14. Securing and Protecting Your Mac
In this chapter, you learn the steps that you can take to secure your Mac and its data, including:
![]() Keeping passwords in Keychain
Keeping passwords in Keychain
![]() Encrypting your account data
Encrypting your account data
![]() Activating the Yosemite firewall
Activating the Yosemite firewall
![]() Backing up your files and information
Backing up your files and information
![]() Using Time Machine to restore backups
Using Time Machine to restore backups
![]() Accessing previous files with Versions
Accessing previous files with Versions
Security on a computer is important—increasingly we store our lives on our computers. We save our memories, our music and video, and our important documents. Having a computer stolen (or losing the contents of your hard drive) can be more traumatic than losing a credit card. Practicing appropriate account, application, and information security can ensure that even if the worst happens, your data remains private.
In addition to protecting your information from theft and unauthorized access, you should take steps to ensure the data’s availability—in other words, you should ensure that your files are available when you need them. By backing up your computer, you can be sure that even in the event your computer is stolen or its hard drive crashes, your work is protected.
Working with Users and Groups
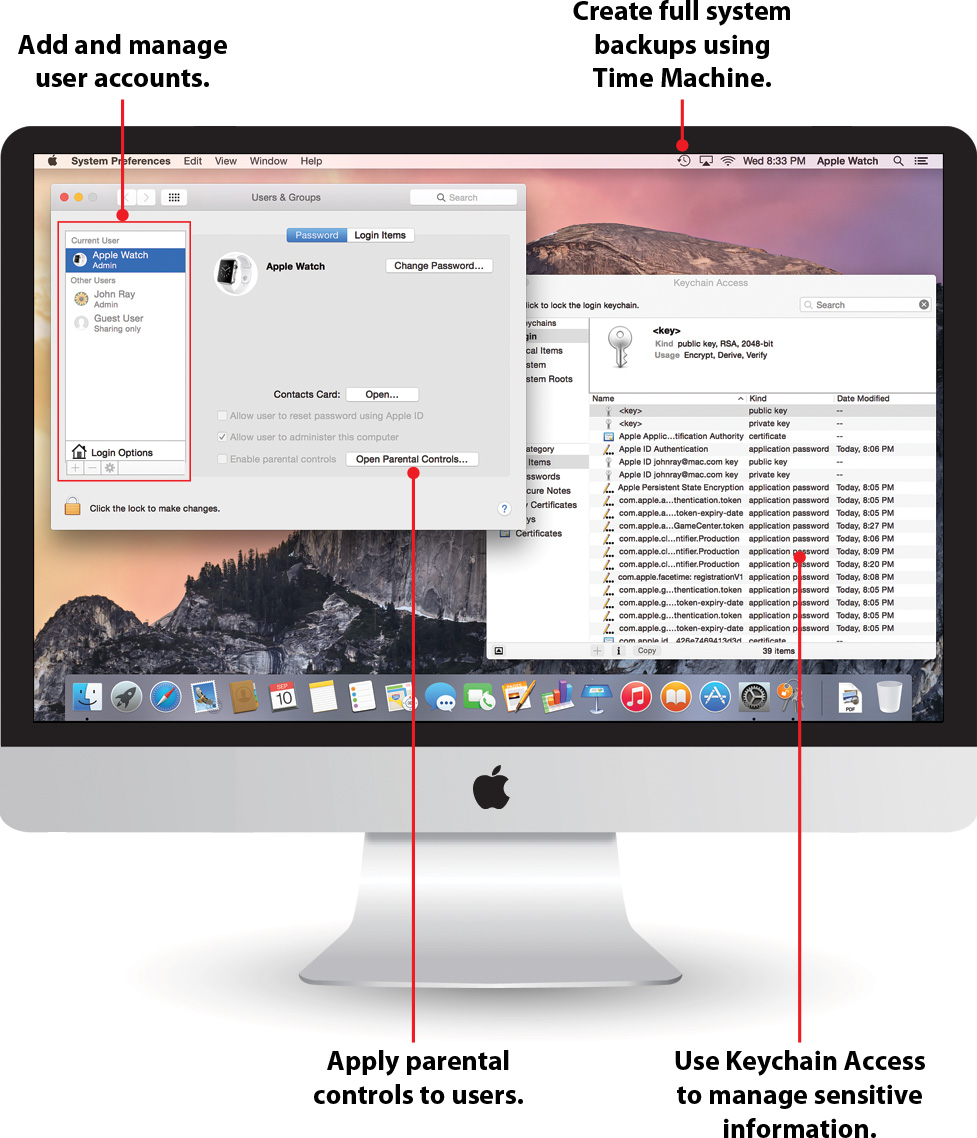
The Yosemite operating system can accommodate multiple users—family members, friends, co-workers, and even guests. By creating and using different accounts, you can limit access to files. In addition, you can combine individual users into groups that have access controls.
Creating User Accounts
When creating a user account, you can control what the users can do by assigning them an account type. There are five account types in Yosemite:
Administrator—An account with full control over the computer and its settings
Standard—An account that can install software and work with the files within the individual account
Managed with Parental Controls—A standard user account that includes parental controls to limit account and application access
Sharing Only—An account that can only be used to access shared files, but not to log into the system
Guest—A preconfigured account that allows the user to log in and use the computer but that automatically resets to a clean state upon logout
By default, your account is an Administrator account, but you should create additional user accounts based on what the users need to do.
Unlock Your Preferences
Before making changes to many of the system preferences, you may first need to click the Lock icon in the lower-left corner of the preference panel and supply your username and password. This extra step is frequently required to help prevent unwanted changes to your Mac.
1. Open the System Preferences window and click the Users & Groups icon.
2. Click the + button below the user list to add a new user.
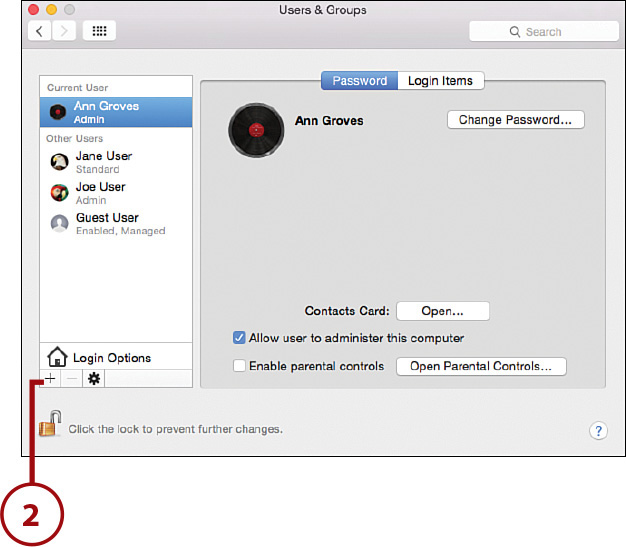
3. The account creation window appears. Use the New Account pop-up menu to choose the account type you want to create.
4. Enter the full name of the user you’re adding.
5. Type the account name for the user. This is the username the person uses to access all Yosemite services.
6. Choose whether to use an iCloud password or a separate password for the account. (A separate password is demonstrated here.)
7. Type a new password for the account into the Password and Verify fields.
8. If desired, provide a hint for the password. The hint is displayed after three unsuccessful login attempts.
9. Click Create User.
10. Close the System Preferences.

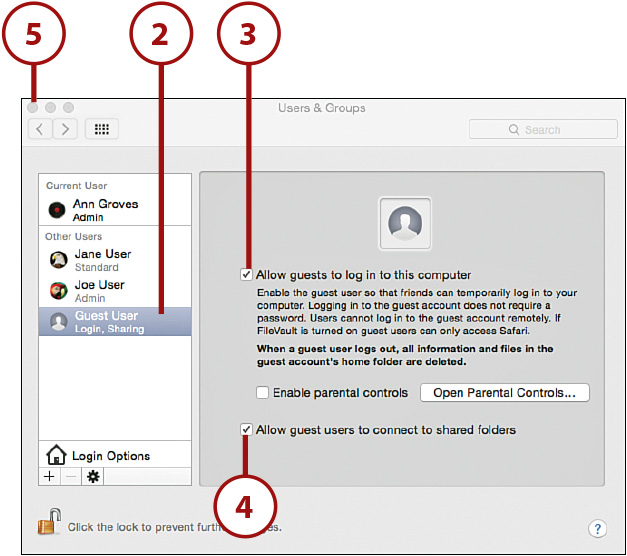
Enabling the Guest Account
The Guest account provides a simple means of giving anyone access to the computer for a short period of time. To enable the Guest account, follow these steps:
1. Open the System Preferences window and click the User & Groups icon.
2. Click the Guest User item within the account list.
3. Check the Allow Guests to Log in to This Computer checkbox.
4. To allow guest access to shared folders, click Allow Guest Users to Connect to Shared Folders.
5. Close the System Preferences.
Applying Parental Controls
If you’ve created a managed account with Parental Controls, or have enabled the Guest account, you can configure which applications a user can run, when the user can run the programs, and what parts of the Internet the user can access.
1. Open the System Preferences window and click the Parental Controls icon.
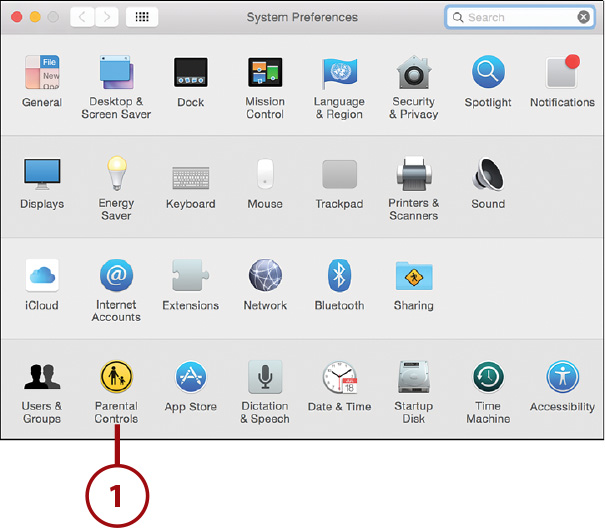
2. Choose the account you want to configure.
3. Click Enable Parental Controls.

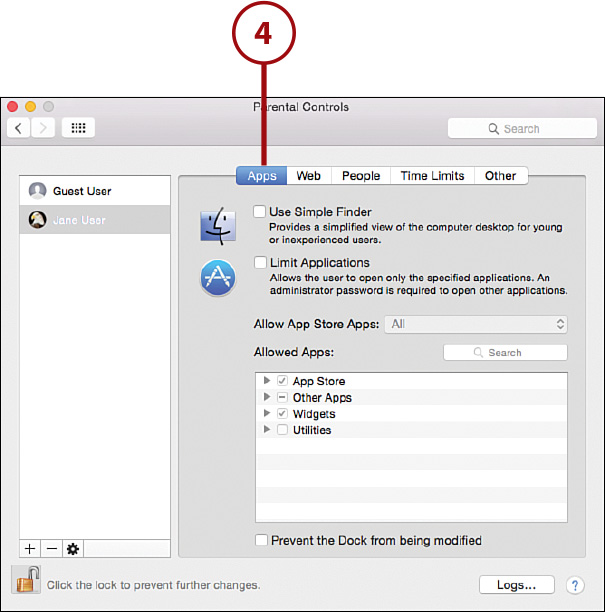
4. Click the Apps button to choose which applications the user can use, what privileges are available in the Finder, what age range of apps can be accessed in the App Store, and whether the Dock can be modified.
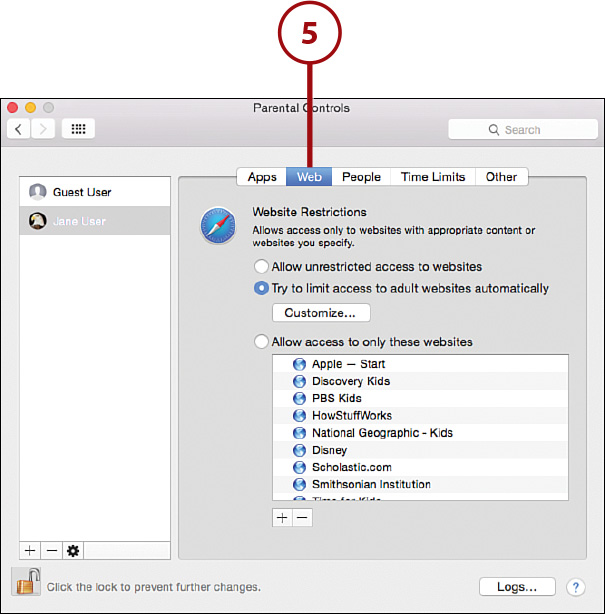
5. Use the Web button to restrict access to websites.
Managed Versus Standard
If you’ve created a Standard account type, you can convert it to a Managed account with Parental Controls by selecting it in the Parental Controls list and then clicking the Enable Parental Controls button.
6. Select the People button to limit the individuals the user can email, message, or game with.
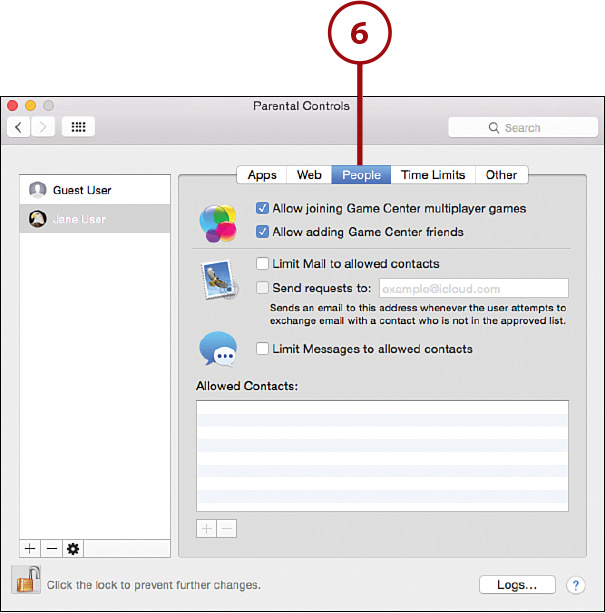
7. Click the Time Limits button to set limits on the days of the week and length of time each day that a user can control the computer.
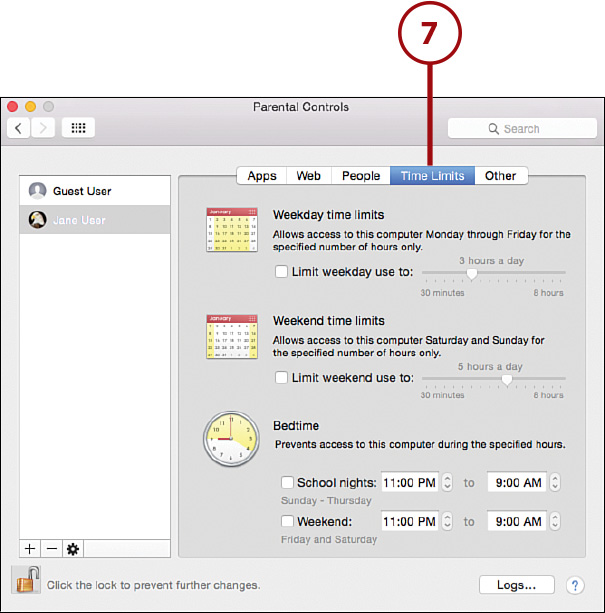
8. Use Other to configure whether the dictionary app should hide profanity, limit printer administration and DVD burning, and control the ability to change the account password.
9. Close the System Preferences.
iCloud Password Without the Cloud
If you choose to create an account using an iCloud password only, you’ll have to provide the account name to Yosemite. There’s nothing wrong with this approach, but keep in mind that the computer will need to be connected to the Internet to sync with your iCloud password. If your system isn’t Internet connected, or connects rarely, you might have trouble with this feature.
Creating Groups
For individuals who should have the same kind of access rights (such as your co-workers), you can group them together. You can then use that group in other parts of Yosemite (such as setting file permissions) to refer to all of the accounts at one time.
1. Open the System Preferences window and click the Users & Groups icon.
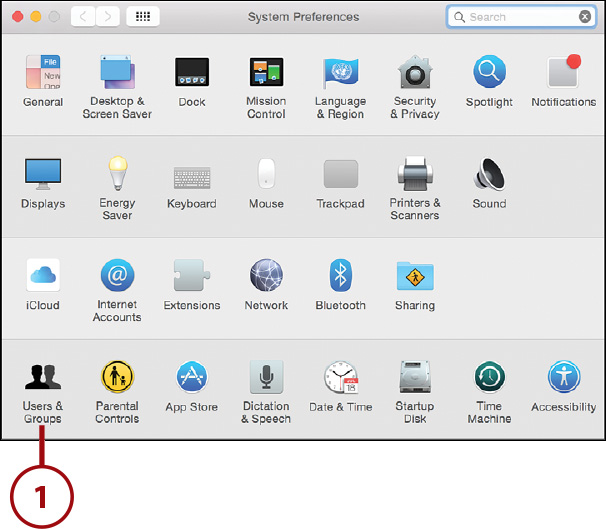
2. Click the + button below the account list to add a new account.
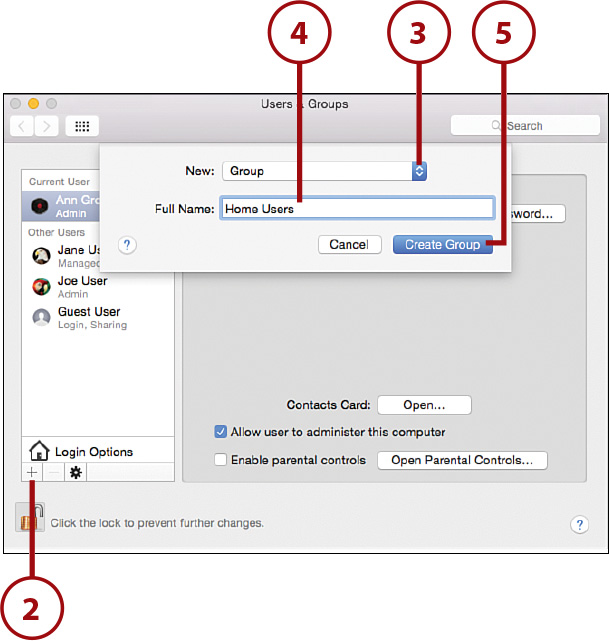
3. The account creation window appears. Use the New Account pop-up menu to choose Group.
4. Enter a name for the group.
5. Click Create Group.
6. The group appears in the account list. Make sure it is selected.
7. Click the checkboxes in front of each user who should be a member of the group.
8. Close the System Preferences.

Configuring General Account Security
To better protect user accounts from potential security problems, Yosemite has a range of security settings in one place.
1. Open the System Preferences window and click the Security & Privacy icon.

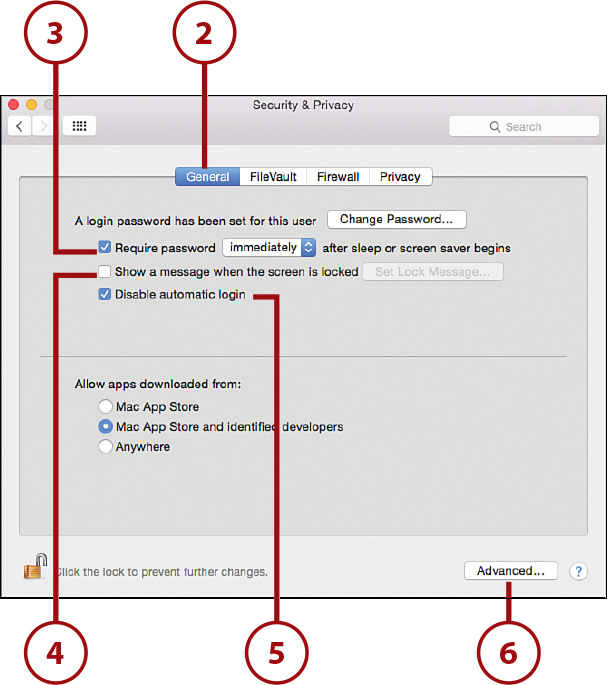
2. Click the General button.
3. Check Require Password and set the pop-up menu to Immediately so that a password is required to wake your computer after the screen saver kicks in.
4. If desired, set a message to display when the screen is locked.
5. Check Disable Automatic Login to disable access to your Mac without a valid username and password.
6. Click the Advanced button.
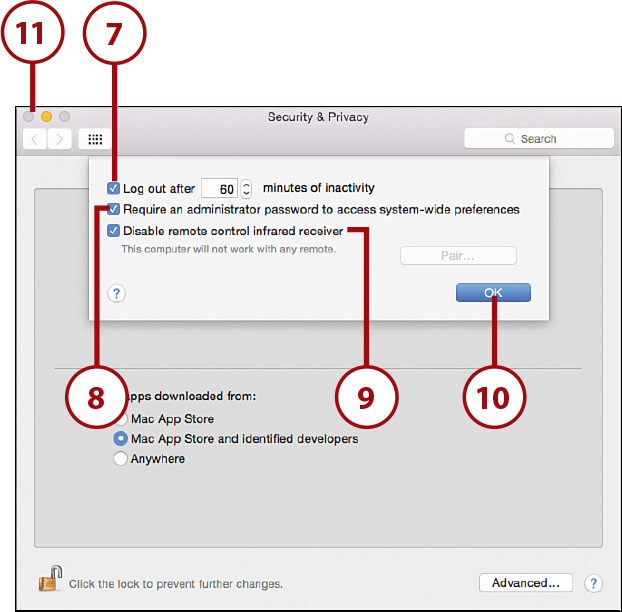
7. Check Log Out after 60 Minutes of Inactivity. You might want to adjust the time to a shorter period. After this option is set, you are automatically logged out of your Mac if you don’t use it for the designated amount of time.
8. Choose to require an administrator password to access locked preferences.
9. Check Disable Remote Control Infrared Receiver. This prevents an infrared remote control from being paired with this computer and does not allow you to use a remote with the computer.
10. Click OK.
11. Close the System Preferences.
Assigning File Permissions for Users and Groups
After you’ve created users and groups, you can begin protecting files and folders so that certain users can access them but others can’t:
1. Select a file or folder in the Finder.
2. Choose Get Info from the File menu.

3. Open the Sharing & Permissions section of the information window.
4. Click the + button to add a user or group to the permission list.
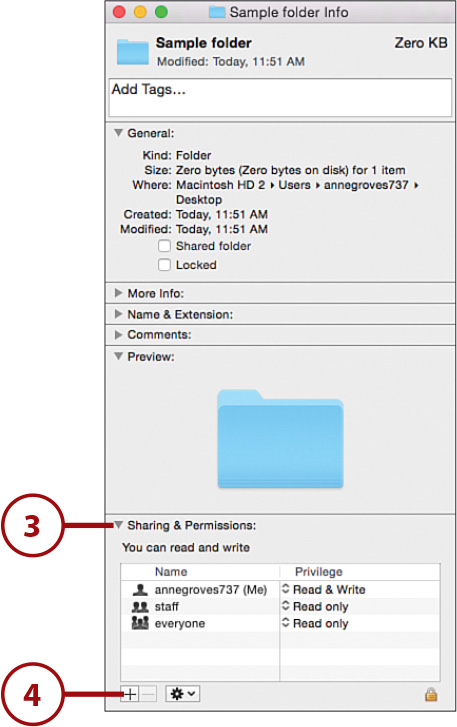
5. Choose a user or group from the window that opens.
6. Click Select.
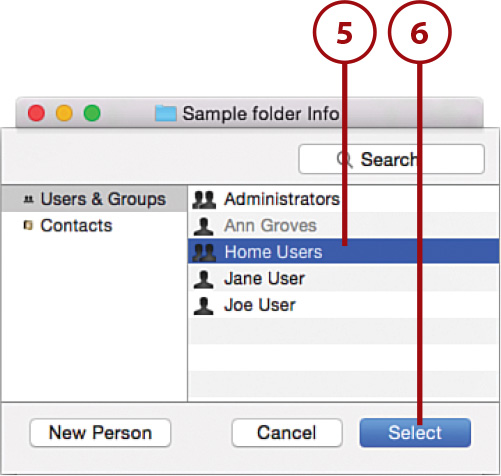
7. Use the pop-up menu in the Privilege column to the right of the user or group to set whether the user can read only, read and write, or write only.
8. To remove access for a user or group, select it and click –.
9. Close the Info window.
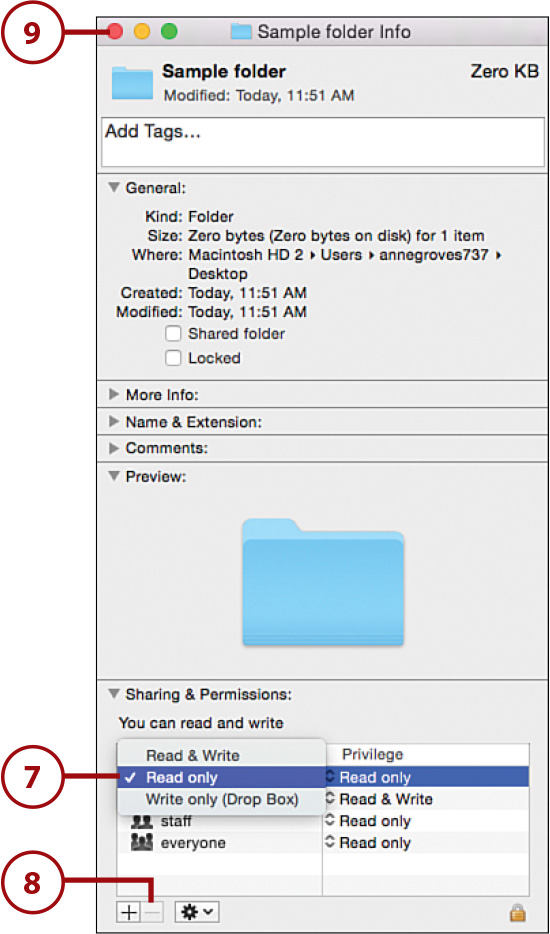
Choose Your Permissions
In addition to these permissions, you can set permissions for network shares. The sharing permissions (see Chapter 6, “Sharing Files, Devices, and Services”) define who can access a folder over the network. The file permissions, however, can also limit access to the files and folders within a share, or who can see the files and folders when they’re logged directly into your computer.
Tracking Passwords with Keychain Access
When you use Safari, connect to file shares, or use other secure services, you’re frequently prompted to Save to Keychain. When you save your passwords, you’re storing them in a special system-wide database that manages secure information—called the keychain.
Unknown to many, you can use the Keychain Access utility (found in the Applications/Utilities folder or in the Utilities Launchpad group) to view and modify records in your keychain. You can even use Keychain Access to store arbitrary data (such as notes, passwords, and so on) that you’d like to have encrypted. Keychain values can only be accessed when the keychain is unlocked.
There are multiple different keychain databases you can access or create. By default, passwords and account information are stored in a keychain named Login, which is automatically unlocked when you log into your account.
Viewing Keychain Items
You can access your Login keychain entries at any time. To view an item that has been stored in your keychain, follow along with these steps:
1. Open the Keychain Access application from the Applications/Utilities folder or Launchpad.
2. Choose the keychain you want to view (Login is where most items are located).
3. Select the category of data you want to view.
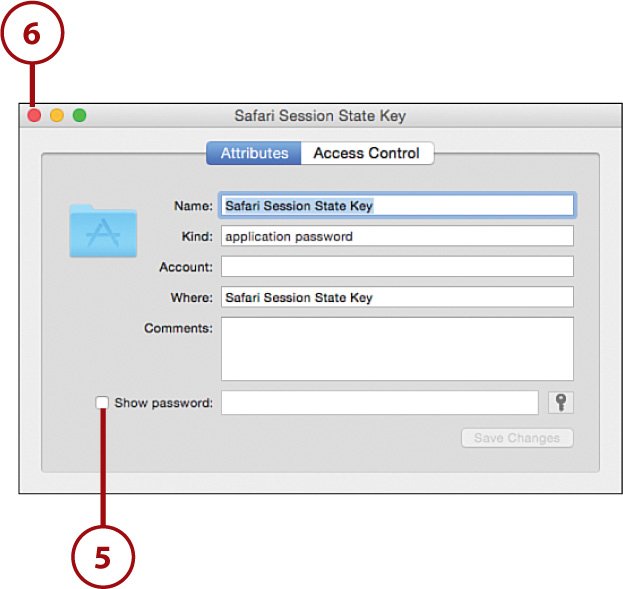
4. Double-click the keychain entry to open a window displaying the details.

5. Click Show Password to authenticate and display the keychain password in clear text.
6. Close the keychain entry window.
Adding Data to the Keychain
There are two types of information you can manually store in a keychain—secure notes and password items. Notes can be arbitrary text, and password items are generally a username, password, and a name for the item you’re adding.
Collect the information you want to add and then follow these steps:
1. Open the Keychain Access application.
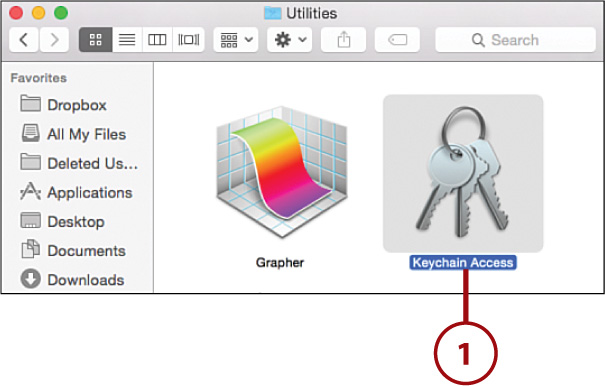
2. Choose the keychain you want to add data to.
3. Select the Passwords or Secure Notes categories to set which type of information you are storing.
4. Click the + button at the bottom of the Keychain Access window.
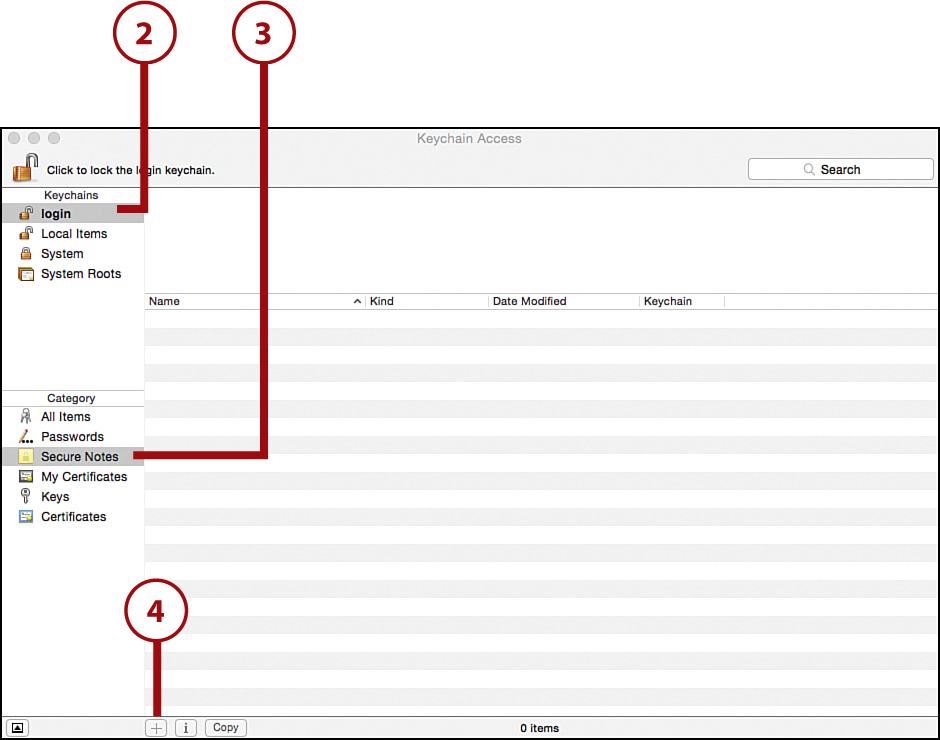
5. Enter your note or account information in the form that appears.
6. Click Add.

7. The new entry appears in the keychain.

Using the Password Assistant
When adding a new password, you might notice a key icon by the password field. Clicking the key launches a password assistant that creates a secure password for you. The key icon and password assistant are found throughout the Yosemite interface where passwords are required.
Creating a New Keychain
The Login keychain stores almost everything related to accounts you’ve configured in Yosemite, but because it is designed to be automatically unlocked at login, you might want to create another keychain that is only unlocked when you want it to be. To do so, follow these steps:
1. Open the Keychain Access application and choose File, New Keychain from the menu.
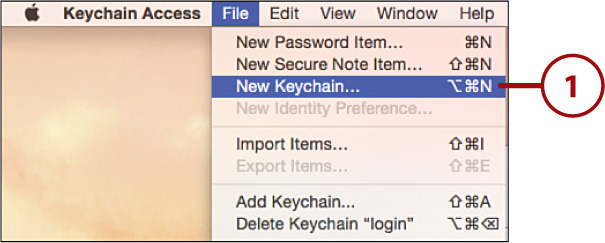
2. Enter a name for the keychain and then click Create.
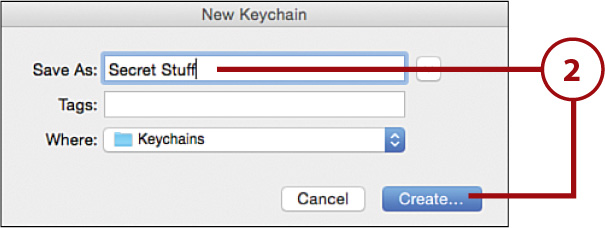
3. You are prompted for a password to secure the new keychain. Enter a secure password in the New Password and Verify fields.
4. Click OK.
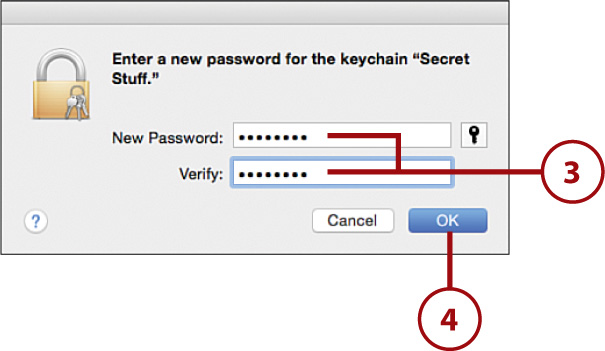
5. The new keychain is displayed in the keychain list and you can store any data you’d like in it.

6. Continue adding items or choose Keychain Access, Quit Keychain Access to exit (not shown).
Adding a Keychain Menu Item
To quickly unlock and lock keychains, you can add a keychain item to your menu bar:
1. Open the Keychain Access application and choose Keychain Access, Preferences from the menu.
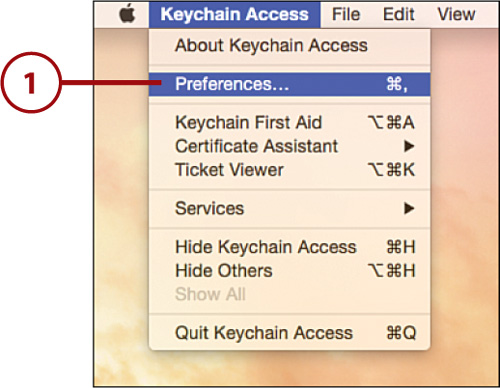
2. Click the General button at the top of the window.
3. Click Show Keychain Status in Menu Bar.
4. Close the Preferences.

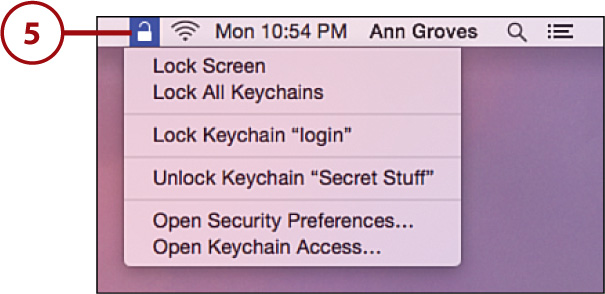
5. The Keychain Lock menu item is added, giving easy access to unlocking and locking your keychains.
Encrypting Your Yosemite Disk
One of the best ways to secure sensitive information is through encryption. The Keychain Utility provides an encryption feature for small pieces of data, but not for your documents. To fully encrypt all data on your Mac, you can make use of FileVault disk-level encryption.
1. Open the System Preferences window and click the Security & Privacy icon.
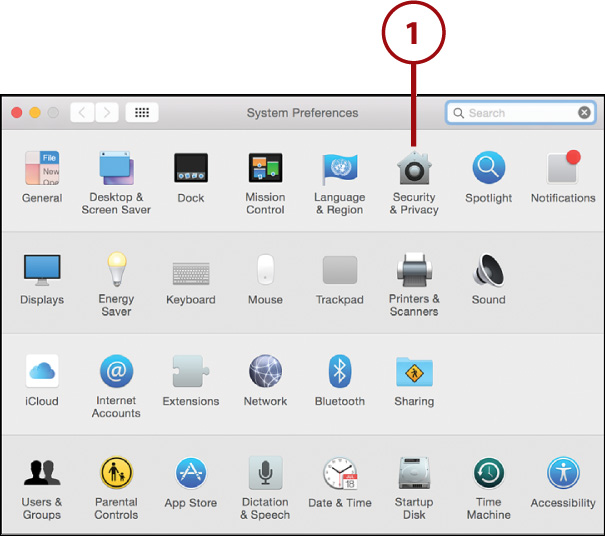
2. Click the FileVault button at the top of the panel.
3. Click Turn On FileVault.
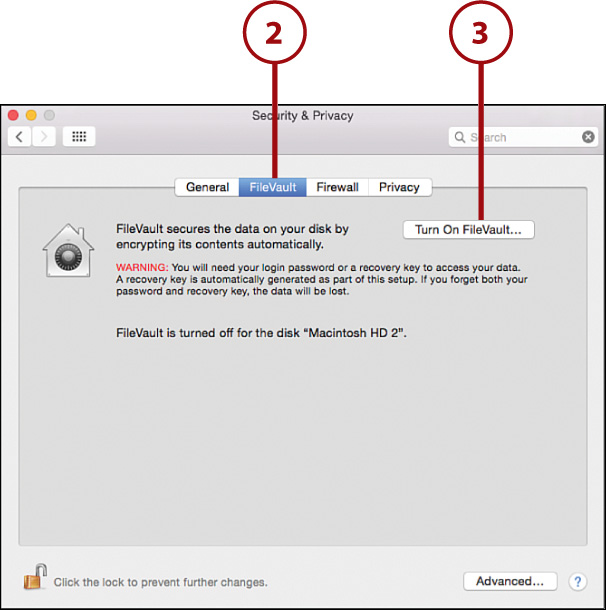
4. Choose whether your iCloud account can unlock FileVault if you forget your password. Alternatively, you can have FileVault create a recovery key that you must manually store in a secure location.
5. Click Continue.
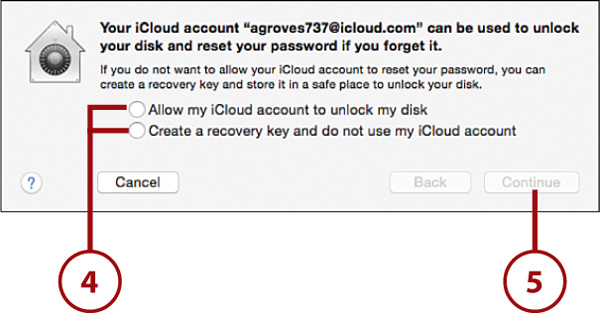
6. Click Enable User and supply each user’s password for those who should be able to unlock the protected disk. By default, the person activating FileVault will have access.
7. Click Continue.
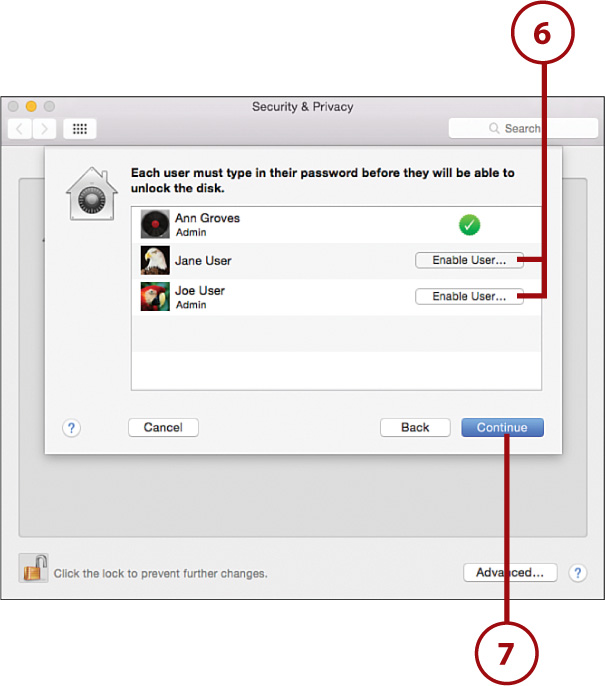
8. Click Restart to restart your Mac and begin encrypting your drive. This process takes place in the background so you can continue to use your computer as you normally would.
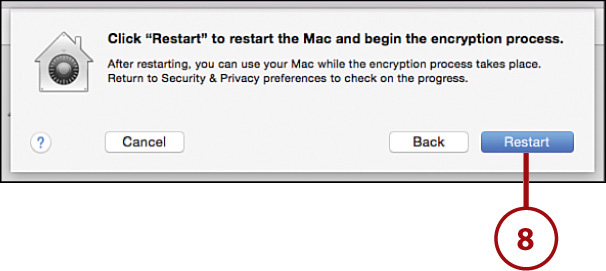
Effortless Encryption
FileVault encryption is completely transparent. Your entire disk is encrypted and made available to you when you log in. If another user tries to access files in your account, or even removes the drive from your computer to try to access its contents, they won’t be able to.
Limiting Application Execution
With Yosemite, you can limit your computer’s ability to run applications from sources other than the App Store or from developers who have registered an ID with Apple. Why would you want to do this? Because software from unknown sources can be hazardous to your system’s health!
By default, Yosemite enables you to install and use applications from the App Store and apps published separately from properly registered developers. To change this to better suit your sense of well-being, follow these steps:
1. Open the System Preferences window and click the Security & Privacy icon.
2. Click the General button at the top of the panel.
3. Use the radio buttons at the bottom of the window to choose which applications you want to be allowed on your system.
4. Close the System Preferences.
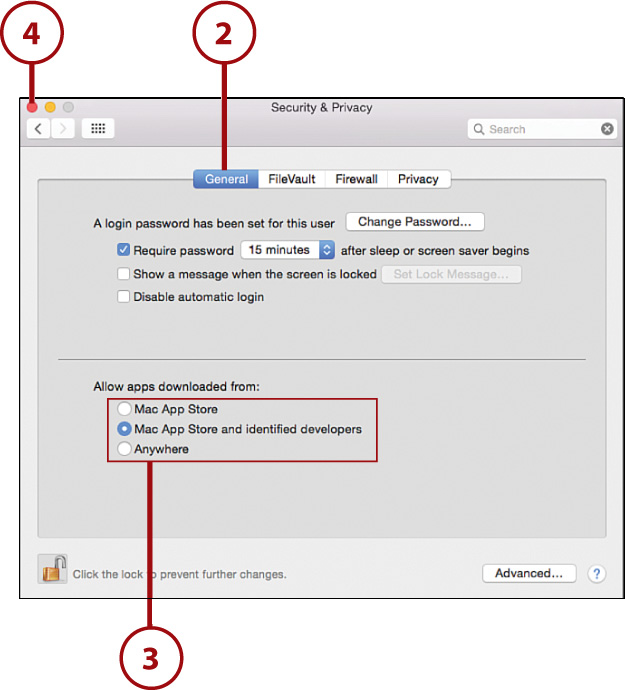
Everyone Is Affected!
The application limits that you set here apply to the entire system, so software that was previously installed and functional might stop working for everyone if you make changes.
Many power users will want to set the limit to allow applications downloaded from anywhere because this provides the greatest flexibility. Most of us, however, will be satisfied (and best protected) using the Mac App Store and Identified Developers setting.
Adding Network Security with the Built-In Firewall
Many applications you run open themselves to connections from the outside world—opening you, in turn, to Internet attacks. The purpose of a firewall is to block these connections before your computer accepts them. Yosemite offers an easy-to-configure firewall that lets you choose what network services your Mac exposes to the world.
1. Open the System Preferences window and click the Security & Privacy icon.
2. Click the Firewall button at the top of the panel.
3. Click Turn On Firewall.
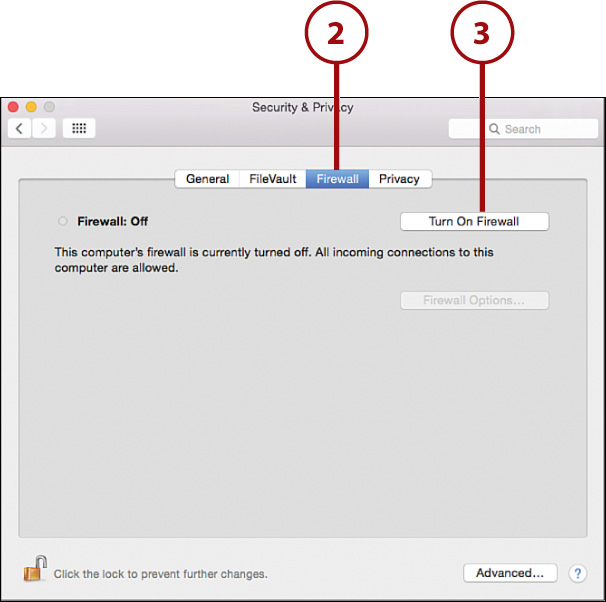
4. The circle beside the Firewall: Off label turns green and the label changes to Firewall: On to indicate that the firewall is active.
5. Close the System Preferences, or continue configuring Incoming Services.

Configuring Incoming Services
After your firewall is active, you need to choose which connections to allow and which to block. To define how the firewall reacts to incoming requests, use this process:
1. Open the System Preferences window and click the Security & Privacy icon.
2. Click the Firewall button at the top of the Panel.
3. Click Firewall Options.
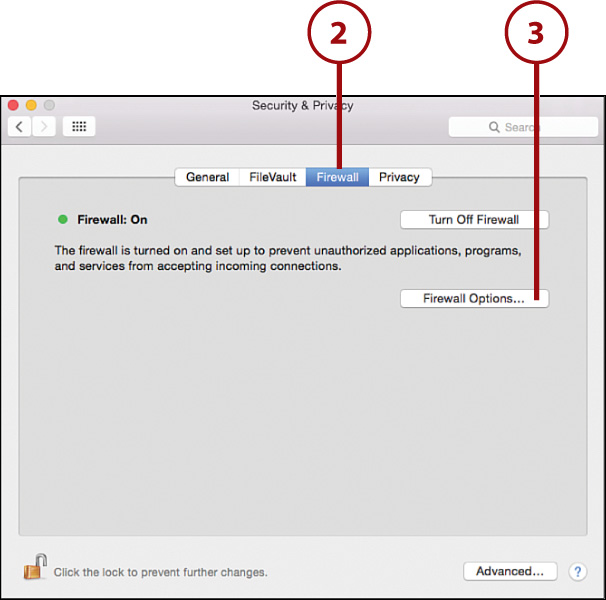
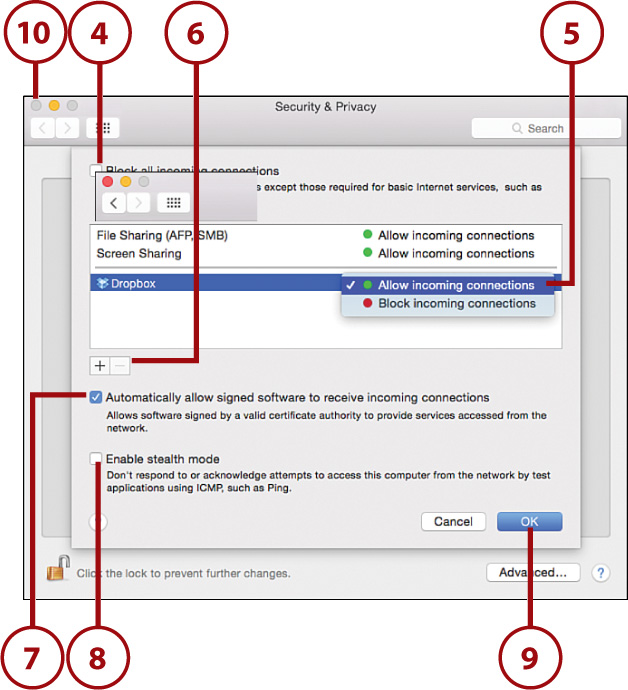
4. To block all incoming connections, click the Block All Incoming Connections checkbox.
5. Use the pop-up menu beside each of your running applications to choose whether it should allow or block incoming connections.
6. Add or remove applications from the list using the + and – buttons.
7. If you want applications that have been signed (where the publisher is a known and registered entity) to automatically accept connections, click the Automatically Allow Signed Software to Receive Incoming Connections checkbox.
8. Enable stealth mode if you’d like your computer to appear offline to most network device scans.
9. Click OK to save your configuration.
10. Close the Security & Privacy Preferences panel.
An application being signed does not make it more or less susceptible to network attack. It does, however, give you a degree of certainty that the application is not a Trojan horse or spyware.
Hiding Location Information and Application Data
If you have an iOS device, you’re probably accustomed to it asking you if it can share your location with an application. In Yosemite, the operating system can also determine your approximate location and share that information as well. It can also collect information on your application usage and send it to Apple for use in “improving its products.” If you’d prefer not to make this information available, follow these steps:
1. Open the System Preferences and click the Security & Privacy icon.
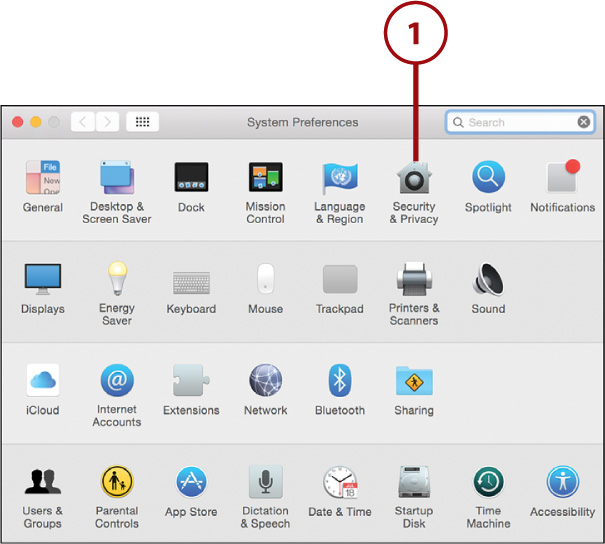
2. Click the Privacy button at the top of the panel.
3. Select a category of information to protect, such as your location, your contacts (address book), and information about your application usage.
4. Use the controls associated with each type of data to enable or disable access to it.
5. Close the System Preferences.
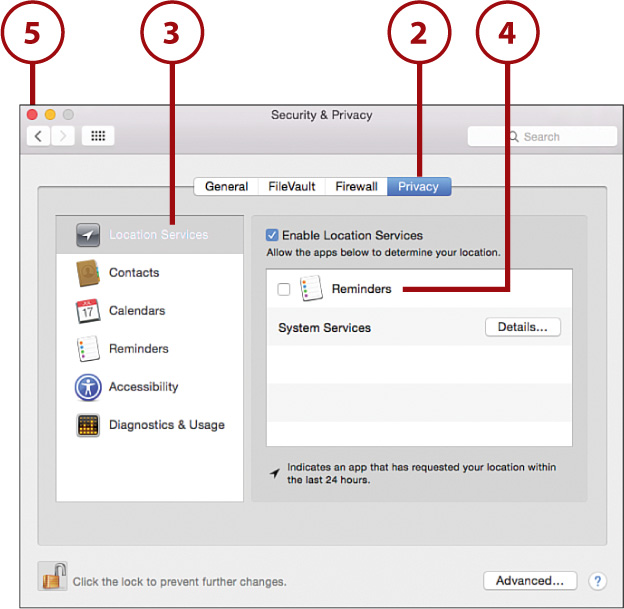
Before disabling all these services, be aware that sending information to Apple can be critical for them to correct bugs in Yosemite—applications that use your location or contacts will prompt you before they do so, so they can’t use location information without permission.
Backing Up Important Information
An often-overlooked part of security is information availability—in other words, ensuring that information is available when it is needed. If your hard drive fails, your data is unavailable, and items of value can be lost.
Backups are the best way to keep your system ready if disaster strikes. Apple provides an extremely simple backup mechanism in the form of Time Machine, a transparent solution built into Yosemite.
Quick Backups
You can create ad-hoc backups in Yosemite by inserting a writeable DVD or CD into your drive and then copying the files you want to protect onto the optical media (which is just like when you add them to a disk).
Using Time Machine
The Time Machine feature in Yosemite is a backup solution that is painless to use, covers your entire system, and can restore files from multiple different points in time. Even better, configuration for Time Machine is actually easier than traditional backup solutions like Apple Backup!
Activating Time Machine
After mounting your Time Machine backup volume on your Mac, follow these steps to configure Time Machine to begin backing up your system:
1. Open the System Preferences window and click the Time Machine icon.
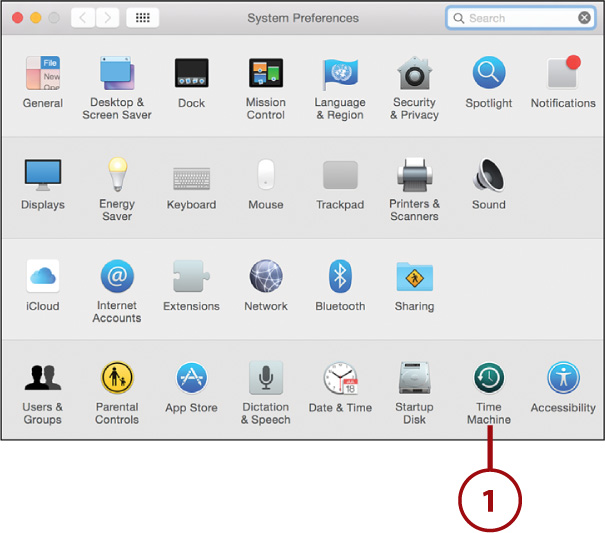
2. Click the ON/OFF switch to turn Time Machine On.
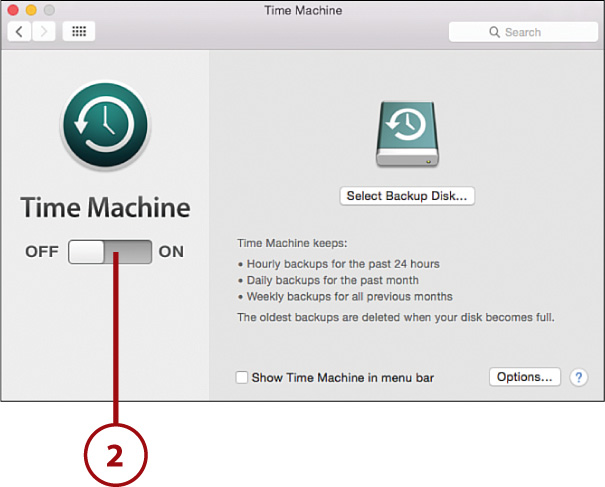
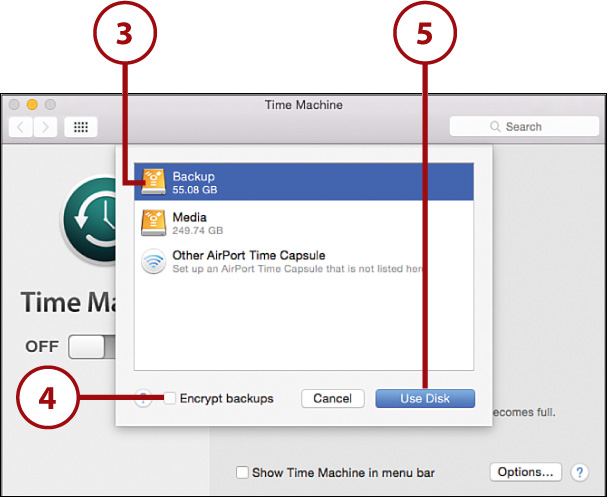
3. Choose an available disk from the list that appears.
4. Click Encrypt Backups if you’d like your backup data to be stored in a fully encrypted format.
5. Click Use Disk. (If using a network volume, enter your username and password, then click Connect.)
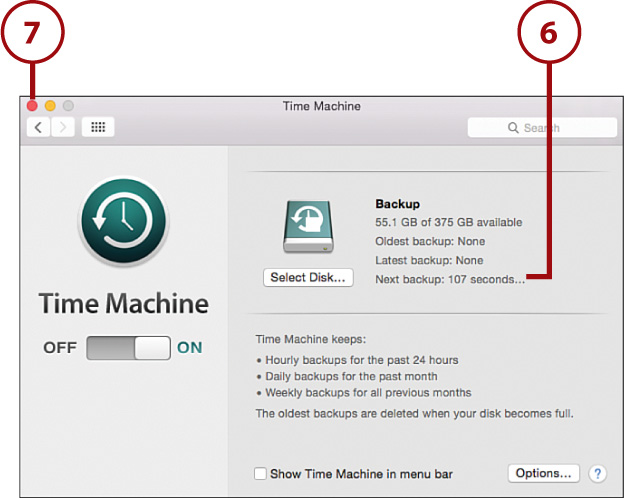
6. The Time Machine backups are scheduled and begin after a few seconds.
7. Close the System Preferences.
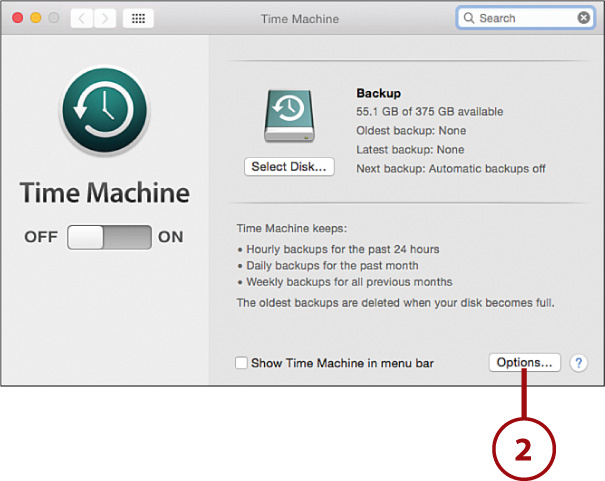
Customizing the Time Machine Backups
To further customize your Time Machine backup, including files that you want skipped, complete these steps:
1. Open the System Preferences window and click the Time Machine icon.

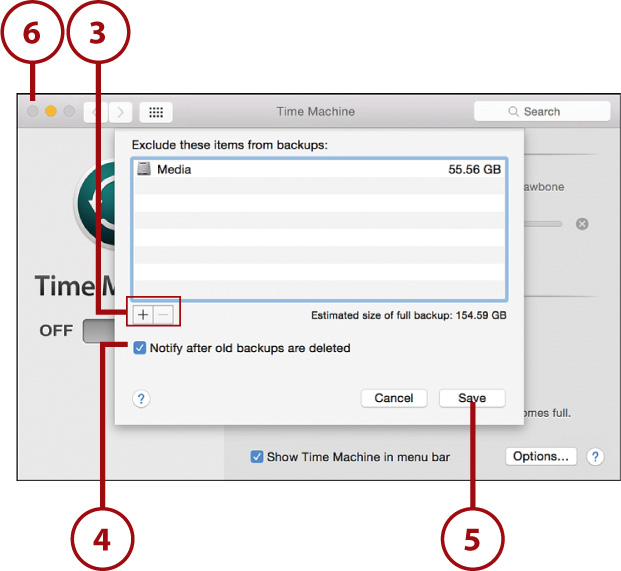
3. Use the + and – to add or remove individual files, folders, and volumes to the Time Machine exclusion list. These items are skipped during the backup.
4. Click Notify After Old Backups Are Deleted to receive warnings as old information is removed to make space for new data.
5. Click Save.
6. Close the System Preferences.
Adding a Time Machine Menu Item
To monitor your Time Machine backups and quickly launch a Time Machine restore, you can add a menu item to your menu bar:
1. Open the System Preferences window and click the Time Machine icon.
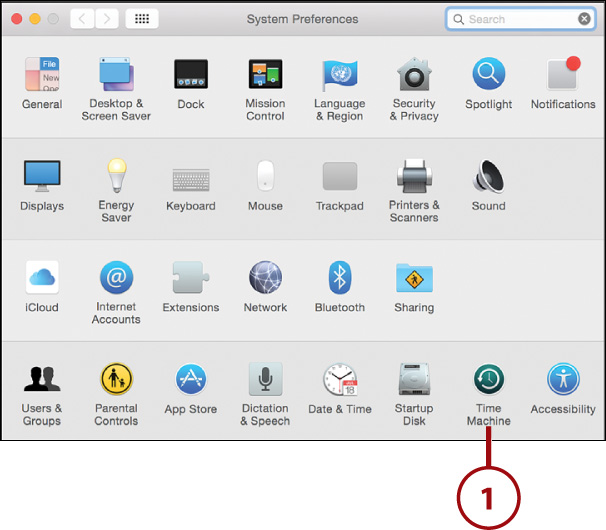
2. Check Show Time Machine in Menu Bar.

3. The menu item is added to your menu bar. A small triangle appears in the icon when a backup is running.
4. Click the Time Machine menu item to start and stop backups and enter the Time Machine restore process.
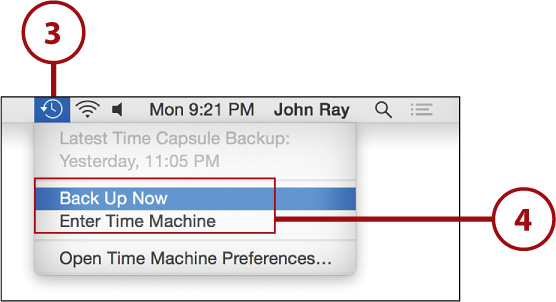
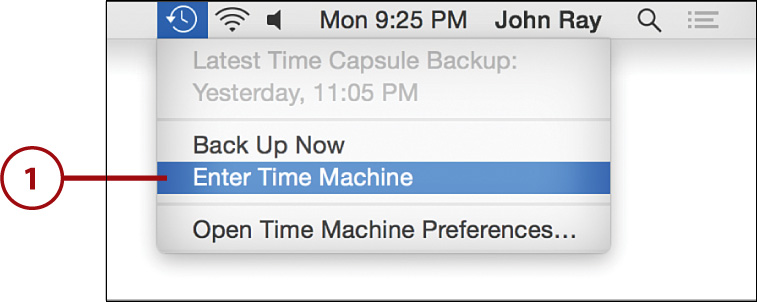
Recovering Data
Recovering data from a Time Machine backup is one of the more unique experiences you can have in Yosemite. Follow these steps to enter the Time Machine and recover files from the past:
1. Open the Time Machine using the application (Applications/Time Machine) or Time Machine menu item.
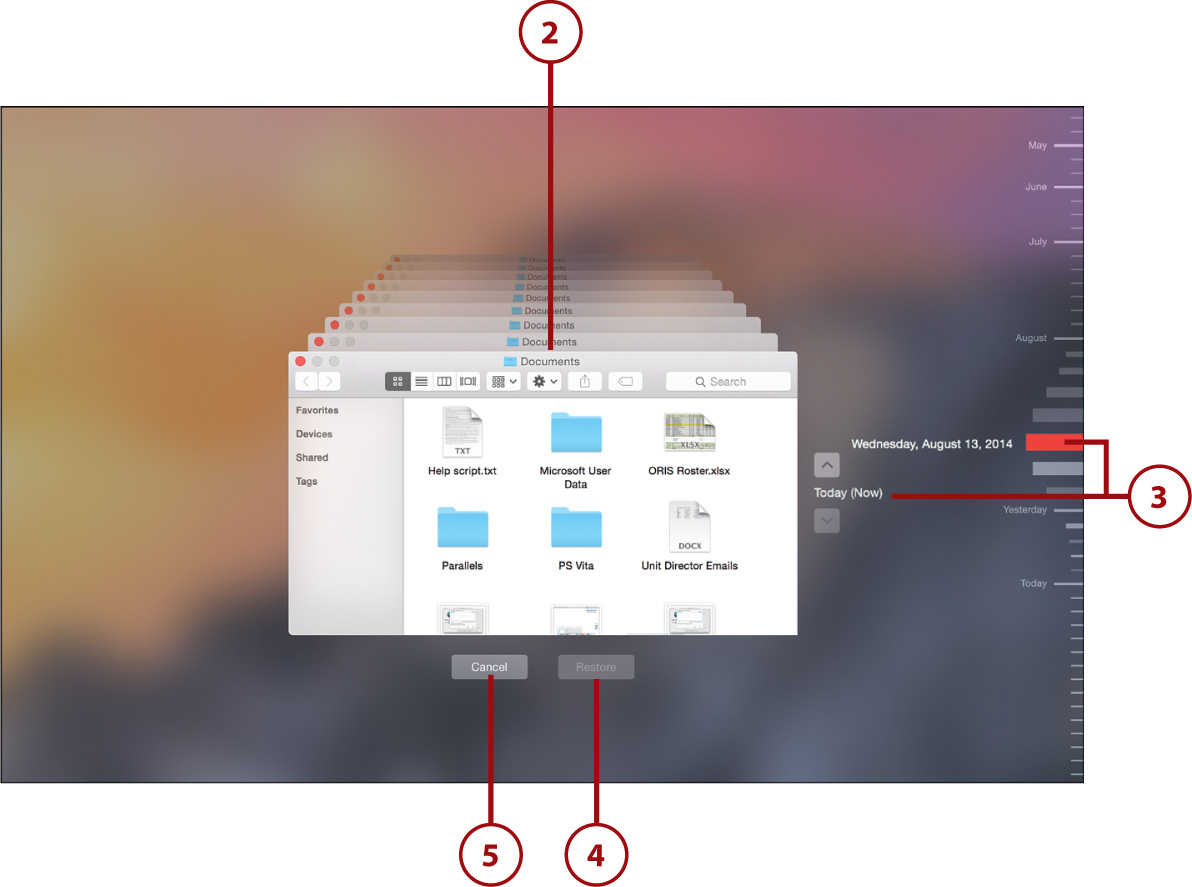
2. Navigate to a location on your disk that holds (or held) the file or folder you want to restore. For example, if you deleted an application and want to restore it, open the Applications folder.
3. Use the arrows on the right (or directly click the timeline) to choose a point in time. The window updates to show the state of the file system at the chosen time.
4. When viewing the files/folders you want to restore, click the Restore button under the file system window. The files are restored to match the snapshot.
5. Click Cancel to exit.
Find the Missing Files
Searches are active in Time Machine. Use the Search field on the Finder window to help identify files to restore.
Restoring a Machine from Scratch
If your Mac suffers a complete hard drive failure, you can use your Time Machine backup to recover everything on your system. Make sure you have a bootable disk or can boot from the recovery partition (Command+R); see the online Chapter 15, “Troubleshooting Your System,” for details.
1. Boot from your media or the Yosemite recovery partition, and then click Restore from Time Machine Backup.
2. Click Continue.
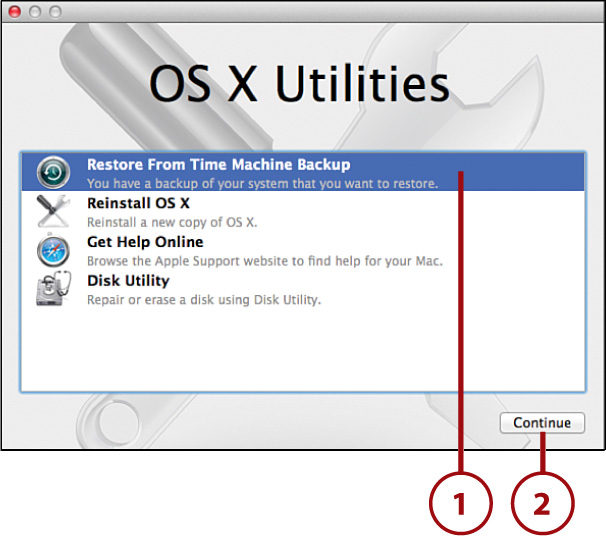
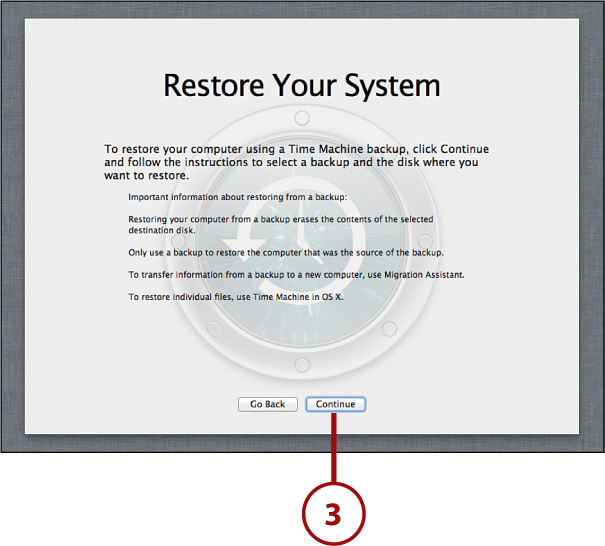
3. When the Restore Your System window appears, click Continue.
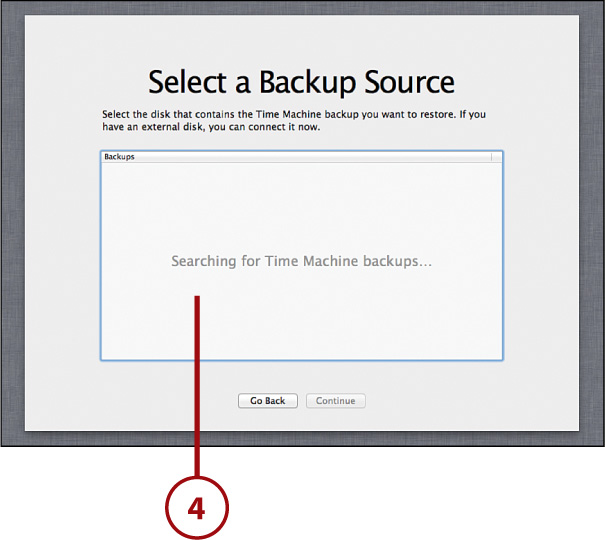
4. Choose your Time Machine disk from the list that appears.
5. Select the backup and backup date that you want to restore, and follow the onscreen steps to complete the restoration (not shown).
If your hard drive is still functional, you can boot off the Yosemite recovery partition that is automatically created when you install the operating system. To do this, simply hold down Command+R while turning on or restarting your computer. Even if your drive has failed, many Mac models made in 2010 and later can boot using the Internet and Apple’s remote servers. Command+R first tries to boot from a local recovery partition; if that fails, it then tries using the Internet recovery method. The recovery feature gives you access to disk repair and formatting tools, Time Machine restores, and even a full reinstall of the operating system.
Using File Versions
Yosemite also includes a Time Machine-like feature called Versions. Unlike Time Machine, however, Versions keeps revisions of your files’ contents. As you make changes, Yosemite automatically saves the changes so that you can browse your editing history over time.
Manually Saving a Version
The Yosemite versioning system is built to automatically save versions of your files as you edit—no manual saving is required. If you’d like to explicitly tell the system to save a version, you can, by following these steps:
1. Make the desired changes to your document.
2. Choose File, Save.
3. A new version is added to the document’s version history (not shown).
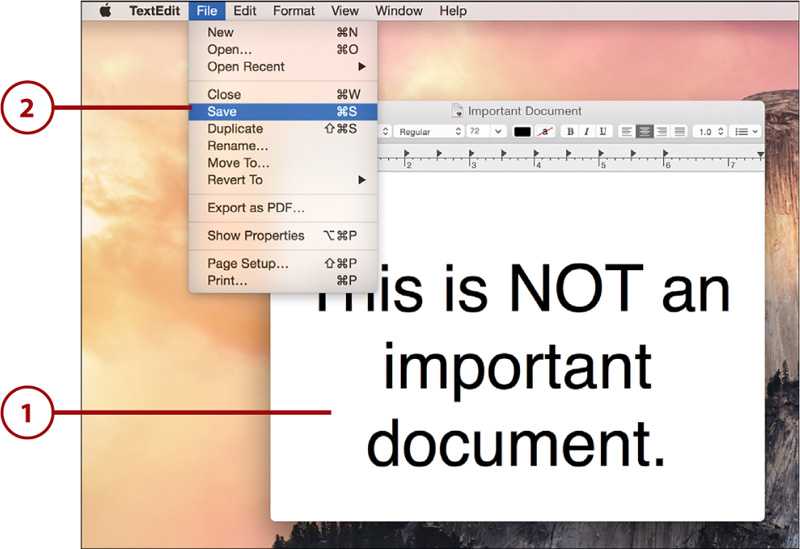
If you find a document that can’t be changed, it is likely locked. You can unlock documents by getting info (File, Get Info) in the Finder and unchecking the Locked box in the General information section.
Restoring a File Version
Accessing the version history of a document is very similar to using Time Machine. To view and access the version history of a file, do the following:
1. Within the document that has history you want to access, choose File, Revert To, Browse All Versions from the menu bar.
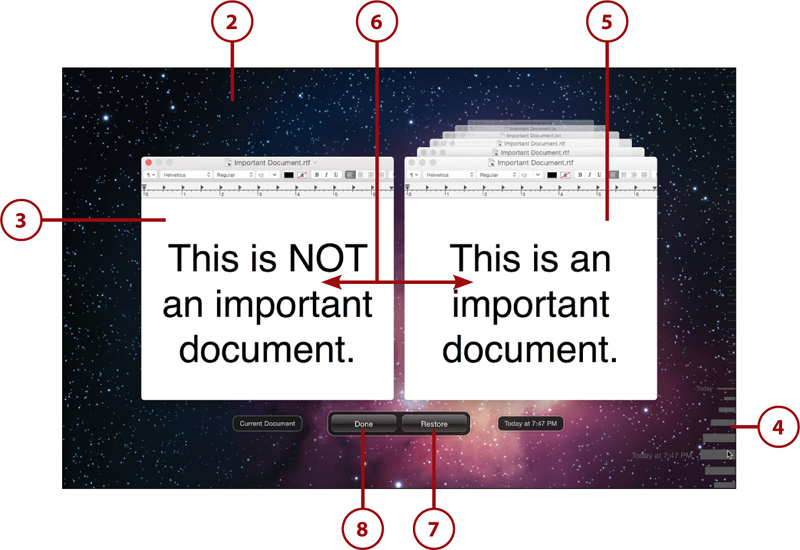
2. The Version screen is displayed.
3. The current document is located on the left.
4. Use the timeline on the right to browse through different versions of your file.
5. The previous versions of the file are displayed on the right.
6. You can copy and paste text from the document on the right into the document on the left, but you cannot make changes to the previous versions.
7. To completely restore a previous version of the file, view the version you want to restore on the right, and then click the Restore button.
8. Click the Done button to exit the file version history.
Use iCloud for Off-Site Storage
To move critical files to iCloud, you can click a document’s name in the title bar when editing and then use the Where drop-down menu to choose one of the options under iCloud Library. Choose the name of your application (followed by iCloud) to move to an iCloud folder specifically for that application, or just pick iCloud Drive to place it at the top level of your iCloud drive storage. The file immediately moves to the cloud. Using iCloud ensures that all your iCloud-connected devices have access to the file as well. Learn more about iCloud in Chapter 4, “Setting Up iCloud and Internet Accounts.”
