CHAPTER 18. Introduction to Wireless Networking
SOME OF THE MAIN TOPICS IN THIS CHAPTER ARE
Why Wireless Networks Have Proliferated 281
Access Points and Ad Hoc Networks 283
Physical Transmission Technologies 286
The IEEE 802.11 Wireless Standard 288
Sources of Interference for Wireless Networks 290
Although the installed base of networked computers today is mainly made up of technologies using copper wire and fiber-optic cable, the growing market for wireless technologies should not be underestimated. The popularity and rapid growth of the cellular telephone market, for both personal and business applications, attests to this fact. Just 10 years or so ago, cellular telephones were high-priced items used mainly by business executives. Today, they are sold in shopping mall kiosks. You can even buy a prepaid cell phone now and pay as you go.
Other than the CB (Citizens’ Band) radio craze that peaked a few decades ago, it was not until cell phones became inexpensive that wireless networking became a hot issue. And now many kinds of wireless networking devices have worked their way into our everyday life.
Today’s wireless phones and other wireless devices now have uses that probably were never envisioned by the creators of this technology. Use your cell phone to report an automobile accident. Put up a wireless camera to monitor a child. Access the Internet through your cell phone. Use a camera phone to capture on-the-spot photos or even video of accidents, crimes, you name it. I could go on and on...
Note
It’s hard to write this chapter without discussing the first wireless network: radio! (Hey, we’re talking electronic technology here, not the village crier.) Broadcast commercial radio is a one-way technique, but there are many variants of two-way radios, from those used by police and fire departments to the CB radios that were a hot item years ago. However, today we’re discussing wireless communications between computers, consumer electronic devices—the sky is the limit.
Many mobile phones today are already equipped to handle text messaging, Internet email, some limited Web-browsing capabilities, and low-resolution digital photography. This chapter will introduce you to just a few of the many problems that wireless networking can solve, and introduce you to some of the technologies basic to many of the wireless technologies. Other networking solutions are found in Chapter 23, “Security and Other Wireless Technologies,” and Bluetooth is covered in Chapter 22, “Bluetooth Wireless Technology.” Although Bluetooth is a wireless technology, its original purpose is not as far reaching as the IEEE 802.11b, 802.11g, or 802.11a technologies (covered in Chapters 19, “IEEE 802.11b: Wi-Fi Pioneer;” 20, “Faster Service: IEEE 802.11a;” and 21, “The IEEE 802.11g Standard”). Instead, Bluetooth was initially designed to replace cables that span only a very short distance. Yet new profiles do indeed enable you to create a small LAN using Bluetooth. Because of distance limitations, however, it still is not the wireless LAN technology of choice for anything but a small LAN with minimal bandwidth requirements.
You can now use Bluetooth to exchange data between a mobile phone and a PC. For example, properly configured, a Bluetooth-enabled wireless phone can be used for a modem connection to a PDA or laptop similarly equipped. Or, you can use a Bluetooth keyboard and mouse with a Bluetooth receiver attached to your computer. This short-distance communication capability does not address the much larger distances that the specifications 802.11a, 802.11b, and 801.11g can cover. But it is important to keep in mind that although you can create a small LAN using Bluetooth, it was not developed to create a LAN or WAN. It works best for short-distance transmissions between peripheral devices and consumer electronic devices. Because it uses a radio spectrum, it is possible to create many devices, such as a TV remote, using Bluetooth, because current devices require a line-of-sight. If your cable box is in the living room and you’re in the bedroom, you could use a Bluetooth-enabled cable box/remote to change the channel, all while staying in bed! Bluetooth should be seen as a complimentary wireless technology to 802.11-based wireless networks rather than as a direct competitor.
Despite my predictions in previous editions of this book, Bluetooth devices have finally started to make it to the low-cost marketplace, and you can expect to see more of this technology as time marches on. More than a few users like the portability of their keyboard and mouse, as well as the convenience of wireless synchronization with a PDA or downloading from a digital camera.
Why Wireless Networks Have Proliferated
If you still don’t already use some type of wireless device, it won’t be long until you do. As with any typical purchase of computer/network equipment, it’s the applications that drive the purchases, especially in a business environment. Wireless technology is already the preferred method for networking homes and small businesses, and large enterprises, particularly those with multi-building campuses, are using wireless networking to extend the reach of their existing 100Mbps and Gigabit Ethernet-wired LANs to cover every part of the campus, indoors or outdoors. Wireless networking is now fast enough that it is being used instead of wired networking in new installations where there was no existing wired network.
Laptop computers provided the first true mobility for computer users. Support for linking these powerful platforms to a computer network is usually built in to today’s laptops, but if your laptop doesn’t have built-in wireless support, it can be accomplished easily by means of either a PC Card/CardBus network adapter or a docking station. By using DHCP to assign network configuration information, it’s easy to move a portable computer from one location to another and still provide a simple connection to the network. However, until the advent of wireless network connectivity, this kind of mobility still depended on a wired connection of some sort. By adding wireless capability to an existing wired network, the mobility and usefulness of the notebook computer are increased dramatically.
For a technology to grow, it must solve some kind of problem. That is, it must be useful in some way. As described previously in the discussion of the types of devices that now use wireless networking, the most obvious benefit this kind of networking provides is mobility. Wireless LANs have become a mainstay networking infrastructure for many SOHO networks as well as home networks where multiple computers may share a single Internet connection. Other benefits that you might get from wireless networking include the following:
![]() Faster installation when compared to cabled networks. Just configure the network adapter (and Access Point if you have one) and start networking with others.
Faster installation when compared to cabled networks. Just configure the network adapter (and Access Point if you have one) and start networking with others.
![]() Adaptability in a dynamic environment.
Adaptability in a dynamic environment.
![]() The capability of sharing an Internet or other WAN connection.
The capability of sharing an Internet or other WAN connection.
![]() The continuing development of new electronic devices (or newer versions) that use wireless technology, such as PDAs; network-ready, all-in-one devices; and digital projectors.
The continuing development of new electronic devices (or newer versions) that use wireless technology, such as PDAs; network-ready, all-in-one devices; and digital projectors.
![]() With the widespread deployment of wireless Access Points that are being constructed in public places, you can now access the Internet from most any place that has a sizable population. In some cases, you might need to use a commercial network on a per-hour, per-day, or per-month access charge basis through various commercial providers. These are common in truck stops, airports, and some restaurants, coffee shops, and copy shops. Some locations offer free service for their customers, so you can surf the Web while you drink a cup of java or grab lunch. Also, some localities are constructing community-wide wireless networks, and many public and university libraries offer open wireless LANs that can be used by anyone in the vicinity. The terms hotspot and hotzone are often used to indicate locations that offer wireless Internet access.
With the widespread deployment of wireless Access Points that are being constructed in public places, you can now access the Internet from most any place that has a sizable population. In some cases, you might need to use a commercial network on a per-hour, per-day, or per-month access charge basis through various commercial providers. These are common in truck stops, airports, and some restaurants, coffee shops, and copy shops. Some locations offer free service for their customers, so you can surf the Web while you drink a cup of java or grab lunch. Also, some localities are constructing community-wide wireless networks, and many public and university libraries offer open wireless LANs that can be used by anyone in the vicinity. The terms hotspot and hotzone are often used to indicate locations that offer wireless Internet access.
![]() Reduced costs in many situations—for example, to avoid having to install cabling throughout a building.
Reduced costs in many situations—for example, to avoid having to install cabling throughout a building.
One caveat to keep in mind is that security is a big issue with wireless networking. Although 802.11b hardware supports Wired Equivalent Privacy (WEP) security, newer and much more secure standards have been developed and are supported by most 802.11a- and 802.11g-based network hardware. See Chapter 23 for more information.
In a typical LAN setup, it is necessary to install and configure the networking software on the client computer and provide the wiring from the network switch to the user’s work area. With a wireless LAN, you only need to install the wireless NIC and configure the computer’s networking software. You don’t have to string cables through the building for each user. In an environment that changes rapidly, this can be an advantage. For example, point-of-sale terminals in a large store can be reconfigured easily for seasonal adjustments, such as the end-of-the-year Christmas buying spree. Hand-held devices can be used for inventory control and for creating checkout tickets that can be presented to a cashier to speed up the process of paying for merchandise. In a warehouse, the floor layout might change during the year for similar kinds of reasons. Relocating computers is much easier when there are no cabling issues to deal with. After the initial investment is made in wireless LAN devices, the capability to reconfigure the physical network topology can result, in many cases, in reduced costs over time.
An ad hoc network or temporary setup (see the following list) is another important aspect. For example, if you are in the consulting business and need to have several consultants exchange information, you can use wireless networking to set up your own local network and bypass your customer’s wired network. Knowing this allows your client to worry less about security than if the client has to go through the typical paperwork and other management functions to get your consulting team connected to the company network.
In addition to these kinds of environments, you will find wireless LANs increasingly being used in situations such as the following:
![]() Hospitals—Patient information can be obtained easily using a standard laptop computer, a specialized terminal, or a Tablet PC. Instead of having to return to a central location, such as the nurse’s station on the hospital floor, doctors and nurses can get information quickly as they make their patient rounds.
Hospitals—Patient information can be obtained easily using a standard laptop computer, a specialized terminal, or a Tablet PC. Instead of having to return to a central location, such as the nurse’s station on the hospital floor, doctors and nurses can get information quickly as they make their patient rounds.
![]() Older buildings—In some cases, it can be difficult to wire the premises for a traditional network. Some older buildings that do not have plenum areas in the ceiling can be difficult to adapt. Using wireless communications makes networking in this kind of environment an easy task.
Older buildings—In some cases, it can be difficult to wire the premises for a traditional network. Some older buildings that do not have plenum areas in the ceiling can be difficult to adapt. Using wireless communications makes networking in this kind of environment an easy task.
![]() Temporary setups—This feature was mentioned in the introductory paragraph to this list. You can extend it further to such situations as a trade show, where the network is usually set up for only a few days; the computers can be configured ahead of time so that the only thing your company representative has to do is turn them on.
Temporary setups—This feature was mentioned in the introductory paragraph to this list. You can extend it further to such situations as a trade show, where the network is usually set up for only a few days; the computers can be configured ahead of time so that the only thing your company representative has to do is turn them on.
![]() Warehouse and factory floors—Laptop computers and handheld bar-code scanners that use wireless LAN technology can quickly return the investment needed for their implementation. In this kind of situation, however, it is important to test the equipment first to ensure that no other machines or devices in the area can interfere with the wireless transmissions.
Warehouse and factory floors—Laptop computers and handheld bar-code scanners that use wireless LAN technology can quickly return the investment needed for their implementation. In this kind of situation, however, it is important to test the equipment first to ensure that no other machines or devices in the area can interfere with the wireless transmissions.
Caution
In a discussion of the applications of wireless networking, the dialogue should not be limited to computers. As data collection devices, such as bar-code scanners, or handheld data-entry terminals, such as cash registers, are equipped with wireless networking connections, many more practical uses for wireless communications will develop in the next few years.
However, you should consider that when making a transaction at this type of service, you can’t be sure of what kind of security is in place. If simple WEP security is used (see Chapter 23), with a small key (40 bits), then it is a simple matter for a hacker to use tools freely available on the Internet to intercept these communications.
Before you give your credit card to a cashier, you might want to find out from the store manager what kind of wireless technology is being used to ensure your privacy. You should also check your credit (or debit) card statement each month to be sure your information has not been compromised!
Access Points and Ad Hoc Networks
Before getting into the specifics about IEEE standards and how data is transmitted on radio frequencies, you first should look at the topology a wireless network can take. In Chapter 2, “Overview of Network Topologies,” you learned that a wireless network doesn’t use a bus topology. Wireless networks that use a WAP use an infrastructure network. The WAP transmits data between stations. If a single WAP is used, the network has a star topology; if multiple WAPs are used, the network has a tree topology. Many WAPs also include a router for Internet access. Another type of wireless network is the ad-hoc network, in which all nodes connect directly with each other. This is a mesh network topology.
Ad Hoc Networks
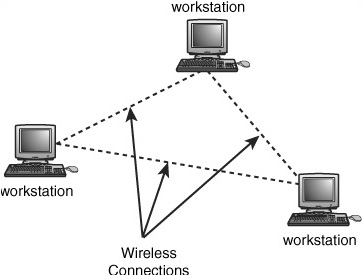
A simple peer-to-peer network, composed of computers that have compatible wireless network adapter cards, can be used to quickly set up a small network on-the-fly. This kind of workgroup LAN can be useful when only a few stations need to communicate in a small geographical area (see Figure 18.1). You can set up your own individual network at a trade show, in a conference room, or even for an entire small-business enterprise. Wireless bridges, which you’ll learn about in Chapter 24, can extend the distance between wireless Access Points so that in a business you can create a network without having to pull cables at all. For a home office, where you probably don’t want to drill holes in your walls and pull cables, wireless products can be the best solution possible.
Figure 18.1. All you need to create a network on-the-fly are a few computers, each with a wireless network adapter.
This network is referred to as an ad hoc network because it involves simple peer-to-peer connections in a wireless environment. No central hub or switch coordinates the communications that occur. Instead, any computer equipped with a compatible wireless adapter can join the ad-hoc network, provided that the appropriate security mechanisms have been implemented. For example, if you are using a Windows operating system and a simple workgroup setup for network communications, any computer that uses that same workgroup name can join your small ad hoc network. If any file or print shares are offered by members of this ad hoc network, you can protect them by using a password. This is not a great way to protect files, because anyone who needs to map to a resource share will use the same password.
Tip
In a very small network, using simple file shares is a good compromise considering the administrative overhead involved in managing a more sophisticated security system, such as that offered by the NTFS file system used by Windows NT/2000/XP and Windows Server. If you need to segregate users who need access to some, but not all, of the same files, then divide those files into a directory (and share it on the network), and then create separate file shares for other files needed by different groups of users. Folders can be configured for read-only or full access as needed.
If you use more secure methods, such as a Unix or Linux system with each workstation requiring a username/password, you can create a more secure wireless ad hoc network. The same goes for using a Windows domain. The only difference is that the network is wireless—there are no cables—and the same security mechanisms you’d use for a wired network should be used for this simple peer-to-peer network.
Tip
Although the term ad hoc network is usually used for a quick setup of wireless stations, another term you’ll hear when reading the literature is Basic Service Set (BSS). A BSS is nothing more than two or more wireless computers that have established communications among themselves. The simplest BSS, consisting of just wireless computers described in this section, is also called an Independent Basic Service Set (IBSS) because it doesn’t have an AP to coordinate the communications between the wireless computers.
Using an Access Point to Mediate Wireless Communications
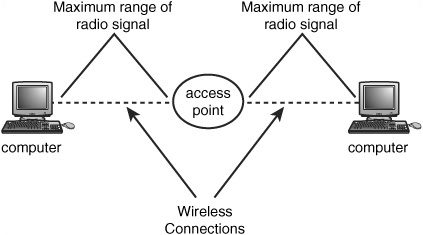
You also can use a wireless Access Point (AP) to create a small wireless network. This device can also be attached to a wired network, which is discussed next, or as a standalone device that can effectively double the distance of the wireless network. As you can see in Figure 18.2, if the Access Point device is placed in the center of the network, each computer equipped with a wireless network adapter can be placed farther away from other computers. This is because each computer only needs to be able to communicate with the AP, which in turn relays the signals to other computers that participate in the wireless LAN. Essentially, an AP performs the same function as a switch in a traditional wired Ethernet network.
Figure 18.2. As you can see, an AP can double the range of a wireless network.
You can add APs to a traditional wired network as well, enabling a mix-and-match network with both wired and wireless clients. The AP coordinates communications to and from the wireless computers and the rest of the network, whether the destination resides on copper or fiber-optic cables (see Figure 18.3) or within the range of another wireless Access Point.
Figure 18.3. APs provide the connection to the wired network for mobile users.
Because multiple APs can be placed throughout the network, this topology allows for a wider geographical range for mobile users. An AP is a simple and very inexpensive device that can connect to the wired network and provide a transmitter/receiver that can be used to communicate with mobile users’ workstations. In addition to providing the wireless communications service, an AP typically is responsible for buffering data between the wireless clients and the wired network. Unlike an ad hoc wireless setup, the AP also is responsible for mediating communications between wireless clients that operate within range of the same AP.
Note
Wireless Access Points are used for devices based on the 802.11a, 802.11b, and 802.11g standards. Some work with only one particular technology, whereas others operate in a “dual mode” and can operate with two or all three standards. Of course, such an Access Point will not increase the bandwidth for a computer that uses a lower-bandwidth wireless network card. The AP will, however, buffer data between that laptop and other faster devices, such as those based on 802.11a or 802.11g.
Many APs made for SOHO or home networks incorporate a 10/100 Ethernet switch, enabling a single device to connect wired and wireless clients into a single network. Most of these APs also contain routers, enabling the device to connect the clients to the Internet.
Most of the consumer devices on the market today support 11–60 wireless clients on a single AP at any given time. However, your mileage can vary depending on the manufacturer. For example, Cisco offers APs that can scale up to 200 or more wireless devices. Many tests by magazine labs, as well as others, indicate that you will not get the full bandwidth, much less close to it, when using wireless transmissions. The ballpark figure, based on several examples, is about one-third to one-half of the bandwidth the technology specifies. You may indeed get close to 90% throughput under ideal conditions. However, all wireless technologies suffer from the fact that barriers (such as large buildings) do exist. Keep this in mind when deciding what kind of network traffic to use in the wireless part of your network. In an outdoor environment, you will probably get a much greater distance between client and AP before the bandwidth begins to degrade.
Caution
Another cause of bandwidth degradation is enabling wireless security. However, don’t let the slowdowns inherent in the use of wireless security persuade you that you don’t need it. The phenomenon of wardriving, in which computer hackers armed with laptops, wireless network adapters, and high-gain antennas look for unsecured wireless networks, is a very real threat to an unprotected wireless network, its data, and your privacy. In my informal tests, I found a dismayingly large number of unsecured wireless networks when I was driving through a neighborhood and when I was walking through an office building. For more details about effective wireless security, see Chapter 23.
APs come in all sizes and shapes. Most use two or more antennas, although some vendors prefer a single antenna. Most APs use a horizontal form factor, although a few vendors prefer a vertical form factor. Most vendors’ standard AP supports 802.11g and 802.11b, but many also produce models that also support 802.11a, and often produce versions that support proprietary extensions designed to improve range and speed. Some of the major vendors for SOHO and small-business wireless networks include Buffalo (www.buffalotech.com), Belkin (www.belkin.com), D-Link (www.d-link.com), Linksys (www.linksys.com; owned by Cisco Systems), and NETGEAR (www.netgear.com).
![]() For more information about important AP features, see “What to Look for in an Access Point,” p. 294.
For more information about important AP features, see “What to Look for in an Access Point,” p. 294.
For enterprise networks where a large number of APs will be needed, and for which greater security is required, networking hardware is generally purchased from an existing vendor. This might result in using one or several vendors for all networking products. Enterprise-level wireless network hardware generally offers stronger encryption, better management, and a greater number of clients per AP than SOHO hardware. Some of the leading enterprise wireless network vendors include Cisco Systems (Aironet; www.cisco.com), 3Com (OfficeConnect; www.3com.com), Symbol (www.symbol.com), Apple (AirPort; www.apple.com), and SonicWALL (www.sonicwall.com).
Physical Transmission Technologies
The next few sections will familiarize you with the details involved in the actual transmission for wireless devices. Two major types of technology are used here: frequency hopping and spread spectrum. Both have been around for quite a few years. And each can be adapted to an environment where their techniques can be useful.
Frequency Hopping Versus Spread Spectrum
The most popular method for providing a communications medium for a wireless LAN is typical radio wave transmissions. Another method for sending data from one device to another without using copper or fiber-optic cabling is the infrared spectrum. However, this technology is primarily used in line-of-sight applications.
As stated earlier, the Federal Communications Commission (FCC) allocated a radio spectrum in 1985 that is called the Industrial, Scientific and Medical (ISM) band. It operates in the 2.400GHz–2.483GHz range and does not require the end user to obtain any kind of license. Similar agencies in other countries have followed suit and set aside this range for the same use. In the development of products for wireless networking using this range, a technique called spread-spectrum broadcasting is used. The 2.4GHz frequency range is used by 802.11b, 802.11g, and Bluetooth wireless networks.
The 5GHz band, another unlicensed frequency, is used by 802.11a wireless networks.
Spread-Spectrum Technology
During World War II, the military began developing a radio transmission technology called spread spectrum. Normal radio signals, such as those you pick up on your car radio, are called narrowband because they concentrate all their transmitting power on a single frequency. Spread-spectrum technology uses a much larger bandwidth instead and can be deployed using two basic methods: DSSS or FHSS. Spread-spectrum techniques are attractive to manufacturers of wireless equipment for many reasons. One of the more important reasons is that they can be difficult to detect or intercept. Additionally, from a security standpoint, spread-spectrum techniques are difficult to “jam” or interfere with.
These are the two main aspects of any spread-spectrum technique:
![]() The signal that is transmitted is of a greater bandwidth than the actual transmitted information’s bandwidth. In other words, more data is transmitted than the actual data the user intends to send.
The signal that is transmitted is of a greater bandwidth than the actual transmitted information’s bandwidth. In other words, more data is transmitted than the actual data the user intends to send.
![]() The resulting bandwidth is determined by some method other than the information being transmitted.
The resulting bandwidth is determined by some method other than the information being transmitted.
For commercial systems, the actual bandwidth used might be from 20 to 200 times the bandwidth of the actual information that is being transmitted, perhaps even larger. Some systems use a bandwidth that is up to 1,000 times larger than the information. Because the signal is spread out over a larger bandwidth, it can occupy the same bands as ordinary narrowband transmissions with little interference. A narrowband transmission can interfere with only a small portion of the signal being sent using spread-spectrum technology, and error-correction techniques can be used to compensate for this.
DSSS systems use a signal that is a combination of a pseudo-noise signal and the actual information modulated on an RF (radio frequency) carrier. By mixing two different signals to produce only one for transmission, the data is masked by the seemingly random signal it is combined with. That is, this results in a signal with a wide bandwidth that appears to be noise. At the receiving end, the pseudonoise signal is used as a mask so that the actual data part of the signal can be recovered. The pseudonoise signal is not truly a random signal, but instead is an agreed-upon method for generating a signal that both ends use.
FHSS employs a much simpler technique. It uses a narrowband carrier that continually changes frequencies. For this to work, the transmitter and receiver must both be synchronized to know which frequencies are used and in what order. The FCC dictates that at least 75 or more frequencies must be used for this technique, and any single frequency cannot be used for a burst of data longer than 400ms. Some methods of FHSS employ a simple pattern of switching from one frequency to the next. Others use a technique in which certain frequencies are skipped or in which frequency changes appear to be random.
The IEEE 802.11 Wireless Standard
The main standard for wireless LANs is the IEEE 802.11 group of standards, which were in definition as early as 1990 and have gone through several drafts since then. This standard includes definitions for the Physical layer (PHY) and the Media Access Control (MAC) layer protocols for wireless networking—both of which are covered later in this chapter. If you are familiar with Ethernet, you know that the MAC address, which is a unique address burned into a network adapter when it is manufactured, is used on a local area network to communicate with other members of the same LAN.
The standard envisions two kinds of clients: ad hoc and client/server. The ad hoc client method involves a peer-to-peer network between clients located close to each other. The client/server method uses an AP device to mediate network communications and possibly provide a connection to a wired network. Note that the first draft of the IEEE 802.11 standard provided for only transmission rates of 1Mbps and 2Mbps, but the newest standards (802.11a, b, and g) provide for much faster data transmission rates. The next few chapters discuss the three main wireless technologies. Before getting into those, however, let’s take a look at the PHY and MAC portions that are the basics of these standards.
The Physical Layer
The Physical layer of a network involves the mechanisms used to actually transmit the signal on the network medium. In this case, the medium is infrared, Frequency Hopping Spread Spectrum (FHSS), or Direct Sequence Spread Spectrum (DSSS). In the original IEEE 802.11 standard using FHSS, the data rate is 1Mbps. For DSSS, the original standard defines both 1Mbps and 2Mbps techniques. Infrared communications (it’s really wireless, after all) also is supported at both 1Mbps and 2Mbps data rates. Because few, if any, infrared devices are on the market today, they aren’t discussed in this chapter. The most important devices are those using radio frequencies (FHSS and DSSS), which you’ll find for sale by many vendors.
Note
Although the standard defines both spread-spectrum and infrared methods at the Physical layer, wireless clients using different Physical layer components may or may not interoperate. In other words, an infrared-equipped client can’t communicate with another computer that uses the radio frequency spectrum for transmissions. Yet there are Access Points that can handle a combination of 802.11a, 802.11b, and 802.11g at the same time. These specifications all involve similar technologies, but operate in different frequencies or use different transmission techniques.
The MAC Layer
For the MAC layer, the standard is similar to the 802.3 standard for traditional Ethernet networks. Before a network node (or station, as they’re usually called in the wireless world) can transmit, it must first determine whether the radio frequency channel is available, and a mechanism must be used to determine whether a transmission was successfully received by the destination station.
Carrier Sense Multiple Access/Collision Avoidance
Chapter 13, “Ethernet: The Universal Standard,” explains the mechanism Ethernet network adapters use to gain access to the network medium (a copper wire, for example): Carrier Sense Multiple Access/Collision Detection (CSMA/CD). The network adapter that wants to transmit a frame of data first listens to the wire. If the wire is silent, the card transmits a frame. It then listens to make sure that no other network adapter tried to transmit at the same time (a collision). If a collision occurs, each of the nodes that caused the collision backs off for a random interval before attempting another transmission. This random back-off mechanism is intended to keep multiple network adapters from trying to transmit at the same time again.
This works well when you have a network adapter card that transmits and receives at the same time, which is exactly how Ethernet network adapters operate. However, when you’re dealing with the airwaves, a wireless adapter can either transmit or receive, but not both at the same time. So another method for gaining access to the medium (the radio frequency on which the network is based) is used. It’s called Carrier Sense Multiple Access/Collision Avoidance, or CSMA/CA for short.
Using this principle, the wireless network adapter card first listens to determine whether any other station is transmitting, just like a traditional Ethernet card does. If the frequency is not being used, the station can transmit a frame. However, because it can’t listen at the same time to determine whether a collision has occurred, another method is used. If the destination of the transmission receives the frame intact, it sends back an acknowledgment packet (ACK). The standard provides for a higher priority for transmission of ACK packets so that they are transmitted before other stations can transmit.
After a wireless adapter has transmitted a frame, it waits to see whether an ACK is sent back. If some other station also has transmitted a frame during the same time, then the receiving end of both communications attempts will not receive an intact frame, no ACKs will be sent back, and thus both stations know they must retransmit the frame. Just as with traditional Ethernet cards, the stations that do not receive an ACK in response to a transmission assume that a collision has occurred, and wait for a random time interval before again listening to the airwaves to determine whether they can retransmit.
Another term used in the specifications for this media access method is Distributed Coordination Function (DCF); all stations based on IEEE 802.11 must implement this method.
Virtual Carrier Sense—RTS/CTS
As stated earlier in this chapter, it’s always possible that two wireless-equipped computers can begin to transmit at the same time. However, what happens when you use an AP and two stations that are so far apart they can’t hear the transmission of the other computer? This is referred to as the hidden node problem. In this situation, another means must be employed to ensure that only one station on the wireless network is transmitting at a given time.
To solve this problem, wireless computers that want to transmit a frame must first make a request for air time. Instead of just listening to the radio frequency and starting a frame transmission if the frequency is not being used, the network adapter instead transmits an RTS (request to send) frame to the AP. This frame contains information that identifies the station that wants to transmit, as well as the duration of time it wants to reserve for the transmission.
If the RTS frame is received by the AP (that is, no collision occurred due to another station also trying to transmit an RTS frame), the AP transmits a CTS (clear to send) frame that grants permission to the original computer to begin its transmission. This frame also contains the ID field of the computer that is being given permission to transmit, as well as the amount of time granted to it. Because all stations participating in the wireless network controlled by the AP can hear the CTS frame, they know they can’t begin a transmission and they also know how long they must wait before making an attempt to send an RTS frame.
This method of accessing the transmission media also is referred to as Point Coordination Function (PCF). Although DCF is required by the IEEE 802.11 standard, PCF is not. It can be implemented but is optional according to the standards.
Other Services Performed at the MAC Layer
The MAC layer also provides other services, such as association and reassociation. Remember that an AP and its clients make up a BSS in the network. A client is associated with a particular BSS. When a client moves from one BSS to another, reassociation takes place. Although the 802.11 standard provides for the concept of reassociation, the actual mechanism for this function is not specified in the standard.
Sources of Interference for Wireless Networks
Because wireless network products use radio waves for the “physical” transmission medium, you need to consider other devices that produce radio waves in the same spectrum that IEEE 802.11b devices use. For example, the most common device, which is present in the home, many offices, and many public places, is the microwave oven. Yes, these devices use radio waves to heat your food, and they have a metal grating surrounding them that is supposed to prevent microwave transmission from emanating outside the box. However, if that were true you wouldn’t see those warnings saying you shouldn’t be close to one if you have a pacemaker and there wouldn’t be a market for inexpensive devices you can purchase to measure leakage from a microwave oven. Microwave ovens do leak microwave signals and these can interfere with IEEE 802.11 devices.
The good news is that microwave ovens aren’t typically operating continuously. However, you still should consider them a source of interference that can dramatically slow wireless communications. Another source of interruption to wireless networks operating in the 2.4GHz radio spectrum is other consumer devices, such as 2.4GHz portable telephones, as well as camera devices that can be used to transmit video back to your PC. Consider this when deciding whether to use a wireless network that uses the same radio spectrum. Note that the newer 5.8GHz wireless telephones do not interfere with 802.11b, 802.11g, and Bluetooth devices because these operate in the 2.4GHz frequency band.
Wireless devices based on these two main standards can interfere with each other. It is beyond the scope of this chapter to discuss the heated debate going on about which technology is better adapted to avoid interference from another wireless device, be it 802.11a, b, g, or even Bluetooth. Each group of supporters can make arguments about the capability of their products to recover from interference, but at this point, there isn’t enough data or testing to prove it one way or the other.
In a business environment, however, other sources of interference must be considered. For example, some companies use microwave lighting. In military installations, radar can cause interference. Magnetic resonance imaging (MRI) devices used in hospitals can interfere with wireless network products. When you get down to it, microwave technology is used in many industrial applications, so you might want to perform testing beforehand instead of just choosing a solution that appears on the surface to solve your networking problem. Interference can be mitigated, in some cases, by simply placing additional APs so that mobile devices are closer to an AP. The farther away from an AP or a home base unit, the weaker the signal and, thus, the greater the chance for interference. As an alternative, many recent APs are designed to use replaceable antennas. You can replace the normal antennas with high-gain omni-directional antennas designed to improve range in all directions, or replace them with directional antennas to improve range in a particular direction.