CHAPTER 12
Malware
In this chapter, you will learn:
• The different types of malware
• About malware analysis
• Anti-virus techniques
Malicious software, commonly called malware, has been around for decades now. Given the more harmful types of malware we see today, one might look back with a certain nostalgic fondness at the kinds of malware that were prevalent even a dozen years ago. But whether the behavior of this early malware was truly malicious is debatable. A piece of software whose only purpose is to spread from system to system may not be a welcome item, but it’s hard to say if it’s truly noxious in nature. Many were more of a nuisance than malevolent. However, regardless of the actual functionality of the software in question, there are specific ways we categorize malicious software, and within each of those categories are additional subcategories.
Malware has become a business. Today’s adversaries are funded and organized. This means they have employees who work for them and some of those employees develop malware that can help the attackers achieve their goals. This may include new types of malware that can either facilitate the generation of revenue or directly generate revenue. Also, in the case that an attacker is looking for intellectual property, malware can be useful to leave behind footholds to allow the attacker to keep coming back in and retrieving critical corporate data.
With the rise in the quantity of malware out there, a new profession has emerged. You can now get a job as a malware analyst. Where previously it was something you may have done if you worked for an anti-virus software vendor, today several companies hire malware analysts. There are techniques for analyzing malware, and as you may expect, performing that analysis safely is a primary consideration. Authors of this type of software don’t make the white hat’s job easy, of course, and they use a number of evasive approaches that must be understood not only by malware analysts but also by those who are responsible for detecting malware like viruses.
Anti-virus software has also been around for a while now, but there are a number of challenges to detecting malware that didn’t exist when the first anti-virus software debuted over 30 years ago. While processing speed has increased by several orders of magnitude, the challenge in detecting malicious software has certainly not diminished over time. Indeed, it has increased dramatically as software creators have become more serious about getting malware deployed and keeping it deployed, especially since there is often a financial reward of some sort for doing so.
Types of Malware
There are several types of malicious software, but these different types are not mutually exclusive. In some cases, a piece of malware may fall into multiple of these categories.
Virus
Over the years, the word virus has become a generic term for malware. But here we’ll be more specific to distinguish it from other types of malware. In actuality, a virus is a program that “infects” a computer by getting a user to run it. It may be attached to another piece of software in order to trick the user into running it. It may also be disguised to look like something else. One example that demonstrates this point is the “I Love You” virus from the late 1990s. The virus was a Visual Basic script that was sent to all the addresses in a mail system’s contact list. Because of the way the mail client was configured at that time, the Visual Basic script would automatically run when the mail was opened. Once run, it infected the system, perhaps by replacing all the user’s pictures with a copy of the script itself. Then, taking advantage of the fact that file extensions are typically hidden, it used .jpg.vbs as the extension—expecting that the .vbs wouldn’t be seen, just the .jpg part—thus making it look like it was really an image. Later, after the system was thought to be cleaned, the user would open one of these pictures to look at it and the system would become infected all over again. Figure 12-1 shows an e-mail message with the I Love You virus attached. Notice that it’s taking advantage of the fact that file extensions are typically hidden by using a .TXT extension in between the filename and the real .vbs extension.

Figure 12-1 An e-mail containing the I Love You virus
I Love You is an example of a piece of malware that is more than just a virus. There are components that make it a virus, but in some cases (such as re-infection) it requires the user to open it, even if the user believes they are opening a picture. There are also, however, components that make it a worm, such as the capability to send itself to addresses in a user’s contact list. The I Love You virus (or worm) does highlight some important aspects of malware, and viruses in particular. One aspect of viruses that is very important is the use of social engineering. Often, viruses like the I Love You virus use social engineering to spread to other systems. While the virus would execute automatically because of the scripting engine settings, it still required that the user open the message for the script to be executed. When a user receives an e-mail message from someone they know with the subject line I Love You, they are likely to open that message.
Since a virus often requires the help of a user, it must have a component of social engineering figured into its creation to get users to do what’s needed to execute it. The I Love You virus played on people’s innate desire to feel loved. Other viruses have masqueraded as games or useful utilities so as to get people to run them and thus infect their systems.
Where viruses once were merely a nuisance or they perhaps altered or deleted some files, modern viruses are typically more dangerous. They may be used to steal information from the user’s system or they may be used to conduct cyber espionage, along the lines of malware like Stuxnet or Flame, discovered in the wild in Middle Eastern countries like Iran.
Worm
You might say that, compared to a virus, a worm has legs. Instead of requiring user intervention, for example, a worm is capable of making its way to other systems and infecting them on its own. The concept of a computer worm, capable of self-replication, was posited by John von Neumann in the middle of the 20th century, and though it was strictly an academic exercise, it’s considered the beginning of computer infections. While he is often credited with describing the first computer virus, the fact that he called them self-replicating computer automata suggests that what he described was actually a worm. Von Neumann did not describe, and may not have even conceived of, a computer program whose purpose was to perform malicious acts like destroying data or stealing information. The malicious acts came later.
Not all worms are malicious. Some of the earliest of these types were created at the Xerox Palo Alto Research Center (PARC), which tested some of the principles of the Ethernet. Other benign worms include the Nachi worms, designed to inoculate systems against the very problems that the worm itself exploited to get into the system. The ethics of something like this are widely debated, of course, since the Nachi worms did perform acts that were unauthorized by the owner of the system, even if the acts performed were to get the system updated with the latest patches so they couldn’t be infected by other, more malicious worms.
One very famous worm, known as the Morris worm (after its creator, Robert T. Morris), may have originally been designed as a benign piece of software, but it went on to wreak havoc in 1988 by effectively shutting down the majority of the ARPANET. While a number of good things resulted from the release of that worm, including the creation of the first Computer Emergency Response Team (CERT), the worm itself and the response required to get it under control took a lot of time and resources, meaning it ultimately cost a lot of money to remove it from the network.
Worms continue to be a major problem, in part because of the devastation they can cause in a short amount of time, and also because of the systems they have targeted. An example is the SQL Slammer worm, which targeted the popular database software Microsoft SQL Server. Since a number of companies relied on MS SQL Server to operate critical business systems, a worm affecting that software was a very big deal.
Worms, unlike traditional viruses that require some sort of intervention on the part of a user to execute them, can spread very quickly and rapidly infect a large number of systems. They typically take advantage of vulnerabilities in system software to infect a host. If the software used as a vector into the host is very popular, the number of systems that can be impacted quickly is enormous. The Conficker worm, first discovered in 2008, infected systems vulnerable to a problem in the Windows network sharing services. After getting itself installed, the worm would then keep itself updated with the latest versions and would also download and install additional malware.
Complex malware like Conficker may also have mechanisms in place to protect itself from detection or removal. Conficker, as an example, blocked certain DNS lookups as well as disabled auto-update to ensure that holes were not patched. One technique that malware may employ is to ensure that the vulnerability used to infect the system gets patched, so as to ensure that no one else gets in and infects the system in the same way. This helps ensure that the software is the only piece of malware on the system, giving it control over the way the system behaves. It may also be about not wanting to share with others.
Trojan Horse
One malware type is named for the legendary wooden horse that was presented as a gift to the city of Troy: the Trojan horse. Hidden inside that horse, of course, were Greek soldiers, who in the middle of the night secretly climbed out of the horse and attacked the city from within. Since that time, things that are not what they seem, particularly if they have a malicious nature, are called Trojan horses. In this case, it’s software that appears to be one thing but that really turns out to be something else. Often, we simply call this a Trojan. A Trojan is frequently a virus, because a virus requires user interaction to propagate, so it’s not uncommon for virus writers to disguise their software as something else, such as a holiday game or a program that purports to do something cute. Of course, if the Trojan doesn’t perform the action claimed, it may not spread very far because users won’t think it worth passing on to friends and family. As a result, either a Trojan may be attached to an existing program, or the virus and the carrier may be written by the virus writer, with the carrier being a throwaway piece of software that exists simply to transport the virus from one system to another.
A Trojan is really a social engineering technique employed to encourage users to behave in a way that is helpful for the author of the malware, making sure the software actually gets run so the system gets infected. The goal of a Trojan might be to gain remote access to a system. NetBus, Sub 7, and Back Orifice were all considered Trojans, providing unauthorized access to a system without the system owner knowing about it. A Trojan might also be a way of getting a piece of software like a key logger onto a system to capture keystrokes, which might include useful pieces of information like names, addresses, credit card numbers, usernames, passwords, and so on. ZeuS was considered a Trojan horse that installed a key logger as well as a form grabber.
In addition to being a Trojan horse, and demonstrating the idea of the complexity of malware and the difficulty of categorizing it, ZeuS actually included a botnet client. On top of that, ZeuS is one of the first toolkits that allowed the creation of custom software. Figure 12-2 displays the creator application, as well as the configuration file, showing the different configuration settings available. Once you have the configuration you want and have selected the language you want to use, you create the executable to be used. ZeuS isn’t the only malware that has a creator toolkit. The Blackhole Exploit Toolkit is another example of a toolkit that allows the user to quickly and easily create malware for their own purposes.
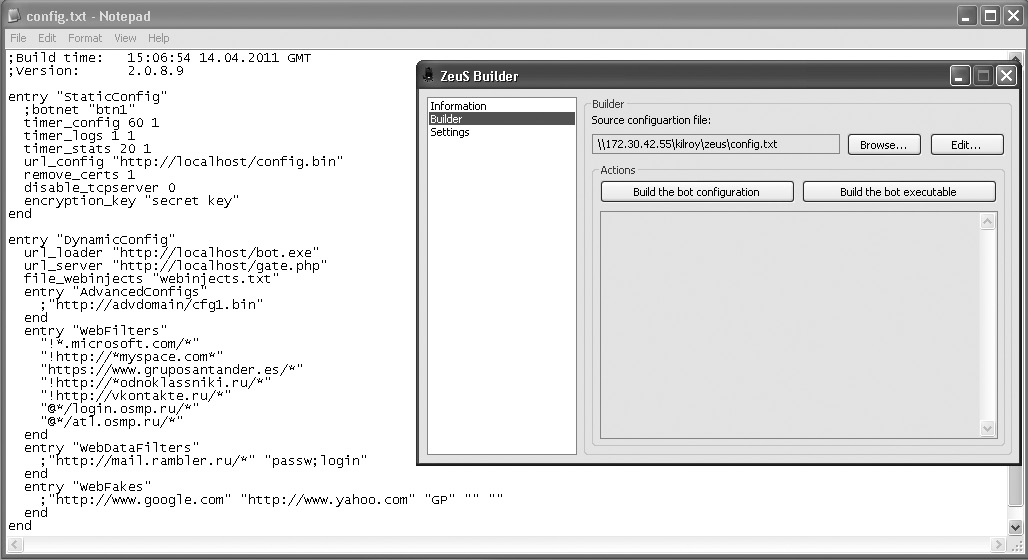
Figure 12-2 The ZeuS creator and config file
Ransomware
Malware that falls under this category also falls under at least one other category. At a minimum, ransomware is also either a virus or a worm. The purpose of ransomware is to extract money directly from users. A common approach with ransomware is to encrypt personal or sensitive data on the user’s computer and demand the user pay a ransom before the attacker will provide a key that will decrypt the data. This is not the only avenue ransomware can take but it is the most common. Demanding money directly in return for decryption is a much more expeditious way to get it than compromising systems and then having to get money indirectly from the systems themselves or from selling the data taken from the systems. Personal or sensitive data is the sort of thing people are likely to pay money to get back, and quickly.
Interestingly, the idea of encryption-based ransomware was floated in 1996 in a research paper for the Institute of Electrical and Electronics Engineers (IEEE), titled “Cryptovirology: Extortion-Based Security Threats and Countermeasures” (written by Adam Young and Moti Yung). This idea, far less viable at the time because of limitations in computing power and less capable propagation methods, has become a common method of attack by organized crime groups. Over the last few years, a handful of types of ransomware have become highly problematic for businesses and individuals alike. Some of these malware strains have even been enough of a problem that they made the mainstream news. One of these is WannaCry. You can see what it looked like to be infected with WannaCry in Figure 12-3.
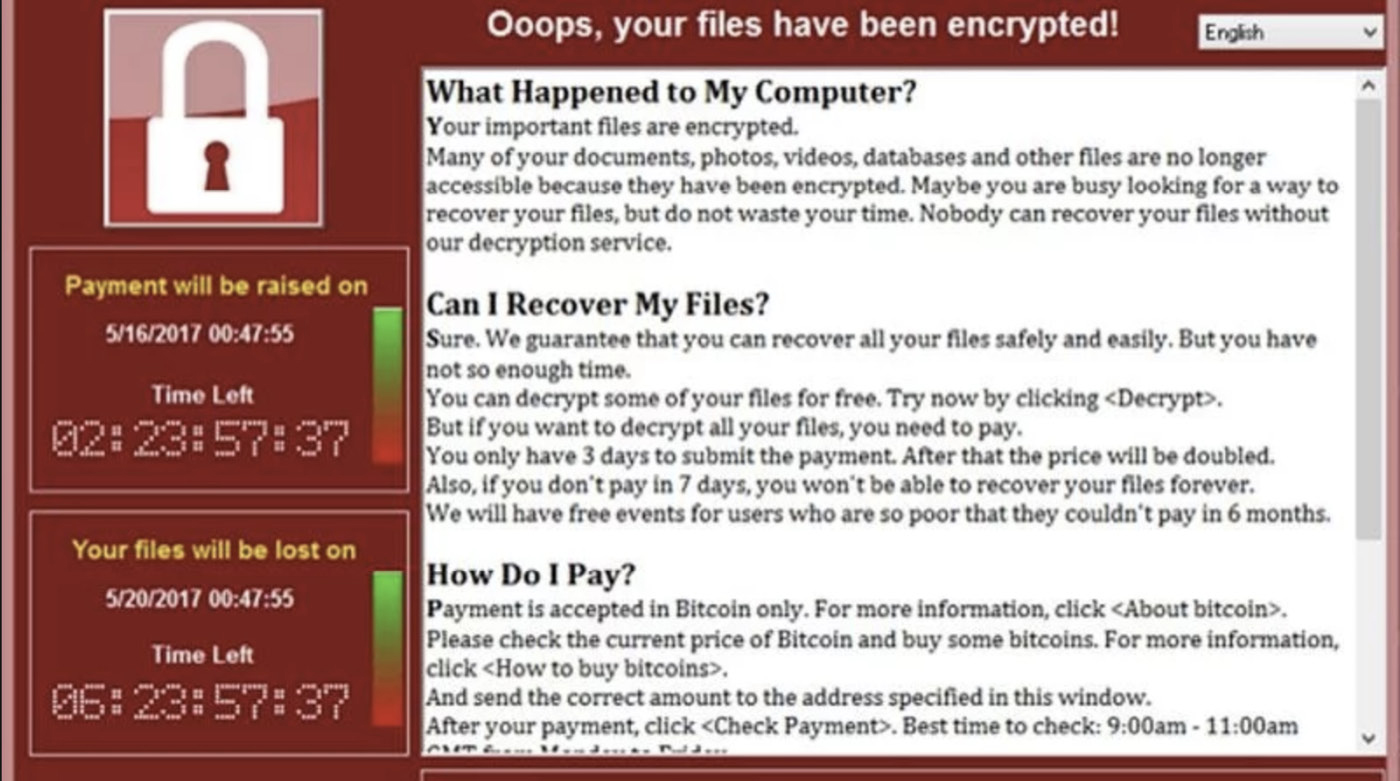
Figure 12-3 System infected with WannaCry
WannaCry is a worm that propagated using the exploit known as EternalBlue, which was developed by the U.S. National Security Agency (NSA) and exposed to the outside world by the Shadow Brokers the year before WannaCry launched in May 2017. Once the system was infected with WannaCry, its files would be encrypted by the malware. The malware would then display the dialog box shown in Figure 12-3, indicating to the user that files had been encrypted. Without backups in place, the only way to retrieve files would be to pay the ransom to the attacker, typically through a cryptocurrency like Bitcoin.
Petya is another family of ransomware that encrypts data on the user’s system, demanding payment in return for a key from the attacker that decrypts the user’s data. Initially, Petya used e-mail attachments as a way of propagating the virus. Subsequently, a version of Petya was released that used EternalBlue, like WannaCry. While the first deployment of Petya happened in 2016, the revised release, referred to as NotPetya, was released in June, 2017, subsequent to the WannaCry release. The majority of attacks of NotPetya were targeted at Russia and Ukraine.
While these ransomware attacks are probably the most notorious, they certainly are not the only ones and weren’t the first. One of the first was called CryptoLocker. CryptoLocker used a 2048-bit RSA key to encrypt data on users’ systems. CryptoLocker used a virus to propagate from one system to another. It also made use of an existing ZeuS botnet. CryptoLocker was launched in 2013 but was isolated in 2014 as part of a takedown operation on the ZeuS botnet.
Rootkit
A rootkit is designed to hide the existence of something from a user. This may be a piece of malware like a virus or worm, but a rootkit can also hide the fact that someone has broken into your system and is making use of it. It is a good way of making sure that the malware the rootkit goes along with isn’t found through the usual system utilities, because the rootkit commonly replaces those utilities with ones that work similarly but provide results that are filtered so as not to show any traces of the malware. A rootkit may prevent the user from displaying files or running programs. This would prevent the user from seeing any files, including the executable the malware is using. While rootkits traditionally targeted Unix-based systems where the system utilities were small programs that could be easily duplicated and replaced, there are rootkits that target other systems as well, like Windows.
Since the rootkit replaces system programs, it should be easy to detect the existence of the rootkit by simply checking whether those files have been replaced. This is the technique employed by host-based intrusion detection systems to protect against this very behavior. However, the rootkit may not only be able to get itself installed but also have ways to get around detection techniques, particularly if those detection techniques are using the operating system, which has already been compromised by the malware and rootkit. Basically, just about anything that uses the operating system should be suspect, and the best way to detect malware and rootkits is by scanning a system that has been booted up using a live CD, where the operating system and its components aren’t reliant on anything on the hard disk. Figure 12-4 shows the results of a program called rkhunter running on a Linux system. rkhunter is designed to look for evidence that a system has been compromised.

Figure 12-4 The results from rkhunter, a rootkit hunter program, on a Linux system
To give you a sense of the popularity of this malware technique, the rkhunter program will currently check for the existence of 498 possible rootkits. This is just on a Linux system. There are a number of rootkits available for Windows as well, with the first appearing in 1999. The first rootkit targeting Mac OS systems appeared in 2009, and the Stuxnet virus that targeted embedded systems included a rootkit component. Including rootkits with malware is a very popular technique to help ensure the malware stays in place and goes undetected.
Botnet Client
A botnet client installed on a computer provides access to a remote administrator of the botnet. The botnet client still needs a way in, so it’s usually just the payload of another piece of malware, whether it’s a virus or a worm. As discussed earlier, ZeuS is an example of a piece of malware that includes a botnet component. Botnets take advantage of the idea of distributed computing, making use of the resources of all of the systems that belong to the botnet. This could mean thousands or even millions of systems end up participating in the botnet. The botnet may be used for a number of purposes, including simply grabbing information off the systems on which they are running or sending out spam messages. They may also be used to participate in attacks on other systems. The widely publicized attacks against a number of U.S. banks in 2012 and 2013 were done by making use of botnets.
Because of the large number of systems involved in a botnet, the botnet’s administrator needs a way of controlling them or better segmenting them into groups where they can be managed more easily. This is usually done using a multitier approach with other systems—something called command and control (C&C) servers. As one example, the website ZeuS Tracker, as of this writing, was tracking 452 C&C servers in the ZeuS botnet, with 100 of them being online at the time. ZeuS remains a resilient piece of malware with multiple, related strains. Even being over a decade old, it still has a good-sized presence.
While there is nothing in the idea of a botnet that is inherently malicious, the word botnet definitely has a negative connotation. In the 1990s, the site distributed.net was using what were effectively botnet clients to engage in complex problems, solved through massive parallel processing over a distributed network of clients. Botnets today use the same notion, but instead perform acts that are far less beneficial. There are, however, botnets that have been used for good purposes, and many botnets have been taken down from the inside.
There are a number of ways botnets listen for commands from the C&C servers. They may employ Internet Relay Chat (IRC) channels to listen in on the server. This was a very early way of controlling botnets, since the infrastructure was already in place and nothing new had to be created in the way of a client–server architecture and implementation. Other ways are for systems to check with web servers using HTTP, since HTTP is a common protocol and wouldn’t normally be noticed in web traffic. The distinguishing feature of botnets, though, concerns the servers they try to connect with. Sometimes, they use hostnames that may look unusual. They also connect to systems that are clearly end-user systems because of the IP address and the block it’s in. Often, the address block belongs to a cable modem or DSL provider or in a dial-up block of IP addresses. You can tell by who owns the IP address in question. Plus, sometimes the reverse lookup on the IP address will provide a hostname, clearly indicating what type of network it belongs to. You may also find that the IP address doesn’t resolve to any hostname, which is typically a concern as well.
Spyware/Adware
Another class of malware is spyware, which is often lumped in with another type of malware called adware. Spyware is intended to monitor the behavior of the users on the system where it lives, and doesn’t generally have any replication mechanism like a virus or worm. The spyware is typically installed along with something else that the user might see as advantageous, like a toolbar for a browser. Installing a Browser Helper Object (BHO) in Internet Explorer can give the spyware a lot of access to its web traffic. The spyware may also be a drive-by installation, where the software is installed automatically because of a vulnerability in the web browser, something which the user may not even be aware of. Spyware can cause performance problems, as well as unusual behaviors on the user’s system. If a system has become too slow, it could be a result of having spyware on that system. In addition to monitoring web activity, spyware may have other capabilities like keystroke logging.
The increase in the amount of spyware available, as well as the number of systems that have been infected with spyware, has caused an increase in the software programs available to remove spyware from systems. To quote Bigweld (Mel Brooks) from the movie Robots, “See a need, fill a need.” The need for software to remove all of the spyware out there has created a nice industry selling the software to remove it. Removing spyware typically requires not only deleting files but also removing entries from the registry. Sometimes, getting all of the spyware removed from your system can be a tricky endeavor.
One of the outcomes from a spyware infiltration might be a number of popup ads, centered on your online interests. This type of intrusion into your online life is sometimes called adware, although adware is also software that is paid for through the use of ads displayed in the user interface of the program. While one is a good way to get decent software for free while still paying the developer for his time, the former is a way of irritating users, and possibly worse. In the case of the adware that generates popups as a result of your browsing behaviors, this is another form of spyware, which also happens to generate ads, making it adware as well. The same software that removes spyware will also commonly remove the bad or malicious kind of adware as well.
Droppers
A dropper is a type of malware that has the purpose of grabbing additional malware. You can think of a dropper as the foot in the door. A single-stage dropper may include the malware as part of the dropper file. The malware is not part of the executable portion of the dropper, because the purpose of the dropper is to drop the malware onto the target system. Not all droppers are single-stage, though. In some cases, the purpose of the dropper is to download additional malware to the system. This may allow the dropper to bypass anti-virus because it contains no malicious executable code. The only thing the dropper does is download additional files, which themselves would be malicious. Agobot is an early example of a dropper, released in 2002. More recently, OnionDuke is a dropper released in 2014 that infected systems trying to download software through an infected Tor proxy. The infected Tor proxy would add a malicious stub to the file being downloaded.
Anti-Virus
Anti-virus is a type of program designed to detect and remove viruses and other types of malware from the system. Not surprisingly, this can be challenging, given the speed at which viruses and other malware are being created. There are different ways for anti-virus systems to work. One of the most common is through the use of a signature. When a new piece of malware has been detected, the anti-virus vendor writes a signature for it. The signature is a set of bytes that appears to be unique to the virus and can be fed through a pattern-matching algorithm to compare files to. If a file has that particular set of bytes, or signature, it will be flagged as being a piece of malware. Once the malware has been identified, the anti-virus system has the option to completely remove the virus, if it can, leave it alone, or quarantine it. Quarantining the virus means moving it to another location in the filesystem. If a persistence mechanism like a Run registry key were to try to run it where it’s expected to be, it would no longer be there and the persistence attempt would fail.
While signature analysis is a common technique used in anti-virus software, it can cause problems with performance because files need to be compared against the anti-virus database before use. Although there are ways to speed this process up, it’s still a lot of processing, and it can slow down your applications. Signature detection is also useless against new viruses that have yet to be assigned a signature and is unreliable against polymorphic viruses that may have many different “looks” to them and thus may not provide a good match against the signature database.
Another way of detecting viruses is by using a heuristic approach. This can be considered anomaly detection because the anti-virus system is looking for any activities that are unusual for a particular executable or that are common to a piece of malware. Heuristic detection does have the advantage of being able to detect polymorphic viruses because it’s looking for behaviors and not checking the way a particular virus looks.
While you may be most familiar with anti-virus running on desktops, it can also run on servers and also in the network. Since a common entry point for viruses is through web servers hosting up bad software, you may use a web proxy that has anti-virus software built into it to make sure that no viruses enter your network. This will provide another way of protecting desktops. Since Windows is the predominant desktop around the world, most malware development targets Windows systems. That doesn’t mean that anti-virus systems are only available for Windows. ClamAV, for instance, is open-source software that can scan Unix-based systems like Linux or even macOS. The version available for macOS is called ClamXAV, but it’s still ClamAV underneath the graphical interface. The Linux version is shown in Figure 12-5. Interestingly, all the files in the directory being scanned are viruses, though several of them are reasonably recent. This does highlight a problem with anti-virus not being 100 percent accurate.

Figure 12-5 The ClamAV anti-virus running on Linux
Anti-virus systems need to be constantly updated since signatures are constantly changing with new malware. This is often a configuration setting where the anti-virus program will update at some specified point during the day or night. Your anti-virus program can also be configured to check every file as it’s accessed on the filesystem, or it can be configured to run on a schedule where every file is checked once a day. While performing scheduled scanning can improve your system performance, it also leaves a large open window for malware to get in and cause a lot of damage before the scanner catches it on the daily run.
Anti-Virus Evasion
Malware has two goals. The first is whatever the malware was written to accomplish, whether it’s to be a nuisance, to be destructive, to steal or encrypt information, to infect other systems, or to achieve some other purpose. There is generally a secondary goal, too, which is to evade detection so that the malware can infect a system for as long as possible. The big threat to that secondary goal, of course, is an anti-virus program. As a result, there are a number of techniques used to evade detection by anti-virus.
Packing
Packing is really just a way of compressing a program. There are two reasons for compressing a malware-infected program. The first is that it makes the program smaller, which causes download times to be much faster, thus helping to infect a system faster. If you are trying to install a piece of malware on a system through an infected web page, you don’t want the page load to take a long time because the user may very well cancel it. Same with e-mail attachments. While today broadband access is common, malware has been around since the days of dialup access when it would take a very long time to download e-mail attachments or large web pages. While packing had the benefit of making transmission faster, that is less of a concern today but packing is still helpful to potentially evade detection. Packing makes the executable smaller, which means faster download times to the end system where you want the executable to reside. This also ensures system performance isn’t impacted by an anti-virus program taking a long time to scan a larger executable. Any time system performance is impacted and the system slows down, users will often notice and perhaps become suspicious. This may result in them taking a look at another anti-virus program or finding another way to root out the malware that has infected their system.
Beyond getting a smaller file size at the end, another big reason for using a packer is that it changes the look of the executable, which can make anti-virus programs miss the virus as it passes through. Any small change in an executable will mean a new cryptographic hash that is generated from the file. Remember that anti-virus commonly uses a signature to detect the virus. When you change the way a piece of malware looks, the signature is no longer valid. This can be done through changing the packing method, as long as the anti-virus program doesn’t know how to unpack the executable. There are a number of different ways to pack a program. One popular packing program is the UPX packer, shown in Figure 12-6. The UPX packer is an efficient packer that has a handful of options depending on how tight you want the executable to be when you’re done.

Figure 12-6 UPX packer
A packed executable is really just a compressed file when all is said and done, with a bit of a twist. Since the file is compressed, it needs to be uncompressed before it can be executed, so the very first thing that needs to happen when the program is run is to uncompress the executable. What the program really looks like, then, from an executable code perspective, is an uncompresser with a largish chunk of data in the middle of it. The uncompresser gets called first, and it decompresses the executable, after which the main program is called. An anti-virus program would need to be able to understand how to uncompress the executable before it could determine whether it’s a piece of malware or not. Simply finding a packed program doesn’t mean anything since there are other, valid reasons for compressing executables.
Encryption
Not surprisingly, encryption is another way to evade anti-virus detection. Again, all you need to do is find a way to make the anti-virus program miss matching on a known signature, which is really just a string of bytes. If the anti-virus program doesn’t see that particular string of bytes, it won’t detect the malware. The easiest way to evade an anti-virus program is to make sure the strings it’s looking for aren’t there. Another way to do that is to encrypt the executable. This is similar to compression in that the first thing that needs to happen is for the real executable to be decrypted so the program really looks like a decryption program, since that’s what the unencrypted code actually looks like. The real code is sitting as data inside, waiting to be decrypted.
Surely, though, all you would need to do would be to determine what the decryption key is and then reverse the decryption in the anti-virus program and you’d be back to being able to see the real program where you could detect the string of bytes and flag it as malware. The way to avoid this is to have variable keys that change from one implementation to another. None of this is an easy or straightforward process. Obviously, the anti-virus program needs to know what the decryption key is before it can decrypt the program, but if there is no constant key from one implementation of the malware to another, as long as the program itself knows the key, the anti-virus program will have a hard time decrypting the file so as to check it.
Code Modifications
Self-modifying code has been around for a long time, so it’s not surprising that malware authors would make use of this technique to evade anti-virus detection. The first strategy of this type is called polymorphic code, and polymorphic code in malware makes use of encryption and decryption as if simply using an encryption approach. The difference is that, with every infection, the encryption process varies. This change means that the program will look different with every infection. While polymorphic code alters the encryption and decryption routines for each infection, some programs will completely rewrite the entire executable on each infection. This is called metamorphic code and can lead to very large and complex programs since it has to be capable of writing a completely different executable each time. One example of metamorphic code is the W32/Simile virus. The vast majority of the code in that virus was dedicated to rewriting the program. The virus itself displayed messages on pre-determined dates and times.
Domain Generation
Anti-malware programs are not the only way to determine that malware is in the environment. In other words, the system doesn’t have to identify the binary solely based on a file hash. Instead, often malware uses known hosts to communicate with command and control systems. These command and control systems are known. Initially, binaries may have had some hostnames hard-coded into the binary and connected to them. These known hostnames and IP addresses could be used to identify when malware is operating. These known hostnames could be detected by network-based intrusion detection systems. Malware could have strings pulled from the executable as part of malware analysis and those strings could be used to block messages using a firewall. Thus, malware needed a way of changing up its means for connecting to systems in a C&C network.
Malware today often employs a domain generation algorithm. This algorithm can be implemented in the malware executable rather than including hostnames in the binary. Instead of IP addresses used for connection, the algorithm will use the generated domain names and use hostnames from those generated domain names for the malware to connect to. This makes detection of network communication harder if the detection is based just on the hostname of the contact point.
This technique was initially used by Conficker. The first algorithm would generate 250 domain names per day. Later on, the malware could generate 25,000 domain names per day. Out of that number, 500 would be contacted by the malware. While Conficker may have started this tactic, other malware authors have picked it up. There are now several malware families that use domain generation algorithms to help evade detection.
Infection Vectors
Not surprisingly, there are a number of ways for malware to get into your system, some of which we touched on earlier in this chapter. And just as there are numerous ways they are introduced to your system, they use numerous methods to stay there and create paths used for infection.
“Sneaker Net”
The term “sneaker net” goes back to the days of shuffling files from one system to another using a removable disk like a 5.25" or 3.5" floppy disk. Rather than using a network where everything is transmitted using an electrical signal, sneaker net relied on copying the files to a disk and then walking the disk to another system and copying the files off the disk onto the new system. Most businesses in the 1980s didn’t have networks, after all. Viruses have long traveled via sneaker net. Back in the 1980s, viruses might remain stored in memory and then copy themselves onto any floppy that was put into the system. This idea continues to this day, particularly with the popularity of USB sticks with flash memory on them. In fact, it’s even worse today since Windows systems in particular have something called autorun. If you have autorun enabled—and it is enabled by default—there is a small file called autorun.inf on a removable disk, typically a CD or DVD, indicating what should be executed automatically when the disk is inserted. A malware author could put the autorun.inf file on a USB stick and have it point to a piece of malware on the stick so it would automatically execute when the stick is inserted into a system.
It is not uncommon for malware to be distributed in this way. In 2017, IBM was shipping USB sticks that contained malware. Studies have indicated that a large number of lost USB sticks contain malware. Some stories, perhaps apocryphal, have indicated that even after users are educated they continue to pick up USB sticks and insert them into their computers. While this is anecdotal, it does clearly describe the problem, which is that even in the face of training, our curious nature or even our nature of accumulating things takes over and all security awareness training goes out the window. Malware transmission through USB sticks continues to be just as much of a problem as transmission through floppies was in the 1980s and early 1990s.
When it comes to e-mail, we again run into a user-awareness issue, and again it’s inadequate. Users are regularly told that they shouldn’t open e-mail attachments from anyone they don’t know. The problem is that the attachments that contain malware are just as often from people they do know. We talked about a couple of classics in the I Love You and Anna Kournikova viruses, where the messages would have absolutely originated from people the recipients knew because they came out of an address book. In some cases, malware sent by e-mail can get automatically executed, as was the case of scripts taking advantage of the fact that the scripting engine was on in Microsoft’s mail clients years ago. In other cases, the user actually opens the attachment either because they are fooled or because they just aren’t paying attention.
In fact, this type of social engineering attack has become commonplace. It’s known that the recent APT1 threat (perpetrated by hackers in China) regularly used e-mail attacks to gain entry into corporate networks. This particular vector is so well known that there is a tool that will generate e-mail messages with infected attachments to test social engineering attacks as part of a penetration test. There is currently a toolkit available for social engineering attacks that makes use of the Metasploit framework to generate infected attachments. You can see the menu-driven interface of the Social Engineer’s Toolkit (SET) in Figure 12-7. SET will walk you through the type of social engineering attack you want to create, the type of attachment needed, and who you want to send it to. It will then send the message for you. It makes the process of performing these types of e-mail attacks much easier.

Figure 12-7 The Social Engineer’s Toolkit interface
Phishing has long been a common attack vector, and often the messages appear to be very legitimate. Just this week, in fact, several messages appearing to come legitimately from a trusted entity showed up in my junk mail box. Determining that they aren’t real can require actually looking at the message headers and tracking the source of the message to a mail server that doesn’t belong to the company that appears to be sending the message. Even that isn’t always enough since some companies employ outside sources for communications, though that’s commonly for marketing and these phishing messages often indicate that you have an issue requiring your immediate attention. Another similar attack, shown in Figure 12-8, is an attachment that appears to be sent from a network scanner. In fact, it’s a virus, and not a scanned document at all. This makes the assumption that the recipient may be using one of these network scanners and has opened the attachment thinking they had a scan job that was being sent to them.
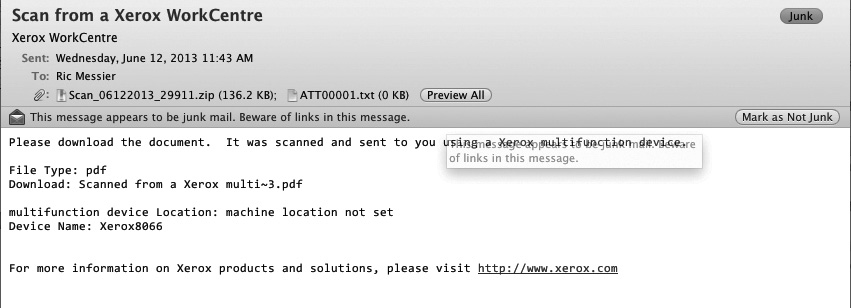
Figure 12-8 A virus attack through e-mail
Network
A network attack often makes use of vulnerable network services to gain entry to a system and install malware. The vulnerability MS08-067, described earlier as the vector used by the Conficker worm, is a good way of gaining entry to a system. If the system is vulnerable to it, the exploit is fast, efficient, and generally highly reliable. Where other vulnerabilities can be harder to exploit, this particular vulnerability could be very reliable. Exploits, though, are not the only way systems can be impacted by a network attack. Any system with a shared drive where the permissions are too loose can be affected by a network attack.
Windows used to have an administrative share for all the hard drives on its NT-based systems. This made it easy to do remote administration on the systems, but it also opened the door to a lot of abuse. If you have remote access to an entire drive, you can easily replace common system executables with malware to ensure the system gets infected. In the days before that was resolved and systems also had firewalls built into them, people would regularly use dialup networking or connect to their Internet service provider without anything in front of their system to protect it. This was a good way to get their system infected with lots of worms and viruses. Unix-based systems were not immune from this sort of open vulnerability either, though viruses and worms were less common on their platforms. A number of vulnerabilities have existed for decades in system software used on those systems. Additionally, some of the remote tools were just as open to access (rsh, rexec, and so on) as the C$ share was on Windows systems.
Copying files to a remote system, though, isn’t enough to infect it. Infection still requires that the executable be run on the system. This, though, can be done in a number of ways. In the case of Windows, you could copy a malware binary onto a Windows system in a particular folder and have it automatically run when the user logged in. This is one way to ensure that it gets infected. Copying over a Windows executable like Notepad or something similar that gets used on a regular basis is another way to ensure a system gets infected. No matter how you get the malware onto the system and get it infected, network attacks can be very effective.
Drive-by Attacks
A drive-by attack is where you entice a user to, say, visit a website that carries a piece of malware that is then downloaded and installed onto the user’s system by using an infected Java applet or some other carrier. While this may occur in such a way that the user is unaware that the download has happened, whether by using an ActiveX control or a Java applet or by exploiting a vulnerability in the web browser, it may also happen through the user’s direct action, such as when the website presents a dialog box to the user and the user clicks a button in it. This may be done using scareware tactics, like an indication that your computer is infected and you should click a particular button to get your computer scanned for free. This has been a common technique for getting malware onto systems. There are a number of scareware tactics using some form of popup to get users to install a piece of malware under the guise of cleaning up or disinfecting the user’s system.
Much like the e-mail attacks used to get malware installed, something which may be considered a type of drive-by attack if the user isn’t aware of what’s happening, the web-based drive-by can be done using the Social Engineer’s Toolkit (SET). Again, it’s entirely automated, and one of the things that can be done with SET is to copy an existing website and then have SET handle hosting it on your local system. SET will copy the existing website, making it look entirely legitimate because it’s an element-for-element copy of a real website. In addition to the complete content that’s already in place, SET will inject infected content into the site. Once you have SET up and running with the infected site content, you can craft a URL and send it out to people to come visit. Figure 12-9 shows the SET menu system offering a way to create a website that can be used to attack a system.
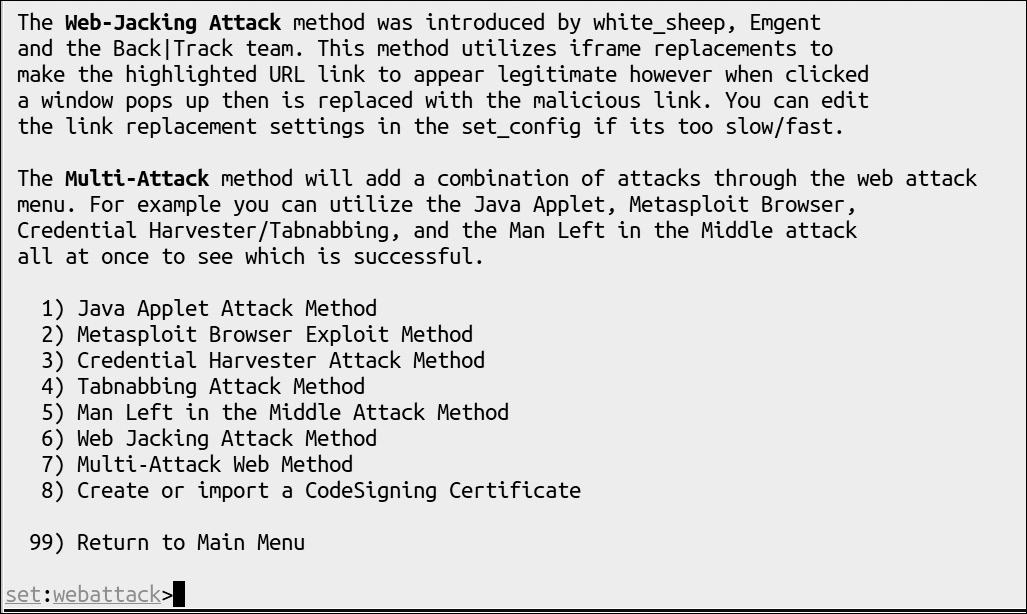
Figure 12-9 Ways to formulate an attack using the Social Engineer’s Toolkit
Similar to a drive-by attack, a watering hole attack uses a website to infect systems. The watering hole attack uses a targeted approach to select the website where the malware will be placed. The watering hole is the place where all the animals congregate to drink and for this reason, the attack has the same name. In technical terms, a website where people visit regularly and linger would be the watering hole. Consider a commonly visited site like that belonging to ESPN, for instance. If this site could be infected with malware, many users could be infected very quickly.
Boot Sector/MBR
While this isn’t an infection vector, per se, it’s worth talking about boot sector viruses in this context. As the name indicates, a boot sector virus is installed in the boot sector, which is a 512-byte piece of the hard drive called the master boot record (MBR). This is where control transfers after the BIOS has completed performing the Power-On Self-Test (POST). The boot code is responsible for getting the actual operating system to load, but the boot code is even smaller than the 512 bytes available in the boot sector because the boot sector also contains the partition table, as well as other small pieces of information. With a boot sector virus, the virus would be responsible for loading up the operating system, but it would also ensure that the system remained infected.
In one example of a boot sector virus called TDSS, the virus not only lives in the boot sector but also creates a very small, hidden partition. This partition can be used to store a copy of the virus to ensure it is capable of re-infecting the system if, for some reason, the virus is removed from the OS. In the case of TDSS, also called Alureon and sometimes TDL-4, it is not only a boot sector virus but also a rootkit and a botnet. Alureon is used to steal credit card information from network traffic.
Virus Infections
Once it’s on the system, a virus may need to infect a file in order to get itself installed and running on a regular basis. One way of accomplishing this is to attach itself to a program on the system. A trusted program, one that may be run constantly, is the best one to use. There are a few different ways for the virus to actually infect an existing program, though they all require doing a rewrite of the program as it exists on disk. The first way is to simply prepend the virus. This would write the virus code ahead of the existing code so the virus code runs first before the real program starts up. This might be done by simply changing the entry value in the program header to point to the virus code, which would jump back to the main program when it was done executing. Another way is to append the virus, allowing the program to start up first, after which the virus code gets executed. The virus may also simply overwrite an existing executable. This would remove the original program altogether, and seems like it would raise some eyebrows and quick detection.
Programs are chunked into different sections. A virus may choose to hide itself in between these different sections. This type of virus is called a cavity infector because it stuffs itself into cavities or gaps in the program file. This can be a complex technique for virus authors to use. An easier way is to just replace a known file with the virus that then calls the legitimate program. This makes it harder for the user to recognize that the virus has been executed.
A virus may be memory resident, which would require it to hook into operating system calls, allowing the virus to infect files as they are accessed and brought into memory. This would only infect programs that were run while the virus was in memory, though. Viruses may also scan disks, looking for programs to infect and thus not remain memory resident at all.
Persistence
Malware often is designed to look for ways to maintain its presence on a system. This requires not only ensuring that the malware continues to exist on the system, as in keeping files around that support the malware, but also ensuring the malware will run after the system has rebooted. This ensures the system remains infected. In the case of malware like a botnet, this is essential, since a botnet client needs to be running all the time or else it won’t get the commands sent by the controllers, which in turn means essential tasks of the botnet won’t get completed. There are many approaches to persistence, so this section focuses on some of the more common ones.
Persistence is operating system specific, since there are differences between how Windows, Linux, and macOS handle processes running at boot. One common approach is through the use of services, though each operating system handles services differently. Windows services are programs the system knows about that can be started at boot or as needed. The malware would need to be installed as a service, which would require administrative access. This would be a way for malware to be running after any boot and be less likely to be seen by a normal user. The executable would be hidden somewhere and there would be no visible evidence of any program running. Linux also has the ability to run services. These are programs that are either registered with the controller, as in the case of systemd-based systems, or programs started by a script, as in the case of init-based systems. macOS uses launch daemons and launch agents, but the essentials of a service remain the same.
On Windows systems, the registry can be used to launch programs either at boot or when a user logs in. There are registry keys that can be added either in the user’s registry hive or in the system’s registry hive. This determines whether the program launches when the user logs in, if the key is in the user’s hive, or when the system boots, if the key is in the system’s hive. On Linux or macOS systems, programs can be called from initialization scripts in the user’s home directory. This would serve a similar function as the user’s registry key. Also on Windows systems, though far more noticeable, would be to place either an executable or a link to an executable in the Startup folder for a user. However, if the user looks in the Startup folder, such as via Start | All Programs, the executable or link will be easy to spot, making this approach less likely to succeed at maintaining persistence.
Malware Analysis
Considering the amount of malware out there, it’s not surprising that there are many security professionals spending a good amount of time on malware analysis. You might expect that this sort of activity takes place only at companies that make anti-virus software, but those are not the only places where malware analysis happens. Companies like Apple and Microsoft, responsible for creating operating systems and related software, need to understand how malware works in order to try to combat it effectively. Additionally, managed security providers need to be able to understand how best to advise their customers on how to protect themselves and how to proceed in the case of infection. There are two ways to go about malware analysis. The first, and easiest, is static analysis. This is done by looking at the executable without running it. The second and more dangerous method, as well as the most complex, is dynamic analysis.
Static Analysis
In static malware analysis, you are taking a look at the executable to determine what it may be doing. This is a very safe approach because it doesn’t require running the malware, which could cause damage to the system. With static analysis, you are simply taking a look at the executable itself on disk. There’s no good reason to do all the work yourself, of course. Most malware you are going to run into will have already been discovered and you can learn a lot about it without actually running anything. A quick way to check is to simply run the file against any anti-virus program. You may need to run multiple anti-virus programs against the file, depending on how obscure the virus you have is. If someone has already done the work on the malware you have, you may not need to do it yourself unless you’re just looking to gain experience doing malware analysis.
Another way to check a virus is to use an online resource like the website VirusTotal. VirusTotal lets you submit a file online and have it checked against the anti-virus definitions there. One advantage to VirusTotal is that it runs multiple anti-virus engines, so you get the benefit of having multiple engines scanning without having to get the anti-virus software and run the scans yourself. Also, VirusTotal will scan files, URLs, and e-mails. If you have to scan a lot of files, you can use the VirusTotal application programming interface (API) to send files directly to VirusTotal without having to go through the web interface. VirusTotal will check your files against the anti-virus engines it uses and provide you with a report, as shown in Figure 12-10. The different names shown in the results aren’t a result of misidentifying as much as they are a result of different vendors providing different names to the same piece of malware.

Figure 12-10 The VirusTotal website
Malware, as discussed previously, is often packed, and before performing any analysis, the malware needs to be unpacked. When we start trying to look at strings within the executable, all we’re going to see is gibberish from the compressed part, plus the information from the code that does the unpacking. You can use a utility like PEiD or PESuite to determine how the application was packed. Figure 12-11 shows an application that was packed using UPX, which can be unpacked using the UPX utility shown earlier in Figure 12-6. Other utilities, like PE Explorer, will provide similar information to PEiD but will also extract the packed executable, assuming it is packed using a packer PE Explorer knows about. PE Explorer, however, is commercial software and is not free like PEiD. PE Explorer can also provide you with a list of dependencies the program has. All of the libraries that it relies on, as well as any libraries those libraries rely on, can be seen clearly in a tree view. This can make it much clearer what types of functions are in use in the executable.

Figure 12-11 The PEiD utility
Exercise 12-1: Using Strings
Either download the Windows Strings utility from the Windows Sysinternals website (look in the Miscellaneous category), or if you are using a Unix-derived operating system, such as macOS, you can use its built-in strings utility. Find a program and run the command line program strings against it, looking for any libraries that may be referenced.
Once you have the output from the unpacker, you have the real executable and can start examining it. While it’s a common technique used for a variety of purposes, the Unix strings utility, also available from Microsoft for Windows (see Exercise 12-1), will show all of the chunks of data that look like strings. Not all of what you get will be real strings from the application, but it’s a starting point. Figure 12-12 shows a portion of the output from the strings utility. In addition to any messages that the program may use to communicate with the user, which may provide some hints about what may be going on, the one thing you will absolutely see is the external function calls. You might see a list of dynamic libraries that the program makes use of. The libraries shown in Figure 12-12 are common Windows libraries and most of the function calls from those libraries are pretty common as well, but we can determine that the program checks the time on a file and also creates and manages some threads. This isn’t a lot of information to go on, though, and if you don’t have a lot of experience looking at malware samples, it may not be enough for you to draw any conclusions.

Figure 12-12 Output from the strings utility
There are a lot of great utilities you can use to peer into a program and make determinations about what you see. A utility called Hook Analyser will help you by providing some pointers about what is going on as it looks through the program for you. It will perform automatic static malware analysis, checking for the program entry point as well as looking into the data segment in the program. It has a database of packers that it knows about and will use this to determine how the executable was packed, and then provide that information for you. Based on the information it finds, you will have more detailed information about what you are looking at and whether it may be malware or not. Figure 12-13 shows example output from Hook Analyser.
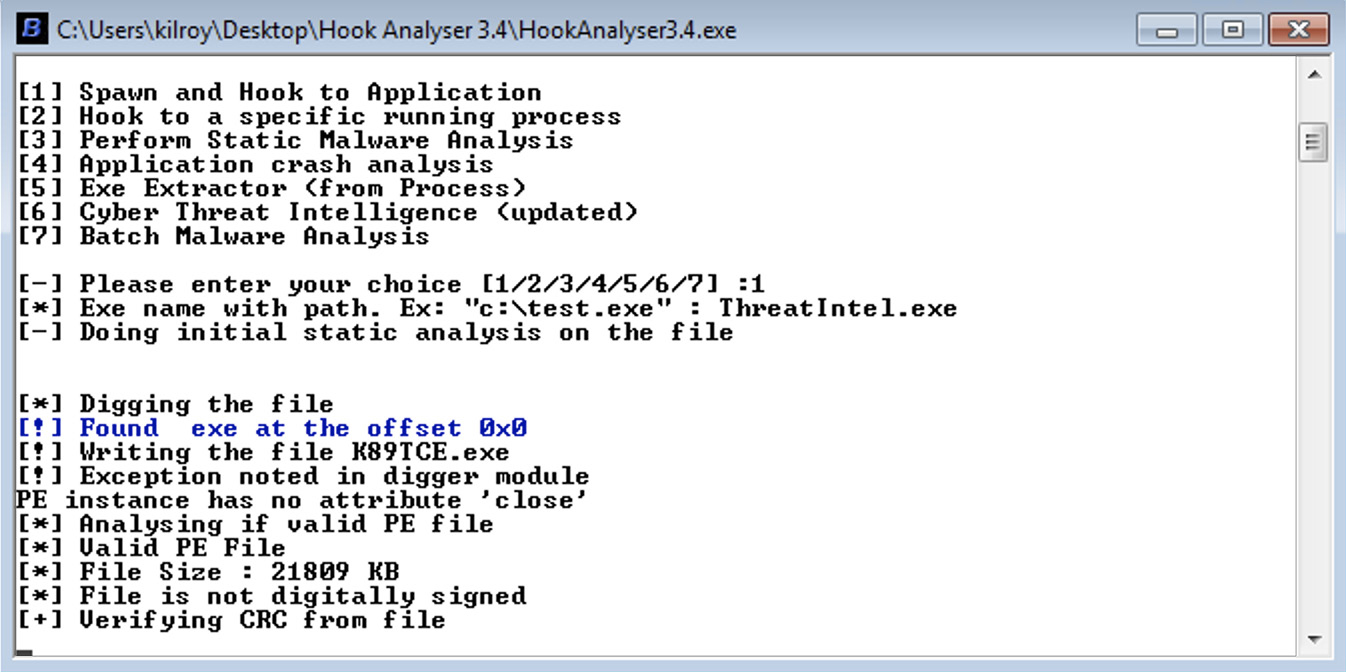
Figure 12-13 Output from the Hook Analyser utility
Once you’re done poking through the file to see what you can determine from the structure and libraries, it’s time to start taking a look at the code itself. If you are really lucky, it may simply be in a scripting language like JavaScript or Visual Basic Script and thus be easy to read. You may require a de-obfuscation tool to turn the code into something actually readable, but at least with a scripting language you have a good chance of seeing the original source. If you are unlucky, you may be stuck with a binary and need to convert it from the raw executable bytes to something you have a better chance of reading. You can do this by using a disassembler, which will convert the raw opcodes in the binary to assembly language, which is a set of mnemonics used to replace the numeric opcodes with something closer to words. Without a lot of practice and study, though, assembly language can be difficult to follow. This is where you may want to find a decompiler.
There are a handful of decompilers available, but decompilers can’t convert binary back to the original source code. The reason for this is that once a compiler has had its way with source code, the code has been optimized and shuffled around, and because writing programs is such a unique activity, it’s impossible to get back to the exact source code. What you can get back is a set of source code that would compile to the resulting executable, but it won’t look like the original source and won’t be nearly as readable. One thing programmers have long been taught is to self-document their code using meaningful variable names. A decompiler has no way of knowing what the original variable names were since they would have been completely lost in the compilation process, so it will make use of iterative variable names that have no meaning when it comes to trying to understand the program. However, in the end you will have something more easily understandable than the assembly language—unless you’ve spent your life writing assembly language, of course.
Dynamic Analysis
Static analysis can provide you with information useful in determining whether you are looking at malware or not. It is a lot harder from static analysis to see what the executable does, however. For that, you need to perform dynamic analysis. Dynamic analysis is a lot more dangerous than static analysis because dynamic analysis involves looking at the executable while it’s running to see different library calls, as well as opening files and registry keys. In executing any malware, you are guaranteeing that your system will be infected. As a result, the best approach to dynamic analysis is using any system other than your primary desktop. Smartest approach is to completely isolate the system. You might even use a virtual machine as a place to perform the analysis. With a virtual machine, you can take a snapshot of your clean system, then infect it with the malware, perform your analysis, and roll it back to the clean version of the virtual machine for the next piece of malware you want to look at.
In fact, there is a piece of software that will do this very thing for you. Cuckoo Sandbox is a set of Python scripts that will launch a virtual machine, inject the malware, and then track the behavior of the program, watching network traffic, seeing what files it may download, and watching the library calls that get made. This will be discussed in more detail in the upcoming “Cuckoo Sandbox” section.
The Windows Sysinternals team has a number of utilities that can look more deeply into a program and see what memory is in use, the strings stored in the running process, and the call stack of all the library functions that have been called. You can also see the system calls made from the program. In Figure 12-14, you can see Process Explorer, one of the utilities available from Sysinternals, which provides a lot of detail about the running process, including the strings. Process Explorer isn’t the only utility available, but it provides considerable detail about the running process and thus makes an excellent starting point. It will also show you all of the processes running at any given time, and since it’s not part of the operating system, it should be less suspect than other ways of getting the process list.
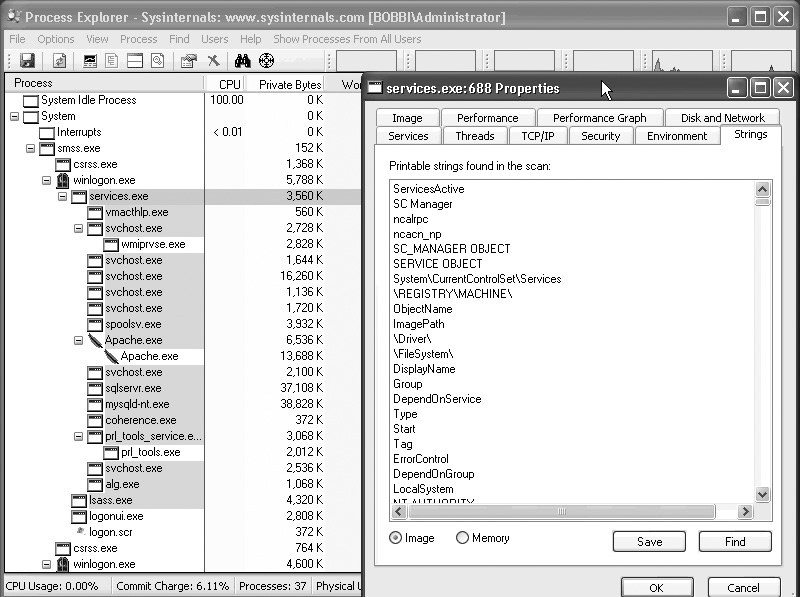
Figure 12-14 The Process Explorer utility
You’ll probably want to keep an eye on registry usage, including keys that may be created and values written. Files may be created that you’ll want to know about, and you’ll certainly want to keep an eye on network activity since the malware may download friends to have a party. It may also be trying to upload information from your system. Beyond the artifacts on your system, you may also want to see what the program is doing while it’s running. For that, you need a debugger. Figure 12-15 shows OllyDbg, which is a good, free debugger available for Windows. There are other debuggers available for Windows, as well as debuggers available for Linux, macOS, and any other operating system you can find. The majority of them work more or less the same way, enabling you to step through the program, one operation at a time, while also enabling you to watch memory and what happens to it. You may run the program directly from the debugger, or you might attach the debugger to a running program, if you happen to already have a piece of malware running on your system.
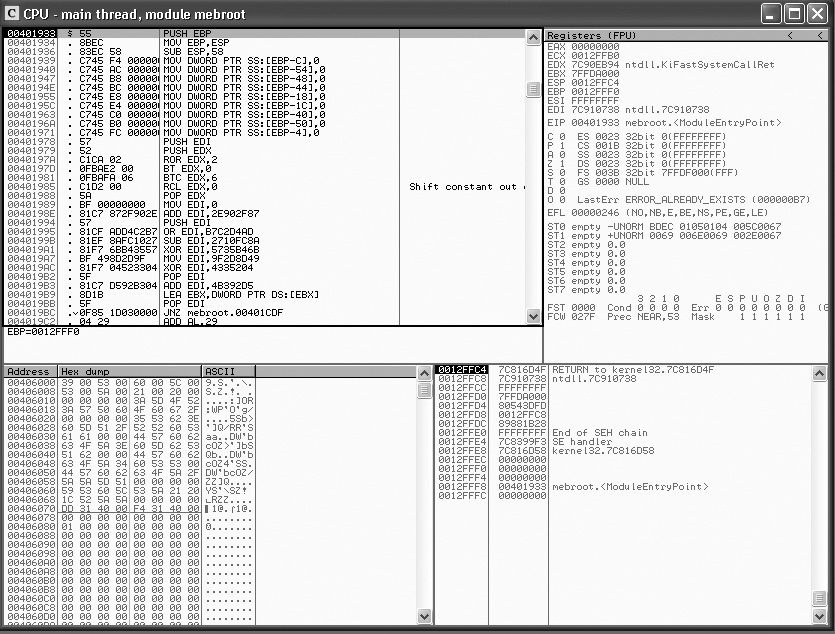
Figure 12-15 The free OllyDbg debugger
The debugger will provide you with a definitive answer about what the program is doing, since you can step through and watch every operation it performs, as well as all the memory it has control of. While other tools will provide you with ways to look at the program from the outside and poke and prod it in that way, the debugger will get you inside the program. Since this is a compiled program, you’ll be looking at machine code, which has been converted back to what looks like assembly language to make it easier to read. It is, though, the raw bytes that the CPU sees when it executes the program. With the debugger, you can alter the flow of the program and dig in as deep as you like. It does take some understanding of assembly language to know what is happening though. The debugger will provide you with a complete view of where you are in the program in memory, all the data the program has access to, and the values of all the CPU registers as they change.
Cuckoo Sandbox
Cuckoos are birds that lay their eggs in the nests of other birds, expecting the foster bird to hatch the cuckoo egg. This behavior of dropping unwanted items into a home is likely the reason for the naming of the Cuckoo Sandbox. Cuckoo Sandbox is an automated way of analyzing potentially malicious software. Cuckoo Sandbox requires a virtual machine set up with a Windows image that can be started up. Once the Windows virtual machine has been started and has had a snapshot created, the file for assessment is dropped into the running system and launched. This isolates the potential malware into an environment where it is locked down. The instance will be torn down once the file has been executed and the output assessed, meaning the malware is dead once the instance is no longer running. When done correctly, the network traffic outbound will be isolated and not allowed to connect to the Internet.
Cuckoo Sandbox’s power is a set of scripts that automate the startup, injection, and teardown of the VM. More importantly, though, is the capability of analysis of the output. These scripts will gather screen captures of the system while it’s running and also will look at the process table and any network connections. On Windows systems, the snapshot’s filesystem is compared against the running system to identify any file changes, including registry changes. This can indicate the presence of a dropper, if there are new files, or of persistence mechanisms, if there are registry or other changes. Figure 12-16 shows the output from Cuckoo Sandbox, after analyzing a PDF file that was attached to an e-mail flagged as junk by an e-mail provider.
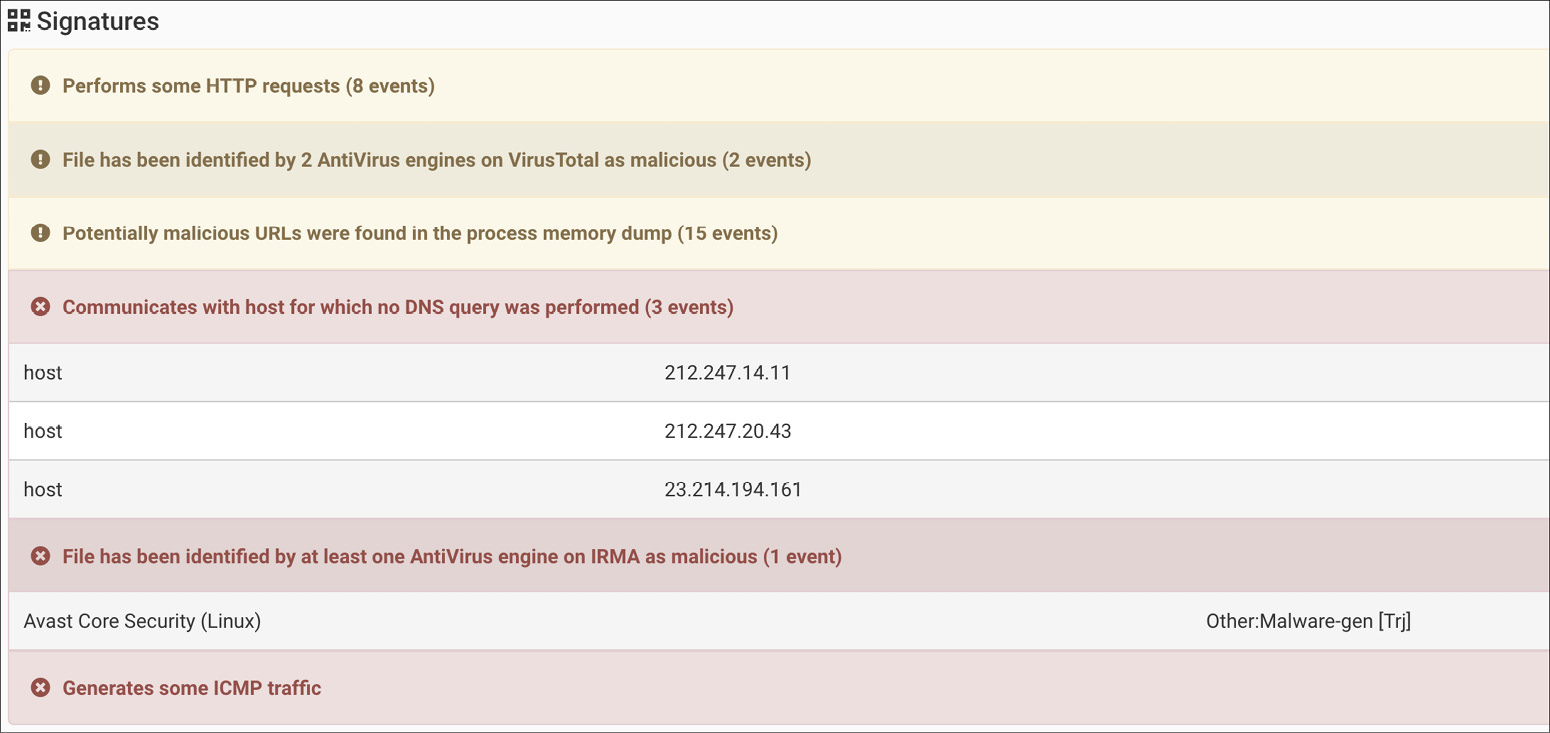
Figure 12-16 Cuckoo Sandbox output
The summary output shown, which is only a small part of everything available from Cuckoo Sandbox, indicates that two anti-virus engines on VirusTotal identified the PDF file as malicious software. Additionally, you can see that after opening the PDF, there was an attempt to connect to multiple IP addresses without the use of DNS hostnames. This is a common approach for malware and, as a result, is considered suspicious. You will also see that some ICMP traffic was generated. For further assessment, Cuckoo Sandbox provides a lot of log files from the execution and also several screen captures that were taken while the file was being opened and the results from having it open.
One of the safest ways to perform any malware analysis is through the use of a tool like Cuckoo Sandbox. It may be more satisfying to look at the malware by hand if you are very curious and technical by nature. However, Cuckoo Sandbox is going to be more reliable and quite a bit safer.
Malware Policies
A company may put policies into place regarding malware handling and prevention. The first common policy is that anti-virus must be run on all company-owned computer systems. This involves not only installing the software but making sure it’s kept up to date. On top of that, there may be policies concerning the use of external storage, like flash drives or even CDs, since any external source can be a way for a virus to get onto your system. There may even be technical controls in place to prevent users from making use of these external storage devices.
Ideally, an organization also has incident response policies related to handling virus intrusion, since containing and removing a virus is critical. A large-scale virus attack can last days or weeks, so having policies and procedures in place on how best to maintain business operations while also trying to keep the virus under control is important. The best way is to simply shut everything off and then treat the dead drives, removing the virus through the use of a LiveCD with a virus scanner on it. This means the virus is no longer infecting devices because it’s not on a live, running system. However, it also means that your business won’t be functioning until all the systems have been cleaned. This is where understanding a priority level of systems that can be shut down until the virus has been cleaned can be important. This may be done through the use of a policy or at least a procedure for handling malware or other incidents.
You may or may not be able to determine when your system has been infected, depending on how active the infection is or how intrusive. However, some common signs of virus infection are that systems become very sluggish all of a sudden. That’s not always a great indicator because there are a number of reasons for a system to become sluggish, but if there appears to be no reason for a system’s slowness, you might do well to investigate it with this in mind. Programs that used to run but simply fail to start can be a sign of a virus attack. If when looking you see a lot of unexplained network activity, this could be a result of a virus infestation. It could be caused by a botnet client reaching out to its handlers. Often, viruses will affect how your web browser behaves, redirecting some of the network traffic to other sites, or blocking access to some sites altogether.
Chapter Review
Whether it’s viruses, worms, Trojans, or some other form of malicious software, their numbers are increasing rapidly each year. But what was once a steadily increasing number has, in the last decade, turned into a nearly exponential curve. This is a very serious problem and, as with many things in security, is almost a war of attrition. Each side escalates based on the actions of the other, thus requiring more and more resources. While we do have technologies capable of combating malware, like anti-virus and intrusion detection, they are not perfect and rely primarily on knowing what the malware looks like, which can limit their effectiveness, particularly when it comes to newer malware that has yet to be analyzed.
Malware analysis can be a dangerous activity since you run the risk of having information removed from your system or having files deleted, or perhaps finding yourself participating in a distributed denial-of-service attack. There are two types of malware analysis: static and dynamic. Static analysis looks at a program’s details and tries to determine whether it’s malware, perhaps finding out what it’s doing, seeing whether it’s packed, and determining what strings may be in the program. You can also use anti-virus programs to perform static malware analysis and they should be able to tell you whether the program is malware and what type it is, assuming it’s one the anti-virus programs know about.
Dynamic malware analysis is more involved and can be automated, though more commonly it is performed by running the program and seeing what effect it has on the system with new registry keys or new files as well as any network activity that may be occurring. Dynamic analysis is best done in a very controlled environment, within a virtual machine that has network access tightly locked down to protect against further infection on your network as well as to prevent leakage of anything about your system to a malware controller somewhere else.
Questions
1. You’ve found what looks like a piece of malware. When you run it, a number of new files show up in your temp directory, and some of those files have records of things you have typed. You received it from a friend via e-mail, but you checked and you don’t see that it was sent out from your e-mail account to anyone. Based on this scenario, what type of malware is this most likely to be?
A. Adware
B. A Trojan
C. A virus
D. A worm
2. You have a piece of malware and you want to do static analysis on it. What might you do?
A. Install it in a virtual machine.
B. Run it through a debugger.
C. Attach it to the running process.
D. Run strings on it.
3. Which of these is NOT a reason for packing a binary?
A. To make it smaller
B. To make it more efficient
C. To hide it from anti-virus scanners
D. To make it easier to transmit
4. The purpose of a rootkit is to do what?
A. Hide malware
B. Provide the root password
C. Copy itself to many other systems
D. Create user accounts
5. From an attacker’s perspective, what is the advantage to using a boot sector virus?
A. It is written in assembly language.
B. It is very small.
C. It can re-infect the system each time it boots up.
D. It creates hidden partitions.
6. One way viruses have historically been able to copy themselves from one system to another is by using what mechanism?
A. Administrative share
B. Remote desktop
C. Remote SSH access
D. Dropbox
7. What is the specialized type of engineering malware makes use of?
A. Chemical
B. Civil
C. Social
D. Mechanical
8. You notice a lot of unusual network traffic to remote systems originating from your computer. When you investigate further, you discover that a number of computers on your network are doing the same thing, and the IP address is in another country. This always seems to happen in the late evening hours. What may you be seeing?
A. Video streaming
B. System updates
C. Synchronization activity
D. Botnet activity
9. Botnets historically have used which protocol to communicate with handlers?
A. SMTP
B. IRC
C. AOL
D. CHAT
10. You regularly get popup ads on your computer, particularly when you are browsing the Web. What is this an example of?
A. A virus
B. A worm
C. A botnet client
D. Adware
11. Your anti-virus software has identified a file named Agobot on your system. What does this mean?
A. Nothing. This is a false positive.
B. Your system has been infected with ransomware.
C. You have been using the Tor network.
D. Your system has a dropper installed.
12. What is the common payment mechanism expected for victims of ransomware?
A. Rubles
B. Dinar
C. Bitcoin
D. PotCoin
13. Which of these would be a common persistence vector?
A. Registry key
B. HKEY
C. Prefetch folder
D. VirusTotal
14. If you wanted to check a possible piece of malware against multiple anti-malware sources, where would you go?
A. Malwarebytes
B. VirusTotal
C. TotalVirus
D. MalwareAggregator
15. What program could you use to extract URLs that a piece of malware connects to while running?
A. Strings
B. PEiD
C. Cuckoo Sandbox
D. ProcessDigger
Answers
1. C. Since the scenario doesn’t indicate evidence of popups or refer to the program claiming to be something that it isn’t, it’s not adware or a Trojan. It potentially could be a worm since it was received via e-mail, but your mail program apparently didn’t send it out to anyone, so it’s probably not a worm because it’s not attempting to self-propagate as far as you can tell. Therefore, it’s most likely a virus.
2. D. Running the strings utility is a valid option for static malware analysis. You wouldn’t install it, either in a virtual machine or anywhere else, because malware is commonly a standalone application, meaning there is no installer. Running it in a debugger or attaching to it while it’s running are dynamic analysis techniques.
3. B. Packing doesn’t make the binary more efficient because the first thing the program needs to do is unpack before running. Packing makes malware smaller because you are compressing it. Because it’s smaller, it’s easier to transmit. When you pack malware, you may be able to hide it from anti-virus scanners.
4. A. The purpose of a rootkit is to hide the existence of something, like remote access from someone or a piece of malware running on the system. It may also act as a backdoor that gives an attacker remote access. A rootkit doesn’t provide the root password, or copy itself to many other systems, and it wouldn’t create user accounts itself.
5. C. A boot sector virus has the capability to re-infect at each boot to ensure the main virus is still in place and persists. While a boot sector virus may also have a component that creates a hidden partition, that isn’t an advantage of boot sector viruses, nor is it because they are small, since you can’t do much in a small space. It may not have originally been written in assembly language.
6. A. Windows NT systems used to have administrative shares for each drive, called C$, D$, and so on, which made remote administration easy but also made the systems more vulnerable to malware. Remote desktop doesn’t provide you with the ability to copy files, nor does remote SSH access (though you can copy files using scp, which makes use of SSH). Dropbox can sync files across multiple systems, but it hasn’t historically been used to copy malware from one system to another.
7. C. Social engineering is often used to get malware onto systems. Chemical, civil, and mechanical engineering aren’t helpful in software development or malware creation.
8. D. This could very well be botnet-related. If the activity mostly happens in the late evening to IP addresses out of the country, it’s unlikely to be system updates or video streaming since there isn’t anyone in the office watching video. The IP addresses out of the country is what makes it unlikely to be system updates. Synchronizing doesn’t make sense without context.
9. B. Botnet clients have historically used IRC, which is where a lot of bots originated. CHAT and AOL as protocols don’t exist. SMTP could conceivably be used, but it isn’t very common.
10. D. This is an example of adware. You’d need more than this to have a virus or a worm and it probably isn’t a botnet client either.
11. D. Agobot is a dropper. This is potentially malicious, though not necessarily so. The dropper itself is not malicious, though the malware it may download and execute would be. The anti-virus program probably correctly identified the file, so it’s not a false positive. Agobot is not ransomware and it has not been linked to ransomware. While you may have been using the Tor network, this alert alone is not an indication of that.
12. C. Ransomware commonly demands payment in the cryptocurrency Bitcoin. Dinar and rubles are both physical currency and aren’t easily transmitted over the Internet. Cryptocurrency is, though. While PotCoin is also a form of cryptocurrency, it is not generally associated with common families of ransomware.
13. A. The registry has keys that can be used to make sure malware keeps running across reboots. While HKEY is a portion of a full path to a registry key, it is not a persistence mechanism. The prefetch folder is where you may find evidence that a program has run, but it is not used for persistence. VirusTotal is a website used to check malware against multiple anti-malware databases.
14. B. VirusTotal is a website that makes use of dozens of anti-malware engines to check potential malware against. Malwarebytes is a single anti-malware software solution. TotalVirus and MalwareAggregator don’t exist.
15. A. The strings program will display printable character strings from a file. This could include URLs that the malware is using, if any. You could use PEiD to gather information about malware, but PEiD doesn’t extract data from the executables that might point to URLs used. Cuckoo Sandbox may include this information but it wouldn’t be extracted from the file. The URLs would have to be called to be identified in Cuckoo Sandbox. ProcessDigger doesn’t exist.
Exercise 12-1 Answer
Under Windows, you may see references to libraries like KERNEL32.DLL or MSVCRT.DLL. Any string that ends in .DLL will be a library reference. Under other operating systems, you’ll have to look for other markers for their libraries. In Linux, you should see files that end in .so, and under macOS, you should see files that end in dylib. These are all dynamic libraries, meaning they get pulled in dynamically as the program is running rather than being linked in at compile time, which would be called static linking.


