Roo supports configuring Spring Security for your application via security setup command. In this recipe, we'll look at the security related configurations added to your application by Roo when you execute the security setup command. In the next recipe, Using Spring Security with Apache Directory Server, we'll look at how we can extend the Spring Security configuration to use Apache Directory Server for addressing security requirements of a Roo-generated web application and how to incorporate method-level security.
Create a sub-directory ch06-security inside the C:
oo-cookbook directory.
Copy the ch06_web_app_security.roo script into the ch06-security directory.
Execute the ch06_web_app_security.roo script, which creates the flightapp-web Roo project, sets up Hibernate as persistence provider, configures MySQL as the database for the application, creates Flight, FlightDescription, and Booking JPA entities, defines a many-to-one relationship between Flight and FlightDescription entities, and a many-to-one relationship between Booking and Flight JPA entities. Also, script makes use of controller all command to scaffold Spring Web MVC application. If you are using a different database than MySQL or your connection settings are different than what is specified in the script, then modify the script accordingly.
Start the Roo shell from the C:
oo-cookbookch06-security directory.
To configure Spring Security for your application through the security setup command, follow the steps given here:
- Execute the
security setupcommand to set up Spring Security for the flightapp-web Spring Web MVC application, as shown here:.. roo> security setup Updated ROOTpom.xml [Added property 'spring-security.version' with value '3.0.5 .RELEASE'] Updated ROOTpom.xml [Added dependencies org.springframework.security:spring-security-core:${spring-security.version}, ...] Created SRC_MAIN_RESOURCESMETA-INFspringapplicationContext-security.xml Created SRC_MAIN_WEBAPPWEB-INFviewslogin.jspx Updated SRC_MAIN_WEBAPPWEB-INFviewsviews.xml Updated SRC_MAIN_WEBAPPWEB-INFweb.xml Updated SRC_MAIN_WEBAPPWEB-INFspringwebmvc-config.xml
- Execute the
performeclipsecommand to update project's classpath settings:.. roo> perform eclipse - Import
flightapp-webEclipse project into Eclipse IDE
The security setup command is processed by the Security add-on
of Roo. The security setup command is available only after you have installed Spring Web MVC artifacts by executing one of the controller commands of Roo. This limits the use of the security add-on only to projects that make use of Spring Web MVC.
Security add-on processes the security setup command and performs the following actions:
- Adds a property named
spring-security-versionwith value 3.0.5 to thepom.xmlfile of theflightapp-webproject, as shown here:<project ...> ... <name>flightapp-web</name> <properties> <roo.version>1.1.2.RELEASE</roo.version> <spring.version>3.0.5.RELEASE</spring.version> <spring-security.version> 3.0.5.RELEASE</spring-security.version> ... </properties> ... </project>The
spring-security-versionproperty identifies the version of Spring Security framework required by the application. The Spring Security version number property is referenced by the<dependency>elements inpom.xml, as shown here:<dependency> <groupId>org.springframework.security</groupId> <artifactId>spring-security-config</artifactId> <version>${spring-security.version}</version> </dependency> <dependency> <groupId>org.springframework.security</groupId> <artifactId>spring-security-web</artifactId> <version>${spring-security.version}</version> </dependency>
As the given configuration shows, defining the version number of Spring Security required by the
flightapp-webapplication as a property inpom.xmlfile can ensure thatpom.xmldefines dependencies on JAR files that belong to the same version of Spring Security. - Creates an application context XML file:
applicationContext-security.xmlinSRC_MAIN_RESOURCES/META-INF/springdirectory. TheapplicationContext-security.xmlfile configures authentication and authorization requirements of the application. - Adds Spring Security's
DelegatingFilterProxyservlet filter to theweb.xmlfile of theflightapp-webapplication, as shown here:<filter> <filter-name>springSecurityFilterChain</filter-name> <filter-class> org.springframework.web.filter.DelegatingFilterProxy </filter-class> </filter> <filter-mapping> <filter-name>springSecurityFilterChain</filter-name> <url-pattern>/*</url-pattern> </filter-mapping>The
DelegatingFilterProxyservlet filter acts as an entry point into Spring Security's web module, which handles web request security. The name of the filterspringSecurityFilterChainrefers to the name of Spring Security'sFlightChainProxyinstance configured in theapplicationContext-security.xmlfile. TheDelegatingFilterProxyfilter delegates web request toFlightChainProxyinstance for performing web request security. - Creates a login JSPX page
login.jspxin theSRC_MAIN_WEBAPPWEB-INFviewsdirectory. - Adds tiles definition for the login page in the
SRC_MAIN_WEBAPPWEB-INFviewsviews.xmltiles definitions XML file, as shown here:<definition extends="public" name="login"> <put-attribute name="body" value="/WEB-INF/views/login.jspx"/> </definition> - Configures a
ParameterizableViewController(viaview-controllerelement ofmvcnamespace of Spring) inwebmvc-config.xmlfile (located inSRC_MAIN_WEBAPPWEB-INFspringdirectory) that dispatches request tologin.jspxpage, as shown here:<mvc:view-controller path="/login"/>
- Updates the
pom.xmlfile of theflightapp-webproject to include dependency on Spring Security JAR files, such asspring-security-core,spring-security-config, and so on.
Let's now look in detail at the applicationContext-security.xml file.
The applicationContext-security.xml file configures Spring Security beans, which are used for authentication and authorization of requests. As we'll see shortly, Roo-generated applicationContext-security.xml doesn't do much but gives a good starting point to configure your application-specific security.
Authentication mechanism for the application is configured in applicationContext-security.xml via the <authentication-manager> element of Spring's security namespace, as shown here:
<authentication-manager alias="authenticationManager">
<authentication-provider>
<password-encoder hash="sha-256"/>
<user-service>
<user name="admin" password="..."
authorities="ROLE_ADMIN"/>
<user name="user" password="..."
authorities="ROLE_USER"/>
</user-service>
</authentication-provider>
</authentication-manager>Let's look in detail at each of the elements in the given configuration and how they work together to provide authentication services to the application:
<authentication-manager>: It registers an instance of Spring Security'sAuthenticationManagerimplementation that is responsible for providing authentication services.AuthenticationManagerdelegate's authentication to theAuthenticationProvideris configured using the<authentication-provider>sub-elements.<authentication-provider>: It registers an instance of Spring Security'sAuthenticationProviderimplementation. Spring Security provides a couple of built-in implementations of theAuthenticationProviderinterface to simplify incorporating different authentication mechanisms in the application. For instance, if you are using JA-SIG CAS for authentication, you can useCasAuthenticationProviderimplementation and if you are using an LDAP server for authentication, you can useLdapAuthenticationProvider, and so on. TheAuthenticationProviderimplementation usage is specified using therefattribute of the<authentication-provider>element. If therefattribute is not specified (as in the case of Roo-generatedapplicationContext-security.xml),DaoAuthenticationProviderimplementation is registered.DaoAuthenticationProvidermakes use of Spring Security'sUserDetailsServiceto authenticate users.UserDetailsServiceloads user details containing username, password, and granted authorities based on the username entered by the application user.DaoAuthenticationProviderauthenticates the user by comparing the password entered by the application user with the user details loaded byUserDetailsService.<user-service>: It creates an in-memoryUserDetailsServiceinstance that reads user details from a properties file or from the nested<user>elements.<user>: It defines a user of the application. Thenameandpasswordattributes identify the username and password required for authentication.<password-encoder>: It converts submitted passwords to hashed versions before comparing the submitted password with the one retrieved byUserDetailsService. Thehashattribute specifies the hashing algorithm to use for encoding password.
The following <http> element shows how web request security is configured in the applicationContext-security.xml file:
<http auto-config="true" use-expressions="true">
<form-login
login-processing-url="/resources/j_spring_security_check"
login-page="/login"
authentication-failure-url="/login?login_error=t"/>
<logout logout-url="/resources/j_spring_security_logout"/>
<intercept-url pattern="/choices/**"
access="hasRole('ROLE_ADMIN')"/>
<intercept-url pattern="/member/**"
access="isAuthenticated()" />
<intercept-url pattern="/resources/**"
access="permitAll" />
<intercept-url pattern="/**" access="permitAll" />
</http>Let's now look in detail at how the elements in the given configuration define web request security:
<http>: It contains the HTTP security configuration elements. It creates an instance of Spring Security'sFilterChainProxywith bean name asspringSecurityFilterChain. It is important to note that the name of theFilterChainProxybean is same as the name of theDelegatingFilterProxyservlet filter configured inweb.xmlfile.The
auto-configattribute automatically configures Spring Security beans, which provide form-based login, logout, and HTTP BASIC authentication services.The
use-expressionattribute specifies whether theaccessattributes of the<intercept-url>element (discussed later in this recipe) can accept EL expressions.<form-login>: It configures Spring Security'sUsernamePasswordAuthenticationFilterfilter bean (a bean that implements thejavax.servlet.Filterinterface of Servlet API) andLoginUrlAuthenticationEntryPointbean in an application context. TheUsernamePasswordAuthenticationFilterfilter bean is used byFilterChainProxyto perform authentication.UsernamePasswordAuthenticationFilteruses the username and password in the submitted request to attempt authentication against the configured authentication provider(s). It is important to note that the names of the request parameters that contain the username and password must bej_usernameandj_password, respectively. If you check the Roo-generatedlogin.jspxfile for parameters thatflightapp-webproject, you'll find that the names of the username and password fields arej_usernameandj_password, respectively. TheLoginUrlAuthenticationEntryPointbean starts off the form login authentication usingUsernamePasswordAuthenticationFilter.The
login-pageattribute specifies the URL of the login page. The value of this attribute is used byLoginUrlAuthenticationEntryPointto render the login page. The value of the attribute is/login, which means that the<mvc:view-controllerpath="/login"/>configured controller inwebmvc-config.xmlis responsible for rendering the login page.The
login-processing-urlattribute specifies the URL to which the login form is submitted. TheUsernamePasswordAuthenticationFilterhandles a request submitted to the URL identified by itsfilterProcessesUrlproperty. The value of thelogin-processing-urlattribute is used to set thefilterProcessesUrlproperty ofUsernamePasswordAuthenticationFilter. The value of thelogin-processing-urlattribute is/resources/j_spring_security_check, which is the same as the value of theactionattribute of the HTML<form>element in the Roo-generatedlogin.jspxfile of theflightapp-webproject.The
authentication-failure-urlattribute specifies the URL to which the user is redirected if login fails. The value of this attribute/login?login_error=tmeans that the<mvc:view-controllerpath="/login"/>configured controller inwebmvc-config.xmlwill render the login page again. Thelogin_errorparameter in the URL is used by thelogin.jspxpage to show an authentication failure message on the login page, as shown here: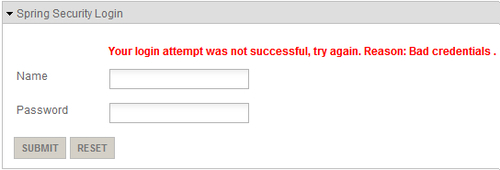
<logout>: It configures theLogoutFilterfilter bean that is responsible for processing logout requests. TheLogoutFilterhandles request submitted to the URL identified by itsfilterProcessesUrlproperty. The value oflogout-urlattribute is used to set thefilterProcessesUrlproperty ofLogoutFilter. In case of Roo-generatedapplicationContext-security.xml, the value oflogout-urlis/resources/j_spring_security_logout. Thefooter.jspxfile (located in/WEB-INF/viewsdirectory) contains the Logout hyperlink that is displayed if the user is logged in. The Logout hyperlink refers to/resources/j_spring_security_logoutURL, which means that when the user clicks the Logout hyperlink, the request is processed by theLogoutFilterfilter bean.<intercept-url>: It defines the URL pattern and the corresponding access permissions. Thepatternattribute specifies the URL pattern and theaccessattribute specifies the access permissions. As mentioned earlier, the<http>element'suse-expressionattribute is set totrue; therefore, theaccessattribute can accept Boolean EL expressions. If the value returned by the expression istrue, then access to the URL pattern, specified by thepatternattribute, is authorized.The
hasRole,isAuthenticated, andpermitAllare examples of built-in expressions. ThehasRole('ROLE_ADMIN')returnstrueif the role of the authenticated principal isROLE_ADMIN. TheisAuthenticated()returnstrueif the user is not an anonymous user. ThepermitAllexpression always returnstrue.The
<http>element registers an implementation Spring Security'sAccessDecisionManager, which makes access decisions regarding web URL access. An incoming web request is matched against the URL patterns specified by the<intercept-url>elements in the order in which they appear within the<http>element. If a match is found, it'll be used byAccessDecisionManagerimplementation for making access decisions. As incoming web requests are matched against the URL patterns (specified by the<intercept-url>elements) in the order in which they appear within the<http>element, more specific URL patterns should be declared before the more general URL patterns.
