11
System Security Profiles with OpenSCAP
SCAP stands for Security Content Automation Protocol, a standardized way to check, verify, and report vulnerability assessment and policy assessment. Red Hat Enterprise Linux (RHEL) 9 includes the OpenSCAP tool and profiles to audit and manage the security of systems. This helps ensure the systems you are managing comply with standard security policies such as the Payment Card Industry Data Security Standard (PCI DSS) or the Protection Profile for General Purpose Operating Systems—or Operating System Protection Profile (OSPP) for short—as well as discovering vulnerabilities. New security profiles, such as the Health Insurance Portability and Accountability Act (HIPAA) security profile, have been added to RHEL 9 to cover systems containing personal health information.
RHEL 9 includes this tool to review security profiles in order to discover possible attack vectors (misconfigurations or vulnerabilities) and can obtain guidance on how to better harden the system. We will learn how to perform a scan on a system and discover what needs to be changed to prepare it, in order to ensure it is completely aligned with the regulatory requirements. We will also learn how this tool can be used to improve the security of a system for general use by reviewing it and applying the recommended changes.
To review how to use OpenSCAP, in this chapter, we will go through the following topics:
- Getting started with OpenSCAP and discovering system vulnerabilities
- Using OpenSCAP with security profiles for OSPP and PCI DSS
Getting started with OpenSCAP and discovering system vulnerabilities
Let’s get started in OpenSCAP in a practical way by first reviewing the Security Tools software group, which has some tools that are good to know, and then proceeding to run some scans.
Our initial step will be to get information on Security Tools. Here’s how we can do this:
[root@rhel-instance ~]# dnf group info "Security Tools"
Updating Subscription Management repositories.
Last metadata expiration check: 0:00:20 ago on Fri Jun 3 08:17:27 2022.
Group: Security Tools
Description: Security tools for integrity and trust verification.
Default Packages:
scap-security-guide
Optional Packages:
aide
hmaccalc
openscap
openscap-engine-sce
openscap-utils
scap-security-guide-doc
scap-workbench
tpm2-tools
tss2
udica
This group includes several security tools, such as aide, to ensure file integrity in the system; tpm2-tools, to manage the Trusted Platform Module (TPM) to store encryption keys; and openscap-utils, to review the security policies in the system.
We can get more information on those tools by using dnf. Let’s review the one that is more relevant for this chapter—openscap-utils—as follows:
[root@rhel-instance ~]# dnf info openscap-utils
Updating Subscription Management repositories.
Last metadata expiration check: 0:01:41 ago on Fri Jun 3 08:17:27 2022.
Available Packages
Name : openscap-utils
Epoch : 1
Version : 1.3.6
Release : 3.el9
Architecture : x86_64
Size : 32 k
Source : openscap-1.3.6-3.el9.src.rpm
Repository : rhel-9-for-x86_64-appstream-rpms
Summary : OpenSCAP Utilities
URL : http://www.open-scap.org/
License : LGPLv2+
Description : The openscap-utils package contains command-line tools build on top
: of OpenSCAP library. Historically, openscap-utils included oscap
: tool which is now separated to openscap-scanner sub-package.
We can see in the output of the previous command what the openscap-utils package is about, with a brief description and a link to the main web page, which includes more extensive information.
Tip
It would be useful to run the dnf info command for each of the tools mentioned and visit their web pages. This way, you will be able to gain a better understanding of the capabilities these tools provide and be able to use them.
Let’s now install openscap-utils, as follows:
[root@rhel-instance ~]# dnf install openscap-utils -y
Updating Subscription Management repositories.
Last metadata expiration check: 0:01:41 ago on Fri Jun 3 08:17:27 2022.
Dependencies resolved.
===========================================================
Package Arch Version Repository Size
===========================================================
Installing:
openscap-utils x86_64 1:1.3.6-3.el9 rhel-9-for-x86_64-appstream-rpms 32 k
Installing dependencies: binutils x86_64 2.35.2-17.el9 rhel-9-for-x86_64-baseos-rpms 5.1 M
[omitted]
xmlsec1-1.2.29-9.el9.x86_64
xmlsec1-openssl-1.2.29-9.el9.x86_64
zip-3.0-33.el9.x86_64
Complete!
Now, let’s install scap-security-guide, which includes the RHEL-specific SCAP profiles. To do so, we’ll run the following command:
[root@rhel-instance ~]# dnf install scap-security-guide -y
Updating Subscription Management repositories.
Last metadata expiration check: 0:08:34 ago on Fri Jun 3 08:17:27 2022.
Dependencies resolved.
===========================================================
Package
Arch Version Repository Size
===========================================================
Installing:
scap-security-guide
noarch 0.1.60-6.el9_0 rhel-9-for-x86_64-appstream-rpms 683 k
Installing dependencies:
xml-common noarch 0.6.3-58.el9 rhel-9-for-x86_64-appstream-rpms 36 k
[omitted]
Installed:
scap-security-guide-0.1.60-6.el9_0.noarch
xml-common-0.6.3-58.el9.noarch
With this package comes the SCAP Security Guides, including the one related to vulnerabilities for RHEL 9, which is located at /usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xml.
The oscap info sub-command can display information about a selected data stream. Extensible Markup Language (XML) files containing data streams are indicated by the -ds string in their filenames. You can find a list of available profiles and their identifiers (IDs) in the Profile section, as illustrated in the following code snippet:
[root@rhel-instance ~]# oscap info /usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xml | grep Title –A 1
WARNING: Datastream component 'scap_org.open-scap_cref_security-data-oval-com.redhat.rhsa-RHEL9.xml.bz2' points out to the remote 'https://access.redhat.com/security/data/oval/com.redhat.rhsa-RHEL9.xml.bz2'. Use '--fetch-remote-resources' option to download it.
WARNING: Skipping 'https://access.redhat.com/security/data/oval/com.redhat.rhsa-RHEL9.xml.bz2' file which is referenced from datastream
Title: ANSSI-BP-028 (enhanced)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_enhanced
Title: ANSSI-BP-028 (high)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_high
[omitted]
Title: [DRAFT] DISA STIG with GUI for Red Hat Enterprise Linux 9
Id: xccdf_org.ssgproject.content_profile_stig_gui
We can check the additional details about any of the profiles using the -–profile parameter and the profile ID. For example, to check the details for the HIPAA profile, we can run the following command:
[root@rhel-instance ~]# oscap info --profile xccdf_org.ssgproject.content_profile_hipaa /usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xml
Document type: Source Data Stream
Imported: 2022-03-28T15:05:12
[skipped]
Profile
Title: Health Insurance Portability and Accountability Act (HIPAA)
Id: xccdf_org.ssgproject.content_profile_hipaa
Description: The HIPAA Security Rule establishes U.S. national standards to protect individuals' electronic personal health information that is created, received, used, or maintained by a covered entity.
[skipped]
Tip
The profiles available in a data stream XML file can be listed using the -–profiles subparameter from the info parameter—for example, oscap info –-profiles /usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xml.
We can now run an initial scan using all the checks included in the profile. Note that this will include 2,323 tests and that this will be done as an exercise to learn about possible vulnerabilities and actions to harden a system. So, let’s run it, as follows:
[root@rhel-instance ~]# oscap oval eval --report
/tmp/vulnerability.html
/usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xml
Definition oval:ssg-zipl_vsyscall_argument:def:1: false
Definition oval:ssg-zipl_slub_debug_argument:def:1: false
Definition oval:ssg-zipl_page_poison_argument:def:1: false
Definition oval:ssg-zipl_bootmap_is_up_to_date:def:1: false
[omitted]
Definition oval:ssg-accounts_logon_fail_delay:def:1: false
Definition oval:ssg-accounts_have_homedir_login_defs:def:1: true
Definition oval:ssg-account_unique_name:def:1: true
Definition oval:ssg-account_disable_post_pw_expiration:def:1: false
A file called vulnerability.html in the /tmp/ folder will be generated with the output of the scan. The results will look like this:
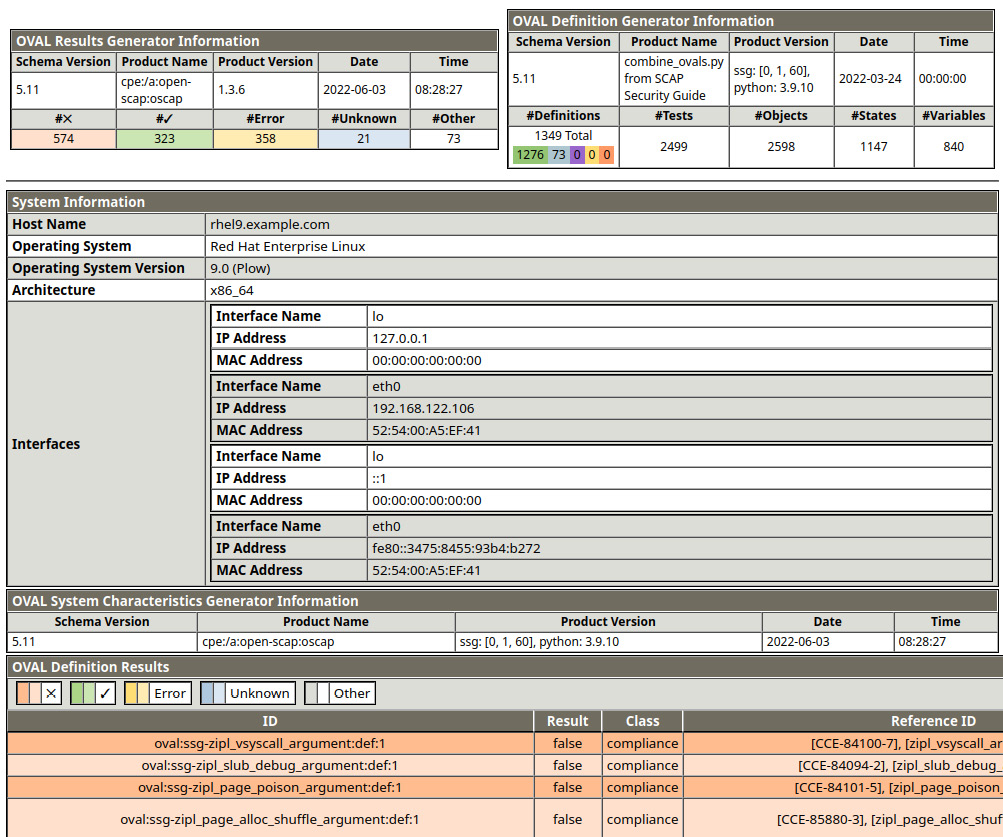
Figure 11.1 – Initial results of an OpenSCAP test scan
Let’s check some of the details of the report. In the top-left corner of the following screenshot, we will find OVAL Results Generator Information, with details of the run and a summary of the results:
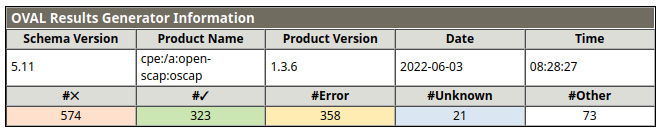
Figure 11.2 – OpenSCAP test scan summary
In the top-right corner of the following screenshot, we can see OVAL Definition Generator Information, with a summary of the definitions used for checks:
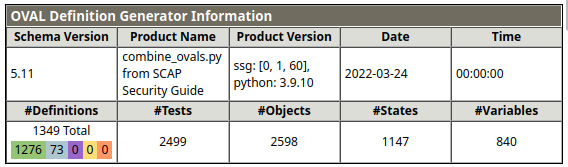
Figure 11.3 – OpenSCAP test scan definitions summary
Right below those tokens of information, we can see a basic summary of the system, which is useful if we have a long list of scans and we want to assign this scan to the proper system. You can see a representation of this in the following screenshot:
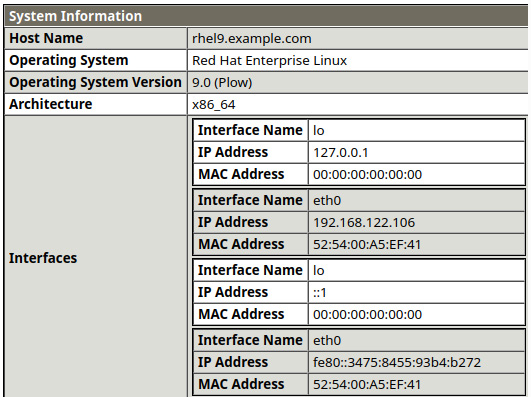
Figure 11.4 – OpenSCAP test scan system summary
Underneath it, we have information on the generator, as shown here:
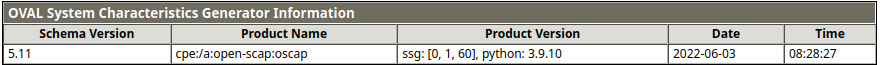
Figure 11.5 – OpenSCAP test scan generator information
And finally, here are the results of the checks. In a full report, you can easily differentiate the checks passed from the rest just by looking at the colors:

Figure 11.6 – OpenSCAP test scan results
With this test, we have run a vulnerability scan on our system, obtaining a set of results that—depending on the usage of the system—will need to be addressed. In many cases, the warnings received do not apply, so we need to review them carefully. This kind of exercise should be done carefully on production systems, taking care of having a proper backup and snapshot of the system before proceeding to apply changes. It is recommended to run the hardening in test environments while building the service before moving it to production when possible.
Important Note
Security hardening for RHEL 9 is a great piece of documentation to get started on system security. It is recommended to read through it in order to extend the knowledge acquired in this chapter. It’s available at https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/9/html/security_hardening/index.
Let’s learn more about the basics. For this scan, we have used the Red Hat Security Advisories’ (RHSAs’) Open Vulnerability and Assessment Language (OVAL) feed, as provided by system packages. To check, we have run the OpenSCAP tool to review different security advisories and vulnerabilities as written in OVAL.
OVAL requires that the analyzed resources are in a certain state to consider them correct. It does so in a declarative manner, which means the end state is described and reviewed, not the manner in how to get to it.
The Red Hat security team generates RHSAs to address the different vulnerabilities that the system may be incurring and releases an OVAL definition for each one of them. These are released openly and are available at https://www.redhat.com/security/data/oval/v2/.
Now, let’s take a look at one example found in our report, as follows:
- ID: oval:ssg-accounts_logon_fail_delay:def:1
- Result: false
- Class: compliance
- Reference ID: [CCE-83635-3],[accounts_logon_fail_delay]
- Title: Ensure that FAIL_DELAY is Configured in login.defs
We can check the manual page for it by running man login.defs. In it, we will find the following information:
FAIL_DELAY (number)
Delay in seconds before being allowed another attempt after a login failure.
This is the value to establish how long a user will have to wait after a failed login attempt. It is intended to avoid brute-force attacks on accounts in the system. We may take, for example, two approaches to fix it, as outlined here:
- Add the FAIL_DELAY variable and value to login.defs.
- Enforce access to the system by only allowing login access using Secure Shell (SSH) keys and not passwords.
Or, even better, we could do both (security in depth, or SID). We could continue to review each of the entries in the list and understand each of them to complete the hardening of the system to avoid as much exposure as possible. This is a task that is usually run in coordination with the security teams and is continuously being reviewed.
In a case where you need to scan remote servers, you can use the oscap-ssh tool that is included in the openscap-utils package. The oscap-ssh tool can be executed remotely in any Linux system that provides SSH access. The syntax is very similar to the oscap command. Let’s try oscap-ssh with the latest RHSA OVAL definition file. First, we need to download the OVAL definition and decompress it. Here’s how we can achieve this:
[root@rhel-instance ~]# wget -O - https://www.redhat.com/security/data/oval/v2/RHEL9/rhel-9.oval.xml.bz2 |bzip2 --decompress > rhel-9.oval.xml
[skipped]
Tip
If the preceding command gives a wget: command not found error, we can install the wget package with the following command: dnf install wget -y.
And then, we can run the oscap-ssh command on a remote server, like so:
root@rhel-instance ~]# oscap-ssh root@remoteserver 22 oval eval --report remote-report.html rhel-9.oval.xml
Connecting to 'root@remoteserver' on port '22'...
The authenticity of host 'remoteserver (::2)' can't be established.
ED25519 key fingerprint is SHA256:nNhsxgLaScC3I5Is5SkKM09l/WmHQ7SboQvEiiqBfqo.
This key is not known by any other names
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'localhost' (ED25519) to the list of known hosts.
root@remotehost's password:
Connected!
Copying input file 'rhel-9.oval.xml' to remote working directory '/tmp/tmp.OXfIp4LxL6'...
rhel-9.oval.xml 100% 308KB 78.6MB/s 00:00
Starting the evaluation...
Definition oval:com.redhat.rhsa:def:20225267: false
Definition oval:com.redhat.rhsa:def:20225214: true
Definition oval:com.redhat.rhsa:def:20225099: true
Definition oval:com.redhat.rhsa:def:20225050: false
Definition oval:com.redhat.rhsa:def:20224990: false
Definition oval:com.redhat.rhsa:def:20224940: true
[skipped]
Definition oval:com.redhat.rhsa:def:20221728: false
Evaluation done.
oscap exit code: 0
Copying back requested files...
report.html 100% 33KB 36.0MB/s 00:00
Removing remote temporary directory...
Disconnecting ssh and removing master ssh socket directory...
Exit request sent.
[root@rhel-instance ~]# ls -la remote-report.html
-rw-r--r--. 1 root root 33558 Jun 29 23:12 remote-report.html
Now that we have run our first vulnerability scan, let’s see how we can do it for compliance in the next section.
Using OpenSCAP with security profiles for OSPP and PCI DSS
There are several security profiles used for compliance in the industry. Two of the most common, which we will review here, are the OSPP and PCI DSS standards.
The OSPP standard is heavily used in the public sector, serving general-purpose systems and also as a baseline for other more restrictive environments (that is, defense-accredited systems).
PCI DSS is one of the most widely used standards in the finance sector, and also applies to other sectors that want to provide online payments using credit cards.
There are different types of descriptions that can be used with OpenSCAP. We already know OVAL. Let’s check the most important ones here:
- Extensible Configuration Checklist Description Format (XCCDF): XCCDF is used to build security checklists. It’s very common for compliance testing and scoring.
- Common Platform Enumeration (CPE): CPE helps identify systems by assigning unique ID (UID) names. This way, it can correlate tests and names.
- Open Checklist Interactive Language (OCIL): OCIL is part of the SCAP standard. It is a way to aggregate other checks from different data stores.
- DataStream (DS): DS is a format that puts together several components into a single file. It is used to distribute profiles easily.
- Script Check Engine (SCE): This allows us to make scripts interoperable with a security policy SCAP extension to allow the script execution from a SCAP policy. For more information, please visit the SCE page (https://www.open-scap.org/features/other-standards/sce/).
- Common Vulnerabilities and Exposures (CVE): CVE is a dictionary of reference for public security vulnerabilities and exposures. CVE allows interoperability between different security tools and provides standardized names of vulnerabilities (IDs).
- Common Weakness Enumeration (CWE): CWE is a community-developed list of software weaknesses. CWE focuses its effort to describe in detail flaws and known security weaknesses. It provides information about the prevention, implementation, and mitigation of a weakness. The MITRE Corporation supports this project (https://www.open-scap.org/features/scap-components/#).
- XCCDF 1.1 tailoring extension: The SCAP standard offers tailoring for XCCDF 1.2. This extension was introduced by OpenSCAP to the XCCDF 1.1 specification, allowing tools and users to create tailoring files, even for XCCDF 1.1.
Tip
More information on the different security descriptions and components can be found on the OpenSCAP web page at the following link: https://www.open-scap.org/features/scap-components/.
In this case, we will use the ssg-rhel9-ds.xml file. Let’s check the information related to it, as follows:
[root@rhel-instance ]# cd /usr/share/xml/scap/ssg/content/
[root@rhel-instance content]# oscap info ssg-rhel9-ds.xml
Document type: Source Data Stream
[omitted]
Profiles:
Title: ANSSI-BP-028 (enhanced)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_enhanced
Title: ANSSI-BP-028 (high)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_high
Title: ANSSI-BP-028 (intermediary)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_intermediar
Title: ANSSI-BP-028 (minimal)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_minimal
Title: [DRAFT] CIS Red Hat Enterprise Linux 9 Benchmark for Level 2 - Server
Id: xccdf_org.ssgproject.content_profile_cis
Title: [DRAFT] CIS Red Hat Enterprise Linux 9 Benchmark for Level 1 - Server
Id: xccdf_org.ssgproject.content_profile_cis_server_l1
[omitted]
Checks:
Ref-Id: scap_org.open-scap_cref_ssg-rhel9-oval.xml
Ref-Id: scap_org.open-scap_cref_ssg-rhel9-ocil.xml
Ref-Id: scap_org.open-scap_cref_--builddir--build--BUILD--scap-security-guide-0.1.60--build--ssg-rhel9-cpe-oval.xml
Ref-Id: scap_org.open-scap_cref_security-data-oval-com.redhat.rhsa-RHEL9.xml.bz2
Dictionaries:
Ref-Id: scap_org.open-scap_cref_--builddir--build--BUILD--scap-security-guide-0.1.60--build--ssg-rhel9-cpe-dictionary.xml
As you can see, it includes profiles for both OSPP and PCI DSS for RHEL 9. Let’s give them a try.
Scanning for OSPP compliance
We can use the --profile option for oscap to get information specific to the OSPP profile, as follows:
[root@rhel-instance content]# oscap info --profile
ospp ssg-rhel9-ds.xml
Document type: Source Data Stream
Imported: 2022-03-28T09:05:12
Stream: scap_org.open-scap_datastream_from_xccdf_ssg-rhel9-xccdf-1.2.xml
Generated: (null)
Version: 1.3
WARNING: Datastream component 'scap_org.open-scap_cref_security-data-oval-com.redhat.rhsa-RHEL9.xml' points out to the remote 'https://www.redhat.com/security/data/oval/com.redhat.rhsa-RHEL9.xml'. Use '--fetch-remote-resources' option to download it.
WARNING: Skipping 'https://www.redhat.com/security/data/oval/com.redhat.rhsa-RHEL9.xml' file which is referenced from datastream
Profile
Title: [DRAFT] Protection Profile for General Purpose Operating Systems
Id: xccdf_org.ssgproject.content_profile_ospp
Description: This profile is part of Red Hat Enterprise Linux 9 Common Criteria Guidance documentation for Target of Evaluation based on Protection Profile for General Purpose Operating Systems (OSPP) version 4.2.1 and Functional Package for SSH version 1.0. Where appropriate, CNSSI 1253 or DoD-specific values are used for configuration, based on Configuration Annex to the OSPP.
We can see in the preceding information that the OSPP profile comes described as xccdf. We can now run oscap, indicating that we want to use that format with the xcddf option and that the action we want to take is to evaluate the system with eval. Here’s the command we need to execute:
[root@rhel-instance content]# oscap xccdf eval
--report /tmp/ospp-report.html --profile ospp ssg-rhel9-ds.xml
[omitted]
Title Set Password Maximum Consecutive Repeating Characters
Rule xccdf_org.ssgproject.content_rule_accounts_password_pam_maxrepeat
Ident CCE-82066-2
Result fail
Title Ensure PAM Enforces Password Requirements - Maximum Consecutive Repeating Characters from Same Character Class
Rule xccdf_org.ssgproject.content_rule_accounts_password_pam_maxclassrepeat
Ident CCE-81034-1
Result fail
[omitted]
Title Disable Kerberos by removing host keytab
Rule xccdf_org.ssgproject.content_rule_kerberos_disable_no_keytab
Ident CCE-82175-1
Result pass
We will obtain an ospp-report.html file with a full report on the OSPP rule results, as shown here:
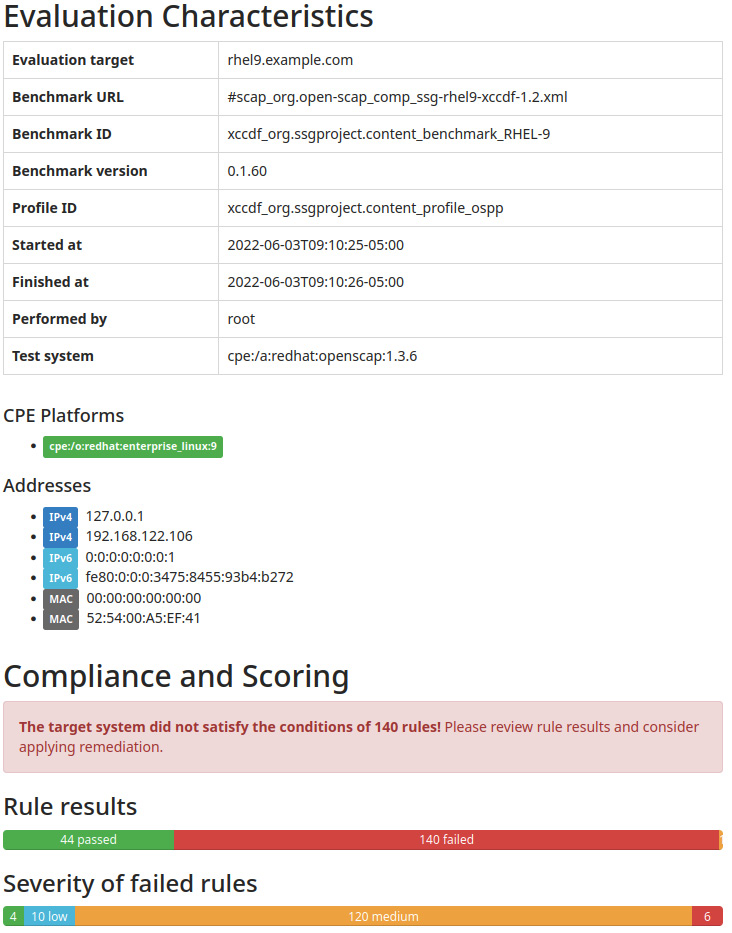
Figure 11.7 – OpenSCAP OSPP scan results
It will show the points that require modification to be compliant with the profile, as indicated in the following screenshot:
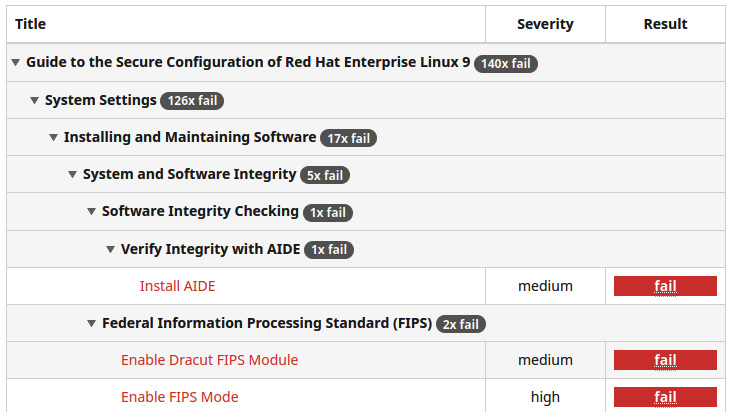
Figure 11.8 – OpenSCAP OSPP scan results: details of rules that require action
We can now follow, step by step, the recommendations and fix them in order to be fully OSPP-compliant. Also, we can use this scan to harden systems that, even when they do not need to be OSPP-compliant, will be in an exposed network such as a demilitarized zone (DMZ), and we want to have them hardened.
Important Note
Red Hat provides a way to automatically apply all those changes. It is based on the Ansible automation tool. It is provided in the form of a playbook—a set of descriptions for Ansible that will apply all the changes required to the system. The playbook for OSPP is located at /usr/share/scap-security-guide/ansible/rhel9-playbook-ospp.yml.
Now that we have reviewed the system for OSPP compliance, let’s move to the next target—PCI DSS compliance.
Scanning for PCI DSS compliance
We can follow the same procedure as before, also using the --profile option for oscap to get information specific to the PCI DSS profile. Here’s the code we need to execute:
[root@rhel-instance content]# oscap info --profile pci-dss
ssg-rhel9-ds.xml
Document type: Source Data Stream
Imported: 2022-03-28T09:05:12
Stream: scap_org.open-scap_datastream_from_xccdf_ssg-rhel9-xccdf-1.2.xml
Generated: (null)
Version: 1.3
WARNING: Datastream component 'scap_org.open-scap_cref_security-data-oval-com.redhat.rhsa-RHEL9.xml' points out to the remote 'https://www.redhat.com/security/data/oval/com.redhat.rhsa-RHEL9.xml'. Use '--fetch-remote-resources' option to download it.
WARNING: Skipping 'https://www.redhat.com/security/data/oval/com.redhat.rhsa-RHEL9.xml' file which is referenced from datastream
Profile
Title: PCI-DSS v3.2.1 Control Baseline for Red Hat Enterprise Linux 9
Id: xccdf_org.ssgproject.content_profile_pci-dss
Description: Ensures PCI-DSS v3.2.1 security configuration settings are applied.
We can run oscap with the same options as in the previous section but this time specify pci-dss as the profile, as illustrated in the following code snippet. This will generate a proper report:
[root@rhel-instance content]# oscap xccdf eval –-report
pci-dss-report.html --profile pci-dss ssg-rhel9-ds.xml
WARNING: Datastream component 'scap_org.open-scap_cref_security-data-oval-com.redhat.rhsa-RHEL9.xml' points out to the remote 'https://www.redhat.com/security/data/oval/com.redhat.rhsa-RHEL9.xml'. Use '--fetch-remote-resources' option to download it.
WARNING: Skipping 'https://www.redhat.com/security/data/oval/com.redhat.rhsa-RHEL9.xml' file which is referenced from datastream
WARNING: Skipping ./security-data-oval-com.redhat.rhsa-RHEL9.xml file which is referenced from XCCDF content
Title Verify File Hashes with RPM
Rule xccdf_org.ssgproject.content_rule_rpm_verify_hashes
Ident CCE-90841-8
Result pass
[omitted]
Title Enable Smartcards in SSSD
Rule xccdf_org.ssgproject.content_rule_sssd_enable_smartcards
Ident CCE-89155-6
Result pass
[root@rhel-instance content]# ls -l /tmp/pci-dss-report.html
-rw-r--r--. 1 root root 4005535 Jun 3 09:17 /tmp/pci-dss-report.html
We can start reviewing the items in the report and begin fixing them.
Important Note
As in the previous section, Red Hat also provides a way to automatically apply all those changes with Ansible. The playbook for PCI DSS is located at /usr/share/scap-security-guide/ansible/rhel9-playbook-pci-dss.yml.
We have seen that changing from one profile to a different one with OpenSCAP is very easy, and we can scan for as many profiles as available.
Summary
By learning the basics of OpenSCAP, we are ready to review and harden systems to make them compliant with the regulations we need them to run under.
Now, if you are requested to comply with any regulatory requisitions, you can find the right SCAP profile for it (or build it if it doesn’t exist) and ensure that your systems are fully compliant.
Also, even when no regulatory requirements apply, the use of OpenSCAP can help you find vulnerabilities in a system, or apply a more secure (and restrictive) configuration to your systems in order to reduce the risks.
There are ways to extend our knowledge and skills by learning Ansible and being able to automatically apply changes to our systems in a way that is easy to scale, as well as Red Hat Satellite, which can help run SCAP scans to the whole information technology (IT) base we are managing, even when we could be talking about thousands of systems.
Now that our security skills are improving and being consolidated, let’s dive deeper into more low-level topics such as local storage and filesystems, as described in the next chapter.
