8
Security Mechanisms and Technologies for Constrained IoT Devices
Marco Tiloca and Shahid Raza
RISE SICS Security Lab, Kista, Stockholm, Sweden
8.1 Introduction
The Internet of Things (IoT) emerging paradigm is commonly identified as the growing information technology trend toward a pervasive network society where all devices that can benefit from a connection will be connected with one another. This means that, in addition to traditional commodity devices and PCs, all kinds of electronic equipments that can benefit from a connection are expected to be available and accessible online.
In such a massively interconnected scenario, security has been immediately acknowledged as a dramatically important requirement to fulfill. On one hand, the well-known security threats, vulnerabilities, and attacks from traditional Information Technology (IT) systems are naturally inherited. This is why communication and management protocols proposed and adopted in the IoT already provide a number of basic fundamental security services. On the other hand, many additional security attack vectors are enabled against easier to target IoT devices, essentially because of two main reasons.
First of all, the long-term IoT vision assumes that the majority of devices are going to be directly connected to the Internet, in order to be directly accessible. This also makes them directly exposed to several kinds of security attacks, especially denial-of-service (DoS), that would be otherwise more difficult and less convenient for an adversary to carry out. Second, a typical IoT environment is expected to include a considerably large number of resource-constrained, often battery-powered, devices. This not only makes a large set of IoT devices considerably more vulnerable and less capable to cope with security attacks, but also results in the additional challenge of designing, implementing, and adopting security solutions that are also affordable for constrained IoT devices and do not significantly impact on performance and scalability of the overall network environment and IoT application scenario.
This chapter overviews the most important and crucial practical aspects concerning security in the IoT. In particular, this chapter first goes through the most important IoT security protocols and mechanisms, which are adopted in a typical IoT communication stack and are currently considered in ongoing standardization activities or have already been released as standards. They include, for instance, CBOR Object Signing and Encryption, OAUTH 2.0, Object Security for CoAP, DTLS, and compressed IPsec. This chapter also presents a number of specific security-related issues in the IoT, and discusses possible solutions to address them based on recent results from the scientific community and activities in standardization bodies. Particular attention is devoted to counteracting DoS attacks against IoT protocols and networks, preserving and improving high performance and scalability in the presence of security services, efficient and scalable protocols for management of cryptographic keys, and detection and counteraction of security attacks.
8.2 Security in IoT Protocols and Technologies
The IoT has the potential to transform the way we work and live on a daily basis. If there is one reason that can limit this transition, it will be the sage in security and privacy. While offering strong security is already hard in the Internet, it is in fact much more challenging in the IoT, since the “things” are going to support the Internet Protocol version 6 (IPv6), be globally reachable and extremely heterogeneous (comprising sensor devices, smartphones, standard computers, and even cloud environments), and usually deployed in physically unprotected, unattended environments. Moreover, most of them do not provide any conventional user interface, such as a display or keyboard. At the same time, IoT-constrained environments inherit the limitations typical of conventional wireless sensor networks (WSNs), for instance, limited processing and energy resources, multihop communication topologies, and lossy wireless links.
In order to meet these challenges, different protocols are being developed and standardized for IoT devices and networks. This section highlights the typical IoT security protocols and mechanisms currently adopted in IoT application scenarios and use cases. In particular, it goes through a typical network stack according to a top-down approach, and presents security services that IoT protocols rely on or directly provide. A quick summary of the presented protocols is provided in Table 8.1 (Section 8.2.7).
Table 8.1 Overview of protocols and mechanisms.
| Protocol/mechanism | Stack layer | Purpose | Reasons to adopt |
| CBOR Object Signing and Encryption | Application | Serialization of data structures for cryptographic formats | Efficient encoding of messages secured at the application layer |
| OSCORE | Application | Secure end-to-end communication between a CoAP client and a CoAP server | Required in the presence of intermediary entities (e.g., proxies) that can legitimately inspect and selectively alter CoAP messages |
| DTLS | Transport | Secure hop-by-hop communication between a DTLS client and a DTLS server | Required to entirely protect CoAP messages |
| Compressed IPsec | Network | Secure hop-by-hop communication between two IPsec nodes | Required to entirely protect transport packets. Compression by 6LoWPAN to deal with limitation of lower layers |
| IEEE 802.15.4 security services | MAC | Secure hop-by-hop communication between two 802.15.4 nodes | Required to entirely protect network packets and especially routing control traffic |
| Bluetooth Low Energy | MAC | Secure hop-by-hop communication between two Bluetooth nodes | Security level equal to that in standard Bluetooth. Possible white lists of private link-level addresses |
| OAuth 2.0 | Application | Issue and enforcement of authorizations for resource access on remote server | Based on an Authorization Server, it totally separates clients and resource owners |
Figure 8.1 shows a resource-constrained IPv6-connected IoT network, also referred to as IPv6 over Low-power Wireless Personal Area Network (6LoWPAN). It also sketches a typical IoT stack with different security protocols and technologies at different layers within an IoT device. At the application layer, OAuth 2.0 is being customized for IoT devices, with the aim to bring fine-grained access control mechanisms in the IoT; object security is being standardized to protect individual data items; and the Constrained Application Protocol (CoAP) has asserted itself as the new web standard for IoT that can carry Object security and OAuth messages. At the transport layer, connectionless UDP is favored for IoT devices, and the Datagram Transport Layer Security (DTLS) protocol is bound with CoAP to form the secure CoAP (CoAPs) protocol. Alternatively, it is possible to use the Internet Key Exchange version 2 (IKEv2) protocol to dynamically establish and manage security associations and related key material when the adoption of IPsec (or network security) is preferred. Furthermore, IPv6 displays a potentially unlimited address space, and is the de facto networking and addressing protocol for the IoT, while the IPv6 Routing Protocol for Low-Power and Lossy Networks (RPL) is the standardized solution for packet routing within constrained, low-power, and lossy networks (Winter et al., 2012). Also, 6LoWPAN has been standardized in order to provide compression/decompression and fragmentation/reassembly mechanisms, and thus make larger packets fit in the IEEE 802.15.4 frames (or similar ones). Finally, there are a number of possibilities at the link and physical layer. Since there is a great potential in IEEE 802.15.4 as well as Bluetooth Low Energy (BLE), security in their presence is also discussed.
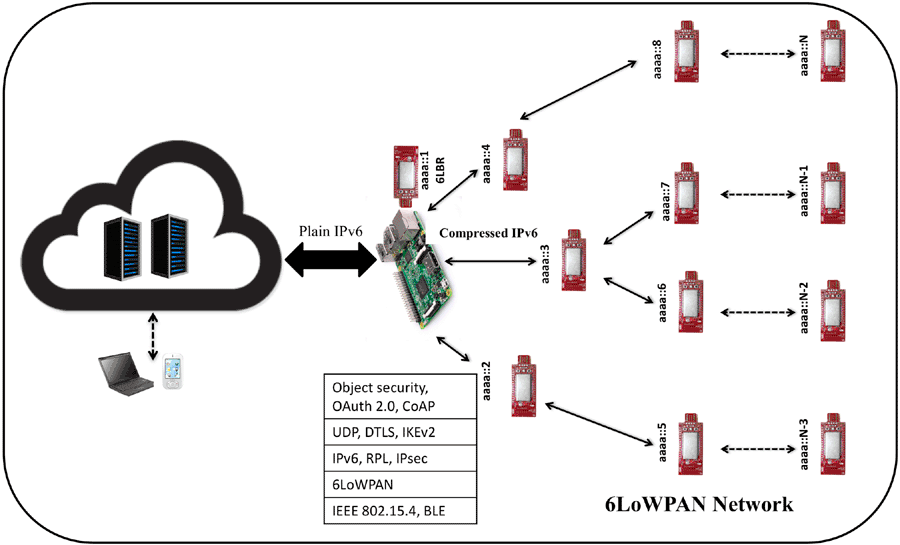
Figure 8.1 Example of resource-constrained IoT network with different security protocols and technologies at different layers.
8.2.1 Lightweight Formats for Cryptosecurity Protocols
Since many IoT devices are expected to be resource constrained, there is the need to provide security services in a particularly efficient way, and hence reduce the amount of information to be stored, transmitted, and processed. This means that not only plain application-level content, but also encrypted content, digital signatures, and even cryptographic keys are required to be represented and encoded in a compact and efficient way.
To this end, CBOR Object Signing and Encryption (COSE) aims at creating cryptographic formats based on Concise Binary Object Representation (CBOR) (Bormann and Hoffman, 2013). CBOR is a succinct binary format for the serialization of data structures, suitable for resource-constrained devices (Bormann et al., 2014). A major share of envisioned billions of IoT devices will consist of battery-powered or energy-harvested devices. For these IoT devices, COSE has a huge potential to produce lightweight CBOR-based representations of cryptographic keys, encryption, message hashes, and digital signatures.
COSE is inspired by JavaScript Object Signing and Encryption (JOSE) that has already standardized cryptographic formats using JavaScript. Although COSE tries to reuse functionalities from JOSE, they are not directly compatible for straightforward adoption. One of the major differences that CBOR brings compared with JOSE is the direct use of binary data format with no need to first convert it into, for example, a string encoded in base64. The CBOR Encoded Message Syntax details the basic COSE structure and common COSE headers (Schaad, 2017). Furthermore, it elaborates the COSE objects by means of dedicated cryptographic key materials, as well as through cryptoalgorithms for data encryption/authentication and for computation of Message Authentication Codes (MACs). There already exist proposals for encoding parameters, keys and outcomes of RSA (Jones, 2017), and other algorithms (Schaad, 2016) as COSE messages. Also, lightweight COSE representation of cryptographic data structures and their implementation and evaluation, when compared with JOSE, could be an interesting research topic.
8.2.2 CoAP and DTLS
CoAP is a novel web transfer protocol especially designed for resource-constrained devices and networks. It relies on request/response interactions between endpoints and can easily integrate with the widely adopted Hyper Text Transfer Protocol (HTTP) for integration with the classical Web (Fielding and Reschke, 2014a, 2014b). Although the CoAP protocol has been designed for constrained devices and networks (Bormann et al., 2014), on the other hand it does not provide itself any particular primitives to secure communication (Shelby et al., 2014). Instead, CoAP messages can be protected either by means of object security, as discussed in Section 8.2.3 or through actual secure communication protocols. In such a case, the CoAP specification recommends to adopt the DTLS protocol (Rescorla and Modadugu, 2012). In particular, Shelby et al. (2014) specify the CoAP binding to DTLS as a set of deltas to plain unsecure CoAP. From a practical perspective, if a CoAP message is secured using DTLS, the coaps://URL scheme is considered, rather than the coap://scheme for unsecure communication. In particular, the three security modes PreSharedKey, RawPublicKey, and Certificate are available. That is, the PreSharedKey mode relies on preshared cryptographic keys, each of which include a list of devices allowed to use that key for secure communication. If the RawPublicKey is considered, a device owns a pair of asymmetric private–public keys with no associated certificate, hence entrusting validation to out-of-band mechanisms. In addition, the device maintains an identity computed from the public key, as well as a list of devices it is allowed to communicate with. Finally, in case it considers the Certificate mode, a device stores an asymmetric private–public key pair, together with an X.509 certificate. The certificate binds the public key to its subject, and includes a digital signature from a well-known trust root (Cooper et al., 2008). In particular, the device additionally maintains a list of root trust anchors, which can be referred to in case certificate validation has to be performed.
Practically, DTLS allows two devices to establish a security association, authenticate with one another, and exchange protected CoAP messages. The Internet Engineering Task Force (IETF) has recently released a profile for Transport Layer Security (TLS) and DTLS 1.2. The profile provides communication security for resource-constrained devices employed for collecting data by means of sensors or for controlling actuators in applications for industrial control systems, home automation, smart cities, and other IoT deployments (Tschofenig and Fossati, 2016).
DTLS has been voluntarily conceived to be very similar to the TLS protocol (Dierks and Rescorla, 2008), and in fact fulfills equivalent security requirements. That is, it makes it possible for applications running on clients and server units to exchange secure messages, namely, DTLS records, especially preventing tampering, forgery, and eavesdropping of such messages. At the same time, DTLS displays a number of differences compared to TLS, so making it possible to provide secure message exchange on top of UDP and other unreliable datagram transport protocols. For instance, RC4 and other stream ciphers are not allowed to be used. Besides, a sequence number value is explicitly included in each DTLS message. So doing, DTLS messages result to be not related with one another, thus making it possible for recipients to correctly process them, even when out-of-sequence delivery occurs. Furthermore, DTLS addresses packet loss through message retransmission and local timeouts. Upon the reception of an invalid message, the related DTLS session may still be preserved, and that message can simply be silently discarded.
In order to exchange protected messages over DTLS, two client and server devices perform a handshake process in order to establish a secure session, as depicted in Figure 8.2. Handshake messages transmitted at a same step are grouped together as part of one DTLS Flight. Optional or situation-dependent messages are indicated in square brackets and not always sent.

Figure 8.2 DTLS message exchange.
The client typically takes the initiative and sends a ClientHello message to the server in order to start establishing the DTLS session. DTLS admits a stateless cookie value that can be optionally exchanged between the server and the client by means of Fligth2 and Flight3, with the intent to address DoS against the server. Then, client and server exchange Flight4 and Flight5 in order to authenticate each other, negotiate a cipher suite and security parameters, and establish cryptographic key material. Finally, Flight6 confirms that a DTLS session has been fully established on both sides, and thus client and server can consider it for secure communication. The reader can refer to Dierks and Rescorla (2008) and (Rescorla and Modadugu), (2012) for additional information concerning the handshake and the specific format of DTLS Flights.
Before starting a handshake, two DTLS peers have to be provided with preliminary security material. This includes, for instance, preinstalled cryptographic keys that are employed to establish a premaster secret during the handshake. Then, client and server use this premaster secret together with self-generated random values in order to derive a master secret, out of which the actual security material for the DTLS session is finally derived. In order to distribute preinstalled keys, there are two main approaches that can be considered. The first one leverages asymmetric keys. Additionally to the typical usage of X.509 certificates (Cooper et al., 2008), there are also available raw public key profiles, where private–public keys are provided without a certificate. In particular, such keys can be generated by device manufacturers and then installed before the device deployment (Wouters et al., 2014). In such a case, a device validates raw public keys received from other peers by means of out-of-band techniques. In particular, it usually stores a list of peers it is allowed to communicate with. Instead, an alternative approach leverages symmetric preshared keys (PSKs) (Eronen and Tschofenig, 2005). That is, the client stores a number of symmetric keys, each of which shared with a server that the client is allowed to communicate with. Then, during the handshake, the client specifies the particular key to use, indicating the related PSK identity. Finally, the client and server derive the DTLS premaster secret out of the symmetric key that they have been sharing. Adopting the approach based on preshared key is especially convenient for environments that are closed and within which one can easily provide cryptographic keys to the deployed devices. Furthermore, it does not require sending and receiving public certificates, or to engage in asymmetric cryptography operations, which are costly and particularly important to limit on resource-constrained DTLS servers. Besides, it makes key management operations considerably easier, particularly in IoT deployments within which manual and early configuration of connections is often common practice, and hence the provisioning of certificates often results to be a nonpreferable or even nonfeasible option.
8.2.3 Object Security for Constrained RESTful Environments
The CoAP standard specifies the possible use of proxies as intermediary entities between CoAP clients and servers, to improve efficiency and scalability in a number of network and application scenarios (Shelby et al., 2014). At the same time, as previously discussed in this chapter, CoAP refers to the DTLS protocol to provide secure communication (Rescorla and Modadugu, 2012). This represents a problem in the presence of intermediary proxies, since the latter must be able to access, and possibly manipulate, specific portions of a CoAP message, in order to perform the intended proxy functionality. As a consequence, proxy operations on CoAP messages require that DTLS communication from a CoAP client terminates at the proxy. On the other hand, it is still very important to prevent the proxy from accessing and/or manipulating portions of the CoAP messages that are not strictly necessary for the correct performance of the intended proxy functionality. In particular, this would also contribute to reduce and relax the security and trust assumptions on the proxy units deployed in the network. To this end, it would be convenient to rely on a secure communication protocol that is able to protect CoAP messages in an end-to-end fashion, even when intermediary nodes are present.
At the time of writing, the document (Selander et al., 2018) describes a relevant proposal named Object Security for Constrained RESTful Environments (OSCORE). In principle, OSCORE is a data object-based security protocol enabling the exchange of CoAP messages that are end-to-end protected across intermediary nodes. OSCORE uses COSE objects (Schaad, 2017) in order to provide integrity, end-to-end encryption, and replay protection of CoAP messages. The usage of OSCORE is signaled in the first place by including a newly defined Object Security CoAP option in the secured CoAP messages. As a possible alternative, message protection can be limited to the payload only of individual messages, according to an akin approach named object security of content (OSCON). The end-to-end security services provided by OSCORE are also particularly desirable in constrained network settings where solutions like DTLS can not be supported. On the other hand, OSCORE can actually be combined and used together with DTLS. That is, OSCORE can enable end-to-end security of CoAP messages between a CoAP server and a CoAP client, together with protection of the entire CoAP messages (i.e., header included) in a hop-by-hop fashion provided by DTLS during the message transport between an endpoint and an intermediary node like a proxy.
More practically, OSCORE assumes that a security context has been preestablished and agreed upon between a CoAP client and a CoAP server considered as endpoints of the secure communication. In particular, a security context is the set of information and parameters that the two OSCORE endpoints use to perform the specific cryptographic operations. Furthermore, OSCORE is very similar to DTLS, and borrows a number of its mechanisms such as key derivation and construction of nonce values. However, OSCORE relies on COSE (Schaad, 2017) rather than the DTLS record layer, and thus is able to use security context identifiers and sequence numbers of variable length.
8.2.4 Compressed IPsec
The 6LoWPAN standard (Hui and Thubert, 2011) defines how heavyweight IPv6 datagrams can be transmitted over low-power and lossy networks based on IEEE 802.15.4 (IEEE Computer Society, 2011). To achieve this, 6LoWPAN introduces a number of schemes for header compression, which are able to considerably reduce the size of the UDP headers, IP datagrams, and IP extensions. In IP networks based on IEEE 802.15.4, also referred to as 6LoWPAN networks, security is particularly important due to the high exposure to the Internet and the resulting network vulnerability. Currently, IP security (IPsec) (Kent and Seo, 2005; Jankiewicz et al., 2011) is the standard security solution for IPv6. In particular, IPv6 hosts on the Internet should implement it and be able to handle and process IPsec-protected packets. In particular, the transport mode of IPsec provides secure end-to-end communication between two nodes on the Internet. Hence, it is expedient to adapt 6LoWPAN in order to enable IPsec communications among IPv6-enabled things (e.g., sensor nodes) in 6LoWPAN networks and generic IPv6 nodes on the Internet.
A number of different proposals have been presented for compressing headers of IPsec packets. The majority of compression schemes is adoptable to generic Internet hosts, and does not specifically consider 6LoWPAN networks composed of resource-constrained devices. Migault et al. have proposed Diet-ESP (Migault and Guggemos, 2015; Migault et al., 2016) that specify how to perform compression of IPsec packets, but needs a number of changes and adoptions in conventional hosts on the Internet. Furthermore, RObust Header Compression (ROHC) relies on a flexible and efficient concept for header compression, but it is intended to generic hosts on the Internet and hence is not specifically intended for 6LoWPAN networks (Sandlund et al., 2010; Ertekin et al., 2010). Therefore, Raza et al. (2011) propose the 6LoWPAN-compressed IPsec, which is primarily targeted for resource-constrained IoT devices and network.
The schemes Diet-ESP and ROHC together with Generic Header Compression (Bormann, 2014) are accessory to the compressed IPsec described in Raza et al. (2011), where mechanisms for header compression specifically target 6LoWPAN networks, work with generic Internet hosts using IPsec, and do not result in any change of the standards Encapsulated Security Protocol (ESP) and IPsec Authentication Header (AH).
Currently, the IPsec's ESP protocol that provides both confidentiality and integrity of the ESP payload is mostly used. For the IoT, a number of use cases are envisioned where it is useful that ESP, as well as AH, protects the integrity of IPv6 headers in addition to the IPsec payloads. Because of different reasons, the usage of AH in the Internet is currently limited. That is, AH is not compatible with Network Address Translation (NAT), which modifies the IP source address while in transit, thus making the packet integrity check fail and ultimately causing the packet rejection at the recipient IPSec host. Moreover, ESP is able to provide both encryption and integrity protection of IPsec packets, but it makes it possible only to secure the application data and the ESP header, while leaving the IP header unprotected. Practically, this is fine in case the tunnel mode of IPsec is used, since the inner application data, ESP header, and IP header are both confidentiality and integrity protected.
Since IoT scenarios relying on IPv6-connectivity do not comprise NATs, it is possible and favorable to use the transport mode for providing end-to-end security. Thus, using AH along with ESP makes particularly more sense in the IoT. In particular, since the AH integrity check takes into account the IP address, IPsec can be effectively used to provide protection against IP spoofing, which is among the most common and likely security attacks mounted against resource-constrained devices communicating over IPv6. In addition, despite the stateless autoconfiguration of IPv6 addresses has been proposed, this is not considered to be an actual requirement to fulfill. That is, resource-constrained nodes in 6LoWPAN networks are assigned with IPv6 addresses at deployment time, and likely maintain the very same address during their lifetime, except in case of manual intervention by means of firmware/software updates. On the other hand, it is practically infeasible to address autoconfiguration in 6LoWPAN networks in a way that ensures end-to-end connectivity, unless a suitable and efficient mechanism specifically targeting 6loWPAN networks is designed and developed; this is in fact an interesting research challenge to take. Note that even if only a single application runs on a 6LoWPAN node, IPv6 potentially provides an unlimited address space. Therefore, one has the luxury to reserve many different IPv6 addresses for one single 6LoWPAN node. As a consequence, this enables the setup of unique IPsec security associations for each different application. In addition, in case IKEv2 (Bormann, 2015) is specifically considered as key management protocol, it is then possible to dynamically establish unique security associations on a per-application basis.
Besides, a number of use cases such as alarm actuating and simple environmental monitoring require only integrity protection, hence the usage of AH only is a convenient choice. At the time of writing, there is a pending IETF standard draft that defines the actual encoding of IPsec AH and ESP (Raza et al., 2016). The detailed implementation and evaluation of this draft are also available in Raza et al. (2011, 2014).
8.2.5 IEEE 802.15.4 and Bluetooth Low Energy
The IEEE 802.15.4 standard provides specifications for the physical and the Media Access Control (MAC) layer intended for wireless low-rate personal area networks. It entrusts other protocols like ZigBee or WirelessHART for additional services at the higher layers, or can alternatively rely on 6LoWPAN as an adaptation layer to operate together with standard Internet protocols.
In addition, the MAC layer of IEEE 802.15.4 directly provides a number of security services, that is, data authenticity, data confidentiality, and replay protection on a per-packet basis (IEEE Computer Society, 2011). In particular, the standard refers to a cryptosuite relying on the Advanced Encryption Standard (AES) 128 bits symmetric-key cryptography (National Institute of Standards and Technology, 2001). In case secure communication is enabled, an Auxiliary Security Header (ASH) is included next to the standard MAC header of each packet, which is secured upon its transmission based on what specified in the ASH. The recipient node receives and correctly unsecures the packet according to the same information.
In particular, IEEE 802.15.4 provides three different security modes, that is, CTR (encryption only), CBC MAC (authentication only), and CCM (encryption and authentication). The CCM and CBC MAC modes use a Message Integrity Code (MIC), which can be 4, 8, or 16 bytes in size. Security operations in IEEE 802.15.4 make use of a fresh nonce value. In particular, a nonce is generated at random on the sender side, and provides protection from replay attacks. The different available security modes and the different available configurations make it possible to trade specific application constraints with the security and performance requirements.
Finally, the IEEE 802.15.4 standard does not describe how to establish and distribute the key material in the network, or how to address device authentication. Instead, it assumes that both such security services are provided and enforced by the higher layers. As a consequence, the standard assumes that a given pair of sender and recipient nodes has successfully agreed on the same security settings and shared common key material, before they can start to securely communicate.
The same security services are provided in the enhanced standard IEEE 802.15.4e, which extends the previous standard IEEE 802.15.4 in order to specifically target embedded applications with critical requirements (e.g., healthcare or industrial applications) (IEEE Computer Society, 2012). In particular, it defines the MAC behavior mode Time Slotted Channel Hopping (TSCH), which combines multichannel and channel hopping functionalities with time slotted access. This not only makes it possible to provide better performance in terms of high reliability, large network capacity, energy efficiency, and predictable latency, but also contributes to make networks more robust against security attacks mounted at the physical layer, such as jamming and radio interference, thanks to the channel hopping mechanisms.
While on one hand IEEE 802.15.4 is currently the de facto standard covering the physical and link layers for 6LoWPAN networks, other new technologies are evolving as well. For instance, BLE, practically marketed as Bluetooth Smart, is among the energy efficient communication technologies currently available, and does represent an appealing alternative. In particular, BLE has asserted itself as a lightweight alternative for resource-constrained devices, compared to Classic Bluetooth. The Bluetooth 4.0 standard now also includes the BLE specifications, which comprise the broadcast communication mode in addition to the power-efficient connections among Bluetooth devices. Bluetooth 4.2 was published in December 2014, and provides a number of novel features which do make BLE a promising and valuable technology for the IoT (Bluetooth Special Interest Group, 2014).
The most important addition that enriches Bluetooth with IoT capabilities is the support for the Internet Protocol Support Profile (IPSP) (Bluetooth Special Interest Group, 2016). IPSP adds IPv6 support in the Bluetooth peripheral device and in the central master device acting as network coordinator, and specifies how devices are supposed to discover one another and to establish a connection at the link layer with each other. Besides, the BLE Generic Attribute Profile (GATT) can be employed in order to determine whether a device has IPSP support enabled, which in turn enables the exchange of IP packets by means of the Bluetooth L2CAP Credit Based Flow Control Mode.
Furthermore, Nieminen et al. connect BLE with 6LoWPAN by specifying the standard way for transmission of compressed IPv6 packets on top of BLE (Nieminen et al., 2015). In particular, they propose using the header compression mechanisms of 6LoWPAN on top of BLE. On the other hand, they do suggest to not use the fragmentation mechanisms of 6LoWPAN, but rather to rely on the ones already outlined in Bluetooth L2CAP.
Also, one of the most relevant improvements brought by Bluetooth 4.2 is the increased size of packets, that is, the BLE payload at the link layer is increased from 27 to 251 bytes. Also, Bluetooth 4.2 improves the throughput up to 2:5 times. These enhanced capabilities enable efficient IPv6 communication over BLE, frequent and speedy updates of device firmware, as well as fast uploading of data from sensor devices to backend units. Also, it makes it possible to run even in the IoT a number of complex security protocols, for example, DTLS (Rescorla and Modadugu, 2012) and IPsec (Kent and Seo, 2005; Jankiewicz et al., 2011).
Prior to Bluetooth 4.2, the Bluetooth standard provides stronger security in comparison with BLE, mostly for achieving energy efficiency. However, it also displays a small packet size of 27 bytes, and hence does not allow devices to use asymmetric-key cryptographic protocols. Instead, Bluetooth 4.2 LE brings BLE to the same security level of the standard Bluetooth, by recommending to rely on Elliptic Curve Cryptography (ECC). Specifically, the National Institute of Standards and Technology (NIST) has recommended to use elliptic curves, whereas the Federal Information Processing Standards (FIPS) has recommended to use AES-CCM symmetric cryptography for encryption and integrity protection.
In addition, Bluetooth 4.2 also brings enhanced privacy by adding private address resolution both in the Bluetooth Host as well as in the controller segments of a Bluetooth node. Also, Bluetooth 4.2 specifies the controller to maintain a white list of private addresses at the link layer. So doing, the controller is able to generate and resolve private addresses at the link layer with no need to interact with the host, and to reject or accept incoming connection according to the maintained white list. This significantly reduces the rate according to which the host has to “wake up,” therefore, considerably limiting the energy consumption of the BLE chip. The enhanced security and privacy with new low-power features and the fact that BLE is supported out of the box in most commodity smartphones makes BLE a valuable and promising technology for IoT deployment that involves mobility and allows a 6LoWPAN network to be directly connected to a smartphone, such as in deployments involving wearables. The standard IEEE 802.15.4 is still a preferable and more suitable choice for static deployments, such as smart homes.
8.2.6 OAUTH-Based Authorization in the IoT
According to the Internet Security Glossary, authorization is defined as the process for granting approval to a client to access a resource (Shirey, 2007). A typically adopted approach consists in managing the authorization of users, services, and their devices by means of dedicated Authorization Server (AS) entities. The OAuth 2.0 authorization framework relies on this fundamental approach, and has asserted itself as one of the most widely adopted standard for managing authentication processes (Hardt, 2012). In fact, it makes it possible to address all typical issues of alternative approaches based on credential sharing, thanks to the introduction of an authorization layer, and the separation of the role of the client from the role of the actual resource owner. In principle, the OAuth 2.0 authorization framework allows a client entity (i.e., a host, a process, a user) to request and obtain a specific, regulated, and limited access to a resource available at a resource server (RS) by enforcing the permission of the related resource owner.
Specifically, the resource owner grants authorization to the client by means of an intermediary AS, which provides the client with the actual authorization-related information specified in an access token. More specifically, an access token is practically represented as a string, which encodes an authorization decision issued to the specific client, and is typically opaque to that client. Among other things, an access token specifies the duration and scope of authorized resource accesses, which are ultimately determined by the AS and enforced by the RS. Furthermore, the AS ensures that possible unauthorized parties are not able to generate, modify, or guess any issued access tokens for producing valid access tokens. Then, the client can contact the RS in order to access the intended resource, according to the credentials specified in the access token. That is, the RS verifies that the access token is valid and, in such a case, proceeds with serving the request received from the requesting client. Before starting to perform the authorization protocol, the client must have registered at the AS, and all access token credentials must be always transferred through a secure communication channel, that is, both from the AS to the client and from the client to the RS. Also, the AS must verify the identity of the resource owner upon every authentication request on behalf of a client, and is required to have preestablished a trust relation with the involved RS hosting the resources to access. Note that the same AS can be associated with, and issue access tokens to be used with, multiple resource servers.
Having said that, it is more than reasonable to assume that end consumers and enterprises will want to adopt the same kind of approach for managing authorization as well as resource access control in IoT application scenarios. Also, this will become more and more likely with the rapidly increasing number of services provided by applications hosted on IoT devices organized in large-scale deployments. This has led to an IETF proposal (Seitz et al., 2018) aimed at reusing the OAuth 2.0 framework to extend authorization to IoT devices with different kinds of constraints, by using the basic OAuth 2.0 mechanisms where possible, while providing implementers with additional guidance, profiles, and extensions for using it in a secure and a friendly way with privacy. In particular, Seitz et al. (2018) describe a framework for authorization in the IoT that combines together a number of building blocks—(i) the original OAuth 2.0 authorization framework, (ii) the transfer protocol CoAP (Shelby et al., 2014), and (iii) the application layer security services, based on object security to CBOR-encoded data (Selander et al., 2018)—required when transport layer security provided by protocols like DTLS is not sufficient, adequate, or convenient. The DTLS protocol as well as object security to CBOR-encoded data have been discussed in more detail in the previous sections of this chapter.
8.2.7 Overview of Security Protocols and Mechanisms in the IoT
Table 8.1 provides a compact overview of the security mechanisms and protocols discussed throughout Section 8.2, highlighting the layer that benefits from their contributions.
8.3 Security Issues and Solutions
Protocols and mechanisms presented in Section 8.2 are typically adopted to fulfill primary fundamental security requirements in the IoT, such as secure communication at different layers, authorization for resource access, and compact encoding for cryptographic formats. Nevertheless, even when such basic security warranties are ensured, IoT systems are prone to a number of security vulnerabilities and exposed to specific security attacks, exploiting weaknesses and inefficiencies of security protocols, as well as poor scalability and efficiency of typically adopted management schemes. Moreover, such attack vectors can be particularly easy to exploit in the IoT for two main reasons. First, the majority of IoT devices are supposed to be directly connected to the Internet in order to be directly reachable, and hence fully exposed to adversaries motivated to carry out, for instance, DoS attacks. Second, many IoT devices are resource constrained, as equipped with a limited amount of memory, computing, and energy resources. This means that attacks that are otherwise fairly feasible to deal with can result in a much more severe impact. Besides, even related security counteractions have to be designed in order to be feasible and adoptable for such classes of constrained devices.
This section presents a number of specific security issues related to IoT systems, protocols, and technologies, and discusses possible solutions to address them based on recent results from the scientific community and activities in standardization bodies. Particular focus is put on different forms of DoS attacks, including (selective) jamming performed at the physical layer, while considering also the need for efficient and scalable protocols for management of cryptographic keys, secure communication in multicast groups of IoT devices, and the adoption of Intrusion Detection Systems (IDSs) and firewalls.
8.3.1 Denial-of-Service Against CoAP
Energy-constrained, even battery-powered, IoT devices are substantially exposed to a number of security attacks, especially if they are directly connected to the Internet with no particular protection implemented through dedicated gateway or firewall boxes. A particular well-known class of security attacks is DoS, which in turn may be mounted with the specific intent to keep IoT devices constantly busy in receiving and processing invalid messages, so preventing them from switching to any energy-saving sleep mode and quickly draining their battery energy supply (see Figure 8.3).

Figure 8.3 Denial-of-service attack against a server IoT device.
This specific kind of DoS attacks is often referred as denial-of-sleep, and is considered a particularly severe security threat against constrained, battery-powered, IoT devices (Stajano and Anderson, 1999; Martin et al., 2004; Raymond et al., 2009; Gehrmann et al., 2015). In addition, their occurrence cannot be avoided altogether. That is, an active adversary that continuously transmits bogus messages can always induce a victim recipient IoT device to receive them and perform processing operations at different layers. This means that a practical countermeasure should instead focus on reducing the attack impact as much as possible, with particular reference to the energy consumption due to the useless message processing. However, counteracting this class of attacks in an effective and efficient way is definitely a challenging task, particularly in the presence of IoT devices that are directly connected to the Internet, that is, globally accessible to enable remote management and configuration, operation requests, and information retrieval.
Nowadays, CoAP has asserted itself as the de facto application layer protocol for the IoT, with particular reference to resource-constrained devices (Shelby et al., 2014). However, when it comes to providing secure communication, CoAP does not provide any particular security primitives or countermeasures against DoS attacks. Instead, CoAP suggests adopting the DTLS protocol (Rescorla and Modadugu, 2012), which relies on a costly and complex handshake process in order to setup a secure session, and results in a nonnegligible overhead to provide a whole set of security assurances, some of which may even not be necessary in some application scenarios.
A number of works have proposed detection techniques against denial-of-sleep attacks, typically considering traffic analysis or other anomaly detection mechanisms. For instance, Bhattasali and Chaki (2012) proposes a probabilistic model to detect denial-of-sleep attacks, based on Absorbing Markov Chains. Instead, Buennemeyer et al. (2007) describe B-SIPS, a system based on an innovative Dynamic Threshold Calculation algorithm that provides alerts upon detecting power changes. As pointed out in Raymond et al. (2009), these solutions based on intrusion detection techniques typically require to capture and analyze a considerable large amount of network traffic, and thus can be difficult or even unfeasible to deploy and run them on resource-constrained IoT devices.
Different proposed approaches consider traditional security services, especially at the link layer. For instance, Martin et al. (2004) propose a power-secure architecture, which processes only requests that deserve a high level of trust, but does not describe any concrete scheme to improve battery drain robustness. Instead, Raymond and Midkiff (2007) present an approach for rate limiting that relies on host-based intrusion detection mechanisms enforced at the link layer, considering messages to be legitimate only if both authenticated and not replayed, and taking actions to mitigate the attack effects. Also, Raymond et al. (2009) propose a framework based on classic link layer authentication, replay protection, and jamming identification. These detection approaches relying on traditional link layer security are however likely to result in a considerable overhead, especially as to energy consumption (Daidone et al., 2011). Also, they imply that validity of messages must be checked by every network node, along the path from the source to the destination device. This evidently produces a considerable additional impact on network performance as a whole. Furthermore, these approaches require to establish secure trust relations among all devices in the communication path (e.g., by distributing pairwise cryptographic keys), thus likely failing in efficiently providing protection against denial-of-sleep attacks from an end-to-end perspective.
More recently, Gehrmann et al. (2015) have proposed a security service relying on a short Message Authentication Code directly embedded in the CoAP message header, in order to early and efficiently detect invalid messages upon their reception. That is, it makes it possible to quickly determine whether received messages are valid or not, namely, whether they have been possibly transmitted by illegitimate sources. In such a case, a victim IoT device can early discard invalid messages and avoid performing useless additional parsing and processing operations. This considerably reduces the impact of denial-of-sleep attacks as to energy consumption, and thus preserves battery life in constrained IoT devices.
8.3.2 Denial-of-Service and Scalability Issues in DTLS
The DTLS handshake process displays two relevant security and performance issues that mostly affect devices acting as DTLS server.
First of all, as also stressed in the DTLS specification, a device acting as DTLS server is particularly vulnerable to DoS attacks mounted during the handshake process (Rescorla and Modadugu, 2012). Specifically, an active adversary has the possibility to continuously transmit ClientHello messages to the DTLS server, and induce it to start a great amount of DTLS handshakes. This in turn forces the server to start the setup of new (invalid) DTLS sessions. From a DTLS server point of view, this means allocating network and memory resources, and performing a number of resource-demanding operations. Moreover, this may exhaust available network and memory resources, so making the server less responsive or, in the worst case, even unavailable to process legitimate requests sent by DTLS clients. As a further drawback, attacks mounted through spoofed valid IP addresses force the DTLS server to send reply messages to “innocent” devices, so displaying a well-known amplification effect. The specification of DTLS provides a tentative solution against the DoS attack mentioned above, which leverages the stateless and optional exchange of a piece of information, namely, cookie, occurring during the first phases of the handshake between a DTLS client and server (Rescorla and Modadugu, 2012). Specifically, the DTLS server may reply to the first ClientHello message with an additional HelloVerifyRequest message, which includes a cookie as a locally generated value. After that, the DTLS client replies with another ClientHello message, which must include exactly the same cookie. However, the cookie exchange process only complicates the considered DoS attack, while it does not fundamentally provide any real protection against it. More in detail, as shown in Figure 8.4, an adversary able to intercept messages sent by the DTLS server during the handshake can still be able to perform the DoS attack, and induce the server to set up a considerable number of invalid, half-open DTLS sessions. It follows that the countermeasure based on the cookie exchange performed between client and server is actually not a good solution against DoS attacks mounted by a resourceful and well determined on-path adversary.
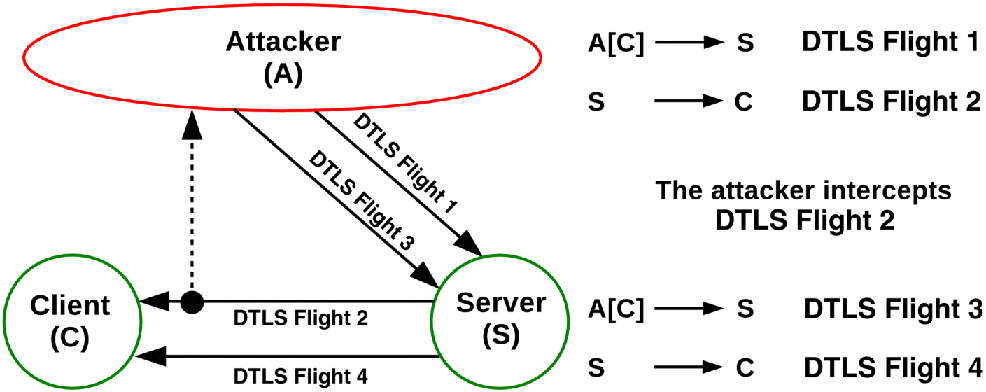
Figure 8.4 Denial-of-service attack targeting a DTLS server.
Furthermore, if the handshake is based on the PSK approach (Eronen and Tschofenig, 2005), the DTLS server may require to store and manage a nonnegligible number of symmetric keys associated with DTLS clients. As shown in Figure 8.5, this means that a DTLS server stores in the worst case one preshared key for every possible DTLS client. Of course, this approach scales poorly with the number of DTLS clients in the network. Moreover, it considerably complicates key provisioning and management operations, especially in dynamic scenarios. Nevertheless, the PSK scheme is very useful, convenient, and widely adopted in several dynamic IoT environments that involve resource-constrained devices as well as end users with no capability to securely manage a more complex public key infrastructure.
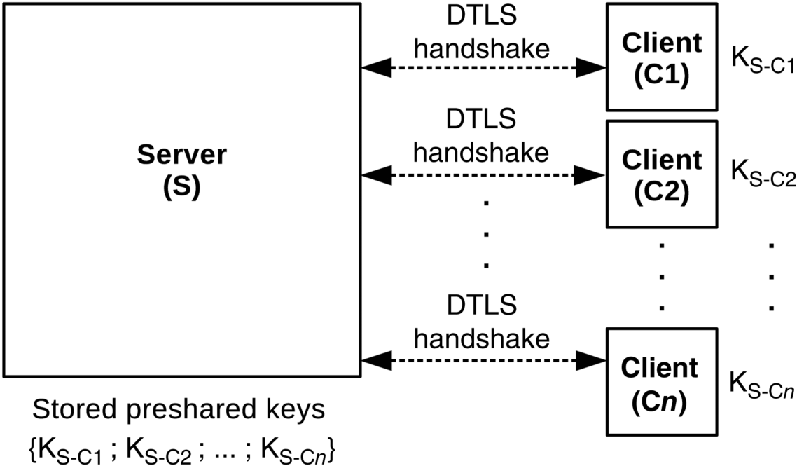
Figure 8.5 Poorly scalable storage of preshared keys on a DTLS server.
In Tiloca et al. (2017c), a security architecture has been proposed in order to address both issues discussed already. In particular, the proposed approach makes it possible for the DTLS server to detect an invalid ClientHello message upon its reception, and then immediately terminate the handshake at its very beginning, so practically neutralizing the attack and substantially limiting its impact. Also, it provides an alternative PSK scheme that greatly reduces the number of preshared keys stored at the server to one, thus preventing scalability and management issues. Furthermore, the proposed solution displays a number of advantages. First, it relies on a standardized method to extend ClientHello messages, and thus it is not required to modify the DTLS standard. Second, the DTLS client and server are not required to perform any further message exchange, and even the cookie exchange is not necessary anymore. Besides, the computing overhead on the client and server is not significantly affected, as the same computational complexity is preserved for the handshake process. Finally, it can be easily readopted in TLS, again with no required changes.
8.3.3 DTLS-Based Group Communication
As discussed in Section 8.2.2, the CoAP protocol (Shelby et al., 2014) mandates the adoption of the DTLS protocol (Rescorla and Modadugu, 2012) to secure unicast communications between a given pair of IoT devices. At the same time, in several IoT deployments involving groups with IoT devices as members, using multicast communication over IPv6 has several advantages, particularly as to scalability and performance. This is the reason why the standard (Rahman and Dijk, 2014) has explicitly defined group communication based on the CoAP protocol, with reference to a number of different use cases where the group communication model is particularly beneficial to IoT devices. For instance, group communication is highly convenient, or even inevitable, in IoT application scenarios such as firmware and software updates, lighting control, configuration and parameter updates, integrated building control, emergency broadcast, and commissioning of 6LoWPAN networks. In many IoT deployments, these use cases display a number of specific security requirements to be fulfilled, including the secure exchange of multicast messages among IoT devices within the same group. However, at the time of writing this chapter, CoAP does not provide support, or recommend an interoperable way, for securing multicast group communications.
At the same time, DTLS is the de facto security protocol to secure IoT unicast communications. Therefore, it is especially convenient to enhance DTLS so that it can also support secure group communication in the IoT. This choice would also be particularly convenient if compared with possible different alternatives. For instance, opting for IPsec multicast (Weis et al., 2008) would also require to use the heavyweight IPsec (Kent and Seo, 2005; Briscoe, 2010), and likely even additional supporting protocols, such as IKEv2 (Kaufman et al., 2014). Furthermore, DTLS is currently supposed to be used for protecting unicast communications in the IoT, hence opting for IPsec solutions would be even less practical and convenient in real-world application scenarios.
So far, there have been only a few initiatives to provide DTLS-based secure group communication for CoAP, in the remit of the standardization activities carried out within the IETF. In particular, the first approaches toward this direction were presented in the two documents Keoh et al. (2014) and Kumar and Struik (2015), which propose to protect communications in a multicast group of IoT devices by conveniently adapting the DTLS record layer, but were questioned because of a number of reasons. Among them it was pointed out that source authentication is a fundamental security requirement to be fulfilled, as group authentication alone may not be enough for several IoT application scenarios. Also, the protection of group response messages to multicast request messages was provided by means of traditional, pairwise, DTLS sessions. However, this can result in a number of practical issues and can display considerable degradation of performance, particularly in highly dynamic and large-scale groups of IoT devices.
On the other hand, the method described in Tiloca et al. (2015, 2017b) and Tiloca (2014) elaborates on the previous approaches, and proposes how to provide two-way secure group communication based on DTLS, while addressing the limitations displayed by the previously proposed approaches. Specifically, all the members of the multicast group consider the same group key material or efficiently derive individual key material. Group members rely on the overall key material in their possession to protect both requests sent to the group as multicast messages as well as possible responses sent back as unicast messages. The common key material is provided to a new group member upon its joining, and it is not necessary to perform DTLS handshakes among group members to enable secure communication in the group. Finally, the proposed approach ensures either source authentication or group authentication of messages sent within the group, according to the requirements of the specific application scenario.
8.3.4 Efficient and Scalable Group Key Management
As already mentioned, group communication is a convenient approach to adopt in many IoT application scenarios, in order to improve performance, responsiveness, and energy efficiency. However, it also requires a complex management of the group key material, as to generation, revocation, and (re)distribution. In general, the group key material comprises the secrets shared among the group members that enable secure communication only among devices in that group, at a given communication layer. For simplicity, the following refers to the group key material as a single symmetric group key, which all the group members commonly share and use to secure communications within the group at the application layer.
According to the group communication model, an IoT device explicitly joins a multicast group in order to become an active member. From then on, the device is able to receive (send) broadcast messages from (to) other devices in the same group. At some point in time, the device may want to leave the group, or can be forced to leave, in case it is compromised or suspected so. In order to allow only the actual group members to participate to the communications in the group, it is necessary to revoke and renew the current group key, that is, rekeying, according to the following policies. When a new device becomes member of the group, it must be prevented from decrypting and accessing messages exchanged before its joining, even if it has recorded them (backward security). Also, when a device decides to leave the group, or is forced to as compromised or suspected so, it must be prevented from decrypting and accessing any further future communication in the group (forward security). Practically, upon a change in the group membership, it is necessary to revoke the current group key and to distribute a new one to the current/remaining devices in the group. Therefore, it is particularly important that rekeying is performed in an efficient and highly scalable way, especially in highly dynamic and large-scale groups where joining and leaving can be very frequent events.
Furthermore, it is of particular importance to effectively deal with collusion attacks, which occur when multiple devices in the group are compromised, share their security material, and take part to the rekeying procedure anyway. Thus, these compromised nodes cooperate to regain knowledge of the group key, and would not be effectively removed from the multicast group. There are no group rekeying protocols that are not exposed to collusion attacks altogether, albeit they are characterized by different levels of resilience. However, only a few provide countermeasures to address collusion attacks. Moreover, several rekeying schemes recover the group from collusion attacks by means of a total member reinitialization, that is, each noncompromised device in the group has to be individually reinitialized. As a consequence, the collusion recovery displays a communication overhead that linearly grows with the group size, and can very negatively impact on the network scalability and performance.
Protocols for group key management have been typically classified as centralized, distributed, and decentralized (Rafaeli and Hutchison, 2003). Centralized approaches are particularly preferable in case of highly dynamic and large-scale groups, and especially good at minimizing communication, storage, and computing overhead. Centralized schemes use a set of administrative key material, which is logically organized for providing scalable rekeying upon node leaving (Dini and Savino, 2011; Dini and Tiloca, 2013; Gu et al., 2009; Tiloca and Dini, 2016; Wallner et al., 1999; Wong et al., 2000).
Furthermore, Logical Key Hierarchy (LKH) is a centralized protocol that relies on a hierarchical logical tree to organize administrative keys (Wallner et al., 1999). Specifically, the group key is the root of the tree, the group members' individual keys are the leaves of the tree, and the additional administrative keys are the internal tree nodes. In a group composed of n members, and assuming the key material to be organized in a balanced tree, both the storage overhead at the device side as well as the leave communication overhead grow as O(log n).
Figure 8.6 shows the key material managed by LKH in a group composed of eight devices, namely, u1, u2,…, u8. In particular, each device owns the keys along the path from its related leaf node in the logical tree, up to the root node associated to the group key KG. For instance, device u3 owns the individual key K3, the additional administrative keys K1–4 and K3–4, and the group key KG.
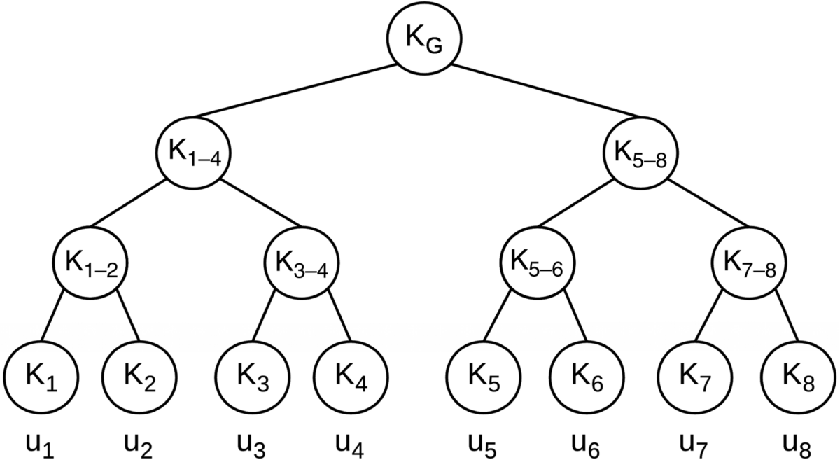
Figure 8.6 Example of LKH key material in the presence of eight group members.
Other protocols deriving from LKH do not achieve better performance (Dini and Savino, 2011; Gu et al., 2009; Wong et al., 2000). Furthermore, the centralized protocols HIghly Scalable Scheme (HISS) (Dini and Tiloca, 2013) and Group REkeying Protocol GREP (Tiloca and Dini, 2016) leverage logical subgrouping in order to provide highly scalable and efficient group rekeying, display the same storage and computing overhead, that is, O(√n), and distribute a new group key by using a number of rekeying messages that is constant, small, and independent of the group size, that is, O(1). In addition, the GREP protocol relies on the novel idea of member join history, and in fact leverages it in order to perform collusion recovery in a considerably more scalable and efficient fashion, with no recourse to a total member reinitialization. Specifically, HISS displays a recovery overhead that always grows as O(n). In contrast, the recovery overhead due to GREP gradually increases with the severity of the specific collusion attack and smoothly grows as O(√n), albeit only in the very unlikely worst case conditions.
On the other hand, distributed protocols rely on key management actions performed in a distributed way, involving the group members themselves or relying on additional key (sub)managers. However, they are harder to implement, are often less scalable, and raise security concerns. Moreover, some do not provide recovery from collusion attacks (Cheung et al., 2007; Fan et al., 2002), while others always require a total member reinitialization (Wang et al., 2008; Younis et al., 2006) or trade performance with collusion resistance (Chorzempa et al., 2005).
8.3.5 Selective Jamming in Wireless Networks
Jamming attacks are well known to be among the most common and severe kinds of DoS attacks against networks relying on wireless communication technologies (Lazos et al., 2009; Lu et al., 2014; Mustafa et al., 2012; Stojanovski and Kulakov, 2015; Xu et al., 2004, 2005, 2006). Specifically, jamming attacks consist in deliberately interfering with the operational frequencies in the network, and have been typically classified as constant, random, deceptive, and reactive (Xu et al., 2005).
On one side of the spectrum, constant jamming is extremely easy to perform. Its main objective consists in corrupting all transmitted network packets, by performing continuous overlapping transmissions of random signals. Note that this jamming strategy can be well considered as “always-on,” since it relies on the constant presence of a high level of interference, which thus makes the attack much easier to detect (Xu et al., 2004, 2005). On the other side of the spectrum, reactive jamming denotes a particularly smart and power-efficient approach, according to which an adversary actively jams communications in the network only during transmissions from other devices. Moreover, it is very likely that reactive jamming is actually confused with normal collisions of network packets, which makes it much more difficult to detect than other forms of jamming attack. Even more specifically, selective jamming is a specific type of reactive jamming, and it aims at interfering with communications between network devices, in accordance to well defined and specific objectives and criteria. With respect to other kinds of jamming attacks and strategies, selective jamming is more power efficient to perform, and even more difficult to counteract and detect, due to the reduced exposure of the adversary. A common criterion considered for selective jamming consists in disrupting all communication of one particular device in the network. In particular, this attack is particularly easy to perform in a wireless network using Time Division Multiple Access (TDMA). Specifically, TDMA divides time into a periodic sequence of superframes, each of which is composed of a fixed amount of transmission slots. However, such slots are typically assigned to network devices in a way that every device can remain active only during its own slot(s), and it can instead go to sleep mode during the other slots, so limiting its energy consumption. On the other hand, a network device typically retains exactly the same slot(s) for several consecutive superframes. As a consequence, an adversary has to simply monitor network communications, determine the slots accessed by its victim devices, and jam them to completely thwart the devices' communications. Note that such an attack is also very efficient from a power consumption point of view, since the adversary requires to keep her radio active only during the transmission slots assigned to her victim devices.
The countermeasures proposed to counteract jamming attack have been typically divided into physical-layer and cyber solutions. In principle, physical-layer solutions try to prevent an adversary from successfully interfering with the frequencies used in the network. The most important techniques belonging to this category have been overviewed in Mpitziopoulos et al. (2009), and are often based on Frequency-Hopping Spread Spectrum (FHSS) (Pickholtz et al., 1982), that is, a method that selects a different carrier from the available frequency channels, in accordance to an algorithm shared by the receiver and transmitter device. However, physical-layer approaches are not actually capable to fundamentally neutralize jamming attacks. Conversely, cyber solutions assume the adversary as always able to interfere at the physical layer with regular transmissions in the network. Hence, cyber solutions contrast jamming attacks by means of appropriate security schemes. Most of cyber countermeasures are specialized to address constant jamming (Cagalj et al., 2007; Raymond and Midkiff, 2008; Xu et al., 2004; Xu et al., 2007). Instead, only a few solutions have been specifically designed to target selective jamming attacks. For instance, Wood et al. (2007) describe Defeating Energy-Efficient JAMming in IEEE 802.15.4-based wireless networks (DEEJAM), that is, a MAC protocol that provides protection against selective jamming attacks mounted by means of hardware supporting IEEE 802.15.4. In principle, DEEJAM tries to hide packets from an adversary jammer node, in order to evade its search and thus limiting the impact due to packets that are corrupted anyway. However, DEEJAM is specifically tailored to IEEE 802.15.4 networks, and results in a considerable computational overhead and energy consumption. Furthermore, Ashraf et al. (2012) proposed the low-overhead framework Jam-Buster, which leverages equal size of packets, multiblock payloads, and randomization wake up time of devices. By doing so, it tends to reduce predictability of transmission times on network devices and to eliminate differentiation of packet types. As a consequence, the adversary has to transmit additional jamming signals, and hence is required to consume additional energy to remain effective, and is faster and easier to detect as source of the jamming attack. However, Jam-Buster does not fundamentally counteract the attack by means of an actual solution against jamming, but instead tries to make selective jamming less efficient and convenient to perform. Proano and Lazos (2012) consider a particular kind of selective jamming, where only specifically important types of packets are jammed upon their transmission, and proposes some techniques to mitigate the attack effects, based on cryptographic primitives. While this can be a good solution to counteract packet classification, it also requires that the packets in their entirety are encrypted, so preventing receiver devices from early aborting the reception of packets not addressed to them. In Daidone et al. (2014), the authors propose a solution that counteracts selective jamming in IEEE 802.15.4 networks and use the mechanism Guaranteed Time Slot (GTS). In the GTS mode, a central coordinator can allocate at most seven reserved time slots to sensor nodes in the network, at each superframe. The proposed solution addresses the GTS severe vulnerability to selective jamming previously described in Sokullu et al. (2009), and entirely relies on the central coordinator node, which computes and randomly changes the utilization pattern of GTS slots at each superframe. This makes it possible to reduce the effectiveness of the attack to 1/7, but at the same time makes the central coordinator a single point of failure. Moreover, the proposed countermeasure specifically considers the IEEE 802.15.4 standard and thus is not general. Finally, Tiloca et al. (2013, 2015) present JAMMY, a dynamic and distributed solution that counteracts selective jamming in general TDMA wireless networks. In principle, JAMMY permutes the slot utilization pattern of network devices in a random way, at each superframe. It follows that the slots associated with every network device unpredictably change on a superframe basis. As a consequence, the adversary has the only option left to jam slots picked at random, hoping to guess the ones that the intended victim device uses for transmission at that superframe. In case only one slot per device is used at every superframe, then a successful selective jamming attack has a probability of 1/N, given N the number of slots composing the superframe. More important, JAMMY does not rely on any central entity and is totally distributed, that is, every network device determines the slots to use for transmission in the next superframe in an autonomous way (i.e., with no data exchange with other devices) and in a consistent fashion (i.e., with no resulting collisions with other devices). Furthermore, JAMMY is dynamic, since multiple devices can join and leave the network at any time. Finally, it is in principle usable in any TDMA wireless network, regardless the specific technology.
8.3.6 Intrusion Detection Systems and Firewalls
Although communication security can protect against attacks that target confidentiality and integrity of sensitive data, there are a number of attacks aimed at disrupting sensor networks as a whole (Karlof and Wagner, 2003), such as DoS attacks. Especially for mission-critical networks, it is therefore necessary to adopt countermeasures against such kinds of attacks.
There are many approaches that can protect sensor networks against DoS attacks, by detecting and possibly counteracting intrusions and other anomalies. These intrusion detection systems (IDS) for sensor networks can be categorized as watchdog-based where a designated component is used for the detection of selfish nodes and malicious attackers (Marti et al., 2000; Rong et al., 2011); signature or rule-based that detect known types of intrusions by recognizing bad patterns (da Silva et al., 2005; Bhuse and Gupta, 2006); anomaly-based that detects deviations from a model of normal or good behavior (Onat and Miri, 2005; Loo et al., 2006); or cluster-based detection where a group of nodes elect a leader that participates in the detection process (Lazos et al., 2005; Rong et al., 2011). These conventional approaches target wireless sensor networks and are not directly applicable in the IoT. In fact, they assume that no central controller or management entity is available, messages within the sensor network are not secured, and nodes are not globally identifiable. Unlike a traditional sensor network, a 6LoWPAN network includes a 6LoWPAN Border Router (6BR) that is always reachable, sensor nodes are globally identified by means of an IPv6 address, and communication security is a fundamental requirement to fulfill. In addition, building an IDS that is suitable to the IoT remains a very challenging task, because 6LoWPAN devices are supposed to be globally reachable, are connected through lossy wireless links, are mostly resource-constrained units, and use not well tested new IoT protocols, for example, CoAP, 6LoWPAN, and RPL.
By exploiting these opportunities and threats, an IDS suitable to the IoT named SVELTE has been developed (Raza et al., 2013). SVELTE primarily defends against routing attacks against 6LoWPAN networks running the RPL protocol. A crucial decision in an IDS design concerns the placement of IDS modules in the network. SVELTE is a hybrid system where heavyweight detection modules are hosted in a 6BR, and lightweight notification functions are added in sensor nodes. SVELTE has two centralized modules hosted in 6BR: (i) the 6LoWPAN Mapper (6Mapper) that collects RPL-specific information from individual sensor nodes and rebuilds the RPL network in the 6BR and (ii) detection modules that analyze the mapped data and then perform the actual intrusion detection. The module 6Mapper has a corresponding function in each individual node that provides the mapping information to the 6BR.
Although SVELTE can protect 6LoWPAN networks against in-network routing attacks, it is fundamental that the sensor devices are safeguarded against global, much powerful, intruders. For example, a host on the Internet can easily perform DoS attacks aimed to deplete a sensor node's limited resources. A firewall is typically used to screen messages from Internet hosts destined to local area networks. For IoT deployments where end-to-end message integrity and confidentiality is enforced between a sensor device and a host on the Internet, a firewall cannot scrutinize the encrypted contents. SVELTE features a distributed mini-firewall for 6LoWPAN networks. Both the 6BR and each constrained node have a firewall module. In addition to offering classic blocking functionalities against external attackers specified by a system administrator, the firewall can filter and block malicious external hosts as notified by the legitimate nodes in the 6LoWPAN network in real time.
8.4 Conclusion
This chapter has overviewed the most notable security protocols and technologies currently available for adoption in the IoT, at different layers of the typical communication stack. Furthermore, this chapter has discussed specific security issues in the IoT and solutions to address them leveraging recent research and standardization efforts. More work is expected to be carried out and further challenges must be taken to achieve a de facto secure IoT, and ultimately pave the way to its pervasive and wide adoption. The following trends and topics are especially going to play a crucial role in the immediate research and standardization agenda about security in the IoT.
First, more and more application scenarios require explicit support for secure group communication, built-in at different stack layers. This encompasses both actual message protection and management of security material, and is expected to focus especially at the application layer (through approaches based on object-security) and at the network layer (through the IPsec and IKEv2 protocols). Second, a comprehensive set of profiles for the IoT has to be specified, in order to define how to take benefit of authorization frameworks based on OAuth 2.0, both for handling the actual authorized access to remote resources and for coassisting the contextual establishment of secure channels with IoT resource servers. Finally, novel approaches are required to improve robustness of IoT units against denial-of-services attacks aimed at thwarting their availability and even exhausting their power resources. These approach should better leverage context-aware information and be adaptive to mutable attack conditions.
Last but not the least, these open issues require efficient solutions that display a sustainable impact on performance and user experience, and that can be realistically deployed and easily maintained even in large-scale, highly dynamic deployments of resource-constrained devices.
References
- Ashraf, F., Hu, Y.-C., and Kravets, R. H. (2012) Bankrupting the jammer in WSN. The IEEE 9th International Conference on Mobile Adhoc and Sensor Systems, 317–325.
- Bhattasali, T. and Chaki, R. (2012) AMC Model for Denial of Sleep Attack Detection. Journal of Recent Research Trends (JRRT). doi: arXiv:1203.1777v1.
- Bhuse, V. and Gupta, A. (2006) Anomaly intrusion detection in wireless sensor networks. Journal of High Speed Networks, Special issue on trusted internet workshop (TIW), 15(1), 33–51.
- Bluetooth Special Interest Group. (2014) Bluetooth Specification - Version 4.2
- Bluetooth Special Interest Group. (2016) Internet Protocol Support Profile: Bluetooth Specification.
- Bormann, C. (2014) 6LoWPAN-GHC: Generic Header Compression for IPv6 over Low-Power Wireless Personal Area Networks (6LoWPANs), RFC 7400, Internet Engineering Task Force.
- Bormann, C. (2015) Signature Authentication in the Internet Key Exchange Version 2 (IKEv2), RFC 7427, Internet Engineering Task Force.
- Bormann, C., Ersue, M., and Keranen, A. (2014) Terminology for Constrained-Node Networks. RFC 7228, Internet Engineering Task Force.
- Bormann, C. and Hoffman, P. (2013) Concise Binary Object Representation (CBOR), RFC 7049, Internet Engineering Task Force.
- Briscoe, B. (2010) Tunnelling of Explicit Congestion Notification. RFC 6040, Internet Engineering Task Force.
- Buennemeyer, T. K., Gora, M., Marchany, R. C., and Tront, J. G. (2007) Battery exhaustion attack detection with small handheld mobile computers. The 2007 IEEE International Conference on Portable Information Devices (PORTABLE 2007), 1–5.
- Cagalj, M., Capkun, S., and Hubaux, J.-P. (2007) Wormhole-based antijamming techniques in sensor networks. IEEE Transactions on Mobile Computing, 6, 100–114.
- Cheung, L., Cooley, J. A., Khazan, R., and Newport, C. (2007) Collusion-Resistant Group Key Management Using Attribute-Based Encryption, International Association for Cryptologic Research.
- Chorzempa, M., Park, J.-M., and Eltoweissy, M. (2005) SECK: survivable and efficient clustered keying for wireless sensor networks. IEEE International Performance, Computing, and Communications Conference 2005, 453–458.
- Cooper, D., Santesson, S., Farrell, S., Boeyen, S., Housley, R., and Polk, W. (2008) Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile. RFC 5280, Internet Engineering Task Force.
- da Silva, A. P. R., Martins, M. H. T., Rocha, B. P. S., Loureiro, A. A. F., Ruiz, L., Linnyer, B., and Wong, H. C. (2005) Decentralized intrusion detection in wireless sensor networks. The 1st ACM International Workshop on Quality of Service and Security in Wireless and Mobile Networks, 16–23.
- Daidone, R., Dini, G., and Tiloca, M. (2011) On experimentally evaluating the impact of security on IEEE 802.15.4 networks. The 3rd International Workshop on Performance Control in Wireless Sensor Networks (PWSN 2011), 20–25.
- Daidone, R., Dini, G., and Tiloca, M. (2014) A solution to the GTS-based selective jamming attack on IEEE 802.15.4 networks. Wireless Networks, 20(5), 1223–1235.
- Dierks, T. and Rescorla, E. (2008) The Transport Layer Security (TLS) Protocol Version 1.2. RFC 5246, Internet Engineering Task Force.
- Dini, G. and Savino, I. M. (2011) LARK: a lightweight authenticated rekeying scheme for clustered wireless sensor networks. ACM Transactions on Embedded Computing Systems, 10(4), 1–35.
- Dini, G. and Tiloca, M. (2013) HISS: a highly scalable scheme for group rekeying. The Computer Journal, 56(4), 508–525.
- Eronen, P. and Tschofenig, H. (2005) Pre-Shared Key Ciphersuites for Transport Layer Security (TLS). RFC 4279, Internet Engineering Task Force.
- Ertekin, E., Jasani, R., Christou, C., and Bormann, C. (2010) Integration of Robust Header Compression over IPsec Security Associations. RFC 5856, Internet Engineering Task Force.
- Fan, J., Judge, P., and Ammar, M. H. (2002) HySOR: group key management with collusion-scalability tradeoffs using a hybrid structuring of receivers. IEEE 2002 International Conference on Computer Communications and Networks, 196–201.
- Fielding, R. T. and Reschke, J. (2014a) Hypertext Transfer Protocol (HTTP/1.1): Message Syntax and Routing. RFC 7230, Internet Engineering Task Force.
- Fielding, R. T. and Reschke, J. (2014b) Hypertext Transfer Protocol (HTTP/1.1): Semantics and Content. RFC 7231, Internet Engineering Task Force.
- Gehrmann, C., Tiloca, M., and Höglund, R. (2015) SMACK: short message authentication ChecK against battery exhaustion in the Internet of Things. IEEE International Conference on Sensing Communication and Networking 2015 (SECON 2015), 274–282.
- Gu, Q., Liu, P., Lee, W.-C., and Chu, C.-H. (2009) KTR: an efficient key management scheme for secure data access control in wireless broadcast services. IEEE Transactions on Dependable and Secure Computing, 6(3), 188–201.
- Hardt, D. (2012) The OAuth 2.0 Authorization Framework. RFC 6749, Internet Engineering Task Force.
- Hui, J. W. and Thubert, P. (2011) Compression Format for IPv6 Datagrams over IEEE 802.15.4-Based Networks. RFC 6282, Internet Engineering Task Force.
- IEEE Computer Society. (2011) IEEE Standard for Local and Metropolitan Area Networks, Part 15.4: Low-Rate Wireless Personal Area Networks (LR-WPANs).
- IEEE Computer Society. (2012) 802.15.4e-2012 - IEEE Standard for Local and Metropolitan Area Networks–Part 15.4: Low-Rate Wireless Personal Area Networks (LR-WPANs) Amendment 1: MAC sublayer.
- Jankiewicz, E., Loughney, J., and Narten, T. (2011) IPv6 Node Requirements. RFC 6434, Internet Engineering Task Force.
- Jones, M. B. (2017) Using RSA Algorithms with CBOR Object Signing and Encryption (COSE) Messages, RFC8230, Internet Engineering Task Force.
- Karlof, C. and Wagner, D. (2003) Secure routing in wireless sensor networks: attacks and countermeasures. Ad Hoc Networks, 1(2), 293–315.
- Kaufman, C., Hoffman, P., Nir, Y., Eronen, P., and Kivinen, T. (2014) Internet Key Exchange Protocol Version 2 (IKEv2). RFC 7296, Internet Engineering Task Force.
- Kent, S. and Seo, K. (2005) Security Architecture for the Internet Protocol. RFC 4301, Internet Engineering Task Force.
- Keoh, S., Kumar, S., Garcia-Morchon, O., Dijk, E., and Rahman, A. (2014) DTLS-based Multicast Security in Constrained Environments, Internet Engineering Task Force.
- Kumar, S. and Struik, R. (2015) Transport-layer Multicast Security for Low-Power and Lossy Networks (LLNs), C Internet Engineering Task Force.
- Lazos, L., Liu, S., and Krunz, M. (2009) Mitigating control-channel jamming attacks in multi-channel ad hoc networks. The second ACM conference on Wireless network security, 169–180.
- Lazos, L., Poovendran, R., Meadows, C. A., Syverson, P. F., and Chang, L. W. (2005) Preventing wormhole attacks on wireless ad hoc networks: a graph theoretic approach. IEEE 2005 Wireless Communications and Networking Conference, vol. 2, 1193–1199.
- Loo, C. E., Ng, M. Y., Leckie, C., and Palaniswami, M. (2006) Intrusion detection for routing attacks in sensor networks. International Journal of Distributed Sensor Networks, 2(4), 313–332.
- Lu, Z., Wang, W., and Wang, C. (2014) Modeling, evaluation and detection of jamming attacks in time-critical wireless applications. IEEE Transactions on Mobile Computing, 13(8), 1746–1759.
- Marti, S., Giuli, T. J., Lai, K., and Baker, M. (2000) Mitigating routing misbehavior in mobile ad hoc networks. In the 6th annual international conference on mobile computing and networking (MobiCom '00), vol. 6, 255–265.
- Martin, T., Hsiao, M., Ha, D., and Krishnaswami, J. (2004) Denial-of-service attacks on battery-powered mobile computers. The Second IEEE International Conference on Pervasive Computing and Communications (PERCOM 2004), 309–318.
- Migault, D. and Guggemos, T. (2015) Implicit IV for AES-CBC, AES-CTR, AES-CCM and AES-GCM, Internet Engineering Task Force.
- Migault, D. and Guggemos, T., and Bormann, C. (2017) ESP Header Compression and Diet-ESP, draft-mglt-ipsecme-diet-esp-05 (work in progress), Internet Engineering Task Force.
- Mpitziopoulos, A., Gavalas, D., Konstantopoulos, C., and Pantziou, G. (2009) A survey on jamming attacks and countermeasures in WSNs. IEEE Communications Surveys Tutorials, 11(4), 42–56.
- Mustafa, H., Zhang, X., Liu, Z., Xu, W., and Perrig, A. (2012) Jamming-resilient multipath routing. IEEE Transactions on Dependable and Secure Computing, 9(6), 852–864.
- National Institute of Standards and Technology. (2001) Federal Information Processing Standards, Specification for the Advanced Encryption Standard (AES).
- Nieminen, J., Savolainen, T., Isomaki, M., Patil, B., Shelby, Z., and Gomez, C. (2015) IPv6 over BLUETOOTH(R) Low Energy, RFC 7668, Internet Engineering Task Force.
- Onat, I. and Miri, A. (2005) An intrusion detection system for wireless sensor networks. In the IEEE 2005 International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob 2005), 253–259.
- Pickholtz, R. L., Schilling, D. L., and Milstein, L. B. (1982) Theory of spread-spectrum communications: a tutorial. IEEE Transactions on Communications, 30(5), 855–884.
- Proano, A. and Lazos, L. (2012) Packet-hiding methods for preventing selective jamming attacks. IEEE Transactions on Dependable and Secure Computing, 9(1), 101–114.
- Rafaeli, S. and Hutchison, D. (2003) A survey of key management for secure group communication. ACM Computing Surveys, 35(3), 309–329.
- Rahman, A. and Dijk, E. (2014) Group Communication for the Constrained Application Protocol (CoAP), RFC 7390, Internet Engineering Task Force.
- Raymond, D. R. and Midkiff, S. F. (2007) Clustered adaptive rate limiting: defeating denial-of-sleep attacks in wireless sensor networks. IEEE 2007 Military Communications Conference (MILCOM 2007), 1–7.
- Raymond, D. R. and Midkiff, S. F. (2008) Denial-of-service in wireless sensor networks: attacks and defenses. IEEE Pervasive Computing, 7(1), 74–81.
- Raymond, D. R., Marchany, R. C., Brownfield, M. I., and Midkiff, S. F. (2009) Effects of denial-of-sleep attacks on wireless sensor network MAC protocols. IEEE Transactions on Vehicular Technology, 58(1), 367–380.
- Raza, S., Duquennoy, S., Höglund, J., Roedig, U., and Voigt, T. (2014) Secure communication for the Internet of Things: a comparison of link-layer security and IPsec for 6LoWPAN. Journal of Security and Communication Networks, 7(12), 2654–2668.
- Raza, S., Duquennoy, S., and Selander, G. (2016) Compression of IPsec AH and ESP Headers for 6LoWPAN Networks.
- Raza, S., Duquennoy, S., Voigt, T., and Roedig, U. (2011) Demo abstract: securing communication in 6LoWPAN with compressed IPsec. The 7th IEEE International Conference on Distributed Computing in Sensor Systems (DCOSS '11).
- Raza, S., Wallgren, L., and Voigt, T. (2013) SVELTE: real-time intrusion detection in the Internet of Things. Ad Hoc Networks, 11(8), 2661–2674.
- Rescorla, E. and Modadugu, N. (2012) Datagram Transport Layer Security Version 1.2. RFC 6347, Internet Engineering Task Force.
- Rong, C., Eggen, S., and Cheng, H. (2011) An efficient intrusion detection scheme for wireless sensor networks. Secure and Trust Computing, Data Management, and Applications, Springer, 116–129.
- Sandlund, K., Pelletier, G., and Jonsson, L.-E. (2010) The RObust Header Compression (ROHC) Framework. RFC 5795, Internet Engineering Task Force.
- Schaad, J. (2016) CBOR Encoded Message Syntax: Additional Algorithms, Internet Engineering Task Force.
- Schaad, J. (2017) CBOR Object Signing and Encryption (COSE), RFC8152, Internet Engineering Task Force.
- Seitz, L., Selander, G., Wahlstroem, E., Erdtman, S., and Tschofenig, H. (2018) Authentication and Authorization for Constrained Environments (ACE), draft-ietf-ace-oauth-authz-10 (work in progress), Internet Engineering Task Force.
- Selander, G., Mattson, J., Palombini, F., and Seitz, L. (2018) Object Security for Constrained RESTful Environments (OSCORE), draft-ietf-core-object-security-09 (work in progress), Internet Engineering Task Force.
- Shelby, Z., Hartke, K., and Bormann, C. (2014) Constrained Application Protocol (CoAP). RFC 7252, Internet Engineering Task Force.
- Shirey, R. W. (2007) Internet Security Glossary, Version 2. FYI 36, RFC 4949, Internet Engineering Task Force.
- Sokullu, R., Korkmaz, I., and Dagdeviren, O. (2009) GTS Attack: an IEEE 802.15.4 MAC layer attack in wireless sensor networks. International Journal On Advances in Internet Technologies, 2(1), 104–114.
- Stajano, F. and Anderson, R. J. (1999) The resurrecting duckling: security issues for ad-hoc wireless networks. The 7th International Workshop on Security Protocols, SpringerVerlag, 172–194.
- Stojanovski, S. and Kulakov, A. (2015) Efficient attacks in industrial wireless sensor networks. ICT Innovations 2014, vol. 311, Advances in Intelligent Systems and Computing, Springer International Publishing, 289–298.
- Tiloca, M. (2014) Efficient Protection of Response Messages in DTLS-Based Secure Multicast Communication. SIN 2014, Glasgow, UK, 466–472.
- Tiloca, M. and Dini, G. (2016) GREP: a Group REkeying protocol based on member join history, IEEE ISCC 2016, Messina (Italy), 326–333.
- Tiloca, M., De Guglielmo, D., Dini, G., and Anastasi, G. (2013) SAD-SJ: a self-adaptive decentralized solution against selective jamming attack in wireless sensor networks. IEEE ETFA 2013, Cagliari (Italy), 1–8.
- Tiloca, M., De Guglielmo, D., Dini, G., Anastasi, G., and Das, S. K. (2017) JAMMY: a distributed and dynamic solution to selective jamming attack in TDMA WSNs. IEEE Transactions on Dependable and Secure Computing, 14(4), 392–405.
- Tiloca, M., Gehrmann, C., and Seitz, L. (2017) On improving resistance to denial of service and key provisioning scalability of the DTLS handshake. International Journal of Information Security, 16(2), 173–193.
- Tiloca, M., Nikitin, K., and Raza, S. (2017) Axiom: DTLS-based secure IoT group communication. ACM Transactions on Embedded Computing Systems, 16(3), 1–29.
- Tiloca, M., Raza, S., Nikitin, K., and Kumar, S. (2015) Secure Two-Way DTLS-Based Group Communication in the IoT, Internet Engineering Task Force.
- Tschofenig, H. and Fossati, T. (2016) Transport Layer Security (TLS)/Datagram Transport Layer Security (DTLS) Profiles for the Internet of Things. RFC 7925, Internet Engineering Task Force.
- Wallner, D., Harder, E., and Agee, R. (1999) Key Management for Multicast: Issues and Architectures. RFC 2627, Internet Engineering Task Force.
- Wang, W., Ma, J., and Moon, S.-J. (2008) CRMS: A collusion-resistant matrix system for group key management in wireless networks. IEEE 2008 International Conference on Communications, 1551–1555.
- Weis, B., Gross, G., and Ignjatic, D. (2008) Multicast Extensions to the Security Architecture for the Internet Protocol. RFC 5374, Internet Engineering Task Force.
- Winter, T., Thubert, P., Brandt, A., Hui, J. W., Kelsey, R., Levis, P., Pister, K., Struik, R., Vasseur, J.P., and Alexander, R. K. (2012) RPL: IPv6 Routing Protocol for Low-Power and Lossy Networks. RFC 6550, Internet Engineering Task Force.
- Wong, C. K., Gouda, M., and Lam, S. S. (2000) Secure group communications using key graphs. IEEE/ACM Transactions on Networking, 8(1), 16–30.
- Wood, A. D., Stankovic, J. A., and Zhou, G. (2007) DEEJAM: defeating energy-efficient jamming in IEEE 802.15.4-based wireless networks. Proceedings of the 4th Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks, 60–69.
- Wouters, P., Tschofenig, H., Gilmore, J., Weiler, S., and Kivinen, T. (2014) Using Raw Public Keys in Transport Layer Security (TLS) and Datagram Transport Layer Security (DTLS). RFC 7250, Internet Engineering Task Force,
- Xu, W., Ma, K., Trappe, W., and Zhang, Y. (2006) Jamming sensor networks: attack and defense strategies. IEEE Network, 20(3), 41–47.
- Xu, W., Trappe, W., and Zhang, Y. (2007) Channel surfing: defending wireless sensor networks from interference. Proceedings of the 6th International Conference on Information Processing in Sensor Networks, 499–508.
- Xu, W., Trappe, W., Zhang, Y., and Wood, T. (2005) The feasibility of launching and detecting jamming attacks in wireless networks. The 6th ACM International Symposium on Mobile Ad Hoc Networking and Computing, 46–57.
- Xu, W., Wood, T., Trappe, W., and Zhang, Y. (2004) Channel surfing and spatial retreats: defenses against wireless denial of service. The 3rd ACM Workshop on Wireless Security (WiSe 2004), 80–89.
- Younis, M. F., Ghumman, K., and Eltoweissy, M. (2006) Location-aware combinatorial key management scheme for clustered sensor networks. IEEE Transactions on Parallel and Distributed Systems, 17(8), 865–882.
