10
The Internet of Things and IT Auditing
John Shu,1 Jason M. Rosenberg,2 Shambhu Upadhyaya,2 and Hejamadi Raghav Rao1
1Department of Information Systems and Cyber Security, University of Texas San Antonio, San Antonio, TX, USA
2University at Buffalo School of Management, The State University of New York at Buffalo, Buffalo, NY, USA
10.1 Introduction
The growth and proliferation of Internet and Communication Technologies (ICTs) within the last decade has resulted in a giant web of interconnected devices. Gartner research currently estimates that there are about 3 billion connected devices in consumer home environments. It is, however, predicted that by the year 2020 we would have nearly 21 billion devices connected and talking to each other (Boorstin, 2016). This growth is not limited to the traditional consumer environments but also comprises the millions of devices that are continually being installed and deployed industrially in facilities such as plants, warehouses. Currently, there are huge cost-saving advantages being realized by the prowess of IoT in industries such as health care, transportation, and retail and logistics in almost every facet of their operation. However, as with the adoption of any burgeoning technology, IoT comes with a gamut of issues such as acceptance, usability, security, among which security usually turns out to be one of the most critical. This is coupled with the fact that on average an individual can be associated with up to three different IoT-related devices, which increase the chances and opportunities for malicious individuals to gain illegal access. A report published by the Gartner Research Group demonstrated an increase of over 300 million dollar in security-related spending on IoT worldwide between 2014 and 2018 as seen in Figure 10.1 (Van der Meulen, 2017)
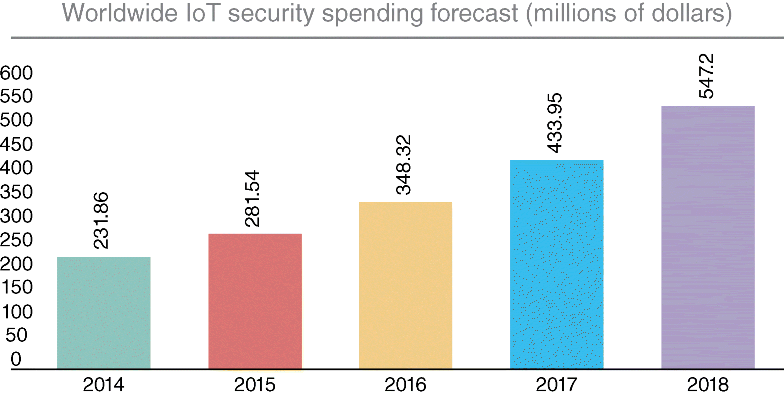
Figure 10.1 Worldwide IoT security spending forecast (in millions of dollars).
This tremendous increase in the spending forecast for the security of IoT is indicative of the potential vulnerability associated with these technologies. Hence, this calls for detailed policies on the use of these technologies in organizations, but more importantly, the implementation of comprehensive routine audit procedures. The implementation of such routine audits will ensure a consistently robust and resilient infrastructure regardless of the changes/upgrades in hardware, software, or patches. This chapter, therefore, discusses and elaborates on the somewhat novel concept of audits in relation to IoT.
10.2 Risks Associated with IoT
In their definition, the International Telecommunication Union (ITU) described IoT as (i) a global infrastructure for Information Systems in the Society that (ii) enables and facilitates advanced services by way of physical and virtual objects interconnection (iii) empowered by existing and evolving interoperable information and communication technologies. (Wortmann et al., 2015). The second point in this definition presents a very interesting and unique scenario hitherto not observed—the concept of interconnecting physical and virtual objects in an interoperable fashion. This essentially adds a layer of interconnectivity that was practically nonexistent as objects, which have traditionally not been considered online capable devices are now obtaining Internet capabilities. Objects such as fridges, thermostats, health devices, and a number of previously Internet technology incapable objects are coming online. The issue with the rapid pace with which these devices are coming alive on the Internet is the lack of security built into the typical IoT devices. Security is sometimes an afterthought once the original communicability objective of the device is attained. HP published an Internet of Things Risk report based on a security analysis of IoT devices in 2015 with some intriguing statistics as seen in Figure 10.2. The study revealed that on the lists of commonly used IoT devices, more than 70% of these devices are highly vulnerable to attacks not being properly secured. A significant number of these devices use unencrypted network services whose connections to the Cloud and associated apps are exposed. This makes them vulnerable to simple exploits such as man in the middle and the likes of it. HP also found that 80% of passwords used in these devices were either commonly used passwords or the same password repeated over multiple devices and accounts creating more opportunities for attackers among other things (see Figure 10.2) (HP News, 2016). These vulnerabilities are a serious concern in any business model where these devices are used and may have serious repercussions if not addressed in a timely manner.
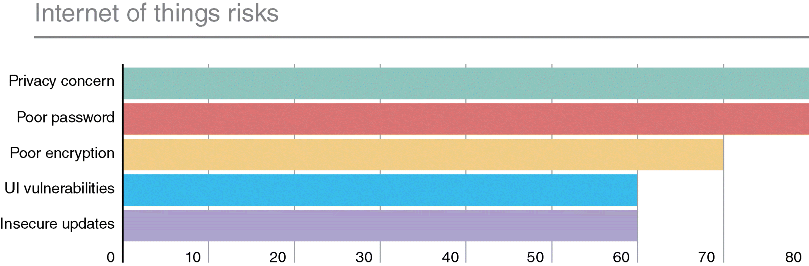
Figure 10.2 Internet of Things risks.
This all goes to show that while the IoT carries a lot of potential and possibilities, there are crucial issues related to risks, threats, security, and auditing that have to be taken into consideration. Here, discussed further are some of the risks that arise and, therefore, need to be considered when considering IoT and auditing.
10.2.1 Privacy
The number one issue in dealing with the IoT is privacy. This is the case because these sensors and devices have come into very close proximity of our lives and our personal spaces like homes, cars, and even our bodies, and hence, maintaining privacy with all the data collected becomes a paramount issue. A vivid example will be that of the hacking of a baby monitor that took place in April of 2014. An intruder was able to gain access to a baby monitor remotely while the family was asleep. He was actually able to swivel the camera to any direction he wanted and was also heard screaming at the baby and yelling very expletive words (Wagstaff, 2014).
This is a glaring example of a traumatizing violation of the privacy of this family. In an organizational setting, the intruder could have used this avenue to monitor the organization. Information such as who is the last to leave or the first to come into the office and the hours spent at the facility could be easily obtained. Not only that but they might be able to obtain passcodes to open doors either visually or by the beep tones produced as the door is unlocked. A statement by the manufacturing company of the baby monitor indicated that the model in question was 3 years old and had not gotten a firmware update, hence creating the avenue for this attack. A routine audit of devices in an organization would be able to identify such devices, which are behind on their firmware update and thus avert any potential privacy violations.
10.2.2 Confidentiality, Integrity, and Availability
Confidentiality is roughly equivalent to privacy (Yang et al., 2010). However, here we are very much concerned with the measures that need to be taken to prevent sensitive information from reaching wrong people. Integrity deals with maintaining consistency, accuracy, and trustworthiness of the data throughout its life cycle (Yan, 2016). Devices connected to a network can be hijacked if the network is breached and the integrity of the data in that network can be compromised or falsified. Availability here deals with maintaining functionality when needed by the user.
In 2014, a study by the SANS institute indicated that 375 health organizations in the United States were compromised all within a month. The intruder infiltrated a set of new and improved radiological imaging units in tandem with the network and was able to gain access to patients files and confidential information (Filkins, 2014). The patients' information was at the mercy of the intruder who could as well have changed or manipulated the data thus violating its integrity. They could also have introduced a bug to the system to hamper the proper functioning of the imaging units denying medical professionals its availability at crucial moments. An audit performed on this category of devices in such medical establishments will reveal the potential areas intruders might exploit and offer recommendations on the best course of action. Admittedly, some manufacturers might not immediately see the need for integrated security in devices such as components of an imaging unit. However, once the industry/organizations start putting standard audit procedures into place, manufactures will be forced to think about how best to integrate security into their products in order to be audit compliant.
10.2.3 Identity Management
Identity management issues might arise if the user uses their social media account to access their IoT service online. In a scenario where their social media account gets compromised, the IoT account/device could also be compromised. For example, an intruder can take control of your home security once they breach your social media account that is connected to a smart watch or Fitbit. The intruder could also perpetrate identity theft once they have access to details from the social media account as well as other personal information available on the devices, for example, financial information used by NFC apps present in phones and also smart watches/bands. Standard audit procedures within any organization would either prevent vulnerable devices from joining the network or notify the network administrators of devices in need of patch or firmware update.
10.2.4 Physical Attacks
Attackers can stage targeted physical attack on the smart network in many ways. Cutting off power or tampering with circuit breakers, installing signal jamming devices on communication lines, and so on, are all possible physical attacks that can debilitate the network. Another facet of physical attacks in scenarios where proximity permits could also include resetting the passwords, changing settings, and redirecting traffic to a server controlled by the hacker. From their servers, attacks can be launched in a number of different ways, for example, studying the firmware of the device and exploiting unmitigated vulnerabilities. Local attacks can also occur over Wi-Fi/Ethernet.
10.2.5 Cloud Infrastructure Attacks
Allowing the users to use weak passwords, not locking out users after unsuccessful attempts, missing two-factor authentication (2FA), unsecured password recovery, and, in general, not enforcing standard security procedures offers an easy target for lurking attackers. Scenarios such as these invariably attract attacks such as brute force attacks, blind SQL injection attacks, and other targeted account-harvesting attacks. Eventually, any successful attack will allow the attacker gain access to the device(s) and personal data. With some of the attacks, such as blind SQL injection attacks, the hacker can end up with read access to the database of the console and obtain the login credentials of the other users connected to the cloud IoT infrastructure.
10.2.6 Malware Attacks
Malware bearing software accidentally downloaded to any device could easily tell the attacker about the devices in the network and perform the previously mentioned attacks. It would just be a matter of time before the attacker can use the device as well as other connected devices to perform attacks like connected toasters that mine crypto currencies or smart TVs that are held ransom by Malware. IoT auditing of these devices will also be to identify anomalous' in the logs and generate alerts to that effect.
10.3 IT Auditing
The purpose of Information Technology (IT) auditing is to examine and scrutinize the management controls in the IT infrastructure. Typically, after the scrutiny, a decision is then made as to whether or not the IT systems are properly espousing the three information assurance tenants (confidentiality, integrity, and availability) while still being properly aligned with the organization's objectives. IoT auditing evidently follows much of already standardized procedures in auditing but requires additional steps to properly ensure a truly multilayered/tiered secured system infrastructure.
10.3.1 IoT Auditing
A proper understanding of the challenges facing IoT devices will elucidate that these IoT devices need a certain degree of security controls and standards. This is evident as the evolution and progress of most of these devices have been disparate. Thus, bringing a huge number of functionally disparate devices into a single network could potentially make for a network with gapping loopholes that is susceptible to cyberattacks. Given their geographically dispersed originating factories, these devices are not always manufactured with the necessary security protocols and standards. A lot of manufacturers already involved in the manufacture of other Internet capable or peripheral devices might use the same procedures and standards to build IoT devices. As with the common Internet capable peripheral devices, such as routers, switches, gaming consoles, manufacturers pressed for time or to meet up with demand surges could ramp up production without necessarily enforcing security. This was the case with Sony games and the recently hacked Jeep Cherokee car replete with IoT-like technology (Newcomb, 2016; Martin, 2016). Hence the result of devices manufactured and built with varying standards could very well imply that they will be vulnerable to attacks common to any device connected to the Internet and possibly other newly developed attacks. An added risk that ensues it that since these devices eventually become part of the network, there is a high probability that these “weak links” in the system can potentially provide a gateway to attack the rest of the network as well as the other devices connected to the network. The vulnerabilities discussed earlier shown in Figure 10.2 would be a serious concern in any business model where these devices are used and may have serious repercussions if not addressed in a timely manner (Rawlinson, 2017).
10.3.2 Need for Auditing
With the proliferation of IoT, billions of devices are to be continually connected to a vastly expanding network all in a bid to improve the quality of peoples' lives, change business processes and models, and reinvent entire industries. On the other hand, IoT also has the potential to provide entrance points for cybercriminals into personal and corporate networks and data storage units. This unequivocally poses a problem that warrants auditing procedures. The loss related to these sorts of attacks have historically been significant when you consider examples like Target, Sony, Home Depot, and Ashley Madison (Keith, 2017).
Clearly the main challenge in today's and future implementations of the IoT is ensuring we have not made any compromises on the security aspect. Lack of proper security measures could provide chances for intruders to access and use personal information that is collected and transmitted to or from a device. Personal information can be misused by the unauthorized person and may result in identity theft or fraud. This may also create risks to physical and public safety in some cases (Alexandra Carmichael, 2011; Tollefson, 2015). To achieve desirable levels of security, IoT systems must adopt and evolve a multilayered security checks and balances, which will be evaluated during auditing. The device, the software, the communication channels must all be tamper proof and ensure data confidentiality. Security should not be an afterthought whereby a layer of protection is wrapped around a finished product. Industry standardization and best practices should push for a “security by design” approach where security is built into the different layers of the device presenting several walls obstructing access to any intruder. This can take several forms, for example, 2F authentication (already commonly used today) or proximity authentication, which will block out most remotely staged attacks. Regardless of the security and assurance technique used, provisions have to be made by the manufacturer to allow for audits within the organization.
Speaking of the organization, incidentally, most of the IoT devices are not actually included in the security audits, as it is currently. An internal audit function can educate the managing body on the competitive edge that a properly functioning IoT implementation can bring to the enterprise. It will also elaborate on the importance, benefits, and potential cost saving advantages in that respect. On the other hand, potential security loopholes and malpractices can be identified and the associated risks dealt with. Moving forward, preventive, corrective, and detective measures and controls could also be implemented to reenforce the IoT infrastructure. This practice of auditing becomes a very important routinely needed exercise especially with the constant progress of the field because the associated risks and vulnerabilities also change with the technology's rapid evolution.
Performing internal audits can be very beneficial as it has the potential to offer strategic advice to the organization's management on the importance, the benefits, and the competitive edge that the IoT could offer the organization. A competent audit can demonstrate to the organization's management how IoT can be effectively implemented in daily operational procedures such as the automated tracking of inventory. These can range from inbound logistics, sales, and marketing all the way to product disbursement. The internal auditing process also permits constructive recommendations and advice to management on how to implement preemptive preventive, detective, and effectively corrective measures. Given the incredible pace at which the IoT is advancing, the inherent risks are a major looming concern, as evidently not enough time will be devoted to the security evaluation of these systems (Salman, 2015).
Furthermore, due to the lack of security audit in IoT, there is no way for an organization to ascertain the source and the type of attack. An organization will be ill-prepared for such an incident and this would affect the business continuity of the organization. To mitigate the risks involved with the use of IoT devices, an organization has to perform a risk-based assessment of all the assets included under the IoT umbrella and perform an end-to-end security audit at appropriate intervals along with the documentation, testing, and reporting of business continuity procedures. Organization can also perform controlled self-assessment (CSA) that would aid in seamless audits. Controlled self-assessment is an internal control assessment technique that has been used in industry for identifying and managing aspects of risk and exposure within an organization. Strong arguments have been made in its favor as it also identifies and highlights areas in the organization with potential opportunities (Ahmed et al., 2003).
10.3.3 Risk Identification and Assessment
Every IT security audit begins with a thorough risk identification and risk assessment along with a holistic validation of the impact of the systems to the goals of the organization. This process essentially starts with risk identification where potential risks to the system are recognized and described. Risk identification is followed by risk assessment, where the likelihood and the consequences of each risk is determined and documented. Control risks, detection risks, inherent risks, and overall audit risk are considered.
After a thorough risk assessment, the auditor must define the scope of the audit by holistically validating the business function to be audited. Typically, prior approval from the senior management is obtained and authority is delegated from the board of directors before the audit process is initiated. An auditor will usually have to consider the points described in Figure 10.3 before auditing the IoT system.
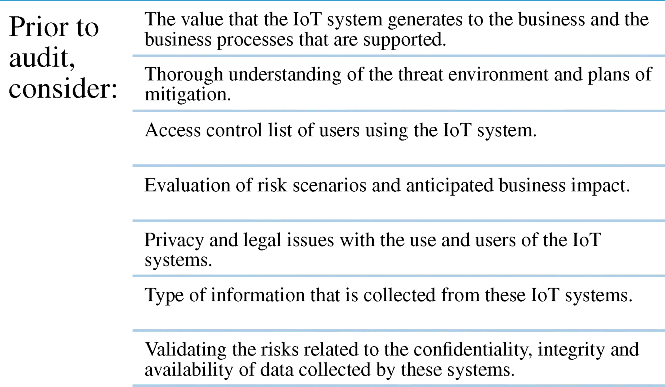
Figure 10.3 Points to consider before the audit procedure.
Figure 10.3 outlines some very important points to consider before any auditing procedure can begin within the organization. Primarily, the value that the IoT system generates to the business or organization is key. A system that is centralized and directly integrated to the production or manufacturing arm of the organization would be very critical as it essentially forms an integral part of the organizations driving engine. This calls for a more critical assessment to ensure that the manufacturing or production engine is robust enough to withstand attacks that can bring the whole system down. IoT systems that are more peripheral in nature or decentralized might not necessarily need such scrutiny. Another important aspect directly related to the value of the IoT system in the organization is the threat environment. Not every IoT system is vulnerable to a particular attack. NFC and Bluetooth-based systems might not be necessarily vulnerable to remotely staged attacks, such as SQL injection, but could be vulnerable to attacks requiring close proximity. An understanding of this threat environment and plans for mitigation is therefore required. It is also worth mentioning that in recent times the damages caused by insider threats call for a closer scrutiny of people on the systems' access control list as they also could be a part of the threat environment. From instances such as that of Snowden and the NSA, we have come to understand that the list of users with access control privileges effectively constitute the threat environment. These insiders are capable of using any kind of IoT device and exfiltration method to siphon data out of the organization that effectively constitutes the threat environment.
Some other important points to consider as specified by Figure 10.3 include the evaluation of risk scenarios and anticipated business impact, privacy and legal issues that arise with the use of the IoT systems, type of information that is collected from these IoT systems, and the damages that can result if this data is obtained by intruders. All of these will permit the auditor draw up a more focused assessment plan for an audit that will better serve the organization. Organizations whose IoT systems are more customer centric will be worried more about privacy and legal issues; whereas, with more manufacturing or production centric organizations, they might be concerned more with risk scenarios and their related impact on business. After considering these points, an effective audit strategy can be developed based on what the expectations are with regard to the result of the audit.
10.3.4 Audit Strategy
An auditor must keep the organizations interest in mind while auditing the IT systems. An auditor's independence is of crucial importance so that he/she is not to be influenced by any factors that could jeopardize the audit. The audit can essentially begin by focusing on the following aspects of the IoT system:
- Security. As the name implies, the IoT devices generally have some built-in Internet connectivity capabilities, and hence, become just as susceptible to attacks from cyber criminals and hacktivists as laptops, notebooks, and other Internet capable devices. A thorough vulnerability assessment of the IoT systems must be conducted and potential risk factors and internal controls have to be identified. These vulnerabilities, threats, and controls have to be documented and periodically tested. The documentation is essential to strengthen the controls for IoT systems. Security of systems provided by third parties must also be considered and audited at frequent intervals. A thorough analysis of the encryption used in IoT systems must also be considered in the audit. Moreover, auditors must also ensure that these devices follow the basic security standards and protocols that have been defined by an appropriate security framework (Kessinger and Duffer, 2017; Hare-Brown, 2017).
- Health and Safety. Of all the risks posed by the IoT devices, risks associated with human life and safety are indispensable. Health and safety are of utmost importance in industries like health care, chemical industries, manufacturing unit, laboratories, where smart devices are employed. Examples of these health devices include pacemaker, defibrillators, or other vital signs tracking devices. These systems must be thoroughly tested before they are deployed into these business units. In addition to that, control measures are needed to ensure that the requisite testing procedures are completed before major overhauls such as upgrades, patches, and other changes are made to IoT systems. This is very critical where health and safety-related faults pose a significant risk (Crossman and Liu, 2015; Kessinger and Duffer, 2017).
- Resilience. Since IoT devices are used in crucial systems that are prone to attacks, an auditor must assess the existence of controls that could recover systems in the event of a failure. An auditor must elucidate the importance of business continuity, disaster recovery, and incident response to the senior management and actively participate in the design and testing of these procedures. These procedures are crucial to identify the organizations preparedness in the event of a mishap. All crucial systems must be considered while testing these scenarios and appropriate documentations must be in place to guide a smooth transition in the event of a change. Performing testing to ensure the continuity of these procedures are of prime importance to identify their concomitance to the RPO (recovery point objective) and RTO (recovery time objective) (Kessinger and Duffer, 2017).
- Monitoring. Akin to any other access-based system, there is a dire need for controls measures that can monitor the functioning of the IoT systems. Frequent testing has to be performed to ensure that the controls are operating as expected. Any exception or error that occurs in the system must be successfully recorded. These recordings can assume the form of any kind of logging available to the system. Logging obviously has been in the past and continues to be a tremendous asset during audits. It has been compared to an administrative partner that is always at work, never complains, never gets tired, and is always on top of things. If properly instructed, such a partner can provide extensive details on the time and place of every event that has taken place in the network or system (Tuli and Sahu, 2013). The SANS Institute identifies different logging levels such as Debug and Informational, Notice, Warning, Error, Critical, Alert, and Emergency in that order of severity (GadAllah, 2003). Considering a more proactive stance, preventive controls need to be consistently maintained and can be tested with penetration tests to ensure their operability. Likewise, detective controls need to log any illegal access to the system and corrective controls must successfully restore data if lost (Hare-Brown, 2017).
- ASSET Management. An auditor must give sufficient importance to the procurement and classification of IoT assets that are used in an organization. A holistic risk-based assessment must be performed while classifying these assets and the data that they transmit. These devices must also contain sufficient amount of encryption to the point where the loss of encrypted data does not pose serious risk to the organization (Hassan, 2016). This is of immense importance as recently U.S. HealthWorks suffered from a data breach via an unencrypted laptop that was lost (Lewis, 2017). Tightening up security measures in asset management evidently should be a major priority.
- CHANGE Management. While upgrading/changing a system from a legacy to an improved system, care must be taken to ensure a smooth transition. The newly employed system must mitigate the risks that possibly plagued the legacy systems while also not compromising on critical controls. As second generation IoT devices begin rolling off assembly lines and factories, it will be imperative to ensure that their integration into the organization does more in the way of mitigating existing loopholes and vulnerabilities. Due to pressing schedules, some legacy SCADA (Supervisory Control and Data Acquisition) systems undergo limited amounts of testing and fail to achieve a compromise between concrete security measures and smooth daily functioning. The security features turn out to be either too stringent and slow down smooth functioning or not stringent enough to promote robust functionality, hence allowing security loopholes and vulnerabilities. An example of such a failed attempt was observed with Windows 7's attempt on enforcing system-wide privacy and security. A thorough assessment of any new IoT devices and systems in general will, therefore, be needed before they can be deployed company wide.
10.4 Use Cases of IoT in IT Auditing
The rapid innovations made possible by IoT are consistently pushing the boundaries of how we interact with technology. A direct result of this is the fact that organizations are seeing new nonstandardized forms of technology entering into their networks. This brings about new scenarios having security implications for which the organization is not adequately prepared to handle, as there have been no prior organizational standards in these areas. Listed below are three use cases in which the use of IT auditing would be useful in preventing or detecting possible security lapses in the IoT.
10.4.1 Bring Your Own Devices
The first use case will deal with a Bring Your Own Device scenario, specifically wearable devices due to their growing popularity and expanding capabilities. Depending on the brand, smart watches can browse the web, sync up to your email, write notes, take voice recordings, and even take pictures. The enhanced functions of these wearable devices would allow for easier corporate espionage due to the ability to carry out small bits of data hidden on the watch. Another potentially dangerous scenario would be if the smart watch was hacked, either through the web function or through Bluetooth-based attacks. A virus could unwittingly be brought into the business office where the virus was then allowed to spread after the watch connected to your work computer or other devices in the office.
10.4.2 Electronic Utility Meter Readers
The next use case will deal with the idea of electronic utility meter readers. An electronic meter makes it easier to keep track of the utility costs in a company, but comes with its own hazards. If an outsider is able to gain access to those meters, they will be able to monitor traffic throughout the building or company. A malicious agent can figure out when a certain area will be least populated and then utilize social engineering to get through that area. It is a lot easier to fool one or two individuals with social engineering techniques than a whole group of people. In addition to that an agent who is out to cause lethal damage could redirect the flow of gas to concentrated areas within the building, which could end up in a fire hazard. Finding ways to cut off the flow of air to these regions of the buildings could have similar lethal effects on human lives.
10.4.3 Smart Parking Meter Interfaces
Another use case can involve smart parking meters and their connections to buildings' or organizations Wi-Fi. Smart parking meters in a particular building will be connected to a main interface that can provide incoming drivers with information on exactly where parking is available in that building. In such a scenario, an incoming driver can quickly query the building's parking interface to obtain information on the parking available in that building. For instance, a vehicle might have just pulled out of Level 1 parking spot 27, making that spot available on the building's parking interface. An incoming vehicle would not have to go to level 5 to find a parking spot. An additional benefit of this interface would be the automated tagging of employees' cars. So, employees would no longer need a physical tag to park but could use RFID tags or possibly have the car computer system connected to the smart parking grid network, which could as well be hosted through the organizations intranet. The first issue that could arise with this is some sort of denial-of-service (DoS) attack where an attacker or malicious agent can breach the system and tag empty lots as occupied thereby denying legitimate users parking service. The situation becomes more critical if the attacker can connect to the organization's intranet and extract valuable information on the organization or trivial information such as what vehicle the CEO drives. There are a number of different ramifications that could come with this particularly the potential loss of valuable information. Organizations who own or share smart parking grid interfaces would have to work together to establish common standards to enhance security and consequently audit procedures.
10.5 Protecting the Business Network
The government created the Federal Trade Commission (FTC) for the purpose of protecting the consumer in their purchase of products and services1. They are an independent agency and as such, do not have direct authority or the upper hand in the enforcement of their ideas in a particular industry. Instead, they come up with their version of a best practice solution, such as in the case of securing the IoT and then would recommend that the industry adopt these practices to handle security and privacy issues all in a bid to protect the consumer (Ohlhausen, 2014). The FTC understands that IoT, for instance, has great potential for communication innovation and would like to see the network grow, but they also understand that users have to believe in the network for them to use it. The apparent dilemma here is that even though they believe in the importance of this security, they lack direct enforcement ability upon companies in the industry. As such they resolve to be more persuasive in their approach by releasing reports that lay out best practices and host on workshops to spread their ideas.
While this seems great, some of the ideas that the FTC has come up with are actually pretty basic (Federal Trade Commission and others, 2015). The fact that these solutions were not already in place is a symptom of the new attention being placed on the IoT network. For example, one of the solutions is to have security be part of the first step of product design and not just put in as an afterthought. It would be easy for us to just blame the producer for not doing enough to protect the privacy of their customers. However, the consumer will not find many products on the market that were made to be tamper proof.
10.5.1 Traditional Security Measures
Another best practice for a company is to minimize the data collected by this network or to notify consumers to make them fully aware of this collection of data. People are wary of any data collection due to “Big Data” being a major buzzword in the media. Unless all players in a certain grouping (e.g., wearables) get together, and all promise to disclose the extent of data collection, this solution will not be taken seriously. If one brand announces the collection of data, consumers will jump ship from that brand to another brand that has not announced collection, even though most likely their some data be produced for a hacker to steal.
The solutions that the FTC is pitching need to be disseminated further before they can be accepted as serious answers. So, while the FTC may only be offering basic ideas, this may eventually create enough public attention to get these ideas implemented in future products to increase security moving forward. The FTC cannot just have workshops attended by industry insiders and expect instant change to current practices. They do have their reports and information on their site, but realistically, if a consumer cared about this topic, they would most likely already have collected all of the relevant and meaningful information from another source. The average consumer is just aware of the benefits they stand to gain from being able to connect to more devices around their house.
There are numerous other big, high-tech firms providing their thoughts on this topic, and there does not seem to be one magic answer as to how to infallibly secure this network is. In the meantime, we just keep growing the network because we do not believe that hackers will crack into our fridges or other such devices. As with credit card theft, we never think that it will happen to us, until it does. And even then, we are already so ingrained into this system that we do not know how to act different so we hope that an issue does not happen again. With this in mind, it calls into question the Federal Trade Commission's warning of doom for the growth of the IoT in relation to consumer buy-in and privacy concerns. By getting the word out to the average consumer about potential dangers and the impact they can have on a company's bottom line if security is not made a top priority, the FTC can help ensure change.
10.5.2 New Policies to Address New Threats
Industries that are keen on implementing these IoT devices must be prepared to efficiently manage IoT devices to gain maximum rewards from it. They must have prepared to mitigate any risks that IoT poses by following specific guidelines and standards. A few recommendations for organizations planning to implement IoT are as follows:
- Designing security into IoT systems from the bottom-up. Security must not be added to these systems after their implementation, but rather, they must be incorporated from the initial stages of development. In other words, security controls must not be a value added to the IoT systems, but an essential integrated feature.
- Understanding vital assets and values and investing in their protection. Health companies focus on the well-being of the patient while commercial organizations focus on great products and sales maximization. These assets and values have to be the central focus when planning on IoT implementations.
- Collecting sufficient amount of data that is required and encrypting the sensitive data.
- Partnering with appropriate vendors on elements of security like identity management, access control management intelligence analytics, and patch management.
- Conducting a comprehensive security audit of the IoT systems including privacy, risks, and fraud assessment.
- Sufficient testing before implementing or changing the IoT systems.
- Training the organization staff on the risks related to IoT systems and reiterating it.
- Creating a security awareness program and educating all the members of the organization on the importance of security practices related to IoT systems (Hare-Brown, 2017).
10.6 Conclusion
The next generation of technology belongs to network-interfaced devices that perform intelligent and complex tasks in order to enhance human lifestyle experiences. The evolution of these devices now allows them to exchange copious amounts of data, process this data, and obtain results, which allow them to make decisions very often without any human intervention.
Unfortunately, this luxury does not come without its drawbacks as these networks teeming with data pose as a very attractive bed for intruders and other ill-intentioned minds. This chapter has highlighted and discussed some of the possible ensuing vulnerabilities and demonstrated the need for routine auditing. The onus, however, does not only lie with the organizational auditing bodies, but manufacturers must find a way for end-to-end security to be incorporated in IoT devices and IoT systems. This should be done in concert with factory level audits to ensure compliance with designated standards. In a nutshell, security at both the device and system levels should be an integral part of their build process followed by recurring audits to ensure standards are met.
Establishing audit procedures for IoT devices might seem far-fetched as these devices cut across a wide array of categories, as seen in the chapter. There however already exist basic tenets for auditing devices that exchange data in today's world. In like manner, rigorous auditing routines akin to the commonly known and widely accepted such as with penetration testing routines or with BYOD infrastructure could easily be referenced. Adapting and modifying these already existing technologies will doubtlessly ensure compliance at every level of society ranging from homes to job sites. As it is, the available technology already possesses the tools and capabilities for built-in security or at the very least periodic audits. To this end, priority must not be placed on investing new technologies and gadgets. The immediate objective must be directed toward conveying the present best in class IT security controls, streamlined for this new and complex ecosystem of technology that is driving the IoT.
Acknowledgments
The research of the second, third, and fourth authors is funded in part by the National Science Foundation through the Scholarship for Service program under grant #1241709. The first author is funded by the University of Texas at San Antonio.
Note
References
- Ahmed, A. M., Yang, J. B., and Dale, B. G. (2003) Self-assessment methodology: the route to business excellence. The Quality Management Journal, 10(1), 43. Available at http://search.proquest.com/openview/0697fb8426fc3c99f60970e174cb1d9b/1?pq-origsite=gscholar.
- Alexandra Carmichael. (2011) HIT – Health Internet of Things. Quantified Self. February 14. Available at http://quantifiedself.com/2011/02/hit-%e2%80%93-health-internet-of-things/.
- Boorstin, J. (2016) Humans hooked on 21 billion of these by 2020. CNBC. February 1. Available at http://www.cnbc.com/2016/02/01/an-internet-of-things-that-will-number-ten-billions.html.
- Crossman, M. A. and Liu, H. (2015) Study of authentication with IoT testbed. 2015 IEEE International Symposium on Technologies for Homeland Security (HST), pp. 1–7. Available at http://ieeexplore.ieee.org/xpls/abs_all.jsp?arnumber=7225303.
- Federal Trade Commission, and others. (2015) Internet of Things: Privacy & Security in a Connected World. Washington, DC: Federal Trade Commission.
- Filkins, B. (2014) Health Care Cyberthreat Report. Widespread Compromises Detected, Compliance Nightmare on Horizon. SANS Institute. http://www.redwoodmednet.org/projects/events/20150731/docs/Norse-SANS-Healthcare-Cyberthreat-Report2014.
- GadAllah, S. M. (2003) The Importance of Logging and Traffic Monitoring for Information Security. Available at https://pdfs.semanticscholar.org/b1bd/427cb53b8ccc7a9b7630dcec77abcbb27c2b.pdf.
- Hare-Brown, N. (2017) How to mitigate security risks associated with IoT. ComputerWeekly. Available at http://www.computerweekly.com/opinion/How-to-mitigate-security-risks-associated-with-IoT (accessed July 10, 2017).
- Hassan, M. K. A. L. (2016) Governance, risk and compliance “GRC” for Internet of Things" IOT. International Journal of New Technology and Research, 2(3), 148–152. Available at https://www.ijntr.org/download_data/IJNTR02030038.pdf.
- HP News (2016) HP News—HP Study Reveals 70 Percent of Internet of Things Devices Vulnerable to Attack. Available at http://www8.hp.com/us/en/hp-news/press-release.html?id=1744676#.V2ByEuYrKgQ (accessed June 14).
- Keith, C. (2017) A Quick Guide to the Worst Corporate Hack. Bloomberg.com. Available at http://www.bloomberg.com/graphics/2014-data-breaches/ (accessed July 10, 2017).
- Kessinger, K. and Duffer, J. (2017) Internet of Things: Risk and Value Considerations. Available at http://www.isaca.org/knowledge-center/research/researchdeliverables/pages/internet-of-things-risk-and-value-considerations.aspx (accessed July 10).
- Lewis, D. (2017) US healthworks suffers data breach via unencrypted laptop. Forbes. Available at http://www.forbes.com/sites/davelewis/2015/06/01/us-healthworks-suffers-data-breach-via-unencrypted-laptop/ (accessed July 10).
- Martin, L. (2016) PlayStation hacked: what to do when your PSN account gets hacked. Express.co.uk. Available at http://www.express.co.uk/pictures/galleries/7133/PlayStation-Store-Summer-Sale-PS4-discounts.
- Newcomb, A. (2016) Jeep hackers' are back with a scary new trick. NBC News. Available at http://www.nbcnews.com/tech/tech-news/jeep-hackers-are-back-scary-new-trick-n623756.
- Ohlhausen, M. K. (2014) Privacy challenges and opportunities: the role of the federal trade commission. Journal of Public Policy & Marketing, 33(1), 4–9. Available at http://journals.ama.org/doi/abs/10.1509/jppm.33.1.4.
- Rawlinson, K. (2017) HP study reveals 70 percent of internet of things devices vulnerable to attack. Available at http://www8.hp.com/us/en/hp-news/press-release.html?id=1744676#.V2ByEuYrKgQ (accessed July 10).
- Salman, S. (2015) Auditing the Internet of Things. Internal Auditor, October 29. Available at https://iaonline.theiia.org/2015/auditing-the-internet-of-things.
- Tollefson, R. (2015) Healthcare data at risk: Internet of Things facilitates healthcare data breaches. Third Certainty, January 9. Available at http://thirdcertainty.com/news-analysis/internet-things-facilitates-healthcare-data-breaches/.
- Tuli, P. and Sahu, P. (2013) System monitoring and security using keylogger. International Journal of Computer Science and Mobile Computing, 2(3), 106–111. Available at http://d.researchbib.com/f/8nq3q3YzydL3AgLl5wo20iMT9wpl9jLKOypaZiGJSlL2tlZQRmY1LlFGZlZQRmZwVhpTEz.pdf.
- Van der Meulen, R. (2017) Gartner says worldwide IoT security spending to reach $348 million in 2016. Available at http://www.gartner.com/newsroom/id/3291817 (accessed July 10)
- Wagstaff, K. (2014) Man hacks monitor, screams at baby girl. NBC News, April 28. Available at http://www.nbcnews.com/tech/security/man-hacks-monitor-screams-baby-girl-n91546.
- Wortmann, F., Flüchter, K., and others. (2015) Internet of Things. Business & Information Systems Engineering, 57(3), 221–224. Available at http://search.proquest.com/openview/ac6643ce2897d57bbad03f45ba9436e1/1.pdf?pq-origsite=gscholar&cbl=816386.
- Yan, W. Q. (2016) Introduction to Intelligent Surveillance, Springer.
- Yang, G., Xu, J., Chen, W., Qi, Z.-H., and Wang, H.-Y. (2010) Security characteristic and technology in the Internet of Things. Journal of Nanjing University of Posts and Telecommunications (Natural Science), 30(4).
