CHAPTER 16
Internet of Things (IoT) and Embedded Devices
In this chapter, you will learn:
• What is the IoT
• Which devices are considered IoT devices
• Which protocols are used for the IoT
• IoT security considerations and protections
You likely have heard about the Internet of Things (IoT). It’s a buzzword that shows up in the news, especially if the news you are reading includes coverage of technology. Certainly, discussion of the IoT has shown up in security-related news. Much like the so-called dark web, the IoT is an overlay network on top of the Internet. The dark web is a subset of devices that are connected by way of the Internet and transmit messages to one another using the same protocols that the Internet uses, but they offer services that are only available through the use of direct connections to one another. These connections are tunneled, meaning they are encapsulated inside of other protocols, and encrypted. If you know how to “talk to” these special systems, you can join the dark web. The same is essentially true of the IoT. It is a subset of Internet-connected devices that communicate using the same protocols as other Internet-connected systems use.
Typically, IoT devices are limited in some way. They are often resource constrained and don’t have the same means of interacting with users that general-purpose computing devices have. This lack of interactivity is one reason compromises of these devices are difficult to detect; users have no good way of detecting that an IoT device has been compromised as long as the essential function of the device is retained.
Because of their limited nature, IoT devices may require special protection or even isolation. The capability to easily identify these devices is also helpful when trying to secure them. There are so many different types of IoT devices, and often when you are looking at an enterprise network, you may not even be aware of which IoT devices are being used or where they are located. Fortunately, there are websites that are designed to help you locate and keep track of the different embedded devices that are Internet-connected.
The Internet of Things
Like so many current technologies, the idea of the IoT has been around for decades. The IoT is the collection of devices around the world that are essentially “dumb” devices, meaning they probably have limited processing power because they are designed to perform a small number of specific functions. They also have nonstandard interfaces, meaning you probably don’t interact with them via a keyboard or a pointing device. An IoT device may be an embedded device, which would perform a specific function and run a real-time operating system, which is different from a general-purpose, interrupt-driven operating system. As an example of a common IoT device, Figure 16-1 shows a smart thermostat (from Nest). The input “mechanisms” you have are a rotating ring and a center that can be pressed. You make selections by rotating the ring until you are on your choice and then pressing the center. This thermostat is network-connected, as shown by the display of the local weather. The nonstandard interface combined with network connectivity and a special purpose makes this an IoT device.

Figure 16-1 Smart thermometer
As you may have read, there are security concerns associated with IoT devices. Some of these devices run Linux as an operating system. This provides the kernel for hardware control, but sometimes there is also a limited shell as an operating environment. An attacker could gain access to a device and get a shell, which would give the attacker a limited command set. This could allow the attacker to install and run additional software. This additional software doesn’t need to do much to be dangerous. In the case of Mirai, which was a botnet comprised of IoT devices, all each device needed to do was send network requests. The Mirai botnet was the source of many distributed denial-of-service (DDoS) attacks.
Mirai was first discovered in 2016 but has remained operational, as the software has been used to create many more networks of bots. In 2018, it was used as the foundation for more than a dozen new botnets. In late 2018, more sophisticated botnet software called Torii was discovered. This botnet client has the capability to achieve persistence in one of six different ways, all related to how Linux typically starts up services. This may be in a startup file like .bashrc. It may also start execution using /etc/init or /etc/inittab. The process may be called System Daemon, which some people, even if they happen to see it, may overlook. Torii makes use of port 443, which is the commonly used port for TLS/SSL. However, Torii does not encrypt any of the traffic. It also wasn’t immediately clear what the purpose of Torii was.
These botnets are built around simple software designed to run on limited-capacity devices. In the case of Mirai, for example, the client was developed in the programming language C. These limited-capacity devices are likely to run on processors such as the Advanced RISC Machine (ARM) family. RISC stands for reduced instruction set computing, and processors using that style of architecture have a small set of instructions compared with a complex instruction set computing (CISC) processor. A RISC-based processor may require less power than a CISC-based processor because of the simplicity of the instructions. This is one reason why these processors are commonly used in devices like those in the IoT.
IoT Device Types
Home automation is a common application for IoT devices. These are devices that are usually small, have little to no user interface, and perform specific functions. In some cases, there is no need to have an interface at all. Some devices, such as light bulbs, require an external device to provide the interface. The Philips Hue bulbs, for instance, require an app on a device like a smartphone or a tablet. In the case of the Philips Hue bulbs, you need an intermediate device to interact with the bulbs. For example, if the Philips Hue bulbs are paired to an Amazon Echo hub, you would use a device that has the Amazon Alexa app installed, the interface for which is shown in Figure 16-2. There is also a hub provided by Philips (at an additional cost on top of the bulbs) that would require a different app on your device. You might also get a hub like the one from Samsung for their smart devices called SmartThings. Each of these different hubs requires its own corresponding app to manage the bulbs.
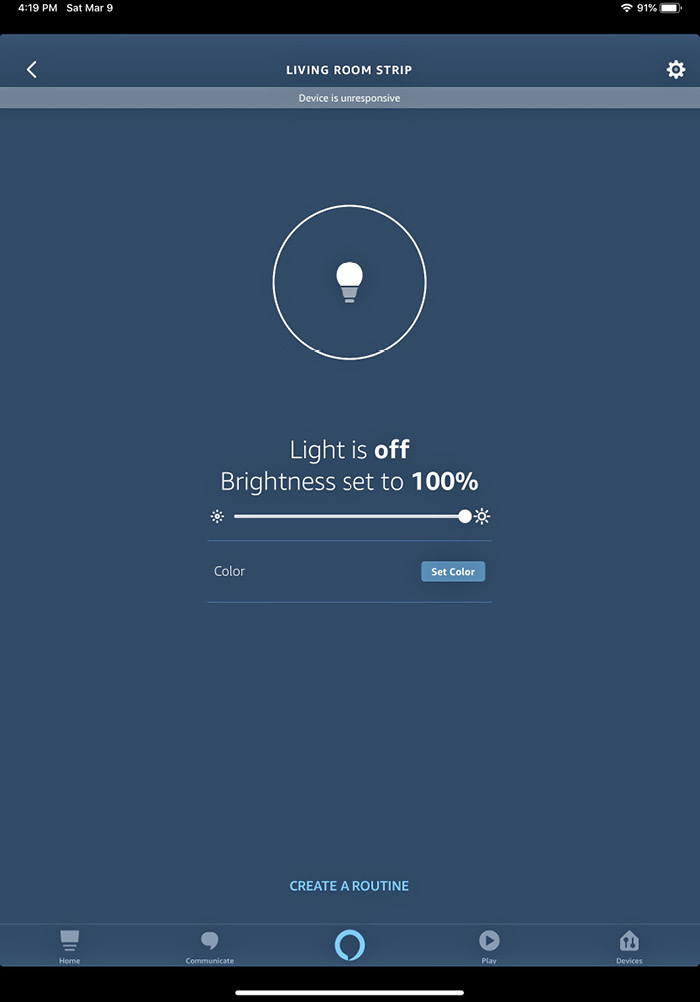
Figure 16-2 Amazon Alexa app
Using these hubs, you can control many different types of home automation devices. In some cases, you may require additional support, as is the case with Amazon Alexa. With Alexa, you need to acquire and enable skills for your Echo hub to be able to manage your smart devices. This may be the case for specific functionality that could be in the specific app but not in the Alexa skill. The Philips Hue bulb is said to have more functionality using the Philips app rather than a third-party app like Amazon Alexa. As you can see in Figure 16-2, there is a color setting. Philips says the functionality in the color portion, specifically, is better in their app. Either way, you require multiple pieces of hardware that may use multiple protocols to function.
The communication from the hub to the end device will commonly use either Zigbee or Z-Wave. As introduced in Chapter 14, these are protocols used for personal area networks (PANs). They are designed for communication over short distances using radios that don’t require a lot of power. In addition, these devices communicate with the network by using Wi-Fi if they have network functions, such as the Nest thermostat (shown in Figure 16-1), which pulls weather information and also pushes data about the device’s functions to server infrastructure managed by the manufacturer. In the case of the Nest thermostat, you can see the history of energy usage, or how much time the thermostat caused the overall system to run. Figure 16-3 shows the number of hours the heating system ran during the beginning of March in my home in Colorado. The color orange indicates heating, whereas the display would be blue for air conditioning. This data is meant to provide you insight into how much energy you are consuming, enabling you to manage your energy budget, if needed, by adjusting the temperature settings in your home.

Figure 16-3 Nest app showing Energy History
One of the great things about these little devices—thermostats, light bulbs, appliances, security cameras—is the amount of processing power they possess. Not to continue to pick on the Nest thermostat, but its technical specifications are generally available. The Nest thermostat has an ARM A8 processor. These processors are capable of running at a clock speed of 1 GHz, or 1 billion cycles per second. With a RISC-based processor, this may be close to one instruction per second, since the instructions in a RISC processor tend to be simple and fast. All of this is to say that there is plenty of power in these devices, and though the Wi-Fi capabilities are generally older, that’s still potentially 50 Mbps of throughput.
The potential of IoT devices is not lost on manufacturers. Figure 16-4 shows a graph of the trajectory of IoT devices according to SRI Business Consulting. We are at a point where we have crossed the border into the physical world.

Figure 16-4 IoT device trajectory over time
A good example of crossing over to the physical world is the Tile tracker, which is a Bluetooth-based device allowing people to find missing items. The thing about the Tile, though, is all the users become a network. If you have the Tile app on your smartphone and you come in range of a Tile, it reports back to the Tile infrastructure so when you go looking for your Tile tracker, you can know exactly where your lost item is, because your Tile tracker is with it.
Medical Devices
Beyond being taken over and used as weapons in botnets, there are other important security issues associated with various types of IoT devices. One type of IoT device that poses very troubling security issues is those that provide medical monitoring functions. Health monitoring devices have become common. These devices may be used, for example, by doctors to monitor their patients’ vital signs without the need for the patient to be in the hospital. While these devices have the potential to lower healthcare costs as well as offer more comfort to patients by enabling them to recuperate at home while still being monitored, they have security issues. Knowing that these devices make personal health information (PHI) digitally available to healthcare providers, attackers commonly target them, as well as the systems that store the data within healthcare facilities. PHI may be valuable to attackers as a means to make money through fraud, extortion, or other criminal behavior.
You may even be familiar with some of these health monitoring devices. It’s possible you are even wearing one. The Fitbit has, for many years, been a popular health monitoring device. It may not fit in the same category necessarily as a fully networked device like a security camera or a smart thermostat, but it does communicate wirelessly and has some processing power. Fitbits (and similar devices) are generally paired with smartphones or maybe even computers. One thing these devices may be good at is keeping track of where you are or have been. This isn’t the same as the breadcrumbs that may be used by some smartphones or mapping applications, but if you are engaged in an activity, your location may be trackable. This means your device, and the servers where data from your device is stored, may have a record of places you have been.
Some of these devices are sometimes referred to as the Internet of Medical Things (IoMT). Remote monitoring is not the only application these devices are good for. They may use local storage in addition to remote storage without the device being network-capable. One example of this is a blood pressure monitoring device. You can get a blood pressure cuff that will pair with your smartphone to keep track of your blood pressure over time. You can see samples of these readings in Figure 16-5. Only one of these readings was taken using the device the screenshot was taken from. All of the others were stored with the provider of the device. This means you can use a device with Bluetooth capabilities to transfer a medical reading to a smartphone that transfers the data to an Internet-based provider.

Figure 16-5 Blood pressure readings
There are many other medical devices that have varying levels of interactivity with the network, as well as varying levels of sensitivity for the data. There are devices like cochlear implants or pacemakers that may be considered IoT devices. Senior citizens can be monitored to make sure they are not experiencing any difficulties, which can be helpful for cases where they have no one else to look in on them. This is similar to or a replacement for the “I’ve fallen and I can’t get up” device that has been sold for years to seniors.
Transportation Devices
If you own or lease a newer model vehicle, it likely has the capability to connect to a network. This capability may be included, in part, to allow your car to install updates to the software. This software may provide entertainment, safety, or navigation features. Either way, if your car’s settings provide a way for your car to connect to a Wi-Fi network, you have a device that runs specific, rather than general-purpose, software and has a network connection. Attacking cars through their computing capability has become popular in the last several years.
Also when it comes to vehicles, you may have run across devices that will scan license plates and read radio frequency identification (RFID) tags. These are devices that sit in toll plazas without attendants, doing their work.
Of course, beyond the vehicles themselves, there are applications in tracking and managing shipping, for instance. When it comes to transportation, we are not limiting ourselves to the wheeled variety. There are also ships. Ships need to be tracked and also shipping containers that ships are carrying. There are likely small tracking devices that are embedded in the ships and the containers so businesses are always aware of their inventory and where it is. You also have planes. While they aren’t specifically IoT, there are transponder devices that can be tracked and, when we start talking about searching for and tracking, you will see planes showing up on sites where all of that information could be found.
Sensors
There are countless sensors in the world, some of which have a form of network connections. There was a time when remote weather stations, for example, needed a person to be present to gather and report data collected by the weather sensors. The same was true for devices like strain gauges that are used to determine the structural integrity and reliability of bridges or even amusement park rides. These sensors (and there are thousands and thousands of them still in use around the world) required a human to be present to either connect a device that could read the sensor or to pull the data out of a monitor connected to the sensor. When you can attach a small, networked system that can read the data and send it along, whether over a local area network or even over a cellular data network, it allows for faster, more reliable collection of the data.
Small-form-factor devices like the Raspberry Pi and Arduino are opening the door to sensors that can have cheap computers to connect the sensor to. A device like a Raspberry Pi has general-purpose input/output (GPIO) connectors. This allows anyone to create a hardware device that could connect to the Raspberry Pi. These GPIO connectors can be read programmatically from the Raspberry Pi. There are many libraries and programs available for addressing the GPIO connectors. These inexpensive devices can be placed anywhere in a very small space without keyboard, mouse, or monitor (a mode commonly called “headless”). They can be connected to a physical Ethernet network by cable or they can support a Wi-Fi USB interface. You could also use a cellular connector with it.
In any case, these are essentially IoT devices. They are small, powerful devices that may not have a traditional way of interacting with them, if the keyboard, mouse, and monitor are not connected. These are also devices, like the Nest thermostat discussed earlier, that use ARM processors. They also regularly run Linux, though beyond just the kernel and a very lightweight user environment, like a thermostat, the Raspberry Pi can run a complete Linux distribution like Debian, Ubuntu, or even Kali, a security-oriented Linux distribution.
Finding the “Things”
There are a few helpful websites that keep track of IoT devices. You can search for and locate IoT devices using these sites. While the different sites will enable you to search for IoT devices, the capabilities from one site to another can be very different. It’s not the same, for instance, as comparing Google and Bing. First, take a look at Shodan, which is available at www.shodan.io. This site offers free accounts but also has enterprise accounts. Shodan also provides an application programming interface (API) for developers. Shodan works by looking at the headers that are returned from services available on the systems. You can search, based on those headers, for specific devices. As an example, Figure 16-6 shows the results from a search for “raspberry pi” to find Raspberry Pi devices. Again, this relies on a banner or header provided by a service having that text.

Figure 16-6 Shodan search for Raspberry Pi
You’ll see along the left side of Figure 16-6 that the results include a list of countries. There are also lists of services, organizations, and operating systems. Interestingly, in the list of OSs, there are results for Raspberry Pi indicating Windows as the operating system. This is because Microsoft supports the ARM processor and the Raspberry Pi with an operating system called Windows 10 IoT Core. By clicking one of the items in the lists on the left, you can narrow your search. Clicking Windows, for instance, brings up the devices that are running Windows and also have indicated Raspberry Pi in some response.
In the list of services along the left side of Figure 16-6, one service of particular note is Minecraft. Selecting that shows a list of Raspberry Pi servers running a Minecraft service. You can see a partial list of those servers in Figure 16-7. The query used to get this list is raspberry pi port:"25565". This list provides us a lot of detail. We not only have the IP address, we also have the Internet service provider (ISP), the country the server is located in, and the date the service was added to the Shodan database. Of course, Shodan offers a lot of other capabilities, including the capability to generate maps showing where the systems are believed to be located.

Figure 16-7 Shodan search for Minecraft servers on Raspberry Pi
The Shodan search capability is very powerful. What we’ve seen so far is minimal. You can drill very deep using the search terms. As an example, let’s say you want to look for any device running the nginx web server on the subnet 125.69.4.0/24, a randomly selected address for the purposes of this example. You can use the following search: nginx net: "125.69.4.0/24". The results will be specific to your target network. You can also search for vendors, such as Cisco. You could look for Cisco devices in Canada, for instance, using the search term cisco country: "CA".
Other search keywords you could use include the following:
• city If you want to look for devices in a specified city
• geo If you want to search based on coordinates, such as those for the company you work at or are helping
• hostname If you know the name of the host you are looking for
• port If you are looking for devices that have a specific port open
• os If you want to indicate the operating system the device should be running
• before or after If you want to search within a particular timeframe
Shodan also provides the ability to export your results, which is unusual for a search engine.
Shodan is not the only website to search for IoT devices. You can also use Thingful (www.thingful.net), which also catalogs these devices so they can be identified. Thingful has a less well-defined search syntax compared to Shodan, but you can still search for IoT devices in Thingful. Just enter a value in the search box and, optionally, a location in the location box. If there are things to be found in the database, you will be shown the results on a map, which is quite different from the list of results shown in Shodan. You can see these results in Figure 16-8 as well as the search boxes. You will have to look closely for results, though. What you’ll get is a colored dot on the map. To get details, you click the dot, which pops up a box similar to what you see in Figure 16-8.

Figure 16-8 Thingful results for Raspberry Pi
You can also search for classes of devices. For example, you can find thousands of weather stations. They are all over the world. If you search for “weather” in Thingful, you will get many results. What you get with Thingful in some cases that you may not get with Shodan is actual weather readings. Some weather stations provide readings that you can see in Thingful. However, there are also many other types of devices in the Thingful database, such as webcams. In Figure 16-9, you can see a live weather webcam in downtown Denver, Colorado. This doesn’t provide any readings, of course, as it’s a webcam. However, you can zoom in on the map and locate exactly where it is.
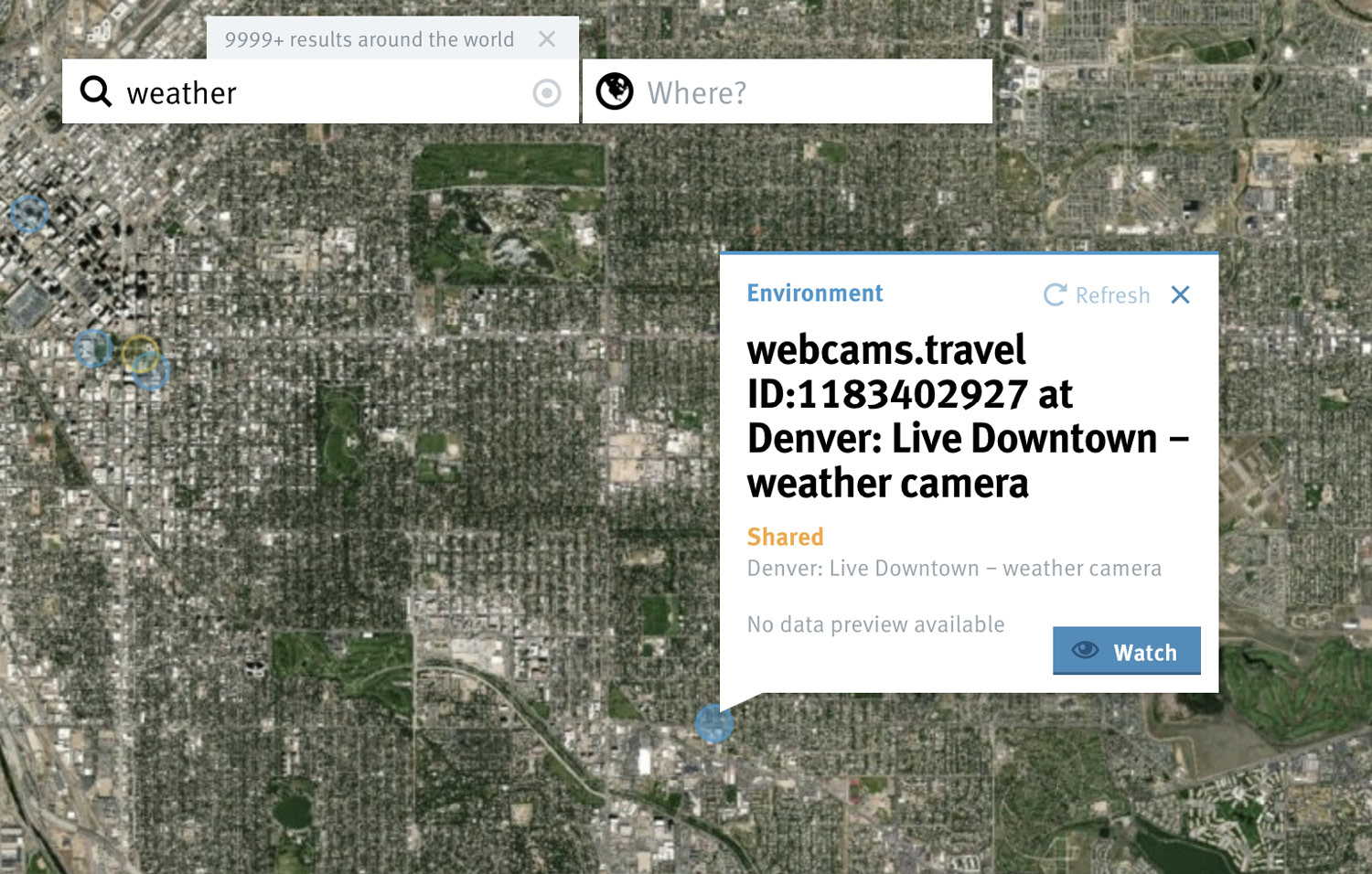
Figure 16-9 Thingful results for weather stations
Since the interface to Thingful is primarily a map rather than just a search box, you can more easily just go exploring. It is a highly interesting collection of data that can be found on this site. As an example, just randomly clicking around turned up some bike-share stations. Global Bike Share at Hiawatha Ave. and 50th St. (as the map in Thingful doesn’t provide place names, a search on Google Maps was required to locate this in Minneapolis, MN) has 3 bikes and 12 spaces. It’s also interesting to find devices in the middle of the ocean. At one point, a while back, I was able to locate the transponder for an airplane by just clicking a dot in the ocean. Recently, I located several buoys in the middle of the ocean, the values from one of which are shown in Figure 16-10.

Figure 16-10 Details from a buoy in the Atlantic
Thingful does not rely on discovered data. Anyone can submit a public repository to be indexed by Thingful. Once the repository has been submitted and indexed, the data discovered would make its way to the map. The submission form also has a place to submit data samples, described in JavaScript Object Notation (JSON) format.
Managing the Things
The website www.statista.com estimates there are about 26 billion IoT devices in the world today and that this number is anticipated to rise to about 75 billion by 2025. So, that means roughly tripling the number of devices in about six years. That’s an extraordinary rate of increase. With so many devices and the devices having no traditional interface, you may wonder how they are managed and controlled.
First, it’s worthwhile to talk about a management architecture. Much like a web application architecture, there may be multiple tiers for the management infrastructure. First, you have the devices themselves. These would connect to an application somewhere, whether it’s local to the network where the device is or if it’s a server somewhere on the Internet. The controllers the devices connect to could be anywhere. Behind the controller would potentially be a data store. Of course, this sort of design would depend on the needs of the application.
One issue with IoT devices is that they need some sort of controller. This controller, especially in the case of consumer devices, would be on the Internet and the device would be behind a network address translation (NAT) device, sometimes called a firewall even if there are no explicit rules configured. You could make an IoT device on the inside of the network accessible by opening a port translation through the NAT device providing a public IP address and port for the controller on the Internet to connect to. This would rely on users’ ability to configure devices they may not be comfortable configuring at all. This requirement would limit the usefulness of these devices and likely restrict their usage. Instead, it’s easier for a device on the inside of the network to communicate out to a server. This means when the controller/server communicates back, there is already an open channel. It does require, though, that the inside device be regularly polling out or checking with the controller device on the Internet.
A protocol that is commonly used for transport of data is the Hypertext Transfer Protocol (HTTP). One reason for its common usage is that it’s the protocol used to communicate with web servers and therefore is well understood. In order to pass messages from a controller to a device and back, there are two things that are needed on top of the transfer protocol. The first is a way to represent the messages. This may be done using JSON, because it’s a self-describing notation. The following code shows an example of what JSON looks like. It uses keys to identify what the data is and then uses values for the actual data. This combination is often called a key-value pair. What you see in this code is a collection of colors and that values can be compound rather than just a single value. Each value could be a nested collection itself, meaning you may have a collection inside of a collection.

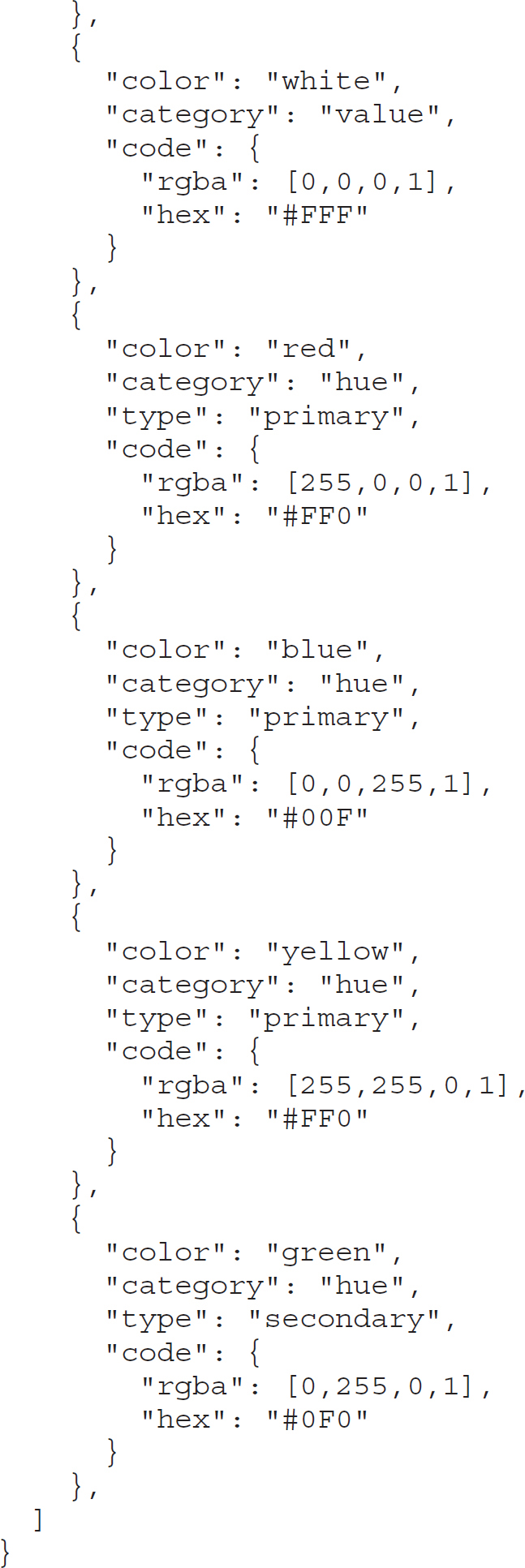
Another possibility when it comes to data representation is the eXtensible Markup Language (XML). This is another self-describing language. XML is the foundation for the Hypertext Markup Language (HTML), so rather than key-value pairs, you have tags with values inside the tags. An example from HTML is <h1>Headline</h1>. The tag is h1, meaning header 1. Anything between the tag open and the tag close, </h1>, would be rendered in header 1 style. You could use the same sort of idea for generating data. For example, rather than the key-value pairs of JSON, you could do something like <color><name>white</name></color>. Again, it’s self-describing if you name the variables in a way that makes sense to the structure of the data.
Because we are passing messages back and forth, there are sometimes messaging protocols that are needed. This may be something like the Message Queuing Telemetry Transport (MQTT) protocol, a lightweight protocol to transport messages from a client to a broker. This is a transfer protocol that would be used in place of HTTP. The difference between MQTT and HTTP is that HTTP is document-centric, meaning it is designed to transfer documents from the server to the client. A web page is a document, as are any images or script files. MQTT, though, is data-centric. MQTT uses a publish/subscribe model, which means a client may subscribe to a data feed. They would get this data feed from a broker when that broker publishes it. Only those who have subscribed to a data stream will get it.
The IoT is another place where we can make use of a cloud computing platform. Cloud providers like Microsoft Azure have offerings for IoT management. Figure 16-11 shows the list of service offerings in Azure that relate to the IoT. As an example, you can use the IoT Hub offering for your devices to connect to. The hub aggregates all the connections. A service like this, in the cloud, could scale based on need, meaning when you get to the point where you have exceeded capacity on one hub, you could create a new instance of an IoT hub, which would take new connections until the capacity for that one is exceeded. And lather, rinse, and repeat.
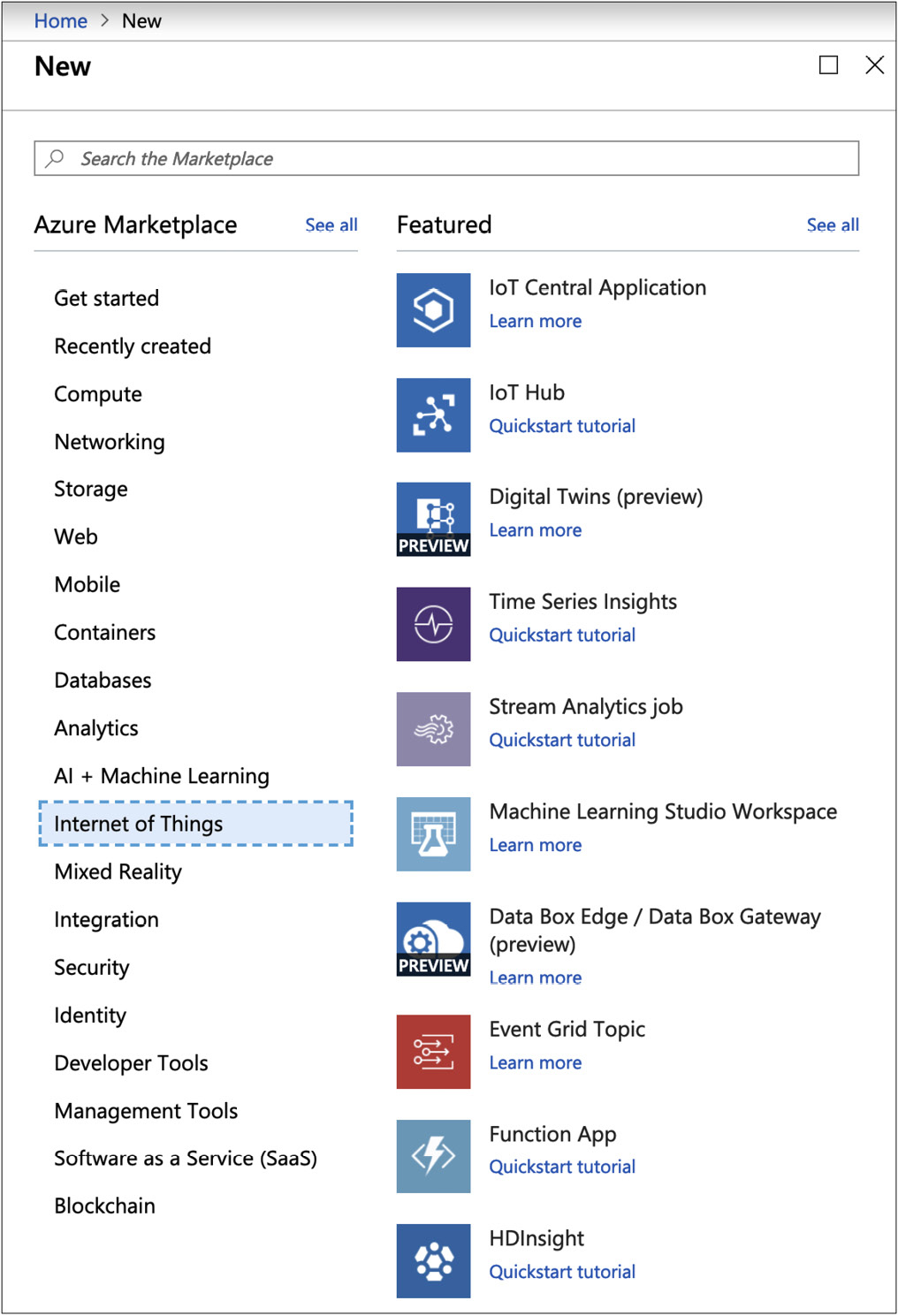
Figure 16-11 IoT offerings from Microsoft Azure
Beyond the hub would be the application. This is another case where Microsoft Azure has offerings. You can see the configuration settings in Figure 16-12 for an IoT application in the Azure portal. Most of what is there is just naming. However, there is also the template. The template determines what the application will look like. You can create a custom application if you want to start from scratch. However, you could also use a development kit for devices that are already known, such as Raspberry Pi or an MXChip.

Figure 16-12 IoT application settings
Of course, other cloud providers have similar offerings. Using predefined services instead of starting from scratch in your own environment makes developing the management platform faster. Another advantage to making use of cloud computing solutions for overall management of the IoT platform is the easy application of analytics engines to your application. These are also services that can be plugged into the IoT infrastructure with your cloud provider, including Microsoft Azure and Google Compute Engine.
Protocols
IoT devices such as those used in the home typically use commonly known protocols like Bluetooth, Wi-Fi, or even Zigbee or Z-Wave, which are wireless protocols for personal area networks. However, these are not the only protocols that are used to communicate with these devices. As an example, Building and Automation Control network (BACnet) is a protocol developed in the late 1980s to allow for systems like lighting control, access control, and heating, ventilating, and air-conditioning (HVAC). BACnet describes how these different systems could communicate with one another and, perhaps more importantly, how they could communicate with computer systems so these devices could be automated. These devices offer functions like read-property and write-property to collect data from them and also to provide management of them.
When it comes to protocols used in automobiles, the Controller Area Network (CANbus) enables multiple small microprocessors to communicate with one another without a centralized host computer managing everything. Similar to BACnet, CANbus is based on passing messages from one device to another in a peer-to-peer manner. This style of architecture is referred to as multi-master, meaning each of the different nodes in the network could function as a master device (as compared with a slave device). The nodes in this sort of network are Electronic Control Units (ECUs).
Another means of engaging with automotive devices is 802.11p, which is known as Wireless Access in Vehicular Environments (WAVE). 802.11p is used for dedicated short-range communications. This is a project from the U.S. Department of Transportation. It is expected to be part of an Intelligent Transportation System (ITS). This would allow for vehicles to communicate with road infrastructure.
Industrial Control Systems
Industrial control systems (ICSs) are also embedded devices and are sometimes targets of attackers. Utilities like power and water are ICSs, as are automated manufacturing systems. In conjunction with ICSs, you will also hear about Supervisory Control and Data Acquisition (SCADA). SCADA is an architecture that can be used for ICSs that encompasses the programmable logic control (PLC) devices in the machines that are running the assembly line or the power generation equipment, all the way up to the human machine interface (HMI). In the middle there may be tiers to make command and control easier by aggregating the communication. This overall design may be used across a large geographic region in systems like power grids or railway systems.
SCADA defines five levels. The field level where sensors and control devices are located is level 0. Level 1 has industrialized input/output modules, which would be the PLCs or remote terminal units (RTUs). Level 2 contains the supervisory computers, which provide the HMI and also collect data from the PLCs. Level 3 is where the production monitoring happens with production control. This would include targets for production so any monitoring knows what should be happening. At level 4 is scheduling. Any automated schedules would happen here.
PLCs may use a protocol like Modbus. Modbus is used to essentially get and set data. The data is stored in coils and registers. A coil is a single bit, suggesting it is either on or off. You might use this for a valve, for instance, if you want to be able to control whether it is open or closed. A coil is a read-write object. Discrete input is a single bit that is read-only. There are also registers, which are 16 bits. A read-write register is called an input register. A holding register, which may be needed to store sensor data, is read-only.
Modbus was originally developed to be used over serial connections. However, network-based communications are getting more common, so Modbus can be used over TCP or UDP, for instance. Programming PLCs is usually done with ladder diagrams (called ladder logic) to show control flows. However, interacting with PLCs using Modbus is reasonably easy. A programming language like Python has libraries available for Modbus. The library takes care of formatting the Modbus message and then transmitting it over whatever transport protocol is being used.
The security issue with ICS/SCADA systems is that they may be highly sensitive because they may be controlling networks of devices like energy grids and other critical infrastructure. The PLCs are not generally high-powered devices, which may expose them to attack. These PLCs often control important hardware devices that may be in a nuclear power plant or a dam, for instance. Traditionally, it’s been thought that they shouldn’t be accessible on any network. However, more and more, these devices are being connected to desktop networks so the operators can sit at a desk and have access to the HMI as well as their e-mail and other business functions. Not everyone controls their essential systems like this, but enough do that it’s become a security issue for power companies and others that use these types of embedded systems.
Chapter Review
The Internet of Things (IoT) has become a common term that describes a large number of devices and device types that are connected to the Internet. There are billions of these devices around the world. They may be used for home automation in such devices as thermostats, light bulbs, garage door openers, and light switches. They may be other devices like digital video recorders, which have a general-purpose operating system and an application that handles all the video elements. Perhaps more troubling is the networking and connectivity options that are being used in medical devices. This may be heart monitors or even pacemakers, for instance. Another category of IoT devices includes sensors, as in the case of a heart monitor or even a strain gauge used to detect movement of bridges. You may also be able to control these IoT devices outside of your network as in the case of a garage door opener or a light bulb.
The locations of IoT devices may be found using websites like Shodan or Thingful. Shodan has search keywords that can be used to identify devices based on ports, operating systems, or locations, as well as other parameters. Thingful doesn’t have the same set of keywords but instead allows you to discover IoT devices by looking around on a map. You can still go searching for device types, such as webcams or weather stations. You may also find other devices that have sensors in them, some of which you may not expect, like buoys in the ocean, which can provide water temperature and wave height data, for instance.
Industrial control systems are commonly used in companies that have automated manufacturing lines. They are also used in places like power generation stations. Supervisory Control and Data Acquisition (SCADA) systems are used to manage these industrial control systems. There are five levels defined for SCADA, starting at the physical controls that are being manipulated. Above that are programmable logic controllers (PLCs), which are small devices capable of accepting and storing data for the use of the physical controls they are connected to, such as valves. You could use a language like Modbus to interact with these PLCs to set or retrieve data.
Questions
1. Which of these would be considered part of the Internet of Things (IoT)?
A. Smartphone
B. iMac
C. Digital video recorder
D. Tablet computer
2. What protocol might you use to directly interface with programmable logic controllers?
A. Ladder language
B. Modbus
C. Java
D. C#
3. Which of these would be a valid search keyword in the Shodan website?
A. geo
B. street
C. service
D. protocol
4. What data representation format might be used to communicate with IoT devices?
A. HTML
B. JavaScript
C. HTTP
D. JSON
5. Which of these is a data-oriented transfer protocol that may be used to send messages to IoT devices?
A. MQTT
B. HTML
C. HTTP
D. TCP
6. Which of these would be a common challenge for communication between an IoT device on a home network and any controlling systems on the Internet?
A. Web proxy
B. Anti-virus
C. Low bandwidth
D. NAT
7. Which of these is malware that was used on IoT devices to attack high-profile targets?
A. WannaCry
B. Ransomware
C. Mirai
D. ILOVEYOU
8. What is one method you may use to program programmable logic controllers?
A. Ladder diagrams
B. Java
C. C
D. TCP
9. Which operating system are you most likely to find in IoT devices?
A. OS/2
B. Linux
C. Windows
D. VM/CMS
10. Which of these is not a protocol that may be commonly used to communicate with an IoT device when you are in close proximity to the device?
A. Zigbee
B. ICMP
C. Bluetooth
D. Z-Wave
Answers
1. C. The digital video recorder does not have a keyboard or a traditional screen in the sense that the screen is only used to display the interface for the recorder. A smartphone, iMac, and tablet computer all have a screen and a keyboard (physical or virtual), both of which are common user interface elements.
2. B. Modbus is a protocol used to communicate with programmable logic controllers (PLCs). While Java was initially developed for devices like set-top boxes, it likely wouldn’t be used to develop PLC-based programs. The same is true for C#, though it was not developed for use in set-top boxes. While ladder diagrams may be used, there isn’t a ladder language.
3. A. The keywords that may be used in Shodan include city, country, geo, hostname, and port. Street, service, and protocol are not keywords that could be used.
4. D. JavaScript Object Notation (JSON) is a data representation format. HTML is a data formatting language that is used to describe the format of a web page and is not used for data representation. JavaScript is a programming language. HTTP is the protocol used to transfer hypertext.
5. A. Message Queuing Telemetry Transport (MQTT) is a data-oriented transfer protocol that is used to transport messages from a client to a broker. HTML is a language used to define what a web page looks like. HTTP is used to transfer documents like HTML pages. TCP is a transport layer protocol.
6. D. Network address translation (NAT) would be a challenge because it prevents Internet-based controllers from reaching out directly to the IoT device. It would be uncommon for a home network to have a web proxy, and an IoT device would not likely go through the proxy. As they are devices in their own right, anti-virus wouldn’t be an issue. An IoT device likely wouldn’t consume much bandwidth, so low-bandwidth connections wouldn’t be a challenge.
7. C. Mirai is a botnet that made use of IoT devices as the foundation for network attacks. WannaCry was ransomware. Ransomware is not a specific malware but instead a category of malware. ILOVEYOU is a very old piece of malware that spread via e-mail.
8. A. Programmable logic controllers (PLCs) are very simple devices that would be programmed using ladder diagrams to describe a process flow. Java and C are high-level languages and wouldn’t be used to program PLCs. TCP is a transport protocol.
9. B. Linux is a common operating system used in IoT devices such as digital video recorders, smart thermometers, and other similar devices. OS/2 is an older operating system from IBM. VM/CMS is an operating system, also from IBM, used on mainframes. Windows may not commonly be used on IoT, though Microsoft does have a Windows 10 IoT Core operating system.
10. B. The Internet Control Message Protocol (ICMP) is used as a diagnostics and error-handling protocol in conjunction with IP. When you are local to an IoT device, you would use Bluetooth, Z-Wave, or Zigbee to communicate with the device.

