5
Modulation Methods
Gordon L. Stüber
5.2 Basic Description of Modulated Signals
5.3 Quadrature Amplitude Modulation
Root Raised Cosine Pulse Shaping
5.4 Phase Shift Keying and π/4-QDPSK
5.5 Continuous Phase Modulation, Minimum Shift Keying, and GMSK
5.6 Orthogonal Frequency Division Multiplexing
5.1 Introduction
Modulation is the process whereby message information is embedded into a radio frequency carrier. Message information can be transmitted in the amplitude, frequency, or phase of the carrier, or a combination thereof, in either analog or digital format. Analog modulation schemes include amplitude modulation (AM) and frequency modulation (FM). Analog modulation schemes are still used today for broadcasting AM/FM radio, but all other communication and broadcast systems now use digital modulation. Digital modulation schemes transmit information using a finite set of waveforms and have a number of advantages over their analog counterparts. Digital modulation is a natural choice for digital sources, for example, computer communications. Source encoding or data compression techniques can reduce the required transmission bandwidth with a controlled amount of signal distortion. Digitally modulated waveforms are also more robust to channel impairments such as delay and Doppler spread, and cochannel and adjacent channel interference. Finally, encryption and multiplexing is easier with digital modulation schemes.
Modulation schemes can be designed to provide power and/or bandwidth efficient communication. In an information theoretic sense, we want to operate close to the Shannon capacity limit of a channel. This generally requires the use of error control coding along with a jointly designed encoder and modulator. However, in this chapter we only consider the modulation schemes by themselves. The bandwidth efficiency of a modulation scheme indicates how much information is transmitted per channel use and is measured in units of bits per second per Hertz of bandwidth (bits/s/Hz). The power efficiency can be measured by the received signal-to-interference-plus-noise ratio (SINR) that is required to achieve reliable communication with specified bandwidth efficiency in the presence of channel impairments such as delay spread and Doppler spread. In general, modulation techniques for spectrally efficient communication systems should have the following properties:
Compact power density spectrum: To minimize the effect of adjacent channel interference, the power radiated into the adjacent band is often limited to be 60–80 dB below that in the desired band. This requires modulation techniques having a power spectrum characterized by a narrow main lobe and fast roll-off of side-lobes.
Robust communication: Reliable communication must be achieved in the presence of delay and Doppler spread, adjacent and cochannel interference, and thermal noise. Modulation schemes that promote good power efficiency in the presence of channel impairments are desirable.
Envelope properties: Portable and mobile devices often employ power-efficient nonlinear (Class-C) power amplifiers to minimize battery drain. However, amplifier nonlinearities will degrade the performance of modulation schemes that transmit information in the amplitude of the carrier and/or have a nonconstant envelope. To obtain suitable performance, such modulation schemes require a less power-efficient linear or linearized power amplifier. Also, spectral shaping is usually performed prior to upconversion and nonlinear amplification. To prevent the regrowth of spectral side lobes during nonlinear amplification, modulation schemes having a relatively constant envelope are desirable.
5.2 Basic Description of Modulated Signals
With any modulation technique, the bandpass signal can be expressed in the form
s(t)=ℜ{˜s(t)ej2πfct}(5.1)
where ˜s(t)=˜sI(t)+j˜sQ(t)
˜s(t)=A∑nb(t−nT,xn)(5.2)
xn=(xn,xn−1,…,xn−K),(5.3)
where A is the amplitude and {xn} is the sequence of complex data symbols that are chosen from a finite alphabet, and K is the modulator memory order which may be finite or infinite. One data symbol is transmitted every T seconds, so that the baud rate is R = 1/T symbols/s. The function b(t,xi) is a generalized shaping function whose exact form, along with the modulator memory order, depends on the type of modulation that is employed. Several examples are provided in this chapter where information is transmitted in the amplitude, phase, or frequency of the bandpass signal.
The power spectral density of the bandpass signal, Sss(f), is related to the power spectral density of the complex envelope, S˜s˜s(f)
Sss(f)=12[S˜s˜s(−f−fc)+S˜s˜s(f+fc)].(5.4)
The power density spectrum of the complex envelope for a digital modulation scheme has the general form
S˜s˜s(f)=A2T∑mSb,m(f)e−j2πfmT,(5.5)
where
Sb,m(f)=12E[B(f,xm)B*(f,x0)],(5.6)
B(f,xm) is the Fourier transform of b(t,xm), and E [·] denotes the expectation operator. Usually symmetric signal sets are chosen so that the complex envelope has zero mean, that is, E [b(t,x0)] = 0. This implies that the power density spectrum has no discrete components. If in addition xm and x0 are independent for |m| > K, then
S˜s˜s(f)=A2T∑|m|<KSb,m(f)e−j2πfmT.(5.7)
Another important case arises with uncorrelated zero-mean data, where Sb,K(f) = 0, K = 1. In this case, only the term Sb,0(f) remains and
S˜s˜s(f)=A2TSb,0(f),(5.8)
where
Sb,0(f)=12E[|B(f,x0)|2].(5.9)
5.3 Quadrature Amplitude Modulation
Quadrature amplitude modulation (QAM) is a bandwidth-efficient modulation scheme that is used in numerous wireless standards. With QAM, the complex envelope of the transmitted waveform is
˜s(t)=A∑nb(t−nT,xn)(5.10)
where
b(t,xn)=xnha(t)(5.11)
ha(t) is the amplitude shaping pulse, and xn = xI,n + jxQ,n is the complex-valued data symbol that is transmitted at epoch n. Each symbol xk is mapped onto log2 M source bits. It is apparent that both the amplitude and the excess phase of a QAM waveform depend on the complex data symbols. QAM has the advantage of high bandwidth efficiency, but amplifier nonlinearities will degrade its performance due to its nonconstant envelope.

FIGURE 5.1 Complex signal-space diagram for square QAM constellations.
5.3.1 QAM Signal Constellations
A variety of QAM signal constellations may be constructed. Square QAM constellations can be constructed when M is an even power of 2 by choosing xI,m,xQ,m ∈ {±1, ±3, …, ±(N − 1)} and N=√M
Eh=A22∞∫−∞h2a(t) dt(5.12)
is the energy in the bandpass pulse Aha(t) cos2πfct under the condition fcT >> 1.
When M is an odd power of 2, the signal constellation is not square. Usually, the constellation is given the shape of a cross to minimize the average energy in the constellation for a given minimum Euclidean distance between signal vectors. Examples of the QAM “cross constellations” are shown in Figure 5.2.
5.3.2 Root Raised Cosine Pulse Shaping
The amplitude shaping pulse is very often chosen to be a square root raised cosine pulse, where the Fourier transform of ha(t) is
Ha(f)={√T0≤ | f | ≤(1−β)/2T√T2[1−sinπTβ(f−12T)](1−β)/2T≤ | f | ≤(1+β)/2T.(5.13)
The receiver implements the matched filter ha(−t) so that the overall pulse produced by the cascade of the transmitter and receiver matched filters is p(t) = ha(t)* ha(−t). It follows that the Fourier transform of p(t) is P(f)=Ha(f)H*a(f)=|Ha(f)|2

FIGURE 5.2 Complex signal-space diagram for cross QAM constellations.
ha(t)={1−β+4β/π,t=0(β/√2)[(1+2/π)sin(π/4β)+(1−2/π)cos(π/4β)],t=±T/4β4β(t/T)cos[(1+β)πt/T]+sin[(1−β)πt/T]π(t/T)[1−(4βt/T)2],elsewhere.(5.14)
The overall pulse p(t) is the raised cosine pulse
p(t)=sinπt/Tπt/T cosβπt/T1−(2βt/T)2.(5.15)
The roll-off factor β usually lies between 0 and 1 and defines the excess bandwidth 100β%. For β = 0, the root raised cosine pulse reduces to the sinc pulse ha(t) = sinc(t/T). Using a smaller β results in a more compact power density spectrum, but the link performance becomes more sensitive to errors in the symbol timing. The raised cosine and root raised cosine pulses corresponding to β = 0.5 are shown in Figure 5.3. Strictly speaking, the root raised cosine pulse in Equation 5.14 is noncausal. Therefore, in practice, a truncated and time-shifted approximation of the pulse must be used. For example, in Figure 5.3 the pulse is truncated to length 6T and right time-shifted by 3T to yield a causal pulse. The time-shifting makes the pulse have a linear phase response, while the pulse truncation will result in a pulse that is no longer strictly bandlimited. Finally, we note that the raised cosine pulse is a Nyquist pulse having equally spaced zero crossings at the baud period T, while the root raised cosine pulse by itself is not a Nyquist pulse.
5.3.3 Power Spectrum of QAM
The power density spectrum of the QAM complex envelope is
S˜s˜s(f)=A2Tσ2x|Ha(f)|2,(5.16)

FIGURE 5.3 Raised cosine and root raised cosine pulses with roll-off factor β = 0.5. The pulses are truncated to length 6T and time shifted by 3T to yield causal pulses.
where σ2x=1/2E[|xk|2]

FIGURE 5.4 PSD of QAM with a truncated square root raised cosine amplitude shaping pulse with various truncation lengths; β = 0.5. Truncation of the amplitude shaping pulse leads to side-lobe regeneration.
5.4 Phase Shift Keying and π/4-QDPSK
With phase shift keying, the complex envelope has the form
˜s(t)=A∑nb(t−nT,xn),(5.17)
where
b(t,xn)=ha(t)ejθn,(5.18)
ha(t) is the amplitude shaping pulse, and the excess phase takes on the values
θn=2πMxn,(5.19)
where xn ∈ {0,1, …, M − 1} and M is the size of the modulation alphabet. Each symbol xk is mapped onto log2M source bits. A quadrature phase shift-keyed (QPSK) signal is obtained by using M = 4 resulting in a transmission rate of 2 bits/symbol.
Unlike conventional QPSK that has four possible transmitted phases, π/4 phase-shifted quadrature differential phase shift keying (π/4-QDPSK) has eight possible transmitted phases. Let θn be the absolute excess phase for the nth data symbol, and let Δθn = θn − θn−1 be the differential excess phase. With π/4-DQPSK, the differential excess phase is related to the quaternary data sequence {xn}, xn ∈ {±1, ±3} through the mapping
Δθn=xnπ4.(5.20)
Note that the excess phase differences are ±π/4 and ±3π/4.
The complex envelope of the π/4-DQPSK signal is
˜s(t)=A∑nb(t−nT,xn),(5.21)
where
b(t,xn)=ha(t)exp{j(θn−1+xnπ4)}=ha(t)exp{jπ4(n−1∑k=−∞xk+xn)}.(5.22)
The summation in the exponent of Equation 5.22 represents the accumulated excess phase, while the last term is the excess phase increment due to the nth data symbol. The absolute excess phase during the even and odd baud intervals belongs to the sets {0,π/2,π,3π/2} and {π/4,3π/4,5π/4,7π/4}, respectively, or vice versa. With π/4-DQPSK the amplitude shaping pulse ha(t) is often chosen to be the root raised cosine pulse in Equation 5.14.
The signal-space diagrams for QPSK and π/4-DQPSK are shown in Figure 5.5, where Eh is the symbol energy. The dotted lines in Figure 5.5 show the allowable phase transitions. The phaser diagram for π/4-DQPSK with root raised cosine amplitude pulse shaping is shown in Figure 5.6. Note that the phase trajectories do not pass through the origin. Like OQPSK, this property reduces the peak-to-average power ratio (PAPR) of the complex envelope, making the π/4-DQPSK waveform less sensitive to power amplifier nonlinearities. Finally, we observe that the excess phase of π/4-DQPSK changes by ±π/4 or ±3π/4 radians during every baud interval. This property makes symbol synchronization easier with π/4-DQPSK as compared with QPSK.
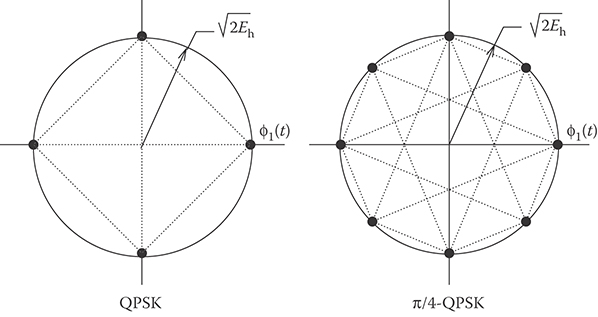
FIGURE 5.5 Complex signal-space diagram QPSK and π/4-DQPSK signals.
The power density spectrum of QPSK and π/4-QPSK is given by
S˜s˜s(f)=A22T|Ha(f)|2.(5.23)
Note that π/4-DQPSK has the same power spectrum as QPSK. Of course π/4-DQPSK has a lower PAPR than QPSK.
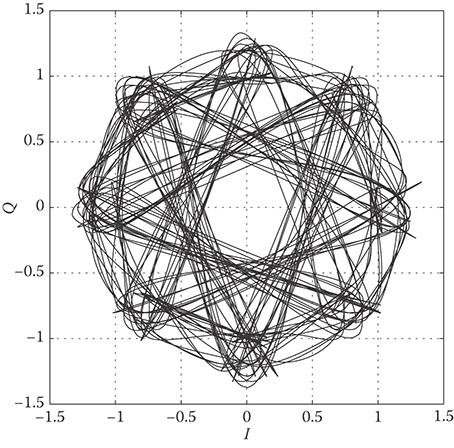
FIGURE 5.6 Phaser diagram for π/4-DQPSK with root raised cosine amplitude pulse shaping; β = 0.5.
5.5 Continuous Phase Modulation, Minimum Shift Keying, and GMSK
Continuous phase modulation (CPM) refers to a broad class of FM techniques where the carrier phase varies in a continuous manner. A comprehensive treatment of CPM is provided in Reference 2. CPM schemes are attractive because they have constant envelope and excellent spectral characteristics. The complex envelope of a CPM waveform has the general form
˜s(t)=Aej(ϕ(t)+θ0),(5.24)
where A is the amplitude, θ0 is initial carrier phase at t = 0, and
ϕ(t)=2πht∫0∞∑k=0xkhf(τ−kT) dτ(5.25)
is the excess phase, h is the modulation index, {xk} is the data symbol sequence, hf(t) is the frequency shaping pulse, and T is the baud period. The CPM waveform can be written in the standard form
˜s(t)=A∑nb(t−nT,xn)(5.26)
where
b(t,xn)=ej2πh∫t0∑∞k=0xkhf(τ−kT)dτuT(t)(5.27)
xn = (xn, xn−1, …, x0), and we have assumed an initial phase θ0 = 0. CPM waveforms have the following properties:
The data symbols are chosen from the alphabet {±1, ±3, …, ±(M − 1)}, where M is the modulation alphabet size and M is even.
h is the modulation index and is directly proportional to the peak and/or average frequency deviation from the carrier. The instantaneous frequency deviation from the carrier is
fdev(t)=12πdϕ(t)dt=h∞∑k=0xkhf(t−kT).(5.28)
fdev(t)=12πdϕ(t)dt=h∑k=0∞xkhf(t−kT).(5.28) hf(t) is the frequency shaping function, which is zero for t < 0 and t > LT, and normalized to have an area equal to 1/2. Full response CPM has L = 1, while partial response CPM has L > 1.
5.5.1 Minimum Shift Keying
Minimum shift keying (MSK) is a special form of binary CPM (xk ∈ {−1, +1}) that uses a rectangular frequency shaping pulse hf(t) = (1/2T)uT(t), and a modulation index h = 1/2. In this case,
b(t,xn)=ej(π2∑n−1k=0xk+π2xntT)uT(t).(5.29)
where uT(t) = u(t) - u(t - T) and u(t) is the unit step function.

FIGURE 5.7 Phase-trellis for MSK.
The MSK waveform can be described by the phase trellis diagram shown in Figure 5.7 which plots the time behavior of the excess phase
ϕ(t)=π2n−1∑k=0xk+π2xnt−nTT.(5.30)
At the end of each symbol interval the excess phase φ(t) takes on values that are integer multiples of π/2. Since excess phases that differ by integer multiples of 2π are indistinguishable, the values taken by φ(t) at the end of each symbol interval belong to the finite set {0, π/2, π, 3π/2}.
An interesting property of MSK can be observed from the MSK bandpass waveform. The bandpass waveform on the interval [nT,(n + 1)T] can be obtained from Equation 5.29 as
s(t)=Acos(2πfct+π2n−1∑k=0xk+π2xnt−nTT)=Acos(2π(fc+xn4T)t+π2n−1∑k=0xk−πn2xn).(5.31)
Observe that the MSK bandpass waveform has one of two possible frequencies in each baud interval
fL=fc−14T and fU=fc+14T(5.32)
depending on the data symbol xn. The difference between these two frequencies is fU − fL = 1/(2T). This is the minimum frequency separation to ensure orthogonality between two cophased sinusoids of duration T and, hence, the name minimum shift keying.
Another interesting representation for MSK waveforms can be obtained by using Laurent's decomposition [3] to express the MSK complex envelope in the quadrature form
˜s(t)=A∑nb(t−2nT,xn),(5.33)
where
b(t,xn)=ˆx2n+1ha(t−T)+jˆx2nha(t)(5.34)
and where xn=(ˆx2n+1,ˆx2n)
ˆx2n=ˆx2n−1x2n(5.35)
ˆx2n+1=−ˆx2nx2n+1(5.36)
ˆx−1=1(5.37)
ha(t)=sin(πt2T)u2T(t).(5.38)
The sequences, {ˆx2n}
To obtain the power density spectrum of MSK, we observe from Equation 5.34 that the MSK baseband signal has the quadrature form
˜s(t)=A∑nb(t−2nT,xn),(5.39)
where
b(t,xn)=ˆx2n+1ha(t−T)+jˆx2nha(t)(5.40)
ha(t)=sin(πt2T)u2T(t),(5.41)
xn=(ˆx2n+1,ˆx2n)
B(f,xn)=(ˆx2n+1e−j2πfT+jˆx2n)Ha(f).(5.42)
Since the data sequence is zero-mean and uncorrelated, the MSK psd is
Sb,0(f)=12E[|B(f,x0)|2]=12E[ˆx21+ˆx20]|Ha(f)|2=|Ha(f)|2.(5.43)
The Fourier transform of the HS pulse in Equation 5.38 is
Ha(f)=2Tπ(1−(4fT)2)(1+e−j4πfT).(5.44)
Hence, the power spectrum becomes
S˜s˜s(f)=A2T| Ha(f) |2=16A2Tπ2[cos2(2πfT)1−(4fT)2]2.(5.45)
The PSD of MSK is plotted in Figure 5.10. Observe that an MSK signal has fairly large sidelobes compared to π/4-QPSK with a truncated square root raised cosine pulse (cf. Figure 5.4).
5.5.2 Gaussian Minimum Shift Keying
The MSK power spectrum has a relatively broad main lobe and slow roll-off of side lobes. A more compact power spectrum can be achieved by low-pass filtering the MSK modulating signal
x(t)=∞∑n=−∞xnhf(t−nT)=12T∞∑n=−∞xnuT(t−nT)(5.46)
prior to FM as shown in Figure 5.8. Such filtering suppresses the higher-frequency components in x(t) thus yielding a more compact power spectrum. GMSK is a special type of partial response CPM that uses a low-pass premodulation filter having the transfer function [4]
H(f)=exp{−(fB)2ln22},(5.47)
where B is the 3 dB bandwidth of the filter. It is apparent that H( f ) is shaped like a Gaussian probability density function with mean f = 0 and, hence, the name “Gaussian” MSK. Convolving the rectangular pulse
12Trect(t/T)=12TuT(t+T/2)with the corresponding filter impulse response h(t) yields the frequency shaping pulse
hf(t)=12T√2πln2(BT)t/T+1/2∫t/T−1/2exp{−2π2(BT)2x2ln2} dx=12T[Q(t/T−1/2σ)−Q(t/T+1/2σ)],(5.48)
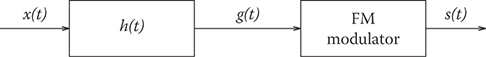
FIGURE 5.8 Premodulation filtered MSK. The MSK modulating signal is low-pass filtered to remove the high-frequency components prior to FM.

FIGURE 5.9 GMSK frequency shaping pulse for various normalized premodulation filter bandwidths BT.
where
Q(α)=∫∞α1√2πe−x2 dx(5.49)
σ2=ln24π2(BT)2.(5.50)
Figure 5.9 plots the GMSK frequency shaping pulse (truncated to 5T and time shifted by 2.5T to yield a causal pulse) for various normalized premodulation filter bandwidths BT. The popular GSM cellular standard uses GMSK with BT = 0.3.
The power density spectrum of GMSK is quite difficult to obtain, but can be computed by using published methods [5]. Figure 5.10 plots the power density spectrum for BT = 0.2, 0.25, and 0.3, obtained from K. Wesolowski (private comm., 1994). Observe that the spectral sidelobes are greatly reduced by the Gaussian low-pass filter.
5.6 Orthogonal Frequency Division Multiplexing
Orthogonal frequency division multiplexing (OFDM) is a block modulation scheme where data symbols are transmitted in parallel on orthogonal subcarriers. A block of N data symbols, each of duration Ts, is converted into a block of N parallel data symbols, each of duration T = NTs. The N parallel data symbols modulate N subcarriers that are spaced in frequency 1/T Hz apart. The OFDM complex envelope is given by
˜s(t)=A∑nb(t−nT,xn),(5.51)
where
b(t,xn)=uT(t)N−1∑k=0xnkej2πktT(5.52)
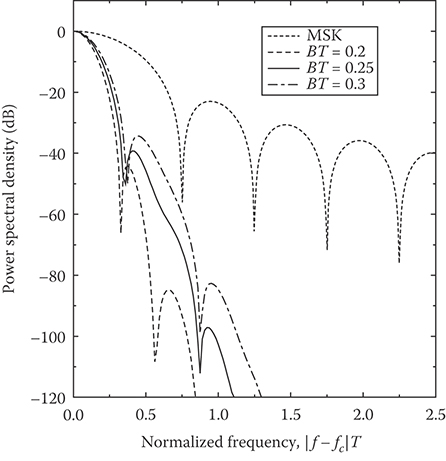
FIGURE 5.10 Power density spectrum of MSK and GMSK.
n is the block index, k is the subcarrier index, N is the number of subcarriers, and xn={xn0,xn1,…,xnN−1}
A cyclic extension (or guard interval) is usually added to the OFDM waveform in Equations 5.51 and 5.52 to combat delay spread. The cyclic extension can be in the form of either a cyclic prefix or a cyclic suffix. With a cyclic suffix, the OFDM complex envelope becomes
˜sg(t)={˜s(t),0≤t≤T˜s(t−T),T≤t≤(1+αg)T,(5.53)
where αgT is the length of the guard interval and ˜s(t)
˜sg(t)=A∑nb(t−nTg,xn),(5.54)
where
b(t,xn)=uT(t)N−1∑k=0xnkej2πktT+uαgT(t−T)N−1∑k=0xnkej2πk(t−T)T,(5.55)
and Tg = (1 + αg)T is the OFDM symbol period with the addition of the guard interval. Likewise, with a cyclic prefix, the OFDM complex envelope becomes
˜sg(t)={˜s(t+T),−αgT≤t≤0˜s(t),0≤t≤T,(5.56)
and
b(t,xn)=uαgT(t+αgT)N−1∑k=0xnkej2πk(t+T)T+uT(t)N−1∑k=0xnkej2πktT.(5.57)
5.6.1 FFT Implementation of OFDM
A key advantage of using OFDM is that the baseband modulator can be implemented by using an inverse discrete-time Fourier transform (IDFT). In practice, an inverse fast Fourier transform (IFFT) algorithm is used to implement the IDFT. Consider the OFDM complex defined by Equations 5.51 and 5.52. During the interval nT ≤ t ≤ (n + 1)T, the complex envelope has the form
˜s(t)=AuT(t−nT)N−1∑k=0xnkej2πk(t−nT)T=AuT(t−nT)N−1∑k=0xnkej2πktNTs, nT≤t≤(n+1)T.(5.58)
Now suppose that the complex envelope in Equation 5.58 is sampled at synchronized Ts second intervals to yield the sample sequence
Xnm=˜s(mTs)=AN−1∑k=0xnkej2πkmN, m=0,1,…,N−1.(5.59)
Observe that the vector Xn={Xnm}N−1m=0
As mentioned earlier, a cyclic extension (or guard interval) is usually added to the OFDM waveform as described in Equations 5.54 and 5.55 to combat delay spread. When a cyclic suffix is used, the corresponding sample sequence is
Xgnm=Xn(m)N(5.60)
=AN−1∑k=0xnkej2πkmN, m=0,1,…,N+G−1,(5.61)
where G is the length of the guard interval in samples, and (m)N is the residue of m modulo N. This gives the vector Xgn={Xgnm}N+G−1m=0
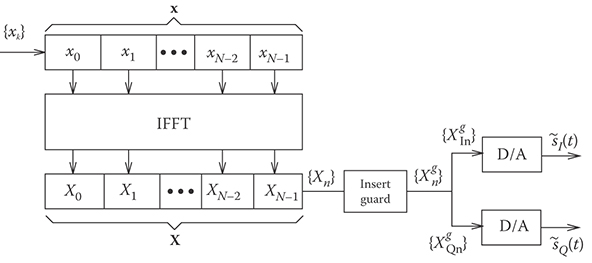
FIGURE 5.11 Block diagram of IDFT-based baseband OFDM modulator with guard interval insertion and digital-to-analog conversion.
Xgnm=Xn(m)N(5.62)
=AN−1∑k=0xnkej2πkmN, m=−G, …,−1, 0, 1, …, N−1.(5.63)
This yields the vector Xgn={Xgnm}N−1m=−G
The OFDM complex envelope can be generated by splitting the complex-valued output vector Xm into its real and imaginary parts, ℜ(Xn) and ℑ(Xn)
It is instructive to realize that the waveform generated by using the IDFT OFDM baseband modulator is not exactly the same as the waveform generated from the analog waveform definition of OFDM. Consider for example, the OFDM waveform without a cyclic guard in Equations 5.51 and 5.52. The analog waveform definition uses the rectangular amplitude shaping pulse uT(t) that is strictly time limited to T seconds. Hence, the corresponding power spectrum will have infinite bandwidth, and any finite sampling rate of the complex envelope will necessarily lead to aliasing and imperfect reconstruction.
5.6.2 Power Spectrum of OFDM
To compute the power spectrum of OFDM, recall that the OFDM waveform with guard interval is given by Equations 5.54 and 5.55. The data symbols xnk
S˜s˜s(f)=A2TgSb,0(f),(5.64)
where
Sb,0(f)=12E[|B(f,x0)|2],(5.65)
and
B(f,x0)=N−1∑k=0x0kTsinc(fT−k)+N−1∑k=0x0kαgTsinc(αg(fT−k))ej2πfT.(5.66)
Substituting Equation 5.66 into Equation 5.65 along with T = NTs yields the result
S˜s˜s(f)=σ2xA2T(11+αgN−1∑k=0sinc2(NfTs−k)+α2g1+αgN−1∑k=0sinc2(αg(NfTs−k))+2αg1+αgcos(2πNfTs)N−1∑k=0sinc(NfTs−k)sinc(αg(NfTs−k))).(5.67)
The OFDM PSD is plotted in Figure 5.12 for N = 16, αg = 0.25.
It is interesting to examine the OFDM power spectrum, when the OFDM complex envelope is generated by using an IDFT baseband modulator followed by a balanced pair DACs as shown in Figure 5.11. The output of the IDFT baseband modulator is given by {Xg}={Xgm,n}
Xgm,n=Xm,(n)N(5.68)
=AN−1∑k=0xm,kej2πknN, n=0, 1, …, N+G−1.(5.69)

FIGURE 5.12 PSD of OFDM with N = 16, αg = 0.25.
The power spectrum of the sequence {Xg} can be calculated by first determining the discrete-time autocorrelation function of the time-domain sequence {Xg} and then taking a discrete-time Fourier transform of the discrete-time autocorrelation function. The PSD of the OFDM complex envelope with ideal DACs can be obtained by applying the resulting power spectrum to an ideal low-pass filter with a cutoff frequency of 1/(2Tgs) Hz
The discrete-time autocorrelation function of the sequence {Xg} is
ϕXgXg(ℓ)={Aσ2Xℓ=0GN+GAσ2Xℓ=−N, N0otherwise.(5.70)
Taking the discrete-time Fourier transform of the discrete-time autocorrelation function in Equation 5.70 gives
SXgXg(f)=Aσ2x(1+GN+Ge−j2πfNTgs+GN+Gej2πfNTgs)=Aσ2x(1+2GN+Gcos(2πfNTgs)).(5.71)
Finally, we assume that the sequence {Xg}={Xgm,n} is passed through a pair of ideal DACs. The ideal DAC is a low-pass filter with cutoff frequency 1/(2Tgs). Therefore, the OFDM complex envelope has the PSD
S˜s˜s(f)=Aσ2x(1+2GN+Gcos(2πfNTgs)) rect(fTgs).(5.72)
Figure 5.13 plots the PSD for N = 16 and G = 4.
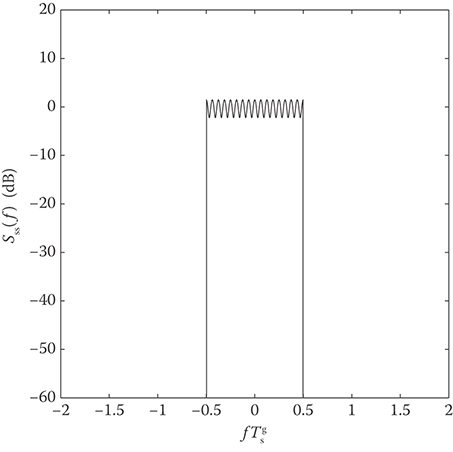
FIGURE 5.13 PSD of IDFT-based OFDM with N = 16, G = 4.
Finally, we note that the PSD plotted in Figure 5.13 assumes an ideal DAC. A practical DAC with a finite-length reconstruction filter will introduce sidelobes into the spectrum. We note that sidelobes are an inherent feature of the continuous-time OFDM waveform in Equations 5.54 and 5.55 due to the use of rectangular amplitude pulse shaping on the subcarriers. However, sidelobes are introduced into the waveform generated with the IDFT implementation by the nonideal (practical) DAC.
5.7 Summary and Conclusions
A variety of modulation schemes are employed in digital communication systems. Wireless modulation schemes in particular must have a compact power density spectrum, while at the same time providing a good bit error rate performance in the presence of channel impairments such as cochannel interference and fading. This chapter has presented a variety of modulation schemes along with their power spectra.
References
1. G. L. Stüber, Principles of Mobile Communication, 3rd edn, Springer Science + Business Media, 2011.
2. J. B. Anderson, T. Aulin, and C. E. Sundberg, Digital Phase Modulation. New York, NY: Plenum, 1986.
3. P. A. Laurent, Exact and approximate construction of digital phase modulations by superposition of amplitude modulated pulses (AMP). IEEE Trans. Commun., 34, 150–160, 1986.
4. K. Murota and K. Hirade, GMSK modulation for digital mobile radio telephony. IEEE Trans. Commun., 29(July), 1044–1050, 1981.
5. G. J. Garrison, A power spectral density analysis for digital FM. IEEE Trans. Commun., 23(November), 1228–1243, 1975.
Further Reading
A good discussion on modulation techniques can be found in Digital Communications, 5th edn., J. G. Proakis and M. Salehi, McGraw-Hill, 2008. Also Principles of Mobile Communication, 3rd edn., G. L. Stüber, Springer Science + Business Media, 2011.
Proceedings of various IEEE conferences such as the Vehicular Technology Conference, International Conference on Communications, and Global Telecommunications Conference, document the latest developments in the field of wireless communications each year.
Journals such as the IEEE Transactions on Communications, IEEE Transactions on Wireless Communications, IEEE Transactions on Vehicular Technology report advances in wireless modulation.
