

Application development
This chapter describes the following topics:
•JTLite/JTOpenLite Java Classes Library for mobile application development
15.1 High-level programming languages
IBM i has a suite of IBM Integrated Language Environment® (ILE) compilers that include RPG, COBOL, C, C++, and CL. IBM Rational® Development Studio for i V7.1 delivers significant enhancements to the compilers.
For more information about ILE Compilers, see 16.3, “IBM Rational Development Studio for i” on page 640.
15.2 Control Language (CL)
This section covers the following topics:
15.2.1 New workload capping commands
New workload capping commands were added to the IBM i commands. You can use workload capping to set a usage limit for a licensed program by restricting the number of processor cores that are available to be used by the licensed program.
Here are the new workload capping commands:
•Add Workload Capping Group (ADDWLCGRP)
•Add Workload Capping Product Entry (ADDWLCPRDE)
•Change Workload Capping Group (CHGWLCGRP)
•Display Workload Capping Group (DSPWLCGRP)
•Remove Workload Capping Group (RMVWLCGRP)
•Remove Workload Capping Product Entry (RMVWLCPRDE)
For more information about these commands, see the following website:
http://publib.boulder.ibm.com/infocenter/iseries/v7r1m0/index.jsp?topic=%2Frbam6%2Frbam6whatsnew.htm
15.2.2 Retrieving CL source support for ILE CL
Developers can move to IBM Integrated Language Environment (ILE) without fear of not being able to retrieve their source statements. IBM i 7.1 included this enhancement with the ILE module. For completeness, even the Declare Processing Options (DCLPRCOPT) command was updated to reflect that the ALWRTVSRC keyword now applies to ILE program as well.
The Retrieve CL Source (RTVCLSRC) command can be used to retrieve control language CL source statements from an Integrated Language Environment ILE module. The module must be created with the Create CL Module (CRTCLMOD) command or the Create Bound CL program (CRTBNDCL) command by specifying *YES for the ALWRTVSRC parameter. The module that contains the CL source to be retrieved can be a module (*MODULE) object or a module within an ILE program (*PGM) or service program (*SRVPGM) object.
The ability to retrieve the CL source from a CL program or CL module can make it easier to diagnose and fix problems in CL code on systems where the original CL source code is not available.
The following command retrieves the CL source from module MOD1 in the ILE program MYCLPGM:
RTVCLSRC PGM(MYCLPGM) MODULE(MOD1) SRCFILE(MYLIB/QCLSRC)
The retrieved CL source is stored in member MOD1 of the source physical file QLCSRC in library MYLIB. The default value for the ALWRTVSRC parameter is *YES.
15.2.3 Longer Integer CL variables for ILE CL
All variables must be declared to the CL program or procedure before they can be used by the program or procedure.
The Declare CL variable (DCL) command supports a value of 8 for the LEN parameter for signed integer *INT and unsigned integer *UINT variables if the CL source is compiled using the CRTCLMOD or the CRTBNDCL commands. This capability is useful when you call API programs and API procedures that define 8-byte integer fields in input or output structures.
|
Important: LEN(8) can be specified only if the CL source is compiled with the Create CL Module (CRTCLMOD) or the Create Bound CL Program (CRTBNDCL) command.
|
15.2.4 Showing DO and SELECT nesting levels in a compiler listing
You can specify a CL compiler option to see the nesting level for all types of DO and
SELECT commands.
SELECT commands.
CL source programs contain DO and SELECT commands where these commands are nested several levels deep. For example, between a DO command and the corresponding ENDDO command can be a DOFOR and another ENDDO command. The CL compiler supports up to 25 levels of nesting for DO commands and SELECT commands.
You can specify OPTION(*DOSLTLVL) and the Create CL Program (CRTCLPGM) command or the CRTCLMOD or the CRTBNDCL commands.
This compiler option adds a column to the compiler listing, which shows the nesting levels for the following elements:
•Do DO
•Do For DOFOR
•Do Until DOUNTIL
•Do While DOWHILE
•SELECT
If you do not want to see this nesting level information, you can specify *NODOSLTLVL for the OPTION parameter.
15.2.5 Encrypting the debug listing view for ILE CL
You can create a compiler listing view of the ILE CL procedure in a CL module by specifying *LIST for the Debugging view DBGVIEW parameter on the CRTCLMOD or the CRTBNDCL command. The listing view can be seen by anyone with sufficient authority to the program or service program object that contains the CL module.
In IBM i 7.1, a new keyword parameter Debug encryption key DBGENCKEY was added to the CRTCLMOD and the CRTBNDCL commands. Specifying an encryption key value for the DBGENCKEY parameter and *LIST for the DBGVIEW parameter causes the debug listing data to be encrypted before it is stored with the module *MODULE or ILE program *PGM object. To see the listing view during debugging, you must provide the same encryption key value.
When you start the debug session, you are prompted for the encryption key value. If the same value is not specified for the debug session that was specified when the CL module was created, no listing view is shown.
15.2.6 Nested INCLUDE support
You can use the Include CL Source (INCLUDE) command to split your CL source code so that the CL source code can be compiled across multiple source file members.
The CL source to be embedded can be in another member of the same source file that is identified on the Source file SRCFILE parameter of the CL compiler commands or another source file. The CL compiler commands include CRTCLPGM, CRTCLMOD, and the CRTBNDCL Program.
You can run the RTVCLSRC command later to retrieve either the original CL source (which contains just the INCLUDE commands) or the expanded CL source (which contains the embedded CL source commands).
15.3 PHP and Zend products
PHP stands for PHP Hypertext Preprocessor. PHP is an open source scripting language that is designed for web application development and enables simple scripting.
PHP applications are easily integrated with data in IBM DB2 for i, RPG, COBOL, and other business applications that are running on IBM i.
PHP is used for content management, customer relationship management, database access, e-commerce, forums, blogs, wikis, and other web-based applications.
Zend and IBM worked together to deliver Zend Solutions for IBM i, a complete PHP development and production environment solution for the IBM i platform.
Here are the Zend Solutions for IBM i:
•Zend Server Community Edition for IBM i (one year Silver Support from Zend)
•Zend Server for IBM i
•Zend Studio for IBM i (One year of Silver Support from Zend)
•Zend DBi
Zend Server Community Edition for IBM i comes with V6.1 and V7.1.
|
Tip: Always use the distribution downloaded from the Zend website, which ensures that you have the latest version of the Zend Server Community Edition.
|
Zend Solutions for IBM i can be downloaded from the Zend website at:
Figure 15-1 shows the Zend application development and deployment architecture for IBM i.
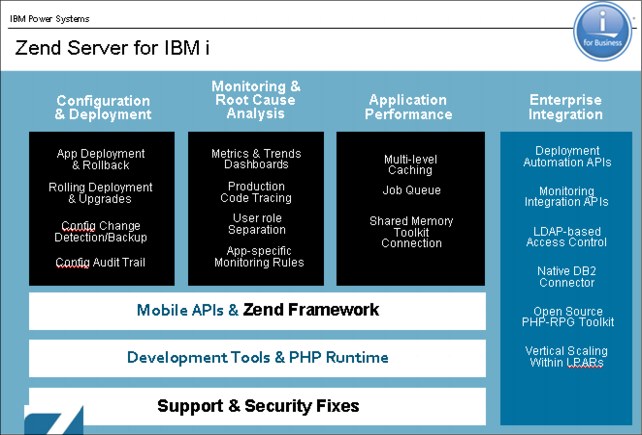
Figure 15-1 Zend PHP Application development and deployment architecture for IBM i
The following sections summarize features and enhancements of Zend products for IBM i.
15.3.1 Zend Server Community Edition for IBM i
Zend Server Community Edition (CE) is a fully tested and enhanced version of the open source PHP. It provides the PHP run time and is packaged to make the software installation easier and faster with the instant PHP setup. It is enhanced to take advantage of IBM i specific resources and capabilities.
Zend Server CE for IBM i is a lightweight version of Zend Server, and replaces Zend Core. It offers the following features:
•Preinstalled on IBM i 6.1 and IBM i 7.1 starting April 2010.
•Includes extensions and a toolkit that provides the following functions:
– Enables PHP application to easily access DB2 for i data
– Takes advantage of RPG and COBOL applications in IBM i
– Supports for Program call, Procedure call, Data Area, Data Queue, Message Queue, Commands, and System values
•Simple to install and to use, and provides basic performance optimization.
•Available at no charge to for using in development or in production, and it comes with an initial year of Silver Support that is provided by IBM.
•Zend Server is the only Zend certified and supported version of PHP for IBM i.
15.3.2 Zend Server for IBM i V6.1.0
Zend Server is a robust PHP production environment that helps ensure that applications written in PHP run smoothly at all time. It is designed for IT personnel and businesses that require commercial grade web applications in highly reliable production environments.
Zend Server replaces the Zend platform. It offers all the features that are provided in Zend Server CE for IBM i and the following additional features:
•High performance and scalability to provide customers with an improved web experience and response time.
•Delivers application uptime and reliability through enhanced PHP monitoring and immediate problem resolution.
•Includes the Java Bridge for integrating PHP application with Java application.
•Includes 5250 bridge for integrating 5250 applications with PHP applications. The 5250 bridge allows running interactive IBM i based applications from a web browser.
•Cloud connected Mobile Deployment
•Zend Framework 2, Zend Server Gateway
•PHP 5.4, PHP 5.3 are supported, PHP 5.2 is not supported
•Side by side Migration of Zend Server 5.6 and 6.0
•Improved User Interface, role-based access
•Global monitoring rules by application
•Shared Memory Toolkit option improves speed 30%+
The following website shows a comparison between the features that are offered in Zend Server CE for IBM i and Zend Server for IBM i:
15.3.3 Zend Studio for IBM i V10
Zend Studio for IBM i is an industry-leading Eclipse-based PHP integrated development environment (IDE) designed for professional developers. It includes all the development components necessary for the full PHP application lifecycle and simplifies complex projects. It now supports development for mobile devices as well using PHP REST XML Web Services.
Zend Studio for IBM i includes the following features and enhancements:
•Enhanced to work with the integration toolkit provided with Zend Server and Zend Server CE for IBM i
•Includes a comprehensive set of editing, debugging, analysis, optimization, database, and testing tools
•Toolkit support for easy integration with earlier IBM i applications and data
•Customizable and context-sensitive templates for IBM i Toolkit functions
•Create / generate PHP Toolkit code quickly
•Call an RPG/CL/COBOL program, run a CL command, retrieve Spooled file entries, and access Data Area, Data Queue, and User Space.
•Zend Studio allows development for mobile clients:
– Web
– Native i/OS (Mac)
– Android
– Windows Mobile
15.3.4 Zend DBi and actual PHP database support
The Zend DBi product provides MySQL implementation for IBM i. DB2 Storage Engine enables MySQL data storage in DB2.
Zend DBi provides support for Open Source based applications. The application uses MySQL data commands against Zend DBi or MySQL database. The storage engine translates the commands, then passes them to DB2 for i. With this solution, there is only one database to manage, backup, and protect. See Figure 15-2.
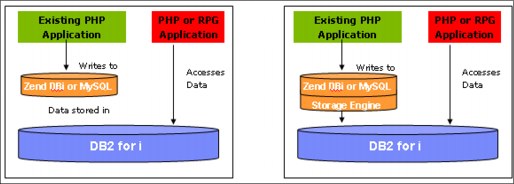
Figure 15-2 Zend DBi and MySQL using DB2 Storage engine
PHP now supports the following database connectivity:
•Local DB support for MySQL and DB2
•Remote DB support for MySQL and Oracle
For more information about Zend products for IBM i, see the following websites:
•Zend and IBM i:
•Zend Products for IBM i:
•Zend Studio:
•Zend DBi:
15.4 XMLSERVICE for IBM i
XMLSERVICE is open source RPG code that enables web XML scripting calls of IBM System i resources, such as PGM, SRVPGM, CMD, PASE utilities, and SQL DB2, over various driver transports (DRDA, ODBC, and REST) through 1-tier (IBM i) or 2-tier clients (Linux/Windows).
XMLSERVICE can be accessed from PHP, Java, Ruby, RPG, Groovy, or other languages that can work with XML.
All the information, including several demonstrations, can be found at the following website:
For more information about XML or open source programming languages, see:
15.4.1 XMLSERVICE highlights
Here are some highlights of XMLSERVICE:
•The code is developed in RPG.
•XMLSERVICE can be licensed to be used at no additional cost (XMLSERVICE library download).
•XMLSERVICE can be deployed as either PC (2-tier) or IBM i (1-tier).
•All communication is through XML documents.
•The called RPG programs can maintain state, commit boundaries, and so on.
•XMLSERVICE provides an interprocess communication (IPC) mechanism that synchronizes multiple web client sources.
•There is traditional DB2 connection security 1–2 tier (when you use the provided DB2 stored procedures).
•XMLSERVICE handles the conversions of XML string text to and from the actual program required parameter type (packed decimal 12p2, zoned decimal 7s2, integer 10i0/5i0, float 4f2/8f4, or hex binary 400b), and character data is converted automatically to ASCII/EBCDIC (1024A/10a varying=‘on’).
•Arrays of data structures are allowed both as parameters and return, including nested data structures or arrays of data structures.
15.4.2 XMLSERVICE start
There are several options to start XMLSERVICE. It can be called from a web server, any application server that handles HTML or REST web services, through the ODBC Driver, or through the PHP toolkit.
To start XMLSERVICE, complete the following steps:
1. Install the XMLSERVICE programs.
2. Define the communication method to use:
– 1 Tier: Apache Web Server or PHP (Zend Server)
– 2 Tier: ODBC Driver or Web Application Server / PHP Server in the middle tier
Installing XMLSERVICE
The XMLSERVICE Library is on your IBM i systems if you apply the latest HTTP Server PTF Group:
•IBM i 7.1: 5770-SS1 SF99368 HTTP PTF Group Level 16, or later
•IBM i 6.1: 5761-SS1 SF99115 HTTP PTF Group Level 28, or later
XMLSERVICE can be downloaded from the Young IBM i Professionals website at:
After you have the XMLSERVICE package, upload it in to your IBM i System by running the commands that are shown in Example 15-1.
Example 15-1 Uploading the XMLSERVICE.zip file
#IBM i CL Command:
CRTSAVF FILE(QGPL/XMLSERVICE)
#PC:
unzip xmlservice-rpg-1.7.3.zip
ftp IBMiHostName ...
bin
cd QGPL
put /path/xmlservice.savf XMLSERVICE
The commands that are shown in Example 15-2 finish the installation process.
Example 15-2 CL Commands to install XMLSERVICE and test programs
#IBM i CL Commands:
RSTLIB SAVLIB(XMLSERVICE) DEV(*SAVF) SAVF(QGPL/XMLSERVICE)
ADDLIBLE XMLSERVICE
CRTCLPGM PGM(XMLSERVICE/CRTXML) SRCFILE(XMLSERVICE/QCLSRC)
CALL CRTXML
#If you want to create some optional programs for testing and demo, execute the #following commands:
CRTCLPGM PGM(XMLSERVICE/CRTTEST) SRCFILE(XMLSERVICE/QCLSRC)
CALL CRTTEST
CRTCLPGM PGM(XMLSERVICE/CRTTEST6) SRCFILE(XMLSERVICE/QCLSRC)
CALL CRTTEST6
#Do not forget to provide the corresponding autorization:
CHGAUT OBJ('/qsys.lib/XMLSERVICE.lib') USER(QTMHHTTP) DTAAUT(*RWX) OBJAUT(*ALL) SUBTREE(*ALL)
CHGAUT OBJ('/qsys.lib/XMLSERVICE.lib') USER(QTMHHTP1) DTAAUT(*RWX) OBJAUT(*ALL) SUBTREE(*ALL)
|
CCSIDs: If you are running an IBM system with CCSID 65535 (hex), you must set the Apache web server to a valid CCSID (such as 37 or 284) by running this command:
DefaultFsCCSID 37 CGIJobCCSID 37
|
Configuring the HTTP Server
To configure the XMLSERVICE REST, open the HTTP administrative console session by using the URL http://hostname:2001/HTTPAdmin and add the interface by using the RPG CGI (xmlcgi.pgm), as shown in Figure 15-3.
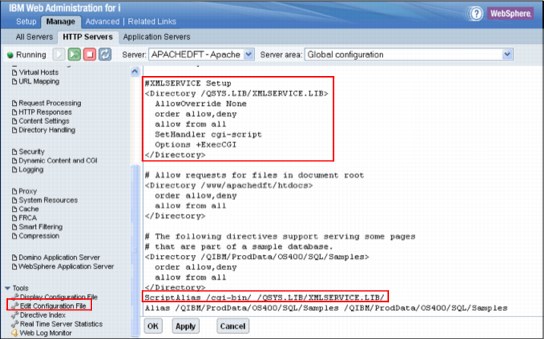
Figure 15-3 HTTP Server configuration to add XMLSERVICE
Testing XMLSERVICE
You can create a few HTML files, including XML tags to call IBM i resources. Figure 15-4 shows a program call example using XMLSERVICE.

Figure 15-4 HTML file with XML tags to call an IBM i program
|
User ID and password: Depending on your security setup, you might need to change the session parameters “uid” and “pwd” to a valid user ID and password.
|
To start the program through the web browser, enter the IBM i URL address or host name and the previous HTML file name:
http://HostName/yourhtmlfilename.html
The resulting XML document is shown in Figure 15-5. It is a basic sample of a Program call. However, you can use a rich set of XML tags with other IBM i resources, such as <cmd>, <sh>, <pgm>, and <sql>.

Figure 15-5 Returned XML file by XMLSERVICE
For more information about XMLSERVICE commands, parameters, and reserved words, see:
15.5 IBM Lotus products for IBM i
Lotus software delivers robust collaboration software that empowers people to connect, collaborate, and innovate when optimizing the way they work. With Lotus, you can achieve better business outcomes through collaboration. The following Lotus Software products are supported on IBM i 7.1:
•IBM Lotus Domino V8.5.1, 8.5.2, and 8.5.3
•IBM Domino 9.0
•IBM Notes Traveller 9.0
•IBM Connections 4.5
•IBM Sametime® V8.5.1, 8.5.2
•IBM Lotus Quickr® 8.5 and 8.5.1 for Domino
•IBM Lotus Enterprise Integrator® (LEI) V8.5.2, 8.5.3
•IBM Enterprise Integrator 9.0
•IBM Lotus Workflow V7.0 or later
•IBM Forms Server V8.0 or later
•IBM Forms Server V4.0 or later
•IBM Lotus Forms Server V3.5.1 FP2 or later
•IBM Integrated Domino Fax for i5/OS V4R5
|
Product withdrawal: Domino Fax for i5/OS V4R5 was withdrawn from worldwide marketing on January 14, 2011 and end of support was on April 30, 2012.
|
Only specific releases of these products are supported on IBM i 7.1. Before you upgrade to IBM i 7.1, check the most current details about the product releases supported at the following website:
15.6 Native archive and unarchive API support
IBM i 7.1 now supports both native creation and extraction of archive files.
This support includes the following native APIs and a service program to create archive files:
•QZIPZIP API
•QZIPUNZIP API
•QZIPUTIL Service program
15.6.1 QZIPZIP API
Multiple files and directories within IBM i can be compressed and packaged into a single archive file using the QZIPZIP() API.
The QZIPZIP syntax is as follows:
#include <qziputil.H>
void QzipZip(
Qlg_Path_Name_T * fileToCompress,
Qlg_Path_Name_T * compressedFileName,
char * formatName,
char * zipOptions,
char * errorStruct)
Parameters
Table 15-1 shows the list of QZIPZIP API parameters.
Table 15-1 Parameters for QZIPZIP API
|
Name
|
Type
|
Description
|
|
fileToCompress
|
Input
|
The name of the file or directory that is to be compressed into an archive file. The path name must be in Qlg_Path_Name_T structure.
|
|
CompressedFileName
|
Input
|
The name of the compressed archive file. This file is created by the API. The path name must be in Qlg_Path_Name_T structure.
|
|
formatName
|
Input
|
The format name to pass the user's options for compressing a file or a directory to an archive file. For more information, see “ZIP00100 format description” on page 600.
|
|
zipOptions
|
Input
|
This pointer passes in the user's options to the QZIPZIP API in ZIP00100 format.
|
|
errorStruct
|
Input/output
|
This item is a pointer to an error code structure to receive error information.
|
Authorities and locks
The user must have at least the following authorities to be able to use the API:
•*R data authority to the file that is to be compressed
•*R data authority to each directory in the path name that precedes that file
•*W data authority to the directory where the compressed file is written
During the time the API reads a file before compressing it, the file is locked and shared with read only mode. The API releases the lock on the file after it reads the file. If the file that is to be compressed is locked, then an error message is sent. Further compression is stopped.
ZIP00100 format description
Table 15-2 shows the format for passing the user's options to compress files or directories.
Table 15-2 Format description
|
Offset
|
Type
|
Field
|
|
|
Dec
|
Hex
|
||
|
0
|
0
|
CHAR(10)
|
Verbose option
|
|
10
|
A
|
CHAR(6)
|
Subtree option
|
|
16
|
10
|
CHAR(512)
|
Comment
|
|
528
|
210
|
BINARY(4), UNSIGNED
|
Length of the comment
|
15.6.2 QZIPUNZIP API
The contents of the (.zip) archive file can be extracted by running QZIPUNZIP on the target IBM i system.
The QZIPUNZIP syntax is as follows:
#include <qziputil.H>
void QzipUnzip(
Qlg_Path_Name_T * compressedFileName,
Qlg_Path_Name_T * dirToPlaceDecompFiles,
char * formatName,
char * unzipOptions,
char * errorStruct)
Parameters
Table 15-3 shows the list of QZIPUNZIP API parameters.
Table 15-3 Parameters for QZIPZIP API
|
Name
|
Type
|
Description
|
|
CompressedFileName
|
Input
|
The name of the archive file that is to be extracted. The path name must be in the Qlg_Path_Name_T structure.
|
|
dirToPlaceDecompFiles
|
Input
|
The directory in which you place the contents of the archive file. The path name must be in the Qlg_Path_Name_T structure.
|
|
formatName
|
Input
|
The format name to pass the user's options for extracting an archive file. See “UNZIP100 format description” for a description of this format.
|
|
unzipOptions
|
Input
|
This item is a pointer that passes in the user's options to the QZIPUNZIP API in UNZIP100 format.
|
|
errorStruct
|
Input/output
|
This item is a pointer to an error code structure to receive error information.
|
Authorities and locks
The user must have at least the following authorities to be able to use the API:
•*R data authority to the file that is to be decompressed
•*R data authority to each directory in the path name that precedes that file
•*W data authority to the directory where the decompressed file is written
During the time, this API reads a compressed archive file for extracting it, and the file is locked and shared for reading only. The API releases the lock on the file after it reads the file completely. If the file that is to be extracted is locked, then an error message is sent. Further extracting is stopped.
UNZIP100 format description
Table 15-4 shows the format for passing the user's options to compress files or directories.
Table 15-4 Format description
|
Offset
|
Type
|
Field
|
|
|
Dec
|
Hex
|
||
|
0
|
0
|
CHAR(10)
|
Verbose option
|
|
10
|
A
|
CHAR(6)
|
Subtree option
|
15.6.3 QZIPUTIL Service program
The service program QZIPUTIL has entry points that can be called by any other ILE program to create and extract archive files. It is a system state user domain service program that adopts *USER authority.
The QZIPUTIL service program exported QZIPZIP and QZIPUNZIP APIs.
15.7 Java for IBM i 7.1
For the latest news on Java for IBM i see the following website:
Java Developer Kit 1.4, 5.0 and 6 (5761JV1 options 6, 7, and 10), which are referred to as classic Java, are no longer supported in IBM i 7.1 and were replaced by IBM Technology for Java. If your applications are still using classic Java, you must upgrade to IBM Technology for Java, but before you do, be aware of the following information (also see Table 15-5):
•Classic Java virtual machine (JVM) is a 64-bit virtual machine. Migrating to the 32-bit IBM Technology for Java (default JVM) reduces the Java object heap to no larger than 3 GB, which is approximately 1000 threads. If you require more than 1000 threads or a Java object heap larger than 3 GB, use the 64-bit version of the IBM Technology for Java.
•If you have ILE programs that use Java Native Interface functions, you must compile these programs with teraspace storage enabled.
•Adopted authority for Java program is not supported by IBM Technology for Java
virtual machine.
virtual machine.
•PASE for i now enforces stack execution disable protection.
•You must install the latest Group PTF for Java SF99572.
Table 15-5 Classic Java levels and the suggested IBM Technology for Java replacement
|
Current product classic Java
|
Option
|
Replacements of IBM Technology for Java
|
Option
|
|
Java Developer Kit 1.4 - 5761JV1
|
6
|
Java SE 6 32 bit - 5761JV11
|
11
|
|
Java SE 6 64 bit - 5761JV1a
|
12
|
||
|
J2SE 5.0 32 bit - 5761JV1
|
8
|
||
|
J2SE 5.0 64 bit - 5761JV1
|
9
|
||
|
J2SE 1.4 64 bit - 5761JV1
|
13
|
||
|
Java Developer Kit 5.0 - 5761JV1
|
7
|
Java SE 6 32 bit - 5761JV1a
|
11
|
|
Java SE 6 64 bit - 5761JV1a
|
12
|
||
|
J2SE 5.0 32 bit - 5761JV1
|
8
|
||
|
J2SE 5.0 64 bit - 5761JV1
|
9
|
||
|
Java Developer Kit 6 - 5761JV1
|
10
|
Java SE 6 64 bit - 5761JV1
|
11
|
|
Java SE 6 64 bit - 5761JV1
|
12
|
1 Use Java SE 6 when migrating from Java Developer Kit 1.4 or 5.0.
For more information about Java for IBM i 7.1, see the IBM i 7.1 Knowledge Center:
|
Supported options: Licensed program product 5761-JV1 options 6, 7, and 10 are the only options that are not supported in IBM i 7.1.
|
15.7.1 Enabling IBM Technology for Java virtual machine
IBM Technology for Java virtual machine is available in both 32-bit and 64-bit versions and is included in the licensed program 5761-JV1 as part of standard distribution set.
To install the IBM Technology for Java virtual machine option, complete the following steps:
1. Enter the Go Licensed Program (GO LICPGM) command and select Option 10.
2. If you do not see the program listed, then complete the following steps:
a. Enter the GO LICPGM command on the command line.
b. Select Option 11 (Install licensed program).
c. Choose option 1 (Install) for licensed program 5761-JV1 *BASE and select the option that you want to install.
3. Load the latest Java PTF group.
4. Set the JAVA_HOME environment variable to the home directory of the Java Development Kit that you want to use. As an example, enter one of the following commands from the command line to select correct Java Development Kit (JDK). Full list of Java Development Kits supported is in the Table 15-6.
– ADDENVVAR ENVVAR(JAVA_HOME) VALUE(‘/QOpenSys/QIBM/ProdData/JavaVM/jdk14/64 bit’)
– ADDENVVAR ENVVAR(JAVA_HOME) VALUE(‘/QOpenSys/QIBM/ProdData/JavaVM/jdk50/32 bit’)
– ADDENVVAR ENVVAR(JAVA_HOME) VALUE(‘/QOpenSys/QIBM/ProdData/JavaVM/jdk50/64 bit’)
– ADDENVVAR ENVVAR(JAVA_HOME) VALUE(‘/QOpenSys/QIBM/ProdData/JavaVM/jdk60/32 bit’)
– ADDENVVAR ENVVAR(JAVA_HOME) VALUE(‘/QOpenSys/QIBM/ProdData/JavaVM/jdk60/64 bit’)
|
Suggestion: Upgrade to IBM Technology for Java before you migrate to IBM i 7.1.
|
Supported options of 5761-JV1 IBM Developer Kit for Java product are listed in Table 15-6.
Table 15-6 shows that a single 5761-JV1 option (like options 11, 12, 14, and 15) can hold 2 different JDKs, like Java 6.0 and 6.2.6 in options 11 and 12, or Java 7.0 and 7.1 in options 14 and 15.
Table 15-6 Supported options of 5761-JV1 IBM Developer Kit for Java product
|
Option
|
JDK
|
JAVA_HOME
|
|
8
|
IBM Technology for Java 5.0 32bit
|
/QOpenSys/QIBM/ProdData/JavaVM/jdk50/32bit
|
|
9
|
IBM Technology for Java 5.0 64bit
|
/QOpenSys/QIBM/ProdData/JavaVM/jdk50/64bit
|
|
11
|
IBM Technology for Java 6.0 32bit
|
/QOpenSys/QIBM/ProdData/JavaVM/jdk60/32bit
|
|
11
|
IBM Technology for Java 6 2.6 32bit
|
/QOpenSys/QIBM/ProdData/JavaVM/jdk626/32bit
|
|
12
|
IBM Technology for Java 6.0 64bit
|
/QOpenSys/QIBM/ProdData/JavaVM/jdk60/64bit
|
|
12
|
IBM Technology for Java 6 2.6 64bit
|
/QOpenSys/QIBM/ProdData/JavaVM/jdk626/64bit
|
|
13
|
IBM Technology for Java 142 64bit
|
/QOpenSys/QIBM/ProdData/JavaVM/jdk14/64bit
|
|
14
|
IBM Technology for Java 7.0 32bit
|
/QOpenSys/QIBM/ProdData/JavaVM/jdk70/32bit
|
|
14
|
IBM Technology for Java 7.1 32bit
|
/QOpenSys/QIBM/ProdData/JavaVM/jdk71/32bit
|
|
15
|
IBM Technology for Java 7.0 64bit
|
/QOpenSys/QIBM/ProdData/JavaVM/jdk70/64bi
|
|
15
|
IBM Technology for Java 7.1 64bit
|
/QOpenSys/QIBM/ProdData/JavaVM/jdk71/64bit
|
For complete and regularly updated table see the following website:
15.7.2 New Java 7.1 support
Java 7.1 is supported as part of option 15 (See Table 15-6 on page 603). It is a hybrid JDK which takes advantage of the J9 JVM. This updated JVM leverages the same class libraries as Java 7 but provides better performance and cloud support.
For more information, see the following website:
15.7.3 PTF Groups and latest service releases and fixpacks
The following website contains the latest updated information for PTF groups and the latest service releases and fixpacks:
15.7.4 Java on IBM i security updates
See the following website for information about Java on IBM i security:
This page also points to the Common Vulnerabilities and Exposures (CVE) web pages.
15.8 IBM Toolbox for Java JDBC
JDBC is an API included in the Java platform that enables Java programs to connect to a wide range of databases.
You can use the IBM Toolbox for Java JDBC driver to use JDBC API interfaces to issue Structured Query Language (SQL) statements to and process results from databases on
the server.
the server.
The following sections describe the enhancements that are done to IBM Toolbox for Java JDBC support for IBM i 7.1.
15.8.1 JDBC 4.1
Java JDBC interface now supports several features of the latest JDBC 4.1 definitions with DB2 i. Java developers can use this enhancement to continue to use the latest defined options for JDBC.
15.8.2 XML Data type support
The JDBC 4.0 interface specification adds new methods and classes for XML Data type support. IBM Toolbox for Java implements XML support in its JDBC 4.0 driver.
This enhancement allows JDBC clients easy access to IBM i 7.1 XML support.
15.8.3 Database metadata updates
Database metadata is obtained by calling methods of the AS400JDBCDatabaseMetaData class. Starting with IBM i 7.1, the default behavior of IBM Toolbox for Java JDBC is to obtain this metadata from a set of standard system stored procedures.
This enhancement brings IBM Toolbox for Java into alignment with IBM i native JDBC support in addition to JDBC drivers on other platforms.
To provide compatibility with earlier versions of the metadata functionality, a new connection property, “metadata source”, can be used to force IBM Toolbox for Java JDBC to use the old method of retrieval of database metadata.
15.8.4 Currently committed support
Lock timeouts and deadlocks can occur under the isolation levels that perform row-level locking, especially with applications that are not designed to prevent such problems. Some high throughput database applications cannot tolerate waiting on locks that are issued during transaction processing, and some applications cannot tolerate processing uncommitted data, but still require non-blocking behavior for read transactions.
Under the new currently committed semantics, if currently committed is enabled, then only committed data is returned, as was the case previously, but now readers do not wait for writers to release row locks. Instead, the data that is returned to readers is based on the currently committed version, that is, data before the start of the write operation.
This feature also implements a way to direct the database manager to wait for the outcome when it encounters data while being updated.
15.8.5 Array type support
IBM Toolbox for Java supports the IBM i 7.1 SQL array data type in stored procedure parameters. Arrays of all of the various DB2 types are supported, except for data that is returned in a locator.
IBM Toolbox for Java JDBC adds support for arrays as IN, OUT, and INOUT parameters to stored procedures. However, ResultSets returned from stored procedures or other queries that contain arrays is not supported.
JDBC supports the calling of stored procedures in the java.sql.CallableStatement class, which IBM Toolbox for Java implements in AS400JDBCCallableStatement.
15.8.6 Long schema name support
IBM i 7.1 DBMS added support for 128 byte schema names. IBM Toolbox for Java JDBC is adding support for long schema names.
15.9 JTLite/JTOpenLite Java Classes Library
JTLite is an alternative to the JT400 and JTOpen Java toolkits, and provides a small footprint (about 420 KB) and good performance that is focused on application development for
mobile devices.
mobile devices.
The Lite version of the Java toolbox for IBM i provides a new smaller foot print toolkit for accessing IBM i native objects from Java running on mobile devices. Table 15-7 shows the difference between both Java libraries.
Table 15-7 Differences between JTOpen and JTOpen Lite
|
JTOpen and JT400
|
JTOpenLite and JTLite
|
|
Database - JDBC (SQL) and record-level access (DDM)
|
Database - JDBC (SQL) and record-level access (DDM)
|
|
Integrated File System
|
Integrated File System - Open, Read, Write, Delete
|
|
Program calls (RPG, COBOL, Service Programs, and so on)
|
Program calls (RPG, COBOL, Service Programs, and so on)
|
|
Commands
|
Commands
|
|
Data Queues
|
|
|
Data Areas
|
|
|
Print/Spool resources
|
|
|
Product and PTF information
|
|
|
Job and Joblogs
|
Job information
|
|
Messages, messages queue, message files
|
|
|
Data Queues
|
|
|
Users and groups
|
User and Group information
|
|
User spaces
|
|
|
System values
|
|
|
System status
|
|
For access to the project, go to the following website:
15.10 Application Runtime Expert for i
IBM Application Runtime Expert for i (ARE) is a new product that has the potential to revolutionize how you do application service and support. ARE can help you ensure consistent performance and deployment for any workload that is running on your system. You can use ARE to build and maintain an application knowledge base that can be used to automatically apply its knowledge to verify a system.
ARE provides a GUI that you can use to collect and verify a customized set of information, system settings, and attributes about the following items:
•Applications
•An IBM i system
•A runtime environment
ARE collects the needed information and builds it into a template. This template can then be used in verifying the application and its environment, on the same system where the template was built, or any other IBM i system.
When you run a template against an IBM i system, the system is verified against the information that is stored in the template, and the results are documented in a set of reports. These reports give a clear and concise view of what changed, or what is different.
Templates can be updated easily to include new information and settings from the ARE GUI.
15.10.1 Deployment template
A deployment template represents the expected attributes and state of a deployment and its environment. Typically, a deployment consists of application attributes and attributes of the environment the application runs in. Users can customize different plug-ins by defining what information to include in the deployment template using the Deployment Template Editor. Each plug-in can verify a different aspect of a deployment.
Here are common examples of a deployment:
•IBM i products
•Applications on IBM i:
– ISV application
– WebSphere Application Server
– Integrated WebSphere Application Server
– RPG application
– Directory tree in IFS
•Custom selection of software products, system, and environment information
The deployment template is used as an input to the ARE Core. ARE Core uses the deployment template as the basis for comparison for the attributes and state of the deployment on the system that is being verified.
Deployment Template Editor
You can use the Deployment Template Editor to create, edit, import, and export deployment templates. Users can use the editor to customize their templates. Templates that are created or edited can be used to verify systems using the console.
15.10.2 Customizing plug-ins for templates
IBM Application Runtime Expert for i has a wide array of application attributes and settings it can collect, along with many of the system settings and values that the most critical for your applications. After the template customization is complete, you can build it by using the Build template button.
The following sections describe some of the possible attributes and values that can be collected by ARE:
•Files and directories
•Software requirements
•Network
•System Environment
•Advanced
Files and directories
You can customize the template to verify various files and directories settings:
•File and Directory Attributes
•File and Directory Authorities
•Configuration Files
•Resource Collector
File and Directory Attributes plug-in
The File and Directory Attributes plug-in verifies attributes such as existence, creation date, last modification date, size, and CCSID. Attributes can be verified for files and directories in IFS, and objects in the Library file system. The precise file and directory attributes that are verified by this plug-in are fully customizable.
This plug-in can also verify that a symbolic link is truly a symbolic link and not a real file. This plug-in is useful to detect cases where a symbolic link was replaced by an actual copy of the file that it is supposed to be a link to.
File and Directory Authorities plug-in
The File and Directory Authorities plug-in verifies authority attributes, such as owner, authorization list, primary group, and private data and object authorities. Authority attributes can be verified for files and directories in IFS, and objects in the Library file system. The precise authority attributes verified by this plug-in are fully customizable.
Configuration Files plug-in
The Configuration Files plug-in verifies that the contents of configuration files are correct.
The following configuration file types are supported:
•XML configuration files
•Property files
•Apache HTTP configuration files
The items to check in a configuration file are fully customizable, as are the types of checks performed (equals, does not equal, contains, exists, exclude, and more). The expected value for configuration items can also be customized, as shown in Figure 15-6.

Figure 15-6 Edit Expected Value
Resource Collector plug-in
You can use the Resource Collector plug-in to collect and package files and objects from the target system into an archive file for more review. This feature allow Application Runtime Expert to verify specific files and attributes and to collect the data that is needed to review and possibly debug an issue on a system.
The plug-in allows specific files and directories from IFS to be collected and packaged into a single archive file. You can also use it to gather native IBM i objects and libraries by saving these native object and libraries into SAVF objects that can then be included in the specified archive file.
Software requirements
You can customize the template to verify various software requirements and prerequisites:
•IBM i Products
•PTFs
IBM i products
You can use this feature to select specific IBM i products from the list of all IBM i products. The selected products are added to the list of products to verify in the template.
You can use the Check Product Option (CHKPRDOPT) CL command during product verification to provide useful, product-specific information. Select the CHKPRODOPT check box to enable this feature, as shown in Figure 15-7.

Figure 15-7 Verify IBM i products
When a problem is found during product verification, the problem is added to the IBM i product verification section of the report. The severity of the problem, which determines how the problem is recorded in the report, can be customized for each product verified.
To select an IBM i product that is not installed on the system, click the Filter button and select the Show all products supported by IBM i option, as shown in Figure 15-8.

Figure 15-8 Filter IBM i products
PTFs
The PTFs plug-in verifies the status of individual and group PTFs on an IBM i system. It also lists all group PTF levels on the system, which is equivalent to the information displayed by the WRKPTFGRP CL command. The specific PTFs and group PTFs that are verified are fully customizable. This plug-in can verify that a group PTF level meets both a minimum and recommended level.
Network
You can use this feature to verify various TCP/IP configuration settings, network characteristics, and ports status:
•Network Configuration
•Port validation
Network Configuration plug-in
The Network Configuration plug-in verifies various TCP/IP configuration settings and network characteristics. Much of the TCP/IP configuration that is verified are the configuration settings viewable by running the CFGTCP CL command.
The primary purpose of this plug-in is to attempt to verify that the system's network configuration is such that applications that require frequent access to the network, such as web applications, can do so in a fast, reliable, and repeatable manner.
Port validation plug-in
The Port validation plug-in verifies whether one or more specified ports are active or inactive on the system. The plug-in can verify whether one or more specified ports are restricted.
Ports on the system can be restricted by running CFGTCP and selecting option 4 - Work with TCP/IP port restrictions. If an application requires a port that is already in use or is restricted, the application might fail to start or not work correctly.
System Environment
You can use this feature to verify various system environments settings, including network attributes, environment variables, and user IDs:
•System Values and Network Attributes
•Environment Variables
•User IDs
•Scripts and Commands
•SQL Query Verifier
System Values and Network Attributes plug-in
The System Values and Network Attributes plug-in verifies system values and that network attributes are configured as a deployment expects. The expected value for a system value or network attribute is customizable, including the capability to specify a single value, list of possible values, a range of possible values, and more.
There is also the option to list, but not check, a value in the report, which is a useful mechanism to automate the collection of system configuration information.
Environment Variables plug-in
The Environment Variables plug-in collects and optionally verifies system-wide environment variables. System-wide environment variables can affect the runtime attributes of any job on the system, so their existence, and their values, are an important part of the environment on which any application runs.
User IDs plug-in
The User IDs plug-in verifies attributes of one or more IBM i user profiles. Over 20 different attributes can be verified, such as special authorities, group profile, supplemental group, profile enabled, and more. The exact attributes to check are customizable, as shown in Figure 15-9.

Figure 15-9 Verify User IDs
Scripts and Commands plug-in
You can use the Scripts and Commands plug-in to verify the results of Qshell scripts or CL commands on a remote system. This plug-in provides a powerful and simple way to extend the base verification function that is provided by Application Runtime Expert for i. The results of each verification are customizable, including the capability to specify the source of a result, expected value, a range of expected values, and more.
SQL Query Verifier plug-in
The SQL Query Verifier plug-in can verify database information using SQL statements. An SQL statement can be specified to be run on the target system. The results of this SQL query can be verified. The verification of specific column data or the number of records that are returned can be verified. The complete query results can also be returned as part of the ARE report.
Advanced
ARE offers some advanced features for plug-in customization:
•Custom plug-ins
•Other Resources
•Plug-in Configuration
Custom plug-ins
You can use this feature to manage custom plug-ins that are included in the deployment template. Custom plug-ins are Java classes that can augment the verification that is performed by a deployment template. Anyone can write a custom plug-in, and after the plug-in is created, it can be added to any deployment template.
A custom plug-in plugs into the IBM Application Runtime Expert for i environment, and is run along with the other plug-ins selected and customized using the deployment template editor.
Other Resources plug-in
You can use this feature to manage other resources, which are any items that are not a custom plug-in and are included in the deployment template. Other resources are commonly needed with a custom plug-in. For example, a custom plug-in might require several other Java classes for it to run. These additional Java classes can be added to the deployment template using the Other Resources window.
Plug-in Configuration
Several advanced plug-in features can be edited through the Plug-in Configuration window. Additionally, any plug-in that can be used by a template, including plug-ins that are not configured elsewhere in the GUI, can be configured and added to a template using the Plug-in Configuration window.
15.10.3 Application Runtime Expert console
After a template is built, there are two ways it can be used to verify a system:
•Use the console web user interface.
•Use a script that can be run from Qshell.
This section describes using the console to verify IBM i systems.
The console is a web user interface that enables a system, or group of systems, to be verified using a deployment template that was created or imported by using the deployment template editor.
Systems are verified by the following sequence of events:
•The console remotely logs in to the system.
•The console starts the ARE to perform the verification, using the specified deployment template.
•The results of the verification go back to the console so that they can be reviewed.
|
Requirement: A valid, enabled user profile name and password for the target system must be provided. The user profile must have *ALLOBJ special authority on the target system because the verification of the target system might involve the inspection of many different files, authorities, PTFs, user profiles, and other items.
|
The Groups feature provides a way to group one or more systems into a discrete entity. Groups are useful for creating different sets of systems to verify, especially when each set of systems needs a different deployment template for verification as shown in Figure 15-10.
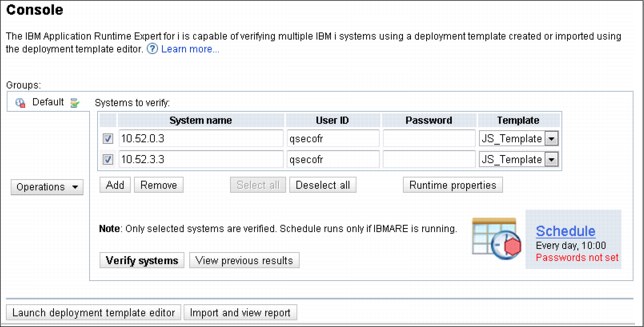
Figure 15-10 Application Runtime Expert console
Verifying systems
Verification can be done for all systems that are specified in the console panel. They can even have different templates. User IDs and passwords for individual systems can be set up directly in the console window, or you can have one general User ID and password for all systems. Such a User ID must have *ALLOBJ authority on all systems where verification must run. This can be set up using the Runtime properties button. The Console Runtime Properties window (Figure 15-11) is then shown. You then can specify a general User ID.

Figure 15-11 Runtime Properties window
Scheduling verification tasks
Notice the Schedule icon in the lower-right corner of the Figure 15-10 on page 614. Clicking Schedule displays the window shown in Figure 15-12.
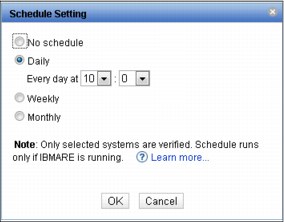
Figure 15-12 Schedule window
After the system verification is complete, a Complete icon is shown in the status column for that system and a brief summary of its verification is shown in the result column. If the console failed to perform the verification on a target system, a red icon is shown followed by a brief reason description of why the verification cannot not be performed as shown in Figure 15-13.
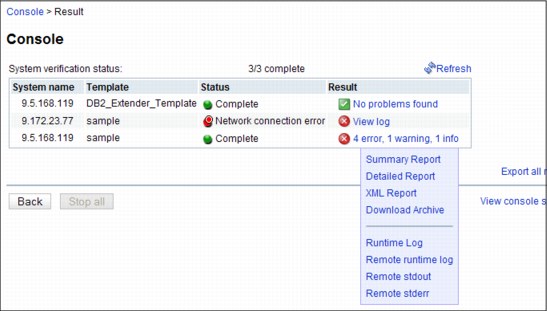
Figure 15-13 System verification status
More details about the failure can be found by clicking the View log link in the result column.
Reports
For systems that were verified, the results column contains a brief summary of the verification results. The summary text in the result column is also a link. This link provides access to the verification reports generated by the ARE core during the verification of the target system, as shown in Figure 15-13 on page 615.
All three ARE reports (summary, detailed, and XML) are available through the link in the result column. You can also download all the reports in an archive file by clicking the Download Archive link.
Summary report
The summary report contains a summary of all problems that are detected during the verification of a system. Each row in the summary table contains the results for a specific plug-in, such as the “Authority Verifier” or “System Value Verifier” plug-ins. The icon directly before the plug-in name indicates the highest severity problem that was found by that plug-in. The other items in each row indicate the number of attributes that are verified by the plug-in, and the number of problems that are found at each severity level (Error, Warning, and Info). The final item in each row, the “Fix actions” column, indicates how many of the detected problems can be fixed directly from the console web interface.
Figure 15-14 and Figure 15-15 show examples of two summary reports.

Figure 15-14 Summary report 1
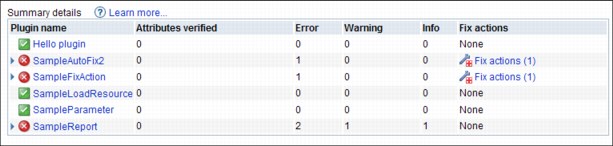
Figure 15-15 Summary report 2
Detailed report
The detailed report is a text report that contains every status and problem message reported during verification. This report is a complete record of everything that was checked during verification and the result of each check, even if the check did not detect a problem.
XML report
The XML report is an XML formatted report that contains every status and problem message reported during verification. This report is a complete record of everything that was checked during verification and the result of each check, even if the check did not detect a problem. In this regard, the XML report is exactly like the detailed report, except in an XML format instead of plain text.
|
XML report details: XML reports include information about how to fix detected problems. ARE Core uses an XML report as a guide for automatically fixing detected problems.
|
Verification status history
From the console window, it is possible to get the history of verifications done in the past (especially if automatic scheduling is in place). History can be displayed by clicking the View previous results. A sample of the status history is shown in Figure 15-16.
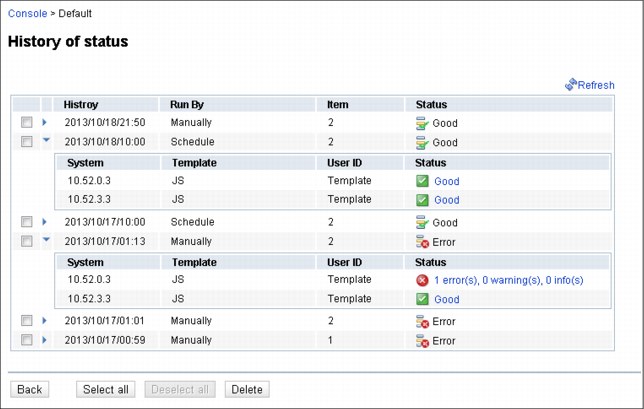
Figure 15-16 History of verification status
Automatic fixes
IBM Application Runtime Expert for i offers another important feature, which is the ability to automatically fix problems that are detected by ARE.
The “Fix actions” column in the summary report allows certain problems that were detected during verification to be fixed directly from the console web interface. You can use this convenient feature to solve certain problems without logging in to a different system.
The following list shows some of the problems that ARE can automatically fix:
•Authority: This category includes ownership, primary group, authorization list, and private authority.
•User Profiles: Some, but not all, user profile attributes can be fixed.
•Symbolic Links: If ARE detects that a symbolic link is missing, it can re-create the link.
|
Important: It is important to understand that only certain types of detected problems can be fixed directly from the console.
|
Figure 15-17 shows a summary report in which the “Authority Verifier” plug-in has a fix action available.
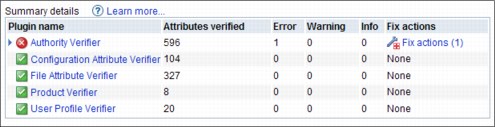
Figure 15-17 Summary report fix action
Clicking the Fix action link opens a new window that summarizes all of the problems that are detected by that plug-in that can be fixed directly from the console. You can select which problems to fix by selecting the check box that precedes each problem description, and then clicking Fix, as shown in Figure 15-18.

Figure 15-18 Fix plug-in problem
The console begins the process of fixing the selected problems on the target system. After the problems are fixed, a second table is displayed that shows the fix results.
Other than the console web user interface, ARE can also fix detected problems using a script. For more information, see the “areFix.sh” script section in the document found at:
15.10.4 Application Runtime Expert requirements
The IBM Application Runtime Expert for i product (5733ARE) requires several IBM i products and PTFs to be installed on the system before you install ARE.
Prerequisite products
Here is the list of required software products on IBM i 7.1:
•5770SS1 option 3 - Extended Base Directory Support
•5770SS1 option 12 - Host Servers
•5770SS1 option 30 - Qshell
•5770SS1 option 33 - PASE
•5761JV1 option 11 - J2SE 6 32 bit
•5770DG1 - IBM HTTP Server for i
PTF requirements
The latest Group PTF level must be installed on the system before you install ARE. For up-to-date PTF requirements, go to:
To benefit from the latest ARE enhancements, you must install the latest PTF. For the latest PTFs, see the ARE support that is found at:
15.10.5 More information
For more information about Application Runtime Expert, see Uncovering Application Runtime Expert, REDP-4805.
15.11 Operably
Operably is a freely available and commercially supported port of the Ruby language. It is a web application development framework (Rails) written in the Ruby language.
This product is available for download from the following website:
PowerRuby does include the native DB2 driver. This means that the use of the MySQL database is not necessary on IBM i. It integrates with XMLSERVICE for access to IBM i programs and objects. For more about XMLSERVICE, see 15.4, “XMLSERVICE for IBM i” on page 594.
To learn more about PowerRuby, see the following website:
..................Content has been hidden....................
You can't read the all page of ebook, please click here login for view all page.
