CHAPTER 11
Information Governance and Privacy and Security Functions*
Privacy and security go hand in hand. Privacy cannot be protected without implementing proper security controls and technologies. Organizations must not only make reasonable efforts to protect privacy of data, but they must go much further as privacy breaches are damaging to customers and reputation. Potentially, they could put companies out of business.
Privacy and data protection awareness skyrocketed in 2018 with the implementation of the EU General Data Protection Regulation (GDPR), which gave new privacy rights to individuals in the EU and EU citizens everywhere, while creating significant new regulatory burdens on companies that handle personal data (PD), personally identifiable information (PII), and protected health information (PHI). Major corporations, after decades of automation, suddenly were being held to account for all instances and uses of personal consumer data. To do so, data maps and information flow diagrams had to be created to inventory all instances of stored personal data and learn how it flows through the organization.
This inventorying step is often one of the first in launching information governance (IG) programs, so the trend provided a significant increase in support for formal IG programs.
Information Privacy
By Andrew Ysasi
In a 2018 survey, Americans stated that they were more concerned with privacy than with healthcare or economic growth.1 Privacy came of age in 2018, when the EU GDPR went into effect. Its impact was felt across the globe, as citizens became more aware of privacy concerns.
Information privacy refers to individuals or corporations controlling what others know about them. Unlike information security, privacy is not objective, but subjective. What one believes needs to be private can vary. (Some think that privacy is a moral or legal right, while others have argued that privacy isn't about controlling information about oneself.)2 Privacy has been a widespread debate for the past century, and as the Internet has become engrained in societies and cultures, it will continue to be a concern for individuals and organizations.3 In the United States, personally identifiable information (PII) is used to determine privacy attributes, for example, last name, home address, place of birth, and so forth. Often, PII is referred to as information that is not publicly available or in public works.4
In the digital age, individuals who are concerned about their privacy are often at the mercy of the corporations and developers of software to control how an individual's information is used. Individuals often use apps to work, manage finances, socialize, and play games on smartphones or tablets. The apps on portable devices often require permission from the user to use the information to operate at their full potential. As a result, individuals permit the organizations that manage the apps to store passwords, credit card information, bank accounts, digital cookies, fingerprints, and a myriad of personal information. If apps or software have privacy controls, an individual may choose to restrict what information is stored, how it is used, and who their information can be shared with. In extreme cases, individuals may opt to share personal information on social media sites with little regard for their privacy. Facebook, Twitter, Tinder, Foursquare, and LinkedIn are some examples of social media where individuals may reveal a great deal of personal information.5
Organizations should have an interest in privacy. Whether consumers or employees demand privacy or privacy is regulated in the countries they operate is something an organization should understand and have plans to address. Many organizations have a responsibility to their shareholders to be profitable or, if not an entity to gain profit, ensure that they are meeting their mission within the guidelines of their corporate structure. Privacy concerns can have a direct impact on an organization. Organizations that are more driven by profits may have fewer privacy concerns or controls than organizations that provide significant privacy protection.6
Further, organizations may operate in jurisdictions or industries where there are laws or rules around privacy. For example, organizations should determine if they operate in an “opt-in” or “opt-out” jurisdiction, or if they are required to protect information because they operate in the healthcare or financial industries. Opt-in climates typically favor the privacy of the individual whereas opt-out favor an organization. Hospitals and insurance companies usually have laws and rules they need to follow to protect PII (personally identifiable information) or PHI (protected health information). Laws and regulations define what constitutes as PII and provide further guidance on how the information should be handled.
Criminals often target organizations to gain access to private information to sell or disrupt the organization. A database of privacy data breaches can be found at privacyrights.org. Privacyrights.org reports over 11.5 billion records have been breached from over 9000 breaches since 2005.7 As data breaches become more prevalent, governments and privacy professionals have advocated for strict laws to protect individuals. Scholars believe that net neutrality, the Internet of Things (IoT), the human genome (medical), and cryptocurrencies will impact privacy for individual and organizations throughout the next decade.8
Generally Accepted Privacy Principles
The Generally Accepted Privacy Principles (GAPP) can be used to guide privacy programs. Please see Chapter 3 for more detail.
Privacy Policies
Privacy policies are ways for organizations to explain what they do with PII. Privacy policies may be found on websites or may be used internally only at an organization. Researchers predict that organizations will have tools available for individuals to choose how their information is used via privacy policies.9 The International Association of Privacy Professionals (IAPP) has provided a template for organizations,10 and it includes the following:
- Why the policy exists—to comply with a law or protection from a data breach.
- Data protection laws—specific examples of laws the organization is subject to follow.
- Policy scope—who the policy applies to, employees, contractors, vendors, and individual.
- Data protection risks—identifying to users what could happen if private information is provided.
- Responsibilities—an explanation of what the organization is responsible to protect, who or whom is ultimately is responsible (e.g. board of directors, data protection officer, privacy officer, IT manager, marketing manager) and what will be done to protect information.
- Guidelines for staff—not sharing information, using a strong password, not sharing credentials, not disclosing information unnecessarily.
- Data storage—how information is stored and where it may be stored.
- Data use—why information is needed for businesses and what is done to the information.
- Data accuracy—that data collected is accurate, updated when wrong, and a way for individuals to report inaccurate information.
- Subject access requests—how individuals can determine what is collected about them and how they can retrieve or edit the information.
- Disclosure—the possibility of disclosing information to authorities or for legal reasons.
- Providing information—clarification on how an individual's information is being processed and what their rights are.11
The IAPP has a privacy policy version that includes the European Union's GDPR provisions for organizations that must comply with the GDPR privacy requirements that can be found at the same site as the template outlined above.
Privacy Notices
Privacy notices are typically exclusive to external facing stakeholders or to the public, where privacy policy could be both.12 The Better Business Bureau in the United States advises that a privacy notice should include five elements:
- Notice (what personal information is being collected on the site or by the organization)
- Choice (what options the customer has about how/whether personal data is collected and used)
- Access (how a customer can see what data has been collected and change/correct it if necessary)
- Security (state how any data that is collected is stored/protected)
- Redress (what customer can do if the privacy policy is not met)
Fair Information Practices (FIPS)
HEW Report
“The first steps toward formally codifying Fair Information Practices began in July 1973, when an advisory committee of the US Department of Health, Education and Welfare proposed a set of information practices to address a lack of protection under the law at that time.”13
As a result of this group, the HEW report was created formerly known as the Records, Computers and the Rights of Citizens. The HEW report summarized fair information practices as:
- There must be no personal data recordkeeping systems whose very existence is secret.
- There must be a way for an individual to find out what information about him is in a record and how it is used.
- There must be a way for an individual to prevent information about him obtained for one purpose from being used or made available for other purposes without his consent.
- There must be a way for an individual to correct or amend a record of identifiable information about him.
- Any organization creating, maintaining, using, or disseminating records of identifiable personal data must assure the reliability of the data for their intended use and must take reasonable precautions to prevent misuse of the data.14
OCED Privacy Principles
In 1980, the Organisation for Economic Co-operation and Development (OECD) published guidelines on the protection of privacy and personal data and were recently updated in 2013.15 The eight fair information principles outlined by the OECD are as follows.
Collection Limitation Principle
There should be limits to the collection of personal data, and any such data should be obtained by lawful and fair means and, where appropriate, with the knowledge or consent of the data subject.
Data Quality Principle
Personal data should be relevant to the purposes for which they are to be used, and, to the extent necessary for those purposes, should be accurate, complete, and kept up to date.
Purpose Specification Principle
The purposes for which personal data are collected should be specified not later than at the time of data collection, and the subsequent use limited to the fulfillment of those purposes or such others as are not incompatible with those purposes and as are specified on each occasion of change of purpose.
Use Limitation Principle
Personal data should not be disclosed, made available, or otherwise used for purposes other than those specified in accordance with Paragraph 9 except:
- With the consent of the data subject; or
- By the authority of law.
Security Safeguards Principle
Personal data should be protected by reasonable security safeguards against such risks as loss or unauthorized access, destruction, use, modification, or disclosure of data.
Openness Principle
There should be a general policy of openness about developments, practices, and policies concerning personal data. Means should be readily available for establishing the existence and nature of personal data, and the main purposes of their use, as well as the identity and usual residence of the data controller.
Individual Participation Principle
An individual should have the right:
- To obtain from a data controller, or otherwise, confirmation of whether or not the data controller has data relating to him;
- To have communicated to him, data relating to him within a reasonable time;
at a charge, if any, that is not excessive;
in a reasonable manner; and
in a form that is readily intelligible to him;
- To be given reasons if a request made under subparagraphs (a) and (b) is denied, and to be able to challenge such denial; and
- To challenge data relating to him and, if the challenge is successful to have the data erased, rectified, completed, or amended.
Accountability Principle
A data controller should be accountable for complying with measures which give effect to the principles stated above.
Madrid Resolution 2009
In 2009, the Madrid Resolution brought 50 countries together to provide further guidance on information privacy. The resolution was designed and signed by executives from 10 international organizations, and one of the most important recommendations is governments “promoting better compliance with the applicable laws regarding data protection matters.”16
While the Madrid Resolution was a big step in achieving global privacy awareness and guidance, it was merely viewed as a starting point for addressing the dynamic landscape of personal privacy across the globe. In 2010, the United States Department of Health Services Privacy Office stated an opinion on the Madrid Resolution, specifically criticizing the fact that governments and regulatory authorities were not included, and recommending that all stakeholders be involved in the development of a global privacy framework.17 It is also worth noting the Director of the Spain Data Protection Agency (AEPD), Artemi Rallo: “These standards are a proposal of international minimums, which include a set of principles and rights that will allow the achievement of a greater degree of international consensus and that will serve as reference for those countries that do not have a legal and institutional structure for data protection.”18 It appeared in 2010 that a global privacy framework was on the horizon.
EU General Data Protection Regulation
The European Union's Data Protection Regulation (GDPR) provided the most significant privacy framework, policy, and regulatory overhaul history.
“In 2016, the EU adopted the General Data Protection Regulation (GDPR), one of its greatest achievements in recent years. It replaces the 1995 Data Protection Directive which was adopted at a time when the Internet was in its infancy.”19
Compliance for GDPR and enforceability requirements went into effect on May 28, 2018, and required organizations to seek consent from individuals before collecting their personal information.20 Further, GDPR requires organizations to assign a Data Controller and provides specific principles related to the processing of personal data found in article 5:
Personal data shall be:
- Processed lawfully, fairly and in a transparent manner in relation to the data subject (“lawfulness, fairness and transparency”);
- Collected for specified, explicit and legitimate purposes and not further processed in a manner that is incompatible with those purposes; further processing for archiving purposes in the public interest, scientific, or historical research purposes or statistical purposes shall, in accordance with Article 89(1), not be considered to be incompatible with the initial purposes (“purpose limitation”);
- Adequate, relevant, and limited to what is necessary in relation to the purposes for which they are processed (“data minimization”);
- Accurate and, where necessary, kept up to date; every reasonable step must be taken to ensure that personal data that are inaccurate, having regard to the purposes for which they are processed, are erased or rectified without delay (“accuracy”);
- Kept in a form which permits identification of data subjects for no longer than is necessary for the purposes for which the personal data are processed; personal data may be stored for longer periods insofar as the personal data will be processed solely for archiving purposes in the public interest, scientific or historical research purposes or statistical purposes in accordance with Article 89(1) subject to implementation of the appropriate technical and organisational measures required by this Regulation in order to safeguard the rights and freedoms of the data subject (“storage limitation”);
- Processed in a manner that ensures appropriate security of the personal data, including protection against unauthorized or unlawful processing and against accidental loss, destruction or damage, using appropriate technical or organizational measures (“integrity and confidentiality”).21
Failure to comply with GDPR requirements comes with hefty penalties. Fines are not assessed without an investigation and guidance. GDPR outlines the 10 criteria to determine the amount an organization can be fined:
- Nature of infringement: The number of people affected, damage they suffered, duration of infringement, and purpose of processing.
- Intention: Whether the infringement is intentional or negligent.
- Mitigation: Actions taken to mitigate damage to data subjects.
- Preventative measures: How much technical and organizational preparation the firm had previously implemented to prevent noncompliance.
- History: Past relevant infringements, which may be interpreted to include infringements under the Data Protection Directive and not just the GDPR, and past administrative corrective actions under the GDPR, from warnings to bans on processing and fines.
- Cooperation: How cooperative the firm has been with the supervisory authority to remedy the infringement.
- Data type:: What types of data the infringement impacts.
- Notification: Whether the infringement was proactively reported to the supervisory authority by the firm itself or a third party.
- Certification: Whether the firm had qualified under approved certifications or adhered to approved codes of conduct.
- Other: Other aggravating or mitigating factors may include the financial impact on the firm from the infringement.22
Lower-level fines can be up to €10 million, or 2% of the worldwide annual revenue of the prior fiscal year, whichever is higher. Higher-level fines can be up to €20 million, or 4% of the worldwide annual revenue of the prior fiscal year, whichever is higher.23 The EU is quite evident through GDPR that consumer privacy is of the utmost importance, and organizations that choose to mishandle the data of EU citizens will suffer substantial financial losses. On the day that organizations were required to be compliant, Facebook and Google were hit with over $8 billion in lawsuits.24 Facebook and other large companies seem to be making strides to comply, but other organizations are trying to block EU citizens from their sites to mitigate risk.25 GDPR provides comprehensive oversight and guidance on how to protect consumer information and what happens if an organization does not comply. However, it is yet to be determined if GDPR will provide adequate privacy protection of consumer data without hindering EU citizens from experience foreign sites or companies wishing to expand their market in the EU.
GDPR: A Look at Its First Year
By Mark Driskill
The EU implemented sweeping new data privacy and protection laws meant to protect the personal data (PD) of those in the EU—importantly—be they citizens, temporary residents or visitors, from unauthorized use, and, extraterritorially, wherever in the world their personal data is stored or used.
The issues stem from the EU's broad definition of PD and the long history in Europe of privacy being viewed as a fundamental human right, against too much history of dictatorships and fascist control. The EU's General Data Protection Regulation (GDPR) took effect, provoking a new era of tech-company corporate accountability.
The GDPR didn't just standardize data privacy and protection across all (current) 28 member states of Europe, but refined both how to seek permission to use personal data and refresh the personal rights of each person in the EU to view and take control of their own personal data.
As 2018 came to a close, it was revealed that some major tech companies use personal data in ways that violate personal privacy in many ways.
Large data handlers like Facebook, Google, and Amazon have come under close examination by EU regulators, forcing CEOs in the “personal surveillance data business” to defend, and even rethink, their business models (e.g. Google then cited privacy regulation as a major threat to their business model in corporate documents). These have included both Privacy Regulators around GDPR (e.g. UK ICO, Ireland DPC, etc.) and EU competition regulators. Under the new GDPR these companies, without exception, must follow EU privacy law. The issues rest primarily with the advertising data insights these companies have created using proprietary algorithms. The invasiveness is secretive and at times unsettling, as these companies seem to know when someone will buy a pair of socks!
At first glance, it might seem as if the first year of GDPR compliance was largely uneventful, at least in terms of other leading global news stories. It's really a journey, as the EU regulators and analysts have shared. With almost 95,000 privacy complaints filed, they have only just started to process those investigations, findings, and enforcements. So many of the “privacy fines” we've seen since GDPR went live were really cases that occurred pre-GDPR and were thus much smaller in scope and penalties under the prior EU privacy regulation. What has been happening quietly, almost behind the scenes, is a tacit acceptance that data privacy from the person-centered perspective must begin with forcing larger companies such as Facebook, Google, and Amazon to comply. This hangs over companies in the consumer tech sector like thick fog. American businesses and culture do not like anyone telling them how to run things. Apparently, this is also true for GDPR compliance, adding to a persistent lack of full compliance.
A December 2018 Forrester survey commissioned by Microsoft found that more than half of businesses failed to meet GDPR compliance checkpoints.26 Other highlights included:
- 57% instituted “privacy by design.”
- 59% “collected evidence of having addressed GDPR compliance risks.”
- 57% “trained business personnel on GDPR requirements.”
- 62% “vetted third-party vendors.”
This last item is perhaps the most troubling: 38% have yet to vet their third-party software vendors. This means that a significant portion of the global economy is not meeting GDPR compliance. The Forrester survey's primary findings were that only 11% of global companies are prepared to undergo the type of digital transformation needed to fully comply with GDPR-based privacy needs of citizens. In its entirety, GDPR has yet to make a significant impact, at least one beyond large tech company compliance.
A key implied issue that ultimately influences GDPR compliance checkpoints is the balance between intrusion into a company's business practices and its ability for profitmaking. Industry leaders note that in order to truly protect personal data, you must know exactly where and whose it is. This necessarily requires intrusion.
Enforcement and Precedent Setting
With the new GDPR mandate in place, EU member countries have a valuable tool for ensuring compliance even as these companies undertake actions to protect their business models. Ireland, for example, has “opened 10 statutory inquiries into Facebook and other Facebook-owned platforms in the first seven months” since GDPR was adopted in May 2018.27
The Irish Data Protection Commission (DPC) commissioner Helen Dixon notes that the inquiries match the public's interest in “understanding and controlling” their own personal data. The Irish DPC fully intends that these be precedent-setting. Given the widespread global use of Facebook and its plethora of connected apps, such inquiries from other EU member countries cannot be far behind.
In perhaps the most egregious case yet, a whistleblower forced Facebook to reveal that “as many as 600 million users’ passwords were stored in plain text and accessible to 20,000 employees, of which 2000 made more than 9 million searches that accessed the passwords going back to 2012.”28 Added to this blatant breach of basic cybersecurity practices is the fact that Facebook knew about the issue back in January and spent several months trying to keep it from the public.29 They would surely have been embarrassing questions to answer during the recent US Congressional hearings.
As Forbes points out, cybersecurity at Facebook just might be obsolete. In the wake of the sensational stories regarding recent Russian interference into American elections, “Facebook did not conduct a top-down security audit of its authentication systems.” This is a profound, if not provocative, revelation, particularly given Mark Zuckerberg's promise to reform Facebook's business practices.
That promise, made to Congress just prior to GDPR's May 2018 rollout, seems now to be empty. While Zuckerberg testified, his company continued its intrusive practices, even as he tried to simplify for legislators Facebook's business practices.
In the business world, laws and regulations are street signs to setting precedent. During this initial phase of GDPR compliance, it is crucial that leading EU countries, such as Germany, take positions of authority. Germany's Federal Cartel Office, the federal agency that regulates Germany's competition laws, set a new precedent in a February 2019 court ruling. In an anti-competition class-action case, the German court severely limited Facebook's ability to collect user data inside Germany. This essentially walls off Germany's Facebook users from the rest of Facebook's user base. The precedent set by German regulators was substantial. Facebook (at least in Germany) can longer use tactics such as using user data to make fictitious profiles. Moreover, it can no longer use Facebook Pixel, a single character imbedded in a page that transmits data back to the company's servers. With the German precedent, Facebook can no longer claim that what it does with user data on its platform is proprietary.
In some ways, the first year of “GDPR-live” was marked by both confusion and denial that such regulation was really needed. Today, the establishment of a nation-specific precedent is the exception, not the rule. However, enough cannot be said about the fact that Germany is one of the main economic powers of the globe. Without German leadership, GDPR might die an unceremonious death. The same must happen in other countries involved in setting global economic policy.
In short, GDPR-style privacy must come to the United States. Thankfully, California is leading the way with its California Consumer Privacy Act (CCPA), which went live in January 2020.
Privacy Programs
Privacy programs are often required to manage the national and international requirements to protect consumer information. The IAPP has a rigorous certification called the Certified Information Privacy Manager (CIPM), and the outline30 for the exam provides a framework to build a privacy program.
- Vision—The purpose of the privacy program and what the program will achieve.
- Team—Key stakeholders who have direct responsibility for privacy matters that may include a Chief Privacy Officer (CPO), Data Protection Officer (DPO), Data Controller (DC), executive sponsorship, inside or outside legal counsel, technology leadership, compliance leadership, and records and information leadership.
- Policies—Privacy policies for websites, social media, e-mail, mobile apps, internal practices, and privacy policies addressing applicable international, national, and local laws should be reviewed and examined.
- Activities—Examples of activities are training, awareness, updating agreements with key stakeholders, addressing cross-border concerns, reviewing insurance and assurance options, evaluating privacy compliance software tools, and conducting privacy impact assessments along with specific risk assessments that relate to privacy concerns or regulations.
- Metrics—Collection, responses time to inquiries, retention, PIA metrics, maturity levels, and resource utilization are some examples of how organizations can measure privacy.
Privacy in the United States
FCRA
Privacy in the United States has a fairly recent history. In 1970, the Fair Credit Reporting Act (FCRA) was placed into law to protect consumers. With the FCRA, consumers were able to correct errors on their credit report.31 FCRA was amended in 1996 and again in 2003 by the Fair and Accurate Credit Transaction Act that addresses issues related to identity theft. Under FCRA there are obligations users of credit reports must follow, which include:
- Users must have a permissible purpose—as in the uses of credit reports are limited.
- Users must provide certifications—they have a right to request the report.
- Users must notify consumers when adverse actions are taken—users must be notified if their credit was a result of something not occurring.
The Federal Trade Commission (FTC) provided updates to the FCRA on their website located at www.ftc.gov.32 Further, the FTC is the enforcement arm of FCRA and FACTA.
HIPAA
The Health Insurance Portability and Accountability Act (HIPAA) of 1996 was created to improve the delivery of healthcare services and to provide standards on how patient records are handled in data exchanges. HIPAA oversight is provided by the Department of Health and Human Services (DHHS) under the Office for Civil Rights (OCR).33 Entities covered under HIPAA are:
- Health care providers
- Health plans
- Health care clearinghouses
The entities were broken up into two Covered Entities (CE) and Business Associates (BA) and personal information they managed is referred to as Protected Health Information (PHI).
Protected health information is any individually identifiable health information transmitted or maintained in any form or medium, which is held by a covered entity or its business associate, identifies an individual or offers a reasonable basis for identification, is created or received by a covered entity or an employer, and relates to a past, present or future physical or mental condition, provision of health care or payment for health care to that individual.34
In 2000, HIPAA was amended to include the “Privacy Rule” that required:
- Privacy Notices
- Authorization of Uses and Disclosures
- Access and Accountings of Disclosures
- “Minimum Necessary” Use or Disclosure
- De-identification
- Safeguards
- Business Associates accountability
- Exceptions35
In 2003, HIPAA was amended further with the Security Rule, which focused on the protection of electronic medical records. It required covered entities to:
- Ensure confidentiality of electronic medical records
- Protect against any threats or hazards to the security or integrity of records
- Protect against any reasonably anticipated users or disclosures that are not permitted
- Ensure compliance with the Security Rule by the staff
- Identify an individual responsible for implementation and oversight of the Security Rule and compliance program
- Conduct an initial and ongoing risk assessments
- Implement a security awareness program
- Incorporate Security Rule requirements into Business Associate Contracts required by the Privacy Rule
In 2009, the Health Information Technology for Economic and Clinical Health (HITECH) Act was enacted as part of the American Recovery and Reinvestment Act of 2009 to promote the adoption and meaningful use of health information technology.36 Further, HITECH separated out four categories of how fines would be distributed, and another noteworthy change was the correction of a violation within 30 days.37 Below is the penalty structure for HIPAA violations:
- Category 1: A violation that the covered entity was unaware of and could not have realistically avoided, had a reasonable amount of care had been taken to abide by HIPAA Rules.
- Category 2: A violation that the covered entity should have been aware of but could not have avoided even with a reasonable amount of care (but falling short of willful neglect of HIPAA Rules).
- Category 3: A violation suffered as a direct result of “willful neglect” of HIPAA Rules, in cases where an attempt has been made to correct the violation.
- Category 4: A violation of HIPAA Rules constituting willful neglect, where no attempt has been made to correct the violation.38
Other US Regulations
The United States has scores of other regulations that have shaped the US privacy landscape:
The Graham-Leach-Bliley Act (GLBA) issued in 1999 prohibited the sale of detailed customer information to, for example, telemarketing firms. GLBA is enforced by the FTC and allows consumers to “opt out” of having their information shared with affiliates. Like HIPAA, GLBA has safeguards and requires administrative, technical, and physical security of consumer information as well as privacy notice requirements.
The Children's Online Privacy Protection Act of 2000 (COPPA) was the result of the FTC's 1998 Privacy Online: A Report to Congress.39 Privacy related to children in the United States was the primary focus of COPPA, and required website companies and other operaters to adhere to a set of requirements, including privacy notices, or be subject to fines.
Controlling the Assault of Non-Solicited Pornography and Marketing Act of 2003 (CAN-SPAM) applies to anyone who advertises products and services by e-mail generated in the United States.40 CAN-SPAM's aim is to reduce deceptive advertising by e-mail, include warnings for sexually explicit content, and the ability to opt-out from future e-mails. CAN-SPAM is governed by the FTC.
Certain states in the United States have taken action to protect the privacy of citizens.
Massachusetts rolled out 940 CMR 27.00: Safeguard of personal information in 201041 and the California Consumer Privacy Act in 2018, which will be enforceable in 2020,42 focus on privacy and security of citizen information as a result of ongoing data breaches. What information is collected, specifically by social media entities Facebook and Google, why it is collected, and obtaining personal information in usable formats are some highlights of the California law. The law also requires children under 16 to opt in to allowing companies to collect their information.43 Further, it is thought that future privacy laws from other states may modify their privacy laws to mirror California.
California Consumer Privacy Act
California's new privacy law went into effect on January 1, 2020. This act is designed to give California residents a better way to control and protect their personal information. California consumers will have the right to order companies to delete their personal data—similar to what Europe's all-encompassing GDPR regulation calls for (but not as strict). Many US states have begun debating new privacy laws using the CCPA and GDPR as models to protect the personal rights of individuals and consumers.44
Privacy regulations are rapidly spreading worldwide in countries such as India, Brazil, and Australia. Even the US Congress has been working on a bill that could soon become federal law.
California consumers will have the legal right to force companies to not only delete their personal information but also disclose what personally identifiable information (PII) has been collected about them, demand the reasons for collecting it, and order the companies to refrain from selling any of it. The personal information protected in these regulations contains a lot more than just financial or banking data; PII includes all “information that identifies, relates to, describes, is associated with, or could be reasonably linked, directly or indirectly, to a consumer or household.” This consists of many different types of information, including IP addresses, biometric data, personal characteristics, browsing history, geolocation data, and much more.
On June 28, 2018, the California Congress passed Assembly Bill 375, the CCPA. The act will apply to any “for-profit” organization that grosses at least $25 million annually and interacts with 50,000 or more Californians, or derives at least half of its annual revenue from selling personal information. Most importantly, the CCPA applies to businesses “regardless of location” that meet the above criteria. You must comply if you process personal information of Californians whether your corporation is located in California or not.
What was interesting is how the CCPA was rushed into law and signed by Governor Jerry Brown in June of 2018, just days before a deadline to withdraw a state ballot measure on a privacy proposition coming up in the November election. Tech companies like Google and Facebook were ready to fight against this voter initiative because it would have been more strict—holding them more accountable with more far-reaching rules and heavier fines. These same tech giants are currently lobbying congress in Washington, DC, to create new federal privacy laws. Not surprisingly, big tech companies are only looking out for themselves as they try to preserve their “surveillance” business model by watering down impending privacy legislation.
It is important to note that the CCPA has already been amended and politicians promise to make more changes before the CCPA goes into full effect in January 2020.
Privacy in Asia
The Asia-Pacific region is no stranger to privacy concerns. The Asia-Pacific Economic Cooperation (APEC) endorsed the 1998 Blueprint for Action on Electronic Commerce that discussed the creation of a fair and open digital economy that promoted confidence and trust with consumers. In 2005, APEC published their privacy principles that included:
- Preventing harm
- Notice
- Collection limitations
- Uses of personal information choice
- Integrity of personal information
- Security safeguards
- Access and correction
- Accountability45
In 2015, APEC added the principle of Choice, which emphasized that individuals should have a choice in how their information is used.46 The APEC privacy framework also provides implementation guidelines to guide organizations of all types on how to implement the privacy framework.
Infonomics and Privacy
Doug Laney explored a concept known as infonomics in his seminal 2018 book that discussed how organizations could monetize, manage, and measure information as an asset.47 While the use of internal or consumer data raises privacy concerns, Laney suggests viewing data as an asset and working within the privacy and legal parameters to maximize the value of information. Sometimes this may involve spinning off a new legal entity to provide some distance between the parent company and a data monetization venture, for legal and branding purposes. Laney's book discusses how information is used to generate new revenue for marketing purposes, providing access to third parties and streamlining operations. While these concepts may go against general privacy principles, it is possible to navigate privacy concerns with Laney's ideas. He provides “Seven Steps to Monetizing Your Information Assets,” and goes on to explain how to report your information assets on your balance sheets, and provides formulas. While doing so, it is essential to understand the impact of privacy risks associated with monetizing information.
Privacy Laws
The protection of personally identifiable information (PII) is a core focus of IG efforts. PII is any information that can identify an individual, such as name, Social Security number, medical record number, credit card number, and so on. Various privacy laws have been enacted in an effort to protect privacy. You must consult your legal counsel to determine which laws and regulations apply to your organization and its data and documents.
The CCPA is waking up other US states to the need for more robust privacy legislation, while at the same time there is a move underfoot for the first national privacy legislation. If this goes forward, then there will be legal battles regarding preemption of the federal law in states having stricter privacy laws, using a “states’ rights” argument, and the federal government will argue that they have preemptive legal authority.
The Federal Wiretap Act “prohibits the unauthorized interception and disclosure of wire, oral, or electronic communications.” The Electronic Communications Privacy Act (ECPA) of 1986 amended the Federal Wiretap Act significantly and included specific on e-mail privacy.48 The Stored Communications and Transactional Records Act (SCTRA) was created as a part of ECPA and is “sometimes useful for protecting the privacy of e-mail and other Internet communications when discovery is sought.” The Computer Fraud and Abuse Act makes it a crime to intentionally breach a “protected computer” (one used by a financial institution or for interstate commerce).
Also relevant for public entities is the Freedom of Information Act, which allows US citizens to request government documents that have not previously been released, although sometimes sensitive information is redacted (blacked out) and specifies the steps for disclosure as well as the exemptions. In the United Kingdom, the Freedom of Information Act 2000 provides for similar disclosure requirements and mandatory steps.
In the United Kingdom, privacy laws and regulations include the following:
- Data Protection Act 1998
- Freedom of Information Act 2000
- Public Records Act 1958
- Common law duty of confidentiality
- Confidentiality National Health Service (NHS) Code of Practice
- NHS Care Record Guarantee for England
- Social Care Record Guarantee for England
- Information Security NHS Code of Practice
- Records Management NHS Code of Practice
Also, the international information security standard ISO/IEC 27002: 2005 comes into play when implementing security.
Cybersecurity
Breaches are increasingly being carried out by malicious attacks, but a significant source of breaches is internal mistakes caused by poor information governance (IG) practices, software bugs, and carelessness. The average cost of a data breach in 2018 was nearly $4 million,49 and some spectacular breaches have occurred, such as the 87 million–plus Facebook accounts and 37 million Panera accounts that were hacked in 2018,50 but perhaps the most colossal was the breach of over 500 million customer records, including credit card and passport numbers, suffered by the Marriott Hotel chain that same year.51 Millions of breaches occur each year: There were an estimated 179 million privacy breaches in the United States in 2017 alone.52
Cyberattacks Proliferate
Online attacks and snooping continue at an increasing rate. Organizations must be vigilant about securing their internal, confidential documents and e-mail messages. In one assessment, security experts at Intel/McAfee “discovered an unprecedented series of cyberattacks on the networks of 72 organizations globally, including the United Nations, governments and corporations, over a five-year period.”53 Dmitri Alperovitch of McAfee described the incident as “the biggest transfer of wealth in terms of intellectual property in history.”54 The level of intrusion is ominous.
The targeted victims included governments, including the United States, Canada, India, and others; corporations, including high-tech companies and defense contractors; the International Olympic Committee; and the United Nations. “In the case of the United Nations, the hackers broke into the computer system of its secretariat in Geneva, hid there for nearly two years, and quietly combed through reams of secret data, according to McAfee.”55 Attacks can be occurring in organizations for years before they are uncovered—if they are discovered at all. This means that an organization may be covertly monitored by criminals or competitors for extended periods of time.
And they are not the only ones spying—look no further than the US National Security Agency (NSA) scandal of 2013. With Edward Snowden's revelations, it is clear that governments are accessing, monitoring, and storing massive amounts of private data.
Where this stolen information is going and how it will be used is yet to be determined. But it is clear that possessing this competitive intelligence could give a government or company a huge advantage economically, competitively, diplomatically, and militarily.
The information assets of companies and government agencies are at risk globally. Some are invaded and eroded daily, without detection. The victims are losing economic advantage and national secrets to unscrupulous rivals, so it is imperative that IG policies are formed, followed, enforced, tested, and audited. It is also imperative to use the best available technology to counter or avoid such attacks.56
Insider Threat: Malicious or Not
Ibas, a global supplier of data recovery and computer forensics, conducted a survey of 400 business professionals about their attitudes toward intellectual property (IP) theft:
- Nearly 70% of employees have engaged in IP theft, taking corporate property upon (voluntary or involuntary) termination.
- Almost one-third have taken valuable customer contact information, databases, or other client data.
- Most employees send e-documents to their personal e-mail accounts when pilfering the information.
- Almost 60% of surveyed employees believe such actions are acceptable.
- Those who steal IP often feel that they are entitled to partial ownership rights, especially if they had a hand in creating the files.57
These survey statistics are alarming, and by all accounts the trend continuing to worsen today. Clearly, organizations have serious cultural challenges to combat prevailing attitudes toward IP theft. A strong and continuous program of IG aimed at securing confidential and sensitive information assets can educate employees, raise their IP security awareness, and train them on techniques to help secure valuable IP. And the change needs to be driven from the top: from the CEO and boardroom. However, the magnitude of the problem in any organization cannot be accurately known or measured. Without the necessary IG monitoring and enforcement tools, executives cannot know the extent of the erosion of information assets and the real cost in cash and intangible terms over the long term.
Countering the Insider Threat
Frequently ignored, the insider has increasingly become the main threat—more than the external threats outside of the perimeter. Insider threat breaches can be more costly than outsider breaches. Most of the insider incidents go unnoticed or unreported.58
Companies have been spending a lot of time and effort protecting their perimeters from outside attacks. In recent years, most companies have realized that the insider threat is something that needs to be taken more seriously.
Malicious Insider
Malicious insiders and saboteurs comprise a very small minority of employees. A disgruntled employee or sometimes an outright spy can cause a lot of damage. Malicious insiders have many methods at their disposal to harm the organization by destroying equipment, gaining unsanctioned access to IP, or removing sensitive information by USB drive, e-mail, or other methods.
Nonmalicious Insider
Fifty-eight percent of Wall Street workers say they would take data from their company if they were terminated, and believe they could get away with it, according to a recent survey by security firm CyberArk.59 Frequently, they do this without malice. The majority of users indicated having sent out documents accidentally via e-mail. So, clearly it is easy to leak documents without meaning to do any harm, and that is the cause of most leaks.
Solutions
Trust and regulation are not enough. In the case of a nonmalicious user, companies should invest in security, risk education, and Security Awareness Training (SAT). A solid IG program can reduce IP leaks through education, training, monitoring, and enforcement. SAT raises user awareness and can be gamified to increase engagement and effectiveness. Newer SAT programs utilize animated cartoon-like videos to keep users interested and engaged.
In the case of the malicious user, companies need to take a hard look and see whether they have any effective IG enforcement and document life cycle security (DLS) technology such as information rights management (IRM) in place. Most often, the answer is no.60
Information Security Assessments and Awareness Training
By Baird Brueseke
Employees’ human errors are the weakest link in securing an organization's confidential information. However, there are some small, inexpensive steps (through employee training) that can reduce information risk.
Security Awareness Training (SAT) programs educate an organization's workforce about the risks to information and potential schemes employed by hackers. SAT provides them with the skills to act consistently in a way that protects the organization's information assets. Bad actors target an employee's natural human tendencies with phishing e-mails and spear-phishing campaigns. SAT training programs often include phishing simulation and other social-engineering tactics such as text message “smishing” and unattended USB drives. SAT products provide a comprehensive approach to employee training, which empowers them to recognize and avoid a broad range of threat vectors.
SAT is an easy effective and easy way to reduce risk. Corporate risk is reduced by changing the (human) behavior of employees. Leading products in this market use innovative methods such as short, animated videos and pop quizzes to teach employees about information security threats.
SAT is not a one-and-done activity. In order to be effective, SAT must be implemented as an ongoing process. Workplace safety programs implemented to meet OSHA requirements serve as a good metaphor. SAT is a continuous improvement process; new threats emerge every day. The leading products incorporate new content on a regular basis and provide employee engagement opportunities that go well beyond the traditional computer-based training activities.
SAT Is a Quick Win for IG Programs
One of the quick—and low cost—wins that an Information Governance (IG) program can bring to an organization is the implementation of an SAT program. IG programs are implemented to reduce risk and maximize information value. Security Awareness Training programs are an excellent way to reduce risk and they are easy to implement. Employees have many bad habits that can leave a company vulnerable to data breach scenarios.
In response to the ever-increasing cyber security threat faced by business, a new subsegment of the Information Security market has emerged and matured in the last five years. The Security Awareness Training market grew 54% from 2015 to 2017. Projected revenues for 2018 were $400 million and growth was strong.
Cybersecurity threats are constantly evolving. One of the important things to understand when evaluating Security Awareness Training programs is the vendor's cycle for new content development and deployment in the training platform. Some of the features to look for and evaluate when selecting a SAT product are:
- Interactive content in varied formats designed to keep learners engaged
- Training designed to teach resistance to multiple forms of social engineering
- Optimization for smartphone and tablet usage
- Gamification and other methods to engage employees and increase participation
- Prestructured campaigns for different types/levels of employees
- Role-based training with optional customization based on corporate environment
- Robust library of existing content and flexible micro-learning topics
- Internal marketing and communication tools for use by the HR department
- Short lessons, approximately 5–10 minutes in length
- Integrated quizzes and metrics to track employee participation and retention
- Integration with corporate LMS
- Integration with end-point security systems
It is important to understand that SAT products typically include not only training, but also simulated attacks. Therefore, the way in which the SAT product interacts with existing cybersecurity defenses is a serious consideration. For example, if the training program administrator sends out a simulated phishing attack e-mail, that e-mail needs to make it through the SPAM filter and into the employee's e-mail inbox before the employee can be tempted into potentially clicking on the bad link.
In smaller companies, it may be sufficient to whitelist to the domain from which the phishing e-mail is being sent. In larger organizations that have Security Information Event Monitoring (SIEM) and other automated cyber defense systems, the company's IT/Security Team would likely request integration of a notification process for the simulated attack campaign in order to avoid a rash of false alarms from the security monitoring systems.
Security Awareness Training can provide a quick win for IG programs. The training immediately reduces risk. At the same time, management can point to the employee participation metrics as proof that proactive efforts are being made to enhance the organizations’ security posture.
Cybersecurity Assessments
In today's cyber threat landscape, companies have a fiduciary duty to assess their cyber security posture. This is the root function of a Cybersecurity Assessment. Typically, third-party vendors are contracted to perform the Assessment. These firms have expertise in a variety of cybersecurity skills that they use to tailor the engagement to a scope appropriate for the organization being assessed.
One of the first steps when starting a Cybersecurity Assessment project is to select a framework. This choice will become part of the project requirements and in large part define the scope of work to be performed by the third-party vendor. There are several frameworks to choose from including: ISO 27001, COBIT 2019, NIST Cybersecurity Framework, NIST 800-53, DOD 8570, DCID 6/3, HITRUST CSF, and the Cloud Security Alliance's Cloud Controls Matrix. Even the Motion Picture Association of America has defined a cybersecurity framework to protect their member's intellectual property.
The NIST Cybersecurity Framework consists of five “functions,” which are: Identify, Protect, Detect, Respond, and Recover, as shown in the following.
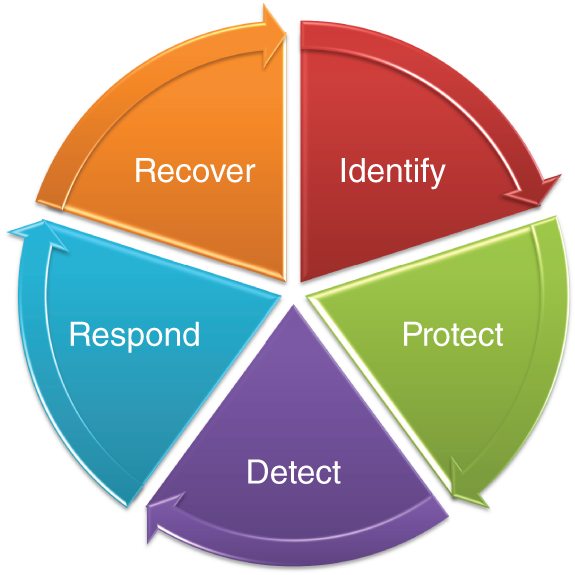
These five functions are subdivided into 22 categories—and then each category has multiple controls. One issue with the NIST framework is that a comprehensive Security Assessment using this framework can quickly become a big project, often too big for the organization's size.
For small and medium-sized business, a good step forward is to specify the Center for Internet Security (CIS) Top 20 controls as the framework the independent Cyber Security team will assess. The CIS Top 20 controls provide an easy to understand assessment tool that senior executives will understand.

Once the CIS controls are evaluated, the organization's security posture can be easily visualized using color coded infographics and risk score heat charts. Many Security Assessments include an evaluation of the business's people, process, and technology. There is no point in spending technology dollars if the existing corporate processes do not support their use. These decisions can be explored using Radar charts to visualize the cyber readiness of three metrics: people, process, and technology. Radar charts depict cybersecurity assessment scores in a circular chart with gradient ranking that shows executives the information they need to act on to enhance their security posture.
The term vulnerability assessment applies to a broad range of systems. For example, in the context of a disaster recovery plan, the vulnerability assessment would include the likelihood of flooding, earthquakes, and other potential disasters. In the digital sphere, a vulnerability assessment is an evaluation of an organization's cybersecurity weaknesses. This process includes identifying and prioritizing specific computer configuration issues that represent vulnerable aspects of an organization's computing platforms.
The Institute for Security and Open Methodologies (ISECOM; www.isecom.org/research/) publishes the Open-Source Security Testing Methodology Manual that documents the components of a vendor neutral approach to a wide range of assessment methods and techniques. A vulnerability assessment project typically includes the following:
- Inventory of computing assets and networked devices
- Ranking those resources in order of importance
- Identification of vulnerabilities and potential threats
- Risk assessment
- Prioritized remediation plan
A vulnerability assessment starts with an inventory of computer systems and other devices connected to the network. Once the items on the network have been enumerated, the network is scanned using an automated tool to look for vulnerabilities. There are two types of scans: credentialed and noncredentialed. A credentialed scan uses domain admin credentials to obtain detailed inventories of software applications on each of the computers. This method provides the security team with the information necessary to identify operating system versions and required patches.
Often, a company's website is an overlooked corporate asset for a vulnerability assessments. The Open Web Application Security Project (OWASP) maintains a list of the top-10 vulnerabilities most commonly found on websites. Surprisingly, many websites fail to properly implement user authentication and data input checking. These types of vulnerabilities have the potential to expose corporate data to anyone with Internet access. Performing a vulnerability assessment exposes these issues so they may be resolved.
The final output of a vulnerability assessment project is the prioritized remediation plan. This plan uses the results of the risk assessment to determine which vulnerabilities represent the greatest risk to the organization. The total list of vulnerabilities is often numbered in the hundreds, if not thousands. However, not all of the vulnerabilities are big problems requiring immediate attention. The prioritized remediation plan allows IT administrators to reduce corporate risk quickly by focusing on the most important weaknesses first.
InfoSec Penetration Testing
Penetration testing (“pen test”) is a technique used by information security (InfoSec) professionals to find weaknesses in an organization's InfoSec defenses. In a penetration test, authorized cybersecurity professionals play the hacker's role.
Penetration testing attempts to circumvent digital safeguards and involves the simulation of an attack by hackers or an internal bad actor. The same techniques used by hackers to attack companies every day are used. The results of a penetration test reveal (in advance) the vulnerabilities and weaknesses that could allow a malicious attacker to gain access to a company's systems and data.
Some techniques used include brute-force attacks, exploitation of unpatched systems, and password-cracking tools. Organizations hire InfoSec experts with specialized training credentials––such as Certified Ethical Hacker (CEH) and Offensive Security Certified Profession (OSCP)––to conduct authorized attempts to breach the organization's security safeguards. These experts begin the pen test by conducting reconnaissance, often creating an attack surface and Internet footprint analysis to passively identify exposures, risks, and gaps in security. Once potential vulnerabilities are identified, the penetration testing team initiates the exploit attempts using automated tools to probe websites, firewalls, and e-mail systems.
Successful exploits often involve multiple vulnerabilities, which are attacked over several days. Individually, none of the weaknesses are a wide-open door. However, when combined together by an expert penetration tester, the result is a snowball effect that provides the pen test expert with an initial foothold inside the network from which they can pivot and gain access to additional systems.
Penetration testing is a useful technique for evaluating the potential damage from a determined attacker, as well as assess the organizational risks posed. Most hackers and criminals go after low-hanging fruit––easy targets. Regular penetration tests ensure that the efforts required to gain access to internal networks are substantial. The result? Most hackers will give up after a few hours and move on to other targets that are not so well defended.
Cybersecurity Considerations and Approaches
By Robert Smallwood
Limitations of Perimeter Security
Traditionally, central computer system security has been primarily perimeter security—securing the firewalls and perimeters within which e-documents are stored and attempting to keep intruders out—rather than securing e-documents directly upon their creation. The basic access security mechanisms implemented, such as passwords, two-factor authentication, and identity verification, are rendered totally ineffective once the confidential e-documents or records are legitimately accessed by an authorized employee. The documents are usually bare and unsecured. This poses tremendous challenges if the employee is suddenly terminated, if the person is a rogue intent on doing harm, or if outside hackers are able to penetrate the secured perimeter. And, of course, it is common knowledge that they do it all the time. The focus should be on securing the documents themselves, directly.
Restricting access is the goal of conventional perimeter security, but it does not directly protect the information inside. Perimeter security protects information the same way a safe protects valuables; if safecrackers get in, the contents are theirs. There are no protections once the safe is opened. Similarly, if hackers penetrate the perimeter security, they have complete access to the information inside, which they can steal, alter, or misuse.61 The perimeter security approach has four fundamental limitations:
- Limited effectiveness. Perimeter protection stops dead at the firewall, even though sensitive information is sent past it and circulates around the Web, unsecured. Today's extended computing model and the trend toward global business means that business enterprises and government agencies frequently share sensitive information externally with other stakeholders, including business partners, customers, suppliers, and constituents.
- Haphazard protections. In the normal course of business, knowledge workers send, work on, and store copies of the same information outside the organization's established perimeter. Even if the information's new digital environment is secured by other perimeters, each one utilizes different access controls or sometimes no access control at all (e.g. copying a price list from a sales folder to a marketing folder; an attorney copying a case brief or litigation strategy document from a paralegal's case folder).
- Too complex. With this multiperimeter scenario, there are simply too many perimeters to manage, and often they are out of the organization's direct control.
- No direct protections. Attempts to create boundaries or portals protected by perimeter security, within which stakeholders (partners, suppliers, shareholders, or customers) can share information, cause more complexity and administrative overhead while they fail to protect the e-documents and data directly.62
Despite the current investment in e-document security, it is astounding that once information is shared today, it is largely unknown who will be accessing it tomorrow.
Defense in Depth
Defense in depth is an approach that uses multiple layers of security mechanisms to protect information assets and reduce the likelihood that rogue attacks can succeed.63 The idea is based on military principles that an enemy is stymied by complex layers and approaches compared to a single line. That is, hackers may be able to penetrate one or two of the defense layers, but multiple security layers increase the chances of catching the attack before it gets too far. Defense in depth includes a firewall as a first line of defense and also antivirus and anti-spyware software, identity and access management (IAM), hierarchical passwords, intrusion detection, and biometric verification. Also, as a part of an overall IG program, physical security measures are deployed, such as smartcard or even biometric access to facilities and intensive IG training and auditing.
Controlling Access Using Identity Access Management
IAM software can provide an important piece of the security solution. It aims to prevent unauthorized people from accessing a system and to ensure that only authorized individuals engage with information, including confidential e-documents.
Today's business environment operates in a more extended and mobile model, often including stakeholders outside of the organization. With this more complex and fluctuating group of users accessing information management applications, the idea of identity management has gained increased importance.
The response to the growing number of software applications using inconsistent or incompatible security models is strong identity management enforcement software. These scattered applications offer opportunities not only for identity theft but also for identity drag, where the maintenance of identities does not keep up with changing identities, especially in organizations with a large workforce. This can result in theft of confidential information assets by unauthorized or out-of-date access and even failure to meet regulatory compliance, which can result in fines and imprisonment.64
IAM—along with sharp IG policies—“manages and governs user access to information through an automated, continuous process.”65 Implemented properly, good IAM does keep access limited to authorized users while increasing security, reducing IT complexity, and increasing operating efficiencies.
Critically, “IAM addresses ‘access creep’ where employees move to a different department of business unit and their rights to access information fail to get updated” (emphasis added).66
In France in 2007, a rogue stock trader at Société Générale had in-depth knowledge of the bank's access control procedures from his job at the home office.67 He used that information to defraud the bank and its clients out of over €7 billion (over $10 billion). If the bank had implemented an IAM solution, the crime may not have been possible.
A robust and effective IAM solution provides for:
- Auditing. Detailed audit trails of who attempted to access which information, and when. Stolen identities can be uncovered if, for instance, an authorized user attempts to log in from more than one computer at a time.
- Constant updating. Regular reviews of access rights assigned to individuals, including review and certification for user access, an automated recertification process (attestation), and enforcement of IG access policies that govern the way users access information in respect to segregation of duties.
- Evolving roles. Role life cycle management should be maintained on a continuous basis, to mine and manage roles and their associated access rights and policies.
- Risk reduction. Remediation regarding access to critical documents and information.
Enforcing IG: Protect Files with Rules and Permissions
One of the first tasks often needed when developing an IG program that secures confidential information assets is to define roles and responsibilities for those charged with implementing, maintaining, and enforcing IG policies. Corollaries that spring from that effort get down to the nitty-gritty of controlling information access by rules and permissions.
Rules and permissions specify who (by roles) is allowed access to which documents and information, and even contextually, from where (office, home, travel), and at what times (work hours, or extended hours). Using the old policy of the need-to-know basis is a good rule of thumb to apply when setting up these access policies (i.e. only those who are at a certain level of the organization or are directly involved in certain projects are allowed access to confidential and sensitive information). The roles are relatively easy to define in a traditional hierarchical structure, but today's flatter and more collaborative enterprises present challenges.
To effectively wall off and secure information by management level, many companies and governments have put in place an information security framework—a model that delineates which levels of the organization have access to specific documents and databases as a part of implemented IG policy. This framework shows a hierarchy of the company's management distributed across a range of defined levels of information access. The US Government Protection Profile for Authorization Server for Basic Robustness Environments is an example of such a framework.
Challenge of Securing Confidential E-Documents
Today's various document and content management systems were not initially designed to allow for secure document sharing and collaboration while also preventing document leakage. These software applications were mostly designed before the invention and adoption of newer business technologies that have extended the computing environment. The introduction of cloud computing, mobile PC devices, smartphones, social media, and online collaboration tools all came after most of today's document and content management systems were developed and brought to market.
Thus, vulnerabilities have arisen that need to be addressed with other, complementary technologies. We need to look no further than the WikiLeaks incident and the myriad of other major security breaches resulting in document and data leakage to see that there are serious information security issues in both the public and private sectors.
Technology is the tool, but without proper IG policies and a culture of compliance that supports the knowledge workers following IG policies, any effort to secure confidential information assets will fail. An old IT adage is that even perfect technology will fail without user commitment.
Protecting Confidential E-Documents: Limitations of Repository-Based Approaches
Organizations invest billions of dollars in IT solutions that manage e-documents and records in terms of security, auditing, search, records retention and disposition, version control, and so on. These information management solutions are predominantly repository-based, including enterprise content management (ECM) systems and collaborative workspaces (for unstructured information, such as e-documents). With content or document repositories, the focus has always been on perimeter security—keeping intruders out of the network. But that provides only partial protection. Once intruders are in, they are in and have full access to confidential e-documents. For those who are authorized to access the content, there are no protections, so they may freely copy, forward, print, or even edit and alter the information.68
The glaring vulnerability in the security architecture of ECM systems is that few protections exist once the information is legitimately accessed.
These confidential information assets, which may include military plans, price lists, patented designs, blueprints, drawings, and financial reports, often can be printed, e-mailed, or faxed to unauthorized parties without any security attached.69
Also, in the course of their normal work processes, knowledge workers tend to keep an extra copy of the electronic documents they are working on stored at their desktop, or they download and copy them to a tablet or laptop to work at home or while traveling. This creates a situation where multiple copies of these e-documents are scattered about on various devices and media, which creates a security problem, since they are outside of the repository and no longer secured, managed, controlled, or audited.
It also creates records management issues in terms of the various versions that might be out there and determining which one is the official business record.
Apply Better Technology for Better Enforcement in the Extended Enterprise
Protecting E-Documents in the Extended Enterprise
Sharing e-documents and collaborating are essential in today's increasingly mobile and global world. Businesses are operating in a more distributed model than ever before, and they are increasingly sharing and collaborating not only with coworkers but also with suppliers, customers, and even at times competitors (e.g. in pharmaceutical research). This reality presents a challenge to organizations dealing in sensitive and confidential information.70
Basic Security for the Microsoft Windows Office Desktop
The first level of protection for e-documents begins with basic protections at the desktop level. Microsoft Office provides ways to password-protect Microsoft Office files, such as those created in Word and Excel, quickly and easily. Many corporations and government agencies around the world use these basic protections. A key flaw or caveat is that passwords used in protecting documents cannot be retrieved if they are forgotten or lost.
Where Do Deleted Files Go?
When you delete a file it is gone, right? Actually, it is not (with the possible exception of solid-state hard drives). For example, after a file is deleted in Windows, a simple undelete DOS command can bring back the file, if it has not been overwritten. That is because when files are deleted, they are not really deleted; rather, the space where they reside is marked for reuse and can be overwritten. If it is not yet overwritten, the file is still there. The same process occurs as drafts of documents are created and temp (for temporary) files are stored. The portions of a hard drive where deleted or temp files are stored can be overwritten. This is called unallocated space. Most users are unaware that deleted files and fragments of documents and drafts are stored temporarily on their computer's unallocated space. So it must be wiped clean and completely erased to ensure that any confidential documents or drafts are completely removed from the hard drive.
IG programs include the highest security measures, which means that an organization must have a policy that includes deleting sensitive materials from a computer's unallocated space and tests that verify such deletion actions are successful periodically.
Lock Down: Stop All External Access to Confidential E-Documents
Organizations are taking other approaches to stop document and data leakage: physically restricting access to a computer by disconnecting it from any network connections and forbidding or even blocking use of any ports. Although cumbersome, these methods are effective in highly classified or restricted areas where confidential e-documents are held. Access is controlled by utilizing multiple advanced identity verification methods, such as biometric means.
Secure Printing
Organizations normally expend a good amount of effort making sure that computers, documents, and private information are protected and secure. However, if your computer is hooked up to a network printer (shared by multiple knowledge workers), all of that effort might have been wasted.71
Some basic measures can be taken to protect confidential documents from being compromised as they are printed. You simply invoke some standard Microsoft Office protections, which allow you to print the documents once you arrive in the copy room or at the networked printer. This process varies slightly, depending on the printer's manufacturer. (Refer to the documentation for the printer for details.)
In Microsoft Office, there is an option in the Print Dialog Box for delayed printing of documents (when you physically arrive at the printer).
Serious Security Issues with Large Print Files of Confidential Data
According to Canadian output and print technology expert William Broddy, in a company's data center, a print file of, for instance, investment account statements or bank statements contains all the rich information that a hacker or malicious insider needs. It is distilled information down to the most important core data about customers, which has been referred to as data syrup since it has been boiled down and contains no mountains of extraneous data, only the culled, cleaned, essential data that gives criminals exactly what they need.72
What most managers are not aware of is that entire print files and sometimes remnants of them stay on the hard drives of high-speed printers and are vulnerable to security breaches. Data center security personnel closely monitor calls to their database. To extract as much data as is contained in print files, a hacker requires hundreds or even thousands of calls to the database, which sets off alerts by system monitoring tools. But retrieving a print file takes only one intrusion, and it may go entirely unnoticed. The files are sitting there; a rogue service technician or field engineer can retrieve them on a routine service call.
To help secure print files, specialized hardware devices designed to sit between the print server and the network and cloak server print files are visible only to those who have a cloaking device on the other end.
Organizations must practice good IG and have specific procedures to erase sensitive print files once they have been utilized. For instance, in the example of preparing statements to mail to clients, files are exposed to possible intrusions in at least six points in the process (starting with print file preparation and ending with the actual mailing). These points must be tightly monitored and controlled. Typically an organization retains a print file for about 14 days, though some keep files long enough for customers to receive statements in the mail and review them. Organizations must make sure that print files or their remnants are secured and then completely erased when the printing job is finished.
E-Mail Encryption
Encrypting (scrambling using advanced algorithms) sensitive e-mail messages is an effective step to securing confidential information assets while in transit. Encryption can also be applied to desktop folders and files and even entire disk drives (full disk encryption, or FDE). All confidential or sensitive data and e-documents that are exposed to third parties or transferred over public networks should be secured with file-level encryption, at a minimum.73
Secure Communications Using Record-Free E-Mail
What types of tools can you use to encourage the free flow of ideas in collaborative efforts without compromising your confidential information assets or risking litigation or compliance sanctions?
Stream messaging is an innovation that became commercially viable around 2006. It is similar in impact to IRM software, which limits the recipients’ ability to forward, print, or alter data in an e-mail message (or reports, spreadsheets, etc.) but goes further by leaving no record on any computer or server.
Stream messaging is a simple, safe, secure electronic communications system ideal for ensuring that sensitive internal information is kept confidential and not publicly released. Stream messaging is not intended to be a replacement for enterprise e-mail but is a complement to it. If you need an electronic record, e-mail it; if not, use stream messaging.74
What makes stream messaging unique is its recordlessness. Streamed messages cannot be forwarded, edited, or saved. A copy cannot be printed as is possible with e-mail. That is because stream messaging separates the sender's and receiver's names and the date from the body of the message, never allowing them to be seen together. Even if the sender or receiver were to attempt to make a copy using the print-screen function, these elements are never captured together.75
The instant a stream message is sent, it is placed in a temporary storage buffer space. When the recipient logs in to read the message, it is removed from the buffer space. By the time the recipient opens it, the complete stream message no longer exists on the server or any other computer.
This communications approach is Web based, meaning that no hardware or software purchases are required. It also works with existing e-mail systems and e-mail addresses and is completely immune to spam and viruses. Other solutions (both past and present) have been offered, but these have taken the approach of encrypting e-mail or generating e-mail that disappears after a preset time. Neither of these approaches is truly recordless.
Stream messaging is unique because its technology effectively eliminates the ability to print, cut, paste, forward, or save a message. It may be the only electronic communications system that separates the header information—date, name of sender, name of recipient—from the body of the message. This eliminates a traceable record of the communication. Soon many other renditions of secure messaging will be developed.
In addition, stream messaging offers the added protection of being an indiscriminate Web-based service, meaning that the messages and headers are never hosted on the subscribing companies’ networks. This eliminates the risk that employers, competitors, or hackers could intercept stream messages, which is a great security benefit for end users.76
Digital Signatures
Digital signatures are more than just digitized autographs—they carry detailed audit information used to “detect unauthorized modifications” to e-documents and to “authenticate the identity of the signatory.”77
Online transactions can be conducted with full trust that they are legal, proper, and binding. They prove that the person whose signature is on the e-document did, in fact, authorize it. A digital signature provides evidence in demonstrating to a third party that the signature was genuine, true, and authentic, which is known as nonrepudiation. To repudiate is to dispute, and with digital signatures, a signatory is unable to claim that the signature is forged.
Digital signatures can be implemented a variety of ways—not just through software but also through firmware (programmed microchips), computer hardware, or a combination of the three. Generally, hardware- and firmware-based implementations are more difficult to hack, since their instructions are hardwired.
Here is a key point: for those who are unfamiliar with the technology, there is a big difference between electronic signatures and digital signatures.78
An “electronic signature is likely to be a bit-map image, either from a scanned image, a fax copy or a picture of someone's signature, or may even be a typed acknowledgment or acceptance.” A digital signature contains “extra data appended to a message which identifies and authenticates the sender and message data using public-key encryption.”79
So digital signatures are the only ones that offer any real security advantages.
Digital signatures are verified by the combination of applying a signatory's private signing key and the public key that comes from the signatory's personal ID certificate. After that, only the public key ID certificate is required for future verifications. “In addition, a checksum mechanism confirms that there have been no modifications to the content.”80
A formal, trusted certificate authority (CA) issues the certificate associated with the public-private key. It is possible to generate self-certified public keys, but these do not verify and authenticate the recipient's identity and are therefore flawed from a security standpoint. The interchange of verified signatures is possible on a global scale, as “digital signature standards are mature and converging internationally.”81
After more than 30 years of predictions, the paperless office is almost here. Business process cycles have been reduced, and great efficiencies have been gained since the majority of documents today are created digitally and spend most of their life cycle in digital form, and they can be routed through work steps using business process management (BPM) and work flow software. However, the requirement for a physical signature frequently disrupts and holds up these business processes. Documents have to be printed out, physically routed, and physically signed—and often they are scanned back into a document or records management (or contract management) system, which defeats the efficiencies sought.
Often multiple signatures are required in an approval process, and some organizations require each page to be initialed, which makes the process slow and cumbersome when it is executed without the benefit of digital signatures. Also, multiple copies are generated—as many as 20—so digital signature capability injected into a business process can account for significant time and cost savings.82
Document Encryption
There is some overlap and sometimes confusion between digital signatures and document encryption. Suffice it to say, they work differently, in that document encryption secures a document for those who share a secret key, and digital signatures prove that the document has not been altered and the signature is authentic.
There are e-records management implications of employing document encryption:
Unless it is absolutely essential, full document encryption is often advised against for use within electronic records management systems as it prevents full-text indexing, and requires that the decryption keys (and application) are available for any future access. Furthermore, if the decryption key is lost or an employee leaves without passing it on, encrypted documents and records will in effect be electronically shredded as no one will be able to read them.
Correctly certified digital signatures do not prevent unauthorized persons reading a document nor are they intended to. They do confirm that the person who signed it is who they say they are, and that the document has not been altered since they signed it. Within a records management system a digital signature is often considered to be an important part of the metadata of a document, confirming both its heritage and its integrity.83
Data Loss Prevention (DLP) Technology
The aforementioned document security challenges have given rise to an emerging but critical set of capabilities by a new breed of IT companies that provide data loss prevention (DLP) (also called data leak prevention). DLP providers create software and hardware appliances that thoroughly inspect all e-documents and e-mail messages before they leave the organization's perimeter and attempt to stop sensitive data from exiting the firewall.
This filtering is based on several factors, but mostly using specified critical content keywords that are flagged by the implementing organization. DLP can also stop the exit of information assets by document types, origin, time of day, and other factors.
DLP systems are designed to detect and prevent unauthorized use and transmission of confidential information.84 In more detail, DLP is a computer security term referring to systems that identify, monitor, and protect data/documents in all three states: (1) in use (endpoint actions), (2) in motion (network actions), and (3) at rest (data/document storage). DLP accomplishes this by deep content inspection and contextual security analysis of transaction data (e.g. attributes of the originator, the data object, medium, timing, recipient/destination, etc.) with a centralized management framework.
Promise of DLP
The global enterprise data loss prevention market is anticipated to grow at a compound annual growth rate of more than 16% from 2018 to 2023, from about $1.2 billion to $2.5 billion by 2023.85 Gartner states, that “with adoption of DLP technologies moving quickly down to the small to medium enterprise, DLP is no longer an unknown quantity.”86 Although the DLP market has matured, it suffers from confusion about how DLP best fits into the new mix of security approaches, how it is best utilized (endpoint or gateway), and even the definition of DLP itself.87
Data loss is very much on managers’ and executives’ minds today. The series of WikiLeaks incidents exposed hundreds of thousands of sensitive government and military documents. According to the Ponemon Institute (as reported by DLP experts), data leaks continue to increase annually. Billions of dollars are lost every year as a result of data leaks, with the cost of each breach ranging from an average of $700,000 to $31 million. Some interesting statistics from the study include:
- Almost half of breaches happen while an enterprise's data was in the hands of a third party.
- Over one-third of breaches involved lost or stolen mobile devices.
- The cost per stolen record is approximately $200 to $225.
- One-quarter of breaches were conducted by criminals or with malicious intent.
- More than 80% of breaches compromised more than 1000 records.88
What DLP Does Well (and Not So Well)
DLP has been deployed successfully as a tool used to map the flow of data inside and exiting the organization to determine the paths that content takes, so that more sophisticated information mapping, monitoring, and content security can take place.
This use as a traffic monitor for analysis purposes has been much more successful than relying on DLP as the sole enforcement tool for compliance and to secure information assets. Today's technology is simply not fast enough to catch everything. It catches many e-mail messages and documents that users are authorized to send, which slows the network and the business down. This also adds unnecessary overhead, as someone has to go back and release each and every one of the e-mails or documents that were wrongly stopped.
Another downside: since DLP relies on content inspection, it cannot detect and monitor encrypted e-mail or documents.
Basic DLP Methods
DLP solutions typically apply one of three methods:
- Scanning traffic for keywords or regular expressions, such as customer credit card or social security numbers.
- Classifying documents and content based on a predefined set to determine what is likely to be confidential and what is not.
- Tainting (in the case of agent-based solutions), whereby documents are tagged and then monitored to determine how to classify derivative documents. For example, if someone copies a portion of a sensitive document into a different document, this document receives the same security clearance as the original document.89
All these methods involve the network administrator setting up a policy clearly defining what is allowed to be sent out and what should be kept in confidence. This policy creating effort is extremely difficult: defining a policy that is too broad means accidentally letting sensitive information get out, and defining a policy that is too narrow means getting a significant number of false positives and stopping the flow of normal business communications.
Although network security management is well established, defining these types of IG policies is extremely difficult for a network administrator. Leaving this job to network administrators means there will be no collaboration with business units, no standardization, and no real forethought. As a result, many installations are plagued with false positives that are flagged and stopped, which can stifle and frustrate knowledge workers. The majority of DLP deployments simply use DLP for monitoring and auditing purposes.
Examining the issue of the dissolving perimeter more closely, a deeper problem is revealed: DLP is binary; it is black or white. Either a certain e-document or e-mail can leave the organization's boundaries or it cannot. This process has been referred to as outbound content compliance.
But this is not how the real world works today. Now there is an increasing need for collaboration and for information to be shared or reside outside the organization on mobile devices or in the cloud.
Most of today's DLP technology cannot address these complex issues on its own. Often additional technology layers are needed.
Data Loss Prevention: Limitations
DLP has been hyped in the past few years, and major security players have made several large acquisitions—especially those in the IRM market. Much like firewalls, DLP started in the form of network gateways that searched e-mail, Web traffic, and other forms of information traveling out of the organization for data that was defined as internal. When it found such data, the DLP blocked transmission or monitored its use.
Soon agent-based solutions were introduced, performing the same actions locally on users’ computers. The next step brought a consolidation of many agent- and network-based solutions to offer a comprehensive solution.
IG policy issues are key. What is the policy? All these methods depend on management setting up a policy that clearly defines what is acceptable to send out and what should be kept in confidence.
With DLP, a certain document can either leave the organization's boundaries or it can't. But this is not how the real world works. In today's world there is an increasing need for information to be shared or reside outside the organization on mobile devices or in the cloud. Simply put, DLP is not capable of addressing this issue on its own, but it is a helpful piece of the overall technology solution.
Missing Piece: Information Rights Management (IRM)
Another technology tool for securing information assets is information rights management (IRM) software (also referred to as enterprise rights management [ERM] and previously as enterprise digital rights management [e-DRM].) For purposes of this book, we use the term “IRM” when referring to this technology set, so as not to be confused with electronic records management. Major software companies also use the term “IRM.”
IRM technology provides a sort of security wrapper around documents and protects sensitive information assets from unauthorized access.90 We know that DLP can search for key terms and stop the exit of sensitive data from the organization by inspecting its content. But it can also prevent confidential data from being copied to external media or sent by e-mail if the person is not authorized to do so. If IRM is deployed, files and documents are protected wherever they may be, with persistent security. The ability to apply security to an e-document in any state (in use, in motion, and at rest), across media types, inside or outside of the organization, is called persistent security. This is a key characteristic of IRM technology, and it is all done transparently without user intervention.91
IRM has the ability to protect e-documents and data wherever they may reside, however they may be used, and in all three data states (at rest, in use, and in transit).92
IRM allows for e-documents to be remote controlled, meaning that security protections can be enforced even if the document leaves the perimeter of the organization. This means that e-documents (and their control mechanisms) can be separately created, viewed, edited, and distributed.
IRM provides persistent, ever-present security and manages access to sensitive e-documents and data. IRM provides embedded file-level protections that travel with the document or data, regardless of media type.93 These protections prevent unauthorized viewing, editing, printing, copying, forwarding, or faxing. So, even if files are somehow copied to a thumb drive and taken out of the organization, e-document protections and usage are still controlled.
The major applications for IRM services include cross-protection of e-mails and attachments, dynamic content protection on Web portals, secure Web-based training, secure Web publishing, and secure content storage and e-mail repositories all while meeting compliance requirements of Sarbanes-Oxley, the Health Insurance Portability and Accountability Act, and others. Organizations can comply with regulations for securing and maintaining the integrity of digital records, and IRM will restrict and track access to spreadsheets and other financial data too.
In investment banking, research communications must be monitored, according to National Association of Securities Dealers (NASD) rule 2711, and IRM can help support compliance efforts. In consumer finance, personal financial information collected on paper forms and transmitted by fax (e.g. auto dealers faxing credit applications), or other low-security media can be secured using IRM, directly from a scanner or copier. Importers and exporters can use IRM to ensure data security and prevent the loss of cargo from theft or even terrorist activities, and they also can comply with U.S. Customs and trade regulations by deploying IRM software. Public sector data security needs are numerous, including intelligence gathering and distribution, espionage, and Homeland Security initiatives. Firms that generate intellectual property (IP), such as research and consulting groups, can control and protect access to IP with it. In the highly collaborative pharmaceutical industry, IRM can secure research and testing data.
IRM protections can be added to nearly all e-document types including e-mail, word processing files, spreadsheets, graphic presentations, computer-aided design (CAD) plans, and blueprints. This security can be enforced globally on all documents or granularly down to the smallest level, protecting sensitive fields of information from prying eyes. This is true even if there are multiple copies of the e-documents scattered about on servers in varying geographic locations. Also, the protections can be applied permanently or within controlled time frames. For instance, a person may be granted access to a secure e-document for a day, a week, or a year.
Key IRM Characteristics
Three requirements are recommended to ensure effective IRM:
- Security is foremost; documents, communications, and licenses should be encrypted, and documents should require authorization before being altered.
- The system can't be any harder to use than working with unprotected documents.
- It must be easy to deploy and manage, scale to enterprise proportions, and work with a variety of common desktop applications.94
IRM software enforces and manages document access policies and use rights (view, edit, print, copy, e-mail forward) of electronic documents and data. Controlled information can be text documents, spreadsheets, financial statements, e-mail messages, policy and procedure manuals, research, customer and project data, personnel files, medical records, intranet pages, and other sensitive information. IRM provides persistent enforcement of IG and access policies to allow an organization to control access to information that needs to be secured for privacy, competitive, or compliance reasons. Persistent content security is a necessary part of an end-to-end enterprise security architecture.
Well, it sounds like fabulous technology, but is IRM really so new? No, it has been around for a decade or more, and continues to mature and improve. It has essentially entered the mainstream around 2004/2005 (when this author began tracking its development and publishing researched articles on the topic).
IRM software currently is used for persistent file protection by thousands of organizations throughout the world. Its success depends on the quality and consistency of the deployment, which includes detailed policy-making efforts. Difficulties in policy maintenance and lack of real support for external sharing and mobile devices have kept first-wave IRM deployments from becoming widespread, but this aspect is being addressed by a second wave of new IRM technology companies.
Other Key Characteristics of IRM
Policy Creation and Management
IRM allows for the creation and enforcement of policies governing access and use of sensitive or confidential e-documents. The organization's IG team sets the policies for access based on role and organizational level, determining what employees can and cannot do with the secured e-documents.95 The IG policy defined for a document type includes these following controls:
- Viewing
- Editing
- Copy/Paste (including screen capture)
- Printing
- Forwarding e-mail containing secured e-documents
Access to sensitive e-documents may be revoked at any time, no matter where they are located or what media they are on, since each time a user tries to access a document, access rights are verified with a server or cloud IRM application. This can be done remotely—that is, when an attempt is made to open the document, an authorization must take place. In cloud-based implementations, it is a matter of simply denying access.
Decentralized Administration
One of the key challenges of e-document security traditionally is that a system administrator had access to documents and reports that were meant only for executives and senior managers. With IRM, the e-document owner administers the security of the data, which considerably reduces the risk of a document theft, alteration, or misuse.
Auditing
Auditing provides the smoking-gun evidence in the event of a true security breach. Good IRM software provides an audit trail of how all documents secured by it are used. Some go further, providing more detailed document analytics of usage.
Integration
To be viable, IRM must integrate with other enterprisewide systems, such as ECM, customer relationship management, product life cycle management, enterprise resource planning, e-mail management, message archiving, e-discovery, and a myriad of cloud-based systems. This is a characteristic of today's newer wave of IRM software.
This ability to integrate with enterprise-based systems does not mean that IRM has to be deployed at an enterprise level. The best approach is to target one critical department or area with a strong business need and to keep the scope of the project narrow to gain an early success before expanding the implementation into other departments.
IRM embeds protection into the data (using encryption technology), allowing files to protect themselves. IRM may be the best available security technology for the new mobile computing world of the permeable perimeter.96
With IRM technology, a document owner can selectively prevent others from viewing, editing, copying, or printing it. Despite its promise, most enterprises do not use IRM, and if they do, they do not use it on an enterprise-wide basis. This is due to the high complexity, rigidity, and cost of legacy IRM solutions.
It is clearly more difficult to use documents protected with IRM—especially when policymaking and maintenance is not designed by role but rather by an individual. Some early implementations of IRM by first-to-market software development firms had as many as 200,000 different policies to maintain (for 200,000 employees). These have since been replaced by newer, second-wave IRM vendors, who have reduced that number to a mere 200 policies, which is much more manageable. Older IRM installations require intrusive plug-in installation; they are limited in the platforms they support, and they largely prevent the use of newer platforms, such as smartphones, iPads, and other tablets. This is a real problem in a world where almost all executives carry a smartphone and use of tablets (especially the iPad) is growing.
Moreover, due to their basic design, first-wave or legacy IRM is not a good fit for organizations aiming to protect documents shared outside company boundaries. These outdated IRM solutions were designed and developed in a world where organizations were more concerned with keeping information inside the perimeter than protecting information beyond the perimeter.
Most initial providers of IRM focused on internal sharing and are heavily dependent on Microsoft Active Directory (AD) and lightweight directory access protocol (LDAP) for authentication. Also, the delivery model of older IRM solutions involves the deployment and management of multiple servers, SQL databases, AD/LDAP integration, and a great deal of configuration. This makes them expensive and cumbersome to implement and maintain. Furthermore, these older IRM solutions do not take advantage of or operate well in a cloud computing environment.
Although encryption and legacy IRM solutions have certain benefits, they are extremely unwieldy and complex and offer limited benefits in today's technical and business environment. Newer IRM solutions are needed to provide more complete DLS.
Embedded Protection
IRM embeds protection into the data (using encryption technology), allowing files to protect themselves. IRM may be the best available security technology for the new mobile computing world of the permeable perimeter.97
Is Encryption Enough?
Many of the early solutions for locking down data involved encryption in one form or another:
- E-mail encryption
- File encryption
- Full disk encryption (FDE)
- Enterprise-wide encryption
These encryption solutions can be divided into two categories: encryption in transit (e.g. e-mail encryption) and encryption at rest (e.g. FDE).
The various encryption solutions mitigate some risks. In the case of data in transit, these risks could include an eavesdropper attempting to discern e-mail or network traffic. In the case of at-rest data, risks include loss of a laptop or unauthorized access to an employee's machine. The most advanced solutions are capable of applying a policy across the organization and encrypting files, e-mails, and even databases. However, encryption has its caveats.
Most simple encryption techniques necessarily involve the decryption of documents so they can be viewed or edited. At these points, the files are essentially exposed. Malware (e.g. Trojan horses, keystroke loggers) installed on a computer may use the opportunity to send out the plain-text file to unauthorized parties. Alternatively, an employee may copy the contents of these files and remove them from the enterprise.
Device Control Methods
Another method that is related to DLP is device control. Many vendors offer software or hardware that prevents users from copying data via the USB port to portable drives and removing them from the organization in this manner. These solutions are typically as simple as blocking the ports; however, some DLP solutions, when installed on the client side, can selectively prevent the copying of certain documents.98
Thin Clients
One last method worth mentioning is the use of thin clients to prevent data leaks. These provide a so-called walled garden containing only the applications users require to do their work, via a diskless terminal. This prevents users from copying any data onto portable media; however, if they have e-mail or Web access applications, they still can send information out via e-mail, blogs, or social networks.
Note about Database Security
Database security and monitoring is addressed in Chapter 10, “Information Governance and Information Technology Functions.”
Compliance Aspect
Compliance has been key in driving companies to invest in improving their security measures, such as firewalls, antivirus software, and DLP systems. More than 400 regulations exist worldwide mandating a plethora of information and data security requirements. One example is the Payment Card Industry Data Security Standard (PCI-DSS), which is one of the strictest regulations for credit card processors. Companies that fail to comply with these regulations are subject to penalties of up to $500,000 per month for lost financial data or credit card information. Forrester Research estimated the per-record cost of a breach is $90 to $305. But do compliance activities always result in adequate protection of your sensitive data? In many cases the answer is no. It is important to keep in mind that being formally compliant does not mean the organization is actually secure. In fact, compliance is sometimes used as a fig leaf, covering a lack of real document security. One needs to look no further than to the recent series of major document leakage incidents to understand this. Those all came from highly secure and regulated entities, such as banks, hospitals, and the military.
Hybrid Approach: Combining DLP and IRM Technologies
An idea being promoted recently is to make IRM an enforcement mechanism for platforms like DLP. Together, DLP and IRM accomplish what they independently cannot. Enterprises may be able to use their DLP tools to discover data flows, map them out, and detect transmissions of sensitive information. They can then apply their IRM or encryption protection to enforce their confidentiality and information integrity goals.99
Several vendors in the fields of DLP, encryption, and IRM have already announced integrated products. However, at this point in time, most IRM solutions are by no means ready for prime time when it comes to this use. Only a select few select second-wave IRM software providers can offer comprehensive, streamlined, persistent security across many platforms.
As the enterprise perimeter dissolves, document and data security should become the focus of the Internet security field. However, most legacy solutions, such as encryption and legacy IRM, are complex and expensive and provide only a partial solution to the key problems. Combining several methods offers effective countermeasures, but an ultimate solution has not yet arrived.
Securing Trade Secrets After Layoffs and Terminations
In today's global economy—which has shifted labor demands—huge layoffs are not uncommon in the corporate and public sectors. The act of terminating an employee creates document security and IP challenges while raising the question: How does the organization retrieve and retain its IP and confidential data? An IG program to secure information assets must also deal with everyday resignations of employees who are in possession of sensitive documents and information.100
According to Peter Abatan, author of the Enterprise Digital Rights Management blog, “As a general rule all organizations should classify all their documents with the aim of identifying the ones that need persistent protection” (emphasis added). That is to say, documents should be protected at all times, regardless of where they travel and who is using them, while the organization still retains control of usage rights. There are two basic technological approaches to this protection:
- The first, as discussed earlier in this chapter, is combining IRM with DLP; DLP is used to conduct deep content inspection and identify all documents that may contain sensitive information, then the DLP agent “notifies the enterprise [information] rights management engine that sensitive information is about to be copied to external media or outside the firewall and therefore needs to be encrypted.”
- The second is using a form of context-sensitive IRM “in which all documents that contain sensitive data defined in the [global] data dictionary [are] automatically encrypted.”
These two technological approaches must be fostered by an IG program. They can have significant positive impact in protecting sensitive information, no matter where it is located, and can help document owners withdraw access to its sensitive documents at any time.
Organizations must educate their employees to increase awareness of the financial and competitive impact of breaches and to clarify that sensitive documents are the property of the organization. If those handling sensitive documents are informed of the benefits of IRM and related technologies, they will be more vigilant in their efforts to keep information assets secure.
Persistently Protecting Blueprints and CAD Documents
Certain IRM software providers have focused on securing large-format engineering and design documents, and they have made great strides in the protection of computer-aided design files. As much as 95% of CAD files are proprietary designs and represent valuable, proprietary IP of businesses worldwide. And CAD files are just as vulnerable as any other e-document in that, when unprotected, they “can be e-mailed or transferred to another party without the knowledge of the owner of the content.”101
In today's global economy, it is common to conduct manufacturing operations in markets where labor is inexpensive and regulations are lax. Many designs are sent to China, Indonesia, and India for manufacturing. Although they usually are accompanied by binding confidential disclosure contracts, but these agreements are often difficult to enforce, especially given the disparity in cultures and laws. And what happens if a rogue employee in possession of designs and trade secrets absconds with them and sells them to a competitor? Or starts a competing business? There are a number of examples of this happening.
Owners of valuable proprietary IP must vigilantly protect it; the very survival of the business may depend on it. Monitoring and securing IP wherever it might travel is now a business imperative.
Theft of IP and confidential information represents a clear and present danger to all types of businesses, especially global brands dependent on proprietary designs for a competitive advantage. Immediate IG action by executive management is required to identify possible leaks and plug the holes. Not safeguarding IP and confidential or sensitive documents puts the organization's competitive position, strategic plans, revenue stream, and very future at risk.
Securing Internal Price Lists
In 2010, it was reported that confidential information about the advertising expenditures of some of Google's major accounts was leaked to the public.102 This may not seem like a significant breach, but, in fact, with this information, Google's customers can determine if they are getting a preferred price schedule, and competitors can easily undercut Google's pricing for major customers. According to Peter Abatan, “[It is clear] why this information is so critical to Google that this information is tightly secured.”
Is your company's price list secured at all times? Price lists are confidential information assets, and if they are revealed publicly, major customers could demand steeper discounts and business relationships could suffer irreparable damage, especially if customers find out they are paying more for a product or service than their competitors.
A company's price list is critical to an organization because it impacts all aspects of the business, from the ability to generate revenue to private dealings with customers and suppliers. IRM should be used to protect price lists, and printing of these valuable lists must be monitored and controlled using secure printing methods and document analytics.
Confidential information should be persistently protected throughout their document life cycle in all three states (at rest, in motion, and in use) so that if they are compromised or stolen, they are still protected and controlled by the owning organization.
Approaches for Securing Data Once It Leaves the Organization
It is obvious with today's trends that, as Andrew Jaquith of Forrester Research states, “The enterprise security perimeter is quickly dissolving.” A lot of valuable information is routed outside the owning organization through unsecured e-mail. A breach can compromise competitive position, especially in cases dealing with personnel files and marketing plans or merger details. Consider for a moment that even proprietary software and company financial statements are sent out. Exposure of this data can have real financial impact. Without additional protections, such as IRM and e-mail encryption, these valuable information assets are often out of the control of the IT department of the owning organization.103
Third-party possession or control of enterprise data is a critical point of vulnerability, and many organizations realize that securing data outside the organizational perimeter is a high priority. But a new concept has cropped up of late that bucks unconventional wisdom: “control does not require ownership.”
Instead of focusing on securing devices where confidential data is accessed, the new thinking focuses on securing the data and documents directly. With this new mind-set, security can be planned under the assumption that the enterprise owns its data but none of the devices that access it. As Jaquith states, “Treat all endpoints as hostile” (emphasis added). Forrester Research refers to this concept as the “zero-trust model of information security.” Zero trust, according to Jaquith, is “centered on the idea that security must become ubiquitous” throughout an organization's infrastructure.
Forrester has developed a new network architecture that builds security into the DNA of a network, using a mixture of five data security design patterns:
- Thin client. Access information online only, with no local operations, using a diskless terminal that cannot store data, documents, or programs so confidential information stays stored and secured centrally. For additional security, “IT can restrict host copy-and-paste operations, limit data transfers, and require strong or two-factor authentication using SecurID or other tokens.”
- Thin device. Devices such as smartphones, which have limited computing resources, Web surfing, e-mail, and basic Web apps that locally conduct no real information processing are categorized as thin devices. In practice, these devices do not hold original documents but merely copies, so the official business record or master copy cannot be altered or deleted. A nice feature of many smartphones is the ability to erase or wipe data remotely, in the event the device is lost. This is a little added insurance, and it makes smartphones “truly ‘disposable,’ unlike PCs,” according to Jaquith.
- Protected process. This approach allows local processing with a PC where confidential e-documents and data are stored and processed in a partition that is highly secure and controlled. This processing can occur even if the PC is not owned and controlled by the organization. “The protected process pattern has many advantages: local execution, offline operation, central management, and a high degree of granular security control, including remote wipe [erase].” A mitigating factor to consider here is most business PCs today are Windows based, and the world is rapidly moving to other, more nimble platforms.
- Protected data. Deploying IRM and embedding security into the documents (or data) provides complete DLS. The newer wave of more sophisticated, easier-to-use IRM vendors have role-based policy implementation and such features as “contextual” enforcement, where document rights are dependent on the context—that is, where and when a user attempts access. For instance, allow access to documents on workers’ desktops but not on their laptops; or provide access to printing confidential documents at the facility during office hours but not after. “Of all the patterns in the Zero Trust data security strategy, protected data is the most fine-grained and effective because it focuses on the information, not its containers.”
- Eye in the sky. This design pattern uses technologies such as DLP to scan network traffic content and halt confidential documents or sensitive data at the perimeter. Deployed properly, DLP is “ideal for understanding the velocity and direction of information flow and for detecting potential breaches, outliers, or anomalous transmissions.” It should be noted that DLP does not provide complete protection. To do so would mean that many legitimate and sanctioned e-mails and documents would be held up for inspection, thus slowing the business process. As stated earlier, DLP is best for discovering information flows and monitoring network traffic. Another negative is that you cannot always require partner organizations and suppliers to install DLP on their computers. So this is a complementary technology, not a complete solution to securing confidential information assets.
By discarding the “age-old conflation of ownership and control, enterprises will be able to build data protection programs that encompass all possible ownership scenarios, including Tech Populism, offshoring, and outsourcing.”
Document Labeling
Document labeling is “an easy way to increase user awareness about the sensitivity of information in a document” (emphasis added).104 What is it? It is the process of attaching a label to classify a document. For instance, who would not know that a document labeled “confidential” is indeed confidential? If the label appears prominently at the top of a document, it is difficult for persons accessing it to claim they did not know it was sensitive.
The challenge is to standardize and formalize the process of getting the label onto the document—enterprise-wide. This issue would be addressed in an IG effort focused on securing confidential e-documents, or may also be a part of a classification and taxonomy design effort. It cannot simply be left up to users to type in labels themselves, or it will not be sufficiently executed and will end up leaving a mishmash of labeled documents without any formal classification.
Another great challenge is legacy or archived documents, which are the lion's share of an organization's information assets. How do you go back and label those? One by one? Nope. Not practical.
Some content repositories or portals, such as Microsoft SharePoint, provide some functionality toward addressing the document labeling challenge. SharePoint is the most popular platform for sharing documents today.
SharePoint has an information management policy tool called Labels, which can be used to add document labels, such as Confidential, to the top of documents.
There are several options available for administrators to customize the labels, including the ability to:
- Prompt users to add the label when they save or print, rather than relying on the user to click the Label button in the ribbon;
- Specify labels containing static text and/or variables such as Project Name;
- Control the appearance of the labels, such as font, size, and justification.105
The labels are easily added from within Microsoft Office Word, PowerPoint, and Excel. One method that can be used is for the user to click the Label button on the Insert ribbon group; another method is to add the label through a prompt that appears when a user saves or prints a document (if the administrator has configured this option).
The labeling capabilities in document and content management systems such as Microsoft's SharePoint are a good start for increasing user awareness and improving the handling of sensitive documents. However, the document labeling capabilities of SharePoint are basic and limited. These basic capabilities may provide a partial or temporary solution, although organizations aiming for a high level of security and confidentiality for their documents will need to search for supplemental technologies from third-party software providers. For instance, finding the capabilities to label documents in bulk rather than one by one, add watermarks, or force users to save or print documents with a standard document label that cannot be altered may require looking at alternatives. Some are software vendors that have enhanced the SharePoint document labeling capability and may provide the complete solution.
Document Analytics
Some software providers also provide document analytics capabilities that monitor the access, use, and printing of documents and create real-time graphical reports of document use activities. These capabilities are very valuable.
Document analytics allow a compliance officer or system administrator to view exactly how many documents a user accesses in a day and how many documents the user accesses on average. Using this information, analytics monitors can look for spikes or anomalies in use. It is also possible to establish baselines and compare usage with that of an employee's peers as well as his or her past document usage. If, for instance, a user normally accesses an average of 25 documents a day and that suddenly spikes to 200, the system sends an alert, and perhaps it is time to pay a visit to that person's office. Or, if an employee normally prints 50 pages per day, then one day prints 250 pages, a flag is raised. Document analytics capabilities can go so far as to calculate the average time a user spends reading a document; significant time fluctuations can be flagged as potentially suspicious activity.
Confidential Stream Messaging
E-mail is dangerous. It contains much of an organization's confidential information, and 99% of the time it is sent out unsecured. It has been estimated that as many as 20% of e-mail messages transmitted pose a legal, financial, or regulatory threat to the organization. Specifically, “34 percent of employers investigated a leak of confidential business information via e-mail, and an additional 26 percent of organizations suffered the exposure of embarrassing or sensitive information during the course of a year,” according to Nancy Flynn, Executive Director of the ePolicy Institute. These numbers are rising, giving managers and business owners cause to look for confidential messaging solutions.106
Since stream messaging (a form of ephemeral messaging) separates the header and identifying information from the message, sends them separately, and leaves no record or trace, it is a good option for executives and managers, particularly when engaged in sensitive negotiations, litigation, or other highly confidential activities. Whereas e-mail leaves behind an indelible fingerprint that lives forever on multiple servers and systems, stream messaging does not.
Business records, IP and trade secrets, and confidential executive communications can be protected by implementing stream messaging. It can be implemented alongside and in concert with a regular e-mail system, but clear rules on the use of stream messaging must be established, and access to it must be tightly restricted to a small circle of key executives and managers.
The ePolicy Institute offers seven steps to controlling stream messaging:
- Work with your legal counsel to define “business record” for your organization on a companywide basis. Establish written records retention policies, disposition and destruction schedules. And litigation hold rules. Support the e-mail retention policy with a bona fide e-mail archiving solution to facilitate the indexing, preservation, and production of legally authentic records. Implement a formal electronic records management system to manage all records.
- Work with your legal counsel to determine when, how, why, and with whom confidential stream messaging is the most appropriate, effective—and legally compliant—way to hold recordless, confidential business discussions when permanent records are not required.
- In order to preserve attorney-client privilege, a phone call or confidential electronic messaging may be preferable to e-mail. Have corporate counsel spell out the manner in which executives and employees should communicate with lawyers when discussing business, seeking legal advice, or asking questions related to specific litigation.
- Define key terms for employees. Don't assume employees understand what management means when using terms like “confidential,” ”proprietary,” “private” or “intellectual property,” and so on. Employees must clearly understand definitions if they are to comply with confidentiality rules.
- Implement written rules and policies governing the use of e-mail and confidential stream messaging. E-policies should be written clearly and should be easy for employees to access and understand. Make them [as] “short and sweet” as possible. Do not leave anything up to interpretation.
- Distribute a hard copy of the new confidential messaging policy, e-mail policy and other electronic communications (e.g., social media, blogs). Insist that each and every employee signs and dates the policy, acknowledging that they understand and accept it and that disciplinary action including termination may result from violation of the organization's established policies.
- Educate, educate, educate. Ensure that all employees who need to know are able to discern between e-mail that leaves a potential business record and stream messaging which does not, and what is confidential.107
Securing confidential information assets effectively requires an eclectic, multifaceted approach. It takes clear and enforced IG policies, a collection of technologies, and regular testing and audits, both internally and by a trusted third party.
Notes
- 1. Dalvin Brown, “Americans Are More Concerned with Data Privacy Than Job Creation, Study Shows,” USA Today, November 9, 2018, https://www.USAToday.com/story/money/2018/11/09/Americans-more-concerned-data-privacy-than-healthcare-study-says/1904796002/.
- 2. F. Bélanger and R. E. Crossler, ”“Privacy in the Digital Age: A Review of Information Privacy Research in Information Systems,” MIS Quarterly 35, no. 4 (2011): 1017–1041. doi:10.2307/41409971.
- 3. R. Gradwohl and R. Smorodinsky, “Perception Games and Privacy,” Games and Economic Behavior 104 (2017): 293–308. doi:10.1016/j.geb.2017.04.006.
- 4. P. Swire and S. Bermann, Information Privacy: Official Reference for the Certified Information Privacy Professional (CIPP) (York, ME: International Association of Privacy Professionals, 2008), 7.
- 5. J. Camenisch, “Information Privacy?” Computer Networks 56, no. 18 (2012): 3834–3848. doi:10.1016/j.comnet.2012.10.012
- 6. O. Shy and R. Stenbacka, “Customer Privacy and Competition,” Journal of Economics & Management Strategy 25, no. 3 (2016): 539–562. doi:10.1111/jems.12157
- 7. https://www.privacyrights.org/data-breaches.
- 8. Shy and Stenbacka, “Customer Privacy and Competition.”
- 9. S. Wilson et al., “Analyzing Privacy Policies at Scale: From Crowdsourcing to Automated Annotations,” ACM Transactions on the Web 13, no. 1 (2018): 1–29. doi:10.1145/3230665
- 10. “Sample Data Protection Policy Template,” https://iapp.org/resources/article/sample-data-protection-policy-template-2/ (accessed June 7, 2019).
- 11. Ibid.
- 12. Bob Siegel, “Privacy Policy or Privacy Notice: What's the Difference?” IDG Contributor Network, May 4, 2016, https://www.csoonline.com/article/3063601/privacy/privacy-policies-and-privacy-notices-whats-the-difference.html.
- 13. Pam Dixon, “A Brief Introduction to Fair Information Practices,” World Privacy Forum, January 4, 2008, https://www.worldprivacyforum.org/2008/01/report-a-brief-introduction-to-fair-information-practices/.
- 14. “The HEW Report: Defining the Fair Information Practices,” CIPP Guide, August 23, 2012, https://www.cippguide.org/2012/08/23/the-hew-report-defining-the-fair-information-practices/.
- 15. “OECD Guidelines on the Protection of Privacy and Transborder Flows of Personal Data,” www.oecd.org/sti/ieconomy/oecdguidelinesontheprotectionofprivacyandtransborderflowsofpersonaldata.htm (accessed June 7, 2019).
- 16. “Data Protection Authorities from over 50 Countries Approve the ‘Madrid Resolution’ on International Privacy Standards,” 31st International Conference of Data Protection and Privacy, Madrid, November 6, 2009, www.privacyconference2009.org/media/notas_prensa/common/pdfs/061109_estandares_internacionales_en.pdf.
- 17. “Comments by the DHS Privacy Office and the Staff of the U.S. Federal Trade Commission on the Joint Proposal for International Standards on the Protection of Privacy with Regard to the Processing of Personal Data,” August 10, 2010, https://www.dhs.gov/xlibrary/assets/privacy/privacy_comments_madrid_resolution_082010.pdf.
- 18. Abu Bakar Munir, “Madrid Resolution: A Step Towards a Privacy Treaty?,” December 29, 2009,http://profabm.blogspot.com/2009/12/another-privacy-standard.html.
- 19. “The History of the General Data Protection Regulation,” European Data Protection Supervisor, https://edps.europa.eu/data-protection/data-protection/legislation/history-general-data-protection-regulation_en (accessed June 7, 2019).
- 20. Brian Fung, “Why You're Getting Flooded with Privacy Notifications in Your Email,” Washington Post, May 25, 2018, https://www.washingtonpost.com/news/the-switch/wp/2018/05/25/why-youre-getting-flooded-with-privacy-notifications-in-your-email/?noredirect=on&utm_term=.56b9d972bfa3.
- 21. “General Data Protection Regulation,” https://gdpr-info.eu/ (accessed June 7, 2019).
- 22. “GDPR Fines and Penalties,” https://www.gdpreu.org/compliance/fines-and-penalties/ (accessed June 7, 2019).
- 23. Ibid.
- 24. Russell Brandom, “Facebook and Google Hit with $8.8 Billion in Lawsuits on Day One of GDPR,” The Verge, May 25, 2018, https://www.theverge.com/2018/5/25/17393766/facebook-google-gdpr-lawsuit-max-schrems-europe.
- 25. James Sanders, “To Save Thousands on GDPR Compliance, Some Companies Are Blocking All EU Users,” Tech Republic, May 7, 2018, https://www.techrepublic.com/article/to-save-thousands-on-gdpr-compliance-some-companies-are-blocking-all-eu-users/.
- 26. Rani Lofstrom, “Securing Your Digital Transformation,” March 6, 2019, https://www.microsoft.com/security/blog/2019/03/06/securing-your-digital-transformation/.
- 27. Alex Scroxton, “Facebook Facing 10 GDPR Investigations in Ireland,” Computer Weekly, March 1, 2019, https://www.computerweekly.com/news/252458664/Facebook-facing-10-GDPR-investigations-in-Ireland.
- 28. Kalev Leetaru, “Facebook's Password Breach Suggests the Public Sees Cybersecurity as Obsolete,” Forbes, March 23, 2019, https://www.forbes.com/sites/kalevleetaru/2019/03/23/facebooks-password-breach-suggests-the-public-sees-cybersecurity-as-obsolete/#7598a3313e24.
- 29. Interview with Scott Renfro. March 21, 2019. “Facebook Stored Hundreds of Millions of User Passwords in Plain Text for Years.” Krebs on Security. https://krebsonsecurity.com/2019/03/facebook-stored-hundreds-of-millions-of-user-passwords-in-plain-text-for-years/
- 30. IAPP, Certified Information Privacy Study Guide, Study Guide edition (CreateSpace Independent Publishing Platform, 2015).
- 31. Swire and Bermann, Information Privacy, 7.
- 32. Fair Credit Reporting Act, 15 U.S.C. §1681, revised September 2018, https://www.ftc.gov/system/files/545a_fair-credit-reporting-act-0918.pdf.
- 33. https://www.hhs.gov/ocr/index.htm.
- 34. Wilson et al., “Analyzing Privacy Policies at Scale.”
- 35. Ibid.
- 36. Ibid.
- 37. “HITECH Act Enforcement Interim Final Rule,” https://www.hhs.gov/hipaa/for-professionals/special-topics/hitech-act-enforcement-interim-final-rule/index.html.
- 38. “What Are the Penalties for HIPAA Violations?” HIPAA Journal, June 25, 2015, https://www.hipaajournal.com/what-are-the-penalties-for-hipaa-violations-7096/.
- 39. Wilson et al., “Analyzing Privacy Policies at Scale.”
- 40. Ibid.
- 41. 940 CMR 27.00: Safeguard of Personal Information, Office of Attorney General Maura Healey, January 22, 2010, https://www.mass.gov/regulations/940-CMR-2700-safeguard-of-personal-information.
- 42. Dipayan Ghosh, “What You Need to Know About California's New Data Privacy Law,” Harvard Business Review, July 11, 2018, https://hbr.org/2018/07/what-you-need-to-know-about-californias-new-data-privacy-law.
- 43. Heather Kelly, “California Passes Strictest Online Privacy Law in the Country,” CNN Business, June 28, 2018, https://money.cnn.com/2018/06/28/technology/california-consumer-privacy-act/index.html.
- 44. Scott Allbert, “CA Consumer Privacy Act,” IG World, June 4, 2019, https://infogovworld.com/ig-topics/ccpa-new-privacy-law/.
- 45. Ibid.
- 46. “APEC Privacy Framework (2015),” Asia-Pacific Economic Cooperation, August 2017, https://www.apec.org/Publications/2017/08/APEC-Privacy-Framework-(2015).
- 47. Douglas B. Laney, Infonomics: How to Monetize, Manage, and Measure Information as an Asset for Competitive Advantage (New York: Taylor & Francis, 2018).
- 48. Shira Scheindlin and Daniel Capra, “The Sedona Conference,” Electronic Discovery and Digital Evidence (Thomson Reuters, 2009), p. 204, www.amazon.com/Scheindlin-Conferences-Electronic-Discovery-Evidence-ebook/dp/B00AUE0LRI.
- 49. “The Global Cost of a Data Breach Is Up in 2018,” https://securityintelligence.com/ponemon-cost-of-a-data-breach-2018/ (accessed December 13, 2018).
- 50. “The 10 Biggest Data Breaches of 2018 … So Far,” July 16, 2018, https://blog.barkly.com/biggest-data-breaches-2018-so-far. .
- 51. “Marriott Data Breach Is Traced to Chinese Hackers as U.S. Readies Crackdown on Beijing,” New York Times, December 11, 2018, https://www.nytimes.com/2018/12/11/us/politics/trump-china-trade.html.
- 52. “Annual Number of Data Breaches and Exposed Records in the United States from 2005 to 2018,” https://www.statista.com/statistics/273550/data-breaches-recorded-in-the-united-states-by-number-of-breaches-and-records-exposed/ (accessed December 13, 2018).
- 53. Jim Finkle, “‘State Actor’ behind Slew of Cyber Attacks,” Reuters, August 3, 2011, www.reuters.com/article/2011/08/03/us-cyberattacks-idUSTRE7720HU20110803.
- 54. Ibid.
- 55. Ibid.
- 56. Ibid.
- 57. Peter Abatan, “Persistently Protecting Your Computer Aided Designs,” Enterprise Digital Rights Management, http://enterprisedrm.tumblr.com/post/1423979379/persistently-protecting-your-computer-aided-designs (accessed August 18, 2011).
- 58. Ari Ruppin, e-mail to author, March 20, 2011.
- 59. Sam Narisi, “IT's Role in Secure Staff Cuts, March 2, 2009, http://www.financetechnews.com/its-role-in-secure-staff-cuts/.
- 60. Ibid.
- 61. Oracle White Paper, “Oracle Information Rights Management 11g—Managing Information Everywhere It Is Stored and Used” (March 2010), www.oracle.com/technetwork/middleware/webcenter/content/irm-technical-whitepaper-134345.pdf, p. 4.
- 62. Ibid.
- 63. Open Web Application Security Project, “Defense in Depth,” https://www.owasp.org/index.php/Defense_in_depth (accessed June 24, 2013).
- 64. HCL, “Identity and Access Management Services,” www.hclisd.com/identity-and-access-management.aspx (accessed September 2, 2011).
- 65. Ibid.
- 66. Ibid.
- 67. Nicola Clark and David Jolly, “Fraud Costs Bank 7.1 Billion,” New York Times, January 25, 2008, www.nytimes.com/2008/01/25/business/worldbusiness/25bank-web.html?hp.
- 68. Oracle White Paper, “Oracle Information Rights Management 11g.”
- 69. Robert Smallwood, “E-DRM Plugs ECM Security Gap,” KM World, April 1, 2008, www.kmworld.com/Articles/News/News-Analysis/E-DRM-plugs-ECM-security-gap-41333.aspx.
- 70. Adi Ruppin, e-mail to author, March 20, 2011.
- 71. Annik Stahl, “Secure Printing: No More Mad Dashes to the Copy Room,” http://office.microsoft.com/en-us/help/secure-printing-no-more-mad-dashes-to-the-copy-room-HA001227631.aspx (accessed August 22, 2011).
- 72. William Broddy, telephone interview by author, August 7, 2011.
- 73. Bill Blake, “WikiLeaks, the Pearl Harbor of the 21st Century,” eDocument Sciences LLC, December 6, 2010, http://edocumentsciences.com/wikileaks-the-pearl-harbor-of-the-21st-century.
- 74. VaporStream, www.vaporstream.com (accessed December 9, 2013).
- 75. Ibid.
- 76. Ibid.
- 77. NIST, “Federal Information Processing Standards Publication,” FIPS PUB 186-3, issued June 2009, http://csrc.nist.gov/publications/fips/fips186-3/fips_186-3.pdf (accessed August 15, 2011). FIPS Publication 186-3 (dated June 2009), was superseded on July 19, 2013 and is provided here only for historical purposes. For the most current revision of this publication, see: http://csrc.nist.gov/publications/PubsFIPS.html.
- 78. Doug Miles, AIIM White Paper, “Digital Signatures – Making the Business Case,” https://www.docusign.com/partner/sharepoint-online-for-cosign-central.
- 79. Computer Desktop Encyclopedia, www.computerlanguage.com (accessed March 30, 2012).
- 80. Doug Miles, AIIM White Paper, “Digital Signatures—Making the Business Case.
- 81. Ibid.
- 82. Ibid.
- 83. Ibid.
- 84. Ari Ruppin, e-mail to author, March 20, 2011.
- 85. “Global Enterprise Data Loss Prevention Market (2018–2023): Industry Trends, Opportunities and Forecasts - CAGR to Grow at 16.28% - ResearchAndMarkets.com,” https://www.businesswire.com/news/home/20180305005642/en/Global-Enterprise-Data-Loss-Prevention-Market-2018-2023
- 86. Fred Donovan, “Gartner: Enterprise Content-Aware Data Loss Prevention Market to Reach $670 Million This Year,” February 7, 2013, www.fierceenterprisecommunications.com/story/gartner-enter-prise-content-aware-data-loss-prevention-market-reach-670-mill/2013-02-07.
- 87. Data Loss Prevention Experts, “DLP Product Guide for RSA Conference Expo 2011,” January 17, 2011, www.dlpexperts.com/dlpxblog/2011/1/17/dlp-product-guide-for-rsa-conference-expo-2011.html.
- 88. Ibid.
- 89. Ibid.
- 90. Ibid.
- 91. Peter Abatan, “Who Should Be Blamed for a Data Breach?” Enterprise Digital Rights Management, February 2011, http://enterprisedrm.tumblr.com/post/1087100940/who-should-be-blamed-for-a-data-breach.
- 92. Peter Abatan, “Understanding Enterprise Rights Management,” Enterprise Digital Rights Management, www.enterprisedrm.info/page/2 (accessed August 3, 2011).
- 93. Robert Smallwood, “Securing Documents in the WikiLeaks Era,” May 28, 2011, www.kmworld.com/Articles/Editorial/Feature/Securing-documents-in-the-WikiLeaks-era-75642.aspx.
- 94. Oracle, “Oracle Information Rights Management 11g—Managing Information Everywhere It Is Stored and Used,” Oracle White Paper, March 2010, https://www.oracle.com/technetwork/middleware/webcenter/content/irm-technical-whitepaper-134345.pdf.
- 95. Abatan, “Understanding Enterprise Rights Management,” http://enterprisedrm.tumblr.com/page/3 (accessed December 9, 2013).
- 96. Ibid.
- 97. Ibid.
- 98. Ibid.
- 99. Ibid.
- 100. This discussion and quotes are from Peter Abatan's blog, “Preparing for Staff Layoffs/Resignations Where Confidential Information Is Concerned,” Enterprise Digital Rights Management (which has been deleted).
- 101. Ibid.
- 102. This discussion and quotes are from Peter Abatan's blog, “Is Your Price List under Lock and Key?” Enterprise Digital Rights Management (which has been deleted).
- 103. This discussion and quotes are from Andrew Jaquith, “Own Nothing—Control Everything: Five Patterns for Securing Data on Devices You Don't Own,” ComputerWeekly.com, September 8, 2010, www.computerweekly.com/Articles/2010/09/10/242661/Own-nothing-control-everything-five-patterns-for-securing-data-on-devices-you-dont.htm.
- 104. This discussion and quotes are from Charlie Pulfer, “Document Labeling in SharePoint,” September 13, 2009
- 105. Ibid.
- 106. Nancy Flynn, The E-Policy Handbook: Rules and Best Practices to Safely Manage Your Company's E-Mail, Blogs, Social Networking, and Other Electronic Communication Tools, 2nd ed. (New York: AMACOM, 2009), 57.
- 107. Ibid., 68–70.
- * Portions of this chapter are adapted from Chapters 11 and 12, Robert F. Smallwood, Safeguarding Critical E-Documents: Implementing a Program for Securing Confidential Information Assets, © John Wiley & Sons, Inc., 2012. Reproduced with permission of John Wiley & Sons, Inc.
