19
The Internet of Flying Things
Daniel Fernando Pigatto1, Mariana Rodrigues2, João Vitor de Carvalho Fontes3, Alex Sandro Roschildt Pinto4, James Smith5 and Kalinka Regina Lucas Jaquie Castelo Branco2
1Graduate Program in Electrical and Computer Engineering (CPGEI), Federal University of Technology Paraná (UTFPR), Curitiba, Paraná, Brazil
2Institute of Mathematics and Computer Sciences (ICMC), University of São Paulo (USP), São Carlos, São Paulo, Brazil
3São Carlos School of Engineering (EESC), University of São Paulo (USP), São Carlos, São Paulo, Brazil
4Federal University of Santa Catarina (UFSC), Blumenau, Santa Catarina, Brazil
5Computer Science and Creative Technologies (FET), University of the West of England (UWE), Bristol, England, United Kingdom
19.1 Introduction
Unmanned aircraft systems have received a lot of attention lately, especially due to their flexibility and reduced acquisition costs. However, in many regions, legislation issues have emerged that curtail their operation in critical environments. In response to well-reported instances, it seems likely that in many countries “no-fly” zones will be established around critical areas, such as airports (where accidental “drone-strikes” could pose a threat to jet planes similar to “bird-strikes”), prisons (where cases have been reported of drones being used to transport contraband goods in to prisoners), and military/confidential areas (where government is combating drones with trained eagles). Security threats from terrorist groups also pose a risk to key infrastructure. In the future, it seems likely that international consensus may arise around certain areas (e.g., commercial airports) but the picture is likely to remain fluid for some time. Meanwhile, significant research efforts are exploring the current capabilities of UAVs, and their potential for autonomous action beyond the line of sight of a dedicated operator, which is likely to fuel further debate and legislation.
The relatively recent concept of Internet of Things (IoT), which consists of a new form of connecting and sharing resources among devices, has been considered as a candidate for potential integration with unmanned aircraft. Such collaboration may provide a new degree of freedom for old applications and a completely new spectrum of applications.
This chapter reviews the main characteristics of the Internet of Flying Things and how the term is related to unmanned aircraft systems and the Internet of Things. The chapter describes how this new concept solves known issues, but also introduces different challenges to the design of systems.
19.2 Flying Things
The popularity and flexibility of embedded systems have introduced new applications in vehicular segments such as cars, drones, and maritime underwater or surface vehicles in recent decades. This section outlines the main concepts of the aerial segment under a new name, flying thing, encompassing not only a limited range of drones, but any type and/or classification of unmanned aircraft system.
19.2.1 Unmanned Aircraft Systems
Unmanned Aerial vehicles (UAVs), popularly known as drones, are considered enablers of a completely new way of performing tasks that were previously either unreachable or high cost, so fulfilling gaps in many modern applications (Marshall et al., 2015). As shown in Figure 19.1, these aircraft can be of many different sizes and shapes, and missions can be accomplished by either a single or multiple UAVs. This richness of form allows them to be used in diverse applications such as search and rescue, surveillance missions, and goods delivery.

Figure 19.1 Examples of UAVs. (a) A drone. (b) A remotely piloted aircraft. (c) A balloon.
UAVs are usually considered as part of a bigger unmanned aircraft system (UAS) that includes all the needed elements to accomplish a mission (Fahlstrom and Gleason, 2012). The components of the UAS may vary according to UAV type, size, and mission, but typically include the ground control station (GCS), the communications subsystem, and the safety and recovery mechanisms.
Creating a UAS with multiple cooperating UAVs brings additional, highly demanding connectivity requirements and in order to meet them, a new network approach has emerged, the Flying Ad Hoc Network.
19.2.2 Flying Ad Hoc Networks
Communication is a crucial aspect of, and one of the biggest challenges in, the design of multiple vehicle systems (Bouachir et al., 2014; Chung et al., 2011). In a UAS, there are three main types of communications: (a) internal machine communications (IMC), which encompasses any communication between UAVs' internal modules or devices, such as the automatic pilot or cameras; (b) machine-to-machine communications (M2M), which encompasses communications among UAVs; and (c) machine-to-infrastructure communications (M2I), which encompasses the communication between UAVs and the network infrastructure (which can be, for instance, a ground control station or a satellite (Frew and Brown, 2009), or even a combination of both).
In the simplest scenario, all vehicles are directly connected to a common infrastructure, and this can act as an intermediary for all communications between them. However, this strategy has several problems. First, each vehicle must be equipped with expensive and complex hardware in order to perform the long-distance communication with the control station or satellite. Second, many factors may compromise communication reliability such as changing environmental conditions, the high mobility of vehicles, different terrain topologies, or obstacles. Finally, the typical use of a ground control station (GCS) to provide the communication infrastructure limits the mission target locations to the GCS coverage area, since beyond that vehicles disconnect from the network, and become unreachable.
The implementation of an ad hoc network connecting all vehicles is one of the most feasible alternatives to infrastructure-based communication. An ad hoc network is composed of nodes that also function as routers, forming a temporary network with no fixed topology or centralized administration (Sarkar et al., 2008). This approach increases the mission target area, since communications between vehicles and the GCS can be routed through other vehicles in a series of hops. Also, even if there is no connection to a GCS, the nodes can form an ad hoc network to share information or work in cooperation.
Ad hoc networks are classified according to their implementation, utilization, communication, and mission objectives. If the nodes that compose an ad hoc network are mobile, the network is classified as MANET (Mobile Ad hoc NETwork). For vehicle-specific applications, MANETs are subdivided into UANET (Underwater Ad hoc NETwork) for aquatic vehicles, VANET (Vehicular Ad hoc NETwork) for terrestrial vehicles, or FANET (Flying Ad hoc NETwork) for aerial vehicles (Bekmezci et al., 2013; Sahingoz, 2013), as illustrated in Figure 19.2.
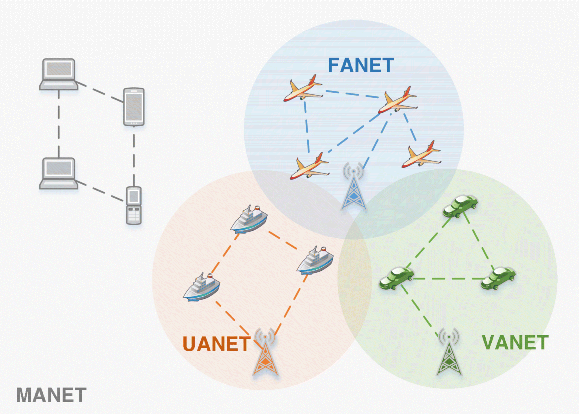
Figure 19.2 Relationships between different types of Mobile Ad Hoc Networks (MANET): Underwater Ad Hoc Networks (UANET), Vehicular Ad Hoc Networks (VANET), and Flying Ad Hoc Networks (FANET). (Figure adapted from Pigatto et al. (2014).)
Each type of vehicular network faces different, unique challenges: For instance, a UANET must deal with an underwater transmission medium and VANETs often encounter unexpected road obstacles. However, it has been recognized that FANETs have to address more challenging issues than other ad hoc networks (Bekmezci et al., 2013; Sahingoz, 2013), because of the following specific characteristics:
- Higher Node Mobility. FANET nodes typically have higher mobility than those in other types of MANET. As a result, a FANET's network topology can change more frequently, which increases the overhead caused by connecting and routing operations.
- Multiple Connections. In many applications, the nodes in FANETs collect environmental data and then retransmit it to the control station, similarly to wireless sensor networks (WSN) (Rieke et al., 2011). Therefore, FANETs have to manage multiple communications between UAVs and monitoring stations, as well as providing support to peer-to-peer connections among UAVs.
- Very Low Node Density. Typical distances among nodes in FANETs are usually longer than in MANETs and VANETs (Clapper et al., 2007); thus, the communication range in FANETs must also be greater than in other networks. This imposes more demanding requirements for radio links and other hardware elements.
- Heterogeneity. UAV systems may include heterogeneous sensors, and each of them may require different strategies for data distribution.
- Obstacles. Due to the higher node mobility, obstacles may randomly block links among UAVs, which must be addressed in order to provide different temporary communication paths, avoiding the disconnection of nodes.
19.2.3 Flying Things: Unmanned Aerial Vehicles and More
Common to the many different visions for the Internet of Things is the ubiquitous presence of everyday objects equipped with identifying, sensing, networking, and processing capabilities that communicate with each other to achieve a common goal (Atzori et al., 2010; Whitmore et al., 2015). In the context of emerging network models such as IoT, a new name for UAVs starts to take place. As a Flying Thing, UAVs (and any other elements able to fly, like autonomous or nonautonomous air vehicles) can be integrated into a network of physical interactive objects that are able to communicate with other internet-enabled devices and systems. This integration has been called the Internet of Flying Things and has the potential of addressing some of the issues in unmanned systems, as well as introducing new, powerful applications.
19.3 The Internet of Flying Things
Following the tendency of our increasingly connected world, UAVs are likely to be integrated with other elements and systems to perform missions with higher complexity. The new Internet of Flying Things (IoFT) gives a new degree of freedom to unmanned aircraft systems, broadening the limits of their missions and enabling new applications, by increasing their connectivity, improving collaboration and cooperation between systems, and also enabling up-to-date data provision.
Although the new Internet of Flying Things is applicable in several different segments, one particular highlight is the affordance it offers in environments that are currently badly served by existing (wired) infrastructures, such as rural areas or poor communities. These examples are big motivators for the creation of solutions merging the flexible adaptive IoT with fast, cheap UAVs, which together are likely to provide high quality services for end users in remote areas. However, an important concept takes place while considering hard-to-reach areas—fog computing. Close relations can be established among fog computing, cloud computing, and Internet-based models such as the Internet of Flying Things. These concepts will be presented in the next subsection.
19.3.1 Fog and Cloud Computing
There are two main trends shaping our networking today: cloud computing and the proliferation of mobile computing. Around 90% of global Internet users now rely on cloud-based service, and that is mainly due to the fact that smartphones worldwide shipment overtook that of PCs in 2011 (Luan et al., 2015). An emerging wave of Internet deployments, such as the notable IoT, requires not only mobility support and geodistribution, but also location awareness and low latency.
Cloud computing is a key concept for the provision of IoFT. A cloud is an on-demand computing model composed of autonomous, networked IT (hardware and/or software) resources (Hassan et al., 2012). As most of the communication managed by IoFT is transmitted via IoT infrastructure, quality of service (QoS) becomes an important aspect, which meets the same requirements of cloud computing. Service providers offer cloud services with predefined QoS terms based on the Internet as a set of managed scalable, easy-to-use, and inexpensive services to gather clients on a subscription basis (Hassan et al., 2012). Therefore, it is essential for the IoFT infrastructure to meet QoS requirements on the provision of services from and to the flying thing, since the criticality of its operations might be higher than ordinary fixed IoT elements. Moreover, some IoFT applications need real-time response, which is done by delegating computational tasks to the cloud, due to limited capacity of mobile devices (Luan et al., 2015). Such fact amplifies the necessity of assertive services provision.
On the other hand, in case of remote areas with limited or no internet connectivity, it would not be always possible to arbitrarily access cloud services with acceptable QoS response times and real-time requirements. However, some applications could still benefit from IoFT by temporarily working with local copies of data and services, imitating the structure of a cloud computing, and then allowing the provision of services that do not rely on frequent updates. This is the case where fog computing takes place as a key element for IoFT networks. Fog computing consists of a highly virtualized platform to compute, store, and provide networking services between end devices and traditional cloud computing data centers, which are typically, but not exclusively located at the edge of the network (Bonomi et al., 2012). On the IoFT perspective, for instance, a smart farm with limited access to the Internet could benefit from a fog infrastructure processing most of the data and services needed for the usual tasks, uploading and downloading only relevant and/or essential information to the Cloud.
As discussed in Chapter 4, cloud/fog computing characteristics have important intersections with IoT scenarios. The main requirements of the IoFT are met by fog computing due to following characteristics: (a) low latency and location awareness allowing the IoFT network to operate at least within a limited range and time, providing services and performing tasks and missions; (b) mobility, a main necessity of IoFT applications; (c) very large number of nodes, which meets the requirements of both IoT and IoFT networks; (d) predominant role of wireless access; (f) strong presence of streaming and real-time applications; and (g) heterogeneity (Bonomi et al., 2012).
A flying thing might play two different roles in an IoFT scenario supported by fog computing, as seen in Figure 19.3. The first is as processing units in a fog layer, serving as providers for the Internet of Flying Things. To give two examples, in remote or disaster areas where connectivity is hard to be achieved, a flexible mobile structure that could provide or extend fog services would be an important enabler. Equally, UAV's could have a role as fog providers in highly connected environments, where some applications might work well being offline for short or even long periods of time, reducing data usage, and creating batches of information to be uploaded to the cloud all-in-once. In a different role, UAVs could function as edge nodes (end users) benefiting from a fog infrastructure.

Figure 19.3 The UAV can be placed either in fog or IoT layers when it comes to remote areas applications.
19.3.2 Characteristics of the Internet of Flying Things
The IoFT is indeed flexible. This characteristic is important for the provision of almost every feature in such model. It helps increase overall cooperation and collaboration, is ready for real-time operations, is usually up-to-date due to the highly connected environment and easy access to the Internet, and is assisted by a powerful remote cloud and/or local fog structure. In terms of cost, since the IoFT merges the benefits of two well-known paradigms, namely, IoT and UAVs, which may vary from cheap to expensive commercial off-the-shelf products, there will be an affordable and adaptive solution for most needs.
Cooperation and collaboration are desired features for most of modern computing systems. Many modern applications distribute tasks and share information in real time, providing better results quickly. In particular, an IoT-ready environment is usually designed to be equipped with more than one way of acquiring data, interacting, and automating specific tasks (Ungurean et al., 2014; Andreev et al., 2015). Although IoT is a scalable model, its expansion can mean high costs for relatively small returns. If an environment does not expand easily, it might have its flexibility compromised, resulting in limited cooperation and collaboration. IoFT addresses this tension in different ways—such as by setting up UAVs in strategic areas serving as gateways, fog, or cloud data link providers, and also by being capable of replacing sensors and actuators in more active and inexpensive ways (for instance, if a traffic light fails, a flying thing might be used to temporarily replace its task). Moreover, real-time operations are also a priority of the model, since it can be reconfigured to meet requirements and provide the best connection to servers and services available locally or through the Internet.
The IoFT integration with IoT infrastructures achieved by strategically positioning UAVs helps the model to meet some key features. Linking to internet-based information processing can collate services from all around the world in real time, providing valuable up-to-date accurate information. This in turn can facilitate interactive decision-making in response to dynamic situations. Those decisions can be processed in powerful datacenters available as cloud providers. The net result is to allow more reliable and more adaptive missions, maximizing their potential benefits, or broadening their applicability.
Table 19.1 summarizes these IoFT features in comparison with UAVs and IoT paradigm. IoT and UAS segments are limited by their inherent infrastructure characteristics. Although they can be expanded, the setup cost, for instance, is a con that must be considered, especially if such infrastructure might end up being underused. In such case, the use of flexible flying things for sensing and actuating is an advantage.
Table 19.1 A comparison of available features of unmanned aircraft systems, Internet of Things, and the new Internet of Flying Things.
| Features | Internet of Things (IoT) | Unmanned aircraft systems (UAS) | Internet of Flying Things (IoFT) |
| Cooperation | Limited by IoT infrastructure | Limited by FANET infrastructure | Includes all the IoT and FANET infrastructure capabilities |
| Collaboration | Limited by IoT infrastructure | Limited by FANET infrastructure | Includes all the IoT and FANET infrastructure capabilities |
| Real-time operations | Limited to the network coverage | Limited to the actuation areas | Reduced limitations due to increased connectivity |
| Connectivity | Internet connected | Locally connected by a FANET | Highly connected—not just to the Internet, but also locally connected |
| Up-to-date data/services | Available | Weakly available | Available |
| Internet-based information processing | Available | Weakly available | Available |
| Interactive decision-making | Available | Available | Available with higher flexibility |
| Mission-assistive multisource information providers | Available | Weakly available | Available with higher variety of sources |
19.3.3 General Modern Applications of the Internet of Flying Things
UAVs and IoT are popular subjects that have gained attention due to their flexibility and low-cost achievements. The benefits of the Internet of Flying Things go beyond the traditional applications being seen on media press lately. The following paragraphs will present some examples of how applications could be taken to a new level by exploiting the flexibility of IoFT.
19.3.3.1 Applications in Emergency Situations
- Search and Rescue. In an emergency scenario with victims, flying things can detect and report the position of the victims in real time. This information can be coordinated with that from weather/traffic sensors providing an efficient rescue.
- First Aid and Supplies. Once the positions of the victims have been identified, flying things which carry first aid and supplies can be moved toward to the specific positions in order to help the victims, and this can be coordinated using information about the availability of useful resources/supplies in nearby locations. Moreover, if the victims were moving for any reason, the location information can be updated in real time. This update can be performed by a flying thing that detects the position and sends this information to the first aid supplier flying thing.
19.3.3.2 Applications in Smart Cities
- Surveillance. Flying things can be used to add additional capacity to existing systems for monitoring crowds or responding to emergency signals. For instance, in a smart city, people can be connected to the city's services via wearable technology; in a dangerous situation, a person may notify the infrastructure in several different ways, and trigger an appropriate action such as assigning a surveillance flying thing to monitor the area (see A in Figure 19.4).
- Traffic Monitoring. Although smart cities have devices and sensors to monitor the traffic, these devices are costly and might be unreliable, so coverage is not always complete. Flying things can be used in two ways when planning a smart city infrastructure: to provide flexible additional coverage that might be planned (for example, to monitor the occasional, but predictable high-traffic density around a sports arena) or unplanned (for example, following a traffic incident in an area that is not, or poorly covered by fixed sensors). Thus, flying things can be used to monitor these areas and help the car traffic management (see B in Figure 19.4).
- Commercial Package Delivery. Flying things provide a flexible resource for delivery services. They could be used both to augment vehicles for meeting existing demand types and also to generate new revenue streams for high-speed delivery in hard-to-access or congested areas (see C in Figure 19.4).
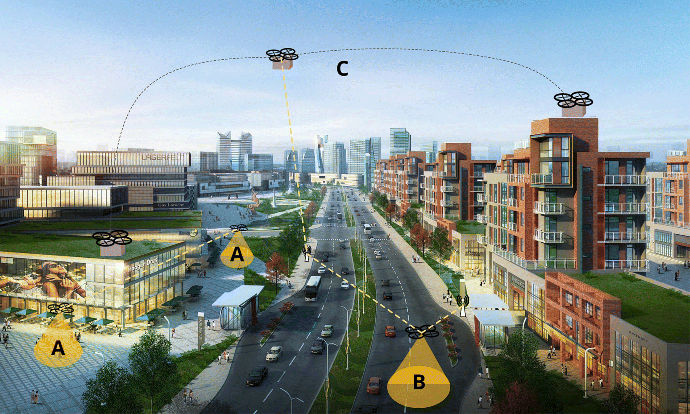
Figure 19.4 Smart city applications taken to the next level with IoFT. A: Surveillance, B: traffic monitoring, and C: commercial package delivery.
19.3.3.3 Applications in smart farms
- Surveillance. Considering that farms are private areas, they may be vulnerable to invasions. The use of flying things to monitor the farms' border might help the surveillance by reporting potential problems in real time using the IoT infrastructure of the smart farm. Moreover, the IoFT serves as a backend infrastructure to IoT-based applications (see A in Figure 19.5).
- Service Integration. Different tasks are required in smart farms, and this is expensive if each is implemented separately. A flexible flying thing can monitor crops, animals, spread products, load supplies, and other tasks. In particular, it can also be connected to other flying things through the Internet even with no line of sight. This feature can improve services in a smart farm by overcoming limitations of traditional communication media (see B in Figure 19.5).
- Identification of Fire or Other Issues. A crop can be damaged by several factors, such as wild animals, fire, and frost. Either through their own sensors or by collected data from fixed sensors, flying things may detect problems in crops (see C in Figure 19.5).
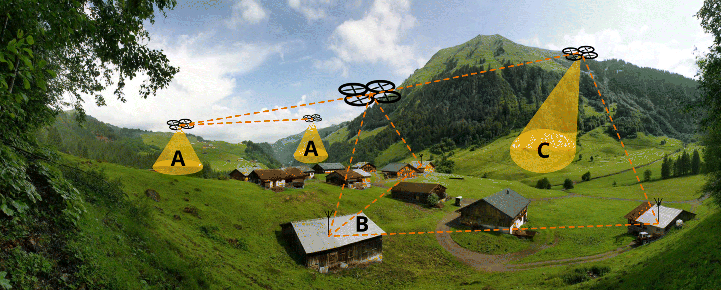
Figure 19.5 Smart farm applications taken to the next level with IoFT. A: Surveillance, B: services integration, and C: identification of fire or other issues.
19.3.3.4 Government Official Missions
- Border Surveillance. Considering the increasing globalization, countries are tending to protect their borders by different ways. Focusing on the improvement of automated surveillance, flying things can identify border crossings and follow illegal immigrants while sending location information in real time via Internet. Such information associated with sensors spread on the ground should provide more accurate results.
- Forest Fire Detection and Illegal Logging. Concerns about global warming are growing stronger every day. One of the causes is the reduction of forest areas around the planet due to fire and illegal logging. Manned aircraft are often used but expensive. Flying things may become a solution to increasing coverage and hence the possibility of identifying problems in real time, so possibly preventing major fires or helping apprehend illegal loggers.
19.3.4 Novel Applications of the Internet of Flying Things
FANETs are enablers of inter-UAV connectivity that simplify the cooperation and collaboration among flying things. However, they are not necessarily connected to the Internet since they operate over swarms of UAVs, which cooperate sharing resources and data in a local offline network. Taking the flying things to a new paradigm, such as IoFT, provides “wings” to the concept of FANETs and makes them more powerful. Imagine flying things geographically distant with no possible line of sight (LoS), but still sharing data, network resources, and services just like if they were all in the same local network. That becomes possible with the introduction of IoFT-oriented networks.
The Wide FANETs (WFANETs) merge the concept of FANETs with IoT, and take wide area networks (WAN) as an inspiration to benefit from all paradigms. A visual representation is seen in Figure 19.6, which illustrates a real scenario with WFANETs.
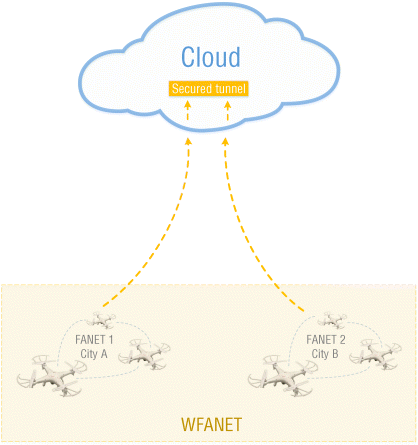
Figure 19.6 A Wide-FANET.
The main characteristic of ad hoc networks is the existence of at least one path to reach every single node in the network. It is usually possible if nodes are within a limited range and if there are strategic LoS links, guaranteeing that the main links will not be interrupted. The new concept of WFANETs benefits from the connection to an IoT infrastructure already available due to smart environments nearby (e.g., smart cities, smart roads, smart homes, smart farms, and even smart cars). Once connected to an infrastructure that can provide broadband Internet access to the local FANET, a tunnel can be created for information exchange and cooperation with remote FANETs. The act of connecting flying things from different geographical locations through a transparent cloud-based tunneling, providing the same features as a local FANET, creates a WFANET.
WFANETs allow for different approaches and applications. A good example is big events, for example, football matches, Olympic games, and concerts, which require high security in order to manage large crowds, monitor suspicious activities, manage ongoing events, and so on.
Another example of application improved by WFANETs is the pavement scanning for distress, helping the provision of better quality roads. A flying thing scanning roads may be helpful for spreading warnings to intelligent transportation systems, reducing car accident rates, improving security and safety services, and also providing information about possible trip delays and/or personal agenda-based notifications. Additional information such as weather conditions, for example, could also be integrated into the scenario, improving services provision.
By logical extension, one can envisage that the sensors carried on UAVs could also be considered as flying things in their own right, that happen to be colocated with a set of others on board. If these services become advertised through an automatic broker, many other agencies might choose to pay to access them. For example, a food retailer might choose to pick video streams from any UAV-mounted cameras that happened to be in the area if they could be used to predict and respond to incoming customer flows (see Figure 19.7).

Figure 19.7 Available cameras in the cloud can be accessed by end users as paid services.
Furthermore, the integration of flying things into smart environments allows improvements to the UAV's operation. For instance, GPS (global positioning system) location is a critical information that is essential for a flying thing. With the existence of an infrastructure to which the flying thing is connected, high accurate location information may be available, helping the UAV operate more precisely. Other sensors such as weather stations mounted on buildings might provide real-time data about flying conditions ahead on the flight path. Some security issues can also be solved with IoFT itself, such as GPS spoofing.
19.4 Challenges
We have already outlined some of the benefits to UAV systems from coupling to an IoT network of sensors, and even more benefits that could arise from adding flexible airborne sensing and networking to an IoT application. However, some security and safety concerns come from opening up the “closed-world” of a UAV system, which is discussed here. This section also highlights how the Internet of Flying Things can help solving old issues as well.
19.4.1 General Issues
The new Internet of Flying Things model combines the best of IoT and UAVs into one solution that inherits characteristics, but it also introduces new challenges that must be overcome. In short, these fall into three categories.
The first set of issues relates to public safety, and to ethical concerns around the collection and distribution of data. Other obvious concerns would be around snooping—either by physically capturing images or by moving into the proximity of local secure wireless networks. It seems likely that many countries will enact legislation requiring certification and authorization to fly UAVs and benefit from the possibilities of IoFT.
The second set of issues arises from a desire to avoid the past mistakes of the computing industry and lower the thresholds to engagement for key stakeholders, so that the entire population can reap the benefits of this technology. These issues are related to standardization, and must involve both the industry and governments. From a technical point of view, standardization is necessary to make all things actually able to “talk” to one another, instead of creating a “Babel Tower Effect” in which devices become split into disjoint subsets (for instance, all devices from the same manufacturer) that can only talk to others from the same subset. Hardware and software design must take into account limitations of memory, storage, processing capabilities, and power source. This is likely to lead to different solutions for flying objects being developed by different manufacturers, using various hardware architectures, platforms, and communication protocols. Thus, there is a pressing need for the emerging standards for communication and data transfer between devices to be implementable in highly resource-efficient algorithms. From a social and economic point of view, standardization will favor the entrance of small and medium companies in the market, stimulating entrepreneurship and competition, benefiting the final customer, and spreading the use of the technology.
The third set of issues that arises is mainly related to security and Big Data. The heterogeneity will also extend to the data being collected, since it is expected that IoT—and consequently IoFT—will bring a large amount of new, most likely nonstructured data. How and where (locally or remotely) this data will be stored and recovered following real time and security requirements will involve the use of Big Data techniques and technologies.
These considerations apply to a single IoFT device, but in many scenarios more than one device may be deployed. As the number of connected devices grows, addressing and managing all of them without prejudicing quality of service become a critical issue. This is compounded by the fact that new devices, offering or requesting new services can join the ad hoc network at any time. Hence, applications must be designed from the ground up to enable extensible services and operations. Moreover, IoFT and WFANETs have a common issue to deal with, which is the possible service unavailability regarding an Internet connection. This raises questions such as what measures should be taken if the LTE/3G/4G connection is lost without prejudicing the mission and data privacy?
19.4.2 Security Issues at Different Internet of Flying Things Conceptual Layers
In general, security challenges are big concerns of computing systems. There are several security issues that could exist in IoFT-based applications, which are mostly inherited from the underlying networks and technologies (e.g., UAS, IoT). The main security issues that could be imposed by the different network layers are listed as follows:
- Physical Layer. Both jamming and tampering attacks are known issues for this layer. Jamming is a well-known attack that causes interferences to the radio frequencies that network's nodes are using. It can interrupt the network if a single frequency is used throughout the network: at worst, interrupting communications with flying things; and at best causing excessive energy consumption. On the other hand, if an attacker can physically tamper nodes, a tampering attack takes place which damages, replaces, and electronically “interrogates” the nodes to acquire information (Sen, 2012). GPS spoofing attacks, which happen in this layer, consist in the use of a signal that is stronger than and mimics the attributes of a genuine GPS signal to take over a GPS receiver, have become more frequent. Such attacks can cause the aircraft to completely lose control, which is a very critical issue.
- Data Link Layer. Collision, exhaustion, and unfairness are the most likely attacks at this level. A collision happens when two nodes simultaneously attempt to transmit on the same frequency, resulting in either partial or complete packet disruption, which will cause an erroneous data transmission through a communication channel. In an IoFT, it is a big issue because the possibility of having an intermittent network condition is likely to cause chaos in a FANET. Therefore, each flying thing can be affected and could crash with each other due to the loss of information on the fly. If repetitive collisions take place, the system may suffer from resource depletion, that is, an exhaustion attack. Finally, rather than blocking access to a service outright, an attacker can degrade it to gain an advantage such as causing other nodes in a real-time MAC protocol to miss their transmission deadline, characterizing an unfairness attack (Sen, 2012).
- Network Layer. There are several attacks found on this layer. In a selective forwarding attack, malicious nodes attempt to stop the packets in the network by refusing to forward or drop messages passing through them (Khan et al., 2012), which could compromise a FANET that relies on strategically placed flying things to reach all the destinations within the network. If an attacker makes the compromised flying thing look more attractive to surrounding ones, which is considerably an easy task since IoFT applications usually take place in open environments, the selective forwarding attack becomes very simple. Then, through the affected flying thing, a data transfer situation may be started leading to a sinkhole attack (Dener, 2014). Another attack on network layer is the Sybil attack, in which a flying thing exhibits multiple identities to other flying things in the network (Dener, 2014). On the other hand, a wormhole is an out-of-band connection between two nodes using wired or wireless links, which can facilitate forwarding packets faster than via normal paths (Wallgren et al., 2013). According to Wallgren et al. (2013), a HELLO flood attack refers to overriding “HELLO” messages by broadcasting a stronger signal, allowing an attacker to introduce himself as a neighbor to many nodes, possibly the entire network, which is very likely to be seen in scenarios with flying things. In operation, the communications systems must balance the desire to maximize throughput (the amount of data transferred per unit time—which suggests large packets) and minimize latency (maximum delay accepted for the data transmitted and received—which suggests small packets). The final issue when multiple devices are deployed is that nodes in FANETs can be fixed or not and the distance among nodes can vary while in motion. To assure the route among nodes, FANETs rely on broadcast techniques, which becomes a problem that can be interpreted as an attack to the communication system: the growing amount of data traffic between flying things and IoFT-infrastructure elements; the increasing number of manned aircraft sharing the same airspace; and the progressive forthcoming of flying things to dispute nonsegregate airspace. To solve the problem of broadcast packets to all nodes and avoid packet redundancy and its associated problems (i.e., Broadcast Storm Problem - BSP), techniques to mitigate BSP must be taken into account (de Melo Pires et al., 2016).
- Transport Layer. Flooding attack causes immense traffic of useless messages on the network. It may result in congestion, and eventually lead to nodes exhaustion (Sastry et al., 2013). The desynchronization attack is made when the adversary repetitively pushes messages, which convey sequence numbers to one or both of the endpoints (Dener, 2014). The GPS spoofing may help attackers to hijack flying things, which is another issue that is strongly related to situations where an attacker secretly relays and possibly alters the communication between two parties, also known as man-in-the-middle attacks. This kind of attack allows an attacker to land the flying thing in an unauthorized place, and taking advantage of its legitimate network access. However, such problem can be neutralized by the high connectivity in IoFT environments: In most cases, a solution lies in techniques that check the accuracy of GPS signals by comparing to the ones provided by access points and other fixed known infrastructures.
From another point of view, some researchers have organized IoT in a new security architecture that also applies to IoFT (Jing et al., 2014). Such architecture is mainly divided in three layers: perception, transportation, and application. This organization with three layers only implements most of the features of Open Systems Interconnection model (OSI model), despite the fact it is not as well separated. Figure 19.8 shows a comparison between the IoT model proposed by Jing et al. (2014) and OSI model. Each layer of IoT model faces specific challenges, which will be discussed further.
- Perception Layer. This layer is mainly about information collection, object perception, and object control. In the perception layer within the Internet of Flying Things, tasks related to security of RFID (radio-frequency identification), WSN, RSN (RFID Sensor Network), GPS technology, and so on will be performed (Wu et al., 2010). The heterogeneity of flying things and ordinary IoT/IoFT-ready devices is one of the main problems that may arise in this layer, which can lead to compatibility problems. Another issue is the limitation of power, computing ability, and storage capacity, especially in flying things, that make them more vulnerable to attacks, allowing for physically stealing information and also functioning modification (Jing et al., 2014).
- Transportation Layer. Also referred to as network layer, the transportation layer's main function is transmitting information obtained from the perception layer (Wu et al., 2010). This layer encompasses the Wi-Fi, establishing and maintaining MANET/FANET and 3G/4G/5G networks, leading to a heterogeneity problem for the exchange of information among different networks, which is even more challenging when it comes to the IoFT and its inherent integration among different networks (IoT, FANETs). Moreover, it also leads to new vulnerabilities on the relevant segments for the implementation of IoFT networks. For instance, the main issues related to Wi-Fi are phishing access attacks, malicious AP, DDoS/DoS attacks, and so on. On MANET/FANET side, the security problems that may be faced are data security, network routing, and DDos/DoS issues. Finally, related to the 3G/4G/5G networks, data security and unlawful attacks are the main concerns (Jing et al., 2014).
- Application Layer. This layer supports all sorts of business services and realizes intelligent computation and resources allocation in screening, selecting, producing, and processing data. The security issues it faces cannot be solved in other layers of the IoT model, such as privacy protection issue, which can become a real demand in certain special contexts. Thus, in operation, the application support layer must be able to recognize untrusted data (e.g., spam data and malicious data), and filter them in real time. The application layer can be organized in different ways according to different services, and usually includes middleware, M2M, cloud computing platform, and service support platform (Jing et al., 2014). The privacy concerns in flying things have been recently discussed as a big threat as storage systems get more sophisticated. There is a tendency to store as much as possible into the flying thing memory, so guaranteeing that the needed information is always available (Hartmann and Steup 2013). However, such approach ends up being a very critical security threat (Jing et al., 2014). As the flying thing is inserted in a highly connected environment, it can be physically stolen or its control can be taken. Thus, the attacker may still use it as a gateway to obtain information from the network, since the flying thing is authorized and will be able to access private and confidential information. This is a consequence of the high connectivity of things and the increased contact surface that generates more possible threats to be explored by malicious entities.

Figure 19.8 A comparison between OSI model and IoT. (Model proposed by Jing et al. (2014).)
19.4.3 Safety Issues of the Internet of Flying Things
The growing popularization of UAVs has increased the research in this field and is fostering the use of such technology in many applications. There are roadmaps published periodically by military and civil organizations—for example, United States Army (US Army), American Department of Defense (DoD), European RPAS Steering Group (ERSG), and Federal Aviation Administration (FAA)—that outline the expected advances for UAVs (US Army, 2010; Yearbook, 2011; UK Civil Aviation Authority, 2012; DoD, 2013). However, there are not enough studies on safety for the specific integration of UAVs and IoT, which is one of the most important topics to be discussed and an open opportunity for researches in safety-critical systems.
There are five challenges of UAS integration, as stated by Dr. Wilson Felder, the Director of the William J. Hughes Technical Center of the FAA, reported by Stark et al. (2013): procedural, technical, aircraft safety, crew credentials, and public acceptance. Sense and Avoid Systems remain as one of the largest obstacles for the safe integration of UAS into airspace. Any person or computer-based system that meets the three mandatory activities to operate an aircraft (flight, navigation, and communication) should assume the command of an aircraft, be it manned or unmanned (Baraldi Sesso et al., 2016). Regulations regarding collision detection and resolution efforts must be met by any UAS designed for nonsegregated airspace.
In short, FAA requirements demand that UAS meet safety levels equivalent to those of manned aircraft. It includes the frequency of collision of a UAS being operated in a FAA-controlled airspace, which is currently 1 × 10−7 events per hour of operation for manned aircraft (Asmat et al., 2006). As for IoFT applications, there will be merged approaches that may include both manned and unmanned aircraft at the same time, leading to the necessity of using the nonsegregated airspace. This fact increases the need for meeting safety requirements and the first step is to point them out and discuss possible solutions.
Despite the security applied to each layer, there is also the need to find joint approaches that ensure safety individually and collectively. Reducing the breaches throughout the layers will consequently reduce the overall chances of attacks to the network. Such characteristics regarding security and safety make it more difficult to ensure the system safety, composing one of the main threats in the area, which is finding approaches that deal with both concepts at once.
The concept of safety has a long tradition for vehicles (ISO, 2011). This is a mature area, and several standards exist for creating safe systems such as RTCA/DO-178C for UAV software (RTCA Inc., 2011) and RTCA/DO-254 for UAV hardware (RTCA Inc., 2000). Safety deals with minimizing the frequency of accidents or failures in a system, mainly when related with loss of life, high-value assets, and it is related with incautious actions or events.
Providing a safe wireless communication means ensuring that the information transmitted is received without any transmission error and loss of the information. Due to noise, interference, and fading effects, wireless network cannot have zero transmission error, since there is no system with zero risk. For wireless network, transmission error and loss of information cannot be avoided, but they can be overcome by reducing or by detecting them. In order to guarantee communications with safety, Pendli (2014) listed a number of requirements that must be satisfied. Communication links should be reliable and immune against noise, jamming signal, interference, and fading effects in order to provide a link without errors and losses. Since flying things are safety-critical systems, communication channels must be continuously available and provide timely delivery information without failure. Ensuring real-time performance means that the technology used must take into consideration the delay during information transmission and retransmission and be able to cope with burst errors. Device mobility, and the changing external environment requires communication links to be robust even under adverse conditions against channel fading, low SNR (signal-to-noise ratio) conditions, and channel losses.
For flying vehicles in general, there are regulation and legislation requirements, which demand that any factors affecting safety must be taken into account, and incorporated into a risk model meeting certain minimum standards before certification is granted. For IoFT devices, the possible failure rates of solutions to all the summarized communications issues must be incorporated. Indeed, in some applications where the flying thing operates above cities or farms, which are critical fields, the need for certification is even higher. Although there is some way to go, it is hoped that the robustness of the IoT infrastructure may help achieving the low failure rates needed.
In short, developers and users of IoFT systems must take safety as one of the main concerns. However, the combination of high mobility and wireless communications highly increases the exposure of these systems to malicious threats and to faults deriving from uncertain connectivity or communication timeliness. Nonfunctional requirements like security have thus become harder to fulfil, creating new challenges to such safety-critical embedded systems (Bloomfield and Lala, 2013). In fact, further research on the development and assurance of both safety and security must be performed, addressing the needs of multidisciplinary approaches like integrated control systems, communication, security mechanisms, artificial intelligence, neural networks, safety assets, and other technological concerns. A key challenge is that the architectural solutions to ensure safety may open further weaknesses from the point of view of security. On the other side, security weaknesses may lead, if exploited by attackers, to safety violations and the implementation of a given security mechanism may impact safety. In the few cases where security is taken into account, the only problem that is addressed is the open network communication, such as wireless systems. Security at large is not handled (or handled in a very general way) without a full support to identify and mitigate security threats. Therefore, the relationship between safety and security seems to be still an open issue in the community.
19.5 Case Studies
Three case studies will be carried out in this section exemplifying real-world applications of the Internet of Flying Things. The first is on smart farms highlighting WFANETs application. The second is on the provision of Internet access and IoT-based services on remote areas, especially on rural zones and peripheries of smart cities. Finally, the third case study is on the management of big events and provision of targeted services.
19.5.1 Case Study 1: WFANETs for Surveillance Tasks in Smart Farms
Farms of hundreds of hectares with varied topology can be formed and subjected to different climatic conditions along their area. They can perform many different tasks in agriculture like raising livestock, becoming specialized units (e.g., vegetable or fruit farm, dairy, pig and poultry farm or even used for the production of natural fibers, biofuel, and other commodities). All of them also have a large infrastructure that may include plantations, pasture, feedlots, orchards, greenhouses, silos, barns and other buildings, and the farmhouse. In modern times, such term has been extended to include industrial operations as wind farms and fish farms, both of which can operate on land or sea. For more information about the various applications of IoT in agriculture, please refer to Chapter 18.
The concept of smart farms has been used to denote a ubiquitous IoT-ready farm environment for increasing general productivity and optimization of everyday tasks. Internet connectivity can be achieved in such environments mostly on strategic administrative buildings, but also in some dedicated fields with specialized technologies for sensing and monitoring. This case study analyzes a scenario from the IoFT perspective through the application of Wide-FANETs.
The concept of Wide-FANETs is an ad hoc network that benefits from the connection to an IoT infrastructure already available due to smart environments nearby. Such connection can provide broadband Internet access to local FANETs and, thereafter, a tunnel can be created for information exchange and cooperation among remote FANETs. More than one flying ad hoc network from different geographical locations connected through a transparent cloud-based tunneling consists of a WFANET.
19.5.1.1 The Problem
Although smart farms are already benefiting from IoT, they still have limited connectivity to the Internet, which usually leads to big areas with no connectivity and no surveillance. Thus, network structures that do not depend on Internet connections have been applied as temporary alternatives for monitoring animals, crop fields, forests, schools of fish, and so on. It is common to find WSN and wireless body area networks (WBAN) spread in many fields. However, the feedback from these networks and sensors is frequently limited, delayed, and poorly updated, which leads to less dynamic operations and limited overall farm management.
The problem addressed in this case study is related to general surveillance of a smart farm, including farm borders, controlled cattle, or suspect activities within the farm field. Such problems get bigger and more complex according to the farm size and also due to the number of different tasks that demand monitoring for safety and security reasons. They can also be considered critical since high-value assets are put at risk.
19.5.1.2 Proposed Solutions
Following topics will discuss the hypothetical application of FANETs and WFANETs to three farm scenarios: border control, cattle monitoring, and crop monitoring. Figure 19.9 illustrates the scenarios discussed further.
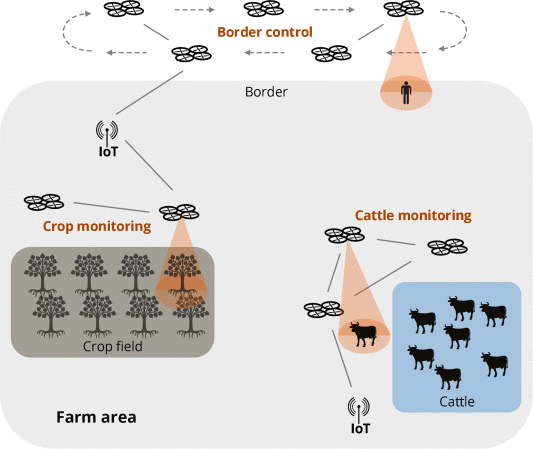
Figure 19.9 Surveillance situations for the study of WFANETs application in smart farms.
The surveillance of farm borders to identify potential threats, such as intruders (humans or not), and trigger appropriate procedures is one of the most important tasks for safety purposes. In a typical scenario, the task would be performed by human patrol and/or surveillance cameras. This solution, besides costly, is not likely to be effective, since the risk of human failure is always present.
A WFANET would provide border control at a lower cost. The UAVs would gain from the available IoT infrastructure to provide surveillance images or data in real time to a control central (e.g., for security guards, a specialized security company or a police station). The use of UAVs would reduce the necessity of surveillance cameras installed over the property border and its required infrastructure (such as batteries or solar cells for power), again reducing the task cost1. The advantages would be even bigger in bigger farms, since the use of WFANETs would allow the exchange of relevant information among more than one local FANET, in a cooperative live border monitoring. Additionally, data from official governmental web services may be used to identify fugitives.
Another situation is related to cattle monitoring. In big farms, it is normal to specify strategic land areas intended for cattle raising. Such areas must be constantly monitored in order to avoid escapes or unauthorized human intervention. Once again, if the solution relies on human resources, the coverage of monitoring might be subject to failures or be too slow to take appropriate actions with little damage to the cattle or other farm fields.
An IoT infrastructure would provide means of cattle tracking by installing cheap sensors in each single animal. Moreover, by surveying the area with UAVs, data acquisition would flow fast from the cattle raising area to monitoring centers, providing means of taking timely actions. As an alternative, automatic actions could also take place as soon as an unwanted behavior is identified, for example, closing backup gates in case of cattle escape. For that, FANETs (in small areas) or WFANETs (in bigger areas) would identify and trigger the appropriate action.
The surveillance of crop fields can be motivated by several factors, such as early identification of pests and plagues, soil checking, and weather conditions monitoring. Once again, appropriate local actions could take place as soon as an atypical situation is identified. In such case, more accurate information could be acquired by starting specialized missions with FANETs and/or WFANETs based on the additional information required to precisely recognize a countermeasure2,3.
UAVs can collect data from wireless sensor networks placed on the ground at strategic frequency, being able to transmit such data in real time to monitoring centers. Moreover, such data collection frequency could be based on weather conditions, originating from both local sensor and web services.
19.5.2 Case Study 2: Internet Access and IoT Services Provision in Remote and Peripheral Areas with IoFT as Fog Enabler
Rural areas and city peripheries might be the trickiest areas for provision of Internet/IoT-based services, especially due to the lack of appropriate infrastructure. In most of the cases, it is not worth installing a full infrastructure that will be rarely used in remote areas. Moreover, as the demand is usually low, there will be no interest by government and business companies to update such infrastructure in order to match the newest technologies requirements.
On the other hand, there are situations when the support of Internet/IoT-based services would positively improve tasks related to search and rescue, life quality levels, special events, people/objects tracking, and so on. This case study will investigate the benefits of using the Internet of Flying Things to amplify the coverage of common smart city services. By doing so, there is a potential opportunity of providing Internet connectivity and IoT-based services for the temporary improvement of special tasks in an inexpensive manner.
19.5.2.1 The Problem
The downtown of a smart city is likely to be the geographic region to first experience novel efforts and updated technologies, while the peripheries will usually be the last ones to face a full integration and also to get relevant investments. That is the natural process given a business model full of potential opportunities which focuses on highly populated areas to be profitable.
In a different context, rural areas might not need Internet connectivity at all times, but they do need to update/synchronize data at some stage. For this, data mules can be used, for example, in vehicles that physically carry computers with dedicated storage servers allowing a slow, limited, once-a-day synchronization. Although this approach can be considered inexpensive and efficient in many situations, it is poorly flexible and does not provide the benefits of a fully connected infrastructure.
The same issue is experienced in emergency situations, for example, search and rescue. A local network infrastructure does not provide the real-time support that such an operation would need to properly and efficiently do the search and also the rescue tasks. In some cases, the inexistence of cellular network coverage limits even more the connectivity, which leads to the necessity of a flexible, inexpensive, easy-to-set-up approach.
Pursuant to such issues, the IoFT paradigm might be a relevant alternative of either temporarily or permanently minimizing the already discussed problems. Next subsection will discuss proposed solutions for recurrent cases demonstrating how this paradigm would solve practical cases.
19.5.2.2 Proposed Solutions
Here, three main applications of this case study will be highlighted. The first investigates how an IoFT network would be important for smart cities peripheries. The second addresses the environmental monitoring in rural areas helping the environmental police to identify illegal actions and take appropriate countermeasures. Last, natural phenomena and emergency operations support are discussed considering that in such situations connectivity becomes an issue due to the loss of infrastructure nearby. Figure 19.10 illustrates the scenarios that will be discussed further.

Figure 19.10 Applications of IoFT in smart cities.
By strategically moving drones to the edges of smart cities, a powerful connection to the Internet will be available for restricted areas helping with the provision of connectivity to city peripheries. From this connection, a complete range of IoFT services will be available for end users nearby for a specific period, allowing the execution of relevant tasks4.
For instance, the smart city's electric power company might automate the reading process of residential energy consumption. Such task is usually performed by a person taking note about the consumption in each residence/building, which takes more time and is susceptible to misreading. Applying appropriate identifiers to each residence (such as RFID tags), which in turn will be recognizable by the IoFT infrastructure, would provide means of reading the energy consumption of a big area in several minutes. That is possible due to the existence of a FANET/WFANET flying over the area, providing such class of services and being able to provide real-time information to both the customer (e.g., bad debt warnings) and the electric power company (e.g., reading issues in specific residences that would require a technical visit).
Moreover, the existence of a single flying thing or a FANET/WFANET over a neighborhood that is not yet equipped with the smart city infrastructure can be used as a traffic support to drivers in that regions. Smart cars would benefit from IoFT warnings about the traffic. Regular cars could also get important updates about the traffic via smartphones connected to the IoFT infrastructure. Actions like these would contribute for a safer and more accurate use of streets, not to mention the emergency situations that could take place, and fully benefit from IoFT infrastructures.
Rural areas usually do not demand Internet connectivity at all times. In some cases, data mules can be used, allowing the transfer of data between remote locations to effectively create a data communication link. Similarly, an IoFT network can be created to transport data to a desired location, but with an intermittent link provided by a mobile ad hoc network connecting the city and the remote area.
The concept of fog computing is clear in this situation, but the IoFT network emerges as an enabler of the model. Section 19.3.1 discussed the application of a UAV as a fog computing infrastructure using the IoFT elements to provide an updated, flexible solution. Such application fits well for rural areas that need better services delivery for more advanced tasks performing.
This model also meets the requirements of environmental monitoring by governmental official agencies, which is a trend due to the global issues being reported lately. The real-time monitoring by flying things can be remotely analyzed by specialists in central offices that will be able to use updated images to identify suspicious activities. If an environmental illegal practice is taking place, the environmental police can promptly move to the region being supported by the IoFT infrastructure at all times, allowing efficient red-handed operation.
A situation that is also frequent in remote areas is related to natural phenomena and emergency operations support. Natural disasters and catastrophic situations can be predictable but usually not controllable. Their destruction might lead to the unavailability of essential services from local infrastructure, such as cellular networks, causing chaos situations.
The application of IoFT to provide means of connectivity from the heart of the city throughout a FANET that reaches the disaster area can be an efficient temporary action to support rescue agents to do their job as qualified as possible5. For instance, if a disaster has led to deaths, one might consider the real-time recognition of bodies by relatives. However, it is not always safe or appropriate to transport people to the disaster area. Also, it is not possible in some situations to remove all the bodies right away, resulting in panic and people flooding agencies with calls demanding information.
IoFT in emergency situations will provide connectivity for basic services provision, governmental central offices, and news agencies to be updated with recent discoveries, and the complete support for ambulances being moved to the target area.
19.5.3 Case Study 3: Targeted Services Delivery on Big Events with IoFT
Big events take place throughout the year basically everywhere. They can be of many types such as local exhibitions, big theatre presentations, and hundreds of simultaneous concerts and presentations in several different venues in a music festival. These big events can be crowded by people coming from multiple places with different accessibility demands.
General safety is an issue that can be supported by an IoFT infrastructure, especially when an event takes place in a remote location (e.g., gigantic music festivals). It is similar to the situation described in Case Study 1, when surveillance tasks may be demanded. However, this case study will focus on targeted services delivery for big events provided by IoFT networks.
19.5.3.1 The Problem
In big events one of the most alarming problem is to lose people, especially children. Sometimes a cellular network signal will not be available and finding someone in a crowded area is almost an impossible mission for one person.
Moreover, due to the high number of people, it is hard to move from one location to another to check if your favorite band started playing or if a boring presentation is about to end. These are desired information that are usually unavailable or partially available in paper guides, which can become outdated in minutes.
19.5.3.2 Proposed Solutions
The applicability of IoFT in the cited situations might be a simple and efficient solution. The following subsections will discuss two cases specifically. First, the application of finding people will be discussed. Second, real-time information about multiple venues in music festivals will be addressed. Figure 19.11 presents the scenario of this case study.
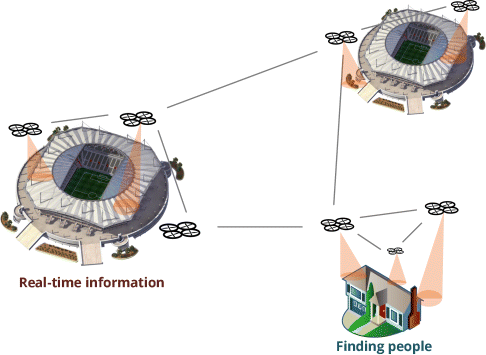
Figure 19.11 Applications of IoFT in big events.
It is common to suddenly find yourself separated from your friends or family in crowded places. If a cellular network is not available for any reason or your phone ran out of battery, then you might have a problem. Plus, the situation gets even worse if a kid is lost by any reason and the parents are desperately looking for him/her.
The identification of people using fixed cameras coupled to the infrastructure of venues is efficient most of the times. However, in crowded places the angle of the camera might be a problem. In case of lost children, it is even more problematic, since the height would negatively influence the camera coverage. For cases like this a reasonable solution would be a flying thing connected to a FANET/WFANET for accurate, fast search on site.
The real-time streaming can be monitored by trained people and also relatives. Such effort would significantly reduce the chances of any hurt to an unattended child and also provide effective means to supporting families.
Another relevant topic in big events, especially the ones with simultaneous attractions in multiple venues, is the possibility of getting access to information in real time. One can wonder whether a concert meant to be played at a specific time has started or is delayed. Moreover, why not have access to the audio or a video streaming to check how is the performance going or how crowded it is?
An IoFT network plus fixed cameras and sensors could provide a set of information about multiple venues in real time to a central server that would redistribute such information all over the network. Personal smartphones or special stations could get access to such information, improving the delivered services during the days of the event.
19.6 Conclusions
The Internet of Flying Things integrates flying things to the Internet of Things paradigm. This new concept increases the cooperation and collaboration among UAVs, amplifying the network coverage, and creating new possibilities for UAS applications, such as interactive decision-making. In the context of IoT, being aware of flying things' basic characteristics, such as capabilities, targets, and limitations, is a key factor to determine how eligible they are to perform sophisticated missions and how likely they are to be integrated onto the IoT. Despite the fact that flying things could be treated as generic nodes on the IoFT paradigm, the development of specific approaches might help reaching more optimized, safe, and secure results.
There are understandable concerns about the threat that networked UAVs could pose to privacy and safety. Legislation is likely to address the design and usage of IoFT-based systems, and to help with public confidence the largest open challenge facing the field is the development and adoption of robust standards for security and safety—of both devices and the data they carry and transmit. Considering the many physical forms that a UAV might take, security policies and algorithms must be devised that are resource efficient, work on many different types of hardware (from data storage devices right through to different aircraft chassis) and software (across the layers of network protocols). When one extends the considerations to multi-UAV swarms, or even disparate groups connected via a WFANET, policies must then take into account the greater “vulnerable surface” of an ad hoc network, and redundancy of information (encryption keys, etc.) that will arise as mobile devices become unavailable for periods of time as they move around.
Despite all the challenges, the Internet of Flying Thing is a promising paradigm with high chances of applicability. For designers of airborne missions, connecting UAVs to smart environments will allow the acquisition and provision of updated information, increasing the accuracy of tasks they perform. Coupling UAVs to the Internet means they can outsource processing to cloud servers, so reducing the need for sophisticated hardware and making them more flexible and easier to use for new scenarios. Conversely, for infrastructure and IoT designers, Flying Ad Hoc Networks offer a flexible new way of connecting environments that might have been separated due to their remoteness, or for temporal reasons such as natural disasters or infrastructure breakdowns. These improvements are a very important innovation in the field, bringing possibilities of new applications, especially hard real-time ones, for example, search and rescue, critical surveillance tasks, and sensitive fields monitoring.
Acknowledgments
Research was sponsored by FAPESP under Process Number 2012/16171-6. Research was also sponsored by the Army Research Office and was accomplished under Grant Number W911NF-18-1-0012. The views and conclusions contained in this document are those of the authors and should not be interpreted as representing the official policies, either expressed or implied, of the Army Research Office or the U.S. Government. The U.S. Government is authorized to reproduce and distribute reprints for government purposes notwithstanding any copyright notation herein.
Notes
References
- Andreev, S., Galinina, O., Pyattaev, A., Gerasimenko, M., Tirronen, T., Torsner, J., Sachs, J., Dohler, M. and Koucheryavy Y. (2015) Understanding the IoT connectivity landscape: a contemporary M2M radio technology roadmap. IEEE Communications Magazine, 53(9), 32–40. doi: 10.1109/MCOM.2015.7263370.
- Asmat, J., Rhodes, B., Umansky, J., Villavicencio, C., Yunas, A., Donohue, G., and Lacher, A. (2006) UAS safety: unmanned aerial collision avoidance system (UCAS). Systems and Information Engineering Design Symposium, 2006 IEEE, 43–49. doi: 10.1109/SIEDS.2006.278711.
- Atzori, L., Iera, A., and Morabito, G. (2010) The Internet of Things: a survey. Computer Networks, 54(15), 2787–2805. doi: 10.1016/j.comnet.2010.05.010.
- Baraldi Sesso, D., Vismari, L. F., Vieira Da Silva Neto, A., Cugnasca, P. S., and Camargo, J. B. Jr. (2016) An approach to assess the safety of ADS-B-based unmanned aerial systems: data integrity as a safety issue. Journal of Intelligent and Robotic Systems, 84 (1–4), 621–38. doi: 10.1007/s10846-015-0321-0.
- Bekmezci, İ., Sahingoz, O. K. and Temel, Ş. (2013) Flying ad-hoc networks (FANETs): a survey. Ad Hoc Networks, 11(3), 1254–70. doi: 10.1016/j.adhoc.2012.12.004.
- Bloomfield, R., and Lala, J. (2013) Safety-critical systems: the next generation. IEEE Security & Privacy, 11(4), 11–13. doi: 10.1109/MSP.2013.95.
- Bonomi, F., Milito, R., Zhu, J., and Addepalli, S. (2012) Fog computing and its role in the internet of things. Proceedings of the First Edition of the MCC Workshop on Mobile Cloud Computing, 13–16. doi: 10.1145/2342509.2342513.
- Bouachir, O., Abrassart, A., Garcia, F. and Larrieu, N. (2014) A mobility model for UAV ad hoc network. 2014 International Conference on Unmanned Aircraft Systems (ICUAS), 383–88.
- Chung, H., Oh, S., Shim, D. H., and Sastry, S S. (2011) Toward robotic sensor webs: algorithms, systems, and experiments. Proceedings of the IEEE, 99(9), 1562–86.
- Clapper, J., Young, J., Cartwright, J., and Grimes, J. (2007) Unmanned Systems Roadmap 2007–2032. Office of the Secretary of Defense, p. 188.
- de Melo Pires, R., Arnosti, S. Z., Pinto, A. S. R., and Branco, K. R. L. J. C. (2016) Experimenting broadcast storm mitigation techniques in FANETs. 2016 49th Hawaii International Conference on System Sciences (HICSS), 5868–77. doi: 10.1109/HICSS.2016.726. IEEE.
- Dener, M. (2014) Security Analysis in Wireless Sensor Networks. International Journal of Distributed Sensor Networks, 10. doi: https://doi.org/10.1155/2014/303501.
- U.S. DoD (2013) Unmanned Systems Integrated Roadmap: 2013–2038. Washington, DC, USA.
- Fahlstrom, P. G., and Gleason, T. J. (2012) Introduction to UAV Systems. 4th edn, John Wiley & Sons, Ltd. Chichester.
- Frew, E. W. and Brown, T. X. (2009) Networking issues for small unmanned aircraft systems. Journal of Intelligent and Robotic Systems, 54 (1–3), 21–37.
- Hartmann, K. and Steup, C. (2013) The vulnerability of UAVs to cyber attacks: an approach to the risk assessment. 2013 5th International Conference on Cyber Conflict (CyCon), 1–23.
- Hassan, Q. F., Riad, A. M., and Hassan, A. E. (2012) Understanding cloud computing. Software Reuse in the Emerging Cloud Computing Era, IGI Global, pp. 204–227.
- ISO. (2011) ISO 26262-1:2011 - Road Vehicles. Available at http://www.iso.org/iso/catalogue_detail?csnumber=43464.
- Jing, Q., Vasilakos, A. V., Wan, J., Lu J., and Qiu, D. (2014) Security of the Internet of Things: perspectives and challenges. Wireless Networks, 20(8), 2481–2501. doi: 10.1007/s11276-014-0761-7.
- Khan, W. Z., Xiang, Y., Aalsalem, M. Y., and Arshad, Q. (2012) The selective forwarding attack in sensor networks: detections and countermeasures. International Journal of Wireless and Microwave Technologies (IJWMT), 2(2), 33.
- Luan, T. H., Gao, L., Li, Z., Xiang, Y., and Sun, L. (2015) Fog computing: focusing on mobile users at the edge. Eprint arXiv:1502.01815, 1–11. doi: 10.1016/j.jnca.2015.02.002.
- Marshall, D. M., Barnhart, R. K., Shappee E., and Most, M. T. (2015) Introduction to Unmanned Aircraft Systems, CRC Press.
- Pendli, P. K. (2014) Contribution of Modelling and Analysis of Wireless Communication for Safety Related Systems with Bluetooth Technology. Kassel university press GmbH.
- Pigatto, D. F., Goncalves, L., Pinto, A. S. R., Roberto, G. F., Fernando Rodrigues Filho, J. and Branco, K. R. L. J. C. (2014) HAMSTER: healthy, mobility and security-based data communication architecture for unmanned aircraft systems. 2014 International Conference on Unmanned Aircraft Systems (ICUAS), 52–63. IEEE. doi: 10.1109/ICUAS.2014.6842238.
- Rieke, M., Foerster, T., and Broering, A. (2011) Unmanned aerial vehicles as mobile multi-sensor platforms. Proceedings of the 14th AGILE International Conference on Geographic Information Science, Utrecht, NL, USA, 18–21.
- RTCA Inc. (2000) RTCA/DO-254, Design Assurance Guidance for Airborne Electronic Hardware. Available at http://www.do254.com/.
- RTCA Inc. (2011) DO-178C Software Considerations in Airborne Systems and Equipment Certification. Available at http://www.rtca.org/store_product.asp?prodid=803.
- Sahingoz, O. K. (2013) Mobile networking with UAVs: opportunities and challenges. 2013 International Conference on Unmanned Aircraft Systems (ICUAS), 933–41. doi: 10.1109/ICUAS.2013.6564779. IEEE.
- Sarkar, S. K., Basavaraju, T. G., and Puttamadappa, C. (2008) Ad Hoc Mobile Wireless Networks: Principles, Protocols and Applications. 1st edn, Auerbach Publications, Boca Raton, FL.
- Sastry, A. S., Sulthana, S., and Vagdevi, S. (2013) Security threats in wireless sensor networks in each layer. International Journal of Advanced Networking and Applications, 4(4), 1657.
- Sen, J. (2012) Security in wireless sensor networks. Wireless Sensor Networks: Current Status and Future Trends CRC Press, Boca Raton, FL, p. 407.
- Stark, B., Stevenson, B., and Chen, Y.Q. (2013) ADS-B for small unmanned aerial systems: case study and regulatory practices. 2013 International Conference on Unmanned Aircraft Systems (ICUAS), 152–59. doi: 10.1109/ICUAS.2013.6564684.
- UK Civil Aviation Authority. (2012) Unmanned Aircraft System Operations in UK Airspace -- Guidance (CAP722). UK.
- Ungurean, I., Gaitan, N.-C., and Gaitan, V. G. (2014) An IoT architecture for things from industrial environment. 2014 10th International Conference on Communications (COMM), 1–4. doi: 10.1109/ICComm.2014.6866713. IEEE.
- US Army. (2010) Unmanned Aircraft Systems Roadmap 2010–2035. Alabama, USA.
- Wallgren, L., Raza, S.. and Voigt, T. (2013) Routing attacks and countermeasures in the RPL-based Internet of Things. International Journal of Distributed Sensor Networks, 9. doi: https://doi.org/10.1155/2013/794326.
- Whitmore, A., Agarwal, A., and Da Xu, L. (2015) The Internet of Things—a survey of topics and trends. Information Systems Frontiers, 17(2), 261–74. doi: 10.1007/s10796-014-9489-2.
- Wu, M., Lu, T. J., Ling, F. Y., Sun, J., and Du, H. Y. (2010) Research on the architecture of Internet of Things. ICACTE 2010, 2010 3rd International Conference on Advanced Computer Theory and Engineering, Proceedings, 5, 484–87. doi: 10.1109/ICACTE.2010.5579493.
- UAS Yearbook (2011) Unmanned Aircraft Systems: The Global Perspective 2011/2012. Blyenburg & Co, pp. 1709–1967.
