What Is Computer Forensics?
Computer forensics is the scientific process for examining data stored on, received from, or transmitted by electronic devices. The data is examined to find evidence about an event or crime. Law enforcement uses computer forensics to investigate almost any type of crime. Consider the following:
- Illinois state prosecutors used cell phone records and data gathered by computer forensic examiners to convict a defendant of murdering two people. The defendant had used his computer to search “hire a hit man.” He had also searched for directions from his home to the victim’s home. The case was unique because almost no physical evidence existed to link the defendant to the murders. A judge sentenced him to life in prison.
- A Hong Kong shipping company pleaded guilty to violating U.S. pollution laws and was fined $10 million. A ship operated by the company ran into the San Francisco Bay Bridge and spilled more than 50,000 gallons of fuel into the San Francisco Bay. Computer forensic examiners found that someone on the ship altered its computerized navigation charts after the crash.
- The U.S. Department of Justice charged nine foreign nationals with stealing more than 31 terabytes of data from U.S. colleges and universities, companies, and government agencies. Computer forensic examiners found that the hackers used several different tactics to gain access to the stolen data.
Computer forensics has many different names. It is also called system or digital forensics, computer forensic analysis, computer examination, data recovery, and sometimes inforensics (information forensics). These terms are used interchangeably. This chapter uses the term computer forensics.
![]() NOTE
NOTE
The word forensics is from the Latin word forensis, which means “belonging to the forum.” It refers to the types of arguments used in a court or public forum to prove or disprove past theories or arguments.
Computer forensic examiners use specialized software and tools to collect and study data stored on electronic devices. The evidence collected is called digital evidence or just electronic evidence. Computer forensics includes all the steps through which this evidence is collected, preserved, analyzed, documented, and presented.2 The goal of computer forensics is to find evidence that helps investigators analyze an event or incident.
Computer forensic examiners study and collect electronic data for many reasons. They do not just investigate crimes. Other computer forensics uses include:
- Individuals—People may hire computer forensic examiners to find evidence to support tort claims. They can find digital evidence about sexual harassment or discrimination. Examiners also can uncover evidence for any type of civil litigation. They also can find evidence to support a criminal defense case.
- Military—The military uses computer forensics to gather intelligence information to support its operations. It also uses computer forensics to prepare for and respond to cyberattacks.
- Organizations—Organizations use computer forensics the same ways that individuals use it. Computer forensic examiners also can investigate employee wrongdoing. They can look for embezzlement or theft of intellectual property (IP). They also can look for unauthorized use of information technology (IT) resources and attempts to harm them. An organization’s incident response (IR) program can include forensic activities.
- Colleges and universities—Many colleges and universities offer programs in computer forensics. Some may have forensic research programs. They also use computer forensics for the institution’s own IR activities.
- Data recovery firms—Data recovery firms use computer forensics to rescue data for their clients. They also advise clients how to keep data safe from loss.
Most electronic devices hold some type of data. Computer forensics can study any of them. Potential sources of digital evidence include:
- Computer systems—This includes laptop and desktop computers, as well as servers. It also includes the hardware and software that the system uses. This category also includes peripheral devices that can be attached to computer systems. These devices enhance the user experience. They may include keyboards, microphones, web cameras, and memory card readers.
- Storage devices—This includes internal and external hard drives, as well as removable media such as floppy disks, Zip disks, compact discs (CDs), digital versatile discs (DVDs), thumb flash drives, and memory cards.
- Mobile devices—This includes cell phones and smartphones. It also includes tablets, personal digital assistants (PDAs), and pagers. Global positioning system (GPS) devices hold data as well. Digital and video cameras, and audio and video multimedia devices, also fall into this category.
- Networking equipment—This includes network hubs, routers, servers, switches, and power supplies. Networking equipment can be wired or wireless.
- Other potential sources—Any device with computer capabilities can potentially hold digital evidence. For example, many office devices have data storage ability. This includes copiers and fax machines, answering machines, printers, and scanners. Entertainment devices store data as well. They include digital video recorders (DVRs), digital audio recorders, and video game systems. Surveillance equipment is included in this category. This category includes any device not already mentioned that can store data. Any Internet of Things (IoT) device can also potentially hold digital evidence because these devices collect data via sensors and transmit it via the internet. Fitness trackers, medical devices, environmental sensors, and even industrial equipment all have data that can be used as digital evidence.
People’s dependence on electronic devices to live their lives continues to grow. Therefore, computer forensics as a special area of study also grows. Computer forensic examiners are not always experts in collecting data from every possible type of electronic device. They often focus on certain types of devices. In addition, most computer forensic examiners focus their skills in specific areas. The three main areas of computer forensics are:
- Media analysis
- Code analysis
- Network analysis
Media analysis focuses on collecting and examining data stored on physical media. This includes computer systems and storage devices. It also includes mobile devices. When people think about computer forensics, they most often think about media analysis. This type of analysis discovers normal and deleted data. It also finds encrypted, hidden, and password-protected data. This chapter focuses mostly on media analysis concepts. These concepts apply to other types of computer forensic analysis as well.
Code analysis, also called malware forensics, focuses on reviewing programming code. This area looks for malicious code or signatures from viruses, worms, and Trojans. It looks for the signature of anything that has modified a system without permission. A signature is the executable part of a malicious code. The need for code analysis continues to grow as malware types change. A 2019 report estimated a rise of almost 14 percent in different types of malware during that year.3
![]() NOTE
NOTE
Most antivirus programs use signatures to help them detect malware on a computer system.
Network analysis focuses on collecting and examining network traffic. An examiner reviews transaction logs and uses real-time monitoring to find evidence. Organizations often use this type of analysis to investigate incidents.
Some computer forensic examiners also might have specialties within these three major categories. For example, some examiners might specialize in email forensics. Email forensics, which includes a combination of media and network analysis, is used to find the sender, recipient, date, time, location information, and contents of email messages. This is a hot area as almost 94 percent of all malware was delivered via email in 2019.4 As technology advances, it is not unusual to find examiners with very specialized skills. FIGURE 15-1 shows examples of different computer forensic categories.
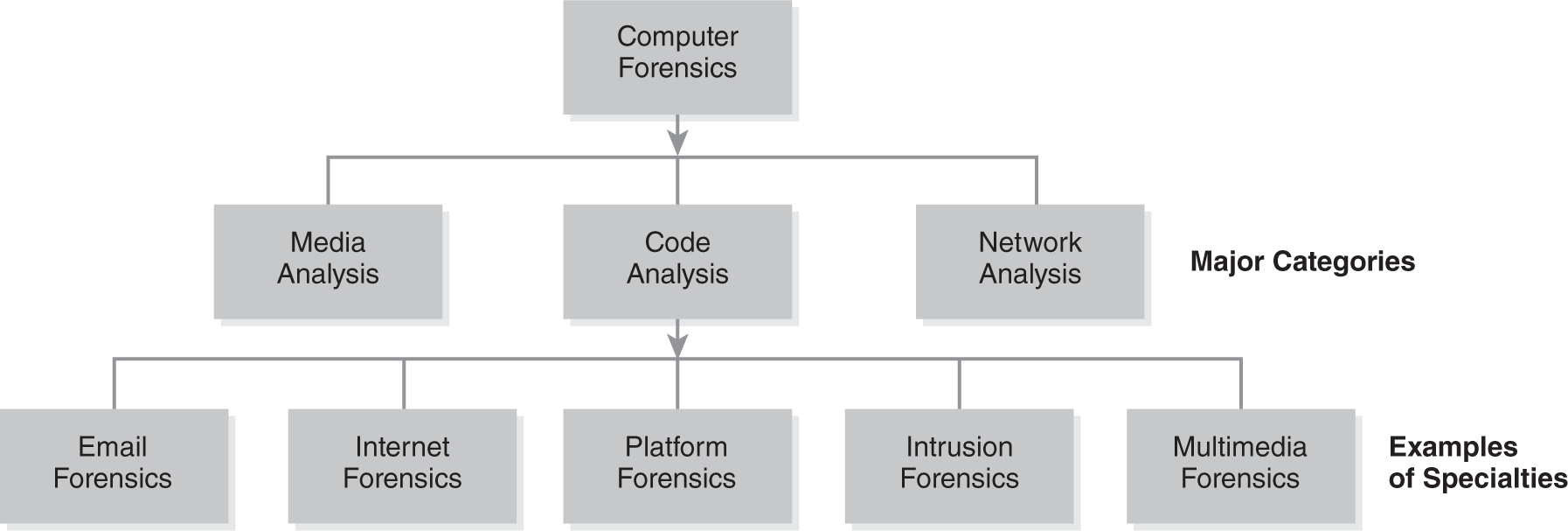
FIGURE 15-1
Computer forensic categories.
