2012,www.gartner.com/newsroom/id/1898914.
- 2. IBM, “Selling Information Governance to Business Leaders,” https://www.information-management.com/news/selling-information-governance-to-business-leaders (accessed December 13, 2018).
- 3. Ibid.
- 4. Ibid.
- 5. Steven Adler, “Six Steps to Data Governance Success,” May 31, 2007, https://www.cio.com/article/2438861/enterprise-architecture/six-steps-to-data-governance-success.html.
- 6. “New Trends and Best Practices for Data Governance Success,” SeachDataManagement.com e-book, http://viewer.media.bitpipe.com/1216309501_94/1288990195_946/Talend_sDM_SO_32247_EBook_1104.pdf (accessed December 12, 2018).
- 7. Ibid.
- 8. “The DGI Data Governance Framework,” DataGovernance.com, www.datagovernance.com/the-dgi-framework/ (accessed December 13, 2018).
- 9. “Information Management,” BusinessDictionary.com, www.businessdictionary.com/definition/information-management.html (accessed December 13, 2018).
- 10. Sunil Soares, Selling Information Governance to the Business (Ketcham, ID: MC Press, 2011), 4.
- 11. Andrew White, “We Are Only Half Pregnant with MDM,” April 17, 2013, https://blogs.gartner.com/andrew_white/2013/04/17/we-are-only-half-pregnant-with-master-data-management/.
- 12. Gartner IT Glossary, “Master Data Management,” https://www.gartner.com/it-glossary/master-data-management-mdm (accessed December 13, 2018).
- 13. Bill Tolson, “Information Governance 101,” May 21, 2013, https://informationgovernance101.com/2013/05/21/the-lifecycle-of-information/.
- 14. Gartner IT Glossary, “Information Lifecycle Management,” www.gartner.com/it-glossary/information-life-cycle-management-ilm (accessed December 13, 2018).
- 15. Soares, Selling Information Governance to the Business.
- 16. “Data Architecture,” BusinessDictionary.com, www.businessdictionary.com/definition/data-architecture.html (accessed December 13, 2018).
- 17. “Data Modeling,” http://searchdatamanagement.techtarget.com/definition/data-modeling (accessed December 13, 2018).
- 18. Ibid.
- 19. Soares, Selling Information Governance to the Business.
- 20. Ibid.
- 21. Malcolm Chisholm, “Master Data Versus Reference Data,” Information Management, April 1, 2006, https://www.information-management.com/news/master-data-versus-reference-data.
- 22. M. N. Kooper, R. Maes, and E.E.O. Roos Lindgreen, “On the Governance of Information: Introducing a New Concept of Governance to Support the Management of Information,” International Journal of Information Management 31 (2011): 195–200, https://www.sciencedirect.com/science/article/pii/S0268401210000708.
- 23. Bryn Phillips, “IT Governance for CEOs and Members of the Board,” 2012, p. 26.
- 24. www.isaca.org/cobit/pages/default.aspx (accessed December 12, 2018).
- 25. “COBIT 2019 Framework: Introduction and Methodology,” www.isaca.org/COBIT/Pages/COBIT-2019-Framework-Introduction-and-Methodology.aspx (accessed December 12, 2018).
- 26. Phillips, “IT Governance for CEOs and Members of the Board.”
- 27. ITIL, “Welcome to the Official ITIL® Website,” https://www.axelos.com/best-practice-solutions/itil (accessed December 13, 2018).
- 28. ITIL, “What Is ITIL?” https://www.axelos.com/best-practice-solutions/itil/what-is-itil (accessed December 13, 2018).
- 29. Ibid.
- 30. ISO, “ISO/IEC 38500:2015: Governance of IT for the Organization,” https://www.iso.org/standard/62816.html (accessed December 12, 2018).
- 31. “ISO 38500 IT Governance Standard” (2008), www.38500.org/ (accessed December 13, 2018).
- 32. The following discussion and quotes are from Phil Neray, “Beating the Breach: 10 Best Practices for Database Security and Compliance,” November 3, 2011, https://datasafestorage.wordpress.com/2011/11/15/beating-the-breach-10-best-practices-for-database-security-and-compliance/.
- 33. Ibid.
