Chapter 11: Implementing Cryptographic Protocols and Algorithms
Securing enterprise networks relies on a strategy called defense in depth. One very important part of defense in depth is protecting data in many different states, primarily at rest, in transit, and in use. When confidentiality is required, we can apply encryption to sensitive data to ensure we can protect that data. In some cases, we must be able to verify the integrity of the data using hashing and signing.
Cryptography can be a daunting subject area for IT professionals, with algorithms consisting of highly complex mathematical ciphers. The job of IT professionals and management is to ask the right questions and ensure the correct standards and protocols have been enabled. Regulatory authorities may have very strict requirements when using cryptographic ciphers to protect data that an enterprise will store, process, and transmit. It is the job of security professionals to ensure the correct configuration and deployment is provided for the appropriate technology.
In this chapter, we will cover the following topics:
- Understanding hashing algorithms
- Understanding symmetric encryption algorithms
- Understanding asymmetric encryption algorithms
- Understanding encryption protocols
- Understanding emerging security technologies
Understanding hashing algorithms
Hashing algorithms are primarily used to validate the integrity of data, though they can also be used to prove that you know something, such as a password secret. Hashing is a one-way process (it is unfeasible to reverse a hash) and does not provide confidentiality for the data. It is important to understand that the original data is not changed in any way. Think of hashing as a way to create a unique digital checksum for a particular document, file, or data payload. Hashing is used for File Integrity Monitoring (FIM), where we can detect if a protected operating system file has been altered. Hashing can be used in digital forensics to capture a unique checksum of a copy image, to match it with the original (this is useful to do before analysts begin the forensic investigation). For security professionals, it is important to understand what would be considered strong and what would represent weak implementations of hashing algorithms. Strong or resilient hashing will generate a larger digest (hash) output, while weak algorithms will generate a small digest (hash) output. Now, let's look at some examples.
Secure Hashing Algorithm (SHA)
SHA is the standard that's used by most commercial and government departments. It is a family of hash functions that was originally published by the National Institute of Standards and Technology (NIST) in 1993. This was approved for use and is documented in Federal Information Processing Standards (FIPS) PUB 180-1.
SHA-1 is a 160-bit cryptographic hash function that creates the same fixed-size output of 40 bytes (or characters). SHA-1 was deprecated in most cryptographic suites around 2010.
SHA-2 is a family of cryptographic hash functions that was approved under FIPS PUB 180-2. It covers the following hash functions:
- SHA-224
- SHA-256
- SHA-384
- SHA-512
It is worth noting that SHA-2 is still the preferred option for most operating systems. Windows operating systems, default tools, and utilities are based around SHA-2
SHA-3 is a family of cryptographic hash functions defined in FIPS PUB 202. The output size in bits is the same as SHA-2 (224, 256, 384, and 512) but uses a SHA-3 descriptor before the hash function. Most Linux/Unix distributions come with hashing utilities. In the following command, we have used a Linux Bash shell command to generate a hash to verify whether the bootstrap log has been tampered with:
sha256sum bootstrap.log
The output of this command is as follows:
1709de6f628968c14d3eed2f306bef4f39e4ab036e51386a59a487ec0
e4213fe bootstrap.log
Windows comes with a Command Prompt utility called CERTUTIL -HASHFILE <Filename>.
We can use this command to capture a hash value for the Windows operating system's kernel file:
certutil -hashfile ntoskrnl.exe sha256
The output of this command is as follows:
SHA256 hash of ntoskrnl.exe:
4ffa3d9c8a12bf45c4de8540f42d460bc2f55320e63caac4fdfabb
b384720b40
Windows PowerShell can also be used to generate hash values. The format is Get-Filehash <Filename> -Algorithm <hashtype>:
Get-FileHash ntoskrnl.exe -Algorithm SHA256
The output of this command is as follows:
Algorithm Hash
--------- ----
SHA256 4FFA3D9C8A12BF45C4DE8540F42D460BC2F55320E6
3CAAC4FDFABBB384720B40
To address both integrity and authentication for a packet, we can use hash functions and a shared secret.
Hash-Based Message Authentication Code (HMAC)
HMAC, often referred to as simply MAC, allows a packet to be authenticated as well as checked for integrity. It will use a secret key, known by both the sender and the receiver, to be used with a hash function to create a unique MAC. The following flowchart shows the process of generating an HMAC and verifying it on the receiving host:
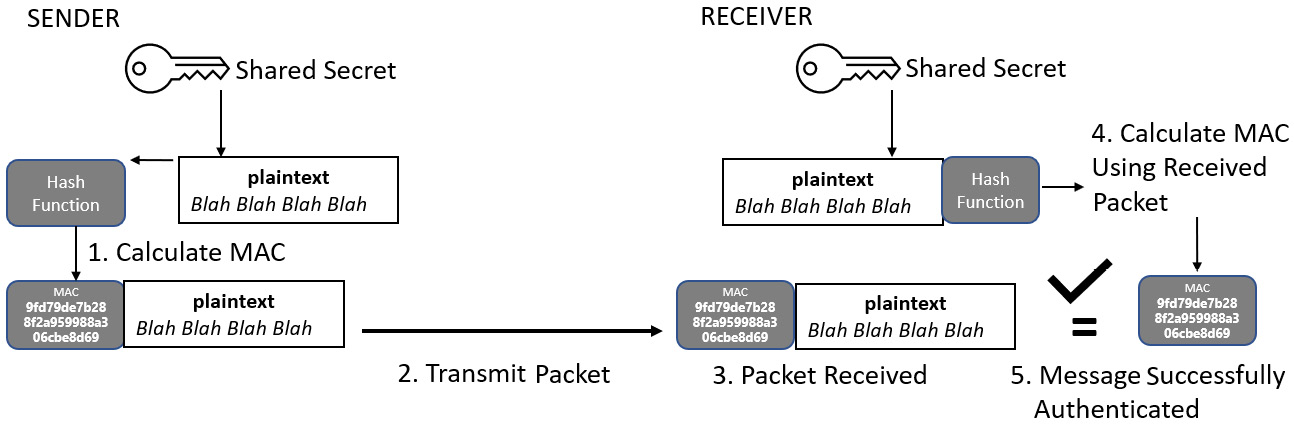
Figure 11.1 – HMAC
Please note that an HMAC provides no confidentiality for the payload; it only authenticates the packets. It does not replace a digital signature, which is used for non-repudiation.
Message Digest (MD)
The Message Digest (MD) hash function was originally published in 1989 as MD2 and was developed by Ronald Rivest. There were several updates, culminating in MD5. It has been in common use up until around 2008. It is now considered vulnerable to exploitation, including hash collisions. A hash collision is where two different inputs create an identical hash output. An attacker may replace a genuine file or document with a modified substitute that exhibits the same hash output.
RACE integrity primitives evaluation message digest (RIPEMD)
RIPEMD provides a family of hash functions. The supported functions include RIPEMD, RIPEMD-128, RIPEMD-160, RIPEMD-256, and RIPEMD-320.
RIPEMD is not used in government or many commercial applications but can be found within academic environments and some products where government approval is not important.
Hashing is very useful for providing integrity but does not allow you to protect data through confidentiality. For confidentiality, we must use symmetric and asymmetric encryption.
Understanding symmetric encryption algorithms
Symmetric encryption provides confidentiality by provisioning bulk encryption. It is highly efficient at encrypting data at rest and data in transit. Due to the relatively small key sizes that are used, it is very fast (in comparison to asymmetric encryption). Symmetric encryption uses a single key to encrypt (or lock) the data and the same key is used to decrypt (unlock) the data.
Symmetric algorithms are divided into two main categories: block and stream ciphers.
Block ciphers
These ciphers are used to encrypt data in blocks, typically 64 or 128 bits. They offer the most robust security but lack the outright speed that's offered by stream ciphers. The following are some examples of block ciphers:
- Triple Digital Encryption Standard (3DES): 3DES replaced the original Data Encryption Standard (DES), which was designed and adopted in the 1970s. DES offered a key size of only 64 bits (56 bits for the key itself). In 1999, 3DES became the new standard, while an alternative was being developed. 3DES can be implemented in several different ways, but the most secure is by using three separate keys. 3DES has an effective key size of 168 bits. NIST guidance stipulates that 3DES will be retired by 2023.
- Advanced Encryption Standard (AES): AES is the official standard that's used in government and military environments; it is also widely adopted in the commercial world. It was approved for use in 2001 after being accepted as the best candidate from several alternate ciphers (including Blowfish and Twofish). It meets government standards as it is FIPS-140 PUB compliant, which describes software and hardware security implementations. FIPS PUB 197 documents the actual details of the AES protocol standard. AES can be implemented with key sizes of 128, 192, and 256. There are additional recommendations when using AES, specifically the block cipher modes that should be implemented. When used for BitLocker Drive Encryption, NIST recommends using XTS-AES cipher mode. For more information, please see https://tinyurl.com/nist800-38e.
Block ciphers are the mainstay of symmetric encryption algorithms, but we must also look at fine-tuning when using these algorithms. Symmetric ciphers can be deployed using specific modes of operation.
Block cipher modes of operation
Block ciphers can be deployed using specific modes of operation. It is important for security professionals to understand the security implications of these different modes. There are also performance considerations we must respect when selecting a block cipher mode. Let's look at the available choices.
Electronic Code Book (ECB)
ECB is the oldest example of a block cipher mode and originates from the original DES implementation. ECB uses the same cipher for each block of data. The following diagram shows the process of encrypting plaintext with the same cipher to generate ciphertext:
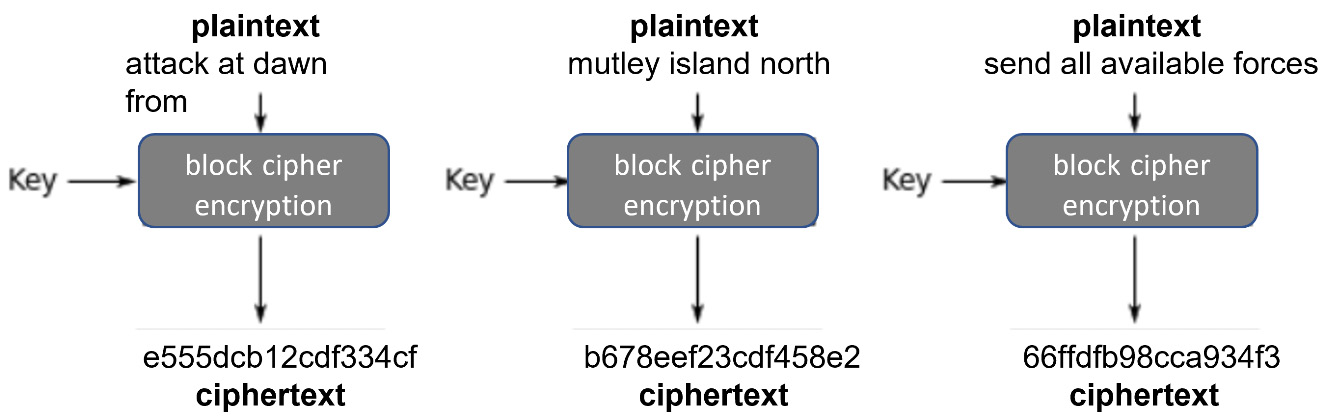
Figure 11.2 – ECB mode
Imagine that you are encrypting a 1,000-page document and that each line on every page is encrypted using the same key. If the ciphertext is subjected to scrutiny using statistical analysis, then patterns can be seen.
In the following figure, we can see an example of an image that has been encrypted using ECB mode. Discernable color patterns are evident due to the repeated use of the same cipher:
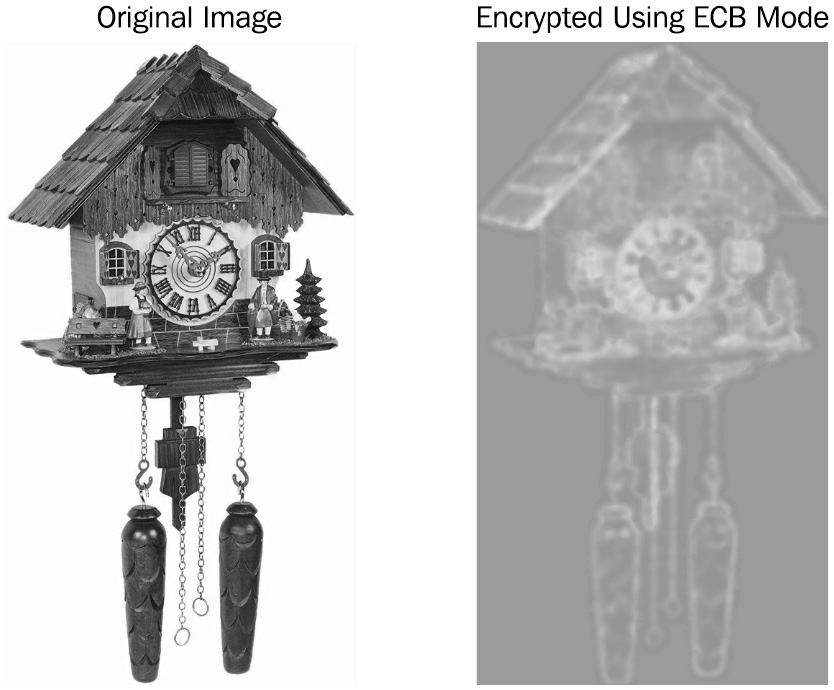
Figure 11.3 – ECB cipher weakness
In this example, if there is a discernable pattern, it will be identified by cryptanalysts.
Cipher block chaining (CBC)
CBC dates back to the mid-1970s, so it is fairly mature. By using CBC mode, every plaintext block is encrypted using a unique cipher. The first block is encrypted using a random Initialization Vector (IV), along with the key. The ciphertext becomes the IV for the next block of plaintext data. The following diagram shows the CBC process:
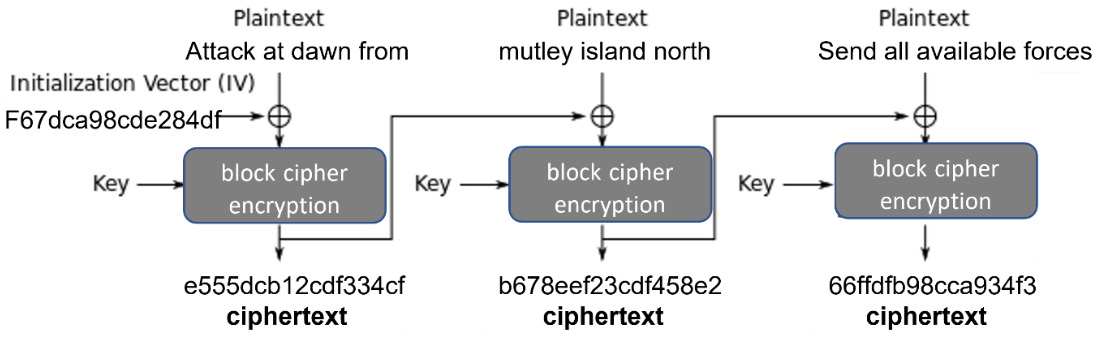
Figure 11.4 – CBC mode
CBC mode operates sequentially, which means it offers no options to improve performance by using parallel processing. Newer block ciphers offer better performance
Output feedback (OFB)
OFB enables a block cipher to behave like a stream cipher. As the cipher can be calculated before the next plaintext is encrypted, it allows the next step to run in parallel. This offers performance advantages over older block ciphers. The following diagram shows how OFB mode operates:
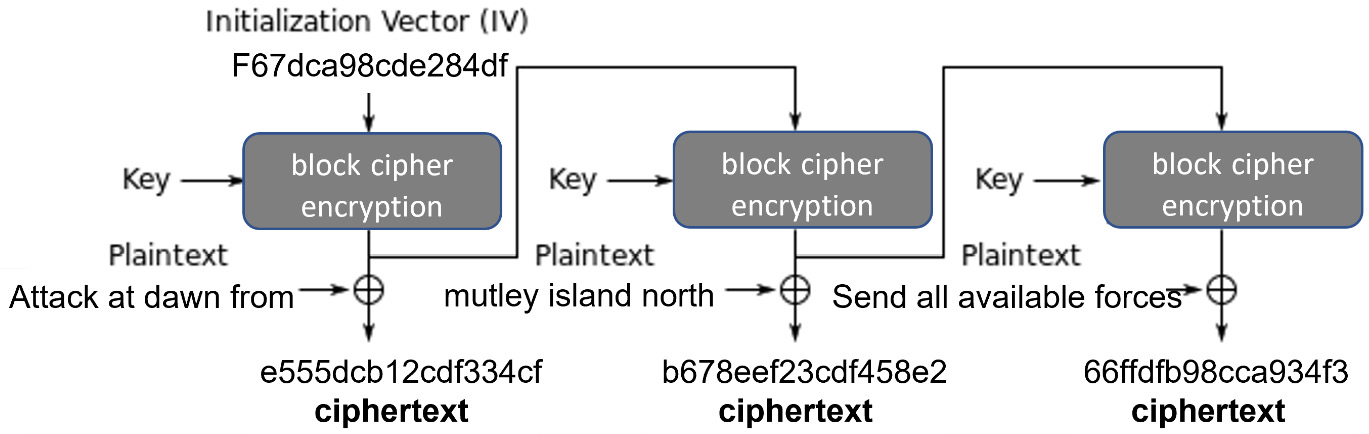
Figure 11.5 – OFB mode
Note that OFB is unlikely to be selected as there are newer blockchain ciphers that offer better performance.
Counter (CTR)
CTR mode also offers a performance advantage over legacy blockchain ciphers. It allows a block cipher to act as a stream cipher by preparing the cipher before the plaintext is encrypted. As there is no need to wait for each block of plaintext to be encrypted (it plays no part in the following cipher), then powerful multi-processor systems can take advantage of the parallel processing of blocks.
The following diagram shows an example of CTR mode:
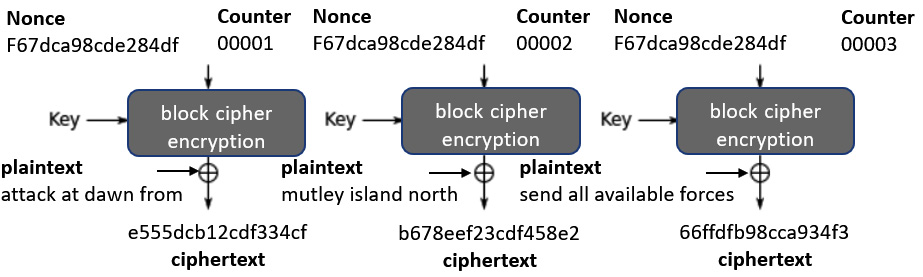
Figure 11.6 – CTR mode
CTR mode has been largely superseded by block ciphers, which offer this performance advantage along with authenticity.
Galois Counter Mode (GCM)
GCM is the default block cipher mode for many implementations of SSL/TLS. It combines the advantages of CTR mode with additional authentication of the packets that are sent using Message Authentication Code (MAC). This is one of the recommended block cipher modes to support Authenticated Encryption with Associated Data (AEAD). This protects against attacks using the chosen ciphertext, where the attacker will forward the ciphertext to a server, which will attempt to decrypt the ciphertext and send a reply. The attacker will use these responses to gain access to the encryption key. AEAD will ensure that the ciphertext will only be trusted if it has the correct MAC value. While AEAD uses a hashing algorithm, this description is included along with cipher mode descriptions, as it is a primary function of GCM mode.
The following diagram shows an example of Mac-then-Encrypt (MtE) being used for SSL/TLS packets:
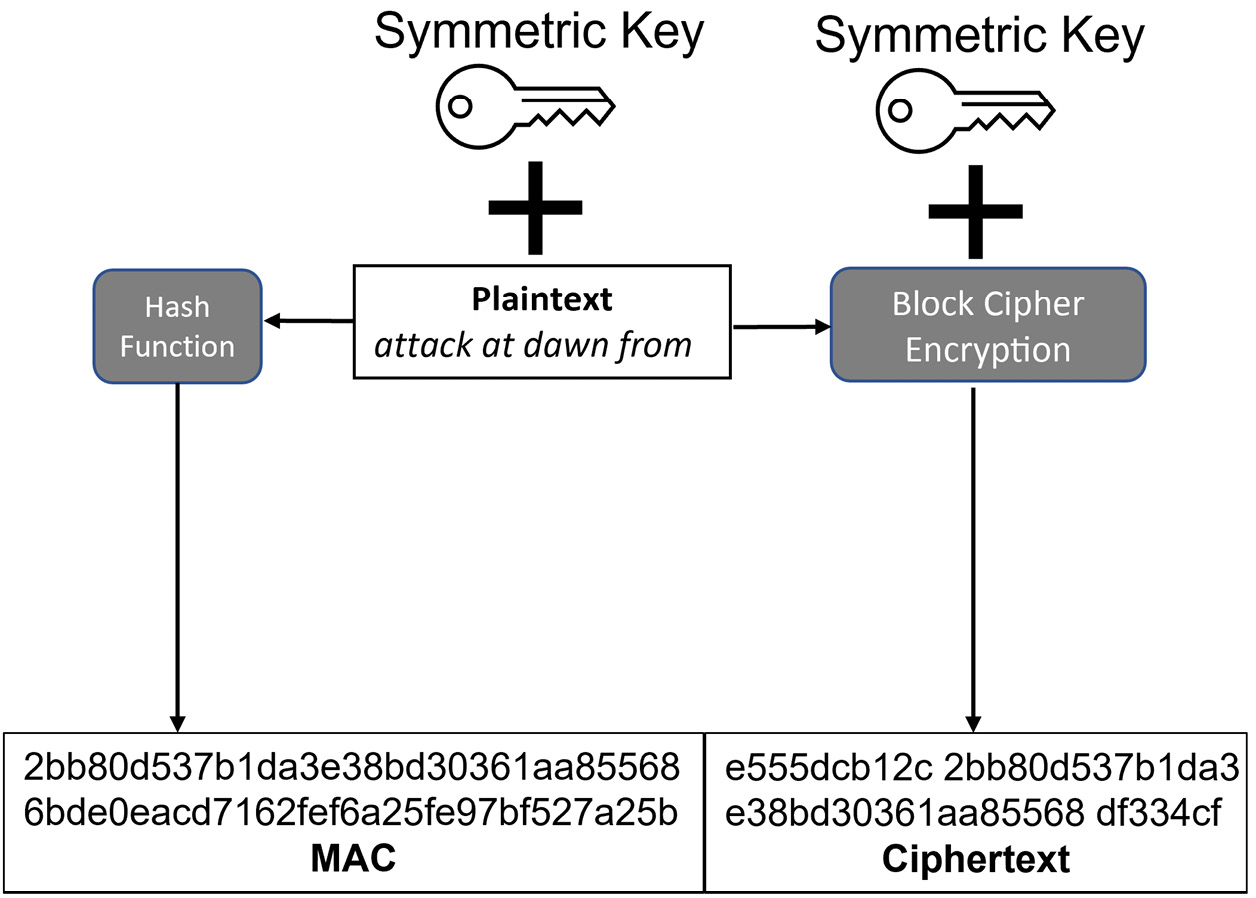
Figure 11.7 – GCM using AEAD
In the preceding example, the plaintext is processed twice; it is used as partial input to create the MAC (along with the key) and is then encrypted using the symmetric key.
Poly1305
Poly1305 is another popular cryptographic-based MAC that's commonly used along with AES (Poly1305-AES), though is also used with ChaCha. Poly1305 is popular with e-commerce providers due to its high speed on standard CPU architectures. This also supports the protocol for AEAD.
In addition to block ciphers, there are use cases where stream ciphers are considered a better option, particularly when considering data in transit.
Stream ciphers
Stream ciphers are optimized for real-time traffic. They are fast and as they process the data as a stream of bits, fewer errors are generated. The previous standard for stream ciphers was RC4, though this is no longer considered a secure cipher and was withdrawn from widespread use in 2015. The following are two popular modern stream ciphers:
- ChaCha: ChaCha was designed for high performance. As a stream cipher, it has many advantages over block ciphers when deployed with real-time applications such as streaming media or VoIP. It was designed as an alternative to AES when deploying SSL/TLS security. It is a refined version of Salsa20. The ChaCha cipher is based on 20 rounds of encryption using a 256-bit key size. One of its major strengths is its speed and resistance to side-channel analysis. ChaCha has been adopted by Cloudflare and Google as its preferred option for TLS 1.3 SSL/TLS connections.
- Salsa20: Salsa20 was developed by the same person (Daniel J. Bernstein) that developed the ChaCha cipher. It is closely related to the ChaCha cipher and offers choices of 128-bit and 256-bit key sizes. It was superseded by the newer ChaCha cipher.
Symmetric ciphers are fast and efficient but do not provide a mechanism for secure symmetric key exchanges, nor do they support concepts that are used within digital signatures. For this, we need asymmetric encryption.
Understanding asymmetric encryption algorithms
Asymmetric encryption has two main goals – one is to support a secure key exchange/agreement process, while the other is to support non-repudiation through the use of digital signatures. It is not used for bulk encryption as the key sizes (compared to symmetric encryption) are large. This would mean that it could be thousands of times slower to encrypt large amounts of data. Asymmetric encryption uses a key pair that is mathematically related; there is a public key and a private key. You can think of the public key as your bank details that you can share with a customer (who wants to make a payment). Your private key is used to securely access your funds. In this analogy, your bank card + pin + CVC code would be your private key. You would not share your private key with anyone.
Rivest, Shamir, and Adleman (RSA)
RSA is used for secure key exchange and digital signatures. It was developed and published in 1977, so it is one of the oldest asymmetric algorithms. It consists of a public and private key that are mathematically related. You can publish your public key but must keep the private key secure. The typical key size for RSA is between 2,048 to 4,096 bits, although current guidance is for keys of 3,072 bits to meet more stringent security standards.
Digital Signature Algorithm (DSA)
DSA is a government standard for digital signatures and is documented in FIPS PUB 186-4 (the current standard). Digital signatures are used for non-repudiation when you're sending a document by email or to validate a certificate hosted by a website. The following diagram shows the signing process when using a key pair:

Figure 11.8 – Digital signature algorithm (DSA)
FIPS standards are used to enforce strong signature algorithms. Signing is a combination of hashing and asymmetric encryption. The public key is used to sign the hash of the document (the email body in the preceding diagram).
The signing process is a little bit more complicated than what's shown in the preceding diagram. We have broken the process down into more granular steps in the following diagram:
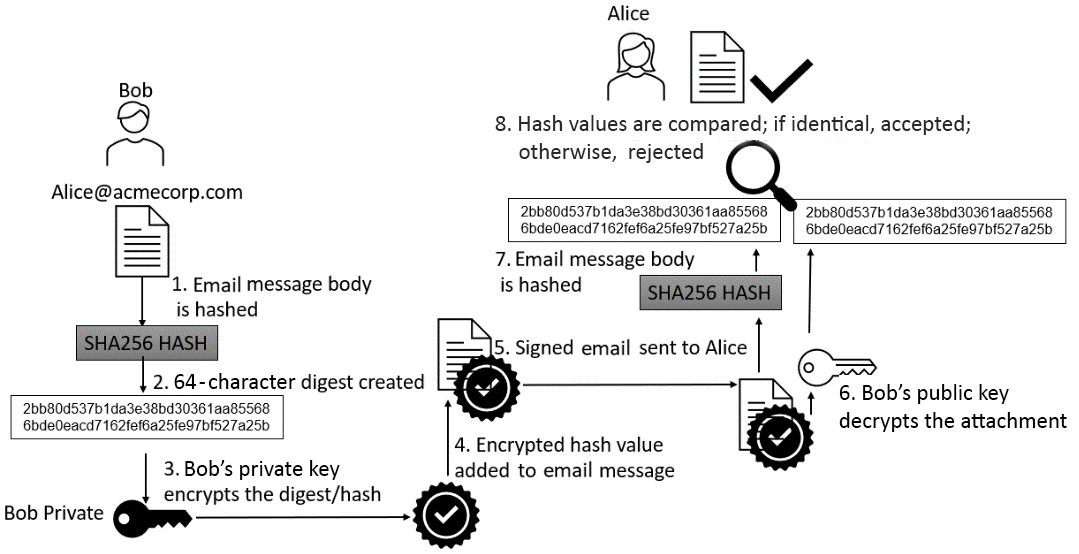
Figure 11.9 – Detailed signing process
The correct cipher suite must be selected. In this example, a cipher suite of RSA-3072 and SHA-256 would be considered a good choice. MD5 would not meet the requirements of FIPS compliance as it is weak and vulnerable to hash collisions. A man-in-the-middle (MITM) attack could allow the document to be intercepted and modified if we use a weak hashing algorithm. If the document is modified and it then matches the original hash value, then the signature will appear valid.
Elliptic-curve Digital Signature Algorithm (ECDSA)
ECDSA uses the same process as DSA by using standard keys, such as RSA keys. The advantage is that the key size is roughly a tenth (1/10) of the size of the equivalent RSA key. This results in a verifiable signature being generated, but with a vast reduction in CPU activity when using these types of keys.
Diffie-Hellman (DH)
DH is a key agreement protocol that's typically used to exchange a secret/session key for IPSec or SSL/TLS. It is not used to exchange a key but allows two parties to generate a secret/session key independently. This is useful as it means the session key was never transmitted, so any MITM attack would be unsuccessful.
Elliptic-curve Cryptography (ECC)
ECC allows key pairs to be generated using algebraic equations to draw an ellipse. Points can be plotted on this ellipse to generate keys (this is a simple description of a complex mathematical process). ECC is used for key agreements and digital signatures. The strength of ECC is in its suitability for low-powered devices. A key size of 256 bits using ECC is equivalent to an RSA key size of around 2,048 bits. ECC's key strengths are measured using p256, p384, and p521. A key size of 384 bits (p384) meets the NSA suite B security standard for top secret classification. Due to concerns about attacks from highly sophisticated threat actors using quantum computing, a new standard has replaced NSA suite B called Commercial National Security Algorithm Suite (CNSA). Check out the following URL for more information: https://tinyurl.com/nsa-cnsa-standards.
Elliptic-curve Diffie-Hellman (ECDH)
ECDH is a key agreement protocol where the actual public/private key pairs are based on ECC. This key exchange protocol is further enhanced by the use of ephemeral keys (also known as temporary keys), which makes this become ECDHE. ECDHE is one example of a method that's referred to as forward secrecy or perfect forward secrecy. This ensures long-term key pairs are not used during the key exchange. If an attacker managed to gain a master key (such as a server private key), they could decrypt sessions in the future until the keys were changed or rotated. When you're using forward secrecy, this is not possible.
Now that we've looked at all the individual encryption algorithms, we will look at some common implementation methods.
Understanding encryption protocols
Hashing, symmetric, and asymmetric encryption are building blocks that are used to support applications and protocols that need to secure how data is stored and transmitted. Many processes will use a cipher suite, drawing on the strengths of the different types of encryption. We depend on these protocols to protect users when we're accessing online banking, remotely accessing the workplace, protecting information systems when they must be administered across a network, and ensuring that emails that are sent and received can be trusted. We will look at some of these common protocols in the following subsections.
Secure Sockets Layer (SSL)/Transport Layer Security (TLS)
SSL/TLS is used to encrypt many application layer protocols, such as HTTP, SMTP, IMAP, LDAP, and many more. It provides confidentiality (through encryption) and integrity (through HMAC). It uses hybrid cryptography through a suite of protocols. SSL is no longer used as it is considered insecure; TLS 1.2 and TLS 1.3 are the current standards. An example of SSL/TLS can be seen in the following diagram:
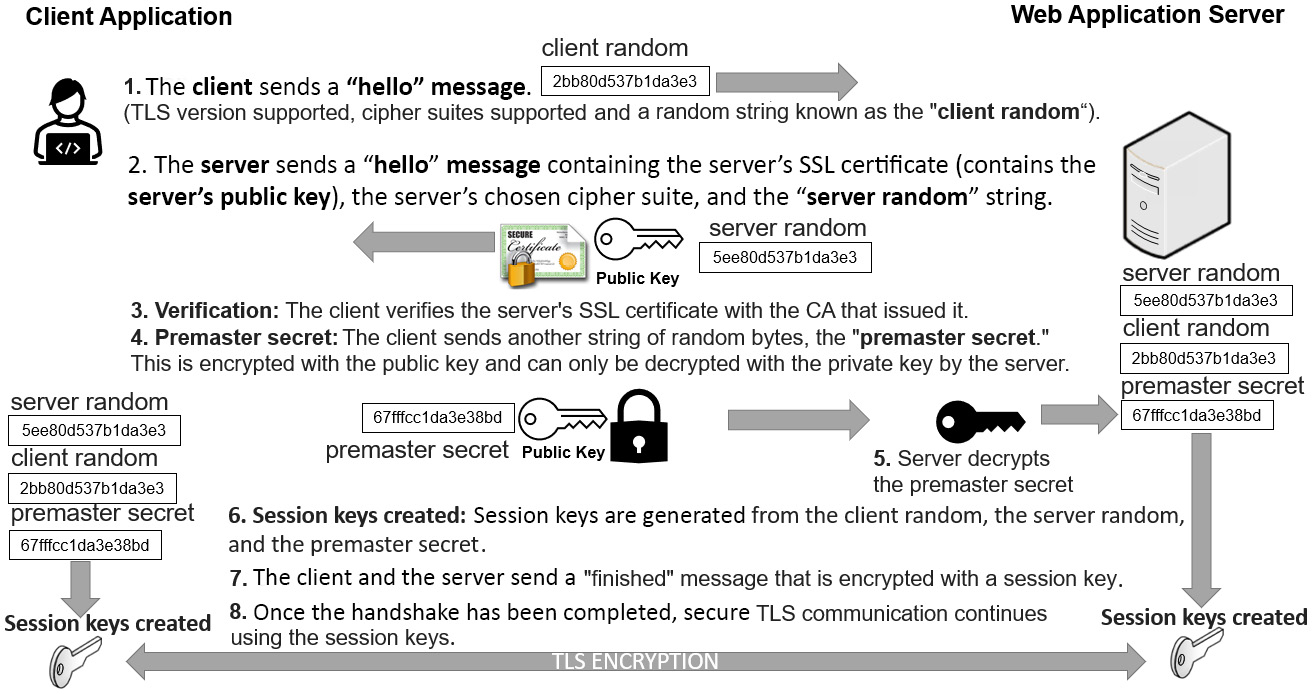
Figure 11.10 – SSL/TLS session handshake
During the SSL/TLS handshake, the client and server must agree upon a cipher suite. If there is no common cipher suite that suits both parties, then a cipher mismatch will occur. If there is a cipher mismatch, the connection will be refused. This may be a result of the client or server proposing a weak cipher suite.
Secure/Multipurpose Internet Mail Extensions (S/MIME)
MIME is the standard for emails and allows for a common protocol. This allows users to choose a mail client so that the enterprise can run an SMTP server from any vendor. To ensure that emails are protected from inbox to inbox, we can encrypt the payload using a combination of the recipient's public key and a session key. The recipient can decrypt the message using their private key.
The following diagram shows the S/MIME process:
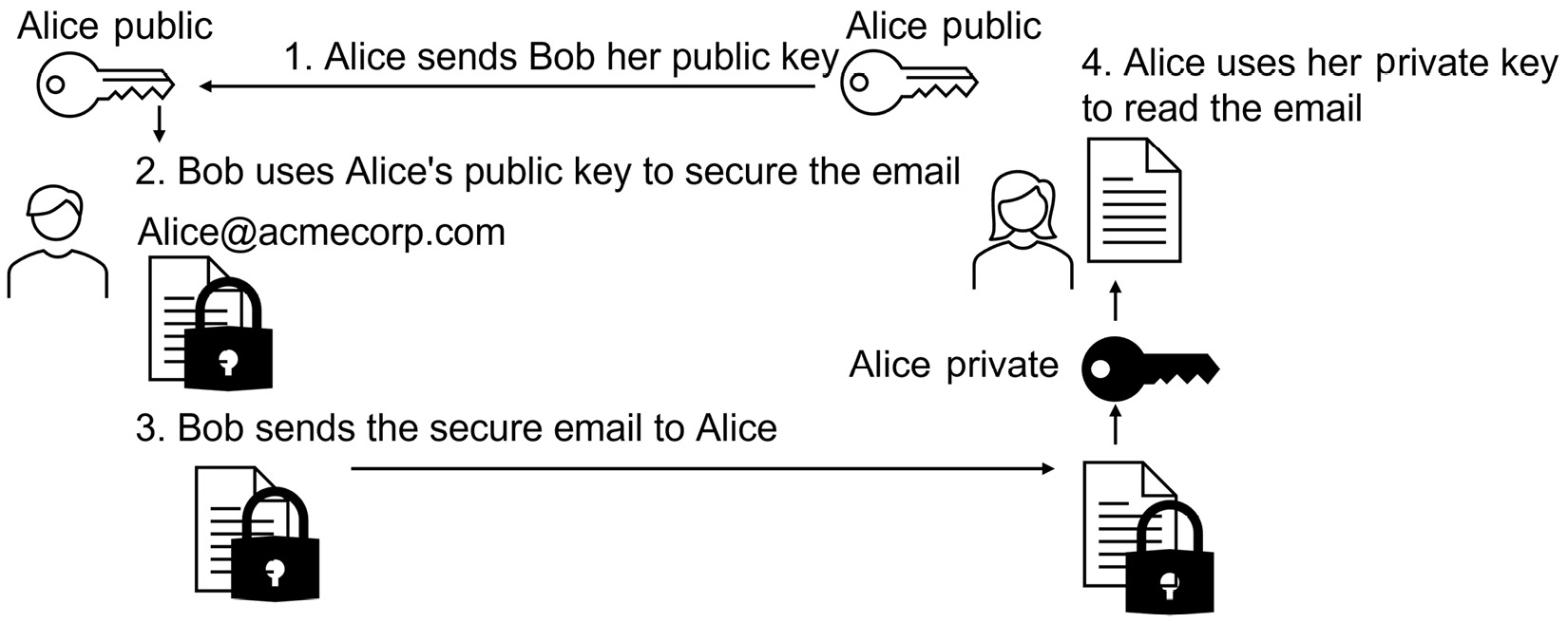
Figure 11.11 – S/MIME
This is a simplified version; in reality, the public key is used to protect the bulk encryption key (the symmetric key); the private key can decrypt the symmetric key.
Internet Protocol Security (IPSec)
IPSec is a mechanism for securing data in transit, typically when supporting Virtual Private Networks (VPNs). This can be used to secure site-to-site links or allow mobile users to secure access to the enterprise network. IPSec will use a cipher suite consisting of hashing (HMAC), symmetric for bulk encryption, and asymmetric for secure key exchange.
Secure Shell (SSH)
SSH is used to manage servers and equipment using a secure shell (or secure console). SSH uses hybrid encryption to secure the connection. A common tool for connecting to a remote device securely is PuTTY. The following screenshot shows the configuration for PuTTY when preparing for an SSH connection:

Figure 11.12 – PuTTY SSH configuration
Note that the configuration allows for a secure key exchange (asymmetric) and the session key (symmetric). It is common to rotate the keys that are used for secure connections. If the asymmetric key pair is rotated (changed) on the server, then the client device will need to download and trust the new public key.
Key stretching
Key stretching is used to protect weak keys. Examples of such keys include the passwords stored in a database. If an attacker gains access to the weak passwords that have been hashed in a database, then they can use offline techniques to crack these passwords. As they will not use the live login option, they will not lock the accounts out. Offline tools/techniques could include dictionary attacks, rainbow tables, and brute-force attacks. When we harden a password using key stretching, the original password is passed through multiple rounds of encryption. An attacker will now need to guess a password string and subject it to multiple rounds of encryption (just like the key stretching algorithm) in an attempt to crack the password. Key stretching will slow down the attacker's attempts to a considerable degree while allowing the legitimate users to access their accounts with little overhead.
Password salting
This is the most basic way to protect a password against offline attacks while using tables and brute-force techniques. A pseudo-random string of characters is generated. This salt is now mixed with the password string and hashed. The following diagram shows the password salting process:
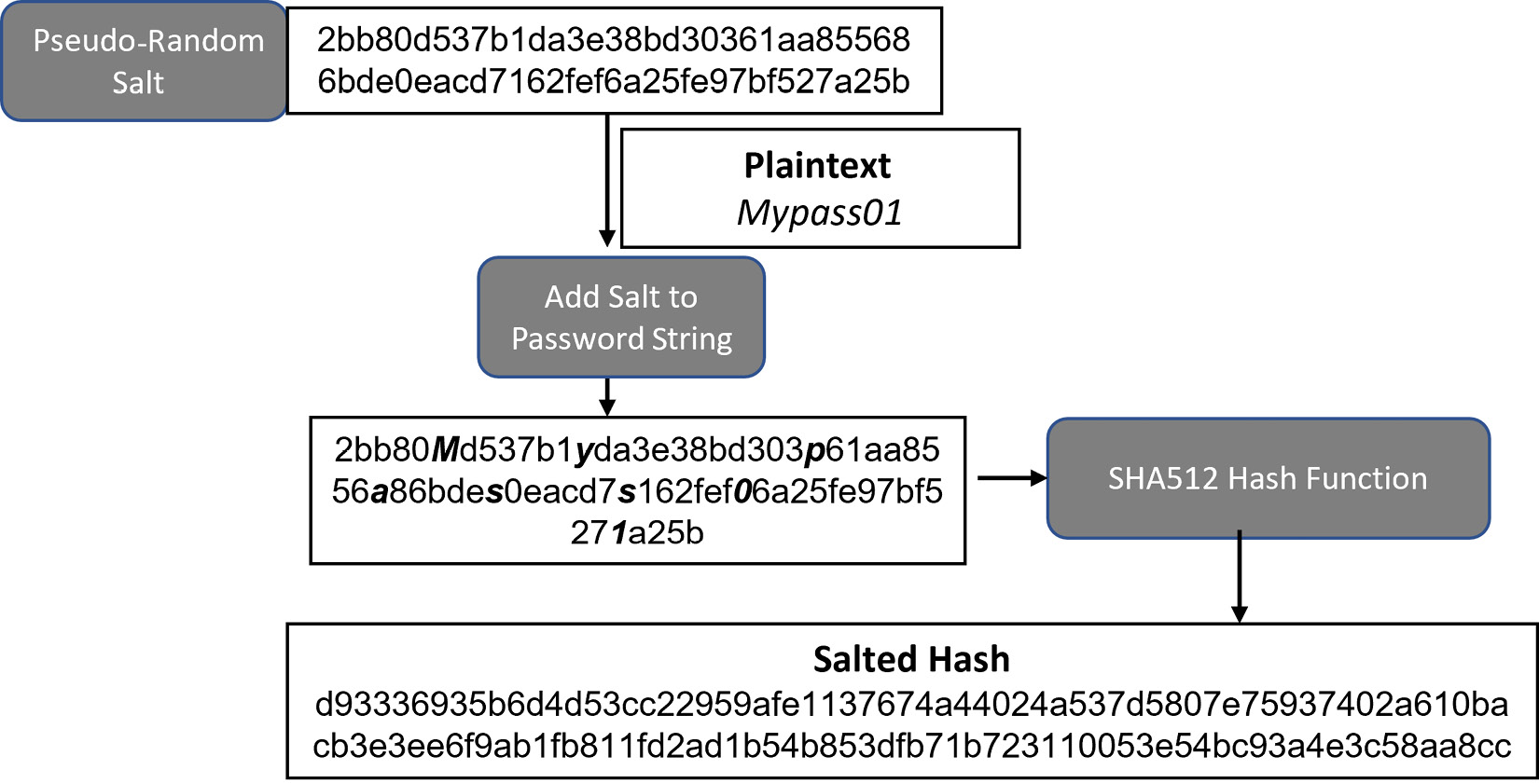
Figure 11.13 – Password salting
This salted password is now stored in the password database. This offers a useful level of protection for passwords that are stored, though can be improved upon by using key stretching techniques.
Password-based key derivation function 2 (PBKDF2)
PBKDF2 uses SHA-2 hashing and a salt of at least 64 characters to protect passwords. NIST recommends a series of 10,000 rounds/cycles of hashing to be applied to the password after the salt has been added. The following diagram shows the principle of key stretching:
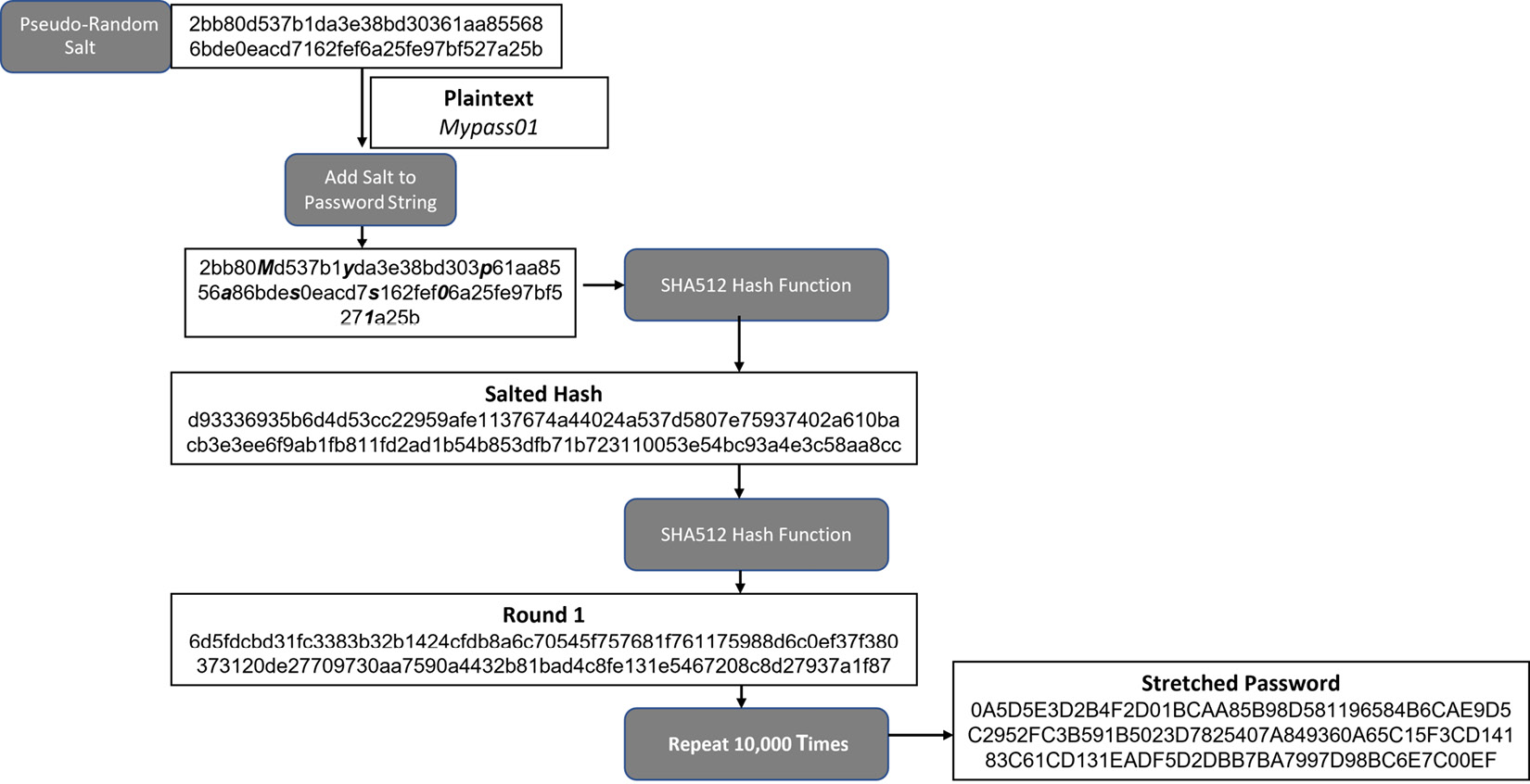
Figure 11.14 – PBKDF2 key stretching
bcrypt is similar to PBKDF2, in the sense that it also allows for key stretching, though it uses a different cipher. bcrypt is based on the Blowfish cipher, although it can also use SHA-2 to encrypt a password using multiple rounds.
Many additional technologies can be used to protect an enterprise from attacks when data, intellectual property, and the integrity of the data may be at risk. Let's learn about some of these emerging technologies.
Understanding emerging security technologies
To maintain a strong security posture, organizations must be willing to adopt new technologies and be aware of these technologies to protect the organization. Increases in computing power may allow adversaries to gain access to data that's protected using weak encryption algorithms. Newer technologies will allow for innovative solutions to address cybersecurity requirements.
Quantum computing
Quantum computing is designed to solve complex problems more efficiently than existing supercomputers. Supercomputers harness the traditional processing capabilities of compute nodes hosting thousands of CPU and GPU cores. Solving a problem using quantum processing may be thousands of times faster than using the existing computing models. A regular computer (or supercomputer) processes 0s and 1s and generates answers to problems using 0s and 1s – this is a solid approach and works well to solve many different computational problems. Let's compare this to a simple problem where a freight company needs to deliver goods to 10 different customers. There are 10 different truck types and 10 different routes to the customer sites, and each customer has a specific payload to be delivered. There may be over 3 million solutions when it comes to optimizing the use of trucks, fuel, and routes. One example quantum algorithm is called Grover's search, which can process the problem on a quantum computer and generate the results in a much more efficient manner (compared to traditional computers). Instead of searching through all 3 million possible solutions, Grover's search will find the solution by checking various solutions – in this case, around 1,732 calculations. For complex computational models, this may mean that an answer is available within seconds rather than weeks.
The adoption of quantum computing and efficient algorithms to harness this technology presents a major cybersecurity threat. At the time of writing, Google has a quantum computer rated at 50 qubits (qubits describe quantum bits). A qubit can represent multiple states. It is estimated that around 20 million qubits would be required to crack existing cryptographic keys. For examples of quantum computing and the threats to cryptography, go to https://tinyurl.com/quantumthreats.
Blockchain
A blockchain is a secure digital ledger that's supported by a public peer-to-peer network. A blockchain is a robust tamper-proof mechanism that's used to protect the integrity and authenticity of data.
Records or transactions are added as a new block and the hash is calculated and added to the chain. The following diagram shows a blockchain:
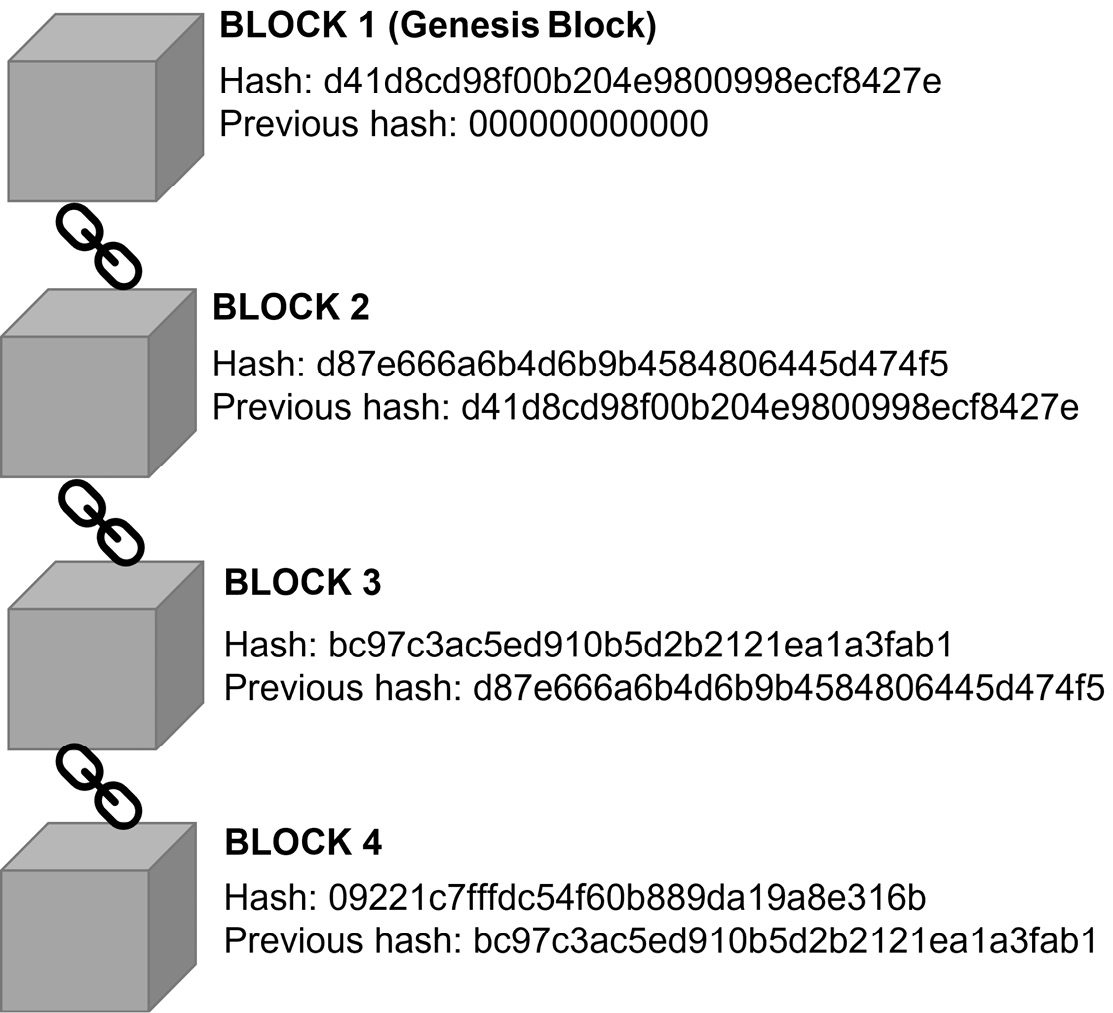
Figure 11.15 – Blockchain
The first block is referred to as the genesis block; there is no previous hash calculation as there is no preceding block.
For the new transactions to be accepted, they must be approved by the majority of the nodes on a Peer-to-Peer (P2P) network. The new transaction (or block) can now be added to the public ledger. We can see the process of approving a new transaction in the following diagram:
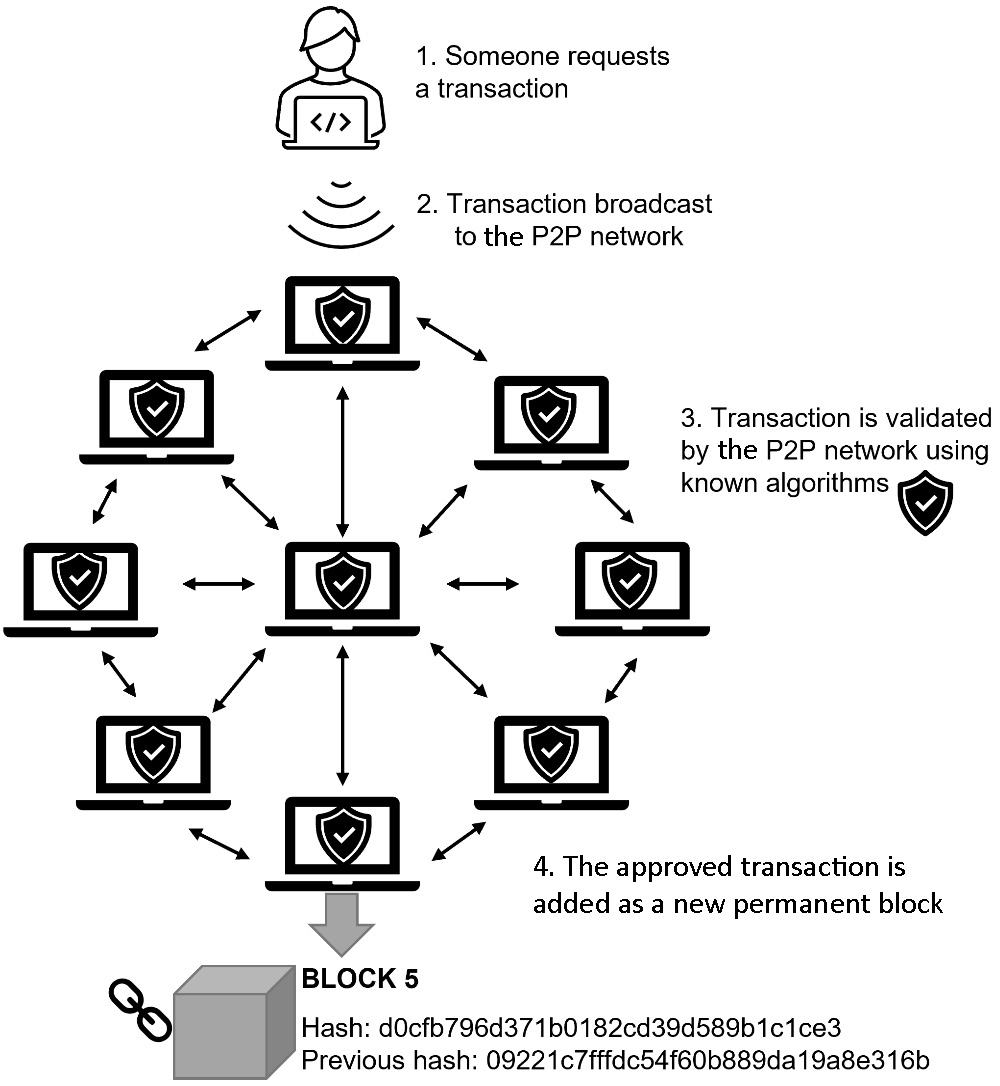
Figure 11.16 – Transaction approved by the P2P network
To tamper with transactions in a blockchain, it would be necessary to recalculate the hashes for all of the blocks (as each is dependent on the preceding block) and be able to take control of more than 50% of the nodes on the P2P network. Aside from cryptocurrencies, there are many practical implementations of blockchains, including secure voting machines, healthcare, financial ledgers, and many more. Spotify uses a decentralized blockchain to store information about artists, tracks, and licensing agreements.
Homomorphic encryption
This type of encryption is used to protect data in use. When sensitive data must be accessed by an application or service, then homomorphic encryption should be considered.
Private Information Retrieval (PIR)
This protocol allows you to retrieve data from a database, without the receiver accessing any sensitive data in the database. A researcher working for a medical company needs to evaluate the effectiveness of drug trials. Rather than send the researcher the entire database of information, with any sensitive data encrypted, PIR will run the query against the secure encrypted database and only return the results that are authorized for the researcher to access.
Secure Function Evaluation (SFE)
This protocol allows a function to be computed on two separate inputs, without revealing the inputs to any party. For example, let's say that Mallory would like to perform statistical analysis on customers' purchasing habits. The values that will be analyzed are held by Acme bank and Home Depot. Acme and Home Depot do not want to share sensitive PII or intellectual property with each other or Mallory. Mallory submits the query/function to the two organizations and can retrieve useful statistical information, without gaining access to any protected data from either party.
Private Function Evaluation (PFE)
This is also known as Multi-party Computation (MPC), which allows multiple parties to submit data (or inputs) to a secure enclave where the function or calculation will be performed. In this case, the function will be kept secret and the data owners will be sent the encrypted results. This protects the intellectual property of all parties, including the program owner.
Biometric impersonation
When considering security within large, complex enterprises, it is important to protect identities with robust authentication schemes. Biometrics has been very useful in providing Multi-factor Authentication (MFA), including facial recognition, gait analysis, and voice patterns. The adoption of very powerful compute nodes has also made biometric impersonation using deep fakes possible.
In 2020, a United Arab Emirates-based bank manager took a phone call from a company director, who instructed him to make a large transfer totaling $35 million. It later transpired that criminals had used deep learning computing techniques to create realistic renditions of the company director's speech patterns. To read more about this story, go to https://tinyurl.com/deepfakeheist.
Deep learning uses Artificial Intelligence (AI) and neural networks to extract distinct traits or features from raw information. This technology can be used to generate deep fakes.
There have been many instances of deep fakes being used to steal the identities of victims. Computer-generated deep fake audio and videos are very difficult to distinguish from the real thing. Deep fakes can also be referred to as synthetic media.
To mitigate the threats posed by deep fakes, there needs to be a robust way to verify that the digital media, images, or voice are original. Blockchains may be a useful solution to verify whether the media is original. The following URL provides an interesting news article on deep fakes: https://tinyurl.com/deepfakereport.
3D printing
This technology is widely adopted and is used by many diverse industries, from motor manufacturers to aircraft production. 3D printing uses a Computer-aided Design (CAD) process to create a blueprint for the printer to use. The printer can lay multiple layers of materials to create prototypes, as well as production components.
The wide adoption of this technology means it is relatively easy for a competitor to recreate designs based on the enterprise's intellectual property. Other risks may involve a hacker gaining access to a network-connected 3D printer and introducing defects into the printing process. However, it may be a useful security mitigation when we would otherwise rely on third-party manufacturers to produce prototypes and early design models. It is of paramount importance to secure the blueprints and manufacturing data that are used by this process. Some 3D printing manufacturers are incorporating technology that allows for digital fingerprinting, allowing a printed component to be traced back to the source.
Summary
In this chapter, we learned about the protocols and technologies that are used to protect data in many different states, primarily at rest, in transit, and in use. We gained an understanding of hashing algorithms, primarily to support integrity. These hashing algorithms include SHA, SHA-2, SHA-3, MD, and RIPE. We also looked at message integrity using HMAC and AEAD.
We then studied the options for ensuring confidentiality using symmetric encryption, including block ciphers such as AES and 3DES. We also identified cipher block modes, including GCM, ECB, CBC, CTR, and OFB. We then looked at common stream ciphers such as ChaCha and Salsa20, where real-time applications must be considered.
After that, we looked at asymmetric encryption, which is used for S/MIME, digital signatures, and key exchange. These asymmetric algorithms include ECC, ECHDE, RSA, and DSA.
We now understand how to deploy secure protocols, including SSL, TLS, S/MIME, IPSec, and SSH.
We also gained an understanding of key stretching using PBKDF2 and bcrypt.
We also looked at new and emerging technologies that can help protect sensitive data and intellectual property. Emerging technologies include blockchains, homomorphic encryption, biometric impersonation, and deep fakes. We then looked at some of the risks to be considered when deploying 3D printing.
These skills will be useful when we study additional security concepts using Public Key Infrastructure (PKI) as this is primarily deployed to support the authenticity of our asymmetric key pairs.
In the next chapter, we will look at how public keys can be trusted by generating digital certificates, as well as how certificates can be revoked and managed within an enterprise.
Questions
Answer the following questions to test your knowledge of this chapter:
- Recent log analysis has revealed that archived documents have been tampered with, even though the hash-matching database shows that the values have not changed. What could have caused this?
- A weak symmetric cipher
- Hash collision
- An asymmetric algorithm with a small key size
- A poor choice of block cipher
- Recent log analysis has revealed that archived documents have been tampered with. To mitigate this vulnerability, which of the following should not be used?
- RACE-320
- MD5
- SHA-384
- SHA3-256
- Developers are creating a File Integrity Monitoring (FIM) solution to market to government agencies. What would be a good choice, considering FIPS compliance?
- RACE-256
- MD5
- SHA-512
- ECC
- Google engineers are configuring security for a new regional data center. They are looking to implement SSL/TLS for customer-facing application servers. What would be a good choice, considering the need for speed and security?
- ChaCha256 and Poly1305
- 3DES and CBC
- AES256 and CBC
- Salsa256 and CBC
- What is used to authenticate packets that are sent over a secure SSL/TLS connection?
- SHA
- HMAC
- MD
- Key exchange
- Hackers can gain access to encrypted data transmissions. Log analysis shows that some application servers have different blockchain cipher configurations. Which log entries would cause the most concern?
- GCM
- ECB
- CBC
- CTR
- When you're choosing a symmetric algorithm for real-time media streaming applications, what would be the best choice?
- 3DES
- AES
- ChaCha
- RC4
- A government department is configuring a VPN connection. They are looking for a highly secure key exchange protocol due to the threats that are being posed by nation state threat actors. What would be a good choice?
- AES
- ECDHE p521
- ChaCha-256
- SHA-512
- What type of key agreement would most likely be used on IPSec tunnels?
- Diffie-Hellman
- DSA
- RSA
- Salsa
- What is a good choice regarding a signing algorithm that will work well on low-powered mobile devices?
- DSA
- RSA
- ECDSA
- HMAC
- What is the first step in the handshake for a secure web session that's using SSL/TLS?
- Server hello
- Session key created
- Client hello
- Pre-master secret
- A government agency needs to ensure that email messages are secure from mailbox to mailbox. It cannot be guaranteed that all SMTP connections are secure. What is the best choice?
- SSL/TLS
- S/MIME
- IPSec
- SSH
- An engineer sees the following output while connecting to a router:
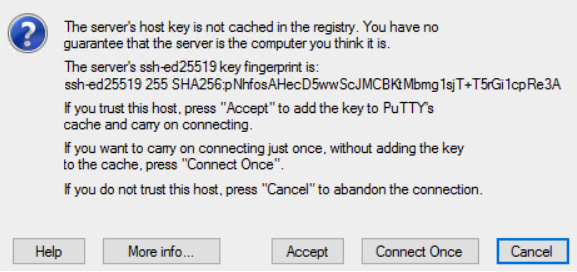
Figure 11.17 – SSH warning
The engineer logged onto the device using SSH the same day earlier. What is the most likely cause of this message?
- Weak ciphers
- Key rotation
- Incorrect password
- Incompatible cipher suite
- While setting up a commercial customer-facing web application server, what would be a good choice regarding a key exchange that will support forward secrecy?
- DH
- RSA
- ChaCha
- ECDHE
- What term is used to describe the message integrity that's provided by protocols such as Poly1305 and GCM?
- Non-repudiation
- Authenticated encryption with associated data
- Perfect forward secrecy
- Collision resistance
- What would be used to provide non-repudiation when you're sending a business associate an email message?
- TLS/SSL
- AES-256
- S/MIME
- IPSec
- A developer is protecting the password field when they're storing customer profiles in a database. What would be a good choice for protecting this data from offline attacks? Choose two.
- PBKDF2
- AES
- bcrypt
- ChaCha
- What do Alice and Bob need to exchange before they send signed email messages to each other?
- Private keys
- Cipher suite
- Public keys
- Pre-shared keys
- What will be used when Alice needs to sign an important business document to her colleague, Bob?
- Alice's public key
- Alice's private key
- Bobs public key
- Bobs private key
- What encryption protocol will be used to encrypt emails while in transit, across untrusted networks, when the client has no encryption keys?
- SSL/TLS
- IPSecC
- SSH
- S/MIME
Answers
- B
- B
- C
- A
- B
- B
- C
- B
- A
- C
- C
- B
- B
- D
- B
- C
- A and C
- C
- B
- A
