3
Tactile Internet Key Enablers
Tara ALI-YAHIYA
Department of Computer Science, University of Paris-Saclay, France
3.1. Introduction
The deployment of the TI cannot occur successfully without the support of some enabling technologies that ensure the ability to perform haptic operations. As illustrated in the previous chapter, the TI architecture is made up of innovative components that embody the network infrastructure, communication paradigm and cloud computing proximity to achieve high availability, low latency and security for the new use cases. In addition, some new softwarization techniques are based on micro-service concepts and virtualization for better management of physical resources in the network. As a step forward to realizing the TI, in this chapter we will discuss the TI-driven technologies that impact the haptic applications and services from the perspective of end-to-end communication architecture. These key technologies will assist in the convergence towards a common set of important design goals, allowing the TI to be realizable.
3.1.1. The fifth-generation system architecture
A key enabler of the TI is the 5G mobile network, considering that the legacy generations of mobile networks cannot meet the rigorous requirements of QoS of mission-critical haptic applications. For this reason, the 3GPP has brought new amendments to the specifications of 5G, known as New Radio (NR) 5G, to support new radio technology and to propose a new service-based architecture (SBA) that enables a flexible network configuration through the interaction of core network functions with each other (Maier et al. 2016). A clear separation between the user plane and control plane is made to guarantee the scaling of resources in both planes independently. Both planes interact with each other via the use of a generic application programming interface (API) (Simsek et al. 2016).

Figure 3.1. 5G architecture (ETSI 2018b). For a color version of this figure, see www.iste.co.uk/ali-yahiya/tactile.zip
The architecture illustrated in Figure 3.1 describes the user equipment (UE) equipped with a 5G NR interface, connected to the next generation node B (gNB) as part of the Radio Access Network (RAN), while the key mobile core network functions can include an authentication server function (AUSF), an access and mobility management function (AMF), a network slice selection function (NSSF), a network repository function (NRF), a policy control function (PCF), a session management function (SMF), unified data management (UDM), a user plane function (UPF), an application function (AF) and a data network (DN) (ETSI 2018a).
The user plane includes the UPF, which is a fundamental component of the 5G architecture, as it is in charge of data forwarding and routing, connecting the components of the architecture to the DN, QoS handling and a mobility anchor among radio access technologies. The control plane, on the other hand, (referring to all the modules on the upper side of Figure 3.1) is composed of a platform that enables mobility management, access authentication and authorization, session management and exposes services to internal or external networks. This is done by means of a repository that contains all the services available in the network, in order that a network function registers either as a consumer or producer for a specified service. Each service in the network requires resources to be used; for that reason, the 5G NR core network provides a network slicing function that allocates a slice (a set of logical resources) to a service requested by a UE with predefined QoS requirements. All these functions, including network slicing, mobility, roaming, charging and control are managed through a unified policy rule platform, i.e. a PCF module.
The NR uses orthogonal frequency-division multiplexing (OFDM); however, the subcarrier spacing ranges from 15, 30 or 60 to 120 kHz which gives a variety of slot lengths for data transmission. This is very beneficial, especially when dealing with the diverse set of services in the TI that require different performances in terms of latency. Hence, when the duration of the slot decreases, the latency of transmission also decreases; choosing this configuration is very useful for the critical real-time application introduced in the TI. As for the QoS in 5G, it is flow-based, as the packets are classified according to the QFI (QoS flow identifier). 5G QoS flows are mapped in the access network to data radio bearers (DRBs), depending on the implicit requirements for each type of application, as shown in Figure 3.2.

Figure 3.2. 5G QoS architecture. For a color version of this figure, see www.iste.co.uk/ali-yahiya/tactile.zip
3.1.2. Network slicing
Network slicing is one of the foremost functionalities that is introduced in the 5G core network, ensuring that operators and telecommunication companies comply with the emerging requirements of enterprises. Enterprises nowadays provide different services that require different resources during a predefined time. Resources, here, can be represented by any network resources that are generally scarce, but, with the concept of network slicing, resources can be perceived as unlimited (Figure 3.3).
Network slicing can be defined as a set of logical networks being shared on the physical network infrastructure. Each logical network will be dedicated or assigned to a service of the TI that requires network resources for a duration of time. The network slicing is performing what is called the isolation of resources; this means that each slice will be independent and can have different types of resources (Ravindran et al. 2017; Rost et al. 2017; Zhang et al. 2017). The main aim is to meet the user’s service level agreement (SLA) while increasing the revenue of the operator.

Figure 3.3. Network slicing (Rost et al. 2017). For a color version of this figure, see www.iste.co.uk/ali-yahiya/tactile.zip
Network slicing is an effective method to optimize the resources in 5G by creating a virtual environment with the elements needed by any application. Its flexibility resides in its creation upon request and a lifecycle duration that lasts until the service ends and the slice is de-allocated. The logical network is instantiated through powerful techniques of virtualization, not only for the resources but also for the network functionalities related to these resources, and this is done by network function virtualization (NFV).
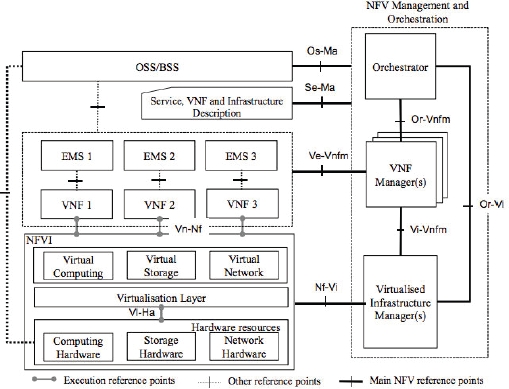
Figure 3.4. Network function visualization (NFV) architecture
3.1.3. Network function virtualization
While NFV tries to execute the functionalities of the network in a virtualized infrastructure, to provide the dynamicity and the adaptive configuration of the network, depending on the context that requires certain reconfiguration (ETSI 2013), the heterogeneous needs of the TI in terms of QoS requirements make NFV the best candidate to satisfy these requirements, especially in terms of latency, as its functionality can be adapted to the frequently changing nature of data and traffic, since tactile services may co-exist with non-tactile Internet services (Sachs et al. 2019). If this is the case, the traditional QoS mechanisms will fail to guarantee the QoS parameters and some mechanisms based on flow priority should be implemented to respect the end-to-end stringent delay of the TI traffic. Congestion solutions, load balancing, data path, physical location of the NFV, mobility tracking, etc.: all these functionalities will have an impact on the QoS guarantee and can be flexibly reconfigured to take into account the 1 ms delay of the TI (Giannoulakis et al. 2014). Finally, virtualization is an ideal technology to test new protocols and new architectures without stopping the operational network (Al Agha et al. 2016).
The advantages of the NFV for the virtualization technique are numerous. The first is being able to run on the same physical network, with the virtual networks using completely different technologies. One can, for example, get a first network using the IOS network operating system from Cisco, a second using JUNOS Juniper, a third and a fourth using the Nokia and Ericsson systems respectively, etc. It is also possible to run several different releases of the same network operating system. Obviously, the above examples have little chance of being realized because network manufacturers do not necessarily want to market their software without their equipment. Decoupling hardware and software will only be available for open systems (Al Agha et al. 2016).

Figure 3.5. Software-defined networking (SDN). For a color version of this figure, see www.iste.co.uk/ali-yahiya/tactile.zip
3.1.4. Software-defined networking
Software-Defined Networking (SDN) is introduced to automate the network management. Indeed, all the functionalities of the hardware and network will be abstracted and softwarized to decouple the infrastructure from the functions. The SDN is aimed at separating the control plane from the delivery plane (data plane), so a centralized entity, i.e. the controller, can make the decision of delivery of the traffic according to actions corresponding to rules defined in the flow table of the controller (Costa-Requena et al. 2015; Ateya et al. 2018; Cabrera et al. 2019).
A protocol of communication should be defined between the control plane and the delivery plane, so the decision can be propagated from the controller to all devices supporting SDN. One of the famous examples is the OpenFlow, as it establishes a secure channel to monitor and configure the nodes located in the delivery plane. According to the context and the functionalities, i.e. routing, resource allocation, security configuration rules, etc., the controller would send its instructions to the network devices where the data plane resides, to be configured, as shown in Figure 3.6. SDN, NFV and network slicing are practical solutions that aid in the automation of the TI architecture while taking into consideration the specific need of each use case, defined by IEEE 1918.1.
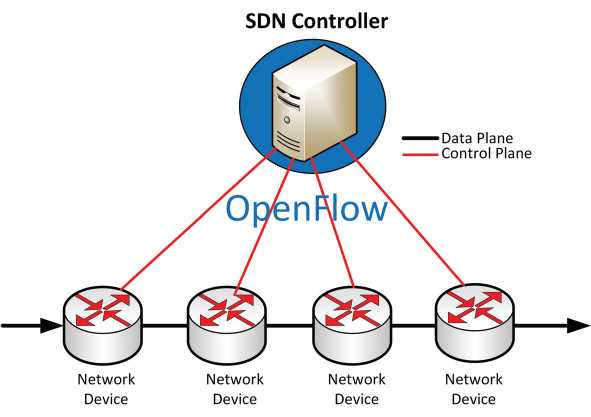
Figure 3.6. SDN with openflow. For a color version of this figure, see www.iste.co.uk/ali-yahiya/tactile.zip
3.1.5. Edge computing
Mobile edge computing (MEC) or multi-access edge computing tries to bring the cloud to the vicinity of the end-user, which enables the centralized cloud capabilities to be distributed to the edge of the radio access network. This paradigm assists in reducing delay, especially for the delay-sensitive applications while bringing the computation and processing closer to the users themselves (Tran et al. 2017). This would also assist in the case of the TI to enable users to track their real-time information, such as behavioral information, that can be predictive based on artificial intelligence algorithms.
The MEC is overcoming the classical cloud by having the edge device close to the user in order to compute, process and deliver instead of sending all the data through the backhaul. This will prevent congestion in which the latency, which the TI intends to guarantee, would collapse. The resource management can also be effectively achieved through a collaborative edge computation, as the task can be divided into small tasks and processed through different edge devices. This would be a good method of offloading the network (Mao et al. 2017). Providing a distributed caching mechanism by extending content delivery network (CDN) services towards the mobile edge can also enhance the users’ QoE while reducing backhaul and core network usage (Skorin-Kapov et al. 2018). Indeed, there is a close relationship between the MEC and the QoE; however, since we are dealing with haptic applications, the codec used should reflect the combination between the tactile and kinesthetic. Consequently, a new design for mean opinion score (MOS) emerges, one that reflects users’ best QoE through different codecs that also combines video and audio applications.
The TI specified, in its architecture, an entity called a support engine (SE), which stands for MEC functionalities for caching and processing. They specified its location in the master domain, where data can be collected from IoT devices nearby. This would mean isolating master network data movement from the core network or network domain and, as a consequence, guaranteeing a high delay of the real-time processing data needed by IoT devices.

Figure 3.7. MEC integrated with 5G. For a color version of this figure, see www.iste.co.uk/ali-yahiya/tactile.zip
3.1.6. Artificial intelligence
The use of AI in applications requiring very low latency is highest when dealing with time-critical applications. AI with the type of network domain will determine the success of communication in the TI, especially for the teleoperation use cases demanding few milliseconds of E2E latency. The importance of latency lies in its effect on the stability of the whole system, as a small delay in delivering the data may cause incorrect manipulation at the teleoperator’s edge. The latency is even more critical in active haptic communication.
The AI, from its definition, endows machines with intelligence, and plays an influential role in reducing low latency to give an environment with a perception of zero delay. The critical application that requires a 1 ms round trip delay requires a speed of light to transfer the packets; however, taking into consideration the distance, only 150 km can be traveled in both directions.
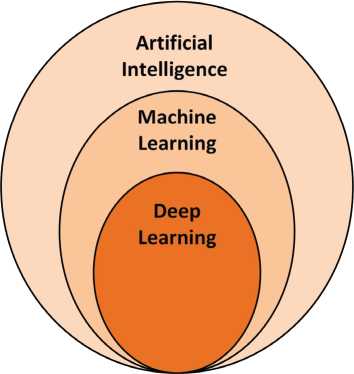
Figure 3.8. Venn diagram of the relationship between artificial intelligence, machine learning and deep learning
By deploying 5G, which is characterized by the high data rate and physical layer features that makes it possible for data to travel within a few milliseconds, it is still hard to deploy the mission-critical applications respecting the 1 ms latency (Morocho-Cayamcela et al. 2019). The network domain combined with AI tools can be the best way to overcome this problem. The AI, with its predictive models in ML, can be implemented in a different part of the network architecture, depending on the functionality that needs this tool. For example, the ML can be enabled in location-based services, caching and computation techniques in MEC, and its combination with SDN to control the traffic in the network. Additionally, networks nowadays tend to be autonomous, and lean towards self-organization without the intervention of humans.
AI as a whole is a vast domain; learning techniques are the most attractive applications to be used in the TI. Machine learning and deep learning fall under the broad category of AI (see Figure 3.8). To investigate their suitability for the TI, it is imperative to understand both of them. The ML techniques try to find a relationship between the input dataset and output actions to converge on an automation of the system without human intervention. An approach to proceed in ML is to break up the whole process into two phases: the training phase and the decision-making phase (Xie et al. 2019).
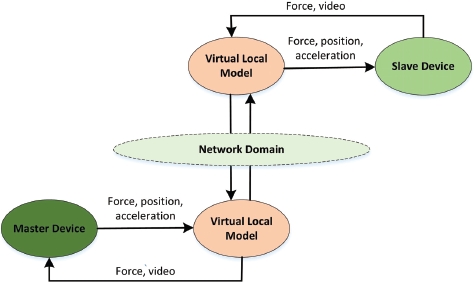
Figure 3.9. Model-mediated architecture. For a color version of this figure, see www.iste.co.uk/ali-yahiya/tactile.zip
According to the training dataset input to the system, the ML is applied, to learn the system model, while, in the decision phase, the output of the system is obtained based on the trained model. Machine learning algorithms are basically distinguished into four categories: supervised, unsupervised, semi-supervised and reinforcement learning.
Deep learning can be considered as a subset of ML; however, it tries to mimic biological nervous systems more and achieve representation learning, using multi-layer transformation. A deep learning prediction algorithm is composed of several layers. Normally, the input data passes through the layers in sequence, and each layer carries out matrix multiplications on the data. The output of a layer is usually the input to the subsequent layer. After data is processed by the final layer, the output is either a feature or a classification output.
The prediction models of ML can be integrated with the model-mediated system in order to predict the reaction of the remote teleoperation at the slave edge. The importance of the predictive models is driven from that fact that they have a critical impact regarding the stability of the whole system. This is why the model-mediated system is the best option when dealing with TI applications requiring very low latency. This model is based on providing a virtual version of the distant environment in the master domain, so the interaction will be in real-time, with different types of network domain. This interaction is based on a predictive model, based on ML, to predict the next movement of the teleoperator. In order to update the master domain and check its correctness and validity, the operator should continuously receive feedback from the teleoperation, in order to ensure that there is no force disturbance caused by any errors that occur (Ateya et al. 2019).
3.2. Conclusion
The key enablers described in this chapter are some technological advancements that can be considered as a step towards the deployment of a successful Tactile Internet use case. The combination of software and hardware involved in the deployment of the Tactile Internet’s application may be the trigger to better understanding of how to build an application, and which key enablers to use. The usage of all key enablers is not necessary to have a successful use case; it depends all on the requirements and needs in terms of QoS, QoE and how each key enabler would contribute to the stability of the whole system.
3.3. References
Al Agha, K., Pujolle, G., Ali-Yahiya, T. (2016). Mobile and Wireless Networks. ISTE Ltd, London and John Wiley & Sons, New York.
Ateya, A.A., Muthanna, A., Gudkova, I., Abuarqoub, A., Vybornova, A., Koucheryavy, A. (2018). Development of intelligent core network for tactile internet and future smart systems. Journal of Sensor and Actuator Networks, 7(1), 1.
Ateya, A.A., Muthanna, A., Vybornova, A., Gudkova, I., Gaidamaka, Y., Abuarqoub, A., Algarni, A.D., Koucheryavy, A. (2019). Model mediation to overcome light limitations - Toward a secure tactile internet system. Journal of Sensor and Actuator Networks, 8(1), 6.
Cabrera, J.A., Schmoll, R., Nguyen, G.T., Pandi, S., Fitzek, F.H.P. (2019). Softwarization and network coding in the mobile edge cloud for the tactile internet. Proceedings of the IEEE, 107(2), 350–363.
Costa-Requena, J., Santos, J.L., Guasch, V.F., Ahokas, K., Premsankar, G., Luukkainen, S., Pérez, O.L., Itzazelaia, M.U., Ahmad, I., Liyanage, M., Ylianttila, M., de Oca, E.M. (2015). SDN and NFV integration in generalized mobile network architecture. 2015 European Conference on Networks and Communications (EuCNC), 154-158, Paris, France, June 29-July 2.
ETSI (2013). Network functions virtualization (NFV); architectural framework v1.1.1, Technical report, ETSI.
ETSI (2018a). 5G; NR; physical layer; general description (3GPP TS 38.201 version 15.0.0 release 15), Technical specification, ETSI.
ETSI (2018b). LTE; 5G; evolved universal terrestrial radio access (E-UTRA) and NR; service data adaptation protocol (SDAP) specification (3GPP TS 37.324 version 15.1.0 release 15), Technical specification, ETSI.
Giannoulakis, I., Kafetzakis, E., Xylouris, G., Gardikis, G., Kourtis, A. (2014). On the applications of efficient NFV management towards 5G networking. 1st International Conference on 5G for Ubiquitous Connectivity, 1-5, Levi, Finland, 26-27 November.
Maier, M., Chowdhury, M., Rimal, B.P., Van, D.P. (2016). The tactile internet: Vision, recent progress, and open challenges. IEEE Communications Magazine, 54(5), 138–145.
Mao, Y., You, C., Zhang, J., Huang, K., Letaief, K.B. (2017). Mobile edge computing: Survey and research outlook. CoRR, abs/1701.01090 [Online]. Available at: http://arxiv.org/abs/1701.01090.
Morocho-Cayamcela, M.E., Lee, H., Lim, W. (2019). Machine learning for 5G/B5G mobile and wireless communications: Potential, limitations, and future directions. IEEE Access, 7, 137184–137206.
Ravindran, R., Chakraborti, A., Amin, S.O., Azgin, A., Wang, G. (2017). 5G-ICN: Delivering ICN services over 5G using network slicing. IEEE Communications Magazine, 55(5), 101–107.
Rost, P., Mannweiler, C., Michalopoulos, D.S., Sartori, C., Sciancalepore, V., Sastry, N., Holland, O., Tayade, S., Han, B., Bega, D., Aziz, D., Bakker, H. (2017). Network slicing to enable scalability and flexibility in 5G mobile networks. IEEE Communications Magazine, 55(5), 72–79.
Sachs, J., Andersson, L.A.A., Araúo, J., Curescu, C., Lundsö, J., Rune, G., Steinbach, E., Wikström, G. (2019). Adaptive 5G low-latency communication for tactile internet services. Proceedings of the IEEE, 107(2), 325–349.
Simsek, M., Aijaz, A., Dohler, M., Sachs, J., Fettweis, G. (2016). 5G-enabled tactile internet. IEEE Journal on Selected Areas in Communications, 34(3), 460–473.
Skorin-Kapov, L., Varela, M.V., HoBfeld, T., Chen, K.-T. (2018). A survey of emerging concepts and challenges for QoE management of multimedia services. ACM Transactions on Multimedia Computing, Communications, and Applications, 14(2s), 29:1-29:29 [Online]. Available at: http://doi.acm.org/10.1145/3176648.
Tran, T.X., Hajisami, A., Pandey, P., Pompili, D. (2017). Collaborative mobile edge computing in 5G networks: New paradigms, scenarios, and challenges. IEEE Communications Magazine, 55(4), 54–61.
Xie, J., Yu, F.R., Huang, T., Xie, R., Liu, J., Wang, C., Liu, Y. (2019). A survey of machine learning techniques applied to software defined networking (SDN): Research issues and challenges. IEEE Communications Surveys Tutorials, 21(1), 393–430.
Zhang, H., Liu, N., Chu, X., Long, K., Aghvami, A., Leung, V.C.M. (2017). Network slicing based 5G and future mobile networks: Mobility, resource management, and challenges. IEEE Communications Magazine, 55(8), 138–145.
