5
RFID in the Internet of Things
Akaa Agbaeze Eteng,1 Sharul Kamal Abdul Rahim,2 and Chee Yen Leow2
1Department of Electronic and Computer Engineering, University of Port Harcourt, Port Harcourt, Nigeria
2Wireless Communication Centre, Universiti Teknologi Malaysia, Johor, Malaysia
5.1 Introduction
The expansion of the current “internet of computers” to the Internet of Things (IoT) requires an ecosystem characterized by interactions between everyday objects with embedded online intelligence. By implication, such smart objects would be capable of data-driven real-time interventions without human mediation. One of the requirements for this pervasive information acquisition and sharing environment is that objects should be characterized by an innate ability to gather contextual data about their internal or external environments (Roselli et al., 2015). This suggests a need to embed sensors in everyday objects. Furthermore, smart objects should be able to communicate acquired data to other entities. Historically, radio frequency identification (RFID) is one of the earliest technologies whose utility required embedding or placing electronics on an object. Given the fact the RFID is also a communications technology, it is currently touted as a promising technology to be incorporated in smart objects for the IoT (Vermesan and Friess, 2013).
This chapter aims to provide a background to the use of RFID in the IoT. It begins with a brief historical perspective of RFID technology, showing how it is associated with the birth and development of the IoT.
5.2 Historical Perspective
The 1906 demonstration of a 2 kW, 100 Hz alternator by Ernst Alexanderson was an important milestone in the development of wireless communication through continuous wave (CW) radio generation and transmission (Ernst, 1906). Radar systems were one of the early technologies to harness the potentials of CW radio wave transmission, using the reflection of such waves to detect the presence and locations of objects. In 1948, the seminal work by Stockman (Stockman, 1948) was published, which explored the potentials of communication through reflected radio waves. Not long after this, the invention of the transistor and the development of the integrated circuit enabled further explorations into ideas inspired by Stockman's work, thus, birthing RFID.
RFID is a technology that employs transmitted and received radio frequency RF) energy for the automatic identification of objects. In a basic sense, RFID systems comprise of two components, namely, the RFID transponder or tag and the RFID interrogator or reader. The RFID tag is a miniaturized electronic circuit containing data, and is attached to or embedded in the object to be identified. The RFID reader is a relatively larger electronic circuit that reads data wirelessly communicated to it by RFID tags.
One of the earliest RFID applications was in electronic article surveillance (EAS) systems, developed in the 1960s. EAS systems provided an inexpensive and effective antitheft measure. Basically, these systems employed inductive coupling between a resonant reader circuit and a tag. Single-bit tags were placed on pieces of merchandise, and EAS systems could detect either their presence or absence. The 1970s were marked by notable advances in RFID technology as a consequence of research at institutions such as Los Alamos Scientific Laboratory in the United States and the Microwave Institute Foundation in Sweden (Landt, 2005). Backscatter RFID systems were developed for operation in the ultrahigh frequency (UHF) spectrum, enabling the deployment of RFID systems at greater ranges than were hitherto possible (Koelle et al., 1975). Also, development efforts were directed at miniaturization of RFID tags and circuitry, and improvements in functionality.
While the 1970s were characterized by RFID research and development, the 1980s were the decade of commercialization of the technology. Short-range RFID technologies were adopted in Europe for livestock tracking, as well as in business and industrial applications. In the United States, however, access control and transportation were the major RFID applications (Landt, 2005). Electronic toll collection was also fast becoming an important niche application for RFID. It is important to note the role played by the personal computers in the development of RFID within this era. The availability of personal computers meant that the data about the presence and location of objects could be transmitted to computing systems for storage and further processing. Consequently, a third component of RFID systems—the middleware—became the focus of considerable research attention.
The decade of the 1990s saw a further consolidation in the use of RFID in transportation management, inventory management, supply chain management, and access control. New applications in health care management were also being developed. Many companies all over the world became actively involved in the development of RFID solutions. This led to the need for the development of standards to ensure interoperability between RFID hardware developed by the different vendors. The US-based Uniform Code Council (UCC) commenced discussions with a similar standards organization, the European Article Number (EAN) International, on global standardization. The Auto-ID Centre, founded in 1999, developed the Electronic Product Code (EPC), with support from the UCC, to serve as a universal RFID system. In 2003, the Auto-ID Centre morphed into two separate entities: the Auto-ID Labs and EPCglobal. While the Auto-ID labs are involved in research activities, with laboratories in seven countries, the EPCglobal is involved in EPC standardization activities. In 2005, EAN International was reorganized and its name changed to GS1 (GS1, 2013). A direct consequence of these standardization efforts was the emergence of multiuse RFID tags, which could be used across different business segments. For instance, a single tag could be used to gain access to an office building, and still serve as an e-wallet for electronic toll collection.
The late 1990s were also characterized by a rapid growth in internet usage. Personal computers were becoming cheaper and wireless connectivity was more readily available. The global surge in internet use, which has continued till present, meant that enormous amounts of data were being continuously generated and communicated through computer networks. Initially, the bulk of data input to computer systems, and hence the Internet, came through human interventions. Especially in industry and business applications, such data often provided qualitative or quantitative descriptions of physical processes and variables. Developers in the RFID community, consequently, began toying with the idea of data input to the Internet coming directly from the objects exposed to the physical processes and variables themselves, without human intermediaries. The idea was that RFID could be adopted to provide a means for computers to gather information about the physical world for themselves. This led to the coinage of the term, “Internet of Things” (IoT), an ecosystem in which data input to the Internet came directly from “things,” and not human beings (Ashton, 2009).Thus, RFID has been associated with the IoT, right from the latter's conceptual origins.
5.3 RFID and the Internet of Things
The specific role of RFID in the IoT can be observed from noting some fundamental components of the IoT, namely, sensing, communication, services, semantics, computation, and identification (Zhu et al., 2015). While sensing deals with data collection by objects, communication technologies enable connections between these heterogeneous objects for specific services. Such services may include information aggregation, real-time decision-making, or ensuring seamless on-demand access to data. The semantic component of the IoT deals with the intelligent extraction of knowledge from collected data to provide required services. Computation, on the other hand, refers to the hardware and software components that process collected data in real time. Finally, the ability to uniquely identify objects enables services to be matched with demand in the physical world. Automatic identification provided by RFID is currently the most widely used functionality to provide a wide range of services. RFID inventory and supply chain management solutions are extensively deployed in many organizations globally.
As a means of data acquisition, RFID technology can provide the link between the physical world and the virtual elements of the IoT (see Figure 5.1). This potential has been demonstrated by researchers at the University of Washington in a building-scale microcosm of the IoT, which they called the “RFID Ecosystem” (Welbourne et al., 2009). Multiple RFID readers were positioned in an 8000 m2 building, while tracking tags were attached to persons and personal objects. Using various tools, low-level RFID data was transformed into higher level contextual information about the tracked persons and objects.

Figure 5.1 Data acquisition for the IoT through RFID.
5.3.1 Object Identification using RFID
Readers and tags are the basic hardware used in RFID. Readers and tags are equipped with antennas for communication. In addition, a typical tag contains a chip that stores a unique identification number (ID) (Liu et al., 2008). However, chipless tags are also available, where the tag ID is encoded onto the physical structure of the tag. Normally, the RFID tag is embedded in or attached to an object to be tracked, so that the tag ID is associated with the object. RFID tags are classified as active, semipassive, or passive, depending on how they are powered. Generally speaking, active and semipassive tags are battery powered, while passive RFID tags do not have independent power sources.
In a conventional RFID interaction, a reader interrogates the tag to obtain its unique ID, which in effect identifies the associated object. Active tags are able to transmit their unique IDs through electromagnetic fields in response to reader electromagnetic transmissions. Semipassive and passive tags, however, are unable to generate their own electromagnetic fields for transmitting data. These tags rather communicate with readers by modulating the magnetic or electromagnetic fields transmitted by readers. Magnetic field-based tag-reader interactions are facilitated by load modulation. Here, a tag changes its impedance in step with the ID data to be transmitted. This variation in impedance is sensed by the reader, and interpreted accordingly. For electromagnetic systems, passive and semipassive tags communicate with the reader using backscatter modulation. In this case, the reader's electromagnetic transmission is reflected back from the tag. This is achieved by intentionally mismatching the tag antennas' input impedance in step with the tag ID data. Thus, tag ID data is encoded in the amplitude and phase of the reflected electromagnetic field and is interpreted accordingly by the reader.
RFID object identification enables multiple applications spanning from access control to RFID-enabled passports (Bogari et al., 2012). This functionality also has practical industrial relevance. Production processes are usually monitored by registering manufactured items at certain checkpoints in the production chain. With RFID technology, this registration process can be automated by equipping such items with tags. Additional scan points can be introduced in the production process, even in hostile environments, thereby enabling closer monitoring of production processes (Evdokimov et al., 2010). Extended further, these same tags can enable the identification and tracking of each manufactured item, right through the supply chain, and possibly throughout their operational life with the final consumer.
The benefits of incorporating RFID technology into the operation of an organization are well known. However, the potentials of the technology are significantly magnified when multiple parties can access and use data acquired through RFID. For example, the efficiency and transparency of supply chains is greatly improved with the IoT serving as a global information service architecture for RFID-tagged items (Evdokimov et al., 2010). For instance, RFID has been employed by an industrial laundry service in the United Kingdom as part of its IoT infrastructure to manage its supply chain (Palmer, 2017). Inconspicuous RFID tags sewn into laundry are connected to an internet-based network, which enables effective management of shipment cycles, consisting of up to a million items daily, across multiple locations. Also, IoT systems based on RFID item tagging are currently being developed to minimize baggage mishandling incidents at airports in compliance with International Air Transport Association (IATA) resolutions (Strukhoff and Yaroshko, 2017). It should be noted that extending the basic identification functionality of RFID tags to include data about the environments in which they are deployed significantly enriches the content of RFID-acquired data, and enhances the utility of RFID item tagging. Environmental sensing, therefore, is potentially a key application of RFID in the IoT (Want, 2004).
5.3.2 RFID Sensors
RFID tags can be enhanced to sense physical or chemical variables in an environment. Some examples of common physical parameters RFID sensors have been developed to sense include temperature (Bhattacharyya et al., 2010; Brenk et al., 2011; Trevisan and Costanzo, 2016), humidity (Nair et al., 2013), pressure (Beriain et al., 2014), light (Colella et al., 2015a), and movement. There are various real-world applications for these RFID sensor enhancements. For example, RFID-based temperature sensors can be used in a cold supply chain to monitor the temperature of frozen goods, while still providing basic article surveillance. Also, RFID-based strain sensors find ready application in structural health monitoring. RFID chemical sensors, on the other hand, can be used in applications such as determining the presence of a potentially harmful gas (Occhiuzzi et al., 2011; Shrestha et al., 2009), and measuring the pH level of bioprocess components (Potyrailo and Wortley, 2011). In health care, RFID chemical sensors can be used to measure glucose levels (Tankiewicz et al., 2013). Motion sensors depend on sensing the acceleration of a sensor from its rest position. Wearable RFID motion sensors have been developed, which are able to track the movement of the human wearer and find medical applications in patient management (Hong et al., 2008; Occhiuzzi et al., 2010; Occhiuzzi and Marrocco, 2010). A key advantage of RFID-based sensing over other wireless sensor approaches is that, with passive tags, wireless sensing can be achieved using battery-free implementations, making them ideal for embedded IoT applications where sensors cannot be periodically retrieved for battery replacement.
Sensing functionality may be incorporated in an RFID tag by exploiting some properties of the tag antenna or chip, such as antenna directivity or impedance. This is possible because any variation in the environment within the near-field region of a tag will alter the tag's electrical properties (Tedjini et al., 2016). On the other hand, it is possible for external sensors to be connected to the RFID tag circuitry. For instance, a passive surface acoustic wave (SAW)-based RFID tag typically comprises of a coding area and an interdigital transducer (IDT) coupled to an antenna. The IDT converts received reader signals into a surface acoustic wave, which is coded according to the configuration of the coding area, and reflected back after reconversion to an electrical signal by the IDT. Directly connecting a sensor as an external load to the IDT alters the tag reflection characteristics according to the measuring signal of the sensor, so that the signal reflected back to the reader contains sensor data. With CMOS RFID tag implementations, however, it is necessary to design interface circuitry in order to connect the external sensor to tag electronics (Ussmueller et al., 2014). The inclusion of external sensor modules invariably increases the complexity and energy demand of RFID tag implementations. Innovative schemes need to be introduced to simplify the tag-sensor operation, as well as minimize energy consumption. For example, the read-out of a resistive temperature sensor can be achieved by tracking the nonlinear characteristic of the tag rectifier as it is loaded by the sensor (Trevisan and Costanzo, 2014). This approach avoids the need for embedding additional active electronics on the sensor for its read-out.
Multisensor RFID tag platforms with additional computational abilities have also been developed. In a recent project, near-field communication (NFC) has been combined with the wireless identification and sensing platform (WISP) to provide a near-field RFID sensing platform (Zhao et al., 2015). This programmable sensing and computing platform can be interrogated by RFID readers and NFC-enabled smartphones. Another example of a multisensor RFID tag platform is the RFID augmented module for smart environmental sensing (RAMSES) (De Donno et al., 2014). RAMSES harvests radio frequency energy to energize circuits that perform environmental sensing, computation, and data communication. RAMSES presents an improvement over the WISP (Sample et al., 2008), which was one of the earliest UHF-RFID multisensor platforms. More recently, the self-powered augmented RFID Tag for autonomous computing and ubiquitous sensing (SPARTACUS) has been developed (Colella et al., 2015b), which combines sensing, computation, and communication functionalities.
5.3.3 RFID Sensor Localization
Information mined about objects and their environments using RFID-based sensors is only useful in the IoT if the locations of sensed processes and events are known. Consequently, the real-time determination of the position of the IoT object is of utmost importance. In supply chain management, location is the primary information required about the tracked assets. Generally, RFID localization technologies can be categorized as tag based, reader based, transceiver-free, or hybrid approaches (Ni et al., 2011). In a tag-based approach, the tracked item is required to carry a tag that periodically transmits beacon signals. In reader-based schemes, readers are attached to tracked objects to gather location information from nearby tags. In transceiver-free approaches, object tracking is achieved without the need for reader or tag in the tracked item. They are rather based on observations of disturbances to wireless signals by movement of the tracked object. One of the hybrid RFID localization techniques involves utilizing the richer bidirectional connectivity provided by traditional wireless sensor networks (WSN) to augment the RFID localization implementation. An example of this approach is COCKTAIL (Zhang et al., 2010), which is implemented by combining a very sparse deployment of WSN motes with a denser deployment of RFID tags over an area. To obtain the spatial position of an intended tag, the WSN motes first segregate a cluster of reference RFID tags closest to the target tag. The final localization of the target tag is then performed by this cluster of reference tags.
5.3.4 Connecting RFID Sensors to the Internet
The incorporation of sensor functionalities into RFID implementations opens up opportunities for pervasive low-cost data gathering and processing. RFID sensors could be interconnected in networks to ensure that sensed information can be extracted over long distances. This has significant implications on the availability of social services and quality of life in general. For example, in virtual health care, patients can be under medical observation irrespective of their physical locations. Ultimately, RFID-acquired data should be available anywhere and anytime. This vision implies IoT implementation on a global scale, as opposed to localized realizations. One way this goal can be achieved is through the integration of RFID sensors with WSN platforms. The argument for this integration is predicated on appropriating the benefits of WSNs, such as increased range through the use of multihop links, non-line-of-sight operability, reliable communications even with node failures, and so on.
Some network topologies for integrating RFID and WSN platforms include the agent network topology, reader-as-sensor topology, and the tag-as-sensor topology (Yang and Yang, 2007). As illustrated in Figure 5.2, the agent network topology is one in which the RFID links and WSN networks logically operate at the same system layer, but are not directly connected to each other. An agent network rather operates as a backbone, connecting both networks to central servers. In the reader-as-sensor topology, the RFID reader is at the same system layer as WSN motes. Consequently, the sensor gateway device linking the WSN motes to a central server also acts as the gateway device connecting the readers to the central server. All RFID tag information sent to the RFID reader is sent to the central server through the sensor gateway. Conceptually, the sensor gateway device treats all incoming data as sensor inputs, irrespective of whether they were sent by WSN motes or RFID readers. On the other hand, the tag-as-sensor topology considers RFID tags and WSN sensors as belonging to the same system layer. Above this layer is the layer in which RFID readers and sensor gateways operate as combined gateway devices, linking the tags and motes to central servers.
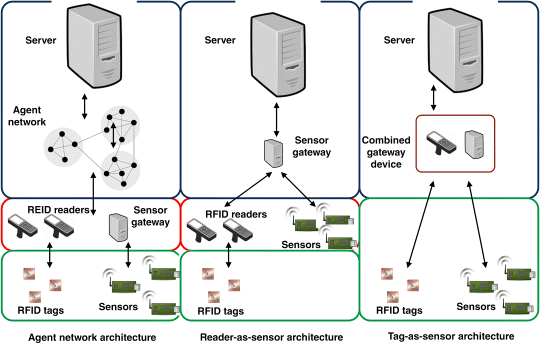
Figure 5.2 Network topologies for linking RFID sensors to the Internet.
Alternatively, WSN nodes can be utilized as the link between RFID sensors and internet gateways. In this role, WSN nodes act as data routers that relay sensed information emanating from RFID sensors through multihop links to gateways. In this scheme, RFID readers are not required, since RFID tags communicate directly with WSN sensors. Consequently, RFID sensors can be viewed as the lowest-level network devices in the hierarchy, as shown in Figure 5.3. Reasons for the elimination of RFID readers from the scheme include the fact that they are comparatively more expensive and bulkier than WSN sensors (Lakafosis et al., 2014).
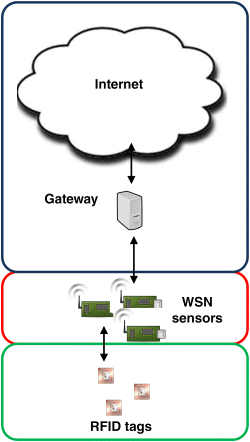
Figure 5.3 WSN sensors as data routers for RFID tags.
Having RFID tags communicate directly with WSN sensors requires a protocol to handle communications between the devices. This implies that signal transmissions from tags to sensors have to occur at an agreed frequency and modulation scheme, and with proper data encapsulation. Using a simple proprietary protocol, this concept has been demonstrated in a prototype solar-powered UHF tag, which communicates with WSN nodes in a localization application (Lakafosis et al., 2010). Connecting such RFID–WSN IoT realizations to the internet, however, requires a two-way translation of addresses and commands at the internet gateway.
In order to realize full intrinsic internet capabilities, smart devices need to provide some form of support for internet integration. The 6LowPAN protocol enables the compression of IPv6 addresses into a few bytes, thereby enabling native support of the IPv6 protocol on a resource-constrained device. An example of this approach is realized in an IPv6-enabled shoe-mounted sensor platform, which is developed for health monitoring (Mariotti et al., 2013). By enabling IPv6 support, the shoe-mounted sensor is able to connect to any existing IP network infrastructure without translation gateways or proxies, and still allow for mesh routing within Wireless Personal Area Network (WPAN) domains. (Doraswamy and Harkins, 2003).
5.4 Emergent Issues
The incorporation of RFID in the IoT no doubt provides numerous novel opportunities. However, these prospects bring along with them several technical challenges, especially with respect to new security vulnerabilities. Each connected IoT end node – RFID devices, WSN motes, sensor gateways, and so on – is a potential security loophole in an IoT infrastructure. The core IoT security issues border on data confidentiality, privacy, and trust (Li et al., 2016).
In the development of standards for RFID, security features have been introduced to address data confidentiality and reader-tag authentication. Methods to ensure the data confidentiality in RFID schemes include the use of signal interference, antenna energy analysis, encryption, among others (Jing et al., 2014). Related to data confidentiality is the issue of location confidentiality, where it is necessary to prevent unauthorized tracking of the location of a tag. Reader-tag authentication, on the other hand, is an issue of trust management. Given the limited resources of RFID tags, it is necessary that lightweight trust management algorithms are developed to ensure data and location privacy (Jing et al., 2014).
WSN implementations are also susceptible to security threats bordering on privacy, authentication, and availability. Unlike RFID systems, the threats to WSN privacy may be internal, that is, an entity acquiring more information than it should (Shah et al., 2016). Furthermore, it is necessary to guard against fake network nodes, fake routes, and fake locations. Jamming signals are one of the most prevalent attacks on the availability of a WSN network.
The integration of RFID and WSNs for the realization of the IoT extends the security challenges of both technologies. This is more especially so given the fact that such integrated networks deal with heterogeneous data. Privacy, data confidentiality, and trust must be ensured throughout the integrated network. End-to-end communication between the multiprotocol devices in such integrated networks must be secure, while the authenticity and integrity of these devices must be assured.
The low cost of RFID sensor-tag implementation provides an impetus for the massive deployment of these devices in various sensing environments. However, the question arises as to the means for preventing these devices from becoming environmental pollutants. In order to address this issue, deployed RFID devices can be categorized as being either locatable or nonlocatable (Roselli et al., 2015). Locatable devices should be recyclable at the end of their operational lives. Nonlocatable devices, which cannot be recovered once dispersed in the environment, have to be implemented using materials that biodegrade soon after the expiration of the operational life of the devices. Consequently, constraints of eco-friendliness must apply to RFID devices in the IoT, namely, recyclability of locatable device and biodegradability of nonlocatable devices. Currently, there is considerable interest in the use of organic materials for the implementation of RFID hardware. Some examples include RFID tags built using organic transistors (Cantatore et al., 2007), organic frequency doublers for chipless RFID tags (Virili et al., 2014), the use of microfluidics in organic UHF-RFID antennas (López et al., 2013), textile tags (Manzari et al., 2012), and inkjet printed antennas on paper substrates (Jankowski-Mihułowicz, 2015).
Sensors will be more increasingly deployed in scenarios for which alternative powering solutions must be sought. Indeed, with sensor deployments running into billions of devices, it is virtually impossible to connect all these devices to the grid. Especially for nonlocatable sensor deployments, battery-powered solutions may not be the best option, as these devices cannot be retrieved when the batteries run down. This is one major advantage passive RFID has over other proposals for IoT sensor implementations, since the power for tag operation is derived from the reader's transmission. However, the incorporation of sensor electronics increases the energy demand of such tags. UHF-RFID readers are based on RF broadcast methods, where the power density of the radiation from the reader antenna obeys an inverse-square law. The power available at the tag is, therefore, considerably lower than what was transmitted. Although inductive RFID links can be perceived as wireless power transfer links, conventionally, these links trade power efficiency for operating distance (Sample et al., 2011). Consequently, it is imperative for RFID links to find an optimal trade-off between operational range and power efficiency to support the expanded functionality.
5.5 Conclusion
One of the key features of the IoT is the embedding of intelligence within objects, enabling them to acquire contextual data about their environments, and transmit such data as required without human intervention. The low-cost, low-complexity, and automatic identification features of RFID technology make it attractive as a means of acquiring data in the IoT. This chapter has presented a brief overview of RFID technology, and highlighted its data acquisition role in the IoT. Although, presently its most widespread application is in its capacity as a replacement to barcodes, environmental sensing will likely be the most important application of RFID in the IoT. The integration of RFID with WSN is an important step toward the realization of ubiquitous sensing, as it provides a means to connect RFID infrastructure to the Internet. Full internet integration can be provided through a linkage between RFID tags and IPv6 addressing. However, these extensions of RFID functionality present new challenges in security, eco-friendliness, and energy consumption, which must be tackled in order to realize the vision of the IoT on a global scale.
References
- Ashton, K. (2009) That “Internet of Things” thing. RFID Journal, Available at http://www.rfidjournal.com/articles/view?4986
- Beriain, A., Berenguer, R., Jimenez-Irastorza, A., Montiel-Nelson, J., Sosa, J., and Pulido, R. (2014) Full passive RFID pressure sensor with a low power and low voltage time to digital interface. Design of Circuits and Integrated Systems Conference, pp. 1–6.
- Bhattacharyya, R., Leo, C. D., Floerkemeier, C., Sarma, S., and Anand, L. (2010) RFID tag antenna based temperature sensing using shape memory polymer actuation. Sensors, 2363–2368.
- Bogari, E. A., Zavarsky, P., Lindskog, D., and Ruhl, R. (2012) An investigative analysis of the security weaknesses in the evolution of RFID enabled passport. International Journal of Internet Technology and Secured Transactions, 4(4), 290. Available at http://doi.org/10.1504/IJITST.2012.054060
- Brenk, D., Essel, J., Heidrich, J., Agethen, R., Kissinger, D., Hofer, G., Holweg, G., Fischer, G., and Weigel, R. (2011) Energy-efficient wireless sensing using a generic ADC sensor interface within a passive multi-standard RFID transponder. Sensors Journal, IEEE, 11(11), 2698–2710.
- Cantatore, E., Geuns, T. C. T., Gelinck, G. H., Van Veenendaal, E., Gruijthuijsen, A. F. A., Schrijnemakers, L., et al. (2007) A 13. 56-MHz RFID System Based on Organic Transponders. IEEE Journal of Solid-State Circuits, 42(1), 84–92.
- Colella, R., Catarinucci, L., and Tarricone, L. (2015) EM design of a passive RFID-based device with sensing and reasoning capabilities. 2015 IEEE 15th Mediterranean Microwave Symposium (MMS) pp. 1–4. Available at http://doi.org/10.1109/MMS.2015.7375387
- Colella, R., Tarricone, L., and Catarinucci, L. (2015) SPARTACUS: self-powered augmented RFID tag for autonomous computing and ubiquitous sensing. IEEE Transactions on Antennas and Propagation, 63(5), 2272–2281. Available at http://doi.org/10.1109/TAP.2015.2407908
- De Donno, D., Catarinucci, L., and Tarricone, L. (2014) RAMSES: RFID augmented module for smart environmental sensing. IEEE Transactions on Instrumentation and Measurement, 63(7), 1701–1708. Available at http://doi.org/10.1109/TIM.2014.2298692
- Doraswamy, N. and Harkins, D. (2003) IPSec: The New Security Standard for the Internet, Intranets, and Virtual Private Networks, Prentice Hall.
- Ernst, A. (1906) Alternating Current Generator. U.S. Patent and Trademark Office.
- Evdokimov, S., Fabian, B., Gunther, O., Ivantysynova, L., and Ziekow, H. (2010) RFID and the Internet of Things: technology, applications, and security challenges. Foundations and Trends® in Technology, Information and Operations Management, 4(2), 105–185. Available at http://doi.org/10.1561/0200000020
- GS1. (2013) Celebrating our 40th anniversary: a history of standards. Available at http://40.gs1.org/historic-timeline.php
- Hong, Y.-J., Kim, I.-J., Ahn, S. C., and Kim, H.-G. (2008) Activity recognition using wearable sensors for elder care. 2008 Second International Conference on Future Generation Communication and Networking pp. 302–305. IEEE. Available at http://doi.org/10.1109/FGCN.2008.165
- Jankowski-Mihułowicz, P. (2015) Flexible antenna design for semi-passive HF RFID transponder in ink-jet technology. Przegląd Elektrotechniczny, 1(4), 3–7. Available at http://doi.org/10.15199/48.2015.04.01
- Jing, Q., Vasilakos, A. V., Wan, J., Lu, J., and Qiu, D. (2014) Security of the Internet of Things: perspectives and challenges. Wireless Networks, 20(8), 2481–2501. Available at http://doi.org/10.1007/s11276-014-0761-7
- Koelle, A. R., Depp, S. W., and Freyman, R. W. (1975) Short-range radio-telemetry for electronic identification, using modulated RF backscatter. Proceedings of the IEEE, 63(8), 1260–1261. Available at http://doi.org/10.1109/PROC.1975.9928
- Lakafosis, V., Vyas, R., Mariotti, C., Le, T., and Tentzeris, M. M. (2014) Integrating tiny RFID- and NFC-based sensors with the Internet, in Roselli, L. (ed.), Green RFID Systems, Cambridge University Press, pp. 152–175.
- Lakafosis, V., Vyas, R., and Tentzeris, M. M. (2010) A localization and position tracking solution utilizing solar-powered RFID tags. Proceedings of the Fourth European Conference on Antennas and Propagation (EuCAP) pp. 1–4.
- Landt, J. (2005) The history of RFID. IEEE Potentials, 24(4), 8–11. Available at http://doi.org/10.1109/MP.2005.1549751
- Li, S., Tryfonas, T., and Li, H. (2016) The Internet of Things: a security point of view. Internet Research, 26(2), 337–359. Available at http://doi.org/10.1108/IntR-07-2014-0173
- Liu, H., Bolic, M., Nayak, A., and Stojmenović, I. (2008) Taxonomy and challenges of the integration of RFID and wireless sensor networks. IEEE Network, 22(6), 26–32. Available at http://doi.org/10.1109/MNET.2008.4694171
- López, A. L. V., Giles, D. B., Khan, W. T., Chlieh, O., and Ponchak, G. E. (2013) Microfluidic channel on organic substrates as size reducing technique for 915 MHz antenna designs, Microwave Conference Proceedings (APMC), 2013 Asia-Pacific, pp. 3–6.
- Manzari, S., Occhiuzzi, C., and Marrocco, G. (2012) Feasibility of body-centric systems using passive textile RFID tags. IEEE Antennas and Propagation Magazine, 54(4), 49–62. Available at http://doi.org/10.1109/MAP.2012.6309156
- Mariotti, C., Lakafosis, V., Tentzeris, M. M., and Roselli, L. (2013) An IPv6-enabled wireless shoe-mounted platform for health-monitoring. WiSNet 2013 - Proceedings: 2013 IEEE Topical Conference on Wireless Sensors and Sensor Networks - 2013 IEEE Radio and Wireless Week, RWW 2013, 46–48. Available at http://doi.org/10.1109/WiSNet.2013.6488629
- Nair, R., Perret, E., Tedjini, S., and Baron, T. (2013) A group delay-based chipless RFID humidity tag sensor using silicon nanowires. Antennas and Wireless Propagation Letters, IEEE, 12, 729–732.
- Ni, L. M., Zhang, D., and Souryal, M. R. (2011) RFID-based localization and tracking technologies. IEEE Wireless Communications, 18(2), 45–51. Available at http://doi.org/10.1109/MWC.2011.5751295
- Occhiuzzi, C., Cippitelli, S., and Marrocco, G. (2010) Modeling, design and experimentation of wearable RFID sensor tag. IEEE Transactions on Antennas and Propagation, 58(8), 2490–2498. Available at http://doi.org/10.1109/TAP.2010.2050435
- Occhiuzzi, C. and Marrocco, G. (2010) The RFID technology for neurosciences: feasibility of limbs' monitoring in sleep diseases. IEEE Transactions on Information Technology in Biomedicine, 14(1), 37–43. Available at http://doi.org/10.1109/TITB.2009.2028081
- Occhiuzzi, C., Rida, A., Marrocco, G., and Tentzeris, M. (2011) RFID passive gas sensor integrating carbon nanotubes. IEEE Transactions on Microwave Theory and Techniques, 59(10), 2674–2684.
- Palmer, D. (2017) The Internet of Laundry: How RFID tags in your sheets help you get a better night's sleep IT director Duncan Macmillan explains how RFID chips and scanners are helping to manage over a million pieces of linen a day for Berendsen. Available at http://www.zdnet.com/article/the-internet-of-laundry-how-rfid-tags-in-your-sheets-help-you-get-a-better-nights-sleep/
- Potyrailo, R. A. and Wortley, T. (2011) Passive multivariable RFID pH sensors. 2011 IEEE International Conference on RFID-Technologies and Applications, pp. 533–536. Available at http://doi.org/10.1109/RFID-TA.2011.6068596
- Roselli, L., Mariotti, C., Mezzanotte, P., Alimenti, F., Orecchini, G., Virili, M., and Carvalho, N. B. (2015) Review of the present technologies concurrently contributing to the implementation of the Internet of Things (IoT) paradigm: RFID, Green Electronics, WPT and Energy Harvesting. 2015 IEEE Topical Conference on Wireless Sensors and Sensor Networks, WiSNet 2015, 1–3. Available at http://doi.org/10.1109/WISNET.2015.7127402
- Sample, A. P., Meyer, D. A., and Smith, J. R. (2011) Analysis, experimental results, and range adaptation of magnetically coupled resonators for wireless power transfer. IEEE Transactions on Industrial Electronics, 58(2), 544–554. Available at http://doi.org/10.1109/TIE.2010.2046002
- Sample, A. P., Yeager, D. J., Powledge, P. S., Mamishev, A. V., and Smith, J. R. (2008) Design of an RFID-based battery-free programmable sensing platform. IEEE Transactions on Instrumentation and Measurement, 57(11), 2608–2615.
- Shah, A., Pal, A., and Acharya, H. B. (2016) The Internet of Things: Perspectives on Security from RFID and WSN. Available at http://arxiv.org/abs/1604.00389
- Shrestha, S., Balachandran, M., Agarwal, M., Phoha, V. V., and Varahramyan, K. (2009) A chipless RFID sensor system for cyber centric monitoring applications. IEEE Transactions on Microwave Theory and Techniques, 57(5), 1303–1309. Available at http://doi.org/10.1109/TMTT.2009.2017298
- Stockman, H. (1948) Communication by Means of Reflected Power. Proceedings of the IRE, 36(10), 1196–1204. Available at http://doi.org/10.1109/JRPROC.1948.226245
- Strukhoff, R. and Yaroshko, S. (2017) IoT for Airlines: Smart Baggage Tracking with RFID Tags and Cloud Foundry. Available at https://www.altoros.com/blog/iot-for-airlines-smart-baggage-tracking-with-rfid-tags-and-cloud-foundry/. (accessed June 13, 2017)
- Tankiewicz, S., Schaefer, J., and DeHennis, A. (2013) A co-planar, near field communication telemetry link for a fully-implantable glucose sensor using high permeability ferrites. 2013 IEEE Sensors pp. 1–4 Available at http://doi.org/10.1109/ICSENS.2013.6688255
- Tedjini, S., Zurita, M., Freire, R. C. S., Duroc, Y., Federal, U., Grande, C., and Lyon, U. C. (2016) Augmented RFID Tags, 67–70.
- Trevisan, R. and Costanzo, A. (2014) Exploitation of passive RFID technology for wireless read-out of temperature sensors. 2014 IEEE RFID Technology and Applications Conference (RFID-TA) pp. 150–154 Available at http://doi.org/10.1109/RFID-TA.2014.6934218
- Trevisan, R. and Costanzo, A. (2016) A UHF near-field link for passive sensing in industrial wireless power transfer systems. IEEE Transactions on Microwave Theory and Techniques, 64(5), 1634–1643. Available at http://doi.org/10.1109/TMTT.2016.2544317
- Ussmueller, T., Hagelauer, A., and Weigel, R. (2014) Technologies for RFID sensors and sensor Tags, in Roselli, L. (ed.), Green RFID Systems, Cambridge University Press, pp. 76–115.
- Vermesan, O. and Friess, P. (eds.) (2013) Internet of Things: Converging Technologies for Smart Environments and Integrated Ecosystems, River Publishers.
- Virili, M., Casula, G., Mariotti, C., Orecchini, G., Alimenti, F., Cosseddu, P., et al. (2014) 7.5–15 MHz organic frequency doubler made with pentacene-based diode and paper substrate. Available at http://doi.org/10.1109/MWSYM.2014.6848395
- Want, R. (2004) Enabling ubiquitous sensing with RFID. Computer, 37(4), 84–86. Available at http://doi.org/10.1109/MC.2004.1297315
- Welbourne, E., Battle, L., Cole, G., Gould, K., Rector, K., Raymer, S., and Balazinska, M. (2009) Building the Internet of Things using RFID. Internet Computing, IEEE, 13(3), 48–55. Available at http://doi.org/10.1109/MIC.2009.52
- Yang, H. Y. and Yang, S.-H. (2007) RFID sensor network – network architectures to integrate RFID, sensor and WSN. Measurement and Control, 40(2), 56–59.
- Zhang, D., Yang, Y., Cheng, D., Liu, S., and Ni, L. M. (2010) COCKTAIL: An RF-based hybrid approach for indoor localization. 2010 IEEE International Conference on Communications, pp. 1–5. Available at http://doi.org/10.1109/ICC.2010.5502137
- Zhao, Y., Smith, J. R., and Sample, A. (2015) NFC-WISP: A sensing and computationally enhanced near-field RFID platform. 2015 IEEE International Conference on RFID (RFID), 174–181. Available at http://doi.org/10.1109/RFID.2015.7113089
- Zhu, C., Leung, V. C. M., Shu, L., and Ngai, E. C. H. (2015) Green Internet of Things for smart world. IEEE Access, 3(January), 2151–2162. Available at http://doi.org/10.1109/ACCESS.2015.2497312
