CHAPTER 3
Information Governance Principles
Using guiding principles to drive your information governance (IG) program can help educate stakeholders, focus efforts, and maintain consistency.
The Sedona Conference® Commentary on Information Governance
The Sedona Conference is a group of mostly legal and technology professionals that meets periodically and develops commentary and guidance on e-discovery, electronic records, privacy, risk, IG, and related issues. They have developed 11 general principles of IG,1 which provide guidance on the expectations and aims of IG programs. These principles can further an IG team's understanding of IG and can be used in an introductory “IG Awareness Training” session in the early stages of your program launch. A good exercise is to have team members rewrite these principles in their own words, and then hold discussions about how each of these principles would apply to their departmental IG efforts, and the overall IG program. The Sedona Conference Commentary on IG, formed as principles, are:
- Organizations should consider implementing an IG program to make coordinated decisions about information for the benefit of the overall organization that address information-related requirements and manage risks while optimizing value.
- An IG program should maintain sufficient independence from any particular department or division to ensure that decisions are made for the benefit of the overall organization.
- All information stakeholders should participate in the IG program.
- The strategic objectives of the IG program should be based upon a comprehensive assessment of information-related practices, requirements, risks, and opportunities.
- An IG program should be established with the structure, direction, resources, and accountability to provide reasonable assurance that the program's objectives will be achieved.
- The effective, timely, and consistent disposal of physical and electronic information that no longer needs to be retained should be a core component of any IG program.
- When IG decisions require an organization to reconcile conflicting laws or obligations, the organization should act in good faith and give due respect to considerations such as privacy, data protection, security, records and information management, risk management, and sound business practices.
- If an organization has acted in good faith in its attempt to reconcile conflicting laws and obligations, a court or other authority reviewing the organization's actions should do so under a standard of reasonableness according to the circumstances at the time such actions were taken.
- An organization should consider reasonable measures to maintain the integrity and availability of long-term information assets throughout their intended useful life.
- An organization should consider leveraging the power of new technologies in its IG program.
- An organization should periodically review and update its IG program to ensure that it continues to meet the organization's needs as they evolve.
Smallwood IG Principles
The following 11 IG principles are the result of the author's research and consulting efforts over the past decade or so, where a great deal of practical information on IG program successes, failures, and best practices was synthesized, analyzed, and distilled.
These 11 IG principles must be adhered to as general guidelines for IG programs to succeed:
- Value information as an asset. Just as any organization has physical assets like buildings, furniture, fixtures, equipment, computers, software, and vehicles, and so on, that have value, information collected and analyzed also has value. The formal management of information assets with the goal of monetizing and leveraging that information is clearly outlined in the book Infonomics: How to Monetize, Manage, and Measure Information as an Asset for Competitive Advantage (Bibliomotion/Taylor & Francis, 2018), written by Doug Laney. It is necessary to identify and map out information assets so that confidential information including personally identifiable information (PII), credit card information (PCI), and protected health information (PHI), may be secured directly, so that if hackers are able to get inside the organization's firewall, this information is encrypted and unreadable. The IG steering committee must also explore which analytic tools could help to maximize information value, which may come in the form of reducing uninformed or poor decisions, improving customer satisfaction, improving operational efficiency, reducing legal costs, improving compliance capabilities, and other related benefits. In addition, clear policies must be established for the secure access and use of information, and those policies must be communicated regularly and crisply to employees, with constant reinforcement. This includes conveying the value and risk of information and the consequences of violating IG policies.
- Stakeholder consultation. IG programs are, by nature, cross-functional efforts. Those who work most closely to information are the ones who best know why it is needed and how to manage it, so business units must be consulted in IG policy development. Records and information management (RIM) professionals know the details and nuances of managing records. They should be deeply involved in electronic records management (ERM) and document management governance efforts, which should be at the core of IG. Effective ERM governance also leads to reduced costs and improved operational efficiency. Therefore, RIM professionals must be an active part of IG programs and their input into the policymaking process is critical. RIM professionals must also work hand-in-hand with privacy and legal professionals to ensure customer (and employee) privacy is protected vigilantly. Privacy has become even more important globally with the implementation of Europe's General Data Protection Regulation (GDPR), which applies to any organization conducting business with European citizens, regardless of location. In-house legal council should be a key player in IG programs and the legal team must be consulted on a variety of legal, regulatory, privacy, and litigation issues as IG program efforts involve all these areas. Further, IG programs can cut electronic discovery collection and review costs and make the legal hold notification (LHN) process more streamlined and effective. The IT department must play a major role as technology is leveraged in IG program efforts. The increased level and sophistication of cybersecurity attacks underscores the need for a robust cybersecurity program, including security awareness training (SAT) to offset information risks. It is clear that cross-functional stakeholder consultation is a necessary component of IG programs.
- Information integrity. The business-to-customer relationship is based on trust, and that trust includes ensuring that accurate customer information is created and also kept secure. IG programs focus heavily on information quality, from the ground up, beginning with data governance. Data governance techniques and tools focus on creating clean, accurate, nonduplicate data in database tables so that downstream reports and analyses are more trusted and accurate. Information integrity considers the consistency of methods used to create, retain, preserve, distribute, and track information. Information integrity means there is the assurance that information is accurate, correct, and authentic. From a legal standpoint, enabling information technologies and data stewardship polices must support the effort to meet legal standards of admissibility and preserve the integrity of information to guard against claims that it has been altered, tampered with, or deleted (called “spoliation”). Audit trails must be kept and monitored to ensure compliance with IG policies to assure information integrity.
- Information organization and classification. This means that not only must customer and business operations records be organized in a standardized taxonomy with a specified metadata approach, but that all information must be organized in a standardized way, categorizing all information and semantically linking it to related information. It also means creating a records retention schedule (RRS) that spells out how long the PII/PCI/PHI as well as business information (e.g., e-mail, e-documents, spreadsheets, reports) should be retained and how it is to be disposed of or archived (disposition). Further, it means developing departmental file plans that are logical and help end users to conduct more complete and accurate searches for information.
- Information security and privacy. This again focuses on the trust proposition between customer and the business or governmental agency. Information security must be in place before information privacy can be assured. This means that every attempt must be made to secure PII, PCI, and PHI in all three states: at rest, in motion, and in use. It means that the organization should conduct regular security awareness training, which can include staged phishing and spear phishing attacks to see if employees handle them properly, and to coach them on mistakes they may make during the test. Ransomware is also a problem. When rogue players launch ransomware attacks, they typically encrypt the storage drives of the organization and demand a modest payment by Bitcoin. To offset this risk a complete backup of your entire information system must be made daily and kept separate from your network, offline. Additional cybersecurity hygiene measures are needed to protect information from damage, theft, or alteration by malicious outsiders and insiders as well as nonmalicious (accidental) actions that may compromise information. For instance, an employee may lose a laptop with confidential information, but if proper IG policies are enforced using security-related information technologies, the information can be kept secure. This can be done by access control methods, data or document encryption, deploying information rights management (IRM) software, using remote digital shredding capabilities, and implementing enhanced auditing procedures. Information privacy awareness training (PAT) should also be conducted, including updates on federal, provincial, state, and even possibly municipal legal requirements. Information privacy is closely related to information security and is critical when dealing with confidential information and other sensitive information such as race or religion.
- Information accessibility. Information accessibility must be balanced with information security concerns. Information accessibility includes making the information as simple as possible to locate and access, which involves not only an intuitive user interface but also utilizing enterprise search principles, technologies, and tools. It further includes basic access controls, such as password management, identity and access management (IAM), and delivering information to a variety of hardware devices. Accessibility to information is essential not only in the short term but also over time. Maintaining records for perhaps decades requires consideration of long-term digital preservation (LTDP) planning, tools, and methods in accordance with international, technology-neutral standards. Today, LTDP capabilities can be provided through cloud services providers that keep a number of copies of the information (typically five to six) on Amazon or Microsoft cloud servers, spread around the world, to reduce the risk of loss. There are privacy implications to this global approach, especially with GDPR legislation, and they must be researched.
- Information control. An enterprise RRS is a key foundational element of IG programs. Non-record information must also be categorized and scheduled. Then a standardized, automated LHN process must be put in place to assign data stewards and lock down information that may be requested in legal proceedings. In addition, key information control technologies must be deployed to control the access, creation, updating, and printing of data, documents, and reports. These technologies include several types of software: enterprise content management (ECM) and enterprise file synch and share (EFSS), document management, document analytics, report management, and workflow. Additional security software including encryption should be deployed to protect confidential or sensitive information.
- Information governance monitoring and auditing. Early on in the development of an IG program a concerted effort must be made to develop metrics to objectively measure program progress and employee conformance with IG polices. To ensure that guidelines and policies are being followed, especially regarding customer privacy and cybersecurity hygiene, information access and use must be monitored. To guard against claims of legal spoliation, the use of e-mail, social media, cloud computing, and report generation should be logged (recorded or archived) in real time and maintained as an audit record. Technology tools such as document analytics can track how many documents users access and print and how long they spend doing so.
- Executive sponsorship. Once again, due to the cross-functional, collaborative nature of IG programs, this is the most crucial factor in IG program success. This is especially true in the healthcare arena, where various clinical specialties that may have their own proprietary information systems are represented. No IG effort will survive and be successful if it does not have an accountable, responsible executive sponsor. The sponsor must develop the business case for IG early on, establish a budget, then assemble the steering committee and drive the effort. The executive sponsor must pay periodic attention to the IG program, monitoring progress based on metrics and milestones. The IG program lead, or perhaps even a chief IG officer, manages the IG program on a day-to-day basis, bringing in the executive sponsor only when support is needed for a particular issue. The executive sponsor must clear obstacles for the IG program lead and IG steering committee while actively communicating the goals and business objectives that the IG program addresses, and at the same time keeping upper management informed on progress, particularly when accomplishing milestones.
- Change management. IG programs require leveraging information as an asset and breaking down functional siloed approaches to managing information. IG programs also often involve changing the way users interact with systems to streamline search and retrieval and improve productivity. These changes must be “sold” to the stakeholders, with an emphasis on how the IG program efforts will help the organization achieve its business objectives. These changes must be clearly communicated and reinforced to employees and change must occur at the core of the organization or target department. This all requires that a purposeful change management initiative accompany the IG program implementation.
- Continuous improvement. IG programs are not one-time projects but rather ongoing programs, akin to a workplace safety program. (In fact, the information security aspects of an IG program could actually be termed “information safety.”) The IG program is a major change management effort, which requires a major training and communications effort. Progress in the IG program must be reviewed periodically and adjusted to account for gaps or shortcomings as well as changes in the business environment, technology usage, or business strategy.
Using these 11 principles as guidelines will help to communicate with stakeholders and IG steering committee what IG is, why it is needed, what it involves, and how to fashion an IG program that is successful. It is essential to continually reinforce the importance of these principles during the course of an IG program, and measure how well the organization is doing in these 11 critical areas.
There are also other sets of principles that apply to IG efforts and can help provide a more complete understanding of IG programs, especially early in the IG program development process. These IG principles reflect, reinforce, and expand on the previous set.
Accountability Is Key
According to Debra Logan at Gartner Group, none of the proffered definitions of IG include “any notion of coercion, but rather ties governance to accountability [italics added] that is designed to encourage the right behavior…. The word that matters most is accountability” [italics in the original]. The root of many problems with managing information is the “fact that there is no accountability for information as such.”2
Establishing policies, procedures, processes, and controls to ensure the quality, integrity, accuracy, and security of business records are the fundamental steps needed to reduce the organization's risk and cost structure for managing these records. Then, it is essential that IG efforts are supported by information technologies (IT). The auditing, testing, maintenance, and improvement of IG is enhanced by using electronic records management (ERM) software, along with other complementary technology sets such as workflow and business process management system (BPMS) software and digital signatures.
Generally Accepted Recordkeeping Principles®
Contributed by Charmaine Brooks
A major part of an IG program is managing formal business records. Although they account for only about 7–9% of the total information that an organization holds, they are the most critically important subset to manage, as there are serious compliance and legal ramifications.
Records and recordkeeping are inextricably linked with any organized business activity. Through the information that an organization uses and records, creates, or receives in the normal course of business, it knows what has been done and by whom. This allows the organization to effectively demonstrate compliance with applicable standards, laws, and regulations, as well as plan what it will do in the future to meet its mission and strategic objectives.
Standards and principles of recordkeeping have been developed by records and information management (RIM) practitioners to establish benchmarks for how organizations of all types and sizes can build and sustain compliant, defensible records management (RM) programs.
The Principles
In 2009 ARMA International published a set of eight Generally Accepted Recordkeeping Principles®, known as “The Principles”3 (or sometimes “GAR Principles”) to foster awareness of good recordkeeping practices. These principles and associated metrics provide an information governance (IG) framework that can support continuous improvement.
The eight Generally Accepted Recordkeeping Principles are:
- Accountability. A senior executive (or person of comparable authority) oversees the recordkeeping program and delegates program responsibility to appropriate individuals. The organization adopts policies and procedures to guide personnel, and ensure the program can be audited.
- Transparency. The processes and activities of an organization's recordkeeping program are documented in a manner that is open and verifiable and is available to all personnel and appropriate interested parties.
- Integrity. A recordkeeping program shall be constructed so the records and information generated or managed by or for the organization have a reasonable and suitable guarantee of authenticity and reliability.
- Protection. A recordkeeping program shall be constructed to ensure a reasonable level of protection to records and information that are private, confidential, privileged, secret, or essential to business continuity.
- Compliance. The recordkeeping program shall be constructed to comply with applicable laws and other binding authorities, as well as the organization's policies.
- Availability. An organization shall maintain records in a manner that ensures timely, efficient, and accurate retrieval of needed information.
- Retention. An organization shall maintain its records and information for an appropriate time, taking into account legal, regulatory, fiscal, operational, and historical requirements.
- Disposition. An organization shall provide secure and appropriate disposition for records that are no longer required to be maintained by applicable laws and the organization's policies.”4
The Generally Accepted Recordkeeping Principles apply to all sizes of organizations, in all types of industries, and in both the private and public sectors, and can be used to establish consistent practices across business units. The Principles are an IG maturity model and this is used as a preliminary evaluation of recordkeeping programs and practices.
Interest and the application of The Principles for assessing an organization's recordkeeping practices have steadily increased since its establishment. It is an accountability framework that includes the processes, roles, standards, and metrics that ensure the effective and efficient use of records and information in support of an organization's goals and business objectives.
As shown in Table 3.1, the Generally Accepted Recordkeeping Principles maturity model associates characteristics that are typical in five levels of recordkeeping capabilities that range from 1 (substandard) to 5 (transformational). The levels are both descriptive and color coded for ease of understanding. The eight principles and levels (metrics) are applied to the current state of an organization's recordkeeping capabilities and can be cross-referenced to the policies and procedures. While it is not unusual for an organization to be at differing levels of maturity in the eight principles, the question “How good is good enough?” must be raised and answered; a rating of less than “transformational” may be acceptable, depending on the organization's tolerance for risk and an analysis of the costs and benefits of moving up each level.
Table 3.1 Generally Accepted Recordkeeping Principles Levels
Source: Based on data from ARMA.
| Level 1 Substandard |
Characterized by an environment where recordkeeping concerns are either not addressed at all or are addressed in an ad hoc manner. |
| Level 2 In Development |
Characterized by an environment where there is a developing recognition that recordkeeping has an impact on the organization, and the organization may benefit from a more defined information governance program. |
| Level 3 Essential |
Characterized by an environment where defined policies and procedures exist that address the minimum or essential legal and regulatory requirements, but more specific actions need to be taken to improve recordkeeping. |
| Level 4 Proactive |
Characterized by an environment where information governance issues and considerations are integrated into business decisions on a routine basis, and the organization consistently meets its legal and regulatory obligations. |
| Level 5 Transformational |
Characterized by an environment that has integrated information governance into its corporate infrastructure and business processes to such an extent that compliance with program requirements is routine. |
The maturity levels define the characteristics of evolving and maturing records management programs. The assessment should reflect the current RM environment and practices. The principles and maturity level definitions, along with improvement recommendations (roadmap), outline the tasks required to proactively approach addressing systematic records management practices and reach the next level of maturity for each principle. While the Generally Accepted Recordkeeping Principles are broad in focus, they illustrate the requirements of good records management practices. The Principles Assessment can also be a powerful communication tool to promote cross-functional dialogue and collaboration among business units and staff.
Accountability
The principle of accountability covers the assigned responsibility for RM at a senior level to ensure effective governance with the appropriate level of authority. A senior-level executive must be high enough in the organizational structure to have sufficient authority to operate the records management program effectively. The primary role of the senior executive is to develop and implement records management policies, procedures and guidance, and to provide advice on all record-keeping issues. The direct responsibility for managing or operating facilities or services may be delegated.
The senior executive must possess an understanding of the business and legislative environment within which the organization operates; business functions and activities; and the required relationships with key external stakeholders. This person must also understand how records management contributes to achieving the corporate mission, aims, and objectives.
It is important for top-level executives to take ownership of the records management issues of the organization identifying corrective actions required for mitigation or ensuring resolution of problems and recordkeeping challenges. An executive sponsor should identify opportunities to raise awareness of the relevance and importance of RM and effectively communicate the benefits of good records management to staff and management.
The regulatory and legal framework for records management must be clearly identified and understood. The senior executive must have a sound knowledge of the organization's information and technological architecture and actively participate in strategic decisions for information technology systems acquisition and implementation.
The senior executive is responsible for ensuring the processes, procedures, governance structures, and related documentation are developed. The policies should identify the roles and responsibilities at all levels of the organization.
An audit process must be developed to cover all aspects of RM within the organization, including substantiating that sufficient levels of accountability have been assigned and accountability deficiencies are identified and remedied. Audit processes should include compliance with the organization policies and procedures for all records, regardless of format or media. Accountability audit requirements for electronic records include employing appropriate technology to audit the information architecture and systems. Accountability structures must be updated and maintained as changes occur in the technology infrastructure.
The audit process must reinforce compliance and hold individuals accountable. The results should be constructive, encourage continuous improvement, but not be used as a means of punishment. The audit should contribute to records program improvements in risk mitigation, control, and governance issues, and have the capacity to support sustainability.
Transparency
Policies are broad guidelines for the operation of the organization and provide a basic guide to action that prescribes the boundaries within which business activities are to take place. They state the course of action to be followed by the organization, business unit, department, and employees.
Transparency of recordkeeping practices includes documenting processes and promoting an understanding of the roles and responsibilities of all stakeholders. To be effective, policies must be formalized and integrated into business processes. Business rules and recordkeeping requirements need to be communicated and socialized at all levels of the organization.
Senior management must recognize that transparency is fundamental to IG and compliance. Documentation must be consistent, current, and complete. A review and approval process must be established to ensure the introduction of new programs or changes can be implemented and integrated into business processes.
Employees must have ready access to RM policies and procedures. They must receive guidance and training to ensure they understand their roles and requirements for records management. Recordkeeping systems and business processes must be designed and developed to clearly define the records lifecycle.
In addition to policies and procedures, the development of guidelines and operational instructions, diagrams and flowcharts, system documentation, and user manuals must include clear guidance on how records are to be created, retained, stored, and dispositioned. The documentation must be readily available and incorporated in communications and training provided to staff.
Integrity
Record-generating systems and repositories must be assessed to determine recordkeeping capabilities. A formalized process must be in place for acquiring or developing new systems, including requirements for capturing the metadata required for lifecycle management of records in the systems. In addition, the record must contain all the necessary elements of an official record, including structure, content, and context. Records integrity, reliability, and trustworthiness are confirmed by ensuring that a record was created by a competent authority according to established processes.
Maintaining the integrity of records means that they are complete and protected from being altered. The authenticity of a record is ascertained from internal and external evidence, including the characteristics, structure, content, and context of the record to verify they are genuine and not corrupted or altered. In order to trust that a record is authentic, organizations must ensure that recordkeeping systems that create, capture, and manage electronic records are capable of protecting records from accidental or unauthorized alteration or deletion while the record has value.
Protection
Organizations must ensure the protection of records and ensure they are unaltered through loss, tampering, or corruption. This includes technological change or the failure of digital storage media and protecting records against damage or deterioration.
This principle applies equally to physical and electronic records, each having unique requirements and challenges.
Access and security controls need to be established, implemented, monitored, and reviewed to ensure business continuity and minimize business risk. Restrictions on access and disclosure include the methods for protecting personal privacy and proprietary information. Access and security requirements must be integrated into the business systems and processes for the creation, use, and storage of records.
Long-term digital preservation (LTDP) is a series of managed activities required to ensure continued access to digital materials for as long as necessary. Electronic records requiring long-term retention may require conversion to a medium and format suitable to ensure long-term access and readability. Cloud-based services for file conversion and long-term storage have emerged that have simplified the LTDP process and made it more affordable for organizations.
Compliance
Records management programs include the development and training of the fundamental components, including compliance monitoring to ensure sustainability of the program.
Monitoring for compliance involves reviewing and inspecting the various facets of records management, including ensuring records are being properly created and captured, implementation of user permissions and security procedures, work flow processes through sampling to ensure adherence to policies and procedures, ensuring records are being retained following disposal authorities, and documentation of records destroyed or transferred to determine whether destruction/transfer was authorized in accordance with disposal instructions.
Compliance monitoring can be carried out by an internal audit, external organization, or records management and must be done on a regular basis.
Availability
Organizations should evaluate how effectively and efficiently records and information are stored and retrieved using present equipment, networks, and software. The evaluation should identify current and future requirements and recommend new systems as appropriate. Certain factors should be considered before upgrading or implementing new systems. These factors are practicality, cost, and effectiveness of new configurations.
A major challenge for organizations is ensuring that timely and reliable access to and use of information and records are accessible and usable for the entire length of the retention period. Rapid changes and enhancements to both hardware and software compound this challenge.
Retention
Retention is the function of preserving and maintaining records for continuing use. The records retention schedule identifies the actions needed to fulfill the requirements for the retention and disposal of records and provides the authority for employees and systems to retain, destroy, or transfer records. The records retention schedule documents the recordkeeping requirements and procedures, identifying how records are to be organized and maintained, what needs to happen to records and when, who is responsible for doing what, and who to contact with questions or guidance.
Organizations must identify the scope of their recordkeeping requirements for documenting business activities based on regulated activities and jurisdictions that impose control over records. This includes business activities regulated by the government for every location or jurisdiction in which you do business. Other considerations for determining retention requirements include operational, legal, fiscal, and historical.
Records appraisal is the process of assessing the value and risk of records to determine their retention and disposition requirements. Legal research is outlined in appraisal reports. This may be accomplished as a part of the process of developing the records retention schedules, as well as conducting a regular review to ensure that citations and requirements are current.
The records retention period is the length of time that records should be retained and the actions taken for them to be destroyed or preserved. The retention periods for different records should be based on legislative or regulatory requirements as well as on administrative and operational requirements. It is important to document the legal research conducted and used to determine whether the law or regulation has been reasonably applied to the recordkeeping practices and provide evidence to regulatory officials or courts that due diligence has been conducted in good faith to comply with all applicable requirements.
Disposition
Disposition is the last stage in the information life cycle. When the retention requirements have been met and the records no longer serve a useful business purpose, they may be destroyed. Records requiring long-term or permanent retention should be transferred to an archive for preservation. The timing of the transfer of physical or electronic records should be determined through the records retention schedule process. Additional methods are often required to preserve electronic records, which may include migration or conversion.
Records must be destroyed in a controlled and secure manner and in accordance with authorized disposal instructions. The destruction of records must be clearly documented to provide evidence of destruction according to an agreed-on program.
Destruction of records must be undertaken by methods appropriate to the confidentiality of the records and in accordance with disposal instructions in the records retention schedule. An audit trail documenting the destruction of records should be maintained and certificates of destruction obtained for destruction undertaken by third parties. In the event disposal schedules are not in place, the written authorization should be obtained prior to destruction. Procedures should specify who must supervise the destruction of records. Approved methods of destruction must be specified for each media type to ensure that information cannot be reconstructed.
Disposition is not synonymous with destruction, though destruction may be one disposal option. Destruction of records must be carried out under controlled, confidential conditions by shredding or permanent disposition. This includes the destruction of confidential microfilm, microfiche, computer cassettes, and computer tapes, as well as paper.
Methods of Disposition
- Discard. The standard destruction method for nonconfidential records. If possible, all records should be shredded prior to recycling. Note that transitory records can also be shredded.
- Shred. Confidential and sensitive records should be processed under strict security. This may be accomplished internally or by secure on-site shredding by a third-party vendor who provides certificates of secure destruction. The shredded material is then recycled.
- Archive. This designation is for records requiring long-term or permanent preservation. Records of enduring legal, fiscal, administrative, or historical value are retained.
- Imaging. Physical records converted to digital images, after which the original paper documents are destroyed.
- Purge. This special designation is for data, documents, or records sets that need to be purged by removing material based on specified criteria. This often applies to structure records in databases and applications.
Assessment and Improvement Roadmap
The Generally Accepted Recordkeeping Principles maturity model can be leveraged to develop a current state assessment of an organization's recordkeeping practices and resources, identify gaps and assess risks, and develop priorities for desired improvements.
The Principles were developed by ARMA International to identify characteristics of an effective recordkeeping program. Each of the eight principles identifies issues and practices that, when evaluated against the unique needs and circumstances of an organization, can be applied to improvements for a recordkeeping program that meets recordkeeping requirements. The principles identify requirements and can be used to guide the incremental improvement in the management and governance of the creation, organization, security, maintenance, and other activities over a one- to five-year period. Fundamentally, records management and information governance are business disciplines that must be tightly integrated with operational policies, procedures, and infrastructure.
The Principles can be mapped to the four improvement areas in Table 3.2.
As an accepted industry guidance maturity model, The Principles provide a convenient and complete framework for assessing the current state of an organization's recordkeeping and developing a roadmap to identify improvements that will bring the organization into compliance. An assessment/analysis of the current record management practices, procedures, and capabilities together with current and future state practices provides two ways of looking at the future requirements of a complete RM (see Table 3.3).
Table 3.2 Improvement Areas for Generally Accepted Recordkeeping Principles
| Improvement Area | Accountability | Transparency | Integrity | Protection | Compliance | Availability | Retention | Disposition |
| Roles and responsibilities | ◊ | ◊ | ◊ | |||||
| Policies and procedures | ◊ | ◊ | ◊ | ◊ | ◊ | ◊ | ◊ | ◊ |
| Communication and training | ◊ | ◊ | ◊ | ◊ | ◊ | |||
| Systems and automation | ◊ | ◊ | ◊ | ◊ | ◊ | ◊ |
Table 3.3 Assessment Report and Roadmap
| Principle | Level | Findings | Requirements to Move to the Next Step |
| Accountability | Level 1 Substandard |
|
|
| Transparency | Level 1 Substandard |
|
|
| Integrity | Level 1 Substandard |
|
|
| Protection | Level 1 Substandard |
|
|
| Compliance | Level 3 Essential |
|
|
| Availability | Level 2 In Development |
|
|
| Retention | Level 2 In Development |
|
|
| Disposition | Level 2 In Development |
|
|
| Overall | Level 1 Substandard |
Information Security Principles
The information security aspects of your IG program should be guided by established principles.
Principle of Least Privilege
The Principle of Least Privilege (POLP) is an important cybersecurity maxim that means users should only be given access to the bare minimum permissions and information needed to do their job.5 Under POLP, users are only given access to the files needed to perform their job function. POLP should be used to control who has access to which information, on which devices, and when.
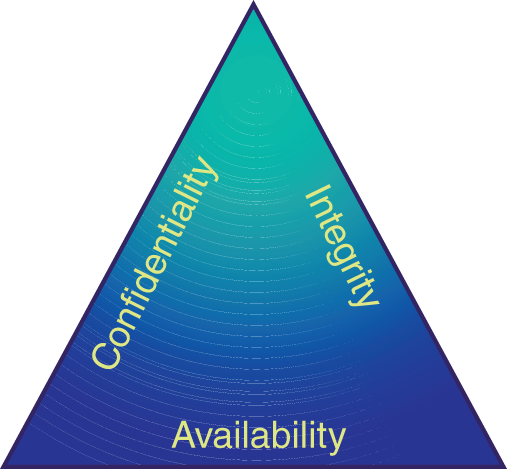
The CIA Triad
The CIA triad (sometimes referred to as the AIC triad to avoid confusion with the US government spy agency) depicts the three “most crucial components” of information security.6
Confidentiality (roughly equivalent to Generally Accepted Recordkeeping Principle® #4, Protection) means that access to private and sensitive is tightly controlled so that only authorized personnel have access to it. Integrity (the same as GAR Principle® #3) means that information has a reasonable assurance of being accurate, reliable, and trusted, throughout its lifecycle. Availability (the same as GAR Principle® #6) is the concept that information can be reliably and consistently accessed and retrieved by authorized employees, which requires software patches and updates are implemented in a timely way, and that hardware is maintained regularly.
Privacy Principles
The Generally Accepted Privacy Principles (GAPP) were developed jointly by the Canadian Institute of Chartered Accountants (CICA) and the American Institute of Certified Public Accountants (AICPA) through the AICPA/CICA Privacy Task Force. These principles can be used to guide the privacy aspects of an IG program. The field of information privacy is rapidly changing, and the International Association of Privacy Professionals (IAPP) is quite active globally with conferences, workshops, and training. IAPP's membership exploded in 2017–2018, when GDPR came into effect. Nevertheless, the 10 Generally Accepted Privacy Principles have been accepted by the privacy profession. The 10 Generally Accepted Privacy Principles and their criteria are:7
- Management
- The organization defines, documents, communicates, and assigns accountability for its privacy policies and procedures.
- Criteria:
- Privacy policies define and document all 10 GAPP.
- Review and approval of changes to privacy policies are conducted by management.
- Risk assessment process is in place to establish a risk baseline and regularly identify new or changing risks to personal data.
- Infrastructure and systems management take into consideration impacts on personal privacy.
- Privacy awareness training
- Notice
- The organization provides notice of its privacy policies and procedures. The organization identifies the purposes for which personal information is collected, used, and retained.
- Criteria:
- Communication to individuals
- Provision of notice
- Use of clear and conspicuous language
- Choice and consent
- The organization describes the choices available to the individual. The organization secures implicit or explicit consent regarding the collection, use, and disclosure of the personal data.
- Criteria:
- Communicating the consequences of denying/withdrawing consent
- Consent for new purposes/uses of the personal data
- Explicit consent for sensitive data
- Consent for online data transfer
- Collection
- Personal information is only collected for the purposes identified in the notice (see #2).
- Criteria:
- Document and describe types of information collected and methods of collection
- Collection of information by fair and lawful means, including collection from third parties
- Inform individuals if information is developed or additional information is acquired
- Use, retention, and disposal
- The personal information is limited to the purposes identified in the notice the individual consented to. The organization retains the personal information only for as long as needed to fulfill the purposes, or as required by law. After this period, the information is disposed of appropriately.
- Criteria:
- Systems and procedures in place to ensure personal information is used, retained, and disposed appropriately
- Access
- The organization provides individuals with access to their personal information for review or update.
- Criteria:
- Confirmation of individual's identity before access is given to personal information
- Personal information presented in understandable format
- Access provided in reasonable time frame and at a reasonable cost
- Statement of disagreement; the reason for denial should be explained to individuals in writing
- Disclosure to third parties
- Personal information is disclosed to third parties only for the identified purposes and with implicit or explicit consent of the individual.
- Criteria:
- Communication with third parties should be made known to the individual.
- Information should only be disclosed to third parties that have equivalent agreements to protect personal information.
- Individuals should be aware of any new uses/purposes for the information
- The organization should take remedial action in response to misuse of personal information by a third party.
- Security for privacy
- Personal information is protected against both physical and logical unauthorized access.
- Criteria:
- Privacy policies must address the security of personal information.
- Information security programs must include administrative, technical, and physical safeguards.
- Logical access controls in place
- Restrictions on physical access
- Environmental safeguards
- Personal information is protected when being transmitted (e.g. mail, Internet, public, or other nonsecure networks).
- Security safeguards should be tested for effectiveness at least once annually.
- Quality
- The organization maintains accurate, complete, and relevant personal information that is necessary for the purposes identified.
- Criteria:
- Personal information should be relevant for the purposes it is being used.
- Monitoring and enforcement
- The organization monitors compliance with its privacy policies and procedures. It also has procedures in place to address privacy-related complaints and disputes.
- Criteria:
- Individuals should be informed on how to contact the organization with inquiries, complaints, and disputes.
- Formal process is in place for inquires, complaints, or disputes.
- Each complaint is addressed and the resolution is documented for the individual.
- Compliance with privacy policies, procedures, commitments, and legislation is reviewed, documented, and reported to management.
Source: American Institute of Certified Public Accountants, https://www.aicpa.org/InterestAreas/InformationTechnology/Resources/PRIVACY/DownloadableDocuments/10252-346_Records%20Management-PRO.pdf.
These 10 privacy principles can be applied by organizations to establish and maintain the privacy aspects of their IG programs.
Utilizing the various sets of complementary IG principles to help educate stakeholders and guide the IG program will help to keep the scope of the program focused by providing some guidelines to keep it on track that help assure the success of the program.
Who Should Determine IG Policies?
When forming an IG steering committee or board, it is essential to include representatives from cross-functional groups, and at differing levels of the organization. It must be driven by an executive sponsor (see later chapter on securing and managing executive sponsorship), and include active members from key business units, as well as other departments or functions including privacy, cybersecurity, IT, legal, risk management, compliance, records management, and possibly finance. Then, corporate training/education and communications must be involved to keep employees trained and current on IG policies. This function may be performed by an outside consulting firm if there is no corporate education staff.
Knowledge workers, those who work with records and sensitive information in any capacity, best understand the nature and value of the records they work with as they perform their day-to-day functions. IG policies must be developed and also communicated clearly and consistently. Policies are worthless if people do not know or understand them, or how to comply. And training is a crucial element that will be examined in any compliance hearing or litigation that may arise. “Did senior management not only create the policies, but provide adequate training on them, on a consistent basis?” This will be a key question raised. For these reasons, a training plan is a necessary piece of IG, and education should be heavily emphasized.8
The need for IG is increasing due to increased and tightened regulations, increased litigation, increased data volumes, and the increased incidence of theft and misuse of internal documents and records. Organizations that do not have active IG programs should reevaluate IG policies and their internal processes following any major loss of records, the inability to produce accurate records in a timely manner, or any document security breach or theft. If IG teams include a broad cross-section of critical players on the IG committee, and strong executive sponsorship, they will be better preparing the organization for legal and regulatory rigors, as well as unlocking new value in their information.
Notes
- 1. https://thesedonaconference.org/publication/The%20Sedona%20Conference%C2%AE%20Commentary%20on%20Information%20Governance (accessed October 14, 2017).
- 2. Debra Logan, “What Is Information Governance? And Why Is It So Hard?” posted January 11, 2010, http://blogs.gartner.com/debra_logan/2010/01/11/what-is-information-governance-and-why-is-it-so-hard/.
- 3. ARMA International, Generally Accepted Recordkeeping Principles, www.arma.org/garp/copyright.cfm (accessed May 8, 2012).
- 4. ARMA International, Information Governance Maturity Model, www.arma.org/garp/Garp%20maturity%20Model%20Grid%20(11x23).pdf (accessed June 12, 2012).
- 5. http://searchsecurity.techtarget.com/definition/principle-of-least-privilege-POLP (accessed March 12, 2018).
- 6. http://whatis.techtarget.com/definition/Confidentiality-integrity-and-availability-CIA (accessed March 12, 2018).
- 7. https://www.cippguide.org/2010/07/01/generally-accepted-privacy-principles-gapp/ (accessed October 31, 2017).
- 8. “Governance Overview (SharePoint Server 2010),” http://technet.microsoft.com/en-us/library/cc263356.aspx (accessed April 19, 2011).
