CHAPTER 53. Adding Wireless Networking to a LAN
SOME OF THE MAIN TOPICS IN THIS CHAPTER
Choosing Locations for Access Points 988
Wireless networking is one of the fastest-growing segments of networking in both business and small office/home office (SOHO) environments. As the family of 802.11-based wireless networks has expanded to embrace faster versions and Wi-Fi interoperability testing has helped assure that Wi-Fi Certified wireless hardware from different vendors can be used on the same network, the price of wireless LAN equipment has fallen dramatically. The introduction of a wireless LAN wizard in Windows XP, starting with Service Pack 2, along with vendor-specific improvements in setup, has made wireless networking easier to implement than ever before. You should consider, however, whether you really need to use wireless networking in your LAN before you decide to implement it. Wireless networking can solve many problems for your organization, but it can also introduce new management, security, and troubleshooting issues. You should make sure that the benefits of wireless networking in a particular situation outweigh potential disadvantages.
One particular environment that can benefit greatly from wireless networking is the SOHO network. Wireless networks are easier to install than having to run cables everywhere.
Note
Three industry-standard 802.11 implementations are currently certified by the Wi-Fi Alliance. IEEE 802.11b, the original Wi-Fi standard, runs at 11Mbps and uses channels in the 2.4GHz frequency band. IEEE 802.11a differs in speed (54Mbps) and frequency (5GHz band). IEEE 802.11g, the most popular Wi-Fi standard, runs at up to 54Mbps (like 802.11a) but uses the same 2.4GHz frequency band as 802.11b and can co-exist on the same network as 802.11b hardware. Currently, 802.11g and various proprietary extensions of this standard are the most common standard for SOHO wireless networks. 802.11a is used primarily in corporate wireless networks or alongside of 802.11g in dualband SOHO implementations. 802.11b is used primarily in older networks, or by some specialized devices. 802.11b is no longer widely available for new installations.
![]() You can read more about the 802.11 standards in Chapters 19, “IEEE 802.11b: Wi-Fi Pioneer;” 20, “Faster Service: IEEE 802.11a;” and 21, “The IEEE 802.11g Standard.”
You can read more about the 802.11 standards in Chapters 19, “IEEE 802.11b: Wi-Fi Pioneer;” 20, “Faster Service: IEEE 802.11a;” and 21, “The IEEE 802.11g Standard.”
Why Go Wireless?
Wireless networking has its place in the home, small office, and enterprise environments. You can use an inexpensive Access Point to create a network of just a few computers, or you can use multiple wireless Access Points (APs) throughout a large company to further enable mobility of your networked clients.
There are many good reasons to use wireless networking. First, it’s a quick way to set up a peer-to-peer network that is needed for only a short period of time, such as in a home office where you only have two or three computers that need a link and you don’t want to be running network cables through your walls. You can also use wireless networking to connect a computer and another device, such as a printer (using either built-in wireless networking or a wireless print server), a digital camera, or a handheld device such as a PDA.
For the home environment, wireless networking may be the perfect choice because it not only eliminates the necessity of pulling cables, but also gives you flexibility in where you locate your equipment. For example, although you might have set aside a portion of your house to use for your home office, it’s nice to be able to take the laptop into the living room (or out on the deck in the back yard) and work while you’re watching that favorite TV show. Wireless networking makes this simple.
Another use for wireless technology is the trade show environment. If you need to network several computers and possibly a printer or two, a network using a wireless Access Point can be a quick way to get your booth up and running in a hurry. This also can be used at a client site if you’re in the consulting business and don’t want to connect your computers to your client’s network. Indeed, it can be an easy way to get your computers into the client’s office because they’ll have no up-front work to do to provide you with networking services.
Finally, you can use a wireless network to extend the reach of your existing LAN. Access points can be connected to a wired LAN to provide an ingress point for wireless clients. On a SOHO network, you can replace an existing router with a wireless router. Both wired and wireless routers typically incorporate a multi-port 10/100 Ethernet switch, so you can use a single device to create a mixed wired/wireless network.
However, just because it’s possible doesn’t mean it’s necessary. Some places in a corporate network that you might find wireless network APs a good idea include
![]() Conference rooms—Users often bring laptop computers to meetings to take notes. Using wireless networking in a conference room can allow that laptop to locate information that exists elsewhere on the LAN that might be useful during the meeting. No more “I’ll get back with you on that” excuses.
Conference rooms—Users often bring laptop computers to meetings to take notes. Using wireless networking in a conference room can allow that laptop to locate information that exists elsewhere on the LAN that might be useful during the meeting. No more “I’ll get back with you on that” excuses.
![]() Temporary workgroups—An Access Point can be useful when you need to bring in temporary workers, using space that’s otherwise not wired for network access. Because many manufacturing plants have seasonal peaks and slumps, this might be an ideal way to quickly set up new clients on a network without the expense of having to go through the process of providing switches and cable runs to all parts of your building. Instead, a single cable run can be used for an AP that can serve a variable number of clients on an as-needed basis. If you choose this approach, make sure you select an AP capable of handling the maximum number of workers who will connect to it at one time. Generally, corporate or enterprise-level APs are designed to support a much higher number of simultaneous users than SOHO APs. If you anticipate needing to support VPN connections, make sure you determine the maximum number of VPN users who will use the AP at the same time, and select a model that meets that requirement as well.
Temporary workgroups—An Access Point can be useful when you need to bring in temporary workers, using space that’s otherwise not wired for network access. Because many manufacturing plants have seasonal peaks and slumps, this might be an ideal way to quickly set up new clients on a network without the expense of having to go through the process of providing switches and cable runs to all parts of your building. Instead, a single cable run can be used for an AP that can serve a variable number of clients on an as-needed basis. If you choose this approach, make sure you select an AP capable of handling the maximum number of workers who will connect to it at one time. Generally, corporate or enterprise-level APs are designed to support a much higher number of simultaneous users than SOHO APs. If you anticipate needing to support VPN connections, make sure you determine the maximum number of VPN users who will use the AP at the same time, and select a model that meets that requirement as well.
![]() Mobile users—For users who mainly work with a laptop and are usually on the road—such as salespeople—a wireless solution might be a good idea. When the user returns to the office for a short time, a docking station can serve to connect the laptop to the wired network. However, a docking station basically means reserving a desk as well and overhead can be expensive in today’s competitive market. Instead, a single office with a few desks and an AP can serve a large number of transient workers.
Mobile users—For users who mainly work with a laptop and are usually on the road—such as salespeople—a wireless solution might be a good idea. When the user returns to the office for a short time, a docking station can serve to connect the laptop to the wired network. However, a docking station basically means reserving a desk as well and overhead can be expensive in today’s competitive market. Instead, a single office with a few desks and an AP can serve a large number of transient workers.
![]() Factory floor—Laptops are not the only computers that can be used in a wireless network. Many PDAs and other small handheld devices are available that can use Wi-Fi network cards. On a factory floor, where mobility is important, it’s easier to use a small portable device than it is to set up a series of PCs throughout the plant. Because many manufacturing plants need to reconfigure the factory floor on a periodic basis to retool for new products, wireless networking can again prove to be a cost saver.
Factory floor—Laptops are not the only computers that can be used in a wireless network. Many PDAs and other small handheld devices are available that can use Wi-Fi network cards. On a factory floor, where mobility is important, it’s easier to use a small portable device than it is to set up a series of PCs throughout the plant. Because many manufacturing plants need to reconfigure the factory floor on a periodic basis to retool for new products, wireless networking can again prove to be a cost saver.
![]() In Chapters 18, “Introduction to Wireless Networking,” and 19, you can find information on how to extend a network with wireless technology.
In Chapters 18, “Introduction to Wireless Networking,” and 19, you can find information on how to extend a network with wireless technology.
Another place that wireless networking can serve a useful purpose is for outdoor activities. I’ve worked at many places that have outdoor locations that employees can use at lunchtime. These areas also can be comfortable places to hold meetings. Sometimes just getting out of the office can boost employee morale and taking the network outside can, as noted previously, make meetings more productive. There are many other uses for wireless networks, and new ideas are being created every day.
Note
In addition to the deployment of wireless networking in the SOHO and enterprise corporate environment, wireless networking is finding its way into many public spaces. At this time, many hotels already offer wireless networking for guests and meeting room clients, along with the plug-in dial-up access that has become the norm. Public libraries, airports, coffee shops, truck stops, and a few entire cities offer a variety of free or paid wireless access services. Although it’s still useful to find out in advance where you can get wireless access as you travel around the city or the country, who provides it, and how much it costs, you can easily stay in touch as you travel.
Choosing Locations for Access Points
Just as you need to test new network configurations or PC configurations in a laboratory before rolling them out for production usage, you need to evaluate the placement of APs should you decide to get into wireless networking. Wi-Fi provides for roaming capabilities, but it also enables you to restrict users to selected APs if you choose to do so. First, decide how you want to use wireless networking and which users it can be used by in a productive manner. Next, decide how many APs you need and where to place them.
You’ll have to do some experimentation. Read the vendor’s documentation to get the basics of the coverage area that the product is capable of, keeping in mind that this is only a general figure. For example, you’ll find that most APs are capable of covering larger distances outside, rather than inside, because there are fewer structural components, such as bricks or steel beams, that can block the signal. You should take a vendor’s specifications about its particular product with a grain of salt. Your mileage can vary.
If you use wireless networking inside and want to cover the entire building, you’ll have to test to see exactly how far the coverage is for each AP. Also note that several factors can influence the performance you’ll get no matter where you place the AP. For example, each AP is capable of supporting only a limited number of users before the available bandwidth begins to become saturated. Although 802.11g hardware is the overall favorite in SOHO and public-access networks, the higher frequency used by 802.11a enables it to support more users than with 802.11g. For maximum speed and flexibility in your business network, using dual-mode 802.11a/802.11g wireless APs and adapters is recommended.
Another thing to consider is source of interference, such as microwave ovens and other wireless devices. If you employ Bluetooth devices, you need to be careful because Bluetooth can interfere with Wi-Fi 2.4GHz (802.11b and 802.11g) devices when used at distances of 2cm or less or distances greater than 10cm (for example, a user with a Bluetooth keyboard/mouse or a Bluetooth wireless headset using a computer with an 802.11g wireless network adapter might have problems). Although Bluetooth has been improved with technology such as adaptive frequency hopping (first introduced in Bluetooth version 1.2) to try to minimize interference, the use of Bluetooth in close proximity to 2.4GHz Wi-Fi devices can virtually shut down the 2.4GHz Wi-Fi devices. If you plan to use Wi-Fi and Bluetooth devices in your organization, consider using 802.11a or dual-band 802.11a/802.11g wireless APs and adapters. 802.11a does not use the same frequency as 802.11g or Bluetooth.
Note
Richard Quinnell provides an excellent summary of the current challenges facing Wi-Fi 2.4GHz and Bluetooth operations in close proximity in his August 2005 article “WiFi and Bluetooth Fight for Bandwidth.” Find it online at www.edn.com/article/CA629312.html.
Another popular SOHO and office device is the 2.4GHz cordless telephone. These telephones operate in the same band as 2.4GHz wireless networks and can cause problems when used in the vicinity of wireless networking devices. Consider upgrading to 5.8GHz wireless phones if you use 2.4GHz Wi-Fi wireless network hardware. If you also use 5GHz (802.11a) wireless networking, don’t worry: 5.8GHz phones do not cause significant interference with 5GHz Wi-Fi (802.11a) wireless networks.
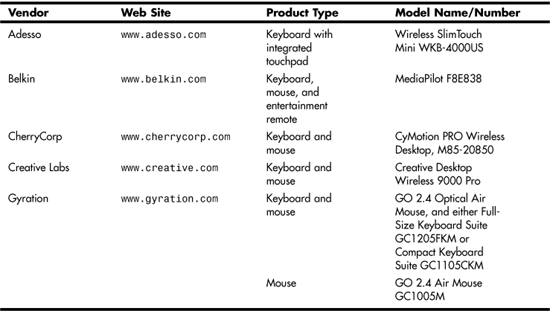
Some types of wireless mouse devices and keyboards also present a risk of conflict. All Bluetooth-based devices, including wireless mouse devices and keyboards, use the 2.4GHz band, as do many non-Bluetooth implementations from various vendors. To help prevent conflicts, many of these devices support multiple channels. Use the contact information in Table 53.1 to determine if a particular 2.4GHz input device might conflict with your existing 2.4GHz devices.
Table 53.1. 2.4GHz Wireless Input Devices (Non-Bluetooth)
Tip
If a wireless mouse or keyboard has a maximum range of six feet or less, it uses 27MHz technology. A wireless mouse or keyboard with a maximum range of 25 feet or further uses 2.4GHz technology. Check the device’s specifications to determine if the device uses Bluetooth or a proprietary implementation.
Table 53.1 lists many popular non-Bluetooth input devices that use the 2.4GHz RF band.
And keep that microwave oven in the break room well shielded! You can purchase an inexpensive device at most consumer discount stores that can measure the amount of microwave radiation that’s leaking from a microwave oven. You might find that simply replacing an old microwave oven with a newer model cures any interference problems. And because most work places don’t need a top-of-the-line microwave that can zap a baked potato in just a few minutes, go with a low-end model that uses less power.
Security Issues
Using wireless technology opens up the possibility of security breaches. Thoroughly read the documentation that comes with your choice of devices to find out what kind of security features can be enabled. It’s probably best to associate the wireless network adapters you buy with one or more APs, depending on the work habits of the user. Also note that many devices come with default settings and that these are known to anyone who owns a similar device or who cares to look up the information on the Internet. To help prevent security problems, implement security procedures such as setting up unique passwords on each AP, using your own SSIDs rather than using the default name that the wireless vendor provides, and disabling SSID broadcast.
Change any default settings used to match up wireless adapters and Access Points to use a value other than the default. Use the security features of your operating system to monitor wireless users. For example, I’d be more concerned with a Windows 2000 or Windows XP user’s resource access permissions if the client computer uses a wireless network card than I would be if it were wired directly to the network. Windows XP, because it is designed to automatically connect to an unsecured wireless network, makes it very easy to connect, but it means that using wireless security settings are no longer a luxury. If you want to keep unauthorized users off your wireless network, you must enable the strongest form of wireless security supported by your wireless AP and wireless adapters.
Although older wireless network hardware used only the first Wireless Equivalency Protocol (WEP) security standard, this standard is not strong enough for today’s networks. WEP uses fixed-length static keys, and even if the newer 128-bit or corporate-level 256-bit encryption is used rather than the older 64-bit encryption, WEP is easy to crack. Many tools are available online that can be used to circumvent WEP encryption, so don’t bet your business on it.
Wi-Fi Protected Access (WPA) and its improved sibling, WPA2, provide much greater wireless network security than WEP. Both can be used with RADIUS authentication servers on your corporate network for even greater security. Even in a SOHO environment, WPA and WPA2 are far more crack-resistant that WEP. If you still have hardware that does not support WPA, consider replacing it if you cannot upgrade its drivers or firmware to support WPA.
Remember that it’s easier to eavesdrop on a wireless network because you don’t have to make any connections to a cable, as in a wired network. Radio waves are out there for anyone within range of your technology to pick up.
![]() You can learn more about wireless security in Chapter 23, “Other Wireless Technologies.”
You can learn more about wireless security in Chapter 23, “Other Wireless Technologies.”
In any case, it’s easy to set up auditing for important resources and to review them using the Event Viewer in Windows 2000/XP and Windows Server 2003. No matter how safe you think your network is, there’s no excuse for not auditing (and checking the audits) to ensure that your security measures are working. Looking for such things as a large number of login failures can alert you to someone trying to break into your wireless network. Unix and Linux (using the syslog utility) can also be used to look for system auditing information. The syslog utility can be configured to also send alerts, by email and other means, so that you can be informed quickly of any possible security breaches (or attempts).
![]() For more information about auditing, see Chapter 43, “Auditing and Other Monitoring Measures.”
For more information about auditing, see Chapter 43, “Auditing and Other Monitoring Measures.”
Another cause for concern is that wireless networking enables the computer to be mobile. A user can take his computer home. Although you might be able to stop users from downloading prohibited Internet files at work, you can’t always police what they do at home. It’s a simple matter to pop out the wireless networking adapter and pop in a modem (or better yet, simply use a wireless Access Point at home also, because it is so inexpensive). As with any computer that leaves the company premises, a regular audit of software on the system should be performed, and your security policy should state what the computer can—and cannot—be used for. Of course, this should be a standard procedure for all computers on your network.
