Figure 16-1: Virtual machines in a hybrid cloud.
Managing Virtualization
A management infrastructure is going to be key in a hybrid cloud world. In fact, when virtualization is used in cloud computing, it’s quite possible that the management software you use in your data center will fall short. You need to consider how you want to handle management, which includes provisioning resources as well as dealing with security and capacity planning. Face it: This is new territory. Although it’s still early, different models are emerging. For example, some of the virtualization vendors are offering management solutions. Service management vendors are also looking to provide tools to manage hybrid virtualization.
When managing virtualization, the service provider (whether it’s your IT organization or a cloud provider) must be able to do the following:
![]() Know and understand the relationships among all elements of the network.
Know and understand the relationships among all elements of the network.
![]() Be able to change things dynamically when elements within this universe change.
Be able to change things dynamically when elements within this universe change.
![]() Keep placement of virtual resources in step with all the other information held in the configuration management database (CMDB). A CMDB stores configuration items that detail the attributes of individual entities in an IT environment. Given that few organizations have anything approaching a comprehensive CMDB, that’s asking a lot. In fact, ideally the CMDB should capture how all service management capabilities are integrated.
Keep placement of virtual resources in step with all the other information held in the configuration management database (CMDB). A CMDB stores configuration items that detail the attributes of individual entities in an IT environment. Given that few organizations have anything approaching a comprehensive CMDB, that’s asking a lot. In fact, ideally the CMDB should capture how all service management capabilities are integrated.
You’re going to have to decide who your hybrid cloud administrator will be and the skills she will need to do the job. Following are some of the issues associated with managing a virtualized hybrid cloud.
Handling foundational issues
Managing a virtual environment involves foundational issues that determine how well the components function as a system. The foundations have to be in sync between the public and private worlds. This means that management needs to understand how the following issues will be treated:
![]() Licenses management: Many license agreements tie the license fee to physical servers rather than virtual servers. Resolve these licenses before using the associated software in a virtual environment. The constraints of such licenses may become an obstacle to efficiency.
Licenses management: Many license agreements tie the license fee to physical servers rather than virtual servers. Resolve these licenses before using the associated software in a virtual environment. The constraints of such licenses may become an obstacle to efficiency.
![]() Service levels: Measuring, managing, and maintaining service levels can become more complicated simply because the environment itself is more complicated. When a public cloud is added to the mix, the cloud consumer is responsible for establishing service levels for both internally virtualized environments and those living in the cloud.
Service levels: Measuring, managing, and maintaining service levels can become more complicated simply because the environment itself is more complicated. When a public cloud is added to the mix, the cloud consumer is responsible for establishing service levels for both internally virtualized environments and those living in the cloud.
![]() Network management: The real target of network management becomes the virtual network, which may be harder to manage than the physical network.
Network management: The real target of network management becomes the virtual network, which may be harder to manage than the physical network.
![]() Capacity planning: Although it’s convenient to think that all servers deliver roughly the same capacity, they don’t. With virtualization, you have more control of hardware purchases and can plan network resources accordingly.
Capacity planning: Although it’s convenient to think that all servers deliver roughly the same capacity, they don’t. With virtualization, you have more control of hardware purchases and can plan network resources accordingly.
Managing virtualization in hybrid environments
In a virtualized hybrid environment, you’ll have lots of images of the environment across multiple environments. However, you’ll need to treat all resources together as though they were a single system, as opposed to an image here or there. If you don’t, you’ll end up having resources that are there but not being used in an effective manner. The issue is how you manage these images in a virtualized hybrid environment. Figure 16-1 illustrates just how complicated this management can be. You can see that you have multiple virtual machines, across multiple environments.
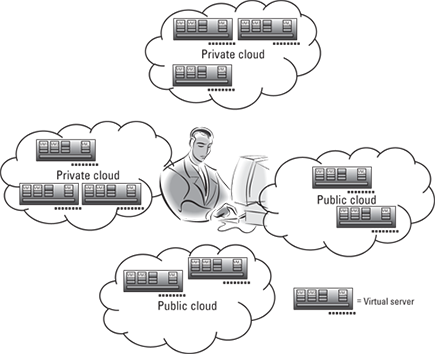
A strong management platform needs to deal with the issues that we describe in this section.
Provisioning software
Provisioning software lets you manually adjust the virtualized environment. Using provisioning software, you can create new virtual machines and modify existing ones to add or reduce resources. This type of provisioning is essential to managing workloads and to moving applications and services from one physical environment to another. Provisioning software enables the following:
![]() Migration of running virtual machines from one physical server to another
Migration of running virtual machines from one physical server to another
![]() Automatic restart of failed virtual machines on a separate physical server
Automatic restart of failed virtual machines on a separate physical server
![]() Clustering, or grouping, of virtual machines across different physical servers
Clustering, or grouping, of virtual machines across different physical servers
In a hybrid environment, you’ll have to make sure that cloud providers offer provisioning software in a consistent manner and can work with your internal resources.
Hardware provisioning
Before virtualization, hardware provisioning was simply a matter of commissioning new hardware and configuring it to run new applications (or possibly repurposing it to run some new application).
Virtualization makes this process a little simpler in one way: You don’t have to link the setup of new hardware to the instantiation of a new application. Now, you can add a server to the pool and enable it to run virtual machines. Thereafter, those virtual machines are ready when they’re needed. When you add a new application, your cloud data center administrator or your service provider (via a self-service interface) will enable you to configure it to run on a virtual machine.
One of the key benefits that companies have found with cloud computing is the ability to quickly and effectively provide additional hardware resources from IaaS providers.
The hypervisor, referenced earlier in this chapter, lets a physical server run many virtual machines at the same time. In a sense, one server does the work of maybe ten. That arrangement is a neat one, but you may not be able to shift those kinds of workloads without consequences. A server running 20 virtual machines, for example, may still have the same network connection with the same traffic limitation, which could act as a bottleneck. Alternatively, if all those applications use local disks, many of them may need to use a SAN or NAS (described in Chapter 20) — and that requirement may have implications in terms of performance.
Security issues
Using virtual machines complicates IT security in a big way for companies running hybrid cloud environments. Virtualization changes the definition of what a server is, so security is no longer trying to protect a physical server or a collection of servers that an application runs on. Instead, it’s protecting collections of virtual machines running across multiple environments. Here, as a result, are some security issues that arise:
![]() Perimeter security: In a hybrid cloud, the data center is no longer a single entity that you can protect. You now have to ask yourself what your perimeter security looks like.
Perimeter security: In a hybrid cloud, the data center is no longer a single entity that you can protect. You now have to ask yourself what your perimeter security looks like.
![]() Hypervisor security: Just as an OS attack is possible, a hacker can also take control of a hypervisor. If the hacker gains control of the hypervisor, he gains control of everything that it controls; therefore, he could do a lot of damage. The hypervisor should have no externally accessible ports that can be accessed by a hacker, and it should be as invisible as possible to a network. It should not have to be patched often.
Hypervisor security: Just as an OS attack is possible, a hacker can also take control of a hypervisor. If the hacker gains control of the hypervisor, he gains control of everything that it controls; therefore, he could do a lot of damage. The hypervisor should have no externally accessible ports that can be accessed by a hacker, and it should be as invisible as possible to a network. It should not have to be patched often.
![]() Storage security: If data is written to a local storage machine and then not cleaned when reallocated to another virtual machine, data leakage can occur.
Storage security: If data is written to a local storage machine and then not cleaned when reallocated to another virtual machine, data leakage can occur.
![]() Configuration and change management: The simple act of changing configurations or patching the software on virtual machines becomes much more complex if the software is locked away in virtual images. In the virtual world, you no longer have a fixed static address to update the configuration.
Configuration and change management: The simple act of changing configurations or patching the software on virtual machines becomes much more complex if the software is locked away in virtual images. In the virtual world, you no longer have a fixed static address to update the configuration.
![]() Network monitoring: Current network defenses are based on physical networks. In the virtualized environment, the network is no longer physical; its configuration can actually change dynamically, which makes network monitoring difficult. To fix this problem, you must have software products (available from companies such as VMware, IBM, CA, and HP) that can monitor virtual networks.
Network monitoring: Current network defenses are based on physical networks. In the virtualized environment, the network is no longer physical; its configuration can actually change dynamically, which makes network monitoring difficult. To fix this problem, you must have software products (available from companies such as VMware, IBM, CA, and HP) that can monitor virtual networks.
Capacity planning
Capacity planning refers to the estimation of how much computer hardware, software, connection infrastructure, and space will be needed over a certain period of time. Although capacity planning in a data center means a lot of forecasting, capacity planning in the cloud model is theoretically easier because of the elastic nature of the cloud. However, that doesn’t mean you shouldn’t do it. You still need to have some idea of what work loads will go where and what the performance will be. Otherwise, although you think you might have infinite resources, you may find that you don’t, or that your costs become uncontrollable.
For example, virtualized servers can get 95 percent utilization, and virtualization makes creating images easy. You may wonder what’s wrong with that. The problem is that people create images and then don’t get rid of them. These images can be haphazard. You can end up with blobs where you don’t know what’s inside. Besides being a security issue, this situation can lead to a proliferation of images. IBM notes that a typical virtual image can range in size from 5GB to 20GB. So, even though virtualization was created to control server sprawl, it’s also created image sprawl, where images are left after a virtual machine is taken offline. This situation can lead to high storage costs, especially because often virtual machines automatically ask for storage.

 Provisioning is now the act of allocating a virtual machine to a specific server from a central console. Be aware of a catch, however. You can run into trouble if you go too far. You may decide to virtualize entire sets of applications and virtualize the servers that those applications are running on, for example. Although you may get some optimization, you also create too many silos that are too hard to manage. You may have optimized your environment so much that you have no room to accommodate peak loads.
Provisioning is now the act of allocating a virtual machine to a specific server from a central console. Be aware of a catch, however. You can run into trouble if you go too far. You may decide to virtualize entire sets of applications and virtualize the servers that those applications are running on, for example. Although you may get some optimization, you also create too many silos that are too hard to manage. You may have optimized your environment so much that you have no room to accommodate peak loads. We won’t use the acronym SaaS for security as a service, because that would be confusing, and security as a service is really a subset of SaaS. However, note that a class of vendors does provide security as a service — in other words, to help monitor and control certain kinds of hybrid deployments.
We won’t use the acronym SaaS for security as a service, because that would be confusing, and security as a service is really a subset of SaaS. However, note that a class of vendors does provide security as a service — in other words, to help monitor and control certain kinds of hybrid deployments.