CHAPTER 7
Windows
In this chapter, you will learn:
• The history of Windows and its product family
• Windows auditing
• Automation and configuration
• Windows network security
• Workgroups and Active Directory
Windows has been around for more than 35 years as of this writing, though development of it began nearly 40 years ago. The first several versions were not technically operating systems. During Windows’ first decade or more of existence it was actually just a shell that ran on top of another operating system: DOS. Windows offered a graphical user interface (GUI) that was much more appealing than the plain command line that DOS provided. It also let users run multiple things at more or less the same time, which DOS didn’t offer. DOS didn’t offer much, actually. Many features of operating systems that we take for granted, and features that had in fact been taken for granted on larger systems, like minicomputers and mainframes, simply didn’t exist in DOS. It didn’t have memory management or process management capabilities. It provided a way to read and write to a disk, but not a lot beyond that. In fact, the disks that DOS was created to support weren’t even hard drives.
Now, more than 35 years later, Windows is a modern operating system with as many advanced features as any other operating system. The Windows family now provides environments for mobile devices, desktops, and servers. The Windows Server line has become a platform to support complete enterprise management, as well as virtualization and a complete application development stack for web applications.
Over the course of this chapter, we’ll talk about where Windows has come from and what it has turned into, both on the desktop side and the server side. Windows offers a lot of features necessary for system administrators, but provides many for security professionals as well, including auditing, encrypted file systems, encrypted network communications, and the ability to authenticate and authorize users for a number of resources on the network. Additionally, resources and users can be organized into different groups to make management easier. This creates some differences when it comes to how systems interact and how authentication happens.
Windows History
In the beginning, there was DOS. Actually, even before DOS there were operating systems that were very similar, like CP/M. DOS wasn’t even a creation of Microsoft. When IBM decided to get into the personal computer (PC) business, they needed an operating system they could ship with it to make it useful. Microsoft, then a small software company shipping BASIC interpreters, got a request from IBM to create an operating system for its PCs. In order to get something out quickly, Microsoft bought the rights to a product called 86-DOS from Seattle Computer Products. Microsoft struck a very good licensing deal with IBM, which enabled them to make a lot of money for a long time as the primary operating system for the new IBM PC. The problem with DOS, though, was that it wasn’t particularly user-friendly. Microsoft announced Windows in 1983 and delivered it in 1985. Windows was an advance over MS-DOS if for no other reason than Windows allowed users to run multiple applications at the same time by employing cooperative multitasking. Cooperative, or non-preemptive, multitasking relies on the applications to yield the processor. This would typically happen because the application came to a point where no further processing could happen, perhaps because of the need for I/O.
Windows 3.x and Windows NT 3.x
In 1990, Windows 3.0 was released and introduced virtual memory and loadable virtual device drivers. Windows for Workgroups was launched in 1993 and was perhaps the greatest leap forward in that it incorporated a peer-to-peer network component using NetBEUI. Windows 3.11, or Windows for Workgroups, allowed businesses to establish a network without the need to invest in an expensive and difficult-to-manage server. Small businesses could easily afford to have their computers work together and share files between individual systems. It’s hard to overstate the importance of inexpensive and accessible networking in a single operating system. Previously, you had to purchase your operating system (as well as Windows if that’s what you wanted to use), then go to a company like Novell and purchase their network operating system and a server to run it on. Once you had your server, you could purchase individual clients for each of the operating systems so those components could interact with your server, which handled some authentication as well as file sharing.
In late 1989, development on a completely different operating system began, though it was originally intended to be an update to OS/2, which was an advanced operating system developed jointly by Microsoft and IBM. OS/2 had many advanced features, including multiprocessing. The development of OS/2 and Microsoft’s effort in that is a very involved story, so to avoid writing an entirely separate book explaining how all of that worked, let’s just say that Microsoft tasted some success with Windows 3.0 and opted to pull the plug on their work with IBM on OS/2, instead focusing their resources and efforts on a version of Windows that included an operating system. This resulted in Windows NT in 1993. NT stood for New Technology and was a result of about four years of development effort with a kernel designed from the ground up, supporting the interface that had already been established with the other version of Windows, which was just a shell that sat on top of DOS. Windows NT did, however, take the look of the interface from Windows 3.1. Figure 7-1 shows what the Windows 3.1 Program Manager looked like and, by extension, how the user interface for Windows NT 3.1 appeared onscreen.

Figure 7-1 The Windows 3.1 Program Manager
Windows NT was a fully 32-bit operating system, while Windows 3.x was a 16-bit operating system. This allowed NT to access more memory than Windows did, and access data on larger hard drives, also. Windows NT was a very advanced operating system that took many concepts from previous operating systems like Digital Equipment Corporation’s VMS, as well as the portable operating system standard, POSIX. NT was released as both a desktop and workstation operating system and became the foundation of the Windows Server line. The original release was Windows NT 3.1 Advanced Server, launched in 1993.
One of the goals of Windows NT was to be a portable operating system. Initially, it was supported on the IA32, MIPS, and Alpha processors, then later PowerPC, Itanium, AMD64, and ARM processor support was added. Over time, support for the MIPS, Alpha, and PowerPC architectures was dropped, leaving primarily support for the various Intel-based processor architectures.
Windows 9x, NT 4.0, and Windows 2000
Windows 95 did a better job of hiding the operating system, though it was still DOS under the hood if you knew how to look for it. Windows 95 was also the first version of Windows to bundle DOS inside of Windows. This was the release of DOS Windows NT. It and Windows remained on separate paths through the releases of Windows NT 4.0, Windows 98, Windows Me, and Windows 2000 (Windows NT 5.0). The interface work tended to be done in Windows, and then replicated in the NT line, so Windows NT 4.0 took the interface from Windows 95 just as Windows NT 3.1 took the interface from Windows 3.1.
Windows 95 was also a turning point in the interface, where Microsoft moved from using Program Manager as the shell users interfaced with to Explorer. Figure 7-2 shows the new shell that came with Windows 95, including the full, working desktop, which the previous versions of Windows didn’t have. Windows was long saddled with the filesystem that was part of DOS, and that continued through the Windows 9x line. The FAT (File Allocation Table) filesystem was a very basic filesystem that didn’t allow for features like file ownership or permissions.

Figure 7-2 The Windows 95 desktop
Windows 95 also moved away from the previously 16-bit Windows. It was a 32-bit preemptively multitasked operating system, but still provided support for 16-bit applications. Windows 95 also came with what Microsoft called Plug and Play, which was meant to move toward a more simplified way of managing devices. The idea behind Plug and Play was that a user could plug in any device and just have it work. While the promise wasn’t entirely delivered, it was an enormous step forward in device management.
Windows 95 was followed by Windows 98 and then Windows ME (Millennium Edition) on the consumer side, where the operating system was still underpinned by DOS, even though hidden under the surface. Windows 98 maintained the Explorer shell but introduced the FAT32 filesystem, which in turn introduced support for larger disk partitions and file sizes. Windows 98 was also the first version of Windows to include Internet Explorer in its initial release. Windows ME was intended to be a stopgap between Windows 98 and the impending release of Windows XP. ME was the last version to be DOS-based.
Meanwhile, the workstation line continued with NT releasing NT 4.0, which took the Explorer shell from the consumer line, making it look just like Windows 95. While it looked the same, NT 4.0 had the NT operating system and all of the NT subsystems under the hood. Windows 2000 is the first operating system from the NT line to drop the NT portion of the name and also drop the numbering convention used previously. It maintained the look of the desktop from the consumer Windows operating systems, just as previous versions of Windows NT had. You can see in Figure 7-3 that the desktop looks very similar to the desktop for Windows 95. Windows 2000 came in multiple server versions, in addition to the desktop version. The server version was the first to introduce Active Directory, essentially replacing the domain model introduced in NT 4.0.

Figure 7-3 The Windows 2000 desktop
Windows XP Through Windows 10
Windows XP was the first time where the two types of Windows had merged and where the DOS underpinnings finally disappeared for the consumer version of Windows. No matter what edition of Windows XP you were using, whether it was a Home edition or Professional, you used the NT kernel and all of the subsystems NT had used. It continued the naming strategy of dropping NT, however, just as Microsoft had done with Windows 2000. Windows XP made some interface changes but still used the familiar Start menu and taskbar to interact with the application menu and run programs. You can see the differences in Figure 7-4. Windows XP came in a number of editions, but it was the first NT descendent to not include a server edition. The server line was split off altogether. Windows XP was a desktop operating system. Windows Server 2003 was the server version that was released two years later.
Figure 7-4 The Windows XP desktop
Server 2003 was a significant upgrade over the Windows 2000 server, and included security features like disabling a number of services by default. This was done for stability reasons, but disabling features by default reduces the potential for exploitation, helping protect operating systems from attack. Both Windows XP and Windows Server 2003 were released in 64-bit versions in 2005. The larger address space ensured that systems could get access to much larger memory sizes, meant to be an advantage to applications like databases that might need to store very large data sets.
One of the security challenges Windows faced for a long time was that users on Windows operating systems had administrative privileges by default. On the consumer operating systems, descended from Windows 1.0, all users were administrators since there was no other type of user available. The consumer side didn’t get different types of users until the Windows and NT operating system lines were merged in Windows XP. It was also the first time the consumer operating system had the capability for a native filesystem that allowed for permissions. Starting with Windows XP, the consumer version of Windows began getting more and more security features, including the User Account Control (UAC), introduced in Windows Vista, that forced privilege elevation to be acknowledged by the user before it could take place. This feature was continued in later versions of Windows.
Windows Server 2008 and subsequently 2012 continued the server line, while Vista, Windows 7, and Windows 8 were successors to the desktop line. There have been minor changes to the interface in each release of the server line, and you can see what the interface for Windows Server 2008 R2 looks like in Figure 7-5. Each server release had its set of advances, including the promise to make Windows boot faster than Windows 7. Windows 7 also introduced Windows PowerShell (described in the next section as well as later in the chapter) and attempted to make the User Account Control from Windows Vista more palatable to users. Windows versions after 7 took into consideration that there were computing devices with touchscreens, and they wanted all implementations of Windows to look and behave the same. As a result of Microsoft’s move toward a touch model, the hardware manufacturers began providing systems that were capable of providing those features.

Figure 7-5 Windows Server 2008 R2
Windows 10 and Windows Server
Windows 8 provided a new look to the desktop line. Part of the point of Windows 8 was to marry the desktop and mobile platforms, providing a unified environment. This allowed application developers to have a single look by developing universal applications that could run on any platform as long as it supported the Universal Windows Platform (UWP). At the same time, the look of the user’s desktop and menu began to focus on devices that had touchscreen capability. This included computers that had touchscreens, tablets like the Microsoft Surface, and also the Windows Mobile platform for smartphones. Microsoft called the look Metro, but it didn’t go over very well with users. When Windows 8.1 was released, Microsoft scaled back the full-screen menu that was a main feature in Windows 8. Windows 10 continued the move to a smaller but still multifunctional menu. You can see the Windows 10 menu in Figure 7-6.
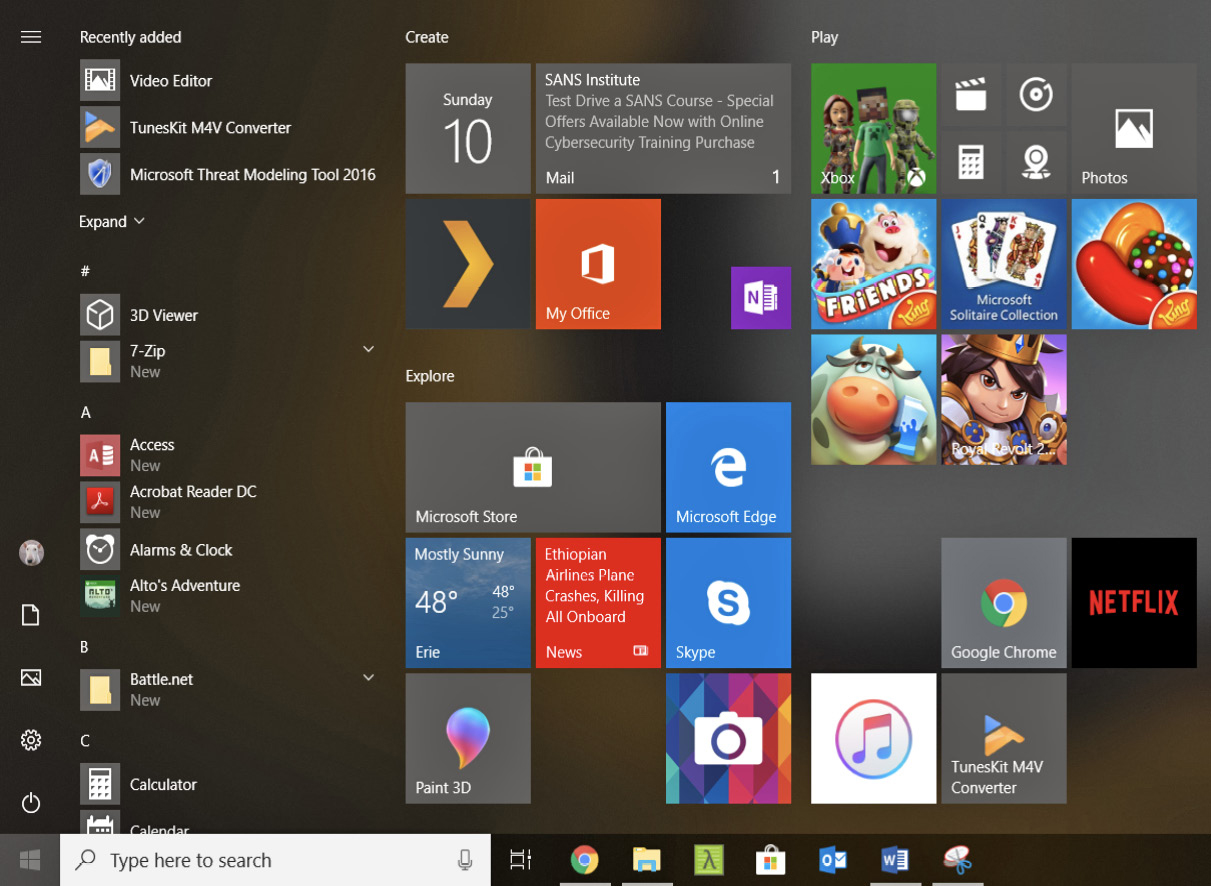
Figure 7-6 Windows 10 menu
With Windows 10, Microsoft is also moving away from the Control Panel that is a main feature in previous versions of Windows. Instead, though the Control Panel is still available, Windows 10 emphasizes using the Settings app, shown in Figure 7-7. This includes most of the features of the Control Panel while completely changing the overall look and also providing some additional features. As an example, prior to Windows 10, in order to change the background and other settings in the desktop appearance, you needed to open a separate settings program, but today that’s all integrated into the Windows Settings program under Personalization. You can still get to the same personalization settings by right-clicking the desktop and selecting Personalize. This means there are multiple ways to get to the same functionality.
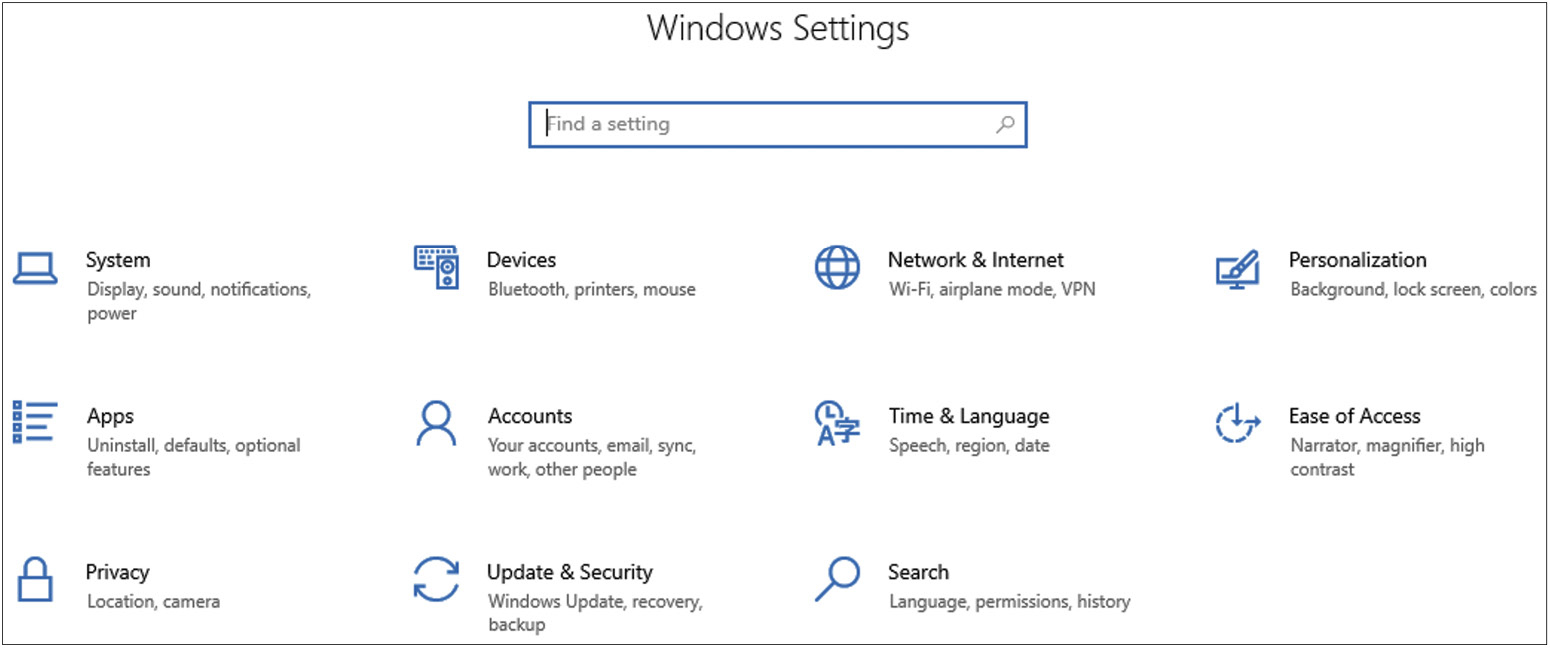
Figure 7-7 Windows 10 Settings
Windows has continued to add to the functionality of PowerShell since its first introduction. Today, PowerShell is a feature-rich programming language commonly used for system management. It has become so powerful, in fact, that attackers are using it as a way of developing attacks and other necessary programmatic functions without needing to have another language, like Python, installed. This is a technique called “living off the land.” It means the attackers don’t have to bring in any additional tools or install anything separate. They have a fully functional programming language they can make use of already installed on the system. This is especially the case on servers.
The Windows Server family has continued movements toward a hardened installation out of the box. This includes not installing any features by default. Since Windows Server 2016, it has also included the option to not include a GUI. The GUI becomes a feature called Desktop Experience, which can be selected at install time, as shown in Figure 7-8. It can also be installed as a feature after the fact, if you have selected one of the install types that don’t include the Desktop Experience. The default installation type is called Server Core.
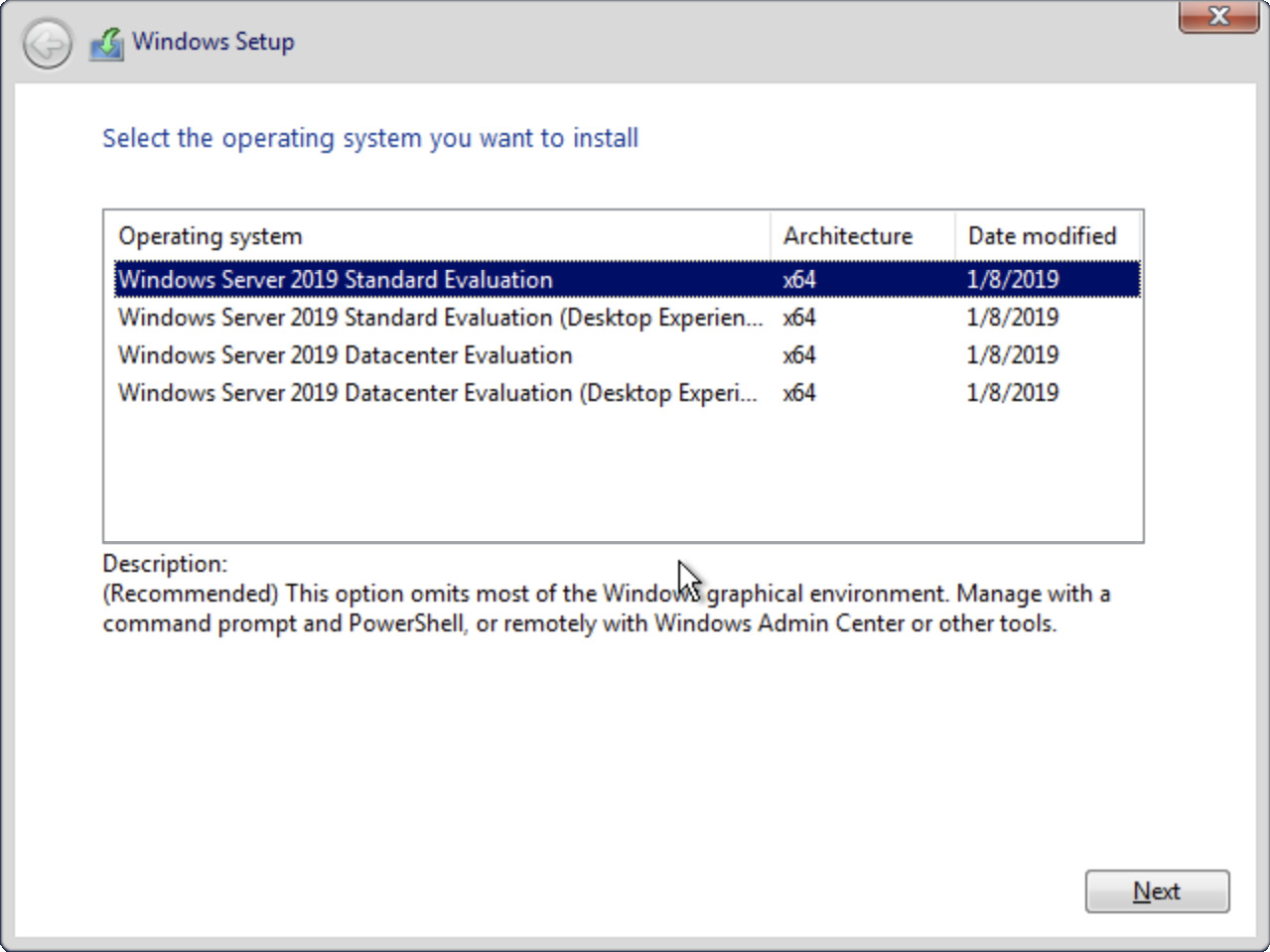
Figure 7-8 Windows Server 2019 installation types
If you select Server Core, once the system boots up, you log in to a text interface, just as you would with a Linux system without a GUI. Once you have logged in, you are presented with the familiar blue background, but instead of seeing the desktop and taskbar, you see a command prompt window. The problem with this is that you are running the old command processor with all the old DOS commands. You are not presented with a PowerShell shell, which opens up a lot more functionality with hundreds of cmdlets that allow you to write powerful scripts and also manage the system. You can, though, change the way the system starts by using a PowerShell cmdlet to change a registry key. You can run the following command in PowerShell to change the default shell from the command processor to the powershell.exe executable:
Set-ItemProperty -Path 'HKLM:SOFTWAREMicrosoftWindows NTCurrentVersionWinlogon' -Name Shell -Value 'powershell.exe'
Windows Networking
Microsoft groups their different networking components into three different classifications: client, service, and protocol. When you look at the network configuration settings on a Windows system, you will see that at least one client and one protocol are needed for the system to function. You may also add a service, depending on your needs. The client is very commonly the Client for Windows Networks, letting your computer interact with other systems on the network that are also Windows systems. You may also have services installed like a service for file and printer sharing on a Windows network so you can share your files and printers with other users on the network.
Windows has supported a number of networking protocols over the years, though primarily it supports TCP/IP today, both IPv4 and IPv6. In addition to supporting IP as the network protocol, Windows has long used Server Message Block (SMB)/Common Internet File System (CIFS) as a session layer protocol to provide internetworking between systems. SMB and CIFS provide the ability to share files and printers, among other things. As a system that runs TCP/IP, Windows also comes with a number of utilities that help with the configuration and management of the network implementation. Figure 7-9 shows how you would go about adding Windows networking components.

Figure 7-9 Adding Windows networking components
Basic Configuration
Windows supports both static and dynamic configurations for its networking settings. When dynamic configuration is selected, it makes use of the Dynamic Host Configuration Protocol (DHCP) to get the configuration of the IP address, subnet mask, default gateway, Domain Name System (DNS) servers, and any other network settings that may be available.
In the early 1980s, IBM developed a set of services called NetBIOS. NetBIOS is an application programming interface (API) that allows computers to communicate over a network. Microsoft had developed an implementation of NetBIOS that could stand alone and provide services on top of a layer 2 protocol that was called NetBEUI. NetBEUI allowed computers to quickly and easily get up and running on a network, sharing services and files. Currently, Windows implements NetBIOS over TCP/IP—an implementation commonly called NetBT. One of the important things NetBIOS provides is a name service, allowing systems to identify themselves on the network. This is separate from a DNS or Internet hostname, though it may be the same. Whereas DNS names are queried from external servers, NetBIOS names are known on the local network.
Whereas most of the network configuration is done in a set of network configuration dialog boxes, the NetBIOS names are set in the system properties during the installation of the system. While a NetBIOS name can be sixteen characters, the sixteenth character is reserved for the NetBIOS suffix, which indicates the type of service associated with the name. As a result, you may have several names announced on your local network for your system, indicating whether you are announcing a file share service or a remote access service, for example.
Networking Utilities
Any system that participates in a network needs a set of utilities for performing basic configuration checks, as well as for troubleshooting and debugging. Windows is no exception and provides a pretty common set of utilities necessary for managing a system on a TCP/IP network. Additionally, there are other utilities more common to Windows itself, letting you connect to other Windows systems and troubleshoot connections on the network.
Ping
Some will tell you that ping stands for Packet InterNet Groper, but in reality it was named after the sound SONAR systems make when trying to locate something, and this is exactly what ping does on a network. A retronym was developed shortly after to give it a network-sounding name. It was developed one evening in 1983 to troubleshoot a faulty network connection. Ping sends Internet Control Message Protocol (ICMP) Echo Request messages to systems or devices on the network. If the device receives the message, it replies with an ICMP Echo Response. The system sending the message makes note of when it sent it and then makes note of the time the response comes in and calculates a round-trip time from those two numbers. In addition to having the knowledge that a system is up, knowing how long it takes a packet to get there and back is helpful to get an idea of how far away a system is or maybe how congested the route to the system is. Shorter round-trip times mean a better connection and one that may be more desirable if you are comparing two systems.
tracert
tracert is the Windows implementation of the common traceroute program, used to determine the route a packet takes through the network. This is done by manipulating the Time To Live (TTL) field as each message is sent. The first message is sent with a TTL of 1, and when it hits its first network device, typically a router, the router will decrement the TTL to 0 and return an ICMP Time Exceeded In Transit message to the sender. That ICMP error message will contain the IP address of the sender, so we know the IP address of the first hop on the path. The next message is sent with a TTL of 2, and so on, until we get to our final destination. If an ICMP Echo Request message is sent, the system will know it has hit its final destination when it receives an ICMP Echo Response in return. If it never receives that message, the tracert will eventually fail. Other implementations use high-numbered User Datagram Protocol (UDP) ports, and when they receive an ICMP error indicating the port is unreachable, the traceroute has completed.
ipconfig
If you need to be able to look at your IP settings, you can use the ipconfig command. On Unix-like systems, this utility is called ifconfig. It will display all of your IP configuration settings for each network interface you may have on your system, including IP address, subnet mask, and default gateway as well as the MAC address for the interface. If your system has IPv6 addresses, it will also show the IPv6 information for each interface.
nslookup
nslookup is a utility to query DNS servers for information about the various records they store. You can look up the IP address for a particular hostname or look up the hostname associated with a particular IP address. You can also query for MX records, which are used to determine the mail server for a particular domain, and search for any other type of DNS record available.
netstat
netstat can provide a lot of network statistics for the system, including programs that are listening to particular ports, as well as connections that are open between two systems. Additionally, netstat can print out the routing tables on your system, meaning all of the networks your system knows how to get to as well as the interfaces used to get to them. This would include the default route, which is the path a packet takes if it doesn’t have a specific route for the destination.
nbtstat
nbtstat is similar to netstat, but instead of providing information oriented around TCP/IP statistics and connections, it returns information about the NetBIOS name service. Figure 7-10 shows the output from nbtstat listing all of the names this particular system, a Windows 2008 Server, knows about.
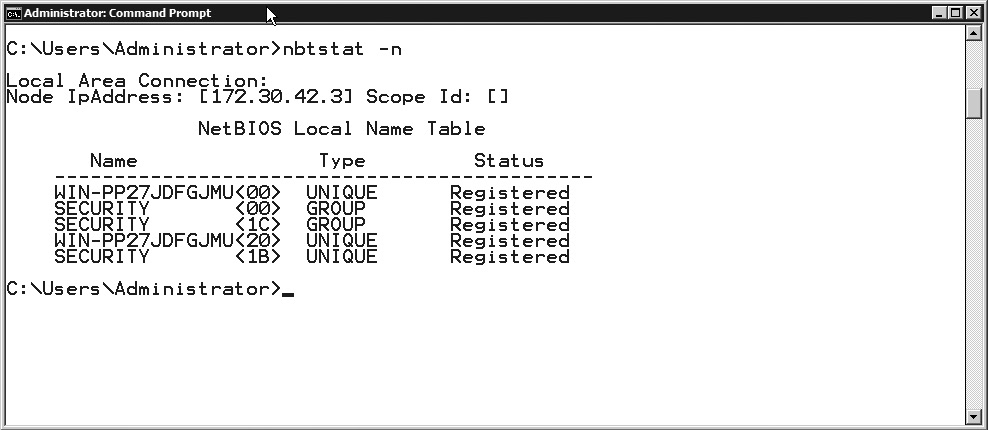
Figure 7-10 Sample nbtstat output
Exercise 7-1: Nbtstat
Access a command prompt on a Windows system and run nbtstat –n to see the local NetBIOS names. How many names do you get?
Securing Windows Networking
As with so many aspects of security, less is more. The fewer components you have in a system or network design, the less complex it will be, and as a result, the likelihood of problems will go down. When it comes to securing your Windows network, removing services is better. Microsoft has done a good job in the last decade or so of turning off a lot of services and requiring users to actively turn them on to make use of them. This can help a lot in keeping systems and networks protected against intrusion or misuse.
Microsoft began delivering a mechanism to help protect against vulnerability exploitation in service pack 2 for Windows XP. Buffer overflows have long been a problem where programs can have their execution path hijacked by manipulation of the program stack. Since the stack is where data is stored, there is generally no good reason that there should be executable code stored in and run from the stack. Microsoft implemented a Data Execution Protection (DEP) system to keep code from executing from the stack. Enabling this feature, if it isn’t already enabled, will help protect services from being exploited, including services that are listening for network connections.
Some hardware supports performing data execution protection directly without needing the software of the operating system to perform the protection. You can change any settings for DEP by going to the System Settings in the Control Panel or the Advanced settings window. You can see in Figure 7-11 that DEP has been enabled by default on the Windows 2016 server the figure was obtained from. You can exclude particular programs or even just have DEP apply to Windows applications and services—those that come with the operating system. The best way to protect your system, though, is to enable DEP for all programs unless it’s absolutely necessary to shut it off for a particular application to get it to function correctly.

Figure 7-11 Settings on the Data Execution Prevention tab
There are other methods of keeping your system protected, some of which are included in the operating system, while others are utilities you can add on later. As always with network security, having a firewall can protect systems against a number of problems, and Windows comes with a firewall built in. Additionally, Windows has the ability to encrypt network communication between systems using IPSec (discussed later in this chapter). That’s built into its networking capabilities. Those two features go a long way in protecting your network communications and your systems. On top of that, Microsoft provides a tool for analyzing other vulnerabilities that may exist on your system, discussed next.
Windows recognizes that many devices today are mobile. This means they are moving from one network to another and not all networks are created equal. Some networks require more protections to the device than others. You may want to expose file sharing on one network while not on another, for instance. Microsoft uses zones to determine what type of network your system is connected to. You can tell Windows that a network you have connected to is public or private. You may see this when you attach to a wireless network and Windows asks you if you are home or on a public network. The use of zones helps to enable some of the firewall capabilities that are available in Windows.
Microsoft Baseline Security Analyzer
The Microsoft Baseline Security Analyzer (MBSA) is a tool available from Microsoft to do a host audit, checking for security updates and potentially dangerous configuration settings for the operating system, as well as SQL Server and Internet Information Services (IIS). Microsoft initially released this tool in 2004 and has since updated it a few times. Some of the checks it performs ensure that you have good password policies in place, and that the Windows Firewall and Automatic Updates are enabled, as well as various user account settings. In addition to doing the audit, the tool can tell you how to fix any errors it finds. While it is capable of scanning the system it is installed on, it can also scan any other computers on your network as well.
Figure 7-12 shows a portion of a report from MBSA—note the findings for the Windows scan, both the passes and the failures. In addition to scanning the Windows setup and configuration, this particular scan also ran a check on a SQL Server instance it found running and turned up a number of issues including a password policy and the fact that SQL Server was found running on a domain controller. Additionally, it checked the Internet Explorer settings. Since Windows Server doesn’t come in a version without the graphical shell, it does have some vulnerabilities resulting from the programs installed with that shell, including Internet Explorer (IE), though Microsoft has done what it can to lock down a number of settings out of the box. For example, IE, by default, doesn’t allow downloads or script execution from any server in the Internet zone. MBSA checks the different security zones to help ensure the settings haven’t been weakened, which may put a server at risk from a careless administrator.
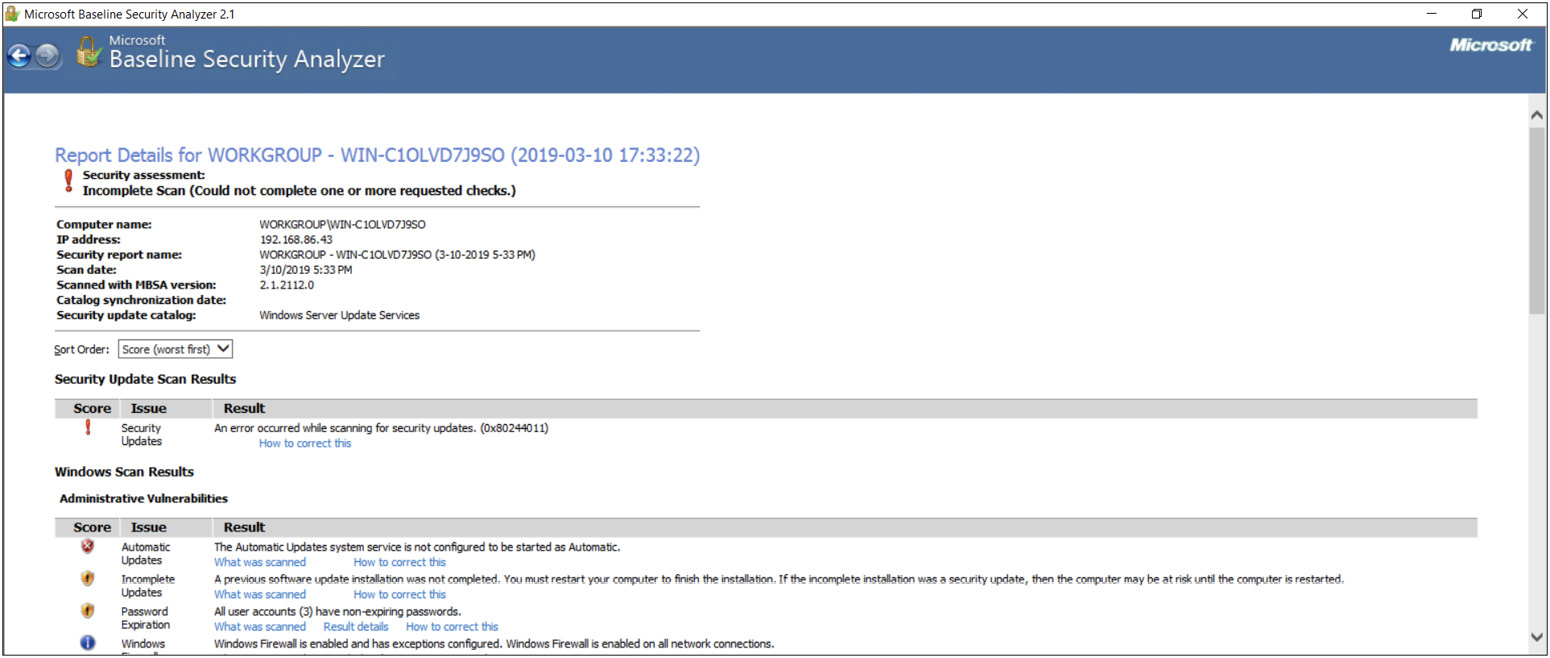
Figure 7-12 The Microsoft Baseline Security Analyzer report (partial)
MBSA will still run on newer operating systems, though it hasn’t been updated in a while and may not be the best solution to get a complete understanding of vulnerabilities on your OS. If you are looking to identify missing updates, using Windows Update, a feature in all Windows installations now, is a better approach.
Windows Defender
Microsoft introduced an optional anti-spyware program called Windows Defender in Windows XP. Until it was enhanced in Windows 8, all Windows Defender provided was anti-spyware. Starting with Windows Vista, Windows Defender was incorporated as a standard feature in Windows. Since Windows 8, Windows Defender has become more than just the basic anti-spyware that it started out as. Today, Windows Defender is an anti-virus solution, but the name has come to encompass all of the security features in Windows. Figure 7-13 shows the home view of the Windows Defender Security Center in Windows 10. This includes features for anti-virus, account protection, and a firewall, along with other features.
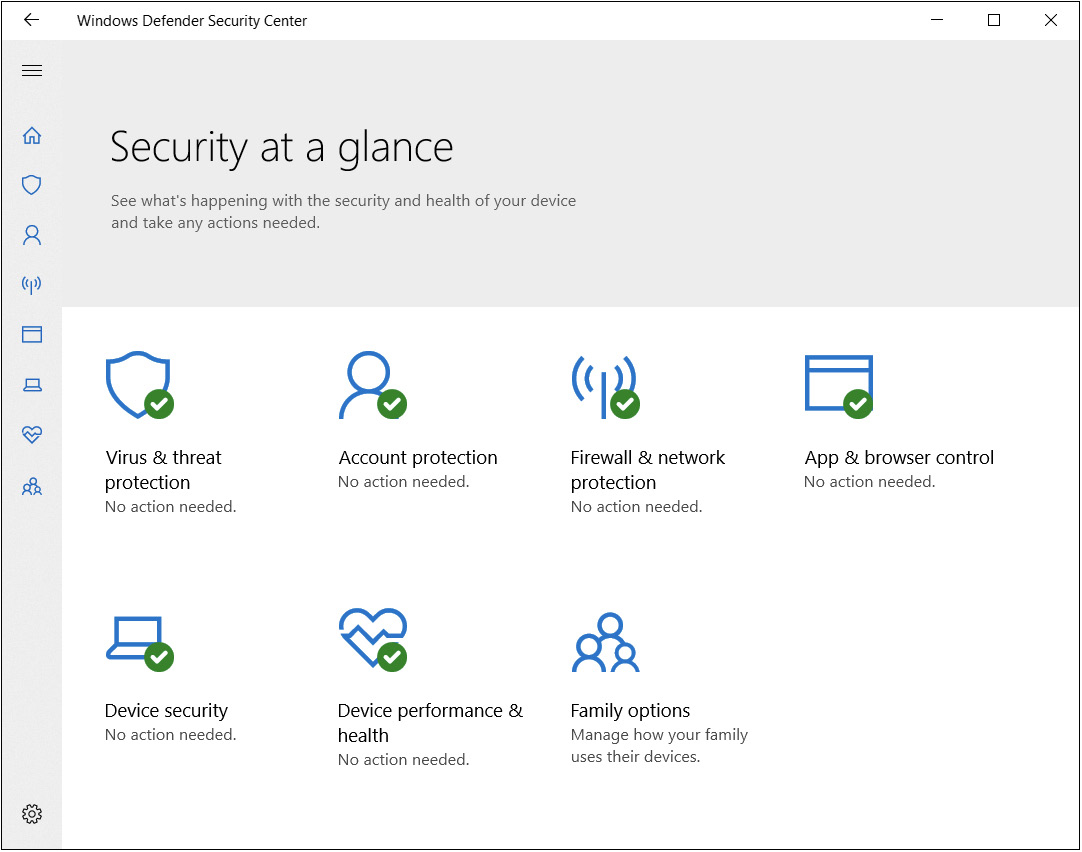
Figure 7-13 Windows Defender Security Center
Windows has had a firewall since the debut of Windows XP in 2001. The problem with the XP firewall was that it wasn’t on by default and the configuration was difficult and hard to find. After XP was hit with some worms, like Blaster and Sasser, Microsoft decided to fix the firewall and the interface, and then rebrand it as Windows Firewall. Later it became Windows Defender Firewall. With XP Service Pack 2, it was on by default. Windows Firewall comes with a set of default rules and exceptions, based on the network you are connecting to. When you first connect to a network, Windows will ask you what type of network it is, whether it’s a public network or a private network. Microsoft generally defines a private network as either a home network or a work network, while a public network is any network you may connect to at, say, a coffee shop or airport.
More traditional firewalls may be focused on addresses, ports, and protocols, but as an endpoint firewall, Windows Defender Firewall can be focused on applications. Figure 7-14 shows the list of applications and features installed on the system. You’ll see check marks next to the applications that are allowed to communicate through the firewall. These settings are based on zones. You can allow some applications to communicate on private networks while restricting their access on public networks.

Figure 7-14 Applications allowed through Windows Defender Firewall
Exercise 7-2: Windows Firewall
Enable the Windows Firewall log and turn on logging connections and dropped packets. After using your system for a while, take a look at the firewall log, which should be stored at C:Windowssystem32LogFilespfirewall.log on a Windows 10 system. Investigate the entries you find there.
Windows Firewall can be configured to log packets that are dropped, as well as connections that are successful. The log files can be parsed by a number of tools to generate reports. The firewall can also be scripted with VBScript or JScript. For example, you can programmatically add exceptions for applications or ports through the firewall. Figure 7-15 shows the settings for turning on the logs and where the log file would be stored.
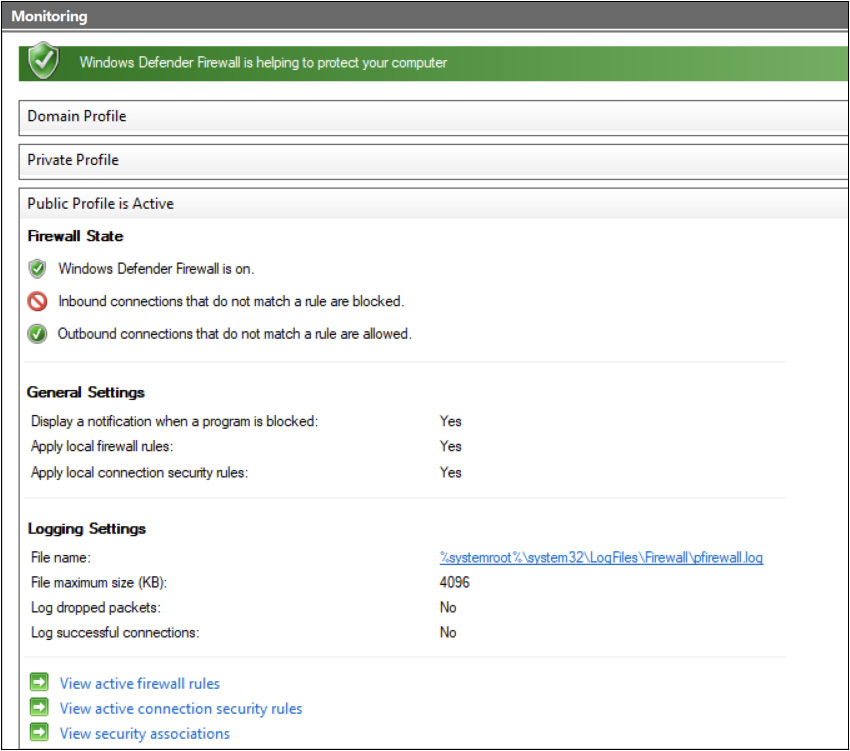
Figure 7-15 Windows Defender Firewall log settings
If you want to get into ports and protocols, you can do that through the use of the advanced settings. Figure 7-16 shows the advanced settings for one of the applications in the firewall. From here you can be specific about the IP addresses that you want to allow your system (and application) to communicate with. You can also determine the specific application binary that is allowed to communicate through the firewall on the specified ports. These rules can be configured in both inbound and outbound directions. Windows Defender Firewall has a lot of capabilities if you need to go digging into it.

Figure 7-16 Windows Defender Firewall advanced settings
IPSec
IPSec was introduced as part of the development of IPv6 and has been used for years as a way of providing remote access to networks over IPv4. One of the ideas behind IPSec was to create a policy database that would allow for security associations to be engaged as necessary. Based on the policy, any communication between two systems could be checked for authenticity or it could be encrypted using a pre-set encryption policy. Windows provides an extensive interface for adding IP Security policies, allowing the creation of a database to establish secure network connections between two systems. Figure 7-17 shows the settings for creating a new IP security policy. You might have a set of policies to enable encryption between a database server and an application server on your network, or you may have a policy on your servers ensuring that users are authenticated before they can initiate a connection between the client system and the server.
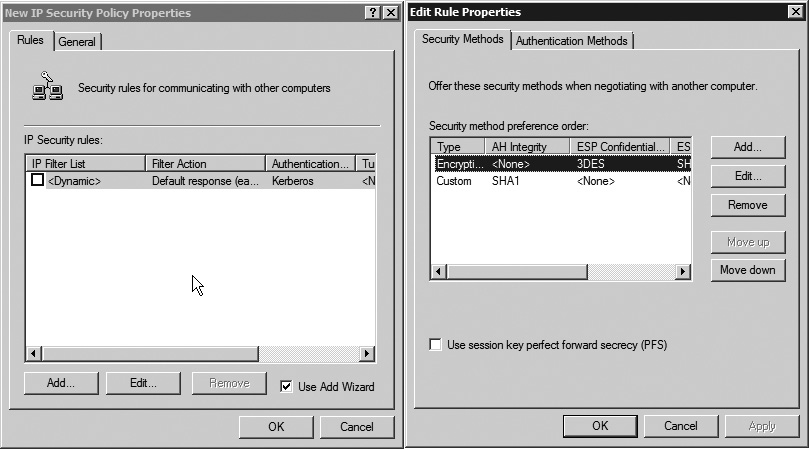
Figure 7-17 IPSec policy creation
VPNs
Windows has long had the ability to support remote access, including the ability to manage virtual private network (VPN) connections. The first remote access server capability was introduced in Windows NT 4.0. Routing and Remote Access Server (RRAS) was introduced with Windows 2000. RRAS can be a dial-up server as well as a VPN server, supporting a number of VPN protocols. In addition to simply terminating VPN connections, RRAS performs routing functions to get the remote connections access to the network the RRAS server sits on. It will also perform authentication or pass the authentication off to a RADIUS server on the network to ensure the remote user has permissions to gain access to the VPN server. RRAS also has the ability to restrict access to specific networks in order to further protect both the server itself and the network the server is providing access to.
While the feature still includes routing as an optional element, it is called Remote Access now. It can be installed by adding a feature from Windows Server Manager. When you add the feature, you have to select whether you want it to be a Direct Access and VPN server or a routing server. You can select both of them or they can be selected separately.
Remote Access has a solid set of routing protocols that it supports, including the Routing Information Protocol (RIP), Open Shortest Path First (OSPF), and Border Gateway Protocol (BGP). Windows Server 2008 introduced support for IPv6 and also introduced Network Access Protection, which checks the health of clients before allowing the VPN connection.
As noted, Remote Access supports a number of VPN protocols. As of Windows Server 2008, Microsoft supports the following protocols for remote VPN access:
• Point-to-Point Tunneling Protocol (PPTP) PPTP uses several protocols, including the General Routing Encryption (GRE) protocol and the Point-to-Point Protocol (PPP), to encapsulate packets and deliver them from the client to the remote access server. PPTP does not provide for encryption but simply general encapsulation of the packets.
• Layer 2 Tunneling Protocol (L2TP) L2TP is similar to PPTP, providing a protocol to tunnel higher-layer protocols. L2TP uses UDP to transport the messages and doesn’t include encryption or strong authentication.
• Secure Socket Tunneling Protocol (SSTP) SSTP allows for tunneling PPP or L2TP traffic through Secure Sockets Layer (SSL), which provides the encryption as well as the authentication. SSTP requires a valid certificate to be installed on the RRAS server in order to work.
• Internet Key Exchange (IKE) v2 IKE is used to establish a security association and is typically part of the IPSec set of protocols. IKE employs certificates and can establish encryption as well as identity.
Remote Access requires a system with multiple interfaces to function. The idea is that clients connect on an externally facing interface and are provided with an IP address on the inside of the network. All of the communication is tunneled through the connection between the client and the external interface and is then routed to the interface on the inside based on the destination address. The return messages are routed to the interface on the inside of the network. The RRAS server then associates the message with a particular tunnel interface back to a client so it is forwarded back through the tunnel.
Resource Management
A Windows server has many resources to manage, not just system resources like memory and storage space. Enterprise networks are composed of systems, users, services, printers, shared drives, and so on. Managing all of these components so that users can quickly and easily get access to whatever they need is important in order to ensure efficiency and productivity. A network operating system (NOS) like Windows Server won’t last long if it doesn’t enable users to perform their tasks easily and, preferably, make them more efficient. Ease of management is also very helpful. When Microsoft jumped into the server market, the predominant NOS was Novell’s NetWare. NetWare provided client software so users could access network resources like shared filesystems on the server, as well as printers and other shared resources. The client software allowed for connections to the NetWare server.
While providing access to shared resources is certainly important and helps save money by pooling resources, a NOS also provides central authentication and authorization for the network. This centralized approach to access control can save a lot of time and money and also put the decisions about who should be part of what groups in order to gain access to particular resources in the hands of administrators. Because of this approach, administrators can ensure that policies are followed appropriately. This centralization of management may be too much for some organizations, and because of that, smaller organizations can still get resource sharing on Windows systems without having to buy into the Windows Server line. Microsoft provides Workgroups to organize systems together in order to locate resources on a small network.
Windows Workgroups vs. Windows Domains
A workgroup is a peer-to-peer network, allowing for sharing of resources between any of the peers on the network. With a peer-to-peer network, there is no central authentication or authorization system. Workgroups can be helpful for small organizations as a way of collecting all of the systems and resources on the network into one group. Any network can have multiple workgroups, which can be seen when you explore the network. In addition to systems in the workgroup you are in, you will see other workgroups that exist on your network. Figure 7-18 shows a Windows 10 system named bobbieharlow in the WASHERE workgroup. Changing workgroups is easy to do. You would use a workgroup in a situation where you don’t have a server that could provide centralized administration. Without the centralized administration, there is nothing to prevent any system from joining a workgroup. Additionally, in order to gain access to shared resources on other systems in the domain, the resources would need to have access granted to everyone; otherwise, someone trying to make use of the resource would have to know a username and password on the hosting system in order to get access to it. This makes scaling, as well as security, more of a challenge with workgroups.

Figure 7-18 The Workgroup setting in Windows 10
A Windows domain, by comparison, is a central database of information about users, computers, and other resources on the network. This centralization allows for better management since users don’t have to be created on all of the workstations. In contrast to workgroups, not everyone can join a domain. In order to join one, you have to have the right permissions. Domain administrators would have these permissions, though individual users or groups could also be given permissions to add systems to the domain. In this case, each computer would have a domain account, and once the computer belonged to the domain, domain users would be able to access the computer by logging in with domain credentials. Being part of the domain allows systems and users to easily gain access to resources on other systems because the domain handles the credentials.
The central systems in a Windows domain are called domain controllers, and they hold the central database of information about users, groups, systems, and other resources on the network. Information across the domain controllers gets synchronized so that all domain controllers in the domain have the same information. This provides fault tolerance in case one domain controller goes offline, as well as load balancing since any domain controller can provide authentication and authorization services on the network.
Active Directory
Windows Active Directory (AD) is an implementation of the Lightweight Directory Access Protocol (LDAP), which is a subset of the larger X.500 directory definition. A very simple way of thinking about it is that AD is a special-purpose database, storing a lot of information about an organization and its information technology resources, including its users. While the information is stored in a flat database with tables, rows, and columns, it is represented as a hierarchy of objects, and each object has its own globally unique identifier (GUID). Each object in the hierarchy can be a container holding other objects, or it can be a leaf node. For example, you may have an organizational unit (OU) container that has a number of group containers underneath it in the hierarchy (or inside of it, if you consider them to be truly containers). Each of those objects is a container. At the ends, you might have a number of users. Each of these users would be a leaf node. Each object would have a number of attributes, including common name (CN), locality name (L), state or province name (ST), organization name (O), organizational unit (OU), and country (C).
Active Directory still has the concept of domains. An Active Directory domain would be composed of an X.500-based directory, a DNS name for the domain to be used for organizational purposes, a mechanism for authorization and authentication, and a set of policies dictating who can access resources and how they would be allowed to access them. However, you may have subdomains underneath the primary domain. All of these subdomains would be part of the domain tree of the primary domain. Each of these subdomains would enjoy a transitive trust with one another as well as their parent, allowing users in each of the domains access to resources in the other domains.
When you have a collection of domain trees, you have a forest. A domain tree is a collection of domains and a forest is a collection of domain trees. A subdomain would share a root domain with its parent, so mybiz.net may be the parent and seattle.mybiz.net may be a subdomain of mybiz.net. Those two domains would exist in the same domain tree. If My Biz had another business it owned that shared the same IT resources, the domain might be myotherbiz.com and it would be another domain tree in the forest named mybiz.net since the first domain created becomes the forest root domain, and the forest is named after it.
While this sort of configuration is possible, it is certainly confusing if you were to look at it hierarchically since mybiz.net would exist as a container for myotherbiz.com. A better organizational solution may be to have a completely separate AD infrastructure for myotherbiz.com in order to keep things as simple as possible. As with anything else, complications can lead to outages or misconfigurations, and these misconfigurations may lead to a variety of problems, not the least of which may be unauthorized access to company resources.
Windows has a rich user interface for managing the resources within Active Directory. This interface is called Active Directory Users and Computers, though there is another application called Active Directory Administrative Center (ADAC). The Active Directory Users and Computers application is shown in Figure 7-19 demonstrating the resources that can be added to the domain, including users, groups, computers, and printers, among other things. The ADAC is a newer interface and is built entirely on top of Windows PowerShell. Actions within the ADAC call PowerShell cmdlets to perform the functions requested.

Figure 7-19 Active Directory management in Windows Server 2016
Each domain can have a number of domain controllers and, not surprisingly, it’s important to keep all of the information between all of the domain controllers synchronized. Each AD has a Global Catalog (GC) where all of the objects for the forest are stored. You can access the GC over standard LDAP ports (3268 for the clear-text port and 3269 for SSL-encrypted) and issue LDAP queries against the GC. When it comes to replication, the objects in the GC are replicated across each of the domain controllers. This is done through the use of site links, and Windows supports two types of site links. The first is an IP site link, allowing replication to be done over remote procedure calls (RPCs). The second type of link is an SMTP link allowing replication to be done over e-mail.
The heart of the AD infrastructure is the domain controller, as has been alluded to before. New servers installed become domain controllers within AD. Introducing any server to the network as a domain controller is done using the dcpromo application. dcpromo handles all of the work of creating the schema for Active Directory and installs all the necessary services for a server to become a domain controller, whether it’s the first controller in the domain or some number well after that. The process of introducing a new domain controller is called promoting, and promoting a domain controller requires you to provide credentials with an appropriate level of access in order to complete the promotion.
With newer versions of Windows Server come more features and functionality. This means not all servers are going to be completely interoperable. Beyond the change in functionality with Windows Server, though, are functionality changes in both the forest and the domain. You select the functional level of both the forest and the domain when you create a new AD installation. You can also upgrade the functionality of servers that you have been upgrading the OS on. Once you upgrade the forest and AD, though, you will lose the ability to manage some of the features from older operating systems and their tools. Figure 7-20 shows the wizard you would use to create a new AD installation, where you would select the forest and domain functional level.

Figure 7-20 Selecting forest and domain functional levels
Users and Groups
Users and groups are some of the fundamental objects that are stored in Active Directory. In addition to storing information about each user, domain controllers will provide authentication and authorization services for users. Each user and group gets a Security Identifier (SID) when they are created, and since some users have been created as defaults for the system, these users and groups have SIDs that are the same across different installations of Windows. This means that the SIDs are well known and can be accessed based on the SID, no matter what Windows system you are trying to get access to. Information about the users, including cryptographic hashes of their passwords, is stored in the Security Accounts Manager (SAM) of the Windows registry.
Active Directory provides more of a phonebook service than simply storing usernames and passwords. With Active Directory, Windows can store addresses, phone numbers, e-mail addresses, job titles, organization names, and many other pieces of information associated with individuals. This can be very useful in navigating large organizations because you can attach people together in an organizational hierarchy with managers and direct reports. If you ever need to figure out what organization a colleague works in, you can find their manager and other people in the same group. In some companies, understanding what a particular organization actually does can be challenging, and having all of this information in AD can be helpful.
Windows uses the users and groups to make determinations about both authentication and authorization. With the Access Control Lists (ACLs) available for resources like files and directories, being able to organize users into groups can help secure filesystems by ensuring that the appropriate users are getting access to the right resources. Groups allow for the implementation of Role-Based Access Control (RBAC), which is easier to manage because users can be placed into the role groups and then permissions can be assigned to the role group rather than to a large number of individual users.
User authentication is handled using Kerberos, which is one of the major underpinnings of Active Directory. When a user attempts to log in, they go to the Key Distribution Center (KDC), which has access to the user information in Active Directory. If they successfully authenticate, they get a Ticket to Get Tickets (also called a Ticket Granting Ticket), which is valid for the local domain and is good for ten hours. It may be renewed anytime during the login session without requiring the user to reenter a password. The Kerberos infrastructure for all of the ticket management and distribution is embedded into Windows and doesn’t require a separate Kerberos infrastructure. One challenge with Kerberos that should be kept in mind when deploying Windows servers is how fussy about time it is. Kerberos is very time-sensitive, and if there is too much difference in the clock settings between clients and the server, it can cause authentication and access problems. Windows sets the maximum differential at five minutes by default.
Users are typically created in a domain context and stored in Active Directory, but in some cases you may have a need to create local users. These situations would be limited since local users would be created on individual systems, which reduces the ability to centrally manage users. In some instances, you may have systems that aren’t part of the domain. In this case, you would have to have a local user. You may also need to create a local user so a service can run as the local user with a specific set of permissions. You may also have a need for users to log in locally to a system that is part of the domain instead of authenticating against the domain.
Users also have profiles, and domain users can have their profiles stored on the server, while local users would obviously have their profiles stored on the system that the user and profile belong to. A profile is a collection of settings and files specific to a particular user. There are two types of user profiles when it comes to domain users: mandatory and roaming. A roaming profile is stored on the server and follows the user no matter what system within the domain they log in to. A mandatory profile can also be stored on the server, but a user can’t change anything.
Resource Sharing
Windows allows you to share a number of resources on your system with other users on the network. This may be simply sharing a folder on your computer, allowing access to your files from other systems, or it may be allowing access to a printer that’s attached to your system. You can also re-share a network printer that you have attached to, making your computer the print spooler that other devices send their print jobs to. Once you have shared network resources, you can assign permissions. These permissions can be different across users and groups, meaning you are using an Access Control List. The ACL is a list of users and groups with the relevant permissions associated with them. Just sharing a folder, drive, or some other resource doesn’t mean you lose control over who can make use of the resource. You need to set appropriate permissions for users on the network. Sometimes this can require some thought to make sure you are restricting permissions as much as possible so that you don’t end up allowing malicious users to cause damage to your files or allowing malware to replicate itself to your system.
Policies and Policy Management
Windows gives you a lot of ability in controlling how a system operates and what permissions are given to users and groups. Depending on whether you have Active Directory, you may be using group policies. There are also local policy settings that can be applied on individual computers. However, if a system belongs to a domain and has local policies applied, those policies will be overridden if there are policies that are pushed down from the domain. The policies have a lot of power and have a great deal of control over systems from a central point, including having the ability to install Microsoft System Installer (MSI) packages using a group policy. The group policy has far more control than the local policy and can be used to provide a great deal of control over the user desktops from a central location. The group policy also has precedence over any local policy settings that may be active. The underlying idea is that domain administrators would be setting specific policies based on the overall policies guiding the organization. Where a local policy may have a password policy indicating that there is a minimum password length of 0, a group policy, pushed down across the domain from Active Directory, may be more in compliance with the organization’s password policy and dictate a minimum password length of eight characters.
Local Policies
As you might expect, local policies provide control over the local system. The local policy provides control over the password policy for users on the system, as well as the account lockout policy, which dictates how many invalid login attempts are allowed before the system locks the account. Once an account is locked, there is a policy that allows it to be reset after a specified number of minutes. The local policy allows for the setting of an audit policy. An audit policy is helpful for detecting unauthorized access by finding failed attempts to access files or other system objects. These failures may indicate someone is trying to access resources they shouldn’t be accessing. This could be benign or perhaps someone being curious or accidentally clicking on something they didn’t mean to. It could also be malicious attempts to gain access to a sensitive file.
The local policy is also capable of specifying what rights users have. There are a number of user rights and they can be assigned to individual users or to groups. Typically, each user right would have a list of users and groups that have been granted a particular right. These rights range from being able to log in through Remote Desktop Services, to accessing the computer from the network, to logging on as a service, and a number of other rights. Figure 7-21 shows the Local Security Policy editor with the User Rights Assignment category selected and a partial list of rights that are available.

Figure 7-21 The Local Security Policy editor with the User Rights Assignment category open
The Local Security Policy editor is a snap-in for the Microsoft Management Console (MMC); the specific plugin to open up the policy editor is secpol.msc. We will discuss the MMC in more detail later in this chapter, but it’s worth noting that the various plugins for the MMC can be mixed and matched as necessary, and while there is a program entry in the Start menu under Administrative Tools for Local Security Policy, you can easily create your own console view including the local policy editor, as well as, for example, the Group Policy Editor, which is also just a plugin for the MMC.
Group Policies
When you read the term group policy, you may think that it refers to a policy that applies to a group. But in fact, what we are talking about is a group of settings that creates a policy. A group policy can be applied to any object in Active Directory, whether it’s a site, a group of users, a domain, or a specific computer. Group policies exist to provide more control over configuration, management, and software deployment within the computers and users of Active Directory. A wide variety of settings for the client systems can be controlled using a group policy. From the group policy Management MMC snap-in (gpmc.msc), you can create new policies and determine where they are applied within Active Directory. In order to configure a group policy, though, you need to use the Group Policy Management Editor (gpedit.msc). You can see the Group Policy Management Editor in Figure 7-22 opened up to the App Locker section. Here you would choose the applications allowed to run or not allowed to run.

Figure 7-22 The Group Policy Management Editor window
Every system could have a number of policies and settings, as well as multiple Group Policy Objects (GPOs), that need to be applied. There should be a way to prioritize these different configurations and policy objects. Fortunately, there is. The order starts with the closest to the user, and then makes its way up through Active Directory until it reaches the highest level. The reason for this is that local control is the least important thing when it comes to applying policies. An organization policy takes precedence over the settings on an individual machine, and a corporate policy takes precedence over an organization policy. The following is the order of precedence for applying policies, starting with the first set of policies to apply, and ending with the last ones:
1. Local group policy
2. Site GPOs
3. Domain GPOs
4. OU GPOs in order of hierarchy
While group policies are applied from Active Directory, it is possible to apply a local group policy to standalone systems and those that don’t belong to Active Directory. This can help ensure that systems adhere to a set of policies for the organization, no matter whether they are centrally managed through AD or not. The policies will be updated every 90 minutes, but rather than every system on the network updating at roughly the same time, there is a 30-minute randomization factor, which means that policies will be updated somewhere between 90 and 120 minutes.
While the majority of management is done through the graphical user interface, you can also use PowerShell to manage the policy objects. We’ll take a closer look at PowerShell later in this chapter, but basically it gives you the ability to script and automate work with the policy objects. Figure 7-23 shows an example of PowerShell getting a GPO and generating a report in HTML format.

Figure 7-23 PowerShell managing group policy
Windows Management
Most of the management of a Windows system, from a graphical tools perspective, is done through the Microsoft Management Console (MMC), which supports plugins. This gives a user an interface framework that has a consistent look and feel across all administrative functions. You would run the MMC and just use a plugin for it to get the specific management feature you were looking for, whether it’s computer management or management of the DNS server. The MMC can be used to manage both local servers and remote servers. Additionally, it gives you the ability to create your own custom management consoles by adding in the sets of plugins you would like and then saving the resulting console. You could have a custom management console with disk management and DNS management together in the same place. Figure 7-24 shows a list of some of the plugins (snap-ins) available for the MMC.

Figure 7-24 Microsoft Management Console plugins (snap-ins)
Microsoft has long provided a set of tools to aid in the administration of Windows servers from remote systems. Primarily, this is the same set of tools you would find on the server itself, but these tools are designed to install on desktop operating systems to facilitate management of the server. Where previously the Remote Server Administration Tools (RSAT) were available as a downloadable installer, they can now be installed as a separate feature from Features on Demand in Windows 10. This has been the case since an update in October 2018. RSAT can be used to administer server versions since Windows Server 2008 and only from desktop operating systems running Windows Vista or later. While both Vista and Windows 2008 are considered outdated, obsolete, and no longer supported by Microsoft, there are still enterprises using these (and even older) operating systems.
Allowing remote system administration access brings up its own set of challenges, including the need to potentially allow access to the appropriate ports on the server from a network where desktops live. There is a risk allowing direct access to server systems from a desktop that may be compromised. Providing this level of access might allow for a full compromise of your server infrastructure. There are ways to mitigate this, which include ensuring that specific subnets where administrators might be located have access to the server network, or even better, forcing your administrators to use a virtualized environment that either straddles the desktop and server networks or lives entirely within the server network but has access to the Remote Desktop Protocol port through a firewall or packet filter. That virtualized desktop environment could have the server administration tools on it, and all servers could be managed from it rather than having to open remote desktop services on all of the Windows servers in your network. The advantage of providing a choke point like that for management of your Windows network is that a single system, or cluster of systems, can be strictly controlled and monitored—it’s much harder to control, manage, audit, and monitor several desktop systems.
Automation
Windows provides a few different ways for system administration tasks to be automated. One of the easiest is making use of the Schedule service and the at command, which specifies that a command, script, or program should run at a designated time or date. The Schedule service could be used to automate a number of system administration tasks, including things like copying critical files off to an external filesystem for storage. This would make a rudimentary backup. Any task that doesn’t have the ability to schedule itself could be scheduled in this way.
You may want to write a batch file that you could schedule using the Schedule service, or it may just be something you want to run manually from time to time, but because it may be a set of commands requiring a minimal amount of programming logic, it may be easier to put it all together using a batch file. The batch file is a way of running multiple commands or programs in sequence while also providing some basic programming and logic constructs like if, for, and while statements that can control the flow of execution of the batch program.
Where batch programming provides some rudimentary capabilities that you could effectively run from the Windows command prompt, Windows PowerShell offers much deeper access to system administration functions, Windows APIs, and the ability to bundle little programs together into something called a cmdlet. A cmdlet is a programming object that makes use of the .NET Framework and implements a specific feature or function. It’s not a standalone executable like a batch file would be, though. The cmdlet runs inside of PowerShell. Cmdlets are typically named in a verb-noun fashion, making it easier to understand what they do. For example, you might name a cmdlet GetUser, which obviously gets a user. Each cmdlet returns a .NET object, so the cmdlets can be chained. Thus, the output of one cmdlet becomes the input to the next, and since it’s an object, it is a compound data type, meaning a number of different parameters can be handed off to the next cmdlet.
PowerShell has become an extensible and powerful tool, adding features like remoting, job scheduling, delegation, and script debugging. These features are common in programming languages and extend the capabilities of PowerShell to create a lot of capabilities for system administration and other power user tasks. For instance, the remoting capabilities in PowerShell give a system administrator the ability to write a script to perform a set of administration tasks and run that script on a large number of systems. This makes administration tasks significantly easier.
The PowerShell functionality is made possible through a set of extensions to the Windows Driver Model called Windows Management Instrumentation (WMI). WMI has been around for well over a decade. It was created as an add-on to Windows NT 4.0 SP4 and is a way of providing a structured and standard way of accessing management data. WMI uses the concept of providers, and Microsoft has been steadily adding WMI providers with each successive release of Windows, both the server and desktop releases. In order to develop a provider, you first need to create a manageable entity model, then develop the provider, creating a template using the Active Template Library (ATL).
The WMI model is similar in some regard to the Simple Network Management Protocol’s use of a Management Information Base (MIB). The MIB defines a model of data that can be populated and queried. Similarly, when you create a provider using WMI, you are defining a way of accessing management data. Where SNMP is defined as a protocol that has a server and client and expects to be accessed over the network, WMI is a programmatic mechanism. While WMI can provide programmatic access, Microsoft also provides console access through a utility called Windows Management Instrumentation Command-line (WMIC). This utility can be used to query different providers offered by the operating system.
There are two other ways that tasks can be automated across multiple systems. The first is PsExec, which was developed by the Sysinternals team at Microsoft. It allows you to remotely execute programs and also allows you to copy the necessary executable. If you don’t copy the executable to the remote system, the program will have to exist in the system path in order to run. Otherwise, you specify the path to the executable.
Windows Remote Management (WinRM) is another means of executing programs on a remote system and performing management functions. WinRM is based on the WS-Management Protocol, which is a Simple Object Access Protocol (SOAP)-based protocol that is considered firewall friendly. WinRM is part of the operating system and is one way to remotely manage installations in Microsoft Azure, which is Microsoft’s cloud computing platform. This makes automating and scripting management much easier in cases where you may not have console or any sort of GUI access to manage the device.
Configuration
A lot of system configuration is done through the use of Control Panel applets. These configuration settings are stored in the system registry, where they can be accessed using the Registry Editor. The Control Panel applets provide a way of organizing all of the different configuration options and settings into functional groups. While there are a lot of areas where you can do system configuration, the Control Panel doesn’t have all of the system configuration settings, and sometimes it can be difficult to keep track of the different places where you would access a particular configuration task. For example, some user configuration is done through a Control Panel applet, but if you belong to Active Directory and want to add and change users for the domain, you would need to get into the AD Users utility. This can be done by going into Administrative Tools in the Programs menu. Figure 7-25 shows some of the utilities in the Administrative Tools menu, including the Active Directory Users and Computers utility.
Figure 7-25 The Administrative Tools folder
The Active Directory Users and Computers utility is provided on Windows servers. If you were on a normal Windows desktop system, you would manage your users by going to the Control Panel and accessing the set of Administrative Tools that give you utilities like Services, which enables you to look at the different services running. You can also look at the services by clicking Manage in the context menu on My Computer or This PC, depending on the version of Windows you are running. Computer Management is a Microsoft Management Console snap-in that gives you access to utilities like Services, Event Log, and Logical Disk Manager. Many of these are also available through the Administrative Tools menu.
Auditing
Auditing is important as a detective mechanism in order to determine when access is being requested to unauthorized users. This can be an indication that there is an attempt to break into a system. Windows provides ways to enable auditing so that specific system events can be monitored and alerted on in case something happens. In Windows, you can generate events based on the success or failure of a particular action. Figure 7-26 shows the different areas where you can generate auditing events. These settings can be managed through the Local Security Policy utility.
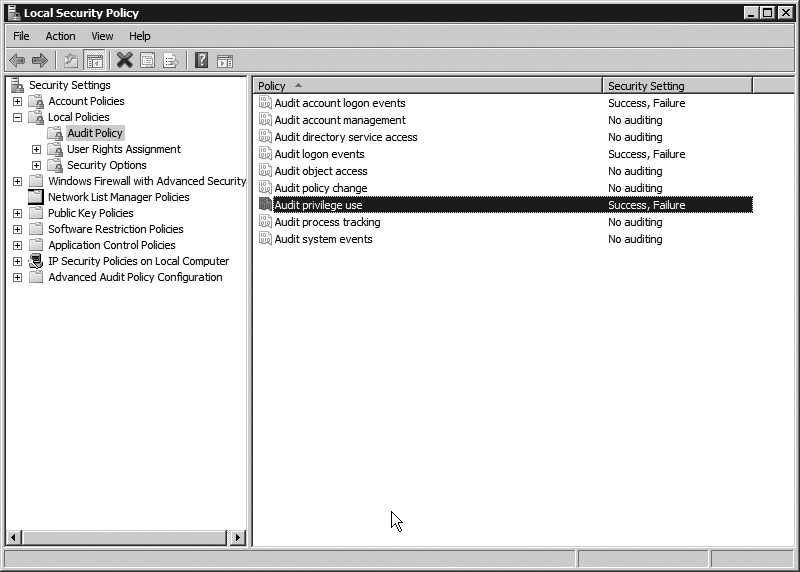
Figure 7-26 Setting auditing
Having an auditing policy can help in the system administration and maintenance of systems. If you were to audit logon failures, you might catch someone trying to gain unauthorized access to a system, and you might also get some indication as to how effective your password policy is. A large number of failures for average users, particularly right after they have had to change their passwords, might lead them to create their own memory aids, like writing their passwords on Post-it Notes. Not a good thing. If users are having difficulty remembering passwords, you can discover that by auditing logon failures. Similarly, if you were to audit object access failures, it may provide indications that different users may not be in the right groups. A user who should belong to a particular role may attempt to access a directory or file and get rejected. That rejection would show up in the audit log if you had the audit policy set appropriately.
With Windows Server 2008 and Windows 7, Microsoft provided 53 additional categories that could be audited. While the original, basic settings are still available under Local Policy Settings, the new settings can be found under Advanced Audit Policy Configuration. These new settings provide a much finer-grained look at what is happening on your system, giving you a look into directory services access, deeper detail on logon events, process event auditing like termination or creation, and object access. You can see the complete list of audit categories and subcategories in Table 7-1. These settings can be applied using a Group Policy Object, though the advanced settings are only available in Windows 7 and higher, so you would have to perform some filtering if you want to apply the settings to a wider range of systems or users than those still using an OS earlier than Windows 7.
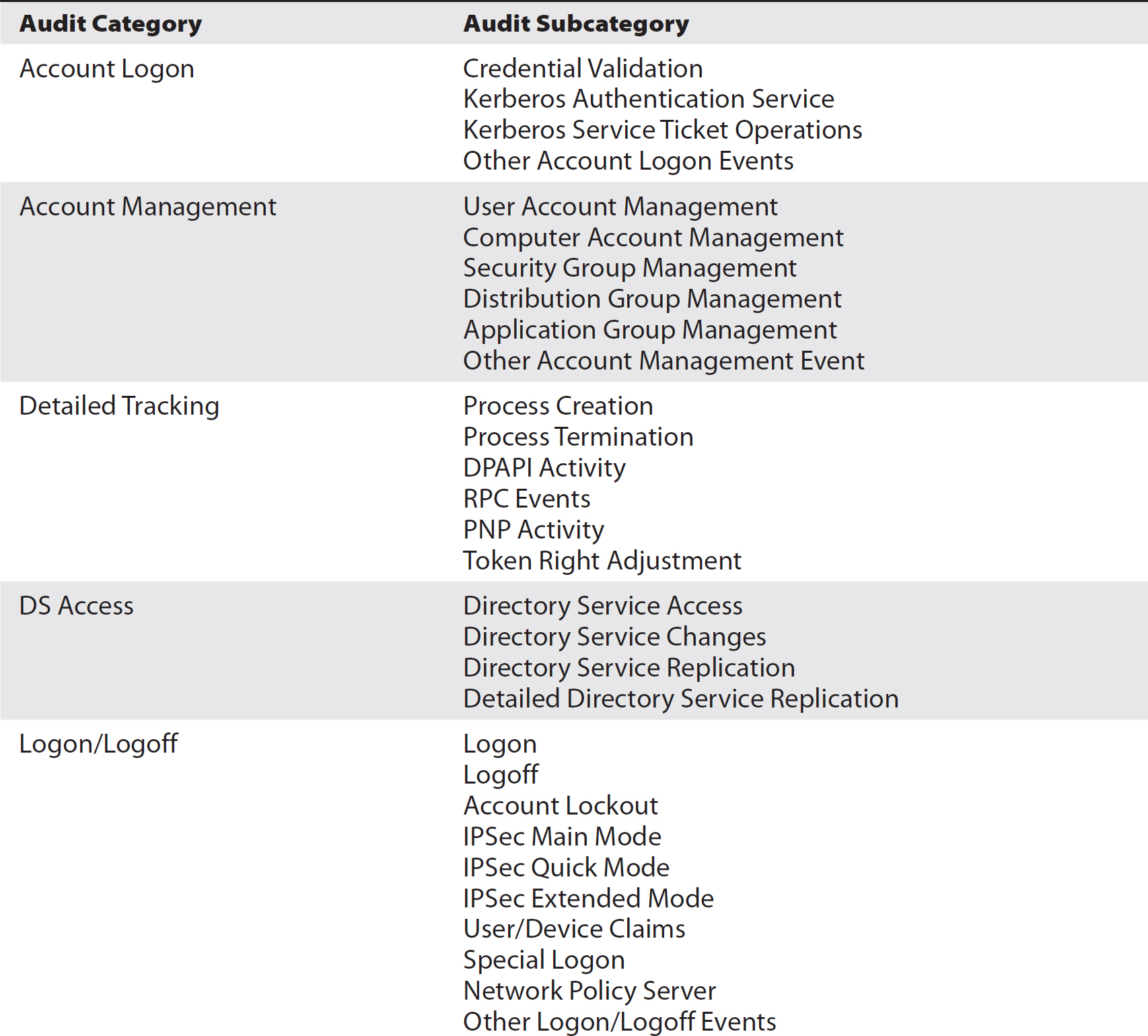
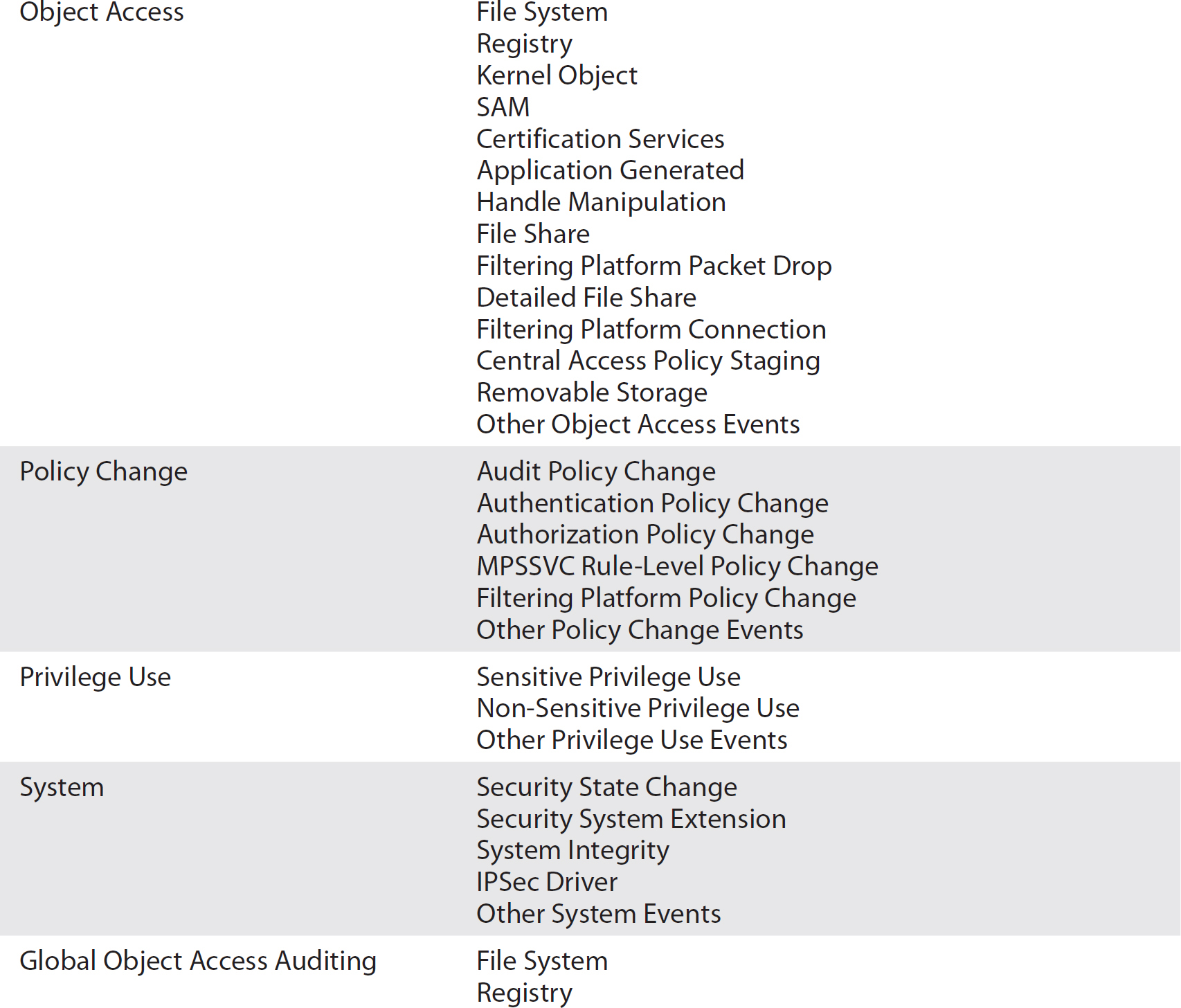
Table 7-1 Audit Categories and Subcategories
Each of these subcategories can be configured to audit success, failure, or both. While you can take a look at the policies using the MMC, you can also use a command-line program to do more specific digging. The utility auditpol can check the different categories, list them all, and check policies for different users and other SIDs. The advantage to the auditpol utility is that it can be included in scripts to either get or set various audit policies.
User Rights
User rights are a set of capabilities a user account has that are both rights and privileges. The rights determine how a user account can interface with the system, and whether they can access a system from the network, log on locally, log on using Remote Desktop Services, or be the user account for a batch job or a service. Table 7-2 shows the set of rights a user account can have on a Windows system.

Table 7-2 Windows User Rights
While rights determine how you can access the system, privileges determine what you can do once you are there. The rights and privileges are administered through the Local Security Policy editor. The different privileges that can be assigned are listed in Table 7-3.

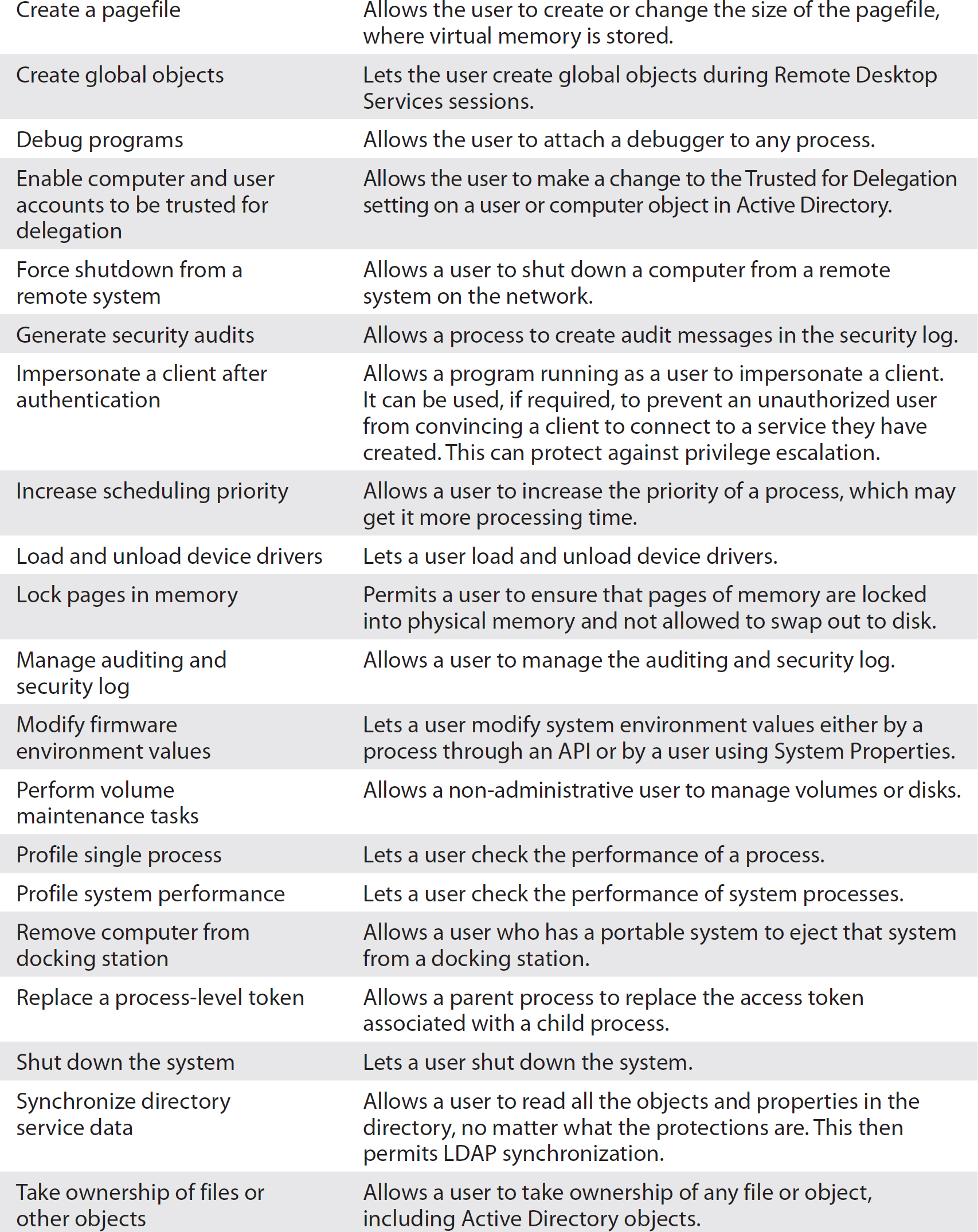
Table 7-3 Windows User Privileges
Figure 7-27 shows the Local Security Policy editor window. While the rights and privileges are not broken out into separate categories, with both falling under the category User Rights Assignment, the icons for each specific setting are different based on whether it’s a right or a privilege. The Local Security Policy editor also permits the editing of different security options on each system. These settings are broken up into the following categories:

Figure 7-27 The Local Security Policy editor window
• Accounts
• Audit
• DCOM
• Devices
• Domain Controller
• Domain Member
• Interactive Logon
• Microsoft Network Client
• Microsoft Network Server
• Network Access
• Network Security
• Recovery Console
• Shutdown
• System Cryptography
• System Objects
• System Settings
• User Account Control
Permissions
You can set permissions on objects in the Windows system, from files to directories to registry keys, group policies, and so on. Permissions can be given to users or groups. These include read, write, read and execute, full control, modify, and list folder contents. While you can certainly add specific permissions to every user on your system, it’s significantly easier to use Role-Based Access Control (RBAC) and place users into groups, then provide permissions to the group. Microsoft recommends using an AGULP (account, global, universal, local, permission), which is a way of using nested groups to implement RBAC. Implementing RBAC in a native-mode Active Directory implementation, the scheme would be called AGDLP (account, global, domain local, permission).
The way this scheme works is that accounts (A) get assigned to global groups (G) that represent a role in the organization based on a specific business need. The global groups would then belong to domain local groups (DL) that would have permissions assigned to them. In Figure 7-28, you can see where a set of permissions is assigned to a group rather than an individual. The advantage to adding users to global groups and then adding those groups into domain local groups is that global groups can contain users and global groups from the same domain, and then those groups are accessible across all domains. This lets you assign the global groups into domain local groups where you can assign permissions. This permits you to more easily assign permissions to users and roles from other domains in your organization.

Figure 7-28 Permissions on a folder
Registry
The system registry is where system configuration settings are stored. Prior to the registry, settings were stored in a text-based format in .INI files. The registry introduced a standardized format for data storage in a binary format since binary processing tends to be faster than text processing. The registry is represented in a hierarchical format, much like Active Directory. The registry supports a number of predefined data types, including string, binary, double word, and multistring. Each of these data types can be stored as values inside one of the keys, which are containers for the values. The registry has up to seven root keys that have been defined by Microsoft:
• HKEY_LOCAL_MACHINE (HKLM)
• HKEY_CLASSES_ROOT (HKCR)
• HKEY_CURRENT_USER (HKCU)
• HKEY_USERS (HKU)
• HKEY_CURRENT_CONFIG (HKCC) This key is only available in Windows 9x/ME and NT-based versions.
• HKEY_PERFORMANCE_DATA This key is only available in NT-based versions, but it’s invisible in the registry editor.
• HKEY_DYN_DATA This key is only available in Windows 9x/ME.
In addition to different parameters for the operating system and applications, the registry also contains the users and passwords for the system. This information is stored in the Security Accounts Manager (SAM) under HKLM. The SAM stores the user identifier in the domain or local system, a cryptographic hash of the user’s password, and the location of their user registry hive, among other details. Normal users wouldn’t see any entries in the SAM if they looked at the registry. Only administrators can see SAM details.
Windows comes with a utility to perform edits to the registry. The registry editor is regedit and provides a graphical interface for looking at the details of the registry. Figure 7-29 shows the Windows Registry Editor window and all the root keys available on the system. regedit can also use command-line parameters to perform specific changes to the registry. Additionally, you could create a .REG file with a list of changes you intended to make, and could use regedit to read the file and execute all the changes in it. regedit is also useful for making changes to permissions settings since the registry has the ability to set permissions for reading, writing, and changing the data stored in it.
Figure 7-29 The Windows Registry Editor window
PowerShell
Windows introduced a scripting language to replace the old DOS batch language in late 2006, called PowerShell. As previously covered in this chapter, PowerShell is not only a scripting language but also a command-line interface. Underneath PowerShell is .NET, and the “library” functionality is in functions called cmdlets that are special .NET classes. PowerShell invokes the .NET runtime and instantiates the classes. These cmdlets follow a verb-noun naming convention and provide a lot of functionality. Each successive version of PowerShell has increased the number of cmdlets available in the language. In Windows 10, running version 5.1, there are 544 cmdlets available.
In lieu of a GUI, PowerShell can be used to manage Windows systems and servers. As an example, you can use Install-WindowsFeature to add additional features to a Windows system. This doesn’t have to be run on the system where you want the feature installed. You can add the -computername parameter and specify the computer you want to install the feature to. If necessary, you can also add -Restart to make sure the system restarts when the installation is complete. Similarly, you can use Uninstall-WindowsFeature to remove features from a Windows system.
One feature of the command line in PowerShell that was missing with the command processor is the ability to pipe the output of one function to the input of another function. This PowerShell feature uses the same character, |, as the Unix command line and it generally works the same way. Output from one command may not necessarily be digestible by the input of another. As an example, in order to get the number of cmdlets installed on a fully up-to-date Windows 10 system running PowerShell 5.1, the following command line was necessary:
get-command | out-string -stream | select-string -pattern "^Cmdlet*" | Measure-Object -Line
In a Unix command line, the get-command output would just be piped into select-string (the PowerShell version of grep in Unix). However, in order for select-string to work, the output of get-command needed to be processed through out-string -stream. This string of commands gets the full list of commands PowerShell knows about and then looks for the string Cmdlet at the beginning of each line. This is necessary because there are other command types in PowerShell. Finally, the Measure-Object -Line counts the number of lines in the output.
You can also manage users, permissions, roles, and other administrative functions using PowerShell. It comes installed on Windows Server 2016 and 2019. If you are managing a Windows server without a graphical interface, you will need to use PowerShell. With PowerShell Core 6.0, you can run PowerShell on Linux and macOS exactly as it runs on Windows. Microsoft has made PowerShell open source and cross-platform.
PowerShell not only has become powerful but also has become ubiquitous, meaning it is installed by default on all modern installations of Windows. This makes it an attractive language to be used by attackers. It’s becoming more common for attackers to “live off the land,” meaning they make use of the tools they find. Linux systems typically have Python. Windows has PowerShell. There is no need to install additional binaries when you can use what’s already on the system. The attacker just needs to create scripts or load them onto the system. There are policies that can protect against unsigned scripts from being run, but this is a restriction that can be overridden with administrative control of the system.
Since attackers may use PowerShell, it’s essential to keep an eye on what is happening with scripts that are being executed. You can enable logging for PowerShell, which would allow you to generate alerts based on unexpected behavior. This logging can be enabled through the use of a group policy. Under Administrative Templates/Windows Components, Windows PowerShell, you will find logging for modules, script blocking, script execution, and PowerShell transcription. Once you are logging these activities, you can create alerts based on them with the right log management infrastructure.
Windows Security
Keeping up to date with the latest fixes in a world where a large number of people and organizations are constantly looking for the latest vulnerabilities and exploits can be challenging. Microsoft has had a Windows Update service since Windows 95, providing a website where people could check on updates for their system. Early on, the Windows Update service checked for updates to the operating system, but over time other Microsoft products like Office were given the ability to provide updates through the same infrastructure.
Back in 2002, Bill Gates announced the Trustworthy Computing Initiative to address issues in the software development life cycle at Microsoft and hopefully get ahead of the many bugs and vulnerabilities being found in their operating systems and applications. While this effort was generally considered highly successful, it hasn’t eliminated all the bugs and vulnerabilities. Considering the complexity of Windows and associated applications, it wouldn’t be possible to find and remove all the bugs. As a result, Microsoft has implemented a process for the regular deployment of updates to their operating systems and applications.
One aspect of security that can be easily overlooked is that of availability—and specifically, recovering from a lack of availability. Performing regular backups to your system is critical, but in these days of multi-terabyte drives or larger, backing up such an extraordinary amount of data can seem daunting. Keeping your system protected with a good set of policies can help with that, and using security templates helps keep things consistent across your organization. Also, securing your Windows services will aid in keeping intruders out.
EFS and BitLocker
Windows has had the ability to encrypt drives on their system since version 3.0 of NTFS in Windows 2000. This ability, called Encrypting File System (EFS), was a feature introduced to NTFS with that operating system release. EFS transparently provides filesystem-level encryption as opposed to drive- or volume-level encryption, which other encryption mechanisms might provide. Some of the settings for EFS can be pushed to systems using a Group Policy Object, though the initialization has to be done at the system in order to generate the keys and initiate the encryption. EFS makes use of a symmetric key, called the File Encrypting Key (FEK), to encrypt and decrypt the files. It uses a symmetric key because of the speed it offers, compared with an asymmetric key, though an asymmetric key is used to encrypt the FEK. The public key associated with the user is the key used to encrypt the FEK, meaning it requires a specific user account to decrypt files the user encrypted.
BitLocker, on the other hand, is a full disk encryption solution that has been offered since Windows Vista with the Ultimate or Enterprise editions and now with Windows 10, the Pro or Enterprise editions. BitLocker makes use of the Trusted Platform Module (TPM) installed on many modern systems. The TPM stores the key used to encrypt and decrypt the hard drive. Since the key is stored in hardware, there is no need to keep a portion of the hard drive unencrypted in order to read the key before decrypting the remainder of the hard drive. The process of accessing the key and accessing the drive, including encrypting for writing and decrypting for reading, is entirely transparent to the user, aside from needing to authenticate to the hardware before the operating system starts up. BitLocker, by default, uses AES encryption with a 128-bit key, although it can be configured to use a 256-bit key. BitLocker differs from EFS in that it offers full disk encryption, which would be in place before the operating system starts up. EFS, on the other hand, is in place to encrypt specific files and folders and not the entire hard drive.
Updates and Hotfixes
Hotfixes and updates apply to individual applications or systems. While Microsoft previously called any patch that was released outside of a service pack a hotfix, they have since started calling everything an update. Updates are deployed through the Windows Update Service, which started in Windows 95, though it has seen a number of changes since then. Initially, you had to check the Windows update server for new updates. Microsoft released the Critical Update Notification tool shortly after releasing Windows 98, which provided a way to regularly check for critical updates in the background without someone having to specifically go to the Windows update server. With Windows Me, Microsoft replaced the notification tool with Automatic Updates, replacing the notification with the ability to just automatically download updates after prompting the user that they were available.
Rather than just releasing hotfixes or updates as they had them available, Microsoft decided to make life easier on system administrators, as well as themselves, and have one day every month where they release all of the updates they have available, regardless of their criticality. This is colloquially called Patch Tuesday and happens on the second Tuesday of every month. Other software vendors have followed suit by either releasing their available patches on the same day or picking another day of the month to release their updates. Infrequently, Microsoft will issue a fix outside of the Patch Tuesday date for extremely critical issues, but it’s very rare. One thing a regular schedule helps with is ensuring that Microsoft has the time to appropriately run their fixes through quality assurance (QA) testing before releasing them, so as to be certain that the issue is fixed and that other issues aren’t introduced. Windows does provide different settings for applying patches. The default is to apply them automatically, as shown in Figure 7-30.

Figure 7-30 Windows Update Advanced Options
While Microsoft performs QA tests on their patches, they can’t possibly check against every piece of third-party software in the world that runs on their systems, and there are times when an update from Microsoft has caused another application to break. Because of this, it’s worth performing testing for all patches on a lab or test system before deploying the updates to production. You can check updates from Microsoft and determine which ones are important to you, and then make use of Windows Servers Update Services (WSUS) to deploy the updates to the systems in your network. Rather than using the Windows Update server, you would have all of the desktops in your network check your WSUS server and update from there. This can go a long way toward reducing outages caused by conflicts between a Windows update and a piece of third-party software.
Service Packs
Service packs are generally a roll-up of all the hotfixes and updates that have occurred since the last release or service pack. A service pack that only included updates since the last service pack would be considered incremental. With an incremental service pack, you would have to apply service pack 1 before applying service pack 2 since the fixes in service pack 1 would not be in service pack 2 and sometimes there would be dependencies. Not all service packs are incremental, however. Many of them are cumulative, meaning that all fixes since the major release are included. If there have been two previous service packs, all of the fixes from those service packs would be included in the third service pack.
Service packs, like updates, are delivered by the Windows Update mechanism. Sometimes, in addition to updates and fixes, a service pack may introduce entirely new features. One example of this is Windows XP, Service Pack 2 (SP 2), which introduced significant functionality. In addition to the updates, SP 2 included significant updates to the firewall and added some Bluetooth support, a pop-up blocker for Internet Explorer, and WPA encryption capability for Wi-Fi, among other enhancements. This resulted from Microsoft’s increased focus on security, which led to the determination that, rather than waiting for the next release of Windows, Windows XP needed these enhancements more quickly.
Backups
It goes without saying that backing up your systems is very important to protect against the loss of critical data. Recognizing the importance of file backups, Microsoft released NTBackup in Windows NT in 1997, where systems could back up to tape using the Microsoft Tape Format (MTF). The Windows NT line continued to have NTBackup until Windows 2003, including Windows XP and Windows 2000. NTBackup supported backing up the System State data, as well as alternate data streams, permissions, the Windows registry, boot files, Exchange Server data, Encrypting File System files, disk quota information, and a variety of other critical system information. With domain controllers, NTBackup could back up Active Directory.
NTBackup was replaced with Windows Backup and Restore, starting with Windows Vista, and Windows Server Backup for the server operating systems, beginning with Windows 2008. Figure 7-31 shows the Windows Server Backup wizard, starting a backup schedule. These more recent backup utilities no longer support tape backups. In order to back up to tape, you need a third-party application to perform tape backups. The new utilities support backing up to optical media, external hard drives, and disk images like the Virtual Hard Disk (VHD) file format. Windows Server Backup now requires a Windows server with a backup role added to be able to back up to. A Windows server cannot back up to a local disk. It needs a backup server to back up to.

Figure 7-31 The Windows Server Backup wizard
There are a few different strategies you can use to perform a system backup. The first would be to perform a full backup every time you backed up your system. This reduces the amount of time and effort required to restore the system, but a great deal of space is needed to store the backups. Another strategy is to perform a differential backup. Using differential backups, you would perform a full backup once, and then subsequent backups until the next full backup, which would include everything that changed since the last full backup. This means you get one large backup of all of your data the first night. The second night, you would back up all of the data that had changed since the night before. The third night, you would get all of the data that changed on the second day, as well as the third day. As a result, every night’s differential backup would get larger than the night before. Again, this takes up storage space, but it can be much easier to do a restore.
Another strategy is an incremental backup. Again, you perform one full backup, probably once a week. Every subsequent backup after that would include only files and data that had changed that day. If you did your full backup Sunday night, on Monday night you would back up the data that had changed on Monday. Tuesday night you would back up the data that changed on Tuesday, and so on. While this reduces the amount of storage space required to back up the data, it does take quite a bit of time to do a full restore. If you had a catastrophic failure on Friday, you would have to restore the full backup from Sunday, and once that was done, you’d have to restore Monday, Tuesday, Wednesday, and Thursday nights’ backups because each day has data that has changed since Sunday’s full backup, and you can’t guarantee that a subsequent update has a newer version of data that changed on an earlier day.
Security Templates
Security templates are good ways of providing protection for the systems on your network. A security template is a stored Group Policy Object with a lot of preconfigured settings that you might want stored for a particular circumstance. Your template might have settings for the following categories:
• Software Settings
• Windows Settings
• Administrative Templates
• Control Panel Settings
Windows comes with some predefined security templates. These templates could be applied to systems where they might be beneficial and would have a generic set of policies and settings that could be used quickly and easily. They could also be used as the starting point for a more specific GPO that would be specifically applicable to your organization. Microsoft provides the following templates, though their availability depends on the operating system you have installed. They can be found, typically, at C:WindowsSecurityTemplates.
• Default Security (Setup Security.inf) This is created at the time of the installation of the operating system and contains all of the settings applied during the installation. Microsoft recommends against applying this template using group policy because it could degrade performance.
• Domain Controller Default Security (DC Security.inf) This policy is created when a server is promoted to a domain controller. It is the set of default settings created at that time. It can be reapplied, but it may overwrite permissions on files and registry keys. This may not be what you want and could cause performance and availability issues.
• Compatible (Compatws.inf) This is a set of changes that would be consistent with the requirements for software that does not adhere to the Windows Logo program for software. This also removes all users from the Power Users group.
• Secure (Secure*.inf) This template applies a number of security settings that are least likely to impact application compatibility. It also makes a number of changes regarding the use of NTLMv2 by default.
• Highly Secure (hisec*.inf) This template is a superset of secure templates and includes additional security measures like restrictions on the levels of encryption and signing required for authentication.
• System Root Security (Rootsec.inf) This template has permissions for the root of the system drive.
• No Terminal Server User SID (notssid.inf) This template would be used to remove unnecessary Terminal Services SIDs on a system that wasn’t using Terminal Server.
• Internet Explorer (ieacls.inf) This allows you to audit Internet Explorer use.
Securing Windows Services
Windows Services are background processes that typically start when the system starts up, though they may be set to start up manually. This might mean that another process will start it up as it needs to in order to perform a specific function. In Figure 7-32, you can see the Properties dialog box for the Background Intelligent Transfer Service, which is set to start up automatically, but delayed. Services are attached to users, and this service, like many others provided by Windows, is running as Local System. Each service must have a user it launches under in order to provide it with specific rights and privileges. One of the major concerns with Windows services is that the user account a service runs on may have too many permissions. If a service is compromised, the attacker inherits the rights and privileges, and if the account has too many privileges and permissions, the attacker can more easily perform functions like adding users or creating backdoors.

Figure 7-32 Windows services
Aside from ensuring that services aren’t running with too many privileges, it’s useful to shut off services that aren’t necessary. Microsoft has been much better about that over the last decade by disabling many services by default. There is still work to do, however. Many services that aren’t necessary are still enabled by default because they are part of the generic set that gets installed so that Windows works well for the widest range of users. These should be disabled. In the case of the server operating system, Windows Server comes with almost nothing installed. As noted earlier, since Windows Server 2016, you can even forego the desktop when you do a server install. Services only get added as roles and functions are added to the system, and that gets done with the full consent of an administrative user. In the case of desktop operating systems, however, a basic set of functionality gets installed whether some of the services are needed or not.
One thing to keep in mind about services is that they are exactly as the name suggests: they are there to provide a service to a user or another application, whether it’s a networked service or a local one. They aren’t applications that might have no communication with other applications. Since they exist solely to provide services, and therefore likely need to communicate, they put the system at risk. Any service that is running can have vulnerabilities. Because of that, disabling as many services as possible will provide some additional protection to the system since one avenue of attack will have been removed.
As you can see from Figure 7-32, there is a setting for Startup type. This setting can have the values of Automatic, Manual, or Disabled. If the service was set to start up manually, it could still be started. The best way to keep a service off is to set the Startup type to Disabled. It may also be worth considering service recovery for those services you want to have installed, particularly those that are critical. Windows services generally have some basic configuration. Usually, the first action of the three that are allowed for each service is Restart Service. The other possibilities are Take No Action, Run a Program, or Restart the System. Depending on how critical the service is, you may need or want to restart the system if a couple of attempts at service restart don’t work. Alternatively, you may want to run a program that can take some additional corrective action.
Securing Windows Services
Windows has a lot of services that it exposes to the outside world, though Microsoft has made a significant effort to restrict the number of listening services enabled by default over the years. However, the Windows Server line exists to offer services, and as a result there are commonly ports open on Windows Server and the applications behind those ports. As with any network service, it’s important to ensure those services are protected as much as possible using a defense-in-depth strategy where possible. Common services you’ll see running on a Windows system are Internet Information Services (IIS), Microsoft SQL Server (MSSQL), and often Terminal Services.
IIS
IIS is one of the most exposed services that Windows offers because web servers are such a common service to offer. In addition to being common, a web server is more likely to be exposed through the firewall than other services, which may only be exposed within a corporate network or be even more tightly restricted. Because of this level of exposure, it’s important (to state it mildly) to make sure you lock down your IIS installation. As with any piece of software, and particularly those exposed to a large group of users the way a web server is, it’s important to keep up to date with service packs and fixes. Even though IIS may not have any current known vulnerabilities in the version you have installed, there may well be unknown vulnerabilities with exploits that could put you at significant risk. Additionally, new vulnerabilities and bugs are discovered on a regular basis. So, step one to ensuring you have a better-secured IIS installation is to get your update process in place.
You should also ensure that the content you are exposing through IIS is on a partition that uses NTFS as the file system. Unlike other file systems that Windows supports, NTFS has support for permissions. You will want to create permissions that only allow limited access to the files and directories being used by the web server. Microsoft creates a built-in user, named IUSR_<computername>, to be used by all users who don’t authenticate against the web server. Most commonly, this would be the majority of accesses to your web server. In order to serve up web pages to these unauthenticated, anonymous users, the IUSR account has to have read privileges to the files. Adding any additional permissions to the IUSR account can be dangerous.
Microsoft also has a couple of utilities that can be used to better lock down IIS. The first is called IIS Lockdown. It’s a wizard that will remove unnecessary functionality from your IIS installation, including disabling features like the FTP or NNTP servers if they are not being used. It will also check for script types you want to disable and any virtual servers you want to remove that may have been installed. The entire configuration for IIS is stored inside something called a metabase. This is an internal, hierarchical database IIS uses for all of the configuration settings. The metabase consists of two files that are stored in XML format in the Windows system directory tree. The IIS Lockdown utility creates a backup of the metabase before making changes, should you choose to roll back to settings prior to the tool being run.
IIS Lockdown also runs another utility called URLScan, which provides a number of Internet Server Application Programming Interface (ISAPI) filters that protect both IIS and your web applications from malicious traffic. URLScan can prevent particular requests from being accepted by the web server. For example, a number of verbs are supported within HTTP that allow for the manipulation of content on the server—for example, PROPFIND, MKCOL, COPY, and MOVE. In order to keep these extensions from being used against your system to make changes you don’t expect, use URLScan to block them. URLScan can also remove particular header fields you don’t want to serve up, like the version of the web server you are running, commonly thought to provide information about avenues of attack for an attacker since the version number can be used to search for known vulnerabilities and exploits.
SQL Server
Microsoft has a number of recommendations for securing a SQL Server installation. Those recommendations fall into four categories: platform, authentication, objects, and applications that access the database.
The platform (physical system and operating system) should be addressed, as with other network-facing servers, by hardening it to remove any unnecessary software and services. It should also be kept up to date with the latest patches. Additionally, making use of a firewall, including Windows Firewall, is a good practice that will help restrict access to the system from unauthorized locations.
Use the appropriate authentication based on your needs, whether it’s Windows authentication, SQL Server authentication, or a mix of the two. Only provide access to those who need it and only the access they need. This principle of least privilege is common and should also be used on a SQL Server installation. Additionally, make sure the sa (system administrator) account has a strong password associated with it; a common attack against SQL Servers is to go after the sa account since many installations have had blank or easily guessable passwords.
Objects are database components like databases and tables. As noted earlier, you should ensure you are providing access to only those users who require it. In addition to restricting access, you may need to pay attention to the access of users directly logged in to the system. You can protect data stored in the database by encrypting it. SQL Server supports its own encryption, but you can also encrypt the data inside of your application before storing it to SQL Server.
Applications are consumers of the data in the database, and as such, they need access to the database. In order to protect the data, you should be using safe coding practices, including input validation to ensure you are not passing a query into the database that may inadvertently expose unexpected data to the end user. If you are using the database as a storage service for a web application, you need to be concerned with SQL injection attacks. One way of protecting against unexpected data is to use stored procedures. A stored procedure will provide a well-defined interface to the database without directly exposing the underlying structure and content of the database. Using this technique can protect against coding errors in the application because the SQL query is stored on the database itself where it can’t be altered, and where, presumably, it has been put after extensive testing.
Terminal Services
Terminal services are how you provide users with remote access to a system in Windows. You would run terminal services on a Windows server and users could connect using a client on their system, getting a desktop session on the server. The client uses the Remote Desktop Protocol (RDP) to connect to the terminal server. An advantage to providing access to users in this way is the ability to better control behavior and limit access while keeping up with all the latest operating system and application updates. You can also ensure that anti-virus is installed and up to date.
When you create a terminal server, you should make sure it’s a standalone server, not a domain controller. Providing users access to a domain controller will put your domain infrastructure at risk. Since you are giving users access to this, you want to make sure nothing critical runs on it, just the user-related functions and applications. Also make certain the disks are formatted with NTFS and not another file system. This will ensure you have the ability to set Access Control Lists on all file permissions so that one user doesn’t have unnecessary or unexpected permissions to the files of another user. While sharing is often a good thing, it can expose sensitive data or create the potential for data to be damaged or destroyed either accidentally or inadvertently. While we are talking about partitions, you should have a separate partition or drive altogether for user data, away from the operating system.
Your terminal server should require network authentication. This forces authentication to happen before the login screen is displayed. Early versions of the client, and even early versions of the terminal server service before Windows Server 2003 SP1, were unable to support this level of authentication. As a result, Microsoft recommends using an IPSec VPN to protect communications between a client and server from a man-in-the-middle attack. While later installations do offer protection against these sorts of attacks by supporting network authentication, providing access to the terminal server over a VPN may still be a good thing. On top of authentication, you should make sure your terminal server requires strong encryption over the communication channel.
Using group policies, you can have a lot of control over what users are capable of doing once they are on your system. This enables you to restrict what applications they are using. You may be using the terminal server to provide access to a single application, for example, and as a result, users shouldn’t be able to run any other program once they are logged in. This level of control over what users can do will help protect your system.
Windows as a Service
With Windows 10, Microsoft has moved away from new releases in a traditional sense. At the moment, there will be no Windows 11, for instance. Instead, Microsoft is releasing new functionality periodically, along with the normal monthly updates. This means there are no upgrades. Instead, everything is just an update. This makes it easier for businesses to keep up with the newest releases, since managing the upgrades to new versions is challenging; it’s time consuming and expensive. The objective to Windows as a Service is to reduce the fragmentation of Windows installations. If it becomes easier to keep systems up to date, they will be kept up to date. This reduces the chances that old vulnerabilities might be exploited.
Microsoft offers a choice of three channels for receiving new Windows 10 features, allowing you to choose how quickly you get new features from Microsoft. This allows you to determine how much vetting through other users new features are subjected to before you get them. If you want the features as soon as they are released to the general public, you can go with the Semi-Annual Channel. Most Windows PCs will get these updates through this channel. The only way to not get them pushed to the PC is to defer them, or to select a faster release, both of which channels we’ll discuss shortly. If an organization is using Windows Server Update Services (WSUS), which is a means of controlling which updates systems in the environment get, the organization can defer updates going to endpoints. Additionally, Microsoft System Center Configuration Manager (SCCM) or Windows Update for Business provide more control over how updates are pushed to desktops and enterprise tablets.
Even if updates are deferred, they will eventually get pushed out to endpoints, again to ensure Windows is kept up to date on as many devices as possible to help protect more devices. Think of it as vaccinating PCs. It prevents bad diseases from spreading, even if one PC gets infected.
The Long-Term Servicing Channel (LTSC) is for mission-critical systems. These may be automated teller machines (ATMs), point-of-sale systems, or medical devices, for example—basically, any system whose outage would cause a serious problem to customers or have a major impact on the business. Devices in this channel will only get quality updates—those designed to fix serious bugs without introducing new features. The LTSC will get major updates every three to five years, which is the same time frame as Windows versions were previously released.
Finally, there is the Windows Insider Channel. This is essentially where beta releases are pushed out. Anyone getting Windows Insider releases gets features before anyone in the Semi-Annual Channel gets them. This helps Microsoft to test early builds of Windows features before they are pushed out to a much wider audience.
A good approach to using these channels is to implement tiers. Any noncritical device could be in the Windows Insider tier. This is useful, even if there are hundreds of thousands of other people around the world, because you can test your own business applications with new features before a wider group in your organization gets the updates. This would allow you to consider whether to defer the update or make configuration changes, for instance. Finally, the innermost tier would be your mission-critical devices. These devices would be in the LTSC.
Chapter Review
Microsoft Windows is an incredibly complex set of operating systems with a lot of management capabilities. The fact that they are generally so easy to use has drawn a large number of users to the platform. Because of this, and because Windows has been installed on most personal computers sold over the last couple of decades, Windows has become the predominant operating system around the world. This also has made Windows a target for those interested in finding vulnerabilities and writing exploits. Microsoft introduced the Trustworthy Computing Initiative in 2002, but systems as complex as Microsoft Windows, with as many third-party developers and users as it has, will always have the potential for vulnerabilities. Due to this, Microsoft has developed a life cycle of security through the planning and development processes that extends all the way to getting updates in the hands of users as quickly as possible.
Microsoft provides a large number of administrative capabilities, and in the last few releases of Windows, they have made it much easier to script those capabilities via Windows PowerShell, which uses the .NET Framework to provide extensive management and instrumentation functionalities. PowerShell is very good at giving system administrators programmatic access to nearly every aspect of management and configuration on the system.
Active Directory is the heart of a Windows network when it has a server infrastructure. Active Directory is an implementation of LDAP, providing a place to store a large amount of data about users and other resources on the network. One other thing Active Directory provides is the ability to store and push out Group Policy Objects to provide a consistent system configuration across all the Windows clients on the network. It also lets you install new software and restrict the types of applications used on a system (it could disable Solitaire, for example).
PowerShell is a scripting language that provides powerful functionality for managing systems. If you have a system where you don’t have access to a GUI, PowerShell can be used to manage it. It uses cmdlets, which are special .NET classes. There are currently 544 cmdlets in PowerShell 5.1. The current version of PowerShell that is available as of this writing is PowerShell Core 6.0. This is a cross-platform implementation of PowerShell that will run on macOS and Linux in addition to Windows.
Windows as a Service is an attempt by Microsoft to reduce the fragmentation of deployed Windows systems. Since most PCs will be in the Semi-Annual Channel, they will get updates semi-annually. This means new features and all quality improvements are pushed automatically to devices. The Windows Insider Channel is used by people who want to get a look at features before the rest of the world does, or the rest of the organization. The Long-Term Stability Channel is used for mission-critical devices. Only quality improvements are pushed out regularly. Every three to five years, a new set of features will get pushed to devices in this channel.
Windows Update will take care of home users and run automatically. In a business environment, Windows Update for Business will provide the same set of functionalities. The Microsoft System Center Configuration Manager (SCCM) provides the means for updates to be controlled to endpoints with different configurations. Also, Windows System Update Services (WSUS) is like hosting your own Windows Update server inside the organization. It also provides the means to control updates, delaying ones you wouldn’t want endpoints to get for stability or compatibility concerns.
Questions
1. What does Microsoft Windows Update use to check your system for updates?
A. JavaScript
B. VBScript
C. An embedded Java applet
D. An ActiveX control
2. Which of the following might cause a tracert to fail?
A. A router dropping ICMP messages
B. A firewall dropping UDP messages
C. A router dropping TCP messages
D. A router dropping ARP messages
3. You want to write a batch file that makes changes to the Windows registry. Which command would you call to make those changes?
A. cmdreg.exe
B. regcfg.exe
C. regedit.exe
D. regedit.bat
4. Windows Firewall logs are stored in what format?
A. W3C Extended log format
B. Windows Firewall log format
C. IIS log format
D. Raw text format
5. You are writing a backup plan. Your goal is to try to ensure you have speed to recovery, but also to reduce the amount of storage space needed for the backups as much as possible. Which backup scheme would you choose?
A. Full backups nightly
B. Full backups weekly; differential backup nightly afterward
C. Full backups weekly; incremental backup nightly afterward
D. Differential backups nightly
6. If you want to enable auditing on the systems on your network, how would you do it?
A. Use the Security Manager snap-in.
B. Use the Audit Logging snap-in.
C. Use the Audit Logging tool.
D. Use the Group Policy Editor.
7. You have a set of users you want to assign some permissions to. What does Microsoft recommend you do to accomplish this?
A. Create a global group with the users in it, and then create a domain local group and assign the permissions to the domain local group.
B. Create a local group, and then create a global group and assign the permissions to the local group.
C. Create a local group, and then create a global group and assign the permissions to the global group.
D. Create a local group and assign the permissions to the local group.
8. You see a system that shows an SID of S-1-15-32-545. What do you know about that SID?
A. It’s the SID for the Administrator user.
B. It’s the SID for the Administrators group.
C. It’s the SID for the Users group.
D. It’s the SID for the Guest user.
9. You want to perform some basic filtering on your network interface but you don’t want to employ the firewall. What could you do instead?
A. Let IIS do the filtering.
B. Establish an IPSec policy to perform the filtering.
C. Encrypt all of the traffic.
D. Install the Advanced Deep Packet Inspection Firewall.
10. You are trying to decide which edition of Windows 10 to install on your systems, which you then expect to connect to Active Directory on your network. Which edition does not support AD?
A. Home Premium
B. Professional
C. Ultimate
D. Enterprise
11. Which protocol is part of the base Windows operating system and enables you to remotely manage a Windows system?
A. SSH
B. WinRM
C. PowerShell
D. WinCP
12. If you need a firewall, anti-virus protection, and an overall endpoint security solution for Windows, what could you use at no cost?
A. VirusTotal
B. McAfee
C. Symantec
D. Windows Defender
13. What is BitLocker used for?
A. Whole disk encryption
B. Key management
C. Key escrow
D. Single file encryption
14. What feature would you install on a Windows server to provide endpoint VPN services that could use L2TP as an encapsulation protocol?
A. VPN Service
B. Remote Access
C. L2TP Service
D. Routing Service
15. If you want to have a GUI on your Windows Server 2016 or Windows Server 2019 installation, what feature should you install?
A. Desktop Experience
B. Desktop Expressions
C. GUI Management
D. Desktop Management
Answers
1. D. Windows Update uses an ActiveX control that must be installed on your system in order to check for the existence of updates. JavaScript and VBScript wouldn’t have the amount of control needed, and Microsoft has a rocky history with Java, so they wouldn’t use a Java applet.
2. B. While some versions of traceroute send UDP messages to high-numbered ports that traceroute is known to use, the Windows version of tracert performs the same function using ICMP Echo Requests. Since it’s ICMP messages going out, and ICMP errors going back, a firewall or router dropping ICMP messages could cause a tracert to fail.
3. C. regedit.exe is the Registry Editor, and in addition to having a GUI mode, it can also be called from the command line to make changes, including reading in a set of registry changes stored in a .reg file. The other commands indicated don’t exist.
4. A. Windows Firewall logs are stored in W3C Extended log format, enabling any tool capable of reading that format to read and parse the firewall logs. While IIS can log in an IIS-specific log file, Windows Firewall doesn’t write logs in that format.
5. B. A full backup once a week followed by a differential each night provides a compromise between speed to recovery and the space required to store the backups. Full backups nightly would take a lot of disk space. Incremental backups save disk space but would be time consuming to restore since all incrementals need to be restored after the full backup is restored. A differential backup nightly has nothing to provide a differential against since there is no indication that there was a full backup at any time.
6. D. The Group Policy Editor allows you to specify a Group Policy Object with auditing enabled that could be used on all the systems on your network. None of the other tools exist.
7. A. Microsoft recommends always assigning permissions to a local group that is made up, ideally, from global groups. This is a way of employing Role-Based Access Control.
8. C. That SID belongs to the Users group.
9. B. An IPSec policy could perform some filtering of network traffic. Internet Information Services (IIS) could only do filtering if the traffic was destined for IIS. Encrypting all of the traffic doesn’t perform filtering, and there is no Advanced Deep Packet Inspection Firewall.
10. A. A standard Windows Home installation does not let you join a corporate domain. All other editions are acceptable.
11. B. WinRM is a protocol that can be used for remote management of Windows systems. SSH is Secure Shell, which is an encrypted protocol used for remotely accessing systems. It is commonly found on Unix-like systems. While you can get implementations for Windows, SSH is not part of the base operating system. PowerShell can be used for remote management but it is a language and command-line environment, not a protocol. WinCP is not a protocol.
12. D. Windows Defender offers a firewall and anti-malware, as well as other security features, and is installed by default on modern Windows systems. VirusTotal is a website that will check possible malware against multiple anti-malware engines. Symantec and McAfee both provide complete endpoint solutions but they are not free.
13. A. BitLocker is used for whole disk encryption. You may be able to store keys in Active Directory, including recovery keys from BitLocker. It also doesn’t do key management. You will get a recovery key from BitLocker in case you forget passwords, but it’s up to you to manage that key. BitLocker does not do single file encryption.
14. B. The Remote Access feature, which used to be called Routing and Remote Access Service (RRAS), provides endpoint VPN capabilities, including the use of L2TP. None of the other answers are real services and, because of that, none of them can offer endpoint VPN capabilities.
15. A. Microsoft is calling the GUI on a server Desktop Experience because it ends up looking like a traditional desktop installation. None of the other answers are real things and so they are not features that could be installed.
Exercise Answers
Exercise 7-1
Your output should look something like this:

Exercise 7-2
Your file should have contents that look like this:




