Security is essential to gaining the trust of users. In our modern age, data breaches are very common and information security is very important. Users are starting to select products based on their security and privacy. Security is a huge field on its own, with many companies having their own security engineers and entire companies devoted to working as consultants to examine other companies' security practices. Security is the responsibility of everyone, just like monitoring, incident response, or UX. You should have experts on your staff to direct you, but you must not be ignorant about the topic and defer to your experts for everything.
When building software, or auditing technology for security matters, try thinking about the three following aspects of a piece of technology:
- Authentication: How do you give a user a token saying they can interact with things? For example, a user logging in with a username and password.
- Authorization: How do you determine whether a user can access something? For example, a user with a token can change a post on a blog. Another example is that anyone on your network subnet can connect to the human resources help pages.
- Risk profile: The idea of a risk profile is what type of information you have, who would be interested in obtaining that information, and their technical capability. For example, a news organization might not have much customer information, but it would seek to protect information about sources and ongoing article research. That being said, a news organization that took donations or sold a print publication could have credit card numbers and shipping information. Credit cards and personal information tend to attract a wide number of attackers, while journalistic sources are of more interest to large crime organizations or state actors (people connected to governments).
By being on the internet, you are at risk of being attacked. The internet lets anyone connect and send traffic to anyone else. The chance of something being insecure is high, so often people are scanning the internet looking for IP addresses with open ports and vulnerable services. Following are some tips for addressing common issues, and in the References section, you can find more external sources to read and watch to continue your learning.
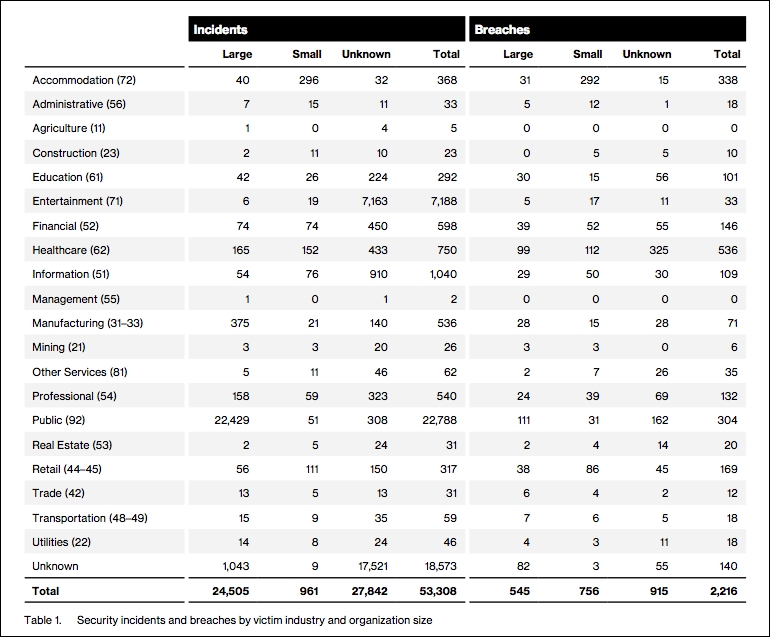
Figure 9: From page 25 of the 2018 Verizon Breach Report (https://www.verizonenterprise.com/resources/reports/rp_DBIR_2018_Report_en_xg.pdf). This shows just one year of attacks that Verizon knew about, categorized by victim industry and organization size. An incident is where an organization is compromised, with the possibility of its information being taken or made unavailable. A breach is an incident where data is explicitly disclosed by a third-party source. Note this table does not show the severity of the incidents.
The following are some basic suggestions for writing code that deals with authentication:
- Always verify contact information. If your user puts in a phone number or email, make sure they actually own it by sending a verification message.
- Do not put a maximum on password length or restrict which characters can be in a password.
- Always store passwords with a one-way hash such as bcrypt. If someone else gets access to your datastore, they should not have access to a user's password.
- For sensitive accounts, support multi-factor authentication. This usually requires a user to have an ID, a password, and some sort of device, such as a cell phone.
- If possible, remove passwords from your authentication flow. Haveibeenpwned.com tracks data breaches and has around five billion passwords at the time of writing. Given that there aren't that many more people on the planet, it's highly possible that a password you use is in there.
- Send notifications when users authenticate with unusual circumstances, such as after changing a password, or from a new location and browser combination.
- Expire authentication after a time, requiring users to re-authenticate, instead of letting users only log in once.
Note that these measures will not guarantee that people will not find a way to get into your system, but they are a good start.
Authorization, as mentioned in the preceding section, is determining whether a user has permission to do what they want to do. Always use authorization with authentication if you can. Just because a user is on your network, or has access to your corporate email system, this does not mean that they should be able to access something. For example, if I walk into an office and plug a computer into a wall socket, or connect to your Wi-Fi from the street, I should not be able to access everything about your organization without also logging in as a user. Also, make sure people are not sharing logins. If the same authentication token means multiple users, you don't actually have authentication because you can't audit which users are doing what. It should be mentioned that adding authorization logging is very useful for knowing which users ask for permission to do which things, and which things you give them permission for.
Determining your risk profile is not a science, but it's something you can think about to determine how paranoid you should be. First, think about an individual person. They have stuff that other people want, such as data or money. Then think about the level of effort an attacker would have to go through to take it from them. If the individual doesn't use two-factor authentication on their bank account, and reuses passwords (or reuses similar passwords), then the possibility that another human could get access to their bank account increases. So, the more valuable a person and their stuff is, the more the risk increases because external actors will target them. Also, the worse a person's security practices are, the more the risk increases because of the chance of automated attacks, and the more the effort required to compromise them decreases.
For example, if I use the same password everywhere for the same email address (for instance [email protected] and qwerty1234256 are my logins for Gmail, Netflix, and my bank) if any one of those companies is compromised and my email and password are leaked, then future attackers can add that combo to their automated scripts. These scripts can just look at every popular website online and start trying every leaked password and email combo ever. Since my username and password is the same, the chance of me being compromised is higher. If I'm a public figure, such as US political consultant John Podesta, for example, and people know my email address, attackers will try targeting my email with phishing scams (described in the next section) and brute forcing my password with scripts, hoping that they can get into an account of mine and gain valuable information.
A service is just like a person: a service belongs to an organization, which has value. Apple, for example, has trillions of US dollars to its name. Most countries have databases on all of their citizens for tax purposes. Apple is more technically advanced than smaller companies, so its risk decreases, as it has the resources to invest in security. Comparably, Wells Fargo bank has high assets, but it is also technically competent. A credit union, on the other hand, might have a decent amount of money, but not have anyone competent taking care of security.
Phishing is one of the most dangerous and common attack vectors in computer security today. It is the act of taking an email that someone might normally interact with and modifying it to have the user who clicks on it be taken to a fake page, where they type in their credentials for a real site (such as their email password). As an operator, phishing is particularly dangerous, because SREs, DevOps engineers, and system administrators are all common targets for phishing, as they often have credentials for many sensitive systems.
In 2014, Edward Snowden, who famously leaked classified information from the US, revealed that sysadmins were some of the National Security Agency's top targets (https://theintercept.com/2014/03/20/inside-nsa-secret-efforts-hunt-hack-system-administrators/). Whether or not that is true anymore, the point remains that people who might target systems might target both your personal and work life to gain access to a system.

Figure 10: An example phishing email from Wired magazine after a large-scale Google Docs scam in 2017 (https://www.wired.com/2017/05/dont-open-google-doc-unless-youre-positive-legit/)
These attacks might come as something as innocuous as an email asking you to renew your Netflix subscription or to change your password for your Gmail. They often work because many people use the same password on many accounts. This is why it is often recommended to use a different password on every website and account. It is also why we recommend using MFA where possible, so that even if someone gets your username and password, they will still need your phone or some other device to get access to the account.
