Securing Oracle WebLogic with authorization, authentication, and so on, is one thing, but there are some other ways to think of a solution to protect your resources.
SSL is the standard security technology for establishing an encrypted link between a Web server and a client.
Why use SSL Certificates:
- Verifying the legal, physical, and operational existence of the clients and/or servers.
- Verifying that the identity of the entity matches official records.
- Verifying that the entity has exclusive right to use the domain.
Using a central solution for user management such as LDAP can store user information for many applications and with this mechanism users can be assigned to the applications of their need. Because their password is stored in the LDAP, it's valid for all the applications to which they are assigned. They do not need to logon over and over again with every new application they use.
These days, the term cyberwar is very real. All kinds of companies and their computer systems are being attacked by intruders using all kinds of techniques such as:
In the "man-in-the-middle" attack, an unknown party (the attacker) poses as a destination host intercepting messages between the client and the real host. Instead of issuing the real destination host's SSL certificate, the attacker issues his/her own certificate hoping that the client will accept it as being from the real destination host.
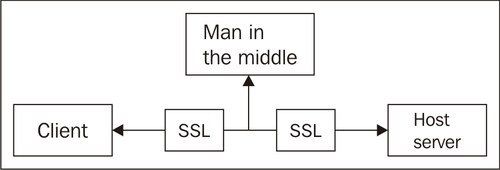
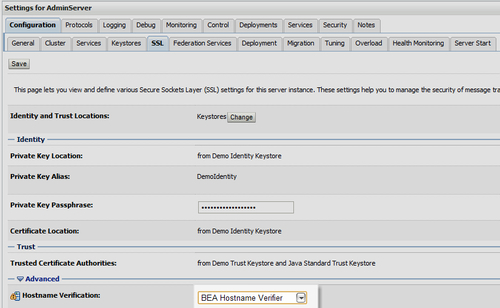
A Hostname Verifier is useful when an Oracle WebLogic Server or a WebLogic client acts as an SSL client to another application server. It prevents the "man-in-the-middle" attacks.
The SSL tab for the specified Server Instance is used to configure the BEA Hostname Verifier. It ensures that the hostname in the URL to which the client connects, matches the hostname in the digital certificate that the server sends back as part of the SSL connection.
Denial of Service (DoS) attacks can disable your computer or your network. Depending on the nature of your enterprise, this can effectively disable your organization.
Some DoS attacks can be executed with limited resources against a large, sophisticated site. This type of attack is sometimes called an "asymmetric attack". For example, an attacker with an old PC and a slow modem may be able to disable much faster and more sophisticated machines or networks.
A well-known method of attack is to bombard the target machine with external communication requests, such that it cannot respond to legitimate traffic. Attacks of this origin are called "floods". Others can be like disrupting specific services or systems.
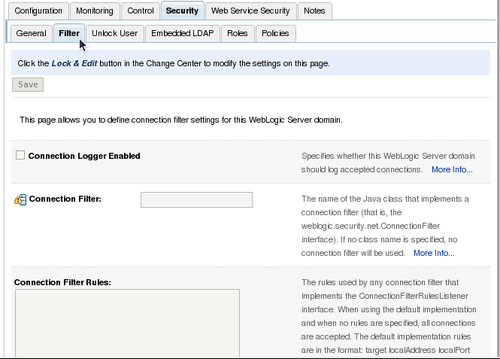
Countermeasures against DoS attacks for WebLogic Server could be as filtering IP addresses using the ConnectionFilter interface. This can be done in the top-level domain from the Admin Console on the Security | Filter tab.
There is a default connection filter class called weblogic.security.net.ConnectionFilterImpl.
So no implementation is required if that fullfills your requirements. More information can be found at http://download.oracle.com/docs/cd/ E12839_01/apirefs.1111/e13952/taskhelp/security/ConfigureConnectionFiltering.html.
A large buffer attack is an attack where a program, while writing data to a buffer, overruns the buffer's boundary and overwrites adjacent memory. This is a special case of violation of memory safety.
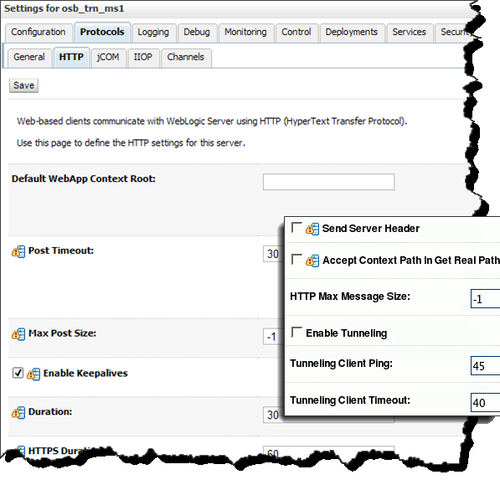
Hackers send large buffers of data to the server that starves the server of memory. WebLogic Server can be set to limit the amount of HTTP data that can be posted to its servers. This can be done using the Administration Console to manage this threshold. Any requests that exceed this threshold are denied access to the server. This can be done on a specific Server Instance tab, Protocols | HTTP tab in the right pane.